- Table of Contents
-
- H3C MSR1000[2600][3600] Routers Configuration Examples All-in-One-R9141-6W100
- 00-Preface
- 01-Local 802.1X Authentication Configuration Examples
- 02-RADIUS-Based 802.1X Authentication Configuration Examples
- 03-AAA Configuration Examples
- 04-ACL Configuration Examples
- 05-MPLS over ADVPN Configuration Examples
- 06-ARP Attack Protection Configuration Examples
- 07-BFD Configuration Examples
- 08-Basic BGP Configuration Examples
- 09-BGP Route Attribute-Based Route Selection Configuration Examples
- 10-EAA Monitor Policy Configuration Examples
- 11-GRE with OSPF Configuration Examples
- 12-HoVPN Configuration Examples
- 13-IGMP Snooping Configuration Examples
- 14-IGMP Configuration Examples
- 15-IPsec Configuration Examples
- 16-IPsec Digital Certificate Authentication Configuration Examples
- 17-IPv6 IS-IS Configuration Examples
- 18-IPv6 over IPv4 GRE Tunnel Configuration Examples
- 19-IPv6 over IPv4 Manual Tunnel with OSPFv3 Configuration Examples
- 20-IS-IS Configuration Examples
- 21-Combined ISATAP Tunnel and 6to4 Tunnel Configuration Examples
- 22-L2TP over IPsec Configuration Examples
- 23-Multi-Instance L2TP Configuration Examples
- 24-L2TP Multidomain Access Configuration Examples
- 25-MPLS L3VPN Configuration Examples
- 26-MPLS OAM Configuration Examples
- 27-MPLS TE Configuration Examples
- 28-Basic MPLS Configuration Examples
- 29-NAT DNS Mapping Configuration Examples
- 30-NetStream Configuration Examples
- 31-NQA Configuration Examples
- 32-NTP Configuration Examples
- 33-OSPFv3 Configuration Examples
- 34-OSPF Configuration Examples
- 35-OSPF Multi-Process Configuration Examples
- 36-OSPF Multi-Instance Configuration Examples
- 37-Portal Configuration Examples
- 38-PPP Configuration Examples
- 39-RBAC Configuration Examples
- 40-RMON Configuration Examples
- 41-IPv4 NetStream Sampling Configuration Examples
- 42-SNMP Configuration Examples
- 43-SRv6 Configuration Examples
- 44-SSH Configuration Examples
- 45-Tcl Commands Configuration Examples
- 46-VLAN Configuration Examples
- 47-VRRP Configuration Examples
- 48-VXLAN over IPsec Configuration Examples
- 49-WLAN AC Configuration Examples
- 50-Small and Medium-Sized Store Configuration Examples
- 51-Cloudnet VPN Configuration Examples
- 52-Ethernet Link Aggregation Configuration Examples
- 53-Ethernet OAM Configuration Examples
- 54-Outbound Bidirectional NAT Configuration Examples
- 55-NAT Hairpin in C-S Mode Configuration Examples
- 56-Load Sharing NAT Server Configuration Examples
- 57-BIDIR-PIM Configuration Examples
- 58-Control Plane-Based QoS Policy Configuration Examples
- 59-Scheduling a Task Configuration Examples
- 60-Client-Initiated L2TP Tunnel Configuration Examples
- 61-LAC-Auto-Initiated L2TP Tunnel Configuration Examples
- 62-Authorized ARP Configuration Examples
- 63-GTS Configuration Examples
- 64-Traffic Policing Configuration Examples
- 65-Traffic Accounting Configuration Examples
- 66-Mobile Communication Modem Management Configuration Examples
- 67-Port Isolation Configuration Examples
- 68-PBR Configuration Examples
- 69-TFTP Client Software Upgrade Configuration Examples
- 70-FTP Client Software Upgrade Configuration Examples
- 71-FTP Server Software Upgrade Configuration Examples
- 72-Routing Policy Configuration Examples
- 73-Software Upgrade from the BootWare Menu Configuration Examples
- 74-Mirroring Configuration Examples
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 37-Portal Configuration Examples | 146.94 KB |
|
|
|
H3C Routers |
|
Portal Configuration Examples |
|
|
|
|
Copyright © 2024 New H3C Technologies Co., Ltd. All rights reserved
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Contents
Example: Configuring cross-subnet portal authentication
Configuring the RADIUS and portal server
Example: Configuring direct portal authentication
Configuring the RADIUS and portal server
Introduction
The following information provides examples for configuring cross-subnet portal authentication and direct portal authentication on routers.
· Cross-subnet authentication—Applies to networks where Layer 3 forwarding devices exist between the authentication client and the access device. After a user passes authentication on an interface, the access device generates an ACL for the user based on the user's IP address to permit packets from the user on the interface.
· Direct authentication—Applies to networks where no layer 3 forwarding devices exist between the authentication client and the access device. In such a network, the access device can learn MAC addresses of users. The access device can use both ACLs and MAC addresses to enhance control on user packet forwarding.
Prerequisites
The following information applies to Comware 9-based routers. Procedures and information in the examples might be slightly different depending on the software or hardware version of the routers.
The configuration examples were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
The following information is provided based on the assumption that you have basic knowledge of portal.
Example: Configuring cross-subnet portal authentication
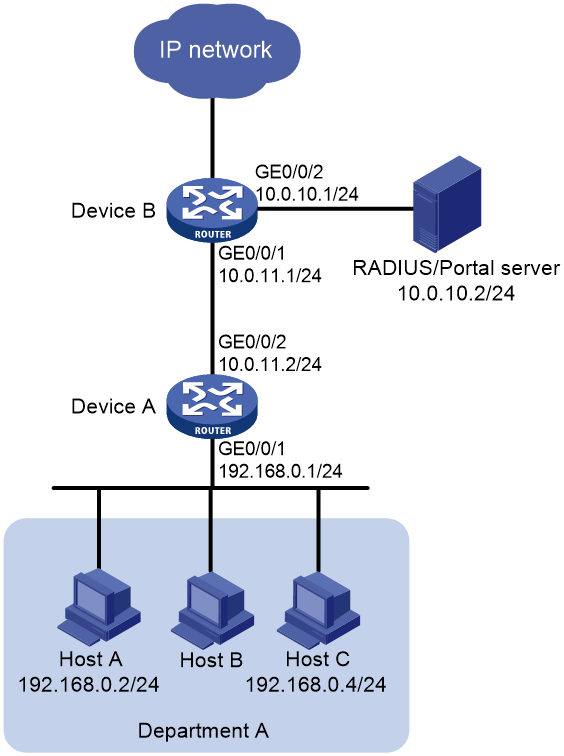
Network configuration
As shown in Figure 1, Device B supports portal authentication. An IMC server acts as the portal authentication server, the portal Web server, and the RADIUS server. Configure the network to meet the following requirements:
· Configure cross-subnet portal authentication.
· Before passing authentication, a host can access only the portal server. After passing authentication, the host can access resources in the IP network.
· Use the RADIUS server to perform authentication, authorization, and accounting on portal users.
· Configure the BAS-IP attribute for portal packets sent to the portal authentication server.
· Enable the RADIUS session control feature to listen and receive session control packets sent by the RADIUS server.
Analysis
· To perform portal authentication for access users from Department A, configure the portal server and enable portal authentication on Device B.
· To use RADIUS to perform authentication, authorization, and accounting for portal users, configure a RADIUS scheme on Device B and use it for authentication, authorization, and accounting and apply it to the ISP domain to which the portal users belongs.
· When a user enters a username without an ISP domain to log in, the user uses the authentication scheme in the default ISP domain.
Software versions used
This configuration example was created and verified on R9141P16 of the MSR2630E-X1 device.
Restrictions and guidelines
Only the RADIUS server can perform authentication, authorization, and accounting for portal users.
On the RADIUS server, configure routes to reach the authentication interfaces and user networks.
Procedures
Configuring the RADIUS and portal server
This example uses IMC as the RADIUS server, which runs IMC PLAT 7.0 (E0202) and IMC EIA 7.0 (E0202).
Adding an access device
1. Log in to IMC and click the User tab.
2. From the navigation pane, select User Access Policy > Access Device Management > Access Device.
3. Click Add.
4. In the Access Configuration area, configure the following parameters:
¡ Enter expert in the Shared Key and Confirm Shared Key fields.
¡ Enter 1812 and 1813 in the Authentication Port and Accounting Port fields, respectively.
¡ Select LAN Access Service from the Service Type list.
¡ Select H3C(General) from the Access Device Type list.
¡ In the Device List area, click Select or Add Manually to add the device at 10.0.10.1 as an access device.
¡ Use the default values for other parameters, and then click OK.
Adding an access policy
1. Click the User tab.
2. From the navigation tree, select User Access Manager > Access Policy.
3. Click Add.
4. On the page that opens, enter a policy name in the Access Policy Name field. This example uses portal.
5. Use the default settings for other parameters.
6. Click OK.
Adding an access service
1. Click the User tab.
2. From the navigation tree, select User Access Manager > Access Service.
3. Click Add.
4. On the page that opens, configure the following parameters:
¡ Enter a service name in the Service Name field. This example uses Portal-auth.
¡ Select portal from the Default Access Policy list.
¡ Use the default settings for other parameters.
¡ Click OK.
Adding an access user
1. Click the User tab.
2. From the navigation pane, select Access User > All Access Users.
3. Click Add.
4. On the page that opens, configure the following parameters:
¡ Enter a username in the User Name field. This example uses hello.
¡ Enter an identity number in the Identity Number field. This example uses 111111.
¡ Use the default settings for other parameters, and then click OK.
¡ In the Access Information area, enter portal in the Account Name field and configure the password for the account.
¡ In the Access Service area, select the access service named Portal-auth.
¡ Use the default settings for other parameters, and then click OK.
Configuring a portal page
1. Click the User tab.
2. From the navigation tree, select User Access Policy > Portal Service > Server.
3. Use the default settings for all parameters.
4. Click OK.
Adding an IP group
1. Click the User tab.
2. From the navigation tree, select User Access Policy > Portal Service > IP Group.
3. Click Add.
4. On the page that opens, configure the following parameters:
¡ Enter Portal_user in the IP Group Name field.
¡ Enter 192.168.0.0 in the Start IP field and 192.168.0.255 in the End IP field. Make sure the host IP address is in the IP group.
¡ Use the default settings for other parameters.
¡ Click OK.
Configuring an access device
1. Click the User tab.
2. From the navigation tree, select User Access Policy > Portal Service > Device.
3. Click Add.
4. On the page that opens, configure the following parameters:
¡ Enter NAS in the Device Name field.
¡ Enter the IP address of the device's interface connected to the access user in the IP Address field. This example uses 10.0.11.1.
¡ Enter portal in the Key and Confirm Key fields. The key must be the same as that for the portal authentication server configured on Device B.
¡ Select Layer 3 from the Access Method list.
¡ Use the default settings for other parameters, and then click OK.
Configuring a port group
1. On the User Access Policy > Portal Service > Device page, click the Port Group icon in the Operation column for the target portal device.
2. Click Add.
3. On the page that opens, configure the following parameters:
¡ Enter group in the Port Group Name field.
¡ Select Portal_user from the IP Group list.
¡ Use the default settings for other parameters, and then click OK.
Configuring Device A
# Assign IP addresses to GigabitEthernet 0/0/1 and GigabitEthernet 0/0/2.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 0/0/1
[DeviceA-GigabitEthernet0/0/1] ip address 192.168.0.1 24
[DeviceA-GigabitEthernet0/0/1] quit
[DeviceA] interface gigabitethernet 0/0/2
[DeviceA-GigabitEthernet0/0/2] ip address 10.0.11.2 24
[DeviceA-GigabitEthernet0/0/2] quit
# Configure a static route to 10.0.10.0/24 with 10.0.11.1 as the next hop.
[DeviceA] ip route-static 10.0.10.0 255.255.255.0 10.0.11.1
Configuring Device B
# Assign IP addresses to GigabitEthernet 0/0/1 and GigabitEthernet 0/0/2.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 0/0/1
[DeviceB-GigabitEthernet0/0/1] ip address 10.0.11.1 24
[DeviceB-GigabitEthernet0/0/1] quit
[DeviceB] interface gigabitethernet 0/0/2
[DeviceB-GigabitEthernet0/0/2] ip address 10.0.10.1 24
[DeviceB-GigabitEthernet0/0/2] quit
# Create a portal authentication server named newpt, specify the IP address as 10.0.10.2 and the portal service port as 50100 (default port).
[DeviceB] portal server newpt
[DeviceB-portal-server-newpt] ip 10.0.10.2 key simple portal
[DeviceB-portal-server-newpt] port 50100
[DeviceB-portal-server-newpt] quit
# Create a portal Web server named newpt and specify http://10.0.10.2:8080/portal as the URL of the server. The URL must be the same as the URL configured for the portal page on the portal Web server.
[DeviceB] portal web-server newpt
[DeviceB-portal-websvr-newpt] url http://10.0.10.2:8080/portal
[DeviceB-portal-websvr-newpt] quit
# Enable cross-subnet portal authentication on the interface connected to Device A.
[DeviceB] interface gigabitethernet 0/0/1
[DeviceB-GigabitEthernet0/0/1] portal enable method layer3
# Configure the BAS-IP attribute as 10.0.11.1 for portal packets sent to the portal authentication server.
[DeviceB-GigabitEthernet0/0/1] portal bas-ip 10.0.11.1
# Specify portal Web server newpt on GigabitEthernet 0/0/1 (the interface connected to Device A).
[DeviceB-GigabitEthernet0/0/1] portal apply web-server newpt
[DeviceB-GigabitEthernet0/0/1] quit
# Create RADIUS scheme imc, and enter its view.
[DeviceB] radius scheme imc
# Specify the primary authentication and accounting servers, and configure the keys for communication with the servers.
[DeviceB-radius-imc] primary authentication 10.0.10.2
[DeviceB-radius-imc] primary accounting 10.0.10.2
[DeviceB-radius-imc] key authentication simple expert
[DeviceB-radius-imc] key accounting simple expert
# Exclude the ISP domain name from the usernames sent to the RADIUS server.
[DeviceB-radius-imc] user-name-format without-domain
[DeviceB-radius-imc] quit
# Enable RADIUS session control.
[Device] radius session-control enable
# Create an ISP domain named portal.com and enter its view.
[DeviceB] domain portal.com
# Configure AAA methods for the ISP domain.
[DeviceB-isp-portal.com] authentication portal radius-scheme imc
[DeviceB-isp-portal.com] authorization portal radius-scheme imc
[DeviceB-isp-portal.com] accounting portal radius-scheme imc
[DeviceB-isp-portal.com] quit
# Specify ISP domain portal.com as the default ISP domain. If a user enters the username without the ISP domain name at login, the AAA methods of the default domain are used for the user.
[DeviceB] domain default enable portal.com
# Configure a static route to Department A.
[DeviceB] ip route-static 192.168.0.0 255.255.255.0 10.0.11.2
Verifying the configuration
A user can perform portal authentication by using the H3C iNode client or through a Web page. This example triggers portal authentication by accessing a Web page.
# Access a Web page through a Web browser on a host. You are redirected to the authentication page http://10.0.10.2:8080/portal. Enter the username and password to log in. After passing the authentication, you are redirected to the authentication success page.
# Execute the display portal user command on Device B to display the portal user information.
[DeviceB] display portal user interface gigabitethernet 0/0/1
Total portal users: 1
Username: portal
Portal server: newpt
State: Online
VPN instance: N/A
MAC IP VLAN Interface
0000-0000-0000 192.168.0.2 -- GigabitEthernet0/0/1
Configuration files
· Device A:
#
interface GigabitEthernet0/0/1
port link-mode route
ip address 192.168.0.1 255.255.255.0
#
interface GigabitEthernet0/0/2
port link-mode route
ip address 10.0.11.2 255.255.255.0
#
ip route-static 10.0.10.0 24 10.0.11.1
#
· Device B:
#
interface GigabitEthernet0/0/2
port link-mode route
ip address 10.0.10.1 255.255.255.0
#
interface GigabitEthernet0/0/1
port link-mode route
ip address 10.0.11.1 255.255.255.0
portal enable method layer3
portal bas-ip 10.0.11.1
portal apply web-server newpt
#
ip route-static 192.168.0.0 24 10.0.11.2
#
radius session-control enable
#
radius scheme imc
primary authentication 10.0.10.2
primary accounting 10.0.10.2
key authentication cipher $c$3$M30nGDQxiOCAxe2AJ9yEZdk8kjoWag==
key accounting cipher $c$3$M23dGDQxiOCAxe2BJ9yEZdk8kjoWag==
user-name-format without-domain
#
domain portal.com
authentication portal radius-scheme imc
authorization portal radius-scheme imc
accounting portal radius-scheme imc
#
domain default enable portal.com
#
portal web-server newpt
url http://10.0.10.2:8080/portal
#
portal server newpt
ip 10.0.10.2 key cipher $c$3$r0VxoIiBrpzju9h2akP4TxyknX8VTuYKfA==
#
Example: Configuring direct portal authentication
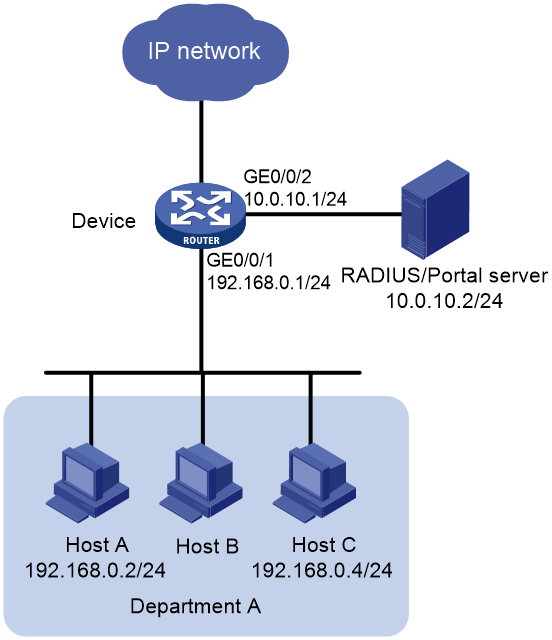
Network configuration
As shown in Figure 2, hosts in Department A are directly connected to the device. Configure direct portal authentication. Configure the network to meet the following requirements:
· An IMC server acts as the portal authentication server, the portal Web server, and the RADIUS server.
· Portal users can only access portal server before passing portal authentication. They cannot access other devices. After passing authentication, the user can properly access the network resources.
· Use the RADIUS server to perform authentication, authorization, and accounting on the user.
· Configure the BAS-IP attribute for portal packets sent to the portal authentication server.
· Enable the RADIUS session control feature to listen and receive session control packets sent by the RADIUS server.
Analysis
· To perform portal authentication for access users from Department A, configure the portal server and enable portal authentication on the device.
· To use RADIUS to perform authentication, authorization, and accounting for portal users, configure a RADIUS scheme on BRAS and use it for authentication, authorization, and accounting and apply it to the ISP domain to which the portal users belongs.
· When a user enters a username without an ISP domain to log in, the user uses the authentication scheme in the default ISP domain.
Software versions used
This configuration example was created and verified on R9141P16 of the MSR2630E-X1 device.
Restrictions and guidelines
Only the RADIUS server can perform authentication, authorization, and accounting for portal users.
On the RADIUS server, configure routes to reach the authentication interfaces and user networks.
Procedures
Configuring the RADIUS and portal server
Configure the RADIUS server and portal server. For more information, see "Configuring the RADIUS and portal server." When you configuring an access device for portal authentication, select Directly Selected from the Access Method list, and enter 192.168.0.1 in the IP Address field.
Configuring the device
# Assign IP addresses to GigabitEthernet 0/0/1 and GigabitEthernet 0/0/2.
<Device> system-view
[Device] interface gigabitethernet 0/0/1
[Device-GigabitEthernet0/0/1] ip address 192.168.0.1 24
[Device-GigabitEthernet0/0/1] quit
[Device] interface gigabitethernet 0/0/2
[Device-GigabitEthernet0/0/2] ip address 10.0.10.1 24
[Device-GigabitEthernet0/0/2] quit
# Create a portal authentication server named newpt, specify the IP address as 10.0.10.2 and the portal service port as 50100 (default port).
[Device] portal server newpt
[Device-portal-server-newpt] ip 10.0.10.2 key simple portal
[Device-portal-server-newpt] port 50100
[Device-portal-server-newpt] quit
# Create a portal Web server named newpt and specify http://10.0.10.2:8080/portal as the URL of the server. The URL must be the same as the URL configured for the portal page on the portal Web server.
[Device] portal web-server newpt
[Device-portal-websvr-newpt] url http://10.0.10.2:8080/portal
[Device-portal-websvr-newpt] quit
# Enable direct portal authentication on the interface connecting the hosts.
[Device] interface gigabitethernet 0/0/1
[Device-GigabitEthernet0/0/1] portal enable method direct
# On GigabitEthernet 0/0/1 (the interface connected to the hosts), configure the BAS-IP attribute as 192.168.0.1 for portal packets sent to the portal authentication server.
[Device-GigabitEthernet0/0/1] portal bas-ip 192.168.0.1
# Specify portal Web server newpt on GigabitEthernet 0/0/1.
[Device-GigabitEthernet0/0/1] portal apply web-server newpt
[Device-GigabitEthernet0/0/1] quit
# Create RADIUS scheme imc, and enter its view.
[Device] radius scheme imc
# Configure the primary authentication server, the primary accounting server, and the keys for the servers to communicate.
[Device-radius-imc] primary authentication 10.0.10.2
[Device-radius-imc] primary accounting 10.0.10.2
[Device-radius-imc] key authentication simple expert
[Device-radius-imc] key accounting simple expert
# Exclude the ISP domain name from the usernames sent to the RADIUS server.
[Device-radius-imc] user-name-format without-domain
[Device-radius-imc] quit
# Enable RADIUS session control.
[Device] radius session-control enable
# Create an ISP domain named portal.com and enter its view.
[Device] domain portal.com
# Configure AAA methods for the ISP domain.
[Device-isp-portal.com] authentication portal radius-scheme imc
[Device-isp-portal.com] authorization portal radius-scheme imc
[Device-isp-portal.com] accounting portal radius-scheme imc
[Device-isp-portal.com] quit
# Specify domain portal.com as the default ISP domain. If a user enters the username without the ISP domain name at login, the authentication and accounting methods of the default domain are used for the user.
[Device] domain default enable portal.com
Verifying the configuration
A user can perform portal authentication by using the H3C iNode client or through a Web page. This example uses the Web page.
# Access a Web page through a Web browser on a host. You are redirected to the authentication page http://10.0.10.2:8080/portal. Enter the username and password to log in. After passing the authentication, you are redirected to the authentication success page.
# Execute the display portal user command to display portal user information on the device.
[DeviceB] display portal user interface gigabitethernet 0/0/1
Total portal users: 1
Username: portal
Portal server: newpt
State: Online
VPN instance: N/A
MAC IP VLAN Interface
0015-e9a6-7cfe 192.168.0.2 -- GigabitEthernet0/0/1
Configuration files
#
interface GigabitEthernet0/0/2
port link-mode route
ip address 10.0.10.1 255.255.255.0
#
interface GigabitEthernet0/0/1
port link-mode route
ip address 192.168.0.1 255.255.255.0
portal enable method direct
portal bas-ip 192.168.0.1
portal apply web-server newpt
#
radius session-control enable
#
radius scheme imc
primary authentication 10.0.10.2
primary accounting 10.0.10.2
key authentication cipher $c$3$M30nGDQxiOCAxe2AJ9yEZdk8kjoWag==
key accounting cipher $c$3$M23dGDQxiOCAxe2BJ9yEZdk8kjoWag==
user-name-format without-domain
#
domain portal.com
authentication portal radius-scheme imc
authorization portal radius-scheme imc
accounting portal radius-scheme imc
#
domain default enable portal.com
#
portal web-server newpt
url http://10.0.10.2:8080/portal
#
portal server newpt
ip 10.0.10.2 key cipher $c$3$r0VxoIiBrpzju9h2akP4TxyknX8VTuYKfA==
#
Related documentation
· User Access and Authentication Configuration Guide in H3C MSR1000[2600][3600] Routers Configuration Guides(V9)
· User Access and Authentication Command Reference in H3C MSR1000[2600][3600] Routers Command References(V9)