- Table of Contents
-
- H3C Low-End and Mid-Range Ethernet Switches Configuration Examples(V1.01)
- 00-1Cover
- 01-Login Configuration Guide
- 02-VLAN Configuration Guide
- 03-GVRP Configuration Guide
- 04-Voice VLAN Configuration Guide
- 05-IP Addressing and Performance Configuration Guide
- 06-QinQ Configuration Guide
- 07-BPDU Tunnel Configuration Guide
- 08-VLAN Mapping Configuration Guide
- 09-MAC Address Table Management Configuration Guide
- 10-Link Aggregation Configuration Guide
- 11-IP Source Guard Configuration Guide
- 12-DLDP Configuration Guide
- 13-MSTP Configuration Guide
- 14-IPv4 Routing Configuration Guide
- 15-IPv6 Configuration Guide
- 16-IPv6 Routing Configuration Guide
- 17-IPv4 Multicast Configuration Guide
- 18-IPv6 Multicast Configuration Examples
- 19-802.1x Configuration Guide
- 20-AAA Configuration Guide
- 21-MAC Authentication Configuration Guide
- 22-Portal Configuration Guide
- 23-ARP Configuration Guide
- 24-DHCP Configuration Guide
- 25-ACL Configuration Guide
- 26-QoS Configuration Guide
- 27-Port Mirroring Configuration Guide
- 28-Cluster Management Configuration Guide
- 29-SNMP-RMON Configuration Guide
- 30-NTP Configuration Guide
- 31-FTP-TFTP Configuration Guide
- 32-UDP Helper Configuration Guide
- 33-Information Center Configuration Guide
- 34-DNS Configuration Guide
- 35-File System Management Configuration Guide
- 36-Remote Upgrade Configuration Guide
- 37-NQA Configuration Guide
- 38-VRRP Configuration Guide
- 39-SSH Configuration Guide
- 40-Port Security Configuration Guide
- 41-Port Isolation Configuration Guide
- 42-LLDP Configuration Guide
- 43-MCE Configuration Guide
- 44-PoE Configuration Guide
- 45-OAM Configuration Guide
- 46-Connectivity Fault Detection Configuration Guide
- 47-RRPP Configuration Guide
- 48-sFlow Configuration Guide
- 49-SSL-HTTPS Configuration Guide
- 50-PKI Configuration Guide
- 51-Track Configuration Guide
- 52-EPON-OLT Configuration Guide
- 53-Smart Link Configuration Guide
- 54-MPLS Configuration Guide
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 40-Port Security Configuration Guide | 122.75 KB |
Table of Contents
1 Port Security Configuration Guide
Configuring the Port Security autolearn Mode
Networking and Configuration Requirements
Configuring the userLoginWithOUI Mode
Networking and Configuration Requirements
Configuring the macAddressWithRadius Mode
Networking and Configuration Requirements
Configuring macAddressElseUserLoginSecure Mode
Networking and Configuration Requirements
Configuring the Port Security autolearn Mode
In the port security mode of autolearn, a port can learn a specified number of MAC addresses and save those addresses as secure MAC addresses. When the number of secure MAC addresses reaches the upper limit, the port changes to work in secure mode, and permits only frames whose source MAC addresses are secure MAC addresses or configured static MAC addresses.
Network Diagram
Figure 1-1 Network diagram for configuring the autolearn mode
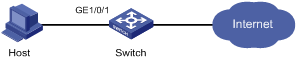
Networking and Configuration Requirements
Restrict port GigabitEthernet 1/01 of the switch as follows:
l Allow up to 64 users to access the port without authentication and permit the port to learn and add the MAC addresses of the users as secure MAC addresses.
l After the number of secure MAC addresses reaches 64, the port stops learning MAC addresses. If any frame with an unknown MAC address arrives, intrusion protection is triggered and the port is disabled for 30 seconds.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5500-SI Series Ethernet Switches |
Release 1207 |
All versions except for S5500-20TP-SI |
|
Release 1301 |
S5500-20TP-SI |
|
|
S5500-EI Series Ethernet Switches |
Release 2102 |
All versions |
|
S7500E Series Ethernet Switches |
Release 6300 |
All versions |
Configuration Procedure
1) Configure port security
# Enable port security.
<Switch> system-view
[Switch] port-security enable
# Enable intrusion protection trap.
[Switch] port-security trap intrusion
# Set the maximum number of secure MAC addresses allowed on the port to 64.
[Switch] interface GigabitEthernet 1/0/1
[Switch-GigabitEthernet1/0/1] port-security max-mac-count 64
# Set the port security mode to autoLearn.
[Switch-GigabitEthernet1/0/1] port-security port-mode autolearn
# Configure the port to be disabled for 30 seconds after the intrusion protection feature is triggered.
[Switch-GigabitEthernet1/0/1] port-security intrusion-mode disableport-temporarily
[Switch-GigabitEthernet1/0/1] quit
[Switch] port-security timer disableport 30
2) Verify the configuration
After completing the above configurations, you can use the following command to view the port security configuration information:
<Switch> display port-security interface gigabitethernet 1/0/1
Equipment port-security is enabled
Intrusion trap is enabled
Disableport Timeout: 30s
OUI value:
GigabitEthernet1/0/1 is link-up
Port mode is autoLearn
NeedToKnow mode is disabled
Intrusion Protection mode is DisablePortTemporarily
Max MAC address number is 64
Stored MAC address number is 0
Authorization is permitted
As shown in the output, the maximum number of secure MAC addresses allowed on the port is 64, the port security mode is autoLearn, the intrusion protection trap is enabled, and the intrusion protection action is to disable the port for 30 seconds.
You can also use the above command repeatedly to track the number of MAC addresses learned by the port, or use the display this command in interface view to display the secure MAC addresses learned, as shown below:
<Switch> system-view
[Switch] interface gigabitethernet 1/0/1
[Switch-GigabitEthernet1/0/1] display this
#
interface GigabitEthernet1/0/1
port-security max-mac-count 64
port-security port-mode autolearn
port-security mac-address security 0002-0000-0015 vlan 1
port-security mac-address security 0002-0000-0014 vlan 1
port-security mac-address security 0002-0000-0013 vlan 1
port-security mac-address security 0002-0000-0012 vlan 1
port-security mac-address security 0002-0000-0011 vlan 1
#
Issuing the display port-security interface command after the number of MAC addresses learned by the port reaches 64, you will see that the port security mode has changed to secure. When any frame with a new MAC address arrives, intrusion protection is triggered and you will see trap messages as follows:
#May 2 03:15:55:871 2000 Switch PORTSEC/1/VIOLATION:Traph3cSecureViolation
A intrusion occurs!
IfIndex: 9437207
Port: 9437207
MAC Addr: 0.2.0.0.0.21
VLAN ID: 1
IfAdminStatus: 1
In addition, you will see that the port security feature has disabled the port if you issue the following command:
<Switch-GigabitEthernet1/0/1> display interface gigabitethernet 1/0/1
GigabitEthernet1/0/1 current state: Port Security Disabled
IP Packet Frame Type: PKTFMT_ETHNT_2, Hardware Address: 000f-cb00-5558
Description: GigabitEthernet1/0/1 Interface
......
The port should be re-enabled 30 seconds later.
[Switch-GigabitEthernet1/0/1] display interface gigabitethernet 1/0/1
GigabitEthernet1/0/1 current state: UP
IP Packet Frame Type: PKTFMT_ETHNT_2, Hardware Address: 000f-cb00-5558
Description: GigabitEthernet1/0/1 Interface
......
Now, if you manually delete several secure MAC addresses, the port security mode of the port will be restored to autoLearn, and the port will be able to learn MAC addresses again.
Complete Configuration
#
port-security enable
port-security trap intrusion
port-security timer disableport 30
#
interface GigabitEthernet1/0/1
port-security max-mac-count 64
port-security port-mode autolearn
port-security intrusion-mode disableport-temporarily
#
Configuration Guidelines
l Before enabling port security, you need to disable 802.1x and MAC authentication globally.
l You cannot configure port security on a port configured with aggregation group.
l The maximum number of users a port supports is the lesser of the maximum number of secure MAC addresses or the maximum number of authenticated users the security mode supports.
l Port security cannot be disabled if there is any user present on a port.
Configuring the userLoginWithOUI Mode
In userLoginWithOUI mode, a port supports one 802.1x user as well as one user whose source MAC address has an OUI value among the specified ones.
Network Diagram
Figure 1-2 Network diagram for configuring the userLoginWithOUI mode
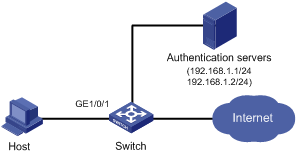
Networking and Configuration Requirements
The user (Host in the figure) is connected to the switch through port GigabitEthernet 1/0/1. The switch authenticates the user by the RADIUS server. If the authentication succeeds, the user is authorized to access the Internet.
Restrict port GigabitEthernet 1/0/1 of the switch as follows:
l Allow only one 802.1x user to be authenticated.
l Allow up to 16 OUI values to be configured and allow one additional user whose MAC address has an OUI among the configured ones to access the port.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5500-SI Series Ethernet Switches |
Release 1207 |
All versions except for S5500-20TP-SI |
|
Release 1301 |
S5500-20TP-SI |
|
|
S5500-EI Series Ethernet Switches |
Release 2102 |
All versions |
|
S7500ESeries Ethernet Switches |
Release 6300 |
All versions |
Configuration Procedure
![]()
l The following configuration steps cover some AAA/RADIUS configuration commands. For details about the commands, refer to AAA RADIUS HWTACACS Configuration.
l Configurations on the host and RADIUS servers are omitted.
1) Configure the RADIUS protocol
# Configure a RADIUS scheme named radsun.
<Switch> system-view
[Switch] radius scheme radsun
# Set the IP addresses of the primary authentication and accounting servers to 192.168.1.1 and 192.168.1.2 respectively.
[Switch-radius-radsun] primary authentication 192.168.1.1
[Switch-radius-radsun] primary accounting 192.168.1.2
# Set the IP addresses of the secondary authentication and accounting servers to 192.168.1.2 and 192.168.1.1 respectively.
[Switch-radius-radsun] secondary authentication 192.168.1.2
[Switch-radius-radsun] secondary accounting 192.168.1.1
# Set the encryption key for the switch to use when interacting with the authentication server to name.
[Switch-radius-radsun] key authentication name
# Set the encryption key for the switch to use when interacting with the accounting server to money.
[Switch-radius-radsun] key accounting money
# Set the RADIUS server response timeout time to five seconds and the maximum number of RADIUS packet transmission attempts to 5.
[Switch-radius-radsun] timer response-timeout 5
[Switch-radius-radsun] retry 5
# Set the interval at which the switch sends real-time accounting packets to the RADIUS server to 15 minutes.
[Switch-radius-radsun] timer realtime-accounting 15
# Specify that the switch sends user names without domain names to the RADIUS server.
[Switch-radius-radsun] user-name-format without-domain
[Switch-radius-radsun] quit
# Create an ISP domain named sun and enter its view.
[Switch] domain sun
# Configure the ISP domain to use RADIUS scheme radsun as its default RADIUS scheme.
[Switch-isp-sun] authentication default radius-scheme radsun
# Allow the ISP domain to accommodate up to 30 users.
[Switch-isp-sun] access-limit enable 30
[Switch-isp-sun] quit
2) Configure port security
# Enable port security.
[Switch] port-security enable
# Add five OUI values.
[Switch] port-security oui 1234-0100-1111 index 1
[Switch] port-security oui 1234-0200-1111 index 2
[Switch] port-security oui 1234-0300-1111 index 3
[Switch] port-security oui 1234-0400-1111 index 4
[Switch] port-security oui 1234-0500-1111 index 5
[Switch] interface GigabitEthernet 1/0/1
# Set the port security mode to userLoginWithOUI.
[Switch-GigabitEthernet1/0/1] port-security port-mode userlogin-withoui
3) Verify the configuration
After completing the above configurations, you can use the following command to view the configuration information of the RADIUS scheme radsun:
<Switch> display radius scheme radsun
SchemeName = radsun
Index = 0 Type = standard
Primary Auth IP = 192.168.1.1 Port = 1812 State = active
Primary Acct IP = 192.168.1.2 Port = 1813 State = active
Second Auth IP = 192.168.1.2 Port = 1812 State = active
Second Acct IP = 192.168.1.1 Port = 1813 State = active
Auth Server Encryption Key = name
Acct Server Encryption Key = money
Accounting-On packet disable, send times = 5 , interval = 3s
Interval for timeout(second) = 5
Retransmission times for timeout = 5
Interval for realtime accounting(minute) = 15
Retransmission times of realtime-accounting packet = 5
Retransmission times of stop-accounting packet = 500
Quiet-interval(min) = 5
Username format = without-domain
Data flow unit = Byte
Packet unit = one
Use the following command to view the configuration information of the ISP domain sun:
<Switch> display domain sun
Domain = sun
State = Active
Access-limit = 30
Accounting method = Required
Default authentication scheme : radius=radsun
Default authorization scheme : local
Default accounting scheme : local
Domain User Template:
Idle-cut = Disable
Self-service = Disable
Use the following command to view the port security configuration information:
<Switch> display port-security interface gigabitethernet 1/0/1
Equipment port-security is enabled
Trap is disabled
Disableport Timeout: 20s
OUI value:
Index is 1, OUI value is 123401
Index is 2, OUI value is 123402
Index is 3, OUI value is 123403
Index is 4, OUI value is 123404
Index is 5, OUI value is 123405
GigabitEthernet1/0/1 is link-up
Port mode is userLoginWithOUI
NeedToKnow mode is disabled
Intrusion Protection mode is NoAction
Max MAC address number is not configured
Stored MAC address number is 0
Authorization is permitted
After an 802.1x user gets online, you can see that the number of secure MAC addresses stored is 1. You can also use the following command to view information about 802.1x users:
<Switch> display dot1x interface gigabitethernet 1/0/1
Equipment 802.1X protocol is enabled
CHAP authentication is enabled
Configuration: Transmit Period 30 s, Handshake Period 15 s
Quiet Period 60 s, Quiet Period Timer is disabled
Supp Timeout 30 s, Server Timeout 100 s
The maximal retransmitting times 2
Total maximum 802.1X user resource number is 1024 per slot
Total current used 802.1X resource number is 1
GigabitEthernet1/0/1 is link-up
802.1X protocol is enabled
Handshake is enabled
The port is an authenticator
Authentication Mode is Auto
Port Control Type is Mac-based
Guest VLAN: 0
Max number of on-line users is 256
EAPOL Packet: Tx 16331, Rx 102
Sent EAP Request/Identity Packets : 16316
EAP Request/Challenge Packets: 6
EAP Success Packets: 4, Fail Packets: 5
Received EAPOL Start Packets : 6
EAPOL LogOff Packets: 2
EAP Response/Identity Packets : 80
EAP Response/Challenge Packets: 6
Error Packets: 0
1. Authenticated user : MAC address: 0002-0000-0011
Controlled User(s) amount to 1
In addition, the port allows an additional user whose MAC address has an OUI among the specified OUIs to access the port. You can use the following command to view the related information:
<Switch> display mac-address interface gigabitethernet 1/0/1
MAC ADDR VLAN ID STATE PORT INDEX AGING TIME(s)
1234-0300-0011 1 Learned GigabitEthernet1/0/1 AGING
--- 1 mac address(es) found ---
Complete Configuration
#
port-security enable
port-security oui 1234-0100-0000 index 1
port-security oui 1234-0200-0000 index 2
port-security oui 1234-0300-0000 index 3
port-security oui 1234-0400-0000 index 4
port-security oui 1234-0500-0000 index 5
#
radius scheme radsun
primary authentication 192.168.1.1
primary accounting 192.168.1.2
secondary authentication 192.168.1.2
secondary accounting 192.168.1.1
key authentication name
key accounting money
timer realtime-accounting 15
timer response-timeout 5
user-name-format without-domain
retry 5
#
domain sun
authentication default radius-scheme radsun
access-limit enable 30
#
interface GigabitEthernet1/0/1
port-security port-mode userlogin-withoui
#
Configuration Guidelines
l Before enabling port security, you need to disable 802.1x and MAC authentication globally.
l You cannot configure port security on a port configured with aggregation group.
l The maximum number of users a port supports is the lesser of the maximum number of secure MAC addresses or the maximum number of authenticated users the security mode supports.
l You can configure multiple OUI values.
l Port security cannot be disabled if there is any user present on a port.
Configuring the macAddressWithRadius Mode
In macAddressWithRadius mode, a port performs MAC authentication of users.
Network Diagram
Figure 1-3 Network diagram for configuring the macAddressWithRadius mode

Networking and Configuration Requirements
The user (Host in the figure) is connected to the switch through GigabitEthernet 1/0/1. The switch authenticates the user by the RADIUS server. If the authentication succeeds, the user is authorized to access the Internet.
Restrict port GigabitEthernet 1/0/1 of the switch as follows:
l Perform MAC authentication of users.
l All users belong to the default domain sun. Use the MAC address of a user as the username and password for MAC authentication of the user.
l Upon receiving packets from users that do not pass MAC authentication, trigger intrusion protection and drop such packets to ensure port security.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5500-SI Series Ethernet Switches |
Release 1207 |
All versions except for S5500-20TP-SI |
|
Release 1301 |
S5500-20TP-SI |
|
|
S5500-EI Series Ethernet Switches |
Release 2102 |
All versions |
|
S7500E Series Ethernet Switches |
Release 6300 |
All versions |
Configuration Procedure
![]()
l The following configuration steps cover some AAA/RADIUS configuration commands. For details about the commands, refer to AAA RADIUS HWTACACS Configuration.
l Configurations on the host and RADIUS servers are omitted.
1) Configure the RADIUS protocol
# Configure a RADIUS scheme named radsun.
<Switch> system-view
[Switch] radius scheme radsun
# Set the IP addresses of the primary authentication and accounting servers to 192.168.1.1 and 192.168.1.2 respectively.
[Switch-radius-radsun] primary authentication 192.168.1.1
[Switch-radius-radsun] primary accounting 192.168.1.2
# Set the IP addresses of the secondary authentication and accounting servers to 192.168.1.2 and 192.168.1.1 respectively.
[Switch-radius-radsun] secondary authentication 192.168.1.2
[Switch-radius-radsun] secondary accounting 192.168.1.1
# Set the encryption key for the switch to use when interacting with the authentication server to name.
[Switch-radius-radsun] key authentication name
# Set the encryption key for the switch to use when interacting with the accounting server to money.
[Switch-radius-radsun] key accounting money
# Set the RADIUS server response timeout time to five seconds and the maximum number of RADIUS packet transmission attempts to 5.
[Switch-radius-radsun] timer response-timeout 5
[Switch-radius-radsun] retry 5
# Set the interval at which the switch sends real-time accounting packets to the RADIUS server to 15 minutes.
[Switch-radius-radsun] timer realtime-accounting 15
# Specify that the switch sends user names without domain names to the RADIUS server.
[Switch-radius-radsun] user-name-format without-domain
[Switch-radius-radsun] quit
# Create an ISP domain named sun and enter its view.
[Switch] domain sun
# Configure the ISP domain to use RADIUS scheme radsun as its default RADIUS scheme.
[Switch-isp-sun] authentication default radius-scheme radsun
[Switch-isp-sun] quit
2) Configure port security
# Enable port security.
[Switch] port-security enable
# Configure the ISP domain for MAC authentication.
[Switch] mac-authentication domain sun
# Set the maximum number of secure MAC addresses allowed on the port to 64.
[Switch-GigabitEthernet1/0/1] port-security max-mac-count 64
# Set the port security mode to macAddressWithRadius.
[Switch-GigabitEthernet1/0/1] port-security port-mode mac-authentication
# Configure the intrusion protection feature as blockmac.
[Switch-GigabitEthernet1/0/1] port-security intrusion-mode blockmac
3) Verify the configuration
After the above configurations, you can use the following command to view the port security configuration information:
<Switch> display port-security interface gigabitethernet 1/0/1
Equipment port-security is enabled
Trap is disabled
Disableport Timeout: 20s
OUI value:
GigabitEthernet1/0/1 is link-up
Port mode is macAddressWithRadius
NeedToKnow mode is disabled
Intrusion Protection mode is BlockMacAddress
Max MAC address number is 64
Stored MAC address number is 1
Authorization is permitted
Use the following command to view the MAC authentication information:
<Switch> display mac-authentication interface gigabitethernet 1/0/1
MAC address authentication is enabled.
User name format is MAC address, like xxxxxxxxxxxx
Fixed username:mac
Fixed password:not configured
Offline detect period is 300s
Quiet period is 60s
Server response timeout value is 100s
The max allowed user number is 1024 per slot
Current user number amounts to 1
Current domain is sun
Silent MAC User info:
MAC Addr From Port Port Index
GigabitEthernet1/0/1 is link-up
MAC address authentication is enabled
Authenticate success: 1, failed: 0
Current online user number is 1
MAC Addr Authenticate State Auth Index
000f-3d80-2b38 MAC_AUTHENTICATOR_SUCCESS 11
In addition, as the blockmac intrusion protection feature is configured, upon receiving packets from users that do not pass MAC authentication, the switch will trigger intrusion protection and drop such packets to ensure port security..
Complete Configuration
#
port-security enable
#
mac-authentication domain sun
#
radius scheme radsun
primary authentication 192.168.1.1
primary accounting 192.168.1.2
secondary authentication 192.168.1.2
secondary accounting 192.168.1.1
key authentication name
key accounting money
timer realtime-accounting 15
timer response-timeout 5
user-name-format without-domain
retry 5
#
domain sun
authentication default radius-scheme radsun
#
interface GigabitEthernet1/0/1
port-security max-mac-count 64
port-security port-mode mac-authentication
port-security intrusion-mode blockmac
#
return
Configuration Guidelines
l Before enabling port security, you need to disable 802.1x and MAC authentication globally.
l You cannot configure port security on a port configured with aggregation group.
l The maximum number of users a port supports is the lesser of the maximum number of secure MAC addresses or the maximum number of authenticated users the security mode supports.
l Port security cannot be disabled if there is any user present on a port.
Configuring macAddressElseUserLoginSecure Mode
The macAddressElseUserLoginSecure mode is the combination of the macAddressWithRadius and userLoginSecure modes, with MAC authentication having a higher priority.
l Upon receiving a non-802.1x frame, a port in this mode performs only MAC authentication.
l Upon receiving an 802.1x frame, the port performs MAC authentication and then, if MAC authentication fails, 802.1x authentication.
Network Diagram
Figure 1-4 configure the macAddressElseUserLoginSecure mode

Networking and Configuration Requirements
The user (Host in the figure) is connected to the switch through GigabitEthernet 1/0/1. The switch authenticates the user by the RADIUS server. If the authentication succeeds, the client is authorized to access the Internet.
Restrict port GigabitEthernet 1/0/1 of the switch as follows:
l Allow more than one MAC authenticated user to log on.
l For 802.1x users, perform MAC authentication first and then, if MAC authentication fails, 802.1x authentication. Allow only one 802.1x user to log on.
l Configure the MAC authentication username type as fixed username. Set the total number of MAC authenticated users and 802.1x-authenticated user to 64.
l Enable NeedToKnow (NTK) to prevent frames from being sent to unknown MAC addresses.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5500-SI Series Ethernet Switches |
Release 1207 |
All versions except for S5500-20TP-SI |
|
Release 1301 |
S5500-20TP-SI |
|
|
S5500-EI Series Ethernet Switches |
Release 2102 |
All versions |
|
S7500E Series Ethernet Switches |
Release 6300 |
All versions |
Configuration Procedure
![]()
l The following configuration steps cover some AAA/RADIUS configuration commands. For details about the commands, refer to AAA RADIUS HWTACACS Configuration.
l Configurations on the host and RADIUS servers are omitted.
1) Configure the RADIUS protocol
Create a RADIUS scheme named radsun.
<Switch> system-view
[Switch] radius scheme radsun
# Set the IP addresses of the primary authentication and accounting servers to 192.168.1.1 and 192.168.1.2 respectively.
[Switch-radius-radsun] primary authentication 192.168.1.1
[Switch-radius-radsun] primary accounting 192.168.1.2
# Set the IP addresses of the secondary authentication and accounting servers to 192.168.1.2 and 192.168.1.1 respectively.
[Switch-radius-radsun] secondary authentication 192.168.1.2
[Switch-radius-radsun] secondary accounting 192.168.1.1
# Set the encryption key for the switch to use when interacting with the authentication server to name.
[Switch-radius-radsun] key authentication name
# Set the encryption key for the switch to use when interacting with the accounting server to money.
[Switch-radius-radsun] key accounting money
# Set the RADIUS server response timeout time to five seconds and the maximum number of RADIUS packet transmission attempts to 5.
[Switch-radius-radsun] timer response-timeout 5
[Switch-radius-radsun] retry 5
# Set the interval at which the switch sends real-time accounting packets to the RADIUS server to 15 minutes.
[Switch-radius-radsun] timer realtime-accounting 15
# Specify that the switch sends user names without domain names to the RADIUS server.
[Switch-radius-radsun] user-name-format without-domain
[Switch-radius-radsun] quit
# Create an ISP domain named sun and enter its view.
[Switch] domain sun
# Configure the ISP domain to use RADIUS scheme radsun as its default RADIUS scheme.
[Switch-isp-sun] authentication default radius-scheme radsun
[Switch-isp-sun] quit
2) Configure port security
# Enable port security.
[Switch] port-security enable
# Configure the ISP domain for MAC authentication.
[Switch] mac-authentication domain sun
# Configure MAC authentication to work in fixed username mode, setting the user name and password to aaa and 123456 respectively.
[Switch] mac-authentication user-name-format fixed account aaa password simple 123456
[Switch] interface gigabitethernet 1/0/1
# Set the maximum number of secure MAC addresses allowed on the port to 64.
[Switch-GigabitEthernet1/0/1] port-security max-mac-count 64
# Set the port security mode to macAddressElseUserLoginSecure.
[Switch-GigabitEthernet1/0/1] port-security port-mode mac-else-userlogin-secure
# Set the NTK mode of the port to ntkonly.
[Switch-GigabitEthernet1/0/1] port-security ntk-mode ntkonly
3) Verify the configuration
After completing the above configurations, you can use the following command to view the port security configuration information:
<Switch> display port-security interface gigabitethernet 1/0/1
Equipment port-security is enabled
Trap is disabled
Disableport Timeout: 20s
OUI value:
GigabitEthernet1/0/1 is link-up
Port mode is macAddressElseUserLoginSecure
NeedToKnow mode is NeedToKnowOnly
Intrusion Protection mode is NoAction
Max MAC address number is 64
Stored MAC address number is 0
Authorization is permitted
Use the following command to view MAC authentication information:
<Switch> display mac-authentication interface gigabitethernet 1/0/1
MAC address authentication is enabled.
User name format is fixed account
Fixed username:aaa
Fixed password:123456
Offline detect period is 300s
Quiet period is 60s
Server response timeout value is 100s
The max allowed user number is 1024 per slot
Current user number amounts to 0
Current domain is sun
Silent MAC User info:
MAC Addr From Port Port Index
GigabitEthernet1/0/1 is link-up
MAC address authentication is enabled
Authenticate success: 3, failed: 1
Current online user number is 3
MAC Addr Authenticate State Auth Index
1234-0300-0011 MAC_AUTHENTICATOR_SUCCESS 13
1234-0300-0012 MAC_AUTHENTICATOR_SUCCESS 14
1234-0300-0013 MAC_AUTHENTICATOR_SUCCESS 15
Use the following command to view 802.1x authentication information:
<Switch> display dot1x interface gigabitethernet 1/0/1
Equipment 802.1X protocol is enabled
CHAP authentication is enabled
Configuration: Transmit Period 30 s, Handshake Period 15 s
Quiet Period 60 s, Quiet Period Timer is disabled
Supp Timeout 30 s, Server Timeout 100 s
The maximal retransmitting times 2
EAD quick deploy configuration:
EAD timeout: 30 m
The maximum 802.1X user resource number is 1024 per slot
Total current used 802.1X resource number is 1
GigabitEthernet1/0/1 is link-up
802.1X protocol is enabled
Handshake is enabled
The port is an authenticator
Authentication Mode is Auto
Port Control Type is Mac-based
802.1X Multicast-trigger is enabled
Guest VLAN: 0
Max number of on-line users is 256
EAPOL Packet: Tx 16331, Rx 102
Sent EAP Request/Identity Packets : 16316
EAP Request/Challenge Packets: 6
EAP Success Packets: 4, Fail Packets: 5
Received EAPOL Start Packets : 6
EAPOL LogOff Packets: 2
EAP Response/Identity Packets : 80
EAP Response/Challenge Packets: 6
Error Packets: 0
1. Authenticated user : MAC address: 0002-0000-0011
Controlled User(s) amount to 1
Complete Configuration
#
port-security enable
#
mac-authentication domain sun
mac-authentication user-name-format fixed account aaa password simple 123456
#
radius scheme radsun
primary authentication 192.168.1.1
primary accounting 192.168.1.2
secondary authentication 192.168.1.2
secondary accounting 192.168.1.1
key authentication name
key accounting money
timer realtime-accounting 15
timer response-timeout 5
user-name-format without-domain
retry 5
#
domain sun
authentication default radius-scheme radsun
#
interface GigabitEthernet1/0/1
port-security max-mac-count 64
port-security port-mode mac-else-userlogin-secure
port-security ntk-mode ntkonly
#
Configuration Guidelines
l Before enabling port security, you need to disable 802.1x and MAC authentication globally.
l You cannot configure port security on a port configured with aggregation group.
l The maximum number of users a port supports is the lesser of the maximum number of secure MAC addresses or the maximum number of authenticated users the security mode supports.
l On a port operating in either macAddressElseUserLoginSecure mode or macAddressElseUserLoginSecureExt mode, intrusion protection is triggered only after both MAC authentication and 802.1x authentication for the same frame fail.
