- Table of Contents
-
- 02-WLAN
- 00-Preface
- 01-AP management configuration
- 02-Radio management configuration
- 03-WLAN access configuration
- 04-WLAN security configuration
- 05-WLAN authentication configuration
- 06-WIPS configuration
- 07-WLAN QoS configuration
- 08-WLAN roaming configuration
- 09-WLAN load balancing configuration
- 10-WLAN radio resource measurement configuration
- 11-Channel scanning configuration
- 12-Band navigation configuration
- 13-WLAN high availability configuration
- 14-802.11r configuration
- 15-Wireless location configuration
- 16-Hotspot 2.0 configuration
- 17-WLAN RRM configuration
- 18-WT configuration
- 19-IoT AP configuration
- 20-CM tunnel configuration
- 21-Cloud connection configuration
- 22-WLAN IP snooping configuration
- 23-WLAN fast forwarding configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 14-802.11r configuration | 134.20 KB |
Intra-AC roaming through over-the-air FT
Inter-AC roaming through over-the-air FT
Intra-AC roaming through over-the-DS FT
802.11r configuration examples
Over-the-DS FT and PSK authentication configuration example
Over-the-air FT and PSK authentication configuration example
Over-the-DS FT and 802.1X authentication configuration example
Over-the-air FT and 802.1X authentication configuration example
Configuring 802.11r
This chapter describes how to configure 802.11r.
802.11r overview
802.11r fast BSS transition (FT) minimizes the delay when a client roams from a BSS to another BSS within the same ESS. During 802.11r FT, a client needs to exchange messages with the target AP. FT provides the following message exchanging methods:
· Over-the-air—The client communicates directly with the target AP for pre-roaming authentication.
· Over-the-DS—The client communicates with the target AP through the current AP for pre-roaming authentication.
802.11r operating mechanism
Intra-AC roaming through over-the-air FT
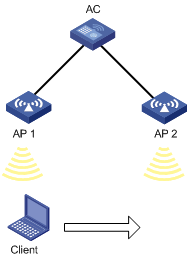
As shown in Figure 1, the client is associated with AP 1. Intra-AC roaming through over-the-air FT uses the following procedure:
1. The client sends an FT authentication request to AP 2.
2. AP 2 sends an FT authentication response to the client.
3. The client sends a reassociation request to AP 2.
4. AP 2 sends a reassociation response to the client.
5. The client roams to AP 2.
Figure 1 Intra-AC roaming through over-the-air FT
Inter-AC roaming through over-the-air FT
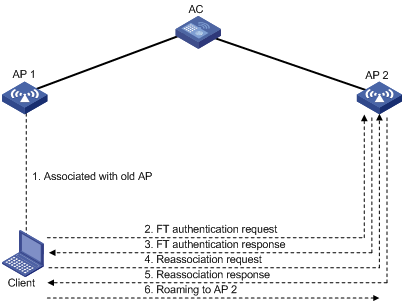
As shown in Figure 2, the client is associated with AP 1. Inter-AC roaming through over-the-air FT uses the following procedure:
1. After the client comes online, AC 1 sends roaming information for the client to AC 2. Roaming information includes the PMK and the client VLAN.
2. The client sends an FT authentication request to AP 2.
3. AP 2 sends an FT authentication response to the client.
4. The client sends a reassociation request to AP 2.
5. AP 2 sends a reassociation response to the client.
6. The client roams to AP 2.
Figure 2 Inter-AC roaming through over-the-air FT
Intra-AC roaming through over-the-DS FT
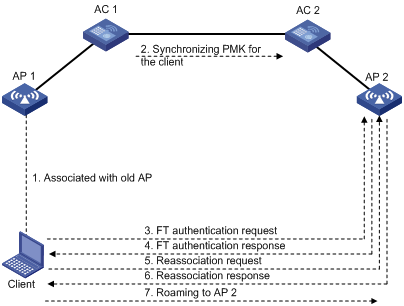
As shown in Figure 3, the client is associated with AP 1. Intra-AC roaming through over-the-DS FT uses the following procedure:
1. After the client comes online, the AC creates a roaming entry and saves it for the client.
2. The client sends an FT authentication request to AP 1.
3. AP 1 sends an FT authentication response to the client.
4. The client sends a reassociation request to AP 2.
5. AP 2 sends a reassociation response to the client.
6. The client roams to AP 2.
Figure 3 Intra-AC roaming through over-the-DS FT
Protocols and standards
Configuring 802.11r
Follow these restrictions and guidelines when you configure 802.11r:
· To enable a client that does not support FT to access the WLAN, create two service templates using the same SSID, with one enabled with FT and the other not.
· To prevent a client from coming online every time the periodic reauthentication timer expires, do not enable FT and periodic reauthentication for the same service template. For more information about periodic reauthentication, see "Configuring WLAN authentication."
· PTK updates are not supported for clients that have been associated with a WLAN through FT. For more information about PTK updates, see "Configuring WLAN security."
To configure 802.11r:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
|
|
2. Enter service template view. |
N/A |
|
|
3. Enable FT. |
ft enable |
By default, FT is disabled. |
|
4. (Optional.) Set the FT method. |
By default, the FT method is over-the-air. |
|
|
5. (Optional.) Set the reassociation timeout timer. |
By default, the association timeout timer is 20 seconds. The roaming process is terminated if a client does not send any reassociation requests before the timeout timer expires. |
802.11r configuration examples
Over-the-DS FT and PSK authentication configuration example
Network requirements
As shown in Figure 4, configure intra-AC roaming through over-the-DS FT to enable the client to roam between AP 1 and AP 2. Configure PSK as the authentication and key management mode.
Configuration procedures
# Create the service template acstname.
[AC] wlan service-template acstname
# Set the SSID to service.
[AC-wlan-st-acstname] ssid service
# Set the authentication and key management mode to PSK, and configure the simple string 12345678 as the PSK.
[AC-wlan-st-acstname] akm mode psk
[AC-wlan-st-acstname] preshared-key pass-phrase simple 12345678
# Set the CCMP cipher suite and enable the RSN IE in the beacon and probe responses.
[AC-wlan-st-acstname] cipher-suite ccmp
[AC-wlan-st-acstname] security-ie rsn
[AC-wlan-st-acstname] ft enable
# Set the reassociation timeout timer to 50 seconds.
[AC-wlan-st-acstname] ft reassociation-timeout 50
# Set the FT method to over-the-DS.
[AC-wlan-st-acstname] ft method over-the-ds
# Enable the service template.
[AC-wlan-st-acstname] service-template enable
[AC-wlan-st-acstname] quit
# Create AP 1, and bind the service template acstname to radio 2 of the AP.
[AC] wlan ap 1
[AC-wlan-ap-1] radio 2
[AC-wlan-ap-1-radio-2] service-template acstname
[AC-wlan-ap-1-radio-2] radio enable
[AC-wlan-ap-1-radio-2] quit
# Create AP 2, and bind the service template acstname to radio 2 of the AP.
[AC] wlan ap 2
[AC-wlan-ap-2] radio 2
[AC-wlan-ap-2-radio-2] service-template acstname
[AC-wlan-ap-2-radio-2] radio enable
[AC-wlan-ap-2-radio-2] quit
[AC-wlan-ap-2] quit
Verifying the configuration
# Verify that the service template is correctly configured.
[AC] display wlan service-template acstname verbose
Service template name : acstname
SSID : service
SSID-hide : Disabled
User-isolation : Disabled
Service template status : Enabled
Maximum clients per BSS : Not configured
Frame format : Dot3
Seamless-roam : Disabled
Seamless-roam RSSI threshold : 50
Seamless-roam RSSI gap : 20
VLAN ID : 1
AKM mode : PSK
Security IE : RSN
Cipher suite : CCMP
TKIP countermeasure time : 0 sec
PTK lifetime : 43200 sec
GTK rekey : Enabled
GTK rekey method : Time-based
GTK rekey time : 86400 sec
GTK rekey client-offline : Disabled
User authentication mode : Bypass
Intrusion protection : Disabled
Intrusion protection mode : Temporary-block
Temporary block time : 180 sec
Temporary service stop time : 20 sec
Fail VLAN ID : Not configured
802.1X handshake : Disabled
802.1X handshake secure : Disabled
802.1X domain : Not configured
MAC-auth domain : Not configured
Max 802.1X users : 4096
Max MAC-auth users : 4096
802.1X re-authenticate : Disabled
Authorization fail mode : Online
Accounting fail mode : Online
Authorization : Permitted
Key derivation : SHA1
PMF status : Disabled
Hotspot policy number : Not configured
Forward policy : Not configured
Forwarder : AC
FT Status : Enable
FT Method : over-the-ds
FT Reassociation Deadline : 50 sec
QoS trust : Port
QoS priority : 0
# Verify that the roaming status is N/A and the FT status is Active.
[AC] display wlan client verbose
Total number of clients: 1
MAC address : fc25-3f03-8361
IPv4 address : 10.1.1.114
IPv6 address : N/A
Username : N/A
AID : 1
AP ID : 1
AP name : 1
Radio ID : 2
SSID : service
BSSID : 000f-e266-7788
VLAN ID : 1
Power save mode : Active
Wireless mode : 802.11gn
Channel bandwidth : 20MHz
SM power save : Enabled
SM power save mode : Static
Short GI for 20MHz : Not supported
Short GI for 40MHz : Not supported
STBC RX capability : Supported
STBC TX capability : Not supported
Support HT-MCS set : 0, 1, 2, 3, 4, 5, 6, 7
QoS mode : WMM
Listen interval : 20
RSSI : 0
Rx/Tx rate : 65/65
Authentication method : Open system
Security mode : RSN
AKM mode : PSK
Encryption cipher : CCMP
User authentication mode : Bypass
Authorization ACL ID : N/A
Authorization user profile : N/A
Roam status : N/A
Key derivation : SHA256
PMF status : N/A
Forward policy : N/A
Online time : 0hr 0min 41sec
FT status : Active
# Moves the client to the coverage of AP 2. (Details not shown.)
# Verify that the authentication method is FT and the roaming status is Intra-AC roam.
[AC] display wlan client verbose
Total number of clients: 1
MAC address : fc25-3f03-8361
IPv4 address : 10.1.1.114
IPv6 address : N/A
Username : N/A
AID : 1
AP ID : 2
AP name : 2
Radio ID : 2
SSID : service
BSSID : 000f-e211-2233
VLAN ID : 1
Power save mode : Active
Wireless mode : 802.11gn
Channel bandwidth : 20MHz
SM power save : Enabled
SM power save mode : Static
Short GI for 20MHz : Not supported
Short GI for 40MHz : Not supported
STBC RX capability : Supported
STBC TX capability : Not supported
Support HT-MCS set : 0, 1, 2, 3, 4, 5, 6, 7
QoS mode : WMM
Listen interval : 20
RSSI : 0
Rx/Tx rate : 0/0
Authentication method : FT
Security mode : RSN
AKM mode : PSK
Encryption cipher : CCMP
User authentication mode : Bypass
Authorization ACL ID : N/A
Authorization user profile : N/A
Roam status : Intra-AC roam
Key derivation : SHA256
PMF status : N/A
Forward policy : N/A
Online time : 0hr 0min 27sec
FT status : Active
Over-the-air FT and PSK authentication configuration example
Network requirements
As shown in Figure 4, configure intra-AC roaming through over-the-air FT to enable the client to roam between AP 1 and AP 2. Configure PSK as the authentication and key management mode.
Configuration procedures
# Create the service template acstname.
<AC> system-view
[AC] wlan service-template acstname
[AC-wlan-st-acstname] ssid service
# Set the authentication and key management mode to PSK, and configure the simple string 12345678 as the PSK.
[AC-wlan-st-acstname] akm mode psk
[AC-wlan-st-acstname] preshared-key pass-phrase simple 12345678
# Enable the RSN IE in the beacon and probe responses.
[AC-wlan-st-acstname] cipher-suite ccmp
[AC-wlan-st-acstname] security-ie rsn
[AC-wlan-st-acstname] ft enable
# Set the reassociation timeout to 50 seconds.
[AC-wlan-st-acstname] ft reassociation-timeout 50
# Enable the service template.
[AC-wlan-st-acstname] service-template enable
[AC-wlan-st-acstname] quit
# Create AP 1, and bind the service template acstname to radio 2 of the AP.
[AC] wlan ap 1
[AC-wlan-ap-1] radio 2
[AC-wlan-ap-1-radio-2] service-template acstname
[AC-wlan-ap-1-radio-2] radio enable
[AC-wlan-ap-1-radio-2] quit
# Create AP 2, and bind the service template acstname to radio 2 of the AP.
[AC] wlan ap 2
[AC-wlan-ap-2] radio 2
[AC-wlan-ap-2-radio-2] service-template acstname
[AC-wlan-ap-2-radio-2] radio enable
[AC-wlan-ap-2-radio-2] quit
[AC-wlan-ap-2] quit
Verifying the configuration
# Verify the following information:
· RSN IE is enabled.
· The AKM mode is PSK.
· The cipher suite is CCMP.
· The FT status is Active.
[AC] display wlan client verbose
Total number of clients: 1
MAC address : fc25-3f03-8361
IPv4 address : 10.1.1.114
IPv6 address : N/A
Username : N/A
AID : 1
AP ID : 1
AP name : 1
Radio ID : 2
SSID : service
BSSID : 000f-e266-7788
VLAN ID : 1
Power save mode : Active
Wireless mode : 802.11gn
Channel bandwidth : 20MHz
SM power save : Enabled
SM power save mode : Static
Short GI for 20MHz : Not supported
Short GI for 40MHz : Not supported
STBC RX capability : Supported
STBC TX capability : Not supported
Support HT-MCS set : 0, 1, 2, 3, 4, 5, 6, 7
QoS mode : WMM
Listen interval : 20
RSSI : 0
Rx/Tx rate : 65/65
Authentication method : Open system
Security mode : RSN
AKM mode : PSK
Encryption cipher : CCMP
User authentication mode : Bypass
Authorization ACL ID : N/A
Authorization user profile : N/A
Roam status : N/A
Key derivation : SHA256
PMF status : N/A
Forward policy : N/A
Online time : 0hr 0min 41sec
FT status : Active
# Move the client to the coverage of AP 2. (Details not shown.)
# Verify that the authentication method is FT and the roaming status is Intra-AC roam.
[AC] display wlan client verbose
Total number of clients: 1
MAC address : fc25-3f03-8361
IPv4 address : 10.1.1.114
IPv6 address : N/A
Username : N/A
AID : 1
AP ID : 2
AP name : 2
Radio ID : 2
SSID : service
BSSID : 000f-e211-2233
VLAN ID : 1
Power save mode : Active
Wireless mode : 802.11gn
Channel bandwidth : 20MHz
SM power save : Enabled
SM power save mode : Static
Short GI for 20MHz : Not supported
Short GI for 40MHz : Not supported
STBC RX capability : Supported
STBC TX capability : Not supported
Support HT-MCS set : 0, 1, 2, 3, 4, 5, 6, 7
QoS mode : WMM
Listen interval : 20
RSSI : 0
Rx/Tx rate : 0/0
Authentication method : FT
Security mode : RSN
AKM mode : PSK
Encryption cipher : CCMP
User authentication mode : Bypass
Authorization ACL ID : N/A
Authorization user profile : N/A
Roam status : Intra-AC roam
Key derivation : SHA256
PMF status : N/A
Forward policy : N/A
Online time : 0hr 0min 27sec
FT status : Active
Over-the-DS FT and 802.1X authentication configuration example
Network requirements
As shown in Figure 4, configure intra-AC roaming through over-the-DS FT to enable the client to roam between AP 1 and AP 2. Configure 802.1X as the authentication and key management mode.
Configuration procedures
# Create the service template acstname.
<AC> system-view
[AC] wlan service-template acstname
[AC-wlan-st-acstname] ssid service
[AC-wlan-st-acstname] akm mode dot1x
# Enable the RSN IE in the beacon and probe responses.
[AC-wlan-st-acstname] cipher-suite ccmp
[AC-wlan-st-acstname] security-ie rsn
# Set the authentication mode to 802.1X for clients.
[AC-wlan-st-acstname] client-security authentication-mode dot1x
[AC-wlan-st-acstname] dot1x domain imc
[AC-wlan-st-acstname] ft enable
# Set the FT method to over-the-DS.
[AC-wlan-st-acstname] ft method over-the-ds
# Enable the service template.
[AC-wlan-st-acstname] service-template enable
[AC-wlan-st-acstname] quit
# Set the 802.1X authentication mode to EAP.
[AC] dot1x authentication-method eap
# Create the RADIUS scheme imcc.
[AC] radius scheme imcc
# Set the IP address of the primary authentication and accounting servers to 10.1.1.3.
[AC-radius-imcc] primary authentication 10.1.1.3
[AC-radius-imcc] primary accounting 10.1.1.3
# Set the shared key for the AC to exchange packets with the authentication and accounting servers to 12345678.
[AC-radius-imcc] key authentication simple 12345678
[AC-radius-imcc] key accounting simple 12345678
# Configure the AC to remove the ISP domain name from usernames sent to the RADIUS server.
[AC-radius-imcc] user-name-format without-domain
[AC-radius-imcc] quit
# Create the ISP domain imc, and configure the domain to use the RADIUS scheme imcc for authentication, authorization, and accounting.
[AC] domain imc
[AC-isp-imc] authentication lan-access radius-scheme imcc
[AC-isp-imc] authorization lan-access radius-scheme imcc
[AC-isp-imc] accounting lan-access radius-scheme imcc
[AC-isp-imc] quit
# Create AP 1, and bind the service template acstname to radio 2 of the AP.
[AC] wlan ap 1
[AC-wlan-ap-1] radio 2
[AC-wlan-ap-1-radio-2] service-template acstname
[AC-wlan-ap-1-radio-2] radio enable
[AC-wlan-ap-1-radio-2] quit
# Create AP 2, and bind the service template acstname to radio 2 of the AP.
[AC] wlan ap 2
[AC-wlan-ap-2] radio 2
[AC-wlan-ap-2-radio-2] service-template acstname
[AC-wlan-ap-2-radio-2] radio enable
[AC-wlan-ap-2-radio-2] quit
[AC-wlan-ap-2] quit
Verifying the configuration
# Verify that the service template is correctly configured.
[AC] display wlan service-template acstname verbose
Service template name : stname
SSID : service
SSID-hide : Disabled
User-isolation : Disabled
Service template status : Enabled
Maximum clients per BSS : Not configured
Frame format : Dot3
Seamless-roam : Disabled
Seamless-roam RSSI threshold : 50
Seamless-roam RSSI gap : 20
VLAN ID : 1
AKM mode : 802.1X
Security IE : RSN
Cipher suite : CCMP
TKIP countermeasure time : 0 sec
PTK lifetime : 43200 sec
GTK rekey : Enabled
GTK rekey method : Time-based
GTK rekey time : 86400 sec
GTK rekey client-offline : Disabled
User authentication mode : 802.1X
Intrusion protection : Disabled
Intrusion protection mode : Temporary-block
Temporary block time : 180 sec
Temporary service stop time : 20 sec
Fail VLAN ID : Not configured
802.1X handshake : Disabled
802.1X handshake secure : Disabled
802.1X domain : imc
MAC-auth domain : Not configured
Max 802.1X users : 4096
Max MAC-auth users : 4096
802.1X re-authenticate : Disabled
Authorization fail mode : Online
Accounting fail mode : Online
Authorization : Permitted
Key derivation : SHA1
PMF status : Disabled
Hotspot policy number : Not configured
Forward policy : Not configured
Forwarder : AC
FT Status : Enable
FT Method : over-the-ds
FT Reassociation Deadline : 20 sec
QoS trust : Port
QoS priority : 0
# Verify that the roaming status is N/A and the FT status is Active.
[AC] display wlan client verbose
Total number of clients: 1
MAC address : fc25-3f03-8361
IPv4 address : 10.1.1.114
IPv6 address : N/A
Username : w2
AID : 1
AP ID : 1
AP name : 1
Radio ID : 2
SSID : service
BSSID : 000f-e266-7788
VLAN ID : 1
Power save mode : Active
Wireless mode : 802.11gn
Channel bandwidth : 20MHz
SM power save : Enabled
SM power save mode : Static
Short GI for 20MHz : Not supported
Short GI for 40MHz : Not supported
STBC RX capability : Supported
STBC TX capability : Not supported
Support HT-MCS set : 0, 1, 2, 3, 4, 5, 6, 7
QoS mode : WMM
Listen interval : 20
RSSI : 0
Rx/Tx rate : 0/0
Authentication method : Open system
Security mode : RSN
AKM mode : 802.1X
Encryption cipher : CCMP
User authentication mode : 802.1X
Authorization ACL ID : N/A
Authorization user profile : N/A
Roam status : N/A
Key derivation : SHA256
PMF status : N/A
Forward policy : N/A
Online time : 0hr 0min 7sec
FT status : Active
# Move the client to the coverage of AP 2. (Details not shown.)
# Verify that the authentication method is FT and the roaming status is Intra-AC roam.
[AC] display wlan client verbose
Total number of clients: 1
MAC address : fc25-3f03-8361
IPv4 address : 10.1.1.114
IPv6 address : N/A
Username : w2
AID : 1
AP ID : 2
AP name : 2
Radio ID : 2
SSID : service
BSSID : 000f-e211-2233
VLAN ID : 1
Power save mode : Active
Wireless mode : 802.11gn
Channel bandwidth : 20MHz
SM power save : Enabled
SM power save mode : Static
Short GI for 20MHz : Not supported
Short GI for 40MHz : Not supported
STBC RX capability : Supported
STBC TX capability : Not supported
Support HT-MCS set : 0, 1, 2, 3, 4, 5, 6, 7
QoS mode : WMM
Listen interval : 20
RSSI : 0
Rx/Tx rate : 0/0
Authentication method : FT
Security mode : RSN
AKM mode : 802.1X
Encryption cipher : CCMP
User authentication mode : 802.1X
Authorization ACL ID : N/A
Authorization user profile : N/A
Roam status : Intra-AC roam
Key derivation : SHA256
PMF status : N/A
Forward policy : N/A
Online time : 0hr 0min 7sec
FT status : Active
Over-the-air FT and 802.1X authentication configuration example
Network requirements
As shown in Figure 4, configure intra-AC roaming through over-the-air FT to enable the client to roam between AP 1 and AP 2. Configure 802.1X as the authentication and key management mode.
Configuration procedures
# Create the service template acstname.
<AC> system-view
[AC]wlan service-template acstname
[AC-wlan-st-acstname] ssid service
[AC-wlan-st-acstname] akm mode dot1x
# Enable the RSN IE in the beacon and probe responses.
[AC-wlan-st-acstname] cipher-suite ccmp
[AC-wlan-st-acstname] security-ie rsn
# Set the authentication mode to 802.1X for clients.
[AC-wlan-st-acstname] client-security authentication-mode dot1x
[AC-wlan-st-acstname] dot1x domain imc
[AC-wlan-st-acstname] ft enable
# Enable the service template.
[AC-wlan-st-acstname] service-template enable
[AC-wlan-st-acstname] quit
# Set the 802.1X authentication mode to EAP.
[AC] dot1x authentication-method eap
# Create the RADIUS scheme imcc.
[AC] radius scheme imcc
# Set the IP address of the primary authentication and accounting servers to 10.1.1.3.
[AC-radius-imcc] primary authentication 10.1.1.3
[AC-radius-imcc] primary accounting 10.1.1.3
# Set the shared key for the AC to exchange packets with the authentication and accounting servers to 12345678.
[AC-radius-imcc] key authentication simple 12345678
[AC-radius-imcc] key accounting simple 12345678
# Configure the AC to remove the ISP domain name from usernames sent to the RADIUS server.
[AC-radius-imcc] user-name-format without-domain
[AC-radius-imcc] quit
# Create the ISP domain imc, and configure the domain to use the RADIUS scheme imcc for authentication, authorization, and accounting.
[AC] domain imc
[AC-isp-imc] authentication lan-access radius-scheme imcc
[AC-isp-imc] authorization lan-access radius-scheme imcc
[AC-isp-imc] accounting lan-access radius-scheme imcc
[AC-isp-imc] quit
# Create AP 1, and bind the service template acstname to radio 2 of the AP.
[AC] wlan ap 1
[AC-wlan-ap-1] radio 2
[AC-wlan-ap-1-radio-2] service-template acstname
[AC-wlan-ap-1-radio-2] radio enable
[AC-wlan-ap-1-radio-2] quit
# Create AP 2, and bind the service template acstname to radio 2 of the AP.
[AC] wlan ap 2
[AC-wlan-ap-2] radio 2
[AC-wlan-ap-2-radio-2] service-template acstname
[AC-wlan-ap-2-radio-2] radio enable
[AC-wlan-ap-2-radio-2] quit
[AC-wlan-ap-2] quit
Verifying the configuration
# Verify the following information:
· RSN IE is enabled.
· The AKM mode is 802.1X.
· The cipher suite is CCMP.
· The FT status is Active.
[AC] display wlan client verbose
Total number of clients: 1
MAC address : fc25-3f03-8361
IPv4 address : 10.1.1.114
IPv6 address : N/A
Username : w2
AID : 1
AP ID : 1
AP name : 1
Radio ID : 2
SSID : service
BSSID : 000f-e266-7788
VLAN ID : 1
Power save mode : Active
Wireless mode : 802.11gn
Channel bandwidth : 20MHz
SM power save : Enabled
SM power save mode : Static
Short GI for 20MHz : Not supported
Short GI for 40MHz : Not supported
STBC RX capability : Supported
STBC TX capability : Not supported
Support HT-MCS set : 0, 1, 2, 3, 4, 5, 6, 7
QoS mode : WMM
Listen interval : 20
RSSI : 0
Rx/Tx rate : 0/0
Authentication method : Open system
Security mode : RSN
AKM mode : 802.1X
Encryption cipher : CCMP
User authentication mode : 802.1X
Authorization ACL ID : N/A
Authorization user profile : N/A
Roam status : N/A
Key derivation : SHA256
PMF status : N/A
Forward policy : N/A
Online time : 0hr 0min 19sec
FT status : Active
# Move the client to the coverage of AP 2. (Details not shown.)
# Verify that the authentication method is FT and the roaming status is Intra-AC roam.
[AC] display wlan client verbose
Total number of clients: 1
MAC address : fc25-3f03-8361
IPv4 address : 10.1.1.114
IPv6 address : N/A
Username : w2
AID : 1
AP ID : 2
AP name : 2
Radio ID : 2
SSID : service
BSSID : 000f-e211-2233
VLAN ID : 1
Power save mode : Active
Wireless mode : 802.11gn
Channel bandwidth : 20MHz
SM power save : Enabled
SM power save mode : Static
Short GI for 20MHz : Not supported
Short GI for 40MHz : Not supported
STBC RX capability : Supported
STBC TX capability : Not supported
Support HT-MCS set : 0, 1, 2, 3, 4, 5, 6, 7
QoS mode : WMM
Listen interval : 20
RSSI : 0
Rx/Tx rate : 0/0
Authentication method : FT
Security mode : RSN
AKM mode : 802.1X
Encryption cipher : CCMP
User authentication mode : 802.1X
Authorization ACL ID : N/A
Authorization user profile : N/A
Roam status : Intra-AC roam
Key derivation : SHA256
PMF status : N/A
Forward policy : N/A
Online time : 0hr 0min 7sec
FT status : Active