- Table of Contents
-
- 02-WLAN
- 00-Preface
- 01-AP management configuration
- 02-Radio management configuration
- 03-WLAN access configuration
- 04-WLAN security configuration
- 05-WLAN authentication configuration
- 06-WIPS configuration
- 07-WLAN QoS configuration
- 08-WLAN roaming configuration
- 09-WLAN load balancing configuration
- 10-WLAN radio resource measurement configuration
- 11-Channel scanning configuration
- 12-Band navigation configuration
- 13-WLAN high availability configuration
- 14-802.11r configuration
- 15-Wireless location configuration
- 16-Hotspot 2.0 configuration
- 17-WLAN RRM configuration
- 18-WT configuration
- 19-IoT AP configuration
- 20-CM tunnel configuration
- 21-Cloud connection configuration
- 22-WLAN IP snooping configuration
- 23-WLAN fast forwarding configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 08-WLAN roaming configuration | 142.09 KB |
Contents
Configuration restrictions and guidelines
Setting an authentication mode for IACTP control messages
Specifying an IP address type for IACTP tunnels
Specifying the source IP address for establishing IACTP tunnels
Adding a mobility group member
Enabling tunnel isolation for mobility groups
Enabling SNMP notifications for WLAN roaming
Displaying and maintaining WLAN roaming
WLAN roaming configuration examples
Configuring WLAN roaming
Overview
WLAN roaming enables clients to seamlessly roam among APs in an ESS while retaining their IP address and authorization information during the roaming process.
H3C ACs also support fast roaming, which enables RSN + 802.1X clients to roam to a new AP without being authenticated again.
Terminology
· Inter Access Controller Tunneling Protocol—IACTP is an H3C-proprietary protocol that provides a generic packet encapsulation and transport mechanism for ACs to securely communicate with each other. ACs providing roaming services establish an IACTP tunnel with each other to exchange control messages and client information.
· Home AC—A home AC is an AC that manages the AP with which a wireless client associates for the first time.
· Foreign AC—A foreign AC is an AC with which a client associates after inter-AC roaming.
WLAN roaming mechanism
Clients can roam between APs managed by ACs in the same mobility group.
Intra-AC roaming
Intra-AC roaming enables clients to roam among APs that are managed by the same AC.
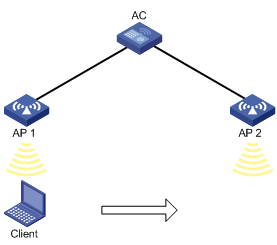
As shown in Figure 1, intra-AC roaming uses the following procedure:
1. The client comes online from AP 1, and the AC creates a roaming entry for the client.
2. The client roams to AP 2. The AC examines the roaming entry for the client and determines whether to perform fast roaming.
If the client is an RSN + 802.1X client, fast roaming is used, and the client can be associated with AP 2 without reauthentication. If it is not, the client needs to be reauthenticated before being associated with AP 2.
Inter-AC roaming
Inter-AC roaming enables clients to roam among APs that are managed by different ACs. These ACs must be in the same mobility group and have established an IACTP tunnel with each other.
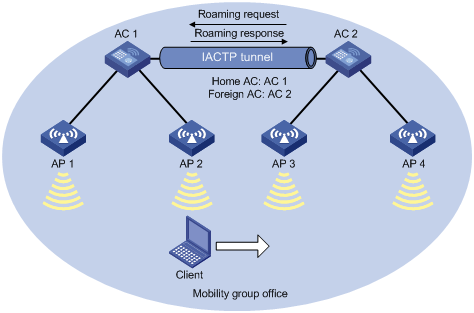
As shown in Figure 2, inter-AC roaming uses the following procedure:
1. The client comes online from AP 2. AC 1 creates a roaming entry for the client and sends the information to AC 2 through the IACTP tunnel.
2. The client roams to AP 3. AC 2 examines the roaming entry for the client and determines whether to perform fast roaming.
If the client is an RSN + 802.1X client, fast roaming is used, and the client can be associated with AP 3 without reauthentication. If it is not, the client needs to be reauthenticated before being associated with AP 3.
3. The client associates with AP 3. AC 2 sends a roaming request to AC 1.
4. AC 1 verifies the roaming request and performs either of the following operations:
¡ Sends a roaming response that indicates roaming failure to AC 2 if the request is invalid. AC 2 logs off the client.
¡ Saves the roaming trace and roam-out information and sends a roaming response that indicates roaming success to AC 2 if the request is valid. AC 2 saves roaming-in information for the client.
Configuration restrictions and guidelines
When you configure WLAN roaming, follow these restrictions and guidelines:
· For a service template where an AP is configured as the client authenticator, WLAN roaming is not supported. For more information about WLAN authentication, see "WLAN authentication overview" and "Configuring WLAN authentication."
· For RSN + 802.1X clients from different VLANs to roam between ACs within a mobility group, make sure uplink interfaces of the member ACs permit all client VLANs.
Configuration task list
|
Tasks at a glance |
|
(Required.) Creating a mobility group |
|
(Optional.) Setting an authentication mode for IACTP control messages |
|
(Required.) Specifying an IP address type for IACTP tunnels |
|
(Required.) Specifying the source IP address for establishing IACTP tunnels |
|
(Required.) Adding a mobility group member |
|
(Required.) Enabling a mobility group |
|
(Optional.) Enabling tunnel isolation for mobility groups |
|
(Optional.) Enabling SNMP notifications for WLAN roaming |
Creating a mobility group
For inter-AC roaming to operate correctly, create the same mobility group and add members to each AC in the mobility group.
To create a mobility group:
|
Command |
Remarks |
|
|
1. Enter system view. |
N/A |
|
|
2. Create a mobility group. |
By default, no mobility group exists on the AC. You can create only one mobility group on the AC. |
Setting an authentication mode for IACTP control messages
This feature enables the AC to verify the integrity of control messages transmitted over IACTP tunnels. WLAN roaming supports only the 128-bit MD5 algorithm.
To set an authentication mode for IACTP control messages:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter mobility group view. |
wlan mobility group group-name |
N/A |
|
3. Set an authentication mode for IACTP control messages. |
authentication-mode authentication-mode { cipher | simple } authentication-key |
By default, no authentication mode is set for IACTP control messages. The AC does not verify the integrity of IACTP control messages. |
Specifying an IP address type for IACTP tunnels
You must specify an IP address type for IACTP tunnels after you create a mobility group.
To specify an IP address type for IACTP tunnels:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter mobility group view. |
wlan mobility group group-name |
N/A |
|
3. Specify an IP address type for IACTP tunnels. |
By default, the IP address type for IACTP tunnels is IPv4. You cannot specify both IPv4 and IPv6 address types for IACTP tunnels. |
Specifying the source IP address for establishing IACTP tunnels
When you specify the source IP address for establishing IACTP tunnels, follow these restrictions and guidelines:
· Make sure the mobility group is disabled before you specify the source IP address for establishing IACTP tunnels.
· You can specify one IPv4 address, one IPv6 address, or both, but only the IP address type that is the same as the IP address type for IACTP tunnels takes effect.
To specify the source IP address for establishing IACTP tunnels:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter mobility group view. |
wlan mobility group group-name |
N/A |
|
3. Specify the source IP address for establishing IACTP tunnels. |
By default, no source IP address is specified for establishing IACTP tunnels. |
Adding a mobility group member
Members in a mobility group are identified by their IP addresses used to establish IACTP tunnels.
You can add both IPv4 and IPv6 members to a mobility group. Only members whose IP address type is the same as the IP address type of IACTP tunnels take effect.
An AC can belong to only one mobility group.
You can add a maximum of 31 IPv4 members and 31 IPv6 members to a mobility group.
To add a mobility group member:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter mobility group view. |
wlan mobility group group-name |
N/A |
|
3. Add a mobility group member. |
By default, a mobility group does not have any members. |
Enabling a mobility group
This feature enables the AC to establish IACTP tunnels and synchronize roaming entries with member ACs.
To enable a mobility group:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter mobility group view. |
wlan mobility group group-name |
N/A |
|
3. Enable the mobility group. |
group enable |
By default, a mobility group is disabled. |
Enabling tunnel isolation for mobility groups
Use this feature when loops exist among ACs in a mobility group. It prevents ACs from forwarding packets between tunnels in the mobility group and avoids broadcast storm.
To enable tunnel isolation for mobility groups:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable tunnel isolation for mobility groups. |
wlan mobility-group-isolation enable |
By default, tunnel isolation is enabled for mobility groups. |
Enabling SNMP notifications for WLAN roaming
To report critical WLAN roaming events to an NMS, enable SNMP notifications for WLAN roaming. For WLAN roaming event notifications to be sent correctly, you must also configure SNMP as described in Network Management and Monitoring Configuration Guide.
To enable SNMP notifications for WLAN roaming:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable SNMP notifications for WLAN roaming. |
snmp-agent trap enable wlan mobility |
By default, SNMP notifications for WLAN roaming are disabled. |
Displaying and maintaining WLAN roaming
Execute display commands in any view.
|
Task |
Command |
|
Display roam-track information for a client on the home AC. |
|
|
Display mobility group information. |
|
|
Display information about clients that have roamed to or from the AC. |
display wlan mobility { roam-in | roam-out } [ member { ip ipv4-address | ipv6 ipv6-address } ] |
WLAN roaming configuration examples
Configuring intra-AC roaming
Network requirements
As shown in Figure 1, configure intra-AC roaming to enable the client to roam from AP 1 to AP 2 that are managed by the same AC.
Configuration procedures
# Create a service template named service, set the SSID to 1, and enable the service template.
[AC] wlan service-template service
[AC-wlan-st-service] ssid 1
[AC-wlan-st-service] service-template enable
[AC-wlan-st-service] quit
# Create a manual AP named ap1, and specify the AP model and serial ID.
[AC] wlan ap ap1 model WA4320i-ACN
[AC-wlan-ap-ap1] serial-id 219801A0CNC13C004126
# Bind the service template to radio 1 of AP 1.
[AC-wlan-ap-ap1-radio-1] radio enable
[AC-wlan-ap-ap1-radio-1] service-template service
[AC-wlan-ap-ap1-radio-1] quit
[AC-wlan-ap-ap1] quit
# Create a manual AP named ap2, and specify the AP model and serial ID.
[AC] wlan ap ap2 model WA4320i-ACN
[AC-wlan-ap-ap2] serial-id 219801A0CNC125002216
# Bind the service template to radio 1 of AP 2.
[AC-wlan-ap-ap2-radio-1] radio enable
[AC-wlan-ap-ap2-radio-1] service-template service
[AC-wlan-ap-ap2-radio-1] quit
[AC-wlan-ap-ap2] quit
Verifying the configuration
# Get the client online on AP 1. (Details not shown.)
# Verify that the client associates with AP 1, and the roaming status is N/A, which indicates that the client has not performed any roaming.
[AC] display wlan client verbose
Total number of clients: 1
MAC address : 9cd3-6d9e-6778
IPv4 address : 10.1.1.114
IPv6 address : N/A
Username : N/A
AID : 1
AP ID : 1
AP name : ap1
Radio ID : 1
SSID : 1
BSSID : 000f-e200-4444
VLAN ID : 1
Sleep count : 242
Wireless mode : 802.11ac
Channel bandwidth : 80MHz
SM power save : Enabled
SM power save mode : Dynamic
Short GI for 20MHz : Supported
Short GI for 40MHz : Supported
Short GI for 80MHz : Supported
Short GI for 160/80+80MHz : Not supported
STBC RX capability : Not supported
STBC TX capability : Not supported
LDPC RX capability : Not supported
SU beamformee capability : Not supported
MU beamformee capability : Not supported
Beamformee STS capability : N/A
Block Ack : TID 0 In
Supported VHT-MCS set : NSS1 0, 1, 2, 3, 4, 5, 6, 7, 8
NSS2 0, 1, 2, 3, 4, 5, 6, 7, 8
Supported HT MCS set : 0, 1, 2, 3, 4, 5, 6, 7,
8, 9, 10, 11, 12, 13, 14,
15, 16, 17, 18, 19, 20,
21, 22, 23
Supported rates : 6, 9, 12, 18, 24, 36,
48, 54 Mbps
QoS mode : WMM
Listen interval : 10
RSSI : 62
Rx/Tx rate : 130/11
Authentication method : Open system
Security mode : PRE-RSNA
AKM mode : Not configured
Cipher suite : N/A
User authentication mode : Bypass
Authorization ACL ID : 3001(Not effective)
Authorization user profile : N/A
Roam status : N/A
Key derivation : SHA1
PMF status : Enabled
Forward policy name : Not configured
Online time : 0days 0hours 1minutes 13seconds
FT status : Inactive
# Verify that the AC has a roaming entry for the client.
[AC] display wlan mobility roam-track mac-address 9cd3-6d9e-6778
Total entries: 1
BSSID Created at Online time AC IP address RID AP name
000f-e200-4444 2017-03-14 11:12:28 00hr 01min 16sec 127.0.0.1 1 ap1
# Make the client roam to AP 2. (Details not shown.)
# Verify that the client has associated with AP 2, and the roaming status is Intra-AC roam.
[AC] display wlan client verbose
Total number of clients: 1
MAC address : 9cd3-6d9e-6778
IPv4 address : 10.1.1.114
IPv6 address : N/A
Username : N/A
AID : 1
AP ID : 2
AP name : ap2
Radio ID : 1
SSID : 1
BSSID : 000f-e203-7777
VLAN ID : 1
Sleep count : 242
Wireless mode : 802.11ac
Channel bandwidth : 80MHz
SM power save : Enabled
SM power save mode : Dynamic
Short GI for 20MHz : Supported
Short GI for 40MHz : Supported
Short GI for 80MHz : Supported
Short GI for 160/80+80MHz : Not supported
STBC RX capability : Not supported
STBC TX capability : Not supported
LDPC RX capability : Not supported
SU beamformee capability : Not supported
MU beamformee capability : Not supported
Beamformee STS capability : N/A
Block Ack : TID 0 In
Supported VHT-MCS set : NSS1 0, 1, 2, 3, 4, 5, 6, 7, 8
NSS2 0, 1, 2, 3, 4, 5, 6, 7, 8
Supported HT MCS set : 0, 1, 2, 3, 4, 5, 6, 7,
8, 9, 10, 11, 12, 13, 14,
15, 16, 17, 18, 19, 20,
21, 22, 23
Supported rates : 6, 9, 12, 18, 24, 36,
48, 54 Mbps
QoS mode : WMM
Listen interval : 10
RSSI : 62
Rx/Tx rate : 130/11
Authentication method : Open system
Security mode : PRE-RSNA
AKM mode : Not configured
Cipher suite : N/A
User authentication mode : Bypass
Authorization ACL ID : 3001(Not effective)
Authorization user profile : N/A
Roam status : Intra-AC roam
Key derivation : SHA1
PMF status : Enabled
Forward policy name : Not configured
Online time : 0days 0hours 5minutes 13seconds
FT status : Inactive
# Verify that the AC has updated the roaming entry for the client.
[AC] display wlan mobility roam-track mac-address 9cd3-6d9e-6778
Total entries: 2
BSSID Created at Online time AC IP address RID AP name
000f-e203-7777 2017-03-14 11:12:28 00hr 01min 02sec 127.0.0.1 1 ap2
000f-e200-4444 2017-03-14 11:12:04 00hr 03min 51sec 127.0.0.1 1 ap1
Configuring inter-AC roaming
Network requirements
As shown in Figure 2, configure inter-AC roaming to enable the client to roam from AP 2 to AP 3 that are managed by different ACs.
Configuration procedures
1. Configure AC 1:
# Create a service template named service, set the SSID to office, and enable the service template.
[AC1] wlan service-template service
[AC1-wlan-st-test] ssid office
[AC1-wlan-st-test] service-template enable
[AC1-wlan-st-test] quit
# Create a manual AP named ap1, and specify the AP model and serial ID.
[AC1] wlan ap ap1 model WA4320i-ACN
[AC1-wlan-ap-ap1] serial-id 219801A0CNC138011454
# Bind the service template to radio 1 of AP 1.
[AC1-wlan-ap-ap1] radio 1
[AC1-wlan-ap-ap1-radio-1] radio enable
[AC1-wlan-ap-ap1-radio-1] service-template service
[AC1-wlan-ap-ap1-radio-1] quit
[AC1-wlan-ap-ap1] quit
# Create a manual AP named ap2, and specify the AP model and serial ID.
[AC1] wlan ap ap2 model WA4320i-ACN
[AC1-wlan-ap-ap2] serial-id 219801A0CNC138011445
# Bind the service template to radio 1 of AP 2.
[AC1-wlan-ap-ap2-radio-1] radio enable
[AC1-wlan-ap-ap2-radio-1] service-template service
[AC1-wlan-ap-ap2-radio-1] quit
[AC1-wlan-ap-ap2] quit
# Create a mobility group named office.
[AC1] wlan mobility group office
# Specify the IP address type for IACTP tunnels as IPv4.
[AC1-wlan-mg-office] tunnel-type ipv4
# Specify the source IP address for establishing IACTP tunnels as 10.1.4.22.
[AC1-wlan-mg-office] source ip 10.1.4.22
# Add AC 2 to the mobility group.
[AC1-wlan-mg-office] member ip 10.1.4.23
# Enable the mobility group.
[AC1-wlan-mg-office] group enable
[AC1-wlan-mg-office] quit
2. Configure AC 2:
# Create a service template named service, specify the SSID as office, and enable the service template.
[AC2] wlan service-template service
[AC2-wlan-st-service] ssid office
[AC2-wlan-st-service] service-template enable
[AC2-wlan-st-service] quit
# Create a manual AP named ap3, and specify the AP model and serial ID.
[AC2] wlan ap ap3 model WA4320i-ACN
[AC2-wlan-ap-ap3] serial-id 219801A0CNC138011439
# Bind the service template to radio 1 of AP 3.
[AC2-wlan-ap-ap3-radio-1] radio enable
[AC2-wlan-ap-ap3-radio-1] service-template service
[AC2-wlan-ap-ap3-radio-1] quit
[AC2-wlan-ap-ap3] quit
# Create a manual AP named ap4, and specify the AP model and serial ID.
[AC2] wlan ap ap4 model WA4320i-ACN
[AC2-wlan-ap-ap4] serial-id 219801A0CNC138011448
# Bind the service template to radio 1 of AP 4.
[AC2-wlan-ap-ap4] radio 1
[AC2-wlan-ap-ap4-radio-1] radio enable
[AC2-wlan-ap-ap4-radio-1] service-template service
[AC2-wlan-ap-ap4-radio-1] quit
[AC2-wlan-ap-ap4] quit
# Create a mobility group named office.
[AC2] wlan mobility group office
# Specify the IP address type for IACTP tunnels as IPv4.
[AC2-wlan-mg-office] tunnel-type ipv4
# Specify the source IP address for establishing IACTP tunnels as 10.1.4.23.
[AC2-wlan-mg-office] source ip 10.1.4.23
# Add AC 2 to the mobility group.
[AC2-wlan-mg-office] member ip 10.1.4.22
# Enable the mobility group.
[AC2-wlan-mg-office] group enable
[AC2-wlan-mg-office] quit
Verifying the configuration
# Verify that a mobility group has been created on AC 1.
[AC1] display wlan mobility group
Mobility group name: office
Tunnel type: IPv4
Source IPv4: 10.1.4.22
Source IPv6: Not configured
Authentication method: Not configured
Mobility group status: Enabled
Member entries: 1
IP address State Online time
10.1.4.23 Up 00hr 00min 12sec
# Verify that a mobility group has been created on AC 2.
[AC2] display wlan mobility group
Mobility group name: office
Tunnel type: IPv4
Source IPv4: 10.1.4.23
Source IPv6: Not configured
Authentication method: Not configured
Mobility group status: Enabled
Member entries: 1
IP address State Online time
10.1.4.22 Up 00hr 00min 05sec
# Get the client online on AP 2 and then make the client roam to AP 3. (Details not shown.)
# Display client roaming information on AC 1 to verify that the client came online from AP 2 and roamed to AP 3.
[AC1] display wlan mobility roam-track mac-address 9cd3-6d9e-6778
Total entries: 2
BSSID Created at Online time AC IP address RID AP name
000f-e203-8889 2017-03-14 11:12:28 00hr 06min 56sec 10.1.4.23 1 ap3
000f-e203-7777 2017-03-14 11:11:28 00hr 03min 30sec 127.0.0.1 1 ap2
# On AC 1, verify that the client has roamed to AC 3.
<AC1> display wlan mobility roam-out
Total entries: 1
MAC address BSSID VLAN ID Online time FA IP address
9cd3-6d9e-6778 000f-e203-8889 1 00hr 01min 59sec 10.1.4.23
# On AC 2, verify that the client has associated with AP 3, and the roaming status is Inter-AC roam.
<AC2> display wlan client verbose
Total number of clients: 1
MAC address : 9cd3-6d9e-6778
IPv4 address : 10.1.1.114
IPv6 address : N/A
Username : N/A
AID : 1
AP ID : 3
AP name : ap3
Radio ID : 1
SSID : 1
BSSID : 000f-e203-8889
VLAN ID : 1
Sleep count : 242
Wireless mode : 802.11ac
Channel bandwidth : 80MHz
SM power save : Enabled
SM power save mode : Dynamic
Short GI for 20MHz : Supported
Short GI for 40MHz : Supported
Short GI for 80MHz : Supported
Short GI for 160/80+80MHz : Not supported
STBC RX capability : Not supported
STBC TX capability : Not supported
LDPC RX capability : Not supported
SU beamformee capability : Not supported
MU beamformee capability : Not supported
Beamformee STS capability : N/A
Block Ack : TID 0 In
Supported VHT-MCS set : NSS1 0, 1, 2, 3, 4, 5, 6, 7, 8
NSS2 0, 1, 2, 3, 4, 5, 6, 7, 8
Supported HT MCS set : 0, 1, 2, 3, 4, 5, 6, 7,
8, 9, 10, 11, 12, 13, 14,
15, 16, 17, 18, 19, 20,
21, 22, 23
Supported rates : 6, 9, 12, 18, 24, 36,
48, 54 Mbps
QoS mode : WMM
Listen interval : 10
RSSI : 62
Rx/Tx rate : 130/11
Authentication method : Open system
Security mode : PRE-RSNA
AKM mode : Not configured
Cipher suite : N/A
User authentication mode : Bypass
Authorization ACL ID : 3001(Not effective)
Authorization user profile : N/A
Roam status : Inter-AC roam
Key derivation : SHA1
PMF status : Enabled
Forward policy name : Not configured
Online time : 0days 0hours 5minutes 13seconds
FT status : Inactive
# Verify that the client has roamed from AC 1 to AC 3.
<AC2> display wlan mobility roam-in
Total entries: 1
MAC address BSSID VLAN ID HA IP address
9cd3-6d9e-6778 000f-e203-8889 1 10.1.4.22