- Table of Contents
-
- H3C Low-End and Mid-Range Ethernet Switches Configuration Examples(V1.01)
- 00-1Cover
- 01-Login Configuration Guide
- 02-VLAN Configuration Guide
- 03-GVRP Configuration Guide
- 04-Voice VLAN Configuration Guide
- 05-IP Addressing and Performance Configuration Guide
- 06-QinQ Configuration Guide
- 07-BPDU Tunnel Configuration Guide
- 08-VLAN Mapping Configuration Guide
- 09-MAC Address Table Management Configuration Guide
- 10-Link Aggregation Configuration Guide
- 11-IP Source Guard Configuration Guide
- 12-DLDP Configuration Guide
- 13-MSTP Configuration Guide
- 14-IPv4 Routing Configuration Guide
- 15-IPv6 Configuration Guide
- 16-IPv6 Routing Configuration Guide
- 17-IPv4 Multicast Configuration Guide
- 18-IPv6 Multicast Configuration Examples
- 19-802.1x Configuration Guide
- 20-AAA Configuration Guide
- 21-MAC Authentication Configuration Guide
- 22-Portal Configuration Guide
- 23-ARP Configuration Guide
- 24-DHCP Configuration Guide
- 25-ACL Configuration Guide
- 26-QoS Configuration Guide
- 27-Port Mirroring Configuration Guide
- 28-Cluster Management Configuration Guide
- 29-SNMP-RMON Configuration Guide
- 30-NTP Configuration Guide
- 31-FTP-TFTP Configuration Guide
- 32-UDP Helper Configuration Guide
- 33-Information Center Configuration Guide
- 34-DNS Configuration Guide
- 35-File System Management Configuration Guide
- 36-Remote Upgrade Configuration Guide
- 37-NQA Configuration Guide
- 38-VRRP Configuration Guide
- 39-SSH Configuration Guide
- 40-Port Security Configuration Guide
- 41-Port Isolation Configuration Guide
- 42-LLDP Configuration Guide
- 43-MCE Configuration Guide
- 44-PoE Configuration Guide
- 45-OAM Configuration Guide
- 46-Connectivity Fault Detection Configuration Guide
- 47-RRPP Configuration Guide
- 48-sFlow Configuration Guide
- 49-SSL-HTTPS Configuration Guide
- 50-PKI Configuration Guide
- 51-Track Configuration Guide
- 52-EPON-OLT Configuration Guide
- 53-Smart Link Configuration Guide
- 54-MPLS Configuration Guide
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 49-SSL-HTTPS Configuration Guide | 49.61 KB |
Configuring SSL-HTTPS
As a security protocol, the Security Socket Layer (SSL) provides secure connections for TCP-based application layer protocols. For example, SSL can provide secure connections for the Hypertext Transfer Protocol (HTTP), that is, HTTP Security (HTTPS).
For a switch supporting the Web management function, after HTTP is enabled, the switch can act as a Web server to allow users to log in using HTTP, and access and control the switch through Web interfaces. However, HTTP cannot authenticate the Web server and cannot ensure the privacy of data transmission, thus unable to ensure security. Therefore, SSL is combined with HTTP to authenticate the client and the server, and encrypt the transmitted data, thus implementing secure management of the device.
HTTPS enhances the security of the device through the SSL protocol in the following ways:
l Uses the SSL protocol to ensure the legal clients to access the device securely and prohibit the illegal clients;
l Defines certificate attribute-based access control policy for the device to control the access right of the client, in order to further avoid attacks from illegal clients.
Network Diagram
Figure 1-1 Network diagram for SSL-HTTPS configuration
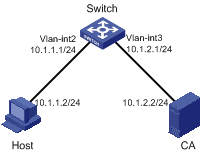
Networking and Configuration Requirements
l Switch acts as the HTTPS server;
l Host acts as the HTTPS client and accesses Switch through SSL-based HTTP;
l CA (Certificate Authority) issues certificates to Switch.
![]()
In this configuration example, Windows Server serves as CA and you need to install Simple Certificate Enrollment Protocol (SCEP) component on CA.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S3610 Series Ethernet Switches |
Release 5301 Release 5303 |
All versions |
|
S5510 Series Ethernet Switches |
Release 5301 Release 5303 |
All versions |
|
S5500-SI Series Ethernet Switches |
Release 1207 |
All versions (except S5500-20TP-SI) |
|
Release 1301 |
S5500-20TP-SI |
|
|
S5500-EI Series Ethernet Switches |
Release 2102 |
All versions |
Configuration Procedure
1) Apply for a certificate for Switch
# Configure a Public Key Infrastructure (PKI) entity.
<Sysname> system-view
[Sysname] pki entity en
[Sysname-pki-entity-en] common-name http-server1
[Sysname-pki-entity-en] fqdn ssl.security.com
[Sysname-pki-entity-en] quit
# Configure a PKI domain.
[Sysname] pki domain 1
[Sysname-pki-domain-1] ca identifier ca1
[Sysname-pki-domain-1] certificate request url http://10.1.2.2/certsrv/mscep/mscep.dll
[Sysname-pki-domain-1] certificate request from ra
[Sysname-pki-domain-1] certificate request entity en
[Sysname-pki-domain-1] quit
# Generate a key pair locally by using the RSA algorithm.
[Sysname] public-key local create rsa
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
It will take a few minutes.
Press CTRL+C to abort.
Input the bits of the modulus[default = 1024]:
Generating Keys...
.......++++++
.............++++++
............++++++++
....++++++++
.....
# Obtain a server certificate from CA.
[Sysname] pki retrieval-certificate ca domain 1
# Apply for a local certificate.
[Sysname] pki request-certificate domain 1
2) Configure an SSL server policy associated with the HTTPS service
# Configure an SSL server policy myssl.
[Sysname] ssl server-policy myssl
# Configure the PKI domain used on the SSL server policy as 1.
[Sysname-ssl-server-policy-myssl] pki-domain 1
# Enable client authentication on the server.
[Sysname-ssl-server-policy-myssl] client-verify enable
[Sysname-ssl-server-policy-myssl] quit
3) # Associate the HTTPS service with the SSL server policy and enable the HTTPS service.
# Configure the SSL policy used in HTTPS service as myssl.
[Sysname] ip https ssl-server-policy myssl
# Enable the HTTPS service.
[Sysname] ip https enable
4) Verify the configuration
Launch the IE explorer on Host, and enter https://10.1.1.1. You can log in to Switch and control it.
Complete Configuration
#
pki entity en
common-name http-server1
fqdn ssl.security.com
#
pki domain 1
ca identifier ca1
certificate request url http://10.1.2.2/certsrv/mscep/mscep.dll
certificate request from ra
certificate request entity en
#
ssl server-policy myssl
pki-domain 1
client-verify enable
#
ip https ssl-server-policy myssl
#
Configuration Guidelines
l Before configuring an SSL server policy, you need to configure a Public Key Infrastructure (PKI) domain first.
l In the case that you have configured the client-verify enable command on the server to authenticate the client using a certificate, if the certificate on the SSL client does not exist or cannot be trusted, you must apply for and install a certificate for the SSL client.
l If the certificate of the SSL server cannot be trusted, please install on the SSL client the root certificate of the CA server that issues a certificate for the SSL server, or re-apply for a certificate for the SSL server to the CA server trusted by the SSL client.
l You can use the display ssl server-policy command to view the encryption components supported by an SSL server policy. If the encryption components supported by the SSL server and client do not match, please use the ciphersuite command to modify the encryption components supported by the SSL server.
l When the HTTPS service is disabled, the association between the HTTPS service and the SSL server policy is automatically removed. To enable it again, you need to re-associate the HTTPS service with an SSL server policy.
l Enabling of the HTTPS service will trigger an SSL handshake negotiation process. During the process, if the local certificate of the device already exists, the SSL negotiation is successfully performed, and the HTTPS service can be started normally. If no local certificate exists, a certificate application process will be triggered by the SSL negotiation. Since the application process takes much time, the SSL negotiation may fail and thus the HTTPS service cannot be started normally. In this case, the ip https enable command must be executed for multiple times to ensure normal startup of the HTTPS service.
