- Table of Contents
-
- H3C MSR5680-X3 Router Configuration Examples All-in-One-R9141-6W100
- 00-Preface
- 01-AAA Configuration Examples
- 02-ACL Configuration Examples
- 03-MPLS over ADVPN Configuration Examples
- 04-ARP Attack Protection Configuration Examples
- 05-BFD Configuration Examples
- 06-Basic BGP Configuration Examples
- 07-BGP Route Attribute-Based Route Selection Configuration Examples
- 08-EAA Monitor Policy Configuration Examples
- 09-GRE with OSPF Configuration Examples
- 10-HoVPN Configuration Examples
- 11-IGMP Configuration Examples
- 12-IPsec Configuration Examples
- 13-IPsec Digital Certificate Authentication Configuration Examples
- 14-IPv6 IS-IS Configuration Examples
- 15-IPv6 over IPv4 GRE Tunnel Configuration Examples
- 16-IPv6 over IPv4 Manual Tunnel with OSPFv3 Configuration Examples
- 17-IS-IS Configuration Examples
- 18-Combined ISATAP Tunnel and 6to4 Tunnel Configuration Examples
- 19-L2TP over IPsec Configuration Examples
- 20-Multi-Instance L2TP Configuration Examples
- 21-L2TP Multidomain Access Configuration Examples
- 22-MPLS L3VPN Configuration Examples
- 23-MPLS OAM Configuration Examples
- 24-MPLS TE Configuration Examples
- 25-Basic MPLS Configuration Examples
- 26-NAT DNS Mapping Configuration Examples
- 27-NetStream Configuration Examples
- 28-NQA Configuration Examples
- 29-NTP Configuration Examples
- 30-OSPFv3 Configuration Examples
- 31-OSPF Configuration Examples
- 32-OSPF Multi-Process Configuration Examples
- 33-OSPF Multi-Instance Configuration Examples
- 34-Portal Configuration Examples
- 35-POS Interace Configuration Examples
- 36-PPP Configuration Examples
- 37-RBAC Configuration Examples
- 38-RMON Configuration Examples
- 39-IPv4 NetStream Sampling Configuration Examples
- 40-SNMP Configuration Examples
- 41-SRv6 Configuration Examples
- 42-SSH Configuration Examples
- 43-Tcl Commands Configuration Examples
- 44-VLAN Configuration Examples
- 45-VRRP Configuration Examples
- 46-VXLAN over IPsec Configuration Examples
- 47-Cloudnet VPN Configuration Examples
- 48-Ethernet Link Aggregation Configuration Examples
- 49-Ethernet OAM Configuration Examples
- 50-Outbound Bidirectional NAT Configuration Examples
- 51-NAT Hairpin in C-S Mode Configuration Examples
- 52-Load Sharing NAT Server Configuration Examples
- 53-BIDIR-PIM Configuration Examples
- 54-Control Plane-Based QoS Policy Configuration Examples
- 55-Scheduling a Task Configuration Examples
- 56-Client-Initiated L2TP Tunnel Configuration Examples
- 57-LAC-Auto-Initiated L2TP Tunnel Configuration Examples
- 58-Authorized ARP Configuration Examples
- 59-GTS Configuration Examples
- 60-Traffic Policing Configuration Examples
- 61-Traffic Accounting Configuration Examples
- 62-PBR Configuration Examples
- 63-TFTP Client Software Upgrade Configuration Examples
- 64-FTP Client Software Upgrade Configuration Examples
- 65-FTP Server Software Upgrade Configuration Examples
- 66-Routing Policy Configuration Examples
- 67-Software Upgrade from the BootWare Menu Configuration Examples
- 68-Mirroring Configuration Examples
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 04-ARP Attack Protection Configuration Examples | 154.10 KB |
|
|
|
H3C Routers |
|
ARP Attack Protection |
|
Configuration Examples |
Copyright © 2024 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Contents
Example: Configuring ARP scanning and fixed ARP
Example: Configuring ARP active acknowledgement
Example: Configuring source MAC-based ARP attack detection
Example: Configuring ARP source suppression
Introduction
The following information provides examples for configuring ARP attack protection on routers.
Prerequisites
This document applies to Comware 9-based routers. Procedures and information in the examples might be slightly different depending on the software or hardware version of the router.
The configuration examples in this document were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
This document assumes that you have basic knowledge of ARP attack protection.
Example: Configuring ARP scanning and fixed ARP
Network configuration
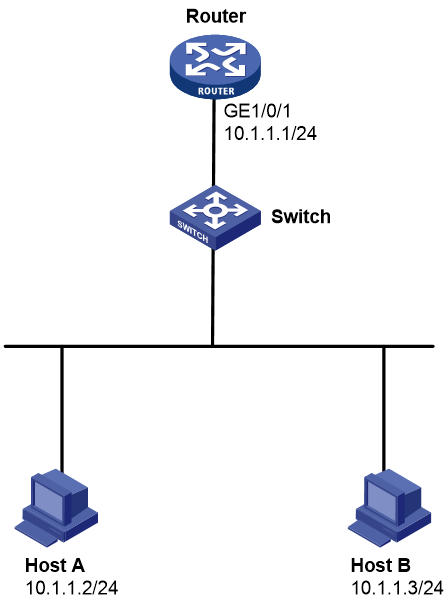
As shown in Figure 1, Host A connects to the external network through a gateway (Router). Configure ARP scanning and fixed ARP to meet the following requirements:
· Disable the router from learning dynamic ARP entries.
· Host B cannot access the router.
Software versions used
This configuration example was created and verified on R9141P16 of the MSR5680-X3 device.
Procedures
# Specify an IP address for GigabitEthernet 1/0/1.
<Router> system-view
[Router] interface gigabitethernet 1/0/1
[Router-GigabitEthernet1/0/1] ip address 10.1.1.1 24
# Enable ARP scanning on GigabitEthernet 1/0/1. (The command is not displayed in the configuration file.)
[Router-GigabitEthernet1/0/1] arp scan
This operation may take a long time to collect these ARP entries, and you can press CTRL_C to break. Please specify a right range. Continue? [Y/N]: y
Scanning ARP. Please wait...
Scanning is complete.
[Router-GigabitEthernet1/0/1]quit
# Display ARP entry information on the router when the network has only one host.
[Router] display arp
Type: S-Static D-Dynamic O-Openflow R-Rule I-Invalid
IP address MAC address VLAN/VSI name Interface Aging Type
10.1.1.2 0015-e943-7e6a -- -- -- D
# Convert the existing dynamic ARP entry to a static ARP entry. (The command is not displayed in the configuration file.)
[Router] arp fixup
This command will convert existing dynamic ARP entries to static ARP entries. Continue? [Y/N]:y
Fixup ARP. Please wait...
Fixup is complete.
# Display the converted ARP entry.
[Router] display arp
Type: S-Static D-Dynamic O-Openflow R-Rule I-Invalid
IP address MAC address VLAN/VSI name Interface Aging Type
10.1.1.2 0015-e943-7e6a -- -- -- S
# Disable GigabitEthernet 1/0/1 from learning dynamic ARP entries.
[Router] interface gigabitethernet 1/0/1
[Router-GigabitEthernet1/0/1] arp max-learning-num 0
[Router-GigabitEthernet1/0/1] quit
Verifying the configuration
# Add Host B to the LAN and display ARP entry information on the router.
[Router] display arp
Type: S-Static D-Dynamic O-Openflow R-Rule I-Invalid
IP address MAC address VLAN/VSI name Interface Aging Type
10.1.1.2 0015-e943-7e6a -- -- -- S
The output shows that the router does not have any ARP entry for Host B.
# Verify that Host B cannot ping the router.
C:\> ping 10.1.1.1
Pinging 10.1.1.1 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 10.1.1.1:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
Configuration files
#
interface GigabitEthernet1/0/1
port link-mode route
ip address 10.1.1.1 255.255.255.0
arp max-learning-num 0
#
Example: Configuring ARP active acknowledgement
Network configuration
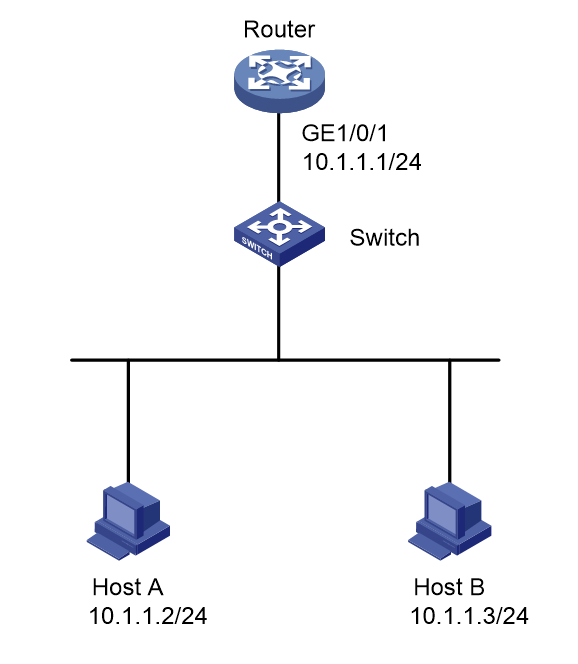
As shown in Figure 2, Host A connects to the external network through a gateway (Router). Configure ARP active acknowledgement to prevent user spoofing.
Software versions used
This configuration example was created and verified on R9141P16 of the MSR5680-X3 device.
Procedures
# Specify an IP address for GigabitEthernet 1/0/1.
<Router> system-view
[Router] interface gigabitethernet 1/0/1
[Router-GigabitEthernet1/0/1] ip address 10.1.1.1 24
[Router-GigabitEthernet1/0/1] quit
# Enable ARP active acknowledgement.
[Router] arp active-ack enable
Verifying the configuration
# Display authorized ARP entry information on the router.
[Router] display arp
Type: S-Static D-Dynamic O-Openflow R-Rule I-Invalid
IP address MAC address VLAN/VSI name Interface Aging Type
10.1.1.2 000f-e123-4568 -- GE1/0/1 20 D
The output shows that the router has an ARP entry for Host A.
# Enable debugging for ARP packets.
<Router> terminal debugging
The current terminal is enabled to display debugging logs.
<Router> debugging arp packet
# Use Host B to send a forged ARP request in which the sender MAC address is 0086-0005-0004 to the gateway. Upon receiving the ARP request, the router finds that the update interval for the corresponding ARP entry is more than 1 minute. Enabled with ARP active acknowledgement, the gateway sends a unicast ARP request in which the target IP and MAC addresses are the IP and MAC addresses in the ARP entry. If the gateway receives an ARP reply within 5 seconds, it compares the sender IP and MAC addresses in the ARP reply with those in the received ARP request.
*Jul 3 18:07:38:660 2013 Router ARP/7/ARP_RCV: Received an ARP message, operation: 1, sender MAC: 0086-0005-0004, sender IP: 10.1.1.2, target MAC: 0cda-41c7-057f, target IP: 10.1.1.1
*Jul 3 18:07:38:660 2013 Router ARP/7/ARP_SEND: Sent an ARP message, operation: 1, sender
MAC: 0cda-41c7-057f, sender IP: 10.1.1.1, target MAC: 000f-e123-4568, target IP: 10.1.1.2
*Jul 3 18:07:38:660 2013 Router ARP/7/ARP_SEND: Sent an ARP message, operation: 2, sender
MAC:0cda-41c7-057f, sender IP: 10.1.1.1, target MAC: 0086-0005-0004, target IP: 10.1.1.2
*Jul 3 18:07:38:660 2013 Router ARP/7/ARP_RCV: Received an ARP message, operation: 2, sender MAC: 000f-e123-4568, sender IP: 10.1.1.2, target MAC: 0cda-41c7-057f, target IP: 10.1.1.1
The output shows that the received ARP reply is sent from Host A. The sender IP and MAC addresses in the ARP reply matches the ARP entry. Then, the gateway regards the received ARP request as an attack packet.
# Display ARP entry information on the router.
<Router> display arp
Type: S-Static D-Dynamic O-Openflow R-Rule I-Invalid
IP address MAC address VLAN/VSI name Interface Aging Type
10.1.1.2 000f-e123-4568 -- GE1/0/1 20 D
The output shows that the ARP entry is not updated.
Configuration files
#
interface GigabitEthernet1/0/1
port link-mode route
ip address 10.1.1.1 255.255.255.0
#
arp active-ack enable
#
Example: Configuring source MAC-based ARP attack detection
Network configuration
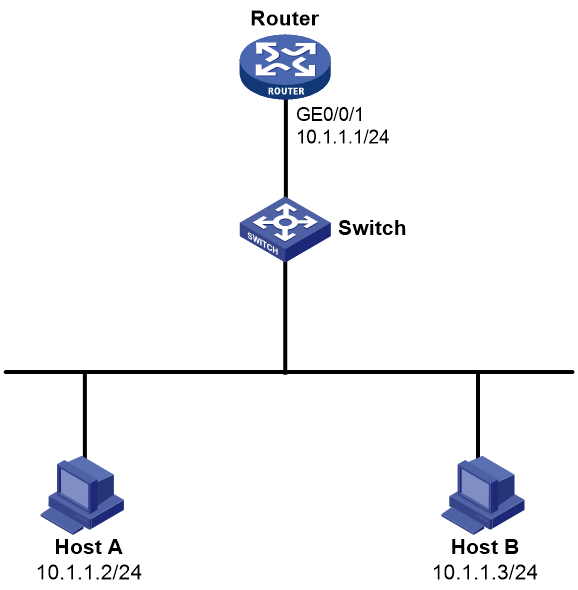
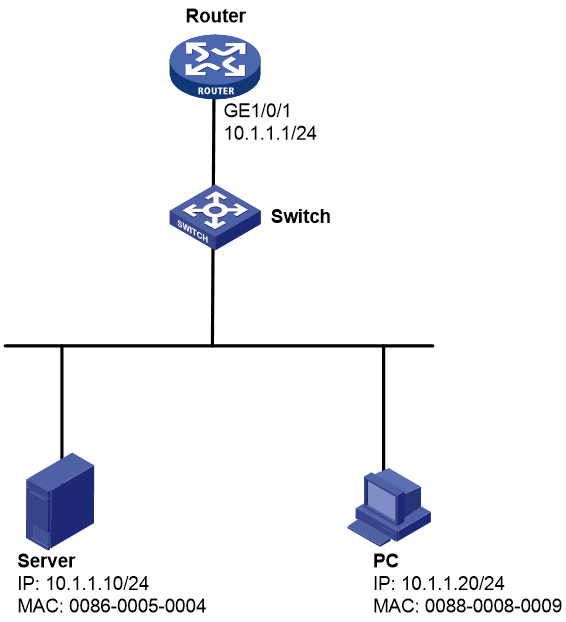
As shown in Figure 3, the server and PC access the Internet through a gateway (Router).
Configure source MAC-based ARP attack detection on the router to meet the following requirements:
· If the number of ARP packets received from the PC within 5 seconds exceeds 30, the device generates log messages and filters out subsequent ARP packets from the PC.
· Exclude the MAC address of the server from source MAC-based ARP attack detection.
Analysis
Enable source MAC-based ARP attack detection on the router and specify the filter handling method.
Software versions used
This configuration example was created and verified on R9141P16 of the MSR5680-X3 device.
Procedures
# Enable source MAC-based ARP attack detection and specify the filter handling method.
<Router> system-view
[Router] arp source-mac filter
# Set the threshold to 30.
[Router] arp source-mac threshold 30
# Set the aging time for ARP attack entries to 60 seconds.
[Router] arp source-mac aging-time 60
# Exclude MAC address 0086-0005-0004 from this detection.
[Router] arp source-mac exclude-mac 0086-0005-0004
# Specify an IP address for GigabitEthernet 1/0/1.
[Router] interface gigabitethernet 1/0/1
[Router-GigabitEthernet1/0/1] ip address 10.1.1.1 24
[Router-GigabitEthernet1/0/1] quit
Verifying the configuration
# Enable debugging for ARP packets.
<Router> terminal debugging
The current terminal is enabled to display debugging logs.
<Router> debugging arp packet
# Use the PC to send ARP packets to the router at a rate of 6 pps. Display ARP attack entries detected by source MAC-based ARP attack detection on the router.
<Router> display arp source-mac interface GigabitEthernet1/0/1
Source-MAC VLAN ID Interface Aging-time
The router does not generate any log message or ARP attack entry.
# Use the PC to send ARP packets to the router at a rate of 10 pps. Display ARP attack entries detected by source MAC-based ARP attack detection on the router.
<Router> display arp source-mac interface GigabitEthernet1/0/1
Source-MAC VLAN ID Interface Aging-time
0088-0008-0009 N/A GE1/0/1 48
The output shows that the router has generated an ARP attack entry.
# Log messages generated by the router are as follows:
*Jun 20 13:54:42:482 2013 Router ARP/7/ARP_RCV: Received an ARP message, opera
tion: 1, sender MAC: 0088-0008-0009, sender IP: 10.1.1.20, target MAC: 0cda-41c7
-057f, target IP: 10.1.1.1
*Jun 20 13:54:42:482 2013 Router ARP/7/ARP_SEND: Sent an ARP message, operatio
n: 2, sender MAC: 0cda-41c7-057f, sender IP: 10.1.1.1, target MAC: 0088-0008-000
9, target IP: 10.1.1.20
*Jun 20 13:54:42:582 2013 Router ARP/7/ARP_RCV: Received an ARP message, opera
tion: 1, sender MAC: 0088-0008-0009, sender IP: 10.1.1.20, target MAC: 0cd
a-41c7-057f, target IP: 10.1.1.1
*Jun 20 13:54:42:582 2013 Router ARP/7/ARP_SEND: Sent an ARP message, operatio
n: 2, sender MAC: 0cda-41c7-057f, sender IP: 10.1.1.1, target MAC: 0088-0008-000
9, target IP: 10.1.1.20
*Jun 20 13:54:42:682 2013 Router ARP/7/ARP_RCV: Received an ARP message, opera
tion: 1, sender MAC: 0088-0008-0009, sender IP: 10.1.1.20, target MAC: 0cda-41c7
-057f, target IP: 10.1.1.1
*Jun 20 13:54:42:682 2013 Router ARP/7/ARP_SEND: Sent an ARP message, operatio
n: 2, sender MAC: 0cda-41c7-057f, sender IP: 10.1.1.1, target MAC: 0088-0008-000
9, target IP: 10.1.1.20
# Use the server to send ARP packets to the router at a rate of 10 pps. Display ARP attack entries detected by source MAC-based ARP attack detection on the router.
<Router> display arp source-mac interface GigabitEthernet1/0/1
Source-MAC VLAN ID Interface Aging-time
The router does not generate any log message or ARP attack entry.
Configuration files
#
interface GigabitEthernet1/0/1
port link-mode route
shutdown
ip address 10.1.1.1 255.255.255.0
#
arp source-mac filter
arp source-mac aging-time 60
arp source-mac exclude-mac 0086-0005-0004
#
Example: Configuring ARP source suppression
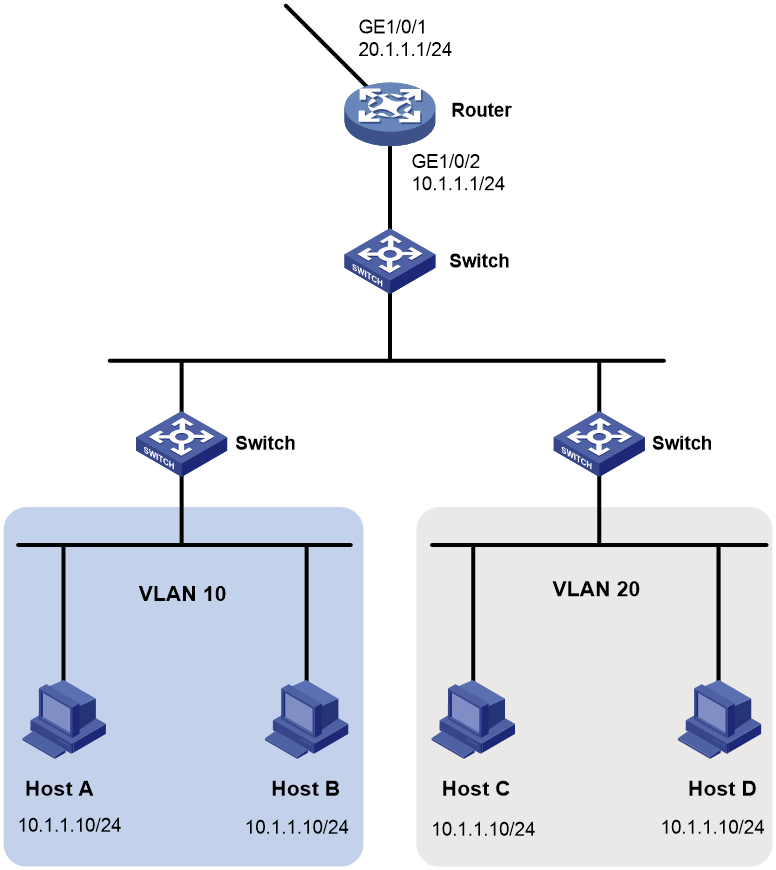
Network configuration
As shown in Figure 4, the hosts in VLAN 10 and VLAN 20 access the Internet through a gateway (Router).
Configure ARP source suppression on the router to protect the router from processing a large number of unresolvable IP packets from the same IP address.
Software versions used
This configuration example was created and verified on R9141P16 of the MSR5680-X3 device.
Procedures
# Specify IP addresses for GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2.
<Router> system-view
[Router] interface gigabitethernet 1/0/1
[Router-GigabitEthernet1/0/1] ip address 20.1.1.1 24
[Router-GigabitEthernet1/0/1] quit
[Router] interface gigabitethernet 1/0/2
[Router-GigabitEthernet1/0/2] ip address 10.1.1.1 24
[Router-GigabitEthernet1/0/2] quit
# Enable ARP source suppression.
[Router] arp source-suppression enable
# Configure the router to process a maximum of 2 unresolvable packets per source IP address within 5 seconds.
[Router] arp source-suppression limit 2
Verifying the configuration
# Use Host D to send IP packets with destination address 20.1.1.2 which does not exist in the LAN to the router. Verify how the router processes ARP packets with ARP source suppression enabled.
# Enable debugging for ARP packets.
<Router> terminal debugging
The current terminal is enabled to display debugging logs.
<Router> debugging arp packet
*Jul 23 17:29:03:061 2014 Router ARP/7/ARP_SEND: Sent an ARP message, operation: 1,
sender MAC: d07e-28e6-6814, sender IP: 20.1.1.1, target MAC: 0000-0000-0000, tar
get IP: 20.1.1.2
*Jul 23 17:29:05:262 2014 Router ARP/7/ARP_SEND: Sent an ARP message, operation: 1,
sender MAC: d07e-28e6-6814, sender IP: 20.1.1.1, target MAC: 0000-0000-0000, tar
get IP: 20.1.1.2
*Jul 23 17:29:07:462 2014 Router ARP/7/ARP_SEND: Sent an ARP message, operation: 1,
sender MAC: d07e-28e6-6814, sender IP: 20.1.1.1, target MAC: 0000-0000-0000, tar
get IP: 20.1.1.2
*Jul 23 17:29:09:662 2014 Router ARP/7/ARP_SEND: Sent an ARP message, operation: 1,
sender MAC: d07e-28e6-6814, sender IP: 20.1.1.1, target MAC: 0000-0000-0000, tar
get IP: 20.1.1.2
*Jul 23 17:29:11:862 2014 Router ARP/7/ARP_SEND: Sent an ARP message, operation: 1,
sender MAC: d07e-28e6-6814, sender IP: 20.1.1.1, target MAC: 0000-0000-0000, tar
get IP: 20.1.1.2
*Jul 23 17:29:14:062 2014 Router ARP/7/ARP_SEND: Sent an ARP message, operation: 1,
sender MAC: d07e-28e6-6814, sender IP: 20.1.1.1, target MAC: 0000-0000-0000, tar
get IP: 20.1.1.2
The output shows that when the router has processed 2 unresolvable packets from Host D within 5 seconds, it stops processing the packets from Host D until the 5 seconds elapse.
Configuration files
#
interface GigabitEthernet1/0/1
port link-mode route
ip address 20.1.1.1 255.255.255.0
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 10.1.1.1 255.255.255.0
#
arp source-suppression enable
arp source-suppression limit 2
#
Related documentation
· Security Configuration Guide in H3C MSR5680-X3 Router Configuration Guides(V9)
· Security Command Reference in H3C MSR5680-X3 Router Command References(V9)