- Table of Contents
-
- H3C Low-End and Mid-Range Ethernet Switches Configuration Examples(V1.01)
- 00-1Cover
- 01-Login Configuration Guide
- 02-VLAN Configuration Guide
- 03-GVRP Configuration Guide
- 04-Voice VLAN Configuration Guide
- 05-IP Addressing and Performance Configuration Guide
- 06-QinQ Configuration Guide
- 07-BPDU Tunnel Configuration Guide
- 08-VLAN Mapping Configuration Guide
- 09-MAC Address Table Management Configuration Guide
- 10-Link Aggregation Configuration Guide
- 11-IP Source Guard Configuration Guide
- 12-DLDP Configuration Guide
- 13-MSTP Configuration Guide
- 14-IPv4 Routing Configuration Guide
- 15-IPv6 Configuration Guide
- 16-IPv6 Routing Configuration Guide
- 17-IPv4 Multicast Configuration Guide
- 18-IPv6 Multicast Configuration Examples
- 19-802.1x Configuration Guide
- 20-AAA Configuration Guide
- 21-MAC Authentication Configuration Guide
- 22-Portal Configuration Guide
- 23-ARP Configuration Guide
- 24-DHCP Configuration Guide
- 25-ACL Configuration Guide
- 26-QoS Configuration Guide
- 27-Port Mirroring Configuration Guide
- 28-Cluster Management Configuration Guide
- 29-SNMP-RMON Configuration Guide
- 30-NTP Configuration Guide
- 31-FTP-TFTP Configuration Guide
- 32-UDP Helper Configuration Guide
- 33-Information Center Configuration Guide
- 34-DNS Configuration Guide
- 35-File System Management Configuration Guide
- 36-Remote Upgrade Configuration Guide
- 37-NQA Configuration Guide
- 38-VRRP Configuration Guide
- 39-SSH Configuration Guide
- 40-Port Security Configuration Guide
- 41-Port Isolation Configuration Guide
- 42-LLDP Configuration Guide
- 43-MCE Configuration Guide
- 44-PoE Configuration Guide
- 45-OAM Configuration Guide
- 46-Connectivity Fault Detection Configuration Guide
- 47-RRPP Configuration Guide
- 48-sFlow Configuration Guide
- 49-SSL-HTTPS Configuration Guide
- 50-PKI Configuration Guide
- 51-Track Configuration Guide
- 52-EPON-OLT Configuration Guide
- 53-Smart Link Configuration Guide
- 54-MPLS Configuration Guide
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 25-ACL Configuration Guide | 186.86 KB |
Table of Contents
1 IPv4 ACL Configuration Guide
Networking and Configuration Requirements
Configuring an Advanced IPv4 ACL
Networking and Configuration Requirements
Configuring an Ethernet Frame Header ACL
Networking and Configuration Requirements
Configuring a User-Defined ACL and a Flow Template
Networking and Configuration Requirements
2 IPv6 ACL Configuration Guide
Networking and Configuration Requirements
Configuring an Advanced IPv6 ACL
Networking and Configuration Requirements
Configuring a Basic IPv4 ACL
Basic IPv4 ACLs match packets based on only source IP address. They are numbered from 2000 to 2999.
Network Diagram
Figure 1-1 Network diagram for basic IPv4 ACL configuration
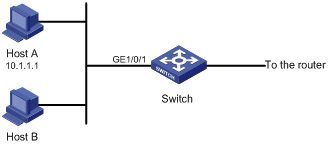
Networking and Configuration Requirements
Host A and Host B are connected to interface GigabitEthernet 1/0/1 of the switch (taking an S5500-EI as an example). The IP address of Host A is 10.1.1.1. Configure a basic IPv4 ACL, so that the switch permits only packets from Host A to pass from 8:00 to 18:00 every day.
Applicable Product Matrix
|
Product series |
Software version |
|
|
S3610 Series Ethernet Switches |
Release 5301, Release 5303 |
All versions |
|
S5510 Series Ethernet Switches |
Release 5301, Release 5303 |
All versions |
|
S5500-SI Series Ethernet Switches |
Release 1207 |
All versions except S5500-20TP-SI |
|
Release 1301 |
S5500-20TP-SI |
|
|
S5500-EI Series Ethernet Switches |
Release 2102 |
All versions |
|
S7500E Series Ethernet Switches |
Release 6100, Release 6300 |
All versions |
Configuration Procedure
# Create a periodic time range that is active from 8:00 to 18:00 every day.
<Switch> system-view
[Switch] time-range trname 8:00 to 18:00 daily
# Create basic IPv4 ACL 2000 and configure a rule for packets with the source address of 10.1.1.1.
[Switch] acl number 2000
[Switch-acl-basic-2000] rule permit source 10.1.1.1 0 time-range trname
[Switch-acl-basic-2000] quit
# Create basic IPv4 ACL 2001 and configure a rule for all packets.
[Switch] acl number 2001
[Switch-acl-basic-2001] rule deny time-range trname
[Switch-acl-basic-2001] quit
# Create class classifier_hostA and configure it to use IPv4 ACL 2000 for traffic classification.
[Switch] traffic classifier classifier_hostA
[Switch-classifier-classifier_hostA] if-match acl 2000
[Switch-classifier-classifier_hostA] quit
# Create traffic behavior behavior_hostA and configure the traffic filtering action as permit.
[Switch] traffic behavior behavior_hostA
[Switch-behavior-behavior_hostA] filter permit
[Switch-behavior-behavior_hostA] quit
# Create class classifier_hostB and configure it to use IPv4 ACL 2001 for traffic classification.
[Switch] traffic classifier classifier_hostB
[Switch-classifier-classifier_hostB] if-match acl 2001
[Switch-classifier-classifier_hostB] quit
# Create traffic behavior behavior_hostB and configure the traffic filtering action as deny.
[Switch] traffic behavior behavior_hostB
[Switch-behavior-behavior_hostB] filter deny
[Switch-behavior-behavior_hostB] quit
# Create policy policy_host and associate class classifier_hostA with traffic behavior behavior_hostA and class classifier_hostB with traffic behavior behavior_hostB respectively. Note that you need to configure actions filter permit and filter deny in different classifier-behavior associations in the correct order to achieve the expected result after applying the policy.
[Switch] qos policy policy_host
[Switch-qospolicy-policy_host] classifier classifier_hostA behavior behavior_hostA
[Switch-qospolicy-policy_host] classifier classifier_hostB behavior behavior_hostB
[Switch-qospolicy-policy_host] quit
# Apply policy policy_host to interface GigabitEthernet 1/0/1.
[Switch] interface GigabitEthernet 1/0/1
[Switch-GigabitEthernet1/0/1] qos apply policy policy_host inbound
Complete Configuration
#
traffic classifier classifier_hostB operator and
if-match acl 2001
traffic classifier classifier_hostA operator and
if-match acl 2000
#
traffic behavior behavior_hostB
filter deny
traffic behavior behavior_hostA
filter permit
#
qos policy policy_host
classifier classifier_hostA behavior behavior_hostA
classifier classifier_hostB behavior behavior_hostB
#
time-range trname 08:00 to 18:00 daily
#
acl number 2000
rule 0 permit source 10.1.1.1 0 time-range trname
acl number 2001
rule 0 deny time-range trname
#
interface GigabitEthernet1/0/1
qos apply policy policy_host inbound
#
Configuration Guidelines
When configuring a basic IPv4 ACL, note that:
l You can only modify the existing rules of an ACL that uses the match order of config. When modifying a rule of such an ACL, you may choose to change just some of the settings, in which case the other settings remain unchanged.
l You cannot create a rule with, or modify a rule to have, the same permit/deny statement as an existing rule in the ACL.
l For a basic IPv4 ACL using the match order of auto, a newly added rule will be inserted among the existing rules according to the depth-first match principles. However, the numbers of all rules will remain unchanged.
l When a basic IPv4 ACL is referenced by a QoS policy for traffic classification, actions specified in its rules, whether permit or deny, do not take effect. Packets matching the ACL will be processed according to the action defined by the traffic behavior in the QoS policy.
l When a basic IPv4 ACL is referenced by a QoS policy for traffic classification, some of its parameters may not be supported, depending on the device model.
Table 1-1 Unsupported parameters
|
Product series |
Unsupported parameters |
|
S3610 Series Ethernet Switches |
logging |
|
S5510 Series Ethernet Switches |
logging |
|
S5500-SI Series Ethernet Switches |
logging |
|
S5500-EI Series Ethernet Switches |
logging |
|
S7500E Series Ethernet Switches |
logging and vpn-instance |
Configuring an Advanced IPv4 ACL
Advanced IPv4 ACLs match packets based on source IP address, destination IP address, protocol carried over IP, and other protocol header fields such as the TCP/UDP source port number, TCP/UDP destination port number, ICMP message type, and ICMP message code.
In addition, advanced IPv4 ACLs allow you to match packets based on three priority criteria: type of service (ToS), IP precedence, and differentiated services codepoint (DSCP) priority.
Advanced IPv4 ACLs are numbered in the range 3000 to 3999. Compared with basic IPv4 ACLs, they allow of more flexible and accurate filtering.
Network Diagram
Figure 1-2 Network diagram for advanced IPv4 ACL configuration
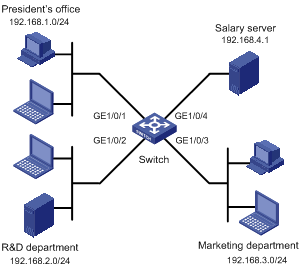
Networking and Configuration Requirements
A company interconnects its departments through a switch, an S5500-EI, for example. Configure an advanced IPv4 ACL to deny access from the R&D department and marketing department to the salary server during office hours (from 8:00 to 18:00) on working days, while allowing the president’s office to access the salary server at any time.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S3610 Series Ethernet Switches |
Release 5301, Release 5303 |
All versions |
|
S5510 Series Ethernet Switches |
Release 5301, Release 5303 |
All versions |
|
S5500-SI Series Ethernet Switches |
Release 1207 |
All versions except S5500-20TP-SI |
|
Release 1301 |
S5500-20TP-SI |
|
|
S5500-EI Series Ethernet Switches |
Release 2102 |
All versions |
|
S7500E Series Ethernet Switches |
Release 6100, Release 6300 |
All versions |
Configuration Procedure
1) Create a time range for office hours
# Create a periodic time range from 8:00 to 18:00 on working days.
<Switch> system-view
[Switch] time-range trname 8:00 to 18:00 working-day
2) Define an ACL to control access to the salary server
# Define an ACL to control access of the R&D department to the salary server.
[Switch] acl number 3000
[Switch-acl-adv-3000] rule deny ip source 192.168.2.0 0.0.0.255 destination 192.168.4.1 0 time-range trname
[Switch-acl-adv-3000] quit
# Define an ACL to control access of the marketing department to the salary server.
[Switch] acl number 3001
[Switch-acl-adv-3001] rule deny ip source 192.168.3.0 0.0.0.255 destination 192.168.4.1 0 time-range trname
[Switch-acl-adv-3001] quit
# Create class classifier_rd and configure it to use IPv4 ACL 3000 for traffic classification.
[Switch] traffic classifier classifier_rd
[Switch-classifier-classifier_rd] if-match acl 3000
[Switch-classifier-classifier_rd] quit
# Create traffic behavior behavior_rd and configure the traffic filtering action as deny.
[Switch] traffic behavior behavior_rd
[Switch-behavior-behavior_rd] filter deny
[Switch-behavior-behavior_rd] quit
# Create class classifier_market and configure it to use IPv4 ACL 3001 for traffic classification.
[Switch] traffic classifier classifier_market
[Switch-classifier-classifier_market] if-match acl 3001
[Switch-classifier-classifier_market] quit
# Create traffic behavior behavior_market and configure the traffic filtering action as deny.
[Switch] traffic behavior behavior_market
[Switch-behavior-behavior_market] filter deny
[Switch-behavior-behavior_market] quit
# Create policy policy_rd and associate traffic class classifier_rd with traffic behavior behavior_rd.
[Switch] qos policy policy_rd
[Switch-qospolicy-policy_rd] classifier classifier_rd behavior behavior_rd
[Switch-qospolicy-policy_rd] quit
# Create policy policy_market and associate traffic class classifier_market with traffic behavior behavior_market.
[Switch] qos policy policy_market
[Switch-qospolicy-policy_market] classifier classifier_market behavior behavior_market
[Switch-qospolicy-policy_market] quit
# Apply policy policy_rd to interface GigabitEthernet 1/0/2.
[Switch] interface GigabitEthernet 1/0/2
[Switch-GigabitEthernet1/0/2] qos apply policy policy_rd inbound
[Switch-GigabitEthernet1/0/2] quit
# Apply policy policy_market to interface GigabitEthernet 1/0/3.
[Switch] interface GigabitEthernet 1/0/3
[Switch-GigabitEthernet1/0/3] qos apply policy policy_market inbound
Complete Configuration
#
traffic classifier classifier_market operator and
if-match acl 3001
traffic classifier classifier_rd operator and
if-match acl 3000
#
traffic behavior behavior_market
filter deny
traffic behavior behavior_rd
filter deny
#
qos policy policy_market
classifier classifier_market behavior behavior_market
qos policy policy_rd
classifier classifier_rd behavior behavior_rd
#
time-range trname 08:00 to 18:00 working-day
#
acl number 3000
rule 0 deny ip source 192.168.2.0 0.0.0.255 destination 192.168.4.1 0 time-range trname
acl number 3001
rule 0 deny ip source 192.168.3.0 0.0.0.255 destination 192.168.4.1 0 time-range trname
#
interface GigabitEthernet1/0/2
qos apply policy policy_rd inbound
#
interface GigabitEthernet1/0/3
qos apply policy policy_market inbound
#
Configuration Guidelines
When configuring an advanced IPv4 ACL, note that:
l You can only modify the existing rules of an ACL that uses the match order of config. When modifying a rule of such an ACL, you may choose to change just some of the settings, in which case the other settings remain unchanged.
l You cannot create a rule with, or modify a rule to have, the same permit/deny statement as an existing rule in the ACL.
l For an ACL using the match order of auto, a newly added rule will be inserted among the existing rules according to the depth-first match principles. However, the numbers of all rules will remain unchanged.
l When an advanced IPv4 ACL is referenced by a QoS policy for traffic classification, some of its parameters and operators may not be supported, depending on the device model. The following table details the restrictions.
Table 1-2 Unsupported parameters
|
Product series |
Unsupported parameters |
|
S3610 Series Ethernet Switches |
logging, reflective, and established |
|
S5510 Series Ethernet Switches |
logging, reflective, and established |
|
S5500-SI Series Ethernet Switches |
l logging, reflective, and established l Operator neq |
|
S5500-EI Series Ethernet Switches |
l Keywords logging and reflective and operator neq when the QoS policy is to be applied on the inbound direction l Keywords logging and reflective and operators gt, lt, neq, and range when the QoS policy is to be applied on the outbound direction |
|
S7500E Series Ethernet Switches |
l Keywords logging, reflective, and vpn-instance and operator neq when the QoS policy is to be applied on the inbound direction l Keywords logging, reflective, and vpn-instance and operators gt, lt, neq, and range when the QoS policy is to be applied on the outbound direction |
Configuring an Ethernet Frame Header ACL
Ethernet frame header ACLs match packets based on Layer 2 protocol header fields such as source MAC address, destination MAC address, 802.1p priority, and link layer protocol type. They are numbered in the range 4000 to 4999.
Network Diagram
Figure 1-3 Network diagram for Ethernet frame header ACL configuration
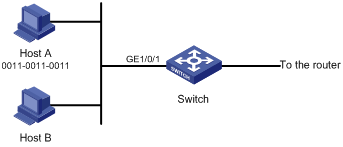
Networking and Configuration Requirements
Host A and Host B are connected to interface GigabitEthernet 1/0/1 of the switch (taking an S5500-EI as an example). The MAC address of Host A is 0011-0011-0011. Configure an Ethernet frame header ACL, so that the switch filters packets from Host A to MAC address 0011-0011-0012 from 8:00 to 18:00 every day.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S3610 Series Ethernet Switches |
Release 5301, Release 5303 |
All versions |
|
S5510 Series Ethernet Switches |
Release 5301, Release 5303 |
All versions |
|
S5500-SI Series Ethernet Switches |
Release 1207 |
All versions except S5500-20TP-SI |
|
Release 1301 |
S5500-20TP-SI |
|
|
S5500-EI Series Ethernet Switches |
Release 2102 |
All versions |
|
S7500E Series Ethernet Switches |
Release 6100, Release 6300 |
All versions |
Configuration Procedure
# Create a periodic time range that is active from 8:00 to 18:00 every day.
<Switch> system-view
[Switch] time-range trname 8:00 to 18:00 daily
# Create Ethernet frame header ACL 4000 and configure a rule for packets from 0011-0011-0011 to 0011-0011-0012.
[Switch] acl number 4000
[Switch-acl-basic-4000] rule deny source-mac 0011-0011-0011 ffff-ffff-ffff dest-mac 0011-0011-0012 ffff-ffff-ffff time-range trname
[Switch-acl-basic-4000] quit
# Create class classifier_hostA and configure it to use IPv4 ACL 4000 for traffic classification.
[Switch] traffic classifier classifier_hostA
[Switch-classifier-classifier_hostA] if-match acl 4000
[Switch-classifier-classifier_hostA] quit
# Create traffic behavior behavior_hostA and configure the traffic filtering action as deny.
[Switch] traffic behavior behavior_hostA
[Switch-behavior-behavior_hostA] filter deny
[Switch-behavior-behavior_hostA] quit
# Create policy policy_hostA and associate traffic class classifier_hostA with traffic behavior behavior_hostA.
[Switch] qos policy policy_hostA
[Switch-qospolicy-policy_hostA] classifier classifier_hostA behavior behavior_hostA
[Switch-qospolicy-policy_hostA] quit
# Apply policy policy_hostA to interface GigabitEthernet 1/0/1.
[Switch] interface GigabitEthernet 1/0/1
[Switch-GigabitEthernet1/0/1] qos apply policy policy_hostA inbound
Complete Configuration
#
traffic classifier classifier_hostA operator and
if-match acl 4000
#
traffic behavior behavior_hostA
filter deny
#
qos policy policy_hostA
classifier classifier_hostA behavior behavior_hostA
#
time-range trname 08:00 to 18:00 daily
#
acl number 4000
rule 0 deny source-mac 0011-0011-0011 ffff-ffff-ffff dest-mac 0011-0011-0012 ffff-ffff-ffff time-range trname
#
interface GigabitEthernet1/0/1
qos apply policy policy_hostA inbound
#
Configuration Guidelines
When configuring an Ethernet frame header ACL, note that:
l You can only modify the existing rules of an ACL that uses the match order of config. When modifying a rule of such an ACL, you may choose to change just some of the settings, in which case the other settings remain unchanged.
l You cannot create a rule with, or modify a rule to have, the same permit/deny statement as an existing rule in the ACL.
l For an ACL using the match order of auto, a newly added rule will be inserted among the existing rules according to the depth-first match principles. However, the numbers of all rules will remain unchanged.
l When an Ethernet frame header ACL is referenced by a QoS policy for traffic classification, actions specified in its rules, whether permit or deny, do not take effect. Packets matching the ACL will be processed according to the action defined by the traffic behavior in the QoS policy.
l When an Ethernet frame header ACL is referenced by a QoS policy for traffic classification, some of its parameters may not be supported, depending on the device model.
Table 1-3 Unsupported parameters
|
Product series |
Unsupported parameters |
|
S3610 Series Ethernet Switches |
lsap |
|
S5510 Series Ethernet Switches |
lsap |
|
S5500-SI Series Ethernet Switches |
lsap |
|
S5500-EI Series Ethernet Switches |
lsap |
|
S7500E Series Ethernet Switches |
lsap |
Configuring a User-Defined ACL and a Flow Template
User-defined ACLs allow you to customize rules based on information in protocol headers such as IP header. You can define a user-defined ACL to deny or permit packets in which a specified number of bytes after the specified offset (relative to the specified header) matches the specified match pattern after being ANDed with a match pattern mask.
User-defined ACLs are numbered in the range 5000 to 5999.
Flow templates are sets of criteria made based on header fields such as source IP address, destination IP address, source TCP port, and destination TCP port. They can be referenced by interfaces to restrict the header fields that can be used as the matching criteria in the ACLs to be referenced. When applying an ACL to an Ethernet interface configured with a flow template for QoS, make sure that the matching criteria defined in the ACL rules are all included in the flow template. Otherwise, the QoS function cannot reference the ACL.
Network Diagram
Figure 1-4 Diagram for user-defined ACL and flow template configuration
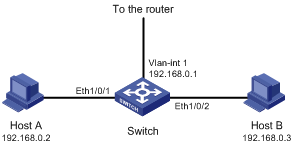
Networking and Configuration Requirements
l A company interconnects its departments through a switch, an S3610, for example. Host A has an IP address of 192.168.0.2, and is connected to interface Ethernet 1/0/1 of the switch. Host B has an IP address of 192.168.0.3, and is connected to interface Ethernet 1/0/2 of the switch.
l Both Host A and Host B belong to VLAN 1, and they have the same gateway address of 192.168.0.1, which is the IP address of the VLAN 1 interface. They access the Internet through the switch.
Configure a user-defined ACL to filter ARP packets that Host A sends using the IP address of the gateway.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S3610 Series Ethernet Switches |
Release 5301, Release 5303 |
All versions |
|
S5510 Series Ethernet Switches |
Release 5301, Release 5303 |
All versions |
Configuration Procedure
# Configure user-defined ACL 5000 to match ARP packets with the source IP address of 192.168.0.1.The characteristic of such packets is that the 13th and 14th bytes starting from the Layer 2 header are 0x0806 (representing the ARP protocol) and the four bytes after the 28th byte are c0a80001, the hexadecimal value of IP address 192.168.0.1.
<Switch> system-view
[Switch] acl number 5000
[Switch-acl-user-5000] rule deny L2 0806 ffff 12 start c0a80001 ffffffff 28
# Create extended user-defined flow template ftemplate_hostA.
[Switch] flow-template ftemplate_hostA extend L2 12 2 start 28 4
# Apply flow template ftemplate_hostA to interface Ethernet 1/0/1.
[Switch] interface Ethernet 1/0/1
[Switch-Ethernet1/0/1] flow-template ftemplate_hostA
[Switch-Ethernet1/0/1] quit
# Create class classifier_hostA and configure it to use user-defined ACL 5000 for traffic classification.
[Switch] traffic classifier classifier_hostA
[Switch-classifier-classifier_hostA] if-match acl 5000
[Switch-classifier-classifier_hostA] quit
# Create traffic behavior behavior_hostA and configure the traffic filtering action as deny.
[Switch] traffic behavior behavior_hostA
[Switch-behavior-behavior_hostA] filter deny
[Switch-behavior-behavior_hostA] quit
# Create policy policy_hostA and associate traffic class classifier_hostA with traffic behavior behavior_hostA.
[Switch] qos policy policy_hostA
[Switch-qospolicy-policy_hostA] classifier classifier_hostA behavior behavior_hostA
[Switch-qospolicy-policy_hostA] quit
# Apply policy policy_hostA to interface Ethernet 1/0/1.
[Switch] interface Ethernet 1/0/1
[Switch-Ethernet1/0/1] qos apply policy policy_hostA inbound
Complete Configuration
#
flow-template ftemplate_hostA extend start 28 4 l2 12 2
#
traffic classifier classifier_hostA operator and
if-match acl 5000
#
traffic behavior behavior_hostA
filter deny
#
qos policy policy_hostA
classifier classifier_hostA behavior behavior_hostA
#
acl number 5000
rule 0 deny start c0a80001 ffffffff 28 l2 0806 ffff 12
#
interface Ethernet1/0/1
flow-template ftemplate_hostA
qos apply policy policy_hostA inbound
#
Configuration Guidelines
When configuring a user-defined ACL, note that:
l Unlike other types of IPv4 ACLs, a user-defined ACL rule cannot be modified. However, you can create a new one to override the old one.
l You cannot create a rule with the same permit/deny statement as an existing rule in the ACL.
l The match order of a user-defined ACL can only be config.
l A user-defined ACL needs the cooperation of an extended user-defined flow template, and the offset range specified in the ACL must fall in the offset range specified in the flow template.
l When a user-defined ACL is referenced by a QoS policy for traffic classification, actions specified in its rules, whether permit or deny, do not take effect. Packets matching the ACL will be processed according to the action defined by the traffic behavior in the QoS policy.
When configuring a flow template, note that:
l S3610 and S5510 Series Ethernet Switches support both default flow templates and user-defined flow templates. The user-defined flow templates can be basic ones or extended ones.
l A basic flow template consists of elements corresponding to the packet fields. An extended one must cooperate with a user-defined ACL to match specified fields in packets.
l Flow templates apply to only hardware-based ACLs. They are ineffective for software-based ACLs.
l A user-defined flow template to be referenced must already exist. One interface can reference only one flow template.
l To apply a flow template to an interface successfully, be sure to disable the following features: 802.1x, cluster management, DHCP snooping, port isolation, MAC+IP+port binding, selective QinQ, and voice VLAN. Note that to disable the cluster management feature, you need to disable the Neighbor Discovery Protocol (NDP), Neighbor Topology Discovery Protocol (NTDP), Huawei Authentication Bypass Protocol (HABP), and the cluster function. In addition, you are not recommended to enable these features after applying a flow template to ports.
l On a port referencing an extended flow template, you cannot apply any QoS policy containing a basic or advanced ACL.
Table 1-4 Elements and their lengths
|
Name |
Description |
Number of bytes |
|
customer-cos |
User network 802.1p priority field |
1 |
|
customer-vlan-id |
User network VLAN ID field |
6 |
|
dip |
Destination IP address field in IP header |
0 |
|
dipv6 |
Destination IPv6 address field in IPv6 header |
10 |
|
dmac |
Destination MAC address field in Ethernet header |
6 |
|
dport |
Destination port field |
2 |
|
ethernet-protocol |
Protocol type field in Ethernet header |
4 |
|
dscp |
DSCP field in IP header |
1 |
|
ip-precedence |
IP precedence field in IP header |
|
|
tos |
ToS field in IP header |
|
|
fragments |
Fragmentation flag bit in IP header |
0 |
|
icmp-code |
ICMP code field |
2 |
|
icmp-type |
ICMP type field |
2 |
|
icmpv6-code |
ICMPv6 code field |
2 |
|
icmpv6-type |
ICMPv6 type field |
2 |
|
ip-protocol |
Protocol field in IP header |
0 |
|
ipv6-dscp |
DSCP field in IPv6 header |
1 |
|
ipv6-fragment |
IPv6 fragmentation flag field |
0 |
|
ipv6-protocol |
Protocol field in IPv6 header |
0 |
|
service-cos |
Provider network 802.1p priority field |
0 |
|
service-vlan-id |
Provider network VLAN ID field |
0 |
|
sip |
Source IP address field in IP header |
0 |
|
sipv6 |
Source IPv6 address field in IPv6 header |
0 |
|
smac |
Source MAC address field in Ethernet header |
6 |
|
sport |
Source port field |
2 |
|
tcp-flag |
Flag field in TCP header |
1 |
![]()
l The dscp, ip-precedence, and tos elements share the same one-byte space, no matter whether you specify one, two, or all of them.
l The icmp-code and icmp-type elements share the same 2-byte space when specified at the same time.
l The icmpv6-code and icmpv6-type elements share the same 2-byte space when specified at the same time.
l If you specify the icmp-code or icmp-type element together with the sport element, they share the same 2-byte space. If you specify the icmpv6-code or icmpv6-type element together with the sport element, they share the same 2-byte space.
Configuring a Basic IPv6 ACL
Basic IPv6 ACLs match packets based on only source IPv6 address. They are numbered in the range 2000 to 2999.
Network Diagram
Figure 2-1 Network diagram for basic IPv6 ACL configuration
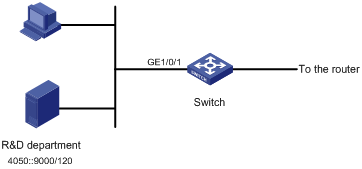
Networking and Configuration Requirements
A company interconnects its departments through a switch, an S5500-EI, for example.
Configure a basic IPv6 ACL to prohibit the R&D department at 4050::9000/120 from accessing the Internet.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S3610 Series Ethernet Switches |
Release 5301, Release 5303 |
All versions |
|
S5510 Series Ethernet Switches |
Release 5301, Release 5303 |
All versions |
|
S5500-SI Series Ethernet Switches |
Release 1207 |
All versions except S5500-20TP-SI |
|
Release 1301 |
S5500-20TP-SI |
|
|
S5500-EI Series Ethernet Switches |
Release 2102 |
All versions |
|
S7500E Series Ethernet Switches |
Release 6100, Release 6300 |
All versions |
Configuration Procedure
# Create basic IPv6 ACL 2000 and configure a rule for the R&D department.
<Switch> system-view
[Switch] acl ipv6 number 2000
[Switch-acl6-basic-2000] rule deny source 4050::9000/120
[Switch-acl6-basic-2000] quit
# Create class classifier_rd and configure it to use IPv6 ACL 2000 for traffic classification.
[Switch] traffic classifier classifier_rd
[Switch-classifier-classifier_rd] if-match acl ipv6 2000
[Switch-classifier-classifier_rd] quit
# Create traffic behavior behavior_rd and configure the traffic filtering action as deny.
[Switch] traffic behavior behavior_rd
[Switch-behavior-behavior_rd] filter deny
[Switch-behavior-behavior_rd] quit
# Create policy policy_rd and associate traffic class classifier_rd with traffic behavior behavior_rd.
[Switch] qos policy policy_rd
[Switch-qospolicy-policy_rd] classifier classifier_rd behavior behavior_rd
[Switch-qospolicy-policy_rd] quit
# Apply policy policy_rd to interface GigabitEthernet 1/0/1.
[Switch] interface GigabitEthernet 1/0/1
[Switch-GigabitEthernet1/0/1] qos apply policy policy_rd inbound
Complete Configuration
#
traffic classifier classifier_rd operator and
if-match acl ipv6 2000
#
traffic behavior behavior_rd
filter deny
#
qos policy policy_rd
classifier classifier_rd behavior behavior_rd
#
acl ipv6 number 2000
rule 0 deny source 4050::9000/120
#
interface GigabitEthernet1/0/1
qos apply policy policy_rd inbound
#
Configuration Guidelines
When configuring a basic IPv6 ACL, note that:
l You can only modify the existing rules of an ACL that uses the match order of config. When modifying a rule of such an ACL, you may choose to change just some of the settings, in which case the other settings remain unchanged.
l You cannot create a rule with, or modify a rule to have, the same permit/deny statement as an existing rule in the ACL.
l For an ACL using the match order of auto, a newly added rule will be inserted among the existing rules according to the depth-first match principles. However, the numbers of all rules will remain unchanged.
l When a basic IPv6 ACL is referenced by a QoS policy for traffic classification, actions specified in its rules, whether permit or deny, do not take effect. Packets matching the ACL will be processed according to the action defined by the traffic behavior in the QoS policy.
l When a basic IPv6 ACL is referenced by a QoS policy for traffic classification, some of its parameters may not be supported, depending on the device model.
Table 2-1 Unsupported parameters
|
Product series |
Unsupported parameters |
|
S3610 Series Ethernet Switches |
logging |
|
S5510 Series Ethernet Switches |
logging |
|
S5500-SI Series Ethernet Switches |
logging and fragment |
|
S5500-EI Series Ethernet Switches |
logging and fragment |
|
S7500E Series Ethernet Switches |
logging and fragment |
Configuring an Advanced IPv6 ACL
Advanced IPv6 ACLs match packets based on the source IPv6 address, destination IPv6 address, protocol carried over IPv6, and other protocol header fields such as the TCP/UDP source port number, TCP/UDP destination port number, ICMP message type, and ICMP message code.
Compared with basic IPv6 ACLs, they allow of more flexible and accurate filtering.
Advanced IPv6 ACLs are numbered in the range 3000 to 3999.
Network Diagram
Figure 2-2 Network diagram for advanced IPv6 ACL configuration
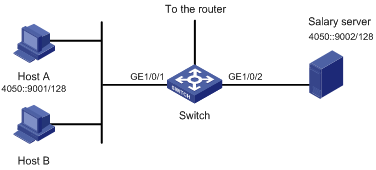
Networking and Configuration Requirements
A company interconnects its departments through a switch, an S5500-EI, for example. Host A and Host B are connected to interface GigabitEthernet 1/0/1 of the switch. The IP address of Host A is 4050::9001, and that of salary server is 4050::9002.
Configure an advanced IPv6 ACL to prohibit Host A from accessing the salary server.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S3610 Series Ethernet Switches |
Release 5301, Release 5303 |
All versions |
|
S5510 Series Ethernet Switches |
Release 5301, Release 5303 |
All versions |
|
S5500-SI Series Ethernet Switches |
Release 1207 |
All versions except S5500-20TP-SI |
|
Release 1301 |
S5500-20TP-SI |
|
|
S5500-EI Series Ethernet Switches |
Release 2102 |
All versions |
|
S7500E Series Ethernet Switches |
Release 6100, Release 6300 |
All versions |
Configuration Procedure
# Create advanced IPv6 ACL 3000 and configure a rule for Host A.
<Switch> system-view
[Switch] acl ipv6 number 3000
[Switch-acl6-adv-3000] rule deny ipv6 source 4050::9001 128 destination 4050::9002 128
[Switch-acl6-adv-3000] quit
# Create class classifier_hostA and configure it to use IPv6 ACL 3000 for traffic classification.
[Switch] traffic classifier classifier_hostA
[Switch-classifier-classifier_hostA] if-match acl ipv6 3000
[Switch-classifier-classifier_hostA] quit
# Create traffic behavior behavior_hostA and configure the traffic filtering action as deny.
[Switch] traffic behavior behavior_hostA
[Switch-behavior-behavior_hostA] filter deny
[Switch-behavior-behavior_hostA] quit
# Create policy policy_hostA and associate traffic class classifier_hostA with traffic behavior behavior_hostA.
[Switch] qos policy policy_hostA
[Switch-qospolicy-policy_hostA] classifier classifier_hostA behavior behavior_hostA
[Switch-qospolicy-policy_hostA] quit
# Apply policy policy_hostA to interface GigabitEthernet 1/0/1.
[Switch] interface GigabitEthernet 1/0/1
[Switch-GigabitEthernet1/0/1] qos apply policy policy_hostA inbound
Complete Configuration
#
traffic classifier classifier_hostA operator and
if-match acl ipv6 3000
#
traffic behavior behavior_hostA
filter deny
#
qos policy policy_hostA
classifier classifier_hostA behavior behavior_hostA
#
acl ipv6 number 3000
rule 0 deny ipv6 source 4050::9001/128 destination 4050::9002/128
#
interface GigabitEthernet1/0/1
qos apply policy policy_hostA inbound
#
Configuration Guidelines
When configuring an advanced IPv6 ACL, note that:
l You can only modify the existing rules of an ACL that uses the match order of config. When modifying a rule of such an ACL, you may choose to change just some of the settings, in which case the other settings remain unchanged.
l You cannot create a rule with, or modify a rule to have, the same permit/deny statement as an existing rule in the ACL.
l For an ACL using the match order of auto, a newly added rule will be inserted among the existing rules according to the depth-first match principles. However, the numbers of all rules will remain unchanged.
l When an advanced IPv6 ACL is referenced by a QoS policy for traffic classification, actions specified in its rules, whether permit or deny, do not take effect. Packets matching the ACL will be processed according to the action defined by the traffic behavior in the QoS policy.
l When an advanced IPv6 ACL is referenced by a QoS policy for traffic classification, some of its parameters and operators may not be supported, depending on the device model. The following table details the restrictions.
Table 2-2 Unsupported parameters
|
Product series |
Unsupported parameters |
|
S3610 Series Ethernet Switches |
l Keyword logging l Keyword fragment when protocol takes a value other than ipv6. |
|
S5510 Series Ethernet Switches |
l Keyword logging l Keyword fragment when protocol takes a value other than ipv6. |
|
S5500-SI Series Ethernet Switches |
l Keywords dscp, logging and fragment l Operator gt, lt, neq and range |
|
S5500-EI Series Ethernet Switches |
l Keywords logging and reflective and operator neq when the QoS policy is to be applied on the inbound direction l Keywords logging and reflective and operators gt, lt, neq, and range when the QoS policy is to be applied on the outbound direction |
|
S7500E Series Ethernet Switches |
l Keywords logging and reflective and operator neq when the QoS policy is to be applied on the inbound direction l Keywords logging and reflective and operators gt, lt, neq, and range when the QoS policy is to be applied on the outbound direction |
