- Table of Contents
-
- H3C Low-End and Mid-Range Ethernet Switches Configuration Examples(V1.01)
- 00-1Cover
- 01-Login Configuration Guide
- 02-VLAN Configuration Guide
- 03-GVRP Configuration Guide
- 04-Voice VLAN Configuration Guide
- 05-IP Addressing and Performance Configuration Guide
- 06-QinQ Configuration Guide
- 07-BPDU Tunnel Configuration Guide
- 08-VLAN Mapping Configuration Guide
- 09-MAC Address Table Management Configuration Guide
- 10-Link Aggregation Configuration Guide
- 11-IP Source Guard Configuration Guide
- 12-DLDP Configuration Guide
- 13-MSTP Configuration Guide
- 14-IPv4 Routing Configuration Guide
- 15-IPv6 Configuration Guide
- 16-IPv6 Routing Configuration Guide
- 17-IPv4 Multicast Configuration Guide
- 18-IPv6 Multicast Configuration Examples
- 19-802.1x Configuration Guide
- 20-AAA Configuration Guide
- 21-MAC Authentication Configuration Guide
- 22-Portal Configuration Guide
- 23-ARP Configuration Guide
- 24-DHCP Configuration Guide
- 25-ACL Configuration Guide
- 26-QoS Configuration Guide
- 27-Port Mirroring Configuration Guide
- 28-Cluster Management Configuration Guide
- 29-SNMP-RMON Configuration Guide
- 30-NTP Configuration Guide
- 31-FTP-TFTP Configuration Guide
- 32-UDP Helper Configuration Guide
- 33-Information Center Configuration Guide
- 34-DNS Configuration Guide
- 35-File System Management Configuration Guide
- 36-Remote Upgrade Configuration Guide
- 37-NQA Configuration Guide
- 38-VRRP Configuration Guide
- 39-SSH Configuration Guide
- 40-Port Security Configuration Guide
- 41-Port Isolation Configuration Guide
- 42-LLDP Configuration Guide
- 43-MCE Configuration Guide
- 44-PoE Configuration Guide
- 45-OAM Configuration Guide
- 46-Connectivity Fault Detection Configuration Guide
- 47-RRPP Configuration Guide
- 48-sFlow Configuration Guide
- 49-SSL-HTTPS Configuration Guide
- 50-PKI Configuration Guide
- 51-Track Configuration Guide
- 52-EPON-OLT Configuration Guide
- 53-Smart Link Configuration Guide
- 54-MPLS Configuration Guide
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 50-PKI Configuration Guide | 100.72 KB |
Table of Contents
Requesting a Certificate from a CA Running RSA Keon
Networking and Configuration Requirements
Requesting a Certificate from a CA Running Windows 2003 Server
Networking and Configuration Requirements
Configuring a Certificate Attribute-Based Access Control Policy
Networking and Configuration Requirements
Requesting a Certificate from a CA Running RSA Keon
The Public Key Infrastructure (PKI) is a hierarchical framework designed for providing information security through public key technologies and digital certificates and verifying the identities of the digital certificate owners.
PKI employs digital certificates, which are bindings of certificate owner identity information and public keys. It allows users to obtain certificates, use certificates, and revoke certificates. By leveraging digital certificates and relevant services like certificate distribution and blacklist publication, PKI supports authenticating the entities involved in communication, and thus guaranteeing the confidentiality, integrity and non-repudiation of data.
Network Diagram
Figure 1-1 Request a certificate from a CA running RSA Keon
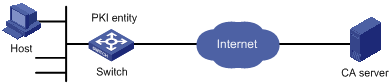
Networking and Configuration Requirements
![]()
In this example, the CA server runs the RSA Keon software.
Configure Switch to work as the PKI entity, so that:
l The device submits a local certificate request to the CA server.
l The device acquires the CRLs for certificate verification.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S3610 Series Ethernet Switches |
Release 5301 Release 5303 |
All versions |
|
S5510 Series Ethernet Switches |
Release 5301 Release 5303 |
All versions |
|
S5500-SI Series Ethernet Switches |
Release 1207 |
All versions (except S5500-20TP-SI) |
|
Release 1301 |
S5500-20TP-SI |
|
|
S5500-EI Series Ethernet Switches |
Release 2102 |
All versions |
Configuration Procedure
Configuring the CA server
1) Create a CA server named myca.
In this example, you need to configure these basic attributes on the CA server at first:
l Nickname: Name of the trusted CA.
l Subject DN: DN information of the CA, including the Common Name (CN), Organization Unit (OU), Organization (O), and Country (C).
The other attributes may be left using the default values.
2) Configure extended attributes.
3) Configure the CRL distribution behavior.
After completing the above configuration, you need to perform CRL related configurations.
In this example, select the local CRL distribution mode of HTTP and set the HTTP URL to http://4.4.4.133:447/myca.crl.
After the above configuration, make sure that the system clock of the device is synchronous to that of the CA, so that the device can request certificates and retrieve CRLs properly.
Configuring Switch
1) Configure the entity DN.
# Configure the entity name as aaa and the common name as Switch.
<Switch> system-view
[Switch] pki entity aaa
[Switch-pki-entity-aaa] common-name Switch
[Switch-pki-entity-aaa] quit
# Create PKI domain torsa and enter its view.
[Switch] pki domain torsa
# Configure the name of the trusted CA as myca.
[Switch-pki-domain-torsa] ca identifier myca
# Configure the URL of the registration server in the format of http://host:port/Issuing Jurisdiction ID, where Issuing Jurisdiction ID is a hexadecimal string generated on the CA server.
[Switch-pki-domain-torsa] certificate request url http://4.4.4.133:446/c95e970f632d27be5e8cbf80e971d9c4a9a93337
# Set the registration authority to CA.
[Switch-pki-domain-torsa] certificate request from ca
# Specify the entity for certificate request as aaa.
[Switch-pki-domain-torsa] certificate request entity aaa
# Configure the URL for the CRL distribution point.
[Switch-pki-domain-torsa] crl url http://4.4.4.133:447/myca.crl
[Switch-pki-domain-torsa] quit
3) Generate a local key pair using RSA.
[Switch] public-key local create rsa
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
It may take a few minutes.
Press CTRL+C to abort.
Input the bits in the modulus [default = 1024]:
Generating keys...
........++++++
....................................++++++
.......++++++++
......................++++++++
.
4) Apply for certificates.
# Retrieve the CA certificate and save it locally.
[Switch] pki retrieval-certificate ca domain torsa
Retrieving CA/RA certificates. Please wait a while......
The trusted CA's finger print is:
MD5 fingerprint:EDE9 0394 A273 B61A F1B3 0072 A0B1 F9AB
SHA1 fingerprint: 77F9 A077 2FB8 088C 550B A33C 2410 D354 23B2 73A8
Is the finger print correct?(Y/N):y
Saving CA/RA certificates chain, please wait a moment......
CA certificates retrieval success.
# Retrieve CRLs and save them locally.
[Switch] pki retrieval-crl domain torsa
Connecting to server for retrieving CRL. Please wait a while.....
CRL retrieval success!
# Request a local certificate manually.
[Switch] pki request-certificate domain torsa challenge-word
Certificate is being requested, please wait......
Enrolling the local certificate,please wait a while......
Certificate request Successfully!
Saving the local certificate to device......
Done!
5) Verify your configuration.
# Use the following command to view information about the local certificate acquired.
<Switch> display pki certificate local domain torsa
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
9A96A48F 9A509FD7 05FFF4DF 104AD094
Signature Algorithm: sha1WithRSAEncryption
Issuer:
C=cn
O=org
OU=test
CN=myca
Validity
Not Before: Jan 8 09:26:53 2007 GMT
Not After : Jan 8 09:26:53 2008 GMT
Subject:
CN=Switch
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00D67D50 41046F6A 43610335 CA6C4B11
F8F89138 E4E905BD 43953BA2 623A54C0
EA3CB6E0 B04649CE C9CDDD38 34015970
981E96D9 FF4F7B73 A5155649 E583AC61
D3A5C849 CBDE350D 2A1926B7 0AE5EF5E
D1D8B08A DBF16205 7C2A4011 05F11094
73EB0549 A65D9E74 0F2953F2 D4F0042F
19103439 3D4F9359 88FB59F3 8D4B2F6C
2B
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 CRL Distribution Points:
URI:http://4.4.4.133:447/myca.crl
Signature Algorithm: sha1WithRSAEncryption
836213A4 F2F74C1A 50F4100D B764D6CE
B30C0133 C4363F2F 73454D51 E9F95962
EDE9E590 E7458FA6 765A0D3F C4047BC2
9C391FF0 7383C4DF 9A0CCFA9 231428AF
987B029C C857AD96 E4C92441 9382E798
8FCC1E4A 3E598D81 96476875 E2F86C33
75B51661 B6556C5E 8F546E97 5197734B
C8C29AC7 E427C8E4 B9AAF5AA 80A75B3C
You can also use some other display commands to view detailed information about the CA certificate and CRLs. Refer to the parts related to display pki certificate ca domain and display pki crl domain commands.
Complete Configuration
#
pki entity aaa
common-name Switch
#
pki domain torsa
ca identifier myca
certificate request url http://4.4.4.133:446/c95e970f632d27be5e8cbf80e971d9c4a9a93337
certificate request from ca
certificate request entity aaa
crl url http://4.4.4.133:447/myca.crl
#
Configuration Guidelines
l The SCEP plug-in is not required when RSA Keon is used. In this case, when configuring a PKI domain, you need to use the certificate request from ca command to specify that the entity requests a certificate from a CA.
l If a PKI domain already has a local certificate, creating an RSA key pair will result in inconsistency between the key pair and the certificate. To generate a new RSA key pair, delete the local certificate and then issue the public-key local create rsa command.
l If a PKI domain has already a local certificate, you cannot request another certificate for it. This is to avoid inconsistency between the certificate and the registration information resulting from configuration changes. To request a new certificate, use the pki delete-certificate command to delete the existing local certificate and the CA certificate stored locally at first.
l When it is impossible to request a certificate from the CA through SCEP, you can save the request information by using the pki request-certificate domain command with the pkcs10 and filename keywords, and then send the file to the CA by an out-of-band means.
l Make sure the clocks of the entity and the CA are synchronous. Otherwise, the validity period of the certificate will be abnormal.
Requesting a Certificate from a CA Running Windows 2003 Server
The Public Key Infrastructure (PKI) is a hierarchical framework designed for providing information security through public key technologies and digital certificates and verifying the identities of the digital certificate owners.
PKI employs digital certificates, which are bindings of certificate owner identity information and public keys. It allows users to obtain certificates, use certificates, and revoke certificates. By leveraging digital certificates and relevant services like certificate distribution and blacklist publication, PKI supports authenticating the entities involved in communication, and thus guaranteeing the confidentiality, integrity and non-repudiation of data.
Network Diagram
Figure 1-2 Request a certificate from a CA running Windows 2003 server
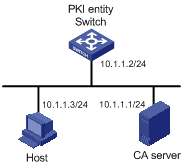
Networking and Configuration Requirements
![]()
In this example, the CA server runs the Windows 2003 server.
Configure PKI entity Switch to request a local certificate from the CA server.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S3610 Series Ethernet Switches |
Release 5301 Release 5303 |
All versions |
|
S5510 Series Ethernet Switches |
Release 5301 Release 5303 |
All versions |
|
S5500-SI Series Ethernet Switches |
Release 1207 |
All versions (except S5500-20TP-SI) |
|
Release 1301 |
S5500-20TP-SI |
|
|
S5500-EI Series Ethernet Switches |
Release 2102 |
All versions |
Configuration Procedure
Configuring the CA server
1) Install the certificate server suites.
From the start menu, select Control Panel > Add or Remove Programs, and then select Add/Remove Windows Components > Certificate Services and click Next to begin the installation.
2) Install the SCEP plug-in.
As a CA server running the Windows 2003 server does not support SCEP by default, you need to install the SCEP plug-in so that the switch can register and obtain its certificate automatically. After the SCEP plug-in installation completes, a URL is displayed, which you need to configure on the switch as the URL of the server for certificate registration.
3) Modify the certificate service attributes.
From the start menu, select Control Panel > Administrative Tools > Certificate Authority. If the CA server and SCEP plug-in have been installed successfully, there should be two certificates issued by the CA to the RA. Right-click on the CA server in the navigation tree and select Properties > Policy Module. Click Properties and then select Follow the settings in the certificate template, if applicable. Otherwise, automatically issue the certificate.
4) Modify the Internet Information Services (IIS) attributes.
From the start menu, select Control Panel > Administrative Tools > Internet Information Services (IIS) Manager and then select Web Sites from the navigation tree. Right-click on Default Web Site in the right pane and select Properties > Home Directory. Specify the path for certificate service in the Local path text box. In addition, you are recommended to specify an available port number as the TCP port number of the default Web site to avoid conflict with existing services.
After completing the above configuration, check that the system clock of the switch is synchronous to that of the CA server, ensuring that the switch can request a certificate normally.
Configuring Switch
1) Configure the entity DN.
# Configure the entity name as aaa and the common name as Switch.
<Switch> system-view
[Switch] pki entity aaa
[Switch-pki-entity-aaa] common-name Switch
[Switch-pki-entity-aaa] quit
2) Configure the PKI domain.
# Create PKI domain torsa and enter its view.
[Switch] pki domain torsa
# Configure the name of the trusted CA as myca.
[Switch-pki-domain-torsa] ca identifier myca
# Configure the URL of the registration server in the format of http://host:port/ certsrv/mscep/mscep.dll, where host:port indicates the IP address and port number of the CA server.
[Switch-pki-domain-torsa] certificate request url http://10.1.1.1:8080/certsrv/mscep/mscep.dll
# Set the registration authority to RA.
[Switch-pki-domain-torsa] certificate request from ra
# Specify the entity for certificate request as aaa.
[Switch-pki-domain-torsa] certificate request entity aaa
3) Generate a local key pair using RSA.
[Switch] public-key local create rsa
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
It may take a few minutes.
Press CTRL+C to abort.
Input the bits in the modulus [default = 1024]:
Generating keys...
........++++++
....................................++++++
.......++++++++
......................++++++++
.
4) Apply for certificates.
# Retrieve the CA certificate and save it locally.
[Switch] pki retrieval-certificate ca domain torsa
Retrieving CA/RA certificates. Please wait a while......
The trusted CA's finger print is:
MD5 fingerprint:766C D2C8 9E46 845B 4DCE 439C 1C1F 83AB
SHA1 fingerprint:97E5 DDED AB39 3141 75FB DB5C E7F8 D7D7 7C9B 97B4
Is the finger print correct?(Y/N):y
Saving CA/RA certificates chain, please wait a moment......
CA certificates retrieval success.
# Request a local certificate manually.
[Switch] pki request-certificate domain torsa challenge-word
Certificate is being requested, please wait......
Enrolling the local certificate,please wait a while......
Certificate request Successfully!
Saving the local certificate to device......
Done!
Verifying your configuration
# Use the following command to view information about the local certificate acquired.
<Switch> display pki certificate local domain torsa
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
48FA0FD9 00000000 000C
Signature Algorithm: sha1WithRSAEncryption
Issuer:
C=US
CN=CA server
Validity
Not Before: Nov 21 12:32:16 2007 GMT
Not After : Nov 21 12:42:16 2008 GMT
Subject:
CN=Switch
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00A6637A 8CDEA1AC B2E04A59 F7F6A9FE
5AEE52AE 14A392E4 E0E5D458 0D341113
0BF91E57 FA8C67AC 6CE8FEBB 5570178B
10242FDD D3947F5E 2DA70BD9 1FAF07E5
1D167CE1 FC20394F 476F5C08 C5067DF9
CB4D05E6 55DC11B6 9F4C014D EA600306
81D403CF 2D93BC5A 8AF3224D 1125E439
78ECEFE1 7FA9AE7B 877B50B8 3280509F
6B
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
B68E4107 91D7C44C 7ABCE3BA 9BF385F8 A448F4E1
X509v3 Authority Key Identifier:
keyid:9D823258 EADFEFA2 4A663E75 F416B6F6 D41EE4FE
DirName:CN=CA server,C=US
serial:3E02B7AA C80BBE8C 49899FD7 E5854B31
X509v3 CRL Distribution Points:
URI:http://l00192b/CertEnroll/CA%20server.crl
URI:file://\\l00192b\CertEnroll\CA server.crl
Authority Information Access:
CA Issuers - URI:http://l00192b/CertEnroll/l00192b_CA%20server.crt
CA Issuers - URI:file://\\l00192b\CertEnroll\l00192b_CA server.crt
1.3.6.1.4.1.311.20.2:
.0.I.P.S.E.C.I.n.t.e.r.m.e.d.i.a.t.e.O.f.f.l.i.n.e
Signature Algorithm: sha1WithRSAEncryption
81029589 7BFA1CBD 20023136 B068840B
(omitted)
You can also use some other display commands to view detailed information about the CA certificate. Refer to information related to the display pki certificate ca domain command.
Complete Configuration
#
pki entity aaa
common-name Switch
#
pki domain torsa
ca identifier myca
certificate request url http://10.1.1.1:8080/certsrv/mscep/mscep.dll
certificate request from ra
certificate request entity aaa
#
Configuration Guidelines
l The SCEP plug-in is required when you use the Windows Server as the CA. In this case, when configuring a PKI domain, you need to use the certificate request from ca command to specify that the entity requests a certificate from an RA.
l The Windows 2000 CA server has some restrictions on the data length of a certificate request. If the entity DN information in a certificate request goes beyond a certain limit, the server does not respond to the certificate request.
l If a PKI domain already has a local certificate, creating an RSA key pair will result in inconsistency between the key pair and the certificate. To generate a new RSA key pair, delete the local certificate and then issue the public-key local create rsa command.
l If a PKI domain has already a local certificate, you cannot request another certificate for it. This is to avoid inconsistency between the certificate and the registration information resulting from configuration changes. To request a new certificate, use the pki delete-certificate command to delete the existing local certificate and the CA certificate stored locally at first.
l When it is impossible to request a certificate from the CA through SCEP, you can save the request information by using the pki request-certificate domain command with the pkcs10 and filename keywords, and then send the file to the CA by an out-of-band means.
l Make sure the clocks of the entity and the CA are synchronous. Otherwise, the validity period of the certificate will be abnormal.
Configuring a Certificate Attribute-Based Access Control Policy
By configuring a certificate attribute-based access control policy, you can further control access to the server, providing additional security for the server.
Network Diagram
Figure 1-3 Configure a certificate attribute-based access control policy
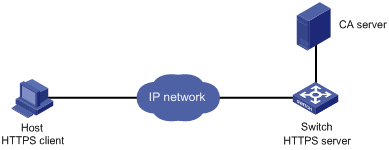
Networking and Configuration Requirements
![]()
The CA server runs RSA Keon in this configuration example.
l The client accesses the remote HTTP Security (HTTPS) server through the HTTPS protocol.
l SSL is configured to ensure that only legal clients log into the HTTPS server.
l Create a certificate attribute-based access control policy to control access to the HTTPS server.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S3610 Series Ethernet Switches |
Release 5301 Release 5303 |
All versions |
|
S5510 Series Ethernet Switches |
Release 5301 Release 5303 |
All versions |
|
S5500-SI Series Ethernet Switches |
Release 1207 |
All versions (except S5500-20TP-SI) |
|
Release 1301 |
S5500-20TP-SI |
|
|
S5500-EI Series Ethernet Switches |
Release 2102 |
All versions |
Configuration Procedure
![]()
The PKI domain to be referenced by the SSL policy must be created in advance.
1) Configure the PKI domain.
# Create PKI domain torsa and enter its view.
[Switch] pki domain torsa
# Configure the name of the trusted CA as myca.
[Switch-pki-domain-torsa] ca identifier myca
# Configure the URL of the registration server in the format of http://host:port/Issuing Jurisdiction ID, where Issuing Jurisdiction ID is a hexadecimal string generated on the CA server.
[Switch-pki-domain-torsa] certificate request url http://4.4.4.133:446/c95e970f632d27be5e8cbf80e971d9c4a9a93337
# Set the registration authority to CA.
[Switch-pki-domain-torsa] certificate request from ca
# Specify the entity for certificate request as aaa.
[Switch-pki-domain-torsa] certificate request entity aaa
# Configure the URL for the CRL distribution point.
[Switch-pki-domain-torsa] crl url http://4.4.4.133:447/myca.crl
[Switch-pki-domain-torsa] quit
2) Configure the HTTPS server.
# Configure the SSL policy for the HTTPS server to use.
<Switch> system-view
[Switch] ssl server-policy myssl
[Switch-ssl-server-policy-myssl] pki-domain torsa
[Switch-ssl-server-policy-myssl] client-verify enable
[Switch-ssl-server-policy-myssl] quit
3) Configure the certificate attribute group.
# Create certificate attribute group mygroup1 and add two attribute rules. The first rule defines that the DN of the subject name includes the string aabbcc, and the second rule defines that the IP address of the certificate issuer is 10.0.0.1.
[Switch] pki certificate attribute-group mygroup1
[Switch-pki-cert-attribute-group-mygroup1] attribute 1 subject-name dn ctn aabbcc
[Switch-pki-cert-attribute-group-mygroup1] attribute 2 issuer-name ip equ 10.0.0.1
[Switch-pki-cert-attribute-group-mygroup1] quit
# Create certificate attribute group mygroup2 and add two attribute rules. The first rule defines that the FQDN of the alternative subject name does not include the string of apple, and the second rule defines that the DN of the certificate issuer name includes the string aabbcc.
[Switch] pki certificate attribute-group mygroup2
[Switch-pki-cert-attribute-group-mygroup2] attribute 1 alt-subject-name fqdn nctn apple
[Switch-pki-cert-attribute-group-mygroup2] attribute 2 issuer-name dn ctn aabbcc
[Switch-pki-cert-attribute-group-mygroup2] quit
4) Configure the certificate attribute-based access control policy.
# Create the certificate attribute-based access control policy of myacp and add two access control rules.
[Switch] pki certificate access-control-policy myacp
[Switch-pki-cert-acp-myacp] rule 1 deny mygroup1
[Switch-pki-cert-acp-myacp] rule 2 permit mygroup2
[Switch-pki-cert-acp-myacp] quit
5) Apply the SSL server policy and certificate attribute-based access control policy to HTTPS service and enable HTTPS service.
# Apply SSL server policy myssl to HTTPS service.
[Switch] ip https ssl-server-policy myssl
# Apply the certificate attribute-based access control policy of myacp to HTTPS service.
[Switch] ip https certificate access-control-policy myacp
# Enable HTTPS service.
[Switch] ip https enable
Complete Configuration
#
pki domain torsa
ca identifier myca
certificate request url http://4.4.4.133:446/c95e970f632d27be5e8cbf80e971d9c4a9a93337
certificate request from ca
certificate request entity aaa
crl url http://4.4.4.133:447/myca.crl
#
pki certificate attribute-group mygroup1
attribute 1 subject-name dn ctn aabbcc
attribute 2 issuer-name ip equ 10.0.0.1
pki certificate attribute-group mygroup2
attribute 1 alt-subject-name fqdn nctn apple
attribute 2 issuer-name dn ctn aabbcc
#
pki certificate access-control-policy myacp
rule 1 deny mygroup1
rule 2 permit mygroup2
#
ssl server-policy myssl
pki-domain torsa
client-verify enable
#
ip https ssl-server-policy myssl
#
ip https certificate access-control-policy myacp
#
Configuration Guidelines
A certificate attribute group must exist to be associated with a rule.
