- Table of Contents
-
- H3C S7500 Series Operation Manual(Release 3100 Series)-(V1.04)
- 00-1Cover
- 00-2Overview
- 01-CLI Configuration
- 02-Login Configuration
- 03-Configuration File Management Configuration
- 04-VLAN Configuration
- 05-Extended VLAN Application Configuration
- 06-IP Address-IP Performance-IPX Configuration
- 07-GVRP Configuration
- 08-QinQ Configuration
- 09-Port Basic Configuration
- 10-Link Aggregation Configuration
- 11-Port Isolation Configuration
- 12-Port Binding Configuration
- 13-DLDP Configuration
- 14-MAC Address Table Configuration
- 15-MSTP Configuration
- 16-Routing Protocol Configuration
- 17-Multicast Configuration
- 18-802.1x Configuration
- 19-AAA-RADIUS-HWTACACS-EAD Configuration
- 20-Traffic Accounting Configuration
- 21-VRRP-HA Configuration
- 22-ARP Configuration
- 23-DHCP Configuration
- 24-ACL Configuration
- 25-QoS Configuration
- 26-Mirroring Configuration
- 27-Cluster Configuration
- 28-PoE Configuration
- 29-UDP-Helper Configuration
- 30-SNMP-RMON Configuration
- 31-NTP Configuration
- 32-SSH Terminal Service Configuration
- 33-File System Management Configuration
- 34-FTP and TFTP Configuration
- 35-Information Center Configuration
- 36-DNS Configuration
- 37-System Maintenance and Debugging Configuration
- 38-HWPing Configuration
- 39-RRPP Configuration
- 40-NAT-Netstream-Policy Routing Configuration
- 41-Telnet Protection Configuration
- 42-Hardware-Dependent Software Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 22-ARP Configuration | 115 KB |
Table of Contents
1.1.5 Introduction to Gratuitous ARP
1.1.6 Introduction to ARP Attack Detection
1.1.7 Introduction to Proxy ARP
1.1.8 Introduction to ARP Source Suppression
1.2.1 ARP Configuration Task List
1.2.2 Adding a Static ARP Entry Manually
1.2.3 Configuring the Maximum Number of ARP Entries that Can Be Learnt
1.2.4 Configuring the Aging Time for Dynamic ARP Entries
1.2.5 Configuring ARP Entry Checking
1.2.6 Configuring the Gratuitous ARP Update Interval
1.2.7 Configuring Gratuitous ARP Learning
1.2.8 Configuring ARP Attack Detection
1.2.10 Configuring ARP Source Suppression
1.3 Displaying and Maintaining ARP Configuration
Chapter 1 ARP Configuration
When configuring ARP, go to these sections for information you are interested in:
l Displaying and Maintaining ARP Configuration
1.1 Introduction to ARP
Address Resolution Protocol (ARP) is used to map network layer protocol addresses (IP addresses) to corresponding data link layer hardware addresses (MAC addresses).
1.1.1 Necessity of ARP
Network devices can directly identify Layer 2 MAC addresses instead of Layer 3 IP addresses. For a Layer 3 packet to be received by its destination host, it must carry the MAC address of the destination host. So, before sending a packet, the source device must map the destination IP address to the MAC address of the destination device.
1.1.2 ARP Packet Format
There are two types of ARP packets: ARP request and ARP reply. Figure 1-1 illustrates the structure of the two types of ARP packets. In this figure:
l All fields except for the target hardware address field are used in an ARP request. The target hardware address is just what the sender wants to obtain.
l All fields are used in an ARP reply.
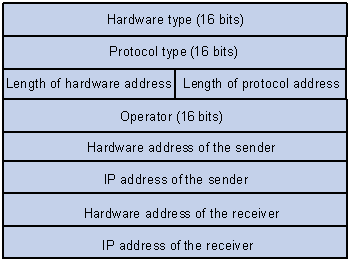
Figure 1-1 ARP packet format
Table 1-1 describes the fields of an ARP packet.
Table 1-1 Description on the fields of an ARP packet
|
Field |
Description |
|
Hardware Type |
Type of the hardware interface. See Table 1-2 for the valid values of this field. |
|
Protocol type |
Type of the protocol address to be mapped. For IP address, the value of this field is 0x0800. |
|
Hardware address length |
Length of the hardware address (in bytes) |
|
Protocol address length |
Length of the protocol address (in bytes) |
|
Operation code |
Type of the packet, which can be: l 1: ARP request l 2: ARP reply l 3: RARP request l 4: RARP reply |
|
Sender hardware address |
Hardware address of the sender |
|
Sender IP address |
IP address of the sender |
|
Target hardware address |
This field is null for an ARP request, and is the hardware address of the receiver for an ARP reply. |
|
Target IP address |
IP address of the receiver |
Table 1-2 Values of the hardware type field
|
Value |
Description |
|
1 |
Ethernet |
|
2 |
Experimental Ethernet |
|
3 |
X.25 |
|
4 |
Proteon ProNET (Token Ring) |
|
5 |
Chaos |
|
6 |
IEEE 802.x |
|
7 |
ARC network |
1.1.3 ARP Table
In an Ethernet network, two hosts must know each other’s MAC address for them to communicate with each other. For this reason, each host on the network maintains an ARP table, which contains some lately used IP address-to-MAC address mapping entries. Note that this manual only introduces basic implementation of ARP table. Different manufactures’ products may provide more information about ARP table. On an S7500 series Ethernet switch, you can use the display arp command to display ARP entries in the table (see ARP Command Manual for details).
Table 1-3 describes the fields of APR table.
Table 1-3 Description on the fields of an ARP table
|
Field |
Description |
|
IF index |
Index of the physical interface or port on the device owning the physical address and IP address in the entry |
|
Physical address |
Physical address of the device, a MAC address |
|
IP address |
IP address of the device |
|
Type |
Entry type, which can be: l 1: Not any of the following l 2: Invalid entry l 3: Dynamic entry l 4: Static entry |
1.1.4 ARP Implementation
The ARP table of a host is empty when the host just starts up. When a dynamic ARP entry has not been used for a specific time period, it is removed from the ARP table. The purpose of this is to save memory space and update the entries in the ARP table. The following describes the implementation procedure of ARP.
l Suppose Host A and Host B are on the same network segment. The IP address of Host A is IP_A and that of Host B is IP_B. To send a packet to Host B, Host A first looks up its own ARP table for an ARP entry that contains IP_B. If such an entry is found, Host A encapsulates the IP packet into a frame by using the MAC address in the entry as the destination MAC address and then sends the frame to Host B.
l If no such an entry is found in the ARP table, Host A puts the packet into the transmission queue, generates an ARP request packet with the IP addresses of Host B and Host A and the MAC address of Host A (IP_B, IP_A and MAC_A), and broadcasts the request on the Ethernet. Since the ARP request is broadcasted, all hosts on the network segment receive it. However, only the host with IP address IP_B (Host B) will process the request further.
l Host B adds the sender IP address and MAC address carried in the request (IP_A and MAC_A of Host A) in an entry to its ARP table and then returns an ARP reply packet to the sender (Host A), with its MAC address carried in the packet. Note that the ARP reply is a unicast packet instead of a broadcasted packet.
l Upon receiving the ARP reply, Host A extracts the IP address and MAC address of Host B from the packet, adds them in an entry to its ARP table, and then sends out all the packets destined for Host B in the transmission queue.
Generally, a host will automatically trigger ARP procedure during IP addressing.
1.1.5 Introduction to Gratuitous ARP
Gratuitous ARP packets have the following characteristics:
l Both source and destination IP addresses of a gratuitous ARP packet are the local addresses; the source MAC address of it is the local MAC address.
l If a device finds that the IP address in an incoming gratuitous packet conflicts with its own IP address, it returns an ARP replay to the sending device to notify the sender of the IP address conflict.
By sending gratuitous ARP packets, a network device can:
l Determine whether or not IP address conflict exists between it and other network devices.
l Trigger other network devices to update its hardware address stored in their caches.
With gratuitous ARP learning enabled on a device, each time the device receives a gratuitous ARP packet, the device updates the ARP entry matching the packet in the cache (if exists) by using the hardware address of the sender carried in the gratuitous ARP packet.
I. Overview of gratuitous ARP update interval
When ARP aging timer expires, some hosts in the network directly delete the ARP entries learned dynamically, incapable of updating ARP entries actively. These hosts have to trigger a new ARP request packet with a new IP packet received to request for the gateway address. As a host can buffer only one packet, when a ping is sent with a long packet, multiple fragments will be lost, which interrupts the ping.
When network load or the CPU occupancy of the receiving host is high, ARP packets may be lost or the host may be unable to process the ARP received timely. In such a case, after the dynamic ARP entries on the host age out, the traffic between the host and the sending device will remain interrupted before the host learns the ARP entries on the sending device again.
To address this issue, you can configure the gratuitous ARP update interval on the S7500 series Ethernet switches. With gratuitous ARP packets sent periodically, the receiving host can update the ARP entry for the gateway in its ARP table timely. In this way, the ARP entry for the gateway has been updated before the host ages out the entry; therefore, this entry will not be deleted. This prevents traffic interruption as mentioned above.
II. How gratuitous ARP update interval works
A switch periodically sends gratuitous ARP packets that carry the master IP address and secondary IP address of VLAN interfaces and the IP addresses of all the VRRP virtual routers to update the ARP entries on the device that is connected to the switch and incapable of updating ARP entries actively.
If a small number of VLAN interfaces and VRRP backup groups are configured, it takes a very time for the device to traverse all the VLAN interfaces and their IP addresses. If the traffic loops without being limited, gratuitous ARP packets are sent to the same IP address at an interval too short. This increases switch work load and network traffic. To solve this problem, the device allows you to configure the gratuitous ARP update interval.
1.1.6 Introduction to ARP Attack Detection
If an attacker sends an ARP message with a fake source IP address to a gateway, the gateway adds the IP-to-MAC mapping into its ARP mapping table. The attacker may send ARP messages with all the IP addresses of the network segment as the source IP addresses to the gateway, causing other devices unable to access the network.
To guard against such attacks, S7500 series Ethernet switches support the ARP attack detection feature. With this feature, you can limit the number of IP addresses to be bound to a MAC address in a VLAN. If a MAC address is bound to more than the specified number of IP addresses, it is considered an attacking MAC address. Consequently, all the ARP messages containing the attacking MAC address as the source MAC address will be discarded unless the ARP request is sent from the local device.
1.1.7 Introduction to Proxy ARP
The proxy ARP function allows devices to forward ARP requests between host in different networks and ARP requests from one host in a network to another host on an isolated port in the same network, so as to provide Layer 3 connectivity between Layer 2 isolated ports.
To provide Layer 3 connectivity between ports in the following conditions, you need to enable the proxy ARP function.
l Super VLAN function is enabled on the S7500 switch.
l The isolate-user-vlan function is enabled on Layer 2 switches connecting with the S7500 switch.
& Note:
l Generally, ports in the same VLAN are interconnected at Layer 2 by default. So, proxy ARP only processes inter-VLAN ARP requests and does not deal with intra-VLAN ARP requests.
l When isolate-user-vlan function is enabled on the Layer 2 switches connected with the S7500, ports in the same VLAN are isolated with each other at Layer 2. To provide Layer 3 connectivity between Layer 2 isolated ports in the same VLAN, you need to enable the intra-VLAN proxy ARP on the S7500 to have proxy ARP process intra-VLAN ARP requests.
1.1.8 Introduction to ARP Source Suppression
With the ARP source suppression function, the switch classifies incoming ARP packets and limits the maximum number of ARP packets with the same type that can be sent to the CPU in a time of time, so as to protect the CPU from being attacked by illegal ARP packets generated by ARP scanning of a host to the whole network.
An S7500 series switch classifies incoming ARP packets into the following types:
l Arbitrary ARP packets, whose source/destination IP addresses are not distinguished
l Pass-through ARP packets, whose source IP addresses are the same one and destination IP addresses are not the IP address of the current switch
l Locally-terminated ARP packets, whose source IP addresses are the same one and destination addresses are the IP address of the current switch.
For each type, you can set the maximum number of ARP packets that can be sent to the CPU in a unit of time on the switch. When the number of ARP packets received in a unit of time exceeds the corresponding setting, the switch will regard the exceeding ones as illegal ARP packets and discard them.
1.2 Configuring ARP
ARP entries in an S7500 series Ethernet switch falls into two types: static and dynamic, as described in Table 1-4.
|
ARP entry |
Generation method |
Maintenance method |
|
Static ARP entry |
Manually configured |
Manual maintenance |
|
Dynamic ARP entry |
Dynamically generated |
A dynamic ARP entry ages out when ARP aging timer expires. |
1.2.1 ARP Configuration Task List
Complete the following tasks to configure ARP:
|
Task |
Remarks |
|
Optional |
|
|
Configuring the Maximum Number of ARP Entries that Can Be Learnt |
Optional |
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
1.2.2 Adding a Static ARP Entry Manually
Follow these steps to add a static ARP entry manually:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Add a static ARP entry manually |
arp static ip-address mac-address [ vlan-id interface-type interface-number ] |
Required By default, there is no static ARP entry in the ARP table, and ARP entries are dynamically created by ARP. |
![]() Caution:
Caution:
l Static ARP entries are valid as long as the Ethernet switch operates normally, unless they are removed as the results of some operations, like changing/removing a VLAN interface, removing a VLAN, and removing a port from a VLAN.
l The VLAN specified by the vlan-id argument in the arp static command must be an existing VLAN, and the port specified by the interface-type and interface-number arguments must belong to the VLAN.
1.2.3 Configuring the Maximum Number of ARP Entries that Can Be Learnt
Follow these steps to configure the maximum number of ARP entries that can be learnt on a port:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure the total maximum number of ARP entries |
arp max-entry number |
Optional It is 8192 by default. |
|
Enter port view |
interface interface-type interface-number |
— |
|
Configure the maximum number of dynamic ARP entries that can be learnt by the port |
arp max-dynamic-entry number |
Optional It is 2048 by default. |
1.2.4 Configuring the Aging Time for Dynamic ARP Entries
Follow these steps to configure the aging time for dynamic ARP entries:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure the aging time for dynamic ARP entries |
arp timer aging aging-time |
Optional By default, this time is 20 minutes. |
1.2.5 Configuring ARP Entry Checking
Follow these steps to enable ARP entry checking:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable ARP entry checking to disable the switch from learning ARP entries with multicast MAC addresses |
arp check enable |
Optional By default, the function is enabled and no multicast MAC address ARP entry will be learnt. |
1.2.6 Configuring the Gratuitous ARP Update Interval
Follow these steps to configure the gratuitous ARP update interval:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable gratuitous ARP packets to be sent periodically |
arp gratuitous-updating enable |
Required By default, this function is disabled on the switch. |
|
Set a gratuitous ARP update interval |
arp timer gratuitous-updating updating-interval |
Optional The gratuitous ARP update interval defaults to five minutes after this function is enabled. |
With VRRP enabled on a VLAN interface of a switch:
l If the switch is the master switch, it sends gratuitous ARP messages with the IP address of the VRRP virtual router.
l If it is not the master switch, it sends gratuitous ARP messages with the primary and all the secondary IP addresses of the VLAN interface.
1.2.7 Configuring Gratuitous ARP Learning
Follow these steps to enable gratuitous ARP learning:
|
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
Enable gratuitous ARP learning |
gratuitous-arp-learning enable |
Required Disabled by default. |
1.2.8 Configuring ARP Attack Detection
Follow these steps to configure ARP attack detection:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Set the maximum number of IP addresses to be bound to a MAC address in a VLAN |
arp mac-arp-map limit number |
Required By default, the maximum number is 2. |
& Note:
If secondary IP addresses are configured for a VLAN interface, the specified maximum number of IP addresses to be bound to a MAC address should be bigger than the total number of the primary and secondary IP addresses of the VLAN interface.
1.2.9 Configuring Proxy ARP
Follow these steps to configure proxy ARP:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter VLAN interface view |
interface Vlan-interface vlan-id |
— |
|
Enable proxy ARP |
arp proxy enable |
Required By default, proxy ARP is disabled. |
|
Enable intra-VLAN proxy ARP |
arp proxy source-vlan enable |
Optional By default, intra-VLAN proxy ARP is disabled, and the proxy ARP only processes inter-VLAN ARP requests. |
1.2.10 Configuring ARP Source Suppression
By setting the maximum numbers of ARP packets of different types that can be sent to the CPU in a unit of time, you can protect the CPU from being attacked by illegal ARP packets.
Follow these steps to configure ARP source suppression:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure the maximum number of ARP packets of a type that can be sent to the CPU in a unit of time |
arp source-suppression limit { total | local | through } limit-value |
Optional The default value varies with the type of ARP packets l When total is adopted, the default value is 100. l When local is adopted, the default value is 3. l When through is adopted, the default value is 3. |
1.3 Displaying and Maintaining ARP Configuration
|
To do… |
Use the command… |
Remarks |
|
Display ARP attack information |
display arp attack-list |
Available in any view |
|
Display ARP entries |
display arp [ static | dynamic | ip-address ] |
|
|
Display the ARP entries matching a specified rule |
display arp | { begin | include | exclude } text |
|
|
Display the number limits of ARP entries |
display arp entry-limit [ interface-type interface-number ] |
|
|
Display the ARP entries of all ports on a specified slot |
display arp slot slot-id |
|
|
Display the ARP entries of all ports in a specified VLAN |
display arp vlan vlan-id |
|
|
Display the ARP entries of a specified interface |
display arp interface interface-type interface-number |
|
|
Display the setting for ARP aging timer |
display arp timer aging |
|
|
Display the status of proxy ARP |
display arp proxy [ interface interface-type interface-number ] |
|
|
Display ARP source suppression configuration |
display arp source-suppression |
|
|
Clear ARP entries |
reset arp [ dynamic | static | interface interface-type interface-number ] |
Available in user view |
|
Clear the ARP attack information |
reset arp attack-list |
