- Table of Contents
-
- H3C Fixed Port Campus Switches Configuration Examples-6W104
- 00-Applicable hardware and software versions
- 01-Login Management Configuration Examples
- 02-RBAC Configuration Examples
- 03-Software Upgrade Examples
- 04-ISSU Configuration Examples
- 05-Software Patching Examples
- 06-Ethernet Link Aggregation Configuration Examples
- 07-Port Isolation Configuration Examples
- 08-Spanning Tree Configuration Examples
- 09-VLAN Configuration Examples
- 10-VLAN Tagging Configuration Examples
- 11-DHCP Snooping Configuration Examples
- 12-Cross-Subnet Dynamic IP Address Allocation Configuration Examples
- 13-IPv6 over IPv4 Tunneling with OSPFv3 Configuration Examples
- 14-IPv6 over IPv4 GRE Tunnel Configuration Examples
- 15-GRE with OSPF Configuration Examples
- 16-OSPF Configuration Examples
- 17-IS-IS Configuration Examples
- 18-BGP Configuration Examples
- 19-Policy-Based Routing Configuration Examples
- 20-OSPFv3 Configuration Examples
- 21-IPv6 IS-IS Configuration Examples
- 22-Routing Policy Configuration Examples
- 23-IGMP Snooping Configuration Examples
- 24-IGMP Configuration Examples
- 25-MLD Snooping Configuration Examples
- 26-IPv6 Multicast VLAN Configuration Examples
- 27-ACL Configuration Examples
- 28-Traffic Policing Configuration Examples
- 29-GTS and Rate Limiting Configuration Examples
- 30-Traffic Filtering Configuration Examples
- 31-AAA Configuration Examples
- 32-Port Security Configuration Examples
- 33-Portal Configuration Examples
- 34-SSH Configuration Examples
- 35-IP Source Guard Configuration Examples
- 36-Ethernet OAM Configuration Examples
- 37-CFD Configuration Examples
- 38-DLDP Configuration Examples
- 39-VRRP Configuration Examples
- 40-BFD Configuration Examples
- 41-NTP Configuration Examples
- 42-SNMP Configuration Examples
- 43-NQA Configuration Examples
- 44-Mirroring Configuration Examples
- 45-sFlow Configuration Examples
- 46-OpenFlow Configuration Examples
- 47-MAC Address Table Configuration Examples
- 48-Static Multicast MAC Address Entry Configuration Examples
- 49-IP Unnumbered Configuration Examples
- 50-MVRP Configuration Examples
- 51-MCE Configuration Examples
- 52-Attack Protection Configuration Examples
- 53-Smart Link Configuration Examples
- 54-RRPP Configuration Examples
- 55-BGP Route Selection Configuration Examples
- 56-IS-IS Route Summarization Configuration Examples
- 57-VXLAN Configuration Examples
- 58-DRNI Configuration Examples
- 59-IRF 3.1 Configuration Examples
- 60-PTP Configuration Examples
- 61-S-MLAG Configuration Examples
- 62-Puppet Configuration Examples
- 63-802.1X Configuration Examples
- 64-MAC Authentication Configuration Examples
- 65-ISATAP Tunnel and 6to4 Tunnel Configuration Examples
- 66-BIDIR-PIM Configuration Examples
- 67-Congestion Avoidance and Queue Scheduling Configuration Examples
- 68-Basic MPLS Configuration Examples
- 69-MPLS L3VPN Configuration Examples
- 70-MPLS OAM Configuration Examples
- 71-EVPN-DCI over an MPLS L3VPN Network Configuration Examples
- 72-DRNI and EVPN Configuration Examples
- 73-Multicast VPN Configuration Examples
- 74-MPLS TE Configuration Examples
- 75-Control Plane-Based QoS Policy Configuration Examples
- 76-Priority Mapping and Queue Scheduling Configuration Examples
- 77-ARP Attack Protection Configuration Examples
- 78-IRF Software Upgrade Configuration Examples
- 79-IRF Member Replacement Configuration Examples
- 80-Layer 3 Multicast on Multicast Source-Side DR System Configuration Examples
- 81-EVPN Multicast Configuration Examples
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 19-Policy-Based Routing Configuration Examples | 98.74 KB |
Contents
Configuration restrictions and guidelines
Applicable hardware and software versions
Applicable hardware and software versions
Introduction
This document provides PBR configuration examples.
PBR uses a user-defined policy to route packets based on fields such as the source address, destination address, IP precedence, and protocol. PBR takes precedence over destination-based routing.
Prerequisites
This document is not restricted to specific software or hardware versions.
The configuration examples in this document were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
This document assumes that you have basic knowledge of PBR.
Configuration restrictions and guidelines
When you configure the action of forwarding traffic to a next hop, do not specify the following addresses:
· An IPv6 address in an IPv4 ACL rule.
· An IPv4 address in an IPv6 ACL rule.
Example: Configuring PBR
Network configuration
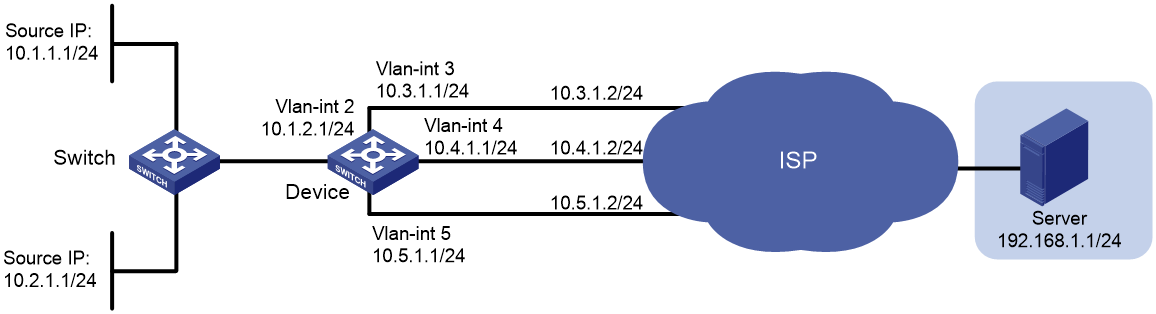
As shown in Figure 1, on Device, all packets destined for Server are forwarded to the next hop 10.4.1.2 by default.
Configure PBR to meet the following requirements:
· Packets with source IPv4 address 10.2.1.1 received on VLAN-interface 2 are forwarded to the next hop 10.5.1.2.
· HTTP packets with source IPv4 addresses other than 10.2.1.1 received on VLAN-interface 2 are forwarded to the next hop 10.3.1.2.
Analysis
To forward the two types of packets to different next hops, you must perform the following tasks:
· Configure two ACLs to classify the two types of packets.
· Configure two policy nodes to forward the packets to the specified next hops.
To ensure that packets with source address 10.2.1.1 are forwarded to the next hop 10.5.1.2, assign a node a smaller node ID to match the packets.
Applicable hardware and software versions
The following matrix shows the hardware and software versions to which this configuration example is applicable:
|
Hardware |
Software version |
|
S6812 switch series S6813 switch series |
Release 6615Pxx, Release 6628Pxx |
|
S6550XE-HI switch series |
Release 6008 and later, Release 8106Pxx |
|
S6525XE-HI switch series |
Release 6008 and later, Release 8106Pxx |
|
S5850 switch series |
Release 8005 and later |
|
S5570S-EI switch series |
Release 11xx |
|
S5560X-EI switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
S5560X-HI switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
S5500V2-EI switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
MS4520V2-30F switch |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
MS4520V2-30C switch MS4520V2-54C switch |
Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
MS4520V2-28S switch MS4520V2-24TP switch |
Release 63xx |
|
S6520X-HI switch series S6520X-EI switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
S6520X-SI switch series S6520-SI switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
S5000-EI switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
MS4600 switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
ES5500 switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
S5560S-EI switch series S5560S-SI switch series |
Release 63xx |
|
S5500V3-24P-SI S5500V3-48P-SI |
Release 63xx |
|
S5500V3-SI switch series (except S5500V3-24P-SI and S5500V3-48P-SI) |
Release 11xx |
|
S5170-EI switch series |
Release 11xx |
|
S5130S-HI switch series S5130S-EI switch series S5130S-SI switch series S5130S-LI switch series |
Release 63xx |
|
S5120V2-SI switch series S5120V2-LI switch series |
Release 63xx |
|
S5120V3-EI switch series |
Release 11xx |
|
S5120V3-36F-SI S5120V3-28P-HPWR-SI S5120V3-54P-PWR-SI |
Release 11xx |
|
S5120V3-SI switch series (except S5120V3-36F-SI, S5120V3-28P-HPWR-SI, and S5120V3-54P-PWR-SI) |
Release 63xx |
|
S5120V3-LI switch series |
Release 63xx |
|
S3600V3-EI switch series |
Release 11xx |
|
S3600V3-SI switch series |
Release 11xx |
|
S3100V3-EI switch series S3100V3-SI switch series |
Release 63xx |
|
S5110V2 switch series |
Release 63xx |
|
S5110V2-SI switch series |
Release 63xx |
|
S5000V3-EI switch series S5000V5-EI switch series |
Release 63xx |
|
S5000E-X switch series S5000X-EI switch series |
Release 63xx |
|
E128C switch E152C switch E500C switch series E500D switch series |
Release 63xx |
|
MS4320V2 switch series MS4320V3 switch series MS4300V2 switch series MS4320 switch series MS4200 switch series |
Release 63xx |
|
WS5850-WiNet switch series |
Release 63xx |
|
WS5820-WiNet switch series WS5810-WiNet switch series |
Release 63xx |
|
WAS6000 switch series |
Release 63xx |
|
IE4300-12P-AC switch IE4300-12P-PWR switch IE4300-M switch series IE4320 switch series |
Release 63xx |
Procedures
# Configure an IPv4 address for VLAN-interface 2.
<Device> system-view
[Device] interface vlan-interface 2
[Device-Vlan-interface2] ip address 10.1.2.1 255.255.255.0
[Device-Vlan-interface2] quit
# Configure IPv4 addresses for other interfaces in the same way VLAN-interface 2 is configured. (Details not shown.)
# Configure three static routes and configure 10.4.1.2 as the default next hop.
[Device] ip route-static 192.168.1.0 24 10.3.1.2
[Device] ip route-static 192.168.1.0 24 10.4.1.2 preference 40
[Device] ip route-static 192.168.1.0 24 10.5.1.2
# Create ACL 3005 to match packets with source address 10.2.1.1.
[Device] acl advanced 3005
[Device-acl-ipv4-adv-3005] rule 0 permit ip source 10.2.1.1 0
[Device-acl-ipv4-adv-3005] quit
# Create ACL 3006 to match HTTP packets with source addresses other than 10.2.1.1.
[Device] acl advanced 3006
[Device-acl-ipv4-adv-3006] rule 0 permit tcp destination-port eq www
[Device-acl-ipv4-adv-3006] quit
# Configure Node 0 for policy pbr1 to forward packets matching ACL 3005 to the next hop 10.5.1.2.
[Device] policy-based-route pbr1 permit node 0
[Device-pbr-pbr1-0] if-match acl 3005
[Device-pbr-pbr1-0] apply next-hop 10.5.1.2
[Device-pbr-pbr1-0] quit
# Configure Node 1 for policy pbr1 to forward packets matching ACL 3006 to the next hop 10.3.1.2.
[Device] policy-based-route pbr1 permit node 1
[Device-pbr-pbr1-1] if-match acl 3006
[Device-pbr-pbr1-1] apply next-hop 10.3.1.2
[Device-pbr-pbr1-1] quit
# Apply policy pbr1 to VLAN-interface 2.
[Device] interface vlan-interface 2
[Device-Vlan-interface2] ip policy-based-route pbr1
[Device-Vlan-interface2] quit
Verifying the configuration
# On Device, display PBR policy information.
[Device] display ip policy-based-route policy pbr1
Policy name: pbr1
node 0 permit:
if-match acl 3005
apply next-hop 10.5.1.2
node 1 permit:
if-match acl 3006
apply next-hop 10.3.1.2
The output shows that the PBR configurations are successful.
# On Switch, display the path for forwarding non-HTTP packets with source address 10.1.1.1.
|
|
NOTE: Before you use a tracert command, perform the following tasks: · Enable sending of ICMP timeout packets on the intermediate devices. · Enable sending of ICMP destination unreachable packets on the destination device. |
<Switch> tracert -a 10.1.1.1 192.168.1.1
traceroute to 192.168.1.1 (192.168.1.1) from 10.1.1.1, 30 hops at most, 52 bytes
each packet, press CTRL+C to break
1 10.1.2.1 (10.1.2.1) 2.178 ms 1.364 ms 1.058 ms
2 10.4.1.2 (10.4.1.2) 1.548 ms 1.248 ms 1.112 ms
3 192.168.1.1 (192.168.1.1) 1.594 ms 1.321 ms 1.093 ms
The output shows that non-HTTP packets with source address 10.1.1.1 are forwarded to the next hop 10.4.1.2.
# On Switch, display the path for forwarding packets with source address 10.2.1.1.
<Switch> tracert -a 10.2.1.1 192.168.1.1
traceroute to 192.168.1.1 (192.168.1.1) from 10.2.1.1, 30 hops at most, 40 bytes
each packet, press CTRL+C to break
1 10.1.2.1 (10.1.2.1) 1.721 ms 1.226 ms 1.050 ms
2 10.5.1.2 (10.5.1.2) 4.494 ms 1.385 ms 1.170 ms
3 192.168.1.1 (192.168.1.1) 1.448 ms 1.304 ms 1.093 ms
The output shows that packets with source address 10.2.1.1 are forwarded to the next hop 10.5.1.2.
Configuration files
|
|
NOTE: Support for the port link-mode bridge command depends on the device model. |
#
vlan 1
#
vlan 2 to 5
#
policy-based-route pbr1 permit node 0
if-match acl 3005
apply next-hop 10.5.1.2
#
policy-based-route pbr1 permit node 1
if-match acl 3006
apply next-hop 10.3.1.2
#
interface Vlan-interface2
ip address 10.1.2.1 255.255.255.0
ip policy-based-route pbr1
#
interface Vlan-interface3
ip address 10.3.1.1 255.255.255.0
#
interface Vlan-interface4
ip address 10.4.1.1 255.255.255.0
#
interface Vlan-interface5
ip address 10.5.1.1 255.255.255.0
#
ip route-static 192.168.1.0 24 10.3.1.2
ip route-static 192.168.1.0 24 10.4.1.2 preference 40
ip route-static 192.168.1.0 24 10.5.1.2
#
acl number 3005
rule 0 permit ip source 10.2.1.1 0
#
acl number 3006
rule 0 permit tcp destination-port eq www
#
Example: Configuring IPv6 PBR
Network configuration
As shown in Figure 2, on Device, all packets destined for Server are forwarded to the next hop 2004::2 by default.
Configure IPv6 PBR to meet the following requirements:
· Packets with source IPv6 address 2002::1 received on VLAN-interface 2 are forwarded to the next hop 2005::2.
· HTTP packets with source IPv6 addresses other than 2002::1 received on VLAN-interface 2 are forwarded to the next hop 2003::2.
Analysis
To forward the two types of packets to different next hops, you must perform the following tasks:
· Configure two ACLs to classify the two types of packets.
· Configure two policy nodes to forward the packets to the specified next hops.
To ensure that packets with source address 2002::1 are forwarded to the next hop 2005::2, assign a node a smaller node ID to match the packets.
Applicable hardware and software versions
The following matrix shows the hardware and software versions to which this configuration example is applicable:
|
Hardware |
Software version |
|
S6812 switch series S6813 switch series |
Release 6615Pxx, Release 6628Pxx |
|
S6550XE-HI switch series |
Release 6008 and later, Release 8106Pxx |
|
S6525XE-HI switch series |
Release 6008 and later, Release 8106Pxx |
|
S5850 switch series |
Release 8005 and later |
|
S5570S-EI switch series |
Release 11xx |
|
S5560X-EI switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
S5560X-HI switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
S5500V2-EI switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
MS4520V2-30F switch |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
MS4520V2-30C switch MS4520V2-54C switch |
Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
MS4520V2-28S switch MS4520V2-24TP switch |
Release 63xx |
|
S6520X-HI switch series S6520X-EI switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
S6520X-SI switch series S6520-SI switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
S5000-EI switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
MS4600 switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
ES5500 switch series |
Release 63xx, Release 65xx, Release 6615Pxx, Release 6628Pxx |
|
S5560S-EI switch series S5560S-SI switch series |
Release 63xx |
|
S5500V3-24P-SI S5500V3-48P-SI |
Release 63xx |
|
S5500V3-SI switch series (except S5500V3-24P-SI and S5500V3-48P-SI) |
Release 11xx |
|
S5170-EI switch series |
Release 11xx |
|
S5130S-HI switch series S5130S-EI switch series S5130S-SI switch series S5130S-LI switch series |
Release 63xx |
|
S5120V2-SI switch series S5120V2-LI switch series |
Release 63xx |
|
S5120V3-EI switch series |
Release 11xx |
|
S5120V3-36F-SI S5120V3-28P-HPWR-SI S5120V3-54P-PWR-SI |
Release 11xx |
|
S5120V3-SI switch series (except S5120V3-36F-SI, S5120V3-28P-HPWR-SI, and S5120V3-54P-PWR-SI) |
Release 63xx |
|
S5120V3-LI switch series |
Release 63xx |
|
S3600V3-EI switch series |
Release 11xx |
|
S3600V3-SI switch series |
Release 11xx |
|
S3100V3-EI switch series S3100V3-SI switch series |
Release 63xx |
|
S5110V2 switch series |
Release 63xx |
|
S5110V2-SI switch series |
Release 63xx |
|
S5000V3-EI switch series S5000V5-EI switch series |
Release 63xx |
|
S5000E-X switch series S5000X-EI switch series |
Release 63xx |
|
E128C switch E152C switch E500C switch series E500D switch series |
Release 63xx |
|
MS4320V2 switch series MS4320V3 switch series MS4300V2 switch series MS4320 switch series MS4200 switch series |
Release 63xx |
|
WS5850-WiNet switch series |
Release 63xx |
|
WS5820-WiNet switch series WS5810-WiNet switch series |
Release 63xx |
|
WAS6000 switch series |
Release 63xx |
|
IE4300-12P-AC switch IE4300-12P-PWR switch IE4300-M switch series IE4320 switch series |
Release 63xx |
Procedures
# Configure an IPv6 address for VLAN-interface 2.
<Device> system-view
[Device] interface vlan-interface 2
[Device-Vlan-interface2] ipv6 address 2007::1 64
[Device-Vlan-interface2] quit
# Configure IPv6 addresses for other interfaces in the same way VLAN-interface 2 is configured. (Details not shown.)
# Configure three static routes and configure 2004::2/64 as the default next hop.
[Device] ipv6 route-static 3001::1 64 2003::2
[Device] ipv6 route-static 3001::1 64 2004::2 preference 40
[Device] ipv6 route-static 3001::1 64 2005::2
# Create IPv6 ACL 3005 to match packets with source address 2002::1.
[Device] acl ipv6 advanced 3005
[Device-acl-ipv6-adv-3005] rule 0 permit ipv6 source 2002::1/128
[Device-acl-ipv6-adv-3005] quit
# Create IPv6 ACL 3006 to match HTTP packets with source addresses other than 2002::1.
[Device] acl ipv6 advanced 3006
[Device-acl-ipv6-adv-3006] rule 0 permit tcp destination-port eq www
[Device-acl-ipv6-adv-3006] quit
# Configure Node 0 for policy pbr1 to forward packets matching IPv6 ACL 3005 to the next hop 2005::2.
[Device] ipv6 policy-based-route pbr1 permit node 0
[Device-pbr6-pbr1-0] if-match acl 3005
[Device-pbr6-pbr1-0] apply next-hop 2005::2
[Device-pbr6-pbr1-0] quit
# Configure Node 1 for policy pbr1 to forward packets matching IPv6 ACL 3006 to the next hop 2003::2.
[Device] ipv6 policy-based-route pbr1 permit node 1
[Device-pbr6-pbr1-1] if-match acl 3006
[Device-pbr6-pbr1-1] apply next-hop 2003::2
[Device-pbr6-pbr1-1] quit
# Apply policy pbr1 to VLAN-interface 2.
[Device] interface vlan-interface 2
[Device-Vlan-interface2] ipv6 policy-based-route pbr1
[Device-Vlan-interface2] quit
Verifying the configuration
# On Device, display IPv6 PBR policy information.
[Device] display ipv6 policy-based-route policy pbr1
Policy name: pbr1
node 0 permit:
if-match acl 3005
apply next-hop 2005::2
node 1 permit:
if-match acl 3006
apply next-hop 2003::2
The output shows that the IPv6 PBR configurations are successful.
# On Device, verify the forwarding of packets with source address 2002::1. (Details not shown.)
· If 2005::2 is reachable, packets are forwarded to the next hop 2005::2.
· If 2005::2 is not reachable, packets are forwarded to the next hop 2004::2.
# On Device, verify the forwarding of HTTP packets. (Details not shown.)
· If 2003::2 is reachable, packets are forwarded to the next hop 2003::2.
· If 2003::2 is not reachable, packets are forwarded to the next hop 2004::2.
Configuration files
|
|
NOTE: Support for the port link-mode bridge command depends on the device model. |
#
vlan 1
#
vlan 2 to 5
#
ipv6 policy-based-route pbr1 permit node 0
if-match acl 3005
apply next-hop 2005::2
#
ipv6 policy-based-route pbr1 permit node 1
if-match acl 3006
apply next-hop 2003::2
#
interface Vlan-interface2
ipv6 policy-based-route pbr1
ipv6 address 2007::1/64
#
interface Vlan-interface3
ipv6 address 2003::1 64
#
interface Vlan-interface4
ipv6 address 2004::1 64
#
interface Vlan-interface5
ipv6 address 2005::1 64
#
ipv6 route-static 3001:: 64 2003::2
ipv6 route-static 3001:: 64 2004::2 preference 40
ipv6 route-static 3001:: 64 2005::2
#
acl ipv6 number 3005
rule 0 permit ipv6 source 2002::1/128
#
acl ipv6 number 3006
rule 0 permit tcp destination-port eq www
#