- Table of Contents
-
- H3C Low-End Ethernet Switches Configuration Guide(V1.01)
- 01-Login Configuration Guide
- 02-VLAN Configuration Guide
- 03-IP Address Configuration Guide
- 04-Voice VLAN Configuration Guide
- 05-GVRP Configuration Guide
- 06-Ethernet Interface Basic Configuration Guide
- 07-Link Aggregation Configuration Guide
- 08-Port Isolation Configuration Guide
- 09-Port Security Configuration Guide
- 10-Port Binding Configuration Guide
- 11-MAC Address Table Management Configuration Guide
- 12-DLDP Configuration Guide
- 13-Auto Detect Configuration Guide
- 14-MSTP Configuration Guide
- 15-Routing Configuration Guide
- 16-Multicast Configuration Guide
- 17-802.1x Configuration Guide
- 18-AAA Configuration Guide
- 19-MAC Authentication Configuration Guide
- 20-VRRP Configuration Guide
- 21-ARP Configuration Guide
- 22-DHCP Configuration Guide
- 23-ACL Configuration Guide
- 24-QoS-QoS Profile Configuration Guide
- 25-Web Cache Redirection Configuration Guide
- 26-Mirroring Configuration Guide
- 27-IRF Configuration Guide
- 28-Cluster Configuration Guide
- 29-PoE-PoE Profile Configuration Guide
- 30-UDP Helper Configuration Guide
- 31-SNMP-RMON Configuration Guide
- 32-NTP Configuration Guide
- 33-SSH Configuration Guide
- 34-FTP and TFTP Configuration Guide
- 35-Information Center Configuration Guide
- 36-VLAN-VPN Configuration Guide
- 37-HWPing Configuration Guide
- 38-DNS Configuration Guide
- 39-Access Management Configuration Guide
- 40-Web Authentication Configuration Guide
- 41-IPv6 Management Configuration Guide
- 42-Smart link - Monitor Link Configuration Guide
- 43-VLAN Mapping Configuration Guide
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 09-Port Security Configuration Guide | 111.81 KB |
1 Port Security Configuration Guide
Configuring Port Security autolearn Mode
Networking and Configuration Requirements
Configuring Port Security mac-authentication Mode
Networking and Configuration Requirements
Configuring Port Security userlogin-withoui Mode
Networking and Configuration Requirements
Configuring Port Security mac-else-userlogin-secure-ext Mode
Networking and Configuration Requirements
Configuring Port Security autolearn Mode
In autolearn mode, a port can learn a specified number of MAC addresses and save those addresses as secure MAC addresses. Once the number of secure MAC addresses learnt by the port exceeds the upper limit defined by the port-security max-mac-count command, the port transits to the secure mode. In secure mode, a port does not save any new secure MAC addresses and permits only packets whose source addresses are secure MAC address or configured dynamic MAC addresses.
Network Diagram
Figure 1-1 Network diagram for configuring port security autolearn mode
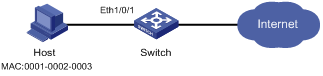
Networking and Configuration Requirements
On port Ethernet 1/0/1 of the switch, perform configurations to meet the following requirements:
l Allow a maximum of 80 users to access the port without authentication, and save the automatically learned user MAC addresses as secure MAC addresses.
l To ensure that the host can access the network, add the MAC address 0001-0002-0003 as a secure MAC address to VLAN 1 on the port.
l Once the number of secure MAC addresses reaches 80, the port stops MAC address learning. If any frame with an unknown source MAC address arrives, intrusion protection is triggered and the port is disabled and kept silent for 30 seconds.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-SI/EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-C-SI series S3100-T-SI series |
Release 2102, Release 2107 |
All versions |
|
S3100-52P |
Release 1602 |
S3100-52P |
Configuration Procedure
# Enter system view.
<Switch> system-view
# Enable port security.
[Switch] port-security enable
# Enter Ethernet 1/0/1 port view.
[Switch] interface Ethernet1/0/1
# Set the maximum number of MAC addresses allowed on the port to 80.
[Switch-Ethernet1/0/1] port-security max-mac-count 80
# Set the port security mode to autolearn.
[Switch-Ethernet1/0/1] port-security port-mode autolearn
# Add the MAC address 0001-0002-0003 as a secure MAC address to VLAN 1.
[Switch-Ethernet1/0/1] mac-address security 0001-0002-0003 vlan 1
# Configure the port to be silent for 30 seconds after intrusion protection is triggered.
[Switch-Ethernet1/0/1] port-security intrusion-mode disableport-temporarily
[Switch-Ethernet1/0/1] quit
[Switch] port-security timer disableport 30
Complete Configuration
#
port-security enable
port-security timer disableport 30
#
interface Ethernet1/0/1
port-security max-mac-count 80
port-security port-mode autolearn
port-security intrusion-mode disableport-temporarily
mac-address security 0001-0002-0003 vlan 1
#
Precautions
l Before enabling port security, be sure to disable 802.1x and MAC authentication globally.
l On a port configured with port security, you cannot configure the maximum number of MAC addresses that the port can learn, reflector port for port mirroring, fabric port or link aggregation.
Configuring Port Security mac-authentication Mode
In mac-authentication mode, a port performs MAC authentication of users.
Network Diagram
Figure 1-2 Network diagram for configuring port security mac-authentication mode
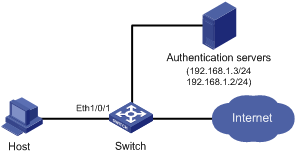
Networking and Configuration Requirements
The host connects to the switch through the port Ethernet 1/0/1, and the switch authenticates the host through the RADIUS server. If the authentication is successful, the host is authorized to access the Internet.
On port Ethernet 1/0/1 of the switch, perform configurations to meet the following requirements:
l The switch performs MAC authentication of users.
l All users belong to the domain aabbcc.net, and each of them uses the MAC address as username and password for authentication.
l Whenever a packet fails MAC authentication, intrusion protection is triggered to filter packets whose source MAC addresses are the same as that of the packet failing the authentication, ensuring the security of the port.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-SI/EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-C-SI series S3100-T-SI series |
Release 2102, Release 2107 |
All versions |
|
S3100-52P |
Release 1602 |
S3100-52P |
Configuration Procedure
![]()
l The following configurations involve some AAA/RADIUS configuration commands. For details about the commands, refer to AAA Operation.
l Configurations on the user host and the RADIUS server are omitted.
l Configure RADIUS parameters
# Create a RADIUS scheme named radius1.
<Switch> system-view
[Switch] radius scheme radius1
# Specify the primary RADIUS authentication server and primary RADIUS accounting server.
[Switch-radius-radius1] primary authentication 192.168.1.3
[Switch-radius-radius1] primary accounting 192.168.1.2
# Specify the secondary RADIUS authentication server and secondary RADIUS accounting server.
[Switch-radius-radius1] secondary authentication 192.168.1.2
[Switch-radius-radius1] secondary accounting 192.168.1.3
# Set the shared key for message exchange between the switch and the RADIUS authentication servers to name.
[Switch-radius-radius1] key authentication name
# Set the shared key for message exchange between the switch and the accounting RADIUS servers to name.
[Switch-radius-radius1] key accounting name
# Configure the switch to send a username without the domain name to the RADIUS server.
[Switch-radius-radius1] user-name-format without-domain
[Switch-radius-radius1] quit
# Create a domain named aabbcc.net and enter its view.
[Switch] domain aabbcc.net
# Specify the RADIUS scheme for the domain.
[Switch-isp-aabbcc.net] scheme radius-scheme radius1
[Switch-isp-aabbcc.net] quit
# Set aabbcc.net as the default user domain.
[Switch] domain default enable aabbcc.net
# Configure the switch to use MAC addresses as usernames for authentication, specifying that the MAC addresses should be lowercase without separators.
[Switch] mac-authentication authmode usernameasmacaddress usernameformat without-hyphen
# Specify the ISP domain for MAC authentication.
[Switch] mac-authentication domain aabbcc.net
# Enable port security.
[Switch] port-security enable
# Set the port security mode to mac-authentication.
[Switch] interface Ethernet 1/0/1
[Switch-Ethernet1/0/1] port-security port-mode mac-authentication
# Configure the port to drop packets whose source addresses are the same as that of the packet failing MAC authentication after intrusion protection is triggered.
[Switch-Ethernet1/0/1] port-security intrusion-mode blockmac
Complete Configuration
#
domain default enable aabbcc.net
#
port-security enable
#
MAC-authentication domain aabbcc.net
#
radius scheme radius1
server-type standard
primary authentication 192.168.1.3
primary accounting 192.168.1.2
secondary authentication 192.168.1.2
secondary accounting 192.168.1.3
key authentication name
key accounting name
user-name-format without-domain
#
domain aabbcc.net
scheme radius-scheme radius1
#
interface Ethernet1/0/1
port-security port-mode mac-authentication
port-security intrusion-mode blockmac
Precautions
l Before enabling port security, be sure to disable 802.1x and MAC authentication globally.
l On a port configured with port security, you cannot configure the maximum number of MAC addresses that the port can learn, reflector port for port mirroring, fabric port, or link aggregation.
Configuring Port Security userlogin-withoui Mode
In the userlogin-withoui mode, a port authenticates users using MAC-based 802.1x and permits only packets from authenticated users. Besides, the port also allows packets whose source MAC addresses have a specified organizationally unique identifier (OUI) value to pass the port.
Network Diagram
Figure 1-3 Network diagram for configuring port security userlogin-withoui mode

Networking and Configuration Requirements
The host connects to the switch through the port Ethernet 1/0/1, and the switch authenticates the host through the RADIUS server. If the authentication is successful, the host is authorized to access the Internet.
On port Ethernet 1/0/1 of the switch, perform configurations to meet the following requirements:
l Allow one 802.1x user to get online.
l Set two OUI values, and allow only one user whose MAC address matches one of the two OUI values to get online.
l Configure port security trapping to monitor the operations of the 802.1x-authenticated user.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-SI/EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-C-SI series S3100-T-SI series |
Release 2102, Release 2107 |
All versions |
|
S3100-52P |
Release 1602 |
S3100-52P |
Configuration Procedure
![]()
l The following configurations involve some AAA/RADIUS configuration commands. For details about the commands, refer to AAA Operation.
l Configurations on the user host and the RADIUS server are omitted.
l Configure RADIUS parameters
# Create a RADIUS scheme named radius1.
<Switch> system-view
[Switch] radius scheme radius1
# Specify the primary RADIUS authentication server and primary RADIUS accounting server.
[Switch-radius-radius1] primary authentication 192.168.1.3
[Switch-radius-radius1] primary accounting 192.168.1.2
# Specify the secondary RADIUS authentication server and secondary RADIUS accounting server.
[Switch-radius-radius1] secondary authentication 192.168.1.2
[Switch-radius-radius1] secondary accounting 192.168.1.3
# Set the shared key for message exchange between the switch and the RADIUS authentication servers to name.
[Switch-radius-radius1] key authentication name
# Set the shared key for message exchange between the switch and the accounting RADIUS servers to name.
[Switch-radius-radius1] key accounting name
# Set the interval and the number of packet transmission attempts for the switch to send packets to the RADIUS server.
[Switch-radius-radius1] timer 5
[Switch-radius-radius1] retry 5
# Set the timer for the switch to send real-time accounting packets to the RADIUS server to 15 minutes.
[Switch-radius-radius1] timer realtime-accounting 15
# Configure the switch to send a username without the domain name to the RADIUS server.
[Switch-radius-radius1] user-name-format without-domain
[Switch-radius-radius1] quit
# Create a domain named aabbcc.net and enter its view.
[Switch] domain aabbcc.net
# Specify radius1 as the RADIUS scheme of the user domain, and the local authentication scheme as the backup scheme when the RADIUS server is not available.
[Switch-isp-aabbcc.net] scheme radius-scheme radius1 local
# Set the maximum number of users of the ISP domain to 30.
[Switch-isp-aabbcc.net] access-limit enable 30
# Enable the idle disconnecting function and set the related parameters.
[Switch-isp-aabbcc.net] idle-cut enable 20 2000
[Switch-isp-aabbcc.net] quit
# Set aabbcc.net as the default user domain.
[Switch] domain default enable aabbcc.net
# Create a local user.
[Switch] local-user localuser
[Switch-luser-localuser] service-type lan-access
[Switch-luser-localuser] password simple localpass
l Configure port security
# Enable port security.
[Switch] port-security enable
# Add two OUI values.
[Switch] port-security oui 1234-0100-1111 index 1
[Switch] port-security oui 1234-0200-1111 index 2
# Set the port security mode to userlogin-withoui.
[Switch] interface Ethernet 1/0/1
[Switch-Ethernet1/0/1] port-security port-mode userlogin-withoui
[Switch-Ethernet1/0/1] quit
# Configure port security trapping.
[Switch] port-security trap dot1xlogfailure
[Switch] port-security trap dot1xlogon
[Switch] port-security trap dot1xlogoff
Complete Configuration
#
domain default enable aabbcc.net
#
port-security enable
port-security trap dot1xlogon
port-security trap dot1xlogoff
port-security trap dot1xlogfailure
port-security oui 1234-0100-0000 index 1
port-security oui 1234-0200-0000 index 2
#
radius scheme radius1
server-type standard
primary authentication 192.168.1.3
primary accounting 192.168.1.2
secondary authentication 192.168.1.2
secondary accounting 192.168.1.3
key authentication name
key accounting name
timer realtime-accounting 15
timer response-timeout 5
retry 5
user-name-format without-domain
#
domain aabbcc.net
scheme radius-scheme radius1 local
access-limit enable 30
idle-cut enable 20 2000
#
local-user localuser
password simple localpass
service-type lan-access
#
interface Ethernet1/0/1
port-security port-mode userlogin-withoui
#
Precautions
l Before enabling port security, be sure to disable 802.1x and MAC authentication globally.
l On a port configured with port security, you cannot configure the maximum number of MAC addresses that the port can learn, reflector port for port mirroring, fabric port, or link aggregation.
Configuring Port Security mac-else-userlogin-secure-ext Mode
In mac-else-userlogin-secure-ext mode, a port first performs MAC authentication of a user. If the authentication is successful, the user can access the port; otherwise, the port performs 802.1x authentication of the user. In this mode, there can be more than one authenticated user on a port.
Network Diagram
Figure 1-4 Network diagram for configuring port security mac-else-userlogin-secure-ext mode

Networking and Configuration Requirements
The host connects to the switch through the port Ethernet 1/0/1, and the switch authenticates the host through the RADIUS server. After successful authentication, the host is authorized to access the Internet.
On port Ethernet 1/0/1 of the switch, perform configurations to meet the following requirements:
l Perform MAC authentication of users and then 802.1x authentication if MAC authentication fails.
l Allow up to 64 802.1x authenticated users to get online. The total number of 802.1x authenticated users and MAC address authenticated users cannot exceed 200.
l All users belong to the domain aabbcc.net, and each user uses the MAC address of the host as the username and password for authentication.
l Enable NeedToKnow feature to prevent packets from being sent to unknown destination MAC addresses.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-SI/EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-52P |
Release 1602 |
S3100-52P |
Configuration Procedure
![]()
l The following configurations involve some AAA/RADIUS configuration commands. For details about the commands, refer to AAA Operation.
l Configurations on the user host and the RADIUS server are omitted.
l Configure RADIUS parameters
# Create a RADIUS scheme named radius1.
<Switch> system-view
[Switch] radius scheme radius1
# Specify the primary RADIUS authentication server and primary RADIUS accounting server.
[Switch-radius-radius1] primary authentication 192.168.1.3
[Switch-radius-radius1] primary accounting 192.168.1.2
# Specify the secondary RADIUS authentication server and secondary RADIUS accounting server.
[Switch-radius-radius1] secondary authentication 192.168.1.2
[Switch-radius-radius1] secondary accounting 192.168.1.3
# Set the shared key for message exchange between the switch and the RADIUS authentication servers to name.
[Switch-radius-radius1] key authentication name
# Set the shared key for message exchange between the switch and the accounting RADIUS servers to name.
[Switch-radius-radius1] key accounting name
# Set the interval and the number of packet transmission attempts for the switch to send packets to the RADIUS server.
[Switch-radius-radius1] timer 5
[Switch-radius-radius1] retry 5
# Set the timer for the switch to send real-time accounting packets to the RADIUS server to 15 minutes.
[Switch-radius-radius1] timer realtime-accounting 15
# Configure the switch to send a username without the domain name to the RADIUS server.
[Switch-radius-radius1] user-name-format without-domain
[Switch-radius-radius1] quit
# Create a domain named aabbcc.net and enter its view.
[Switch] domain aabbcc.net
# Specify the RADIUS scheme for the domain.
[Switch-isp-aabbcc.net] scheme radius-scheme radius1
# Enable the idle disconnecting function and set the related parameters.
[Switch-isp-aabbcc.net] idle-cut enable 20 2000
[Switch-isp-aabbcc.net] quit
# Set aabbcc.net as the default user domain.
[Switch] domain default enable aabbcc.net
# Set the maximum number of concurrent 802.1x users.
[Switch] dot1x max-user 64
# Configure the switch to use MAC addresses as usernames for authentication, specifying that the MAC addresses should be lowercase without separators.
[Switch] mac-authentication authmode usernameasmacaddress usernameformat without-hyphen
# Specify the ISP domain for MAC authentication.
[Switch] mac-authentication domain aabbcc.net
# Enable port security.
[Switch] port-security enable
# Set the maximum number of secure MAC addresses allowed on the port to 200.
[Switch] interface Ethernet 1/0/1
[Switch-Ethernet1/0/1] port-security max-mac-count 200
# Set the port security mode to mac-else-userlogin-secure-ext.
[Switch-Ethernet1/0/1] port-security port-mode mac-else-userlogin-secure-ext
# Set the NeedToKnow mode of the port to ntkonly.
[Switch-Ethernet1/0/1] port-security ntk-mode ntkonly
Complete Configuration
#
domain default enable aabbcc.net
#
port-security enable
#
MAC-authentication domain aabbcc.net
#
radius scheme radius1
server-type standard
primary authentication 192.168.1.3
primary accounting 192.168.1.2
secondary authentication 192.168.1.2
secondary accounting 192.168.1.3
key authentication name
key accounting name
timer realtime-accounting 15
timer response-timeout 5
retry 5
user-name-format without-domain
#
domain aabbcc.net
scheme radius-scheme radius1
idle-cut enable 20 2000
#
interface Ethernet1/0/1
port-security max-mac-count 200
port-security port-mode mac-else-userlogin-secure-ext
port-security ntk-mode ntkonly
dot1x max-user 64
Precautions
l Before enabling port security, be sure to disable 802.1x and MAC authentication globally.
l On a port configured with port security, you cannot configure the maximum number of MAC addresses that the port can learn, reflector port for port mirroring, fabric port, or link aggregation.
