- Table of Contents
-
- H3C Low-End Ethernet Switches Configuration Guide(V1.01)
- 01-Login Configuration Guide
- 02-VLAN Configuration Guide
- 03-IP Address Configuration Guide
- 04-Voice VLAN Configuration Guide
- 05-GVRP Configuration Guide
- 06-Ethernet Interface Basic Configuration Guide
- 07-Link Aggregation Configuration Guide
- 08-Port Isolation Configuration Guide
- 09-Port Security Configuration Guide
- 10-Port Binding Configuration Guide
- 11-MAC Address Table Management Configuration Guide
- 12-DLDP Configuration Guide
- 13-Auto Detect Configuration Guide
- 14-MSTP Configuration Guide
- 15-Routing Configuration Guide
- 16-Multicast Configuration Guide
- 17-802.1x Configuration Guide
- 18-AAA Configuration Guide
- 19-MAC Authentication Configuration Guide
- 20-VRRP Configuration Guide
- 21-ARP Configuration Guide
- 22-DHCP Configuration Guide
- 23-ACL Configuration Guide
- 24-QoS-QoS Profile Configuration Guide
- 25-Web Cache Redirection Configuration Guide
- 26-Mirroring Configuration Guide
- 27-IRF Configuration Guide
- 28-Cluster Configuration Guide
- 29-PoE-PoE Profile Configuration Guide
- 30-UDP Helper Configuration Guide
- 31-SNMP-RMON Configuration Guide
- 32-NTP Configuration Guide
- 33-SSH Configuration Guide
- 34-FTP and TFTP Configuration Guide
- 35-Information Center Configuration Guide
- 36-VLAN-VPN Configuration Guide
- 37-HWPing Configuration Guide
- 38-DNS Configuration Guide
- 39-Access Management Configuration Guide
- 40-Web Authentication Configuration Guide
- 41-IPv6 Management Configuration Guide
- 42-Smart link - Monitor Link Configuration Guide
- 43-VLAN Mapping Configuration Guide
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 18-AAA Configuration Guide | 103.18 KB |
Configuring RADIUS Authentication for Telnet Users
Networking and Configuration Requirements
Configuring Dynamic VLAN Assignment with RADIUS Authentication
Networking and Configuration Requirements
Configuring Local Authentication for Telnet Users
Networking and Configuration Requirements
Configuring HWTACACS Authentication for Telnet Users
Networking and Configuration Requirements
Networking and Configuration Requirements
Configuring RADIUS Authentication for Telnet Users
Authentication, Authorization and Accounting (AAA) is a uniform framework used to configure the three functions for network security management. It can be implemented by multiple protocols.
RADIUS configurations are made in RADIUS schemes. When performing RADIUS configurations, you first create a RADIUS scheme and then specify the IP addresses and UDP port numbers of the RADIUS servers for the scheme. These RADIUS servers include the primary and secondary authentication/authorization severs and accounting servers. In addition, you need to configure the shared key and specify the RADIUS server type.
In practice, you can configure the above parameters as required. But you should configure at least one authentication/authorization server and one accounting server. If no accounting server is needed, you must configure the accounting optional command. Besides, the RADIUS server port settings on the switch must be consistent with those on the RADIUS servers.
Network Diagram
Figure 1-1 Network diagram for configuring RADIUS authentication for Telnet users
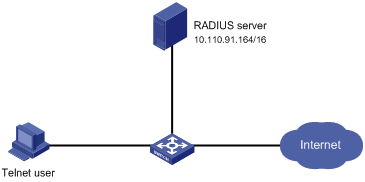
Networking and Configuration Requirements
As shown inFigure 1-1, configure the switch so that Telnet users logging into the switch are authenticated remotely by the RADIUS server.
l A RADIUS authentication server with an IP address of 10.110.91.164 is connected to the switch.
l On the switch, set the shared key for exchanging messages with the authentication RADIUS server to aabbcc.
l A CAMS server is used as the RADIUS server. Select extended as the server-type in the RADIUS scheme.
l On the RADIUS server, set the shared key for exchanging messages with the switch to aabbcc, configure the authentication port number, and add Telnet usernames and login passwords. Note that the Telnet usernames added to the RADIUS server must be in the format of userid@isp-name.
l Configure the switch to include domain names in the usernames to be sent to the RADIUS server in the RADIUS scheme.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-SI/EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-C-SI series S3100-T-SI series |
Release 0011, Release 2102, Release 2107 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration Procedure
# Enter system view.
<Sysname> system-view
# Configure the switch to use AAA authentication for Telnet users.
[Sysname] user-interface vty 0 4
[Sysname-ui-vty0-4] authentication-mode scheme
# Configure an ISP domain.
[Sysname] domain cams
[Sysname-isp-cams] access-limit enable 10
[Sysname-isp-cams] quit
# Configure a RADIUS scheme.
[Sysname] radius scheme cams
[Sysname-radius-cams] accounting optional
[Sysname-radius-cams] primary authentication 10.110.91.164
[Sysname-radius-cams] key authentication aabbcc
[Sysname-radius-cams] server-type extended
[Sysname-radius-cams] user-name-format with-domain
[Sysname-radius-cams] quit
# Associate the ISP domain with the RADIUS scheme.
[Sysname] domain cams
[Sysname-isp-cams] scheme radius-scheme cams
Complete Configuration
#
system-view
#
user-interface vty 0 4
authentication-mode scheme
#
domain cams
access-limit enable 10
quit
#
radius scheme cams
accounting optional
primary authentication 10.110.91.164
key authentication aabbcc
server-type extended
user-name-format with-domain
quit
#
domain cams
scheme radius-scheme cams
Precautions
The Telnet user needs to enter the username with the domain name cams, in the format userid@cams, so that the user is authenticated according to the configuration of the domain cams.
Configuring Dynamic VLAN Assignment with RADIUS Authentication
With the dynamic VLAN assignment function, a switch can dynamically assign an authenticated user to a specific VLAN according to the attributes issued by the RADIUS server, thus restricting the user to specific network resources.
Network Diagram
Figure 1-2 Network diagram for configuring dynamic VLAN assignment with RADIUS authentication
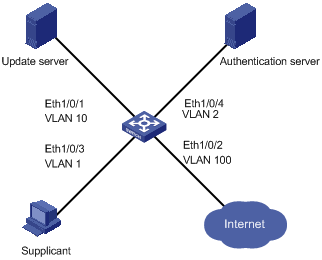
Networking and Configuration Requirements
You are required to configure the switch so that users logging into the switch are authenticated and restricted to specific network resources. The detailed requirements are as follows:
l All users must pass authentication to access the network.
l Users can access only VLAN 10 before passing authentication.
l Users passing authentication can access VLAN 100.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-SI/EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-C-SI series S3100-T-SI series |
Release 0011, Release 2102, Release 2107 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration Procedure
# Add users and configure VLAN assignment on the RADIUS server (omitted).
# Create a RADIUS scheme named cams and specify the primary and secondary servers.
<Sysname> system-view
[Sysname] radius scheme cams
[Sysname-radius-cams] primary authentication 192.168.1.19
[Sysname-radius-cams] primary accounting 192.168.1.19
[Sysname-radius-cams] secondary authentication 192.168.1.20
[Sysname-radius-cams] secondary accounting 192.168.1.20
# Set the shared key for message exchange with the authentication and accounting RADIUS servers to expert.
[Sysname-radius-cams] key authentication expert
[Sysname-radius-cams] key accounting expert
# Configure the switch to send a username with the domain name.
[Sysname-radius-cams] user-name-format with-domain
# Specify the server type as extended.
[Sysname-radius-cams] server-type extended
# Create an ISP domain named abc, bind RADIUS scheme cams for authentication, and configure dynamic VLAN assignment.
[Sysname] domain abc
[Sysname-isp-abc] radius-scheme cams
[Sysname-isp-abc] vlan-assignment-mode integer
[Sysname-isp-abc] quit
# Configure the ISP domain abc as the default ISP domain.
[Sysname] domain default enable abc
# Enable guest VLAN on the port.
[Sysname] interface Ethernet 1/0/3
[Sysname-Ethernet1/0/3] dot1x port-method portbased
[Sysname-Ehternet1/0/3] dot1x guest-vlan 10
# Enabled 802.1x.
[Sysname] dot1x
# Enable 802.1x in interface view.
[Sysname] interface Ethernet 1/0/3
[Sysname-Ethernet1/0/3] dot1x
Complete Configuration
#
system-view
radius scheme cams
primary authentication 192.168.1.19
primary accounting 192.168.1.19
secondary authentication 192.168.1.20
secondary accounting 192.168.1.20
key authentication expert
key accounting expert
user-name-format with-domain
server-type extended
#
domain abc
radius-scheme cams
vlan-assignment-mode integer
quit
#
domain default enable abc
#
interface Ethernet 1/0/3
dot1x port-method portbased
dot1x guest-vlan 10
#
dot1x
#
interface Ethernet 1/0/3
dot1x
Precautions
The above describes only the configurations on the switch. Configurations like adding users and configuring VLAN assignment on the RADIUS server are omitted.
Configuring Local Authentication for Telnet Users
In local authentication mode, user information including the username, password and related attributes are stored in the switch. Local authentication features high speed and low cost, but the amount of stored information depends on the hardware capacity.
Network Diagram
Figure 1-3 Network diagram for configuring local authentication for Telnet users
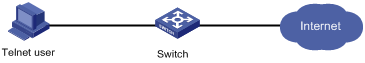
Networking and Configuration Requirements
As shown inFigure 1-3, you are required to configure the switch so that Telnet users logging into the switch are authenticated locally by the switch.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-SI/EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-C-SI series S3100-T-SI series |
Release 0011, Release 2102, Release 2107 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration Procedure
# Enter system view.
<Sysname> system-view
# Configure the switch to use AAA authentication for Telnet users.
[Sysname] user-interface vty 0 4
[Sysname-ui-vty0-4] authentication-mode scheme
[Sysname-ui-vty0-4] quit
# Configure a local user named telnet.
[Sysname] local-user telnet
[Sysname-luser-telnet] service-type telnet
[Sysname-luser-telnet] password simple aabbcc
[Sysname-luser-telnet] attribute idle-cut 300 access-limit 5
[Sysname] domain system
[Sysname-isp-system] scheme local
Complete Configuration
#
system-view
#
user-interface vty 0 4
authentication-mode scheme
quit
#
local-user telnet
service-type telnet
password simple aabbcc
attribute idle-cut 300 access-limit 5
domain system
scheme local
Precautions
The Telnet user needs to enter the username with the domain name system (that is, telnet@system), so that the user is authenticated according to the configuration of the system domain.
The configurations of local authentication for FTP users are similar to those for Telnet users.
Configuring HWTACACS Authentication for Telnet Users
Huawei Terminal Access Controller Access Control System (HWTACACS) is an enhanced security protocol based on TACACS (RFC 1492). Similar to the RADIUS protocol, it adopts the client/server model and implements AAA for multiple types of users through communicating with TACACS servers.
Compared with RADIUS, HWTACACS provides more reliable transmission and encryption, and therefore is more suitable for security control.
Network Diagram
Figure 1-4 Network diagram for configuring HWTACACS authentication for Telnet users
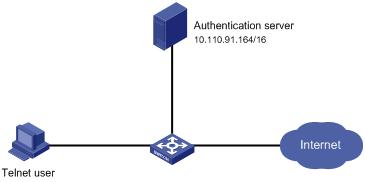
Networking and Configuration Requirements
As shown inFigure 1-4, you are required to configure the switch so that Telnet users logging into the switch are authenticated and authorized by the TACACS servers.
l A TACACS server with the IP address 10.110.91.164 is connected to the switch. It will be used as the authentication, authorization and accounting server.
l On the switch, set the shared keys for exchanging authentication, authorization and accounting messages with the TACACS server to expert. Configure the switch to strip domain names off usernames before sending usernames to the TACACS server.
l On the TACACS server, configure the shared keys to expert for exchanging messages with the switch, and add Telnet usernames and login passwords.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-SI/EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-C-SI series S3100-T-SI series |
Release 0011, Release 2102, Release 2107 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration Procedure
# Configure a HWTACACS scheme.
<Sysname> system-view
[Sysname] hwtacacs scheme hwtac
[Sysname-hwtacacs-hwtac] primary authentication 10.110.91.164 49
[Sysname-hwtacacs-hwtac] primary authorization 10.110.91.164 49
[Sysname-hwtacacs-hwtac] key authentication expert
[Sysname-hwtacacs-hwtac] key authorization expert
[Sysname-hwtacacs-hwtac] user-name-format without-domain
[Sysname-hwtacacs-hwtac] quit
# Configure domain hwtacacs to use HWTACACS scheme hwtac.
[Sysname] domain hwtacacs
[Sysname-isp-hwtacacs] scheme hwtacacs-scheme hwtac
[Sysname-isp-hwtacacs] accounting optional
Complete Configuration
#
system-view
hwtacacs scheme hwtac
primary authentication 10.110.91.164 49
primary authorization 10.110.91.164 49
key authentication expert
key authorization expert
user-name-format without-domain
quit
#
domain hwtacacs
scheme hwtacacs-scheme hwtac
accounting optional
Precautions
The above describes only the configuration of the HWTACACS scheme on the switch. The configuration of Telnet users on the HWTACACS server is omitted.
Configuring EAD
Endpoint Admission Defense (EAD) is an attack defense solution. By controlling access of terminals, it enhances the active defense capability of network endpoints and prevents viruses and worms from spreading on the network, thus securing the entire network.
With the cooperation of the switch, AAA sever, security policy server and security client, EAD is able to evaluate the security compliance of network endpoints and dynamically control their access rights.
With EAD, a switch verifies the validity of the session control packets it receives according to the source IP addresses of the packets:
l It regards only packets from the authentication and security policy servers valid.
l It assigns ACLs according to session control packets, thus controlling the access rights of users dynamically.
Network Diagram
Figure 1-5 Network diagram for configuring EAD
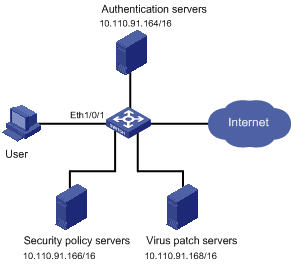
Networking and Configuration Requirements
As shown inFigure 1-5, a user host is connected to Ethernet 1/0/1 on the switch. On the host runs the 802.1x client supporting H3C EAD extended function. You are required to configure the switch to use the RADIUS server for remote user authentication and the security policy server for EAD control of users.
A CAMS server acts as the RADIUS server and another acts as the security policy server.
Applicable Product Matrix
|
Software version |
Hardware version |
|
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration Procedure
# Configure 802.1x on the switch.
Omitted
# Configure an ISP domain.
<Sysname> system-view
[Sysname] domain system
[Sysname-isp-system] quit
# Configure a RADIUS scheme.
[Sysname] radius scheme cams
[Sysname-radius-cams] primary authentication 10.110.91.164 1812
[Sysname-radius-cams] accounting optional
[Sysname-radius-cams] key authentication expert
[Sysname-radius-cams] server-type extended
# Specify the IP address of the security policy server.
[Sysname-radius-cams] security-policy-server 10.110.91.166
# Associate the ISP domain with the RADIUS scheme.
[Sysname-radius-cams] quit
[Sysname] domain system
[Sysname-isp-system] radius-scheme cams
Complete Configuration
#
system-view
domain system
quit
#
radius scheme cams
primary authentication 10.110.91.164 1812
accounting optional
key authentication expert
server-type extended
security-policy-server 10.110.91.166
#
quit
domain system
radius-scheme cams
Precautions
To support all extended functions of CAMS, you are recommended to configure the 802.1x authentication method as EAP and the RADIUS scheme server type as extended on the switch.
