- Table of Contents
-
- H3C Fixed Port Campus Switches Configuration Examples-6W103
- 00-Applicable hardware and software versions
- 01-Login Management Configuration Examples
- 02-RBAC Configuration Examples
- 03-Software Upgrade Examples
- 04-ISSU Configuration Examples
- 05-Software Patching Examples
- 06-Ethernet Link Aggregation Configuration Examples
- 07-Port Isolation Configuration Examples
- 08-Spanning Tree Configuration Examples
- 09-VLAN Configuration Examples
- 10-VLAN Tagging Configuration Examples
- 11-DHCP Snooping Configuration Examples
- 12-Cross-Subnet Dynamic IP Address Allocation Configuration Examples
- 13-IPv6 over IPv4 Tunneling with OSPFv3 Configuration Examples
- 14-IPv6 over IPv4 GRE Tunnel Configuration Examples
- 15-GRE with OSPF Configuration Examples
- 16-OSPF Configuration Examples
- 17-IS-IS Configuration Examples
- 18-BGP Configuration Examples
- 19-Policy-Based Routing Configuration Examples
- 20-OSPFv3 Configuration Examples
- 21-IPv6 IS-IS Configuration Examples
- 22-Routing Policy Configuration Examples
- 23-IGMP Snooping Configuration Examples
- 24-IGMP Configuration Examples
- 25-MLD Snooping Configuration Examples
- 26-IPv6 Multicast VLAN Configuration Examples
- 27-ACL Configuration Examples
- 28-Traffic Policing Configuration Examples
- 29-GTS and Rate Limiting Configuration Examples
- 30-Traffic Filtering Configuration Examples
- 31-AAA Configuration Examples
- 32-Port Security Configuration Examples
- 33-Portal Configuration Examples
- 34-SSH Configuration Examples
- 35-IP Source Guard Configuration Examples
- 36-Ethernet OAM Configuration Examples
- 37-CFD Configuration Examples
- 38-DLDP Configuration Examples
- 39-VRRP Configuration Examples
- 40-BFD Configuration Examples
- 41-NTP Configuration Examples
- 42-SNMP Configuration Examples
- 43-NQA Configuration Examples
- 44-Mirroring Configuration Examples
- 45-sFlow Configuration Examples
- 46-OpenFlow Configuration Examples
- 47-MAC Address Table Configuration Examples
- 48-Static Multicast MAC Address Entry Configuration Examples
- 49-IP Unnumbered Configuration Examples
- 50-MVRP Configuration Examples
- 51-MCE Configuration Examples
- 52-Attack Protection Configuration Examples
- 53-Smart Link Configuration Examples
- 54-RRPP Configuration Examples
- 55-BGP Route Selection Configuration Examples
- 56-IS-IS Route Summarization Configuration Examples
- 57-VXLAN Configuration Examples
- 58-DRNI Configuration Examples
- 59-IRF 3.1 Configuration Examples
- 60-PTP Configuration Examples
- 61-S-MLAG Configuration Examples
- 62-Puppet Configuration Examples
- 63-802.1X Configuration Examples
- 64-MAC Authentication Configuration Examples
- 65-ISATAP Tunnel and 6to4 Tunnel Configuration Examples
- 66-BIDIR-PIM Configuration Examples
- 67-Congestion Avoidance and Queue Scheduling Configuration Examples
- 68-Basic MPLS Configuration Examples
- 69-MPLS L3VPN Configuration Examples
- 70-MPLS OAM Configuration Examples
- 71-EVPN-DCI over an MPLS L3VPN Network Configuration Examples
- 72-DRNI and EVPN Configuration Examples
- 73-Multicast VPN Configuration Examples
- 74-MPLS TE Configuration Examples
- 75-Control Plane-Based QoS Policy Configuration Examples
- 76-Priority Mapping and Queue Scheduling Configuration Examples
- 77-ARP Attack Protection Configuration Examples
- 78-IRF Software Upgrade Configuration Examples
- 79-IRF Member Replacement Configuration Examples
- 80-Layer 3 Multicast on Multicast Source-Side DR System Configuration Examples
- 81-EVPN Multicast Configuration Examples
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 64-MAC Authentication Configuration Examples | 583.49 KB |
Example: Configuring local MAC authentication
Applicable hardware and software versions
Example: Configuring MAC authentication with authorization VSI assignment
Applicable hardware and software versions
Example: Configuring MAC authentication with ACL assignment
Introduction
The following information provides examples for configuring MAC authentication to ensure network access security.
Prerequisites
The configuration examples were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
The following information is provided based on the assumption that you have basic knowledge of MAC authentication.
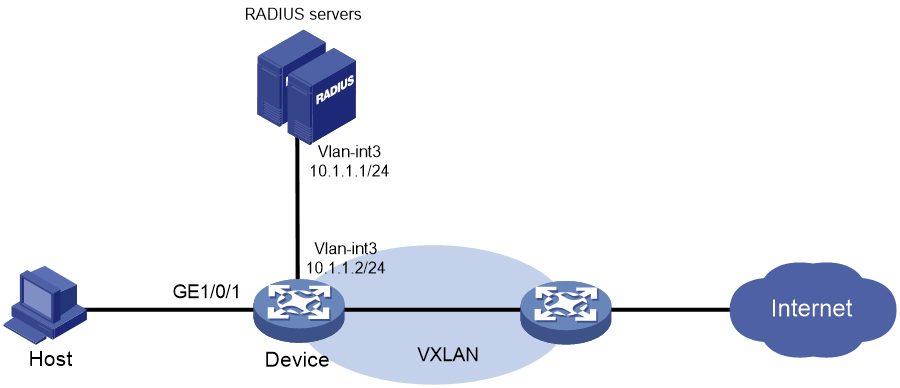
Example: Configuring local MAC authentication
Network configuration
As shown in Figure 1, the device performs local MAC authentication on GigabitEthernet 1/0/1 to control Internet access of users.
Configure the device to meet the following requirements:
· Detect whether a user has gone offline every 180 seconds.
· Deny a user for 180 seconds if the user fails MAC authentication.
· Authenticate all users in ISP domain bbb.
· Use the MAC address of each user as both the username and password for authentication. The MAC addresses are in hexadecimal notation with hyphens, and letters are in lower case. In this example, both the username and password are 08-00-27-00-98-d2.
Applicable hardware and software versions
The following matrix shows the hardware and software versions to which this configuration example is applicable:
|
Hardware |
Software version |
|
S6812 switch series S6813 switch series |
Release 66xx |
|
S6550XE-HI switch series |
Release 6008 and later |
|
S6525XE-HI switch series |
Release 6008 and later |
|
S5850 switch series |
Release 8005 and later |
|
S5570S-EI switch series |
Release 11xx |
|
S5560X-EI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S5560X-HI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S5500V2-EI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
MS4520V2-30F switch |
Release 63xx, Release 65xx, Release 66xx |
|
MS4520V2-30C switch MS4520V2-54C switch |
Release 65xx, Release 66xx |
|
MS4520V2-28S switch MS4520V2-24TP switch |
Release 63xx, Release 65xx |
|
S6520X-HI switch series S6520X-EI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S6520X-SI switch series S6520-SI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S5000-EI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
MS4600 switch series |
Release 63xx, Release 65xx, Release 66xx |
|
ES5500 switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S5560S-EI switch series S5560S-SI switch series |
Release 63xx |
|
S5500V3-24P-SI switch S5500V3-48P-SI switch |
Release 63xx |
|
S5500V3-SI switch series (except the S5500V3-24P-SI and S5500V3-48P-SI switches) |
Release 11xx |
|
S5170-EI switch series |
Release 11xx |
|
S5130S-HI switch series S5130S-EI switch series S5130S-SI switch series S5130S-LI switch series |
Release 63xx |
|
S5120V2-SI switch series S5120V2-LI switch series |
Release 63xx |
|
S5120V3-EI switch series |
Release 11xx |
|
S5120V3-36F-SI switch S5120V3-28P-HPWR-SI switch S5120V3-54P-PWR-SI switch |
Release 11xx |
|
S5120V3-SI switch series (except the S5120V3-36F-SI, S5120V3-28P-HPWR-SI, and S5120V3-54P-PWR-SI switches) |
Release 63xx |
|
S5120V3-LI switch series |
Release 63xx |
|
S3600V3-EI switch series |
Release 11xx |
|
S3600V3-SI switch series |
Release 11xx |
|
S3100V3-EI switch series S3100V3-SI switch series |
Release 63xx |
|
S5110V2 switch series |
Release 63xx |
|
S5110V2-SI switch series |
Release 63xx |
|
S5000V3-EI switch series S5000V5-EI switch series |
Release 63xx |
|
S5000E-X switch series S5000X-EI switch series |
Release 63xx |
|
E128C switch E152C switch E500C switch series E500D switch series |
Release 63xx |
|
MS4320V2 switch series MS4320V3 switch series MS4300V2 switch series MS4320 switch series MS4200 switch series |
Release 63xx |
|
WS5850-WiNet switch series |
Release 63xx |
|
WS5820-WiNet switch series WS5810-WiNet switch series |
Release 63xx |
|
WAS6000 switch series |
Release 63xx |
|
IE4300-12P-AC switch IE4300-12P-PWR switch IE4300-M switch series IE4320 switch series |
Release 63xx |
Restrictions and guidelines
· To avoid valid users from being blocked, do not enable MAC authentication globally before you finish all settings.
· When you create a local user, the username and password must match the user account policy for MAC authentication. If MAC-based accounts are used, make sure the username and password of each user account are the same as the MAC address of the corresponding MAC authentication user.
Procedures
# Add a network access user, set both the username and password to the MAC address of the host, and allow the user to use the LAN access service.
<Device> system-view
[Device] local-user 08-00-27-00-98-d2 class network
[Device-luser-network-08-00-27-00-98-d2] password simple 08-00-27-00-98-d2
[Device-luser-network-08-00-27-00-98-d2] service-type lan-access
[Device-luser-network-08-00-27-00-98-d2] quit
# Configure ISP domain bbb to use local authentication for LAN users.
[Device] domain bbb
[Device-isp-bbb] authentication lan-access local
[Device-isp-bbb] quit
# Specify ISP domain bbb as the global MAC authentication domain.
[Device] mac-authentication domain bbb
# Configure MAC authentication timers.
[Device] mac-authentication timer offline-detect 180
[Device] mac-authentication timer quiet 180
# Use the MAC address of each user as both the username and password for MAC authentication. The MAC addresses are in hexadecimal notation with hyphens, and letters are in lower case.
[Device] mac-authentication user-name-format mac-address with-hyphen lowercase
# Enable MAC authentication on interface GigabitEthernet 1/0/1.
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] mac-authentication
[Device-GigabitEthernet1/0/1] quit
# Enable MAC authentication globally.
[Device] mac-authentication
Verifying the configuration
|
IMPORTANT: Support for VSI- and microsegment-related fields depends on the device model. |
# Display MAC authentication settings and statistics.
<Device> display mac-authentication
Global MAC authentication parameters:
MAC authentication : Enabled
Authentication method : PAP
Username format : MAC address in lowercase(xx-xx-xx-xx-xx-xx)
Username : mac
Password : Not configured
MAC range accounts : 0
MAC address Mask Username
Offline detect period : 180 s
Quiet period : 180 s
Server timeout : 100 s
Reauth period : 3600 s
User aging period for critical VLAN : 1000 s
User aging period for critical VSI : 1000 s
User aging period for guest VLAN : 1000 s
User aging period for guest VSI : 1000 s
User aging period for critical microsegment: 1000 s
Authentication domain : bbb
HTTP proxy port list : Not configured
HTTPS proxy port list : Not configured
Online MAC-auth wired users : 1
Silent MAC users:
MAC address VLAN ID From port Port index
GigabitEthernet1/0/1 is link-up
MAC authentication : Enabled
Carry User-IP : Disabled
Authentication domain : Not configured
Auth-delay timer : Disabled
Periodic reauth : Disabled
Re-auth server-unreachable : Logoff
Guest VLAN : Not configured
Guest VLAN reauthentication : Enabled
Guest VLAN auth-period : 30 s
Critical VLAN : Not configured
Critical voice VLAN : Disabled
Host mode : Single VLAN
Offline detection : Enabled
Authentication order : Default
User aging : Enabled
Server-recovery online-user-sync : Disabled
Guest VSI : Not configured
Guest VSI reauthentication : Enabled
Guest VSI auth-period : 30 s
Critical VSI : Not configured
Critical microsegment ID : Not configured
URL user logoff : No
Auto-tag feature : Disabled
VLAN tag configuration ignoring : Disabled
Max online users : 4294967295
Authentication attempts : successful 1, failed 0
Current online users : 1
MAC address Auth state
0800-2700-98d2 Authenticated
Configuration files
#
mac-authentication
mac-authentication timer offline-detect 180
mac-authentication timer quiet 180
mac-authentication domain bbb
mac-authentication user-name-format mac-address with-hyphen lowercase
domain bbb
authentication lan-access local
#
local-user 08-00-27-00-98-d2 class network
password cipher $c$3$rTXB/eL1h+bXc/t2nyQOrhDMC0PWfyiPb93BqMCK+JFYwvn5
service-type lan-access
authorization-attribute user-role network-operator
#
interface GigabitEthernet1/0/1
mac-authentication
#
Example: Configuring MAC authentication with authorization VSI assignment
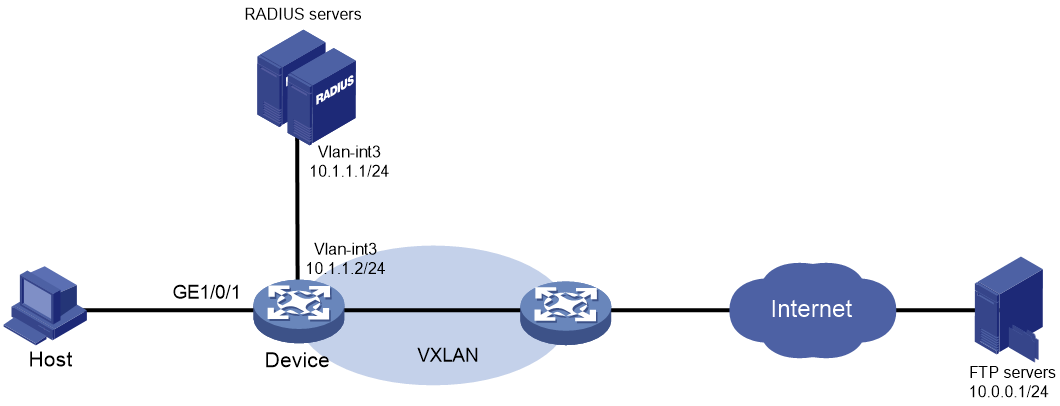
Network configuration
As shown in Figure 2:
· Configure the device to use the RADIUS servers to perform authentication, authorization, and accounting for the user on the host that is connected to GigabitEthernet 1/0/1.
· Enable MAC authentication on GigabitEthernet 1/0/1 to control Internet access.
· Configure the RADIUS servers to assign VSI bbb to the user when the user passes MAC authentication. After that, the user can access resources in the VXLAN created on the VSI. In this example, the VXLAN is VXLAN 5.
· Authenticate the user in ISP domain 2000.
· Use the MAC address of the host as both the username and password for MAC authentication. The MAC address is in hexadecimal notation with hyphens, and letters are in lower case. In this example, both the username and password are d4-85-64-be-c6-3e.
IMC acts as the RADIUS servers.
Analysis
· For the device to use IMC as the RADIUS servers for user authentication, authorization, and accounting, perform the following tasks on IMC:
a. Add the device to IMC as an access device.
b. Add an access policy.
c. Add an access service and specify the access policy in the access service.
d. Add an access user and specify the access service for the access user.
· For the device to perform RADIUS-based authentication, authorization, and accounting for the MAC authentication access user, configure AAA settings on the device, including ISP domain settings and RADIUS scheme settings.
· To assign a VSI to the user after the user passes authentication and allow the user to access resources in the VXLAN created on the VSI, perform the following tasks:
¡ On IMC, specify the VSI for the user when you add an access policy for the user.
¡ On the device, create the VSI and its VXLAN.
Applicable hardware and software versions
The following matrix shows the hardware and software versions to which this configuration example is applicable:
|
Hardware |
Software version |
|
S6812 switch series S6813 switch series |
Release 66xx |
|
S6550XE-HI switch series |
Release 6008 and later |
|
S6525XE-HI switch series |
Release 6008 and later |
|
S5850 switch series |
Not supported |
|
S5570S-EI switch series |
Not supported |
|
S5560X-EI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S5560X-HI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S5500V2-EI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
MS4520V2-30F switch |
Release 63xx, Release 65xx, Release 66xx |
|
MS4520V2-30C switch MS4520V2-54C switch |
Release 65xx, Release 66xx |
|
MS4520V2-28S switch MS4520V2-24TP switch |
Not supported |
|
S6520X-HI switch series S6520X-EI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S6520X-SI switch series S6520-SI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S5000-EI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
MS4600 switch series |
Release 63xx, Release 65xx, Release 66xx |
|
ES5500 switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S5560S-EI switch series S5560S-SI switch series |
Not supported |
|
S5500V3-24P-SI switch S5500V3-48P-SI switch |
Not supported |
|
S5500V3-SI switch series (except the S5500V3-24P-SI and S5500V3-48P-SI switches) |
Not supported |
|
S5170-EI switch series |
Not supported |
|
S5130S-HI switch series S5130S-EI switch series S5130S-SI switch series S5130S-LI switch series |
Not supported |
|
S5120V2-SI switch series S5120V2-LI switch series |
Not supported |
|
S5120V3-EI switch series |
Not supported |
|
S5120V3-36F-SI switch S5120V3-28P-HPWR-SI switch S5120V3-54P-PWR-SI switch |
Not supported |
|
S5120V3-SI switch series (except the S5120V3-36F-SI, S5120V3-28P-HPWR-SI, and S5120V3-54P-PWR-SI switches) |
Not supported |
|
S5120V3-LI switch series |
Not supported |
|
S3600V3-EI switch series |
Not supported |
|
S3600V3-SI switch series |
Not supported |
|
S3100V3-EI switch series S3100V3-SI switch series |
Not supported |
|
S5110V2 switch series |
Not supported |
|
S5110V2-SI switch series |
Not supported |
|
S5000V3-EI switch series S5000V5-EI switch series |
Not supported |
|
S5000E-X switch series S5000X-EI switch series |
Not supported |
|
E128C switch E152C switch E500C switch series E500D switch series |
Not supported |
|
MS4320V2 switch series MS4320V3 switch series MS4300V2 switch series MS4320 switch series MS4200 switch series |
Not supported |
|
WS5850-WiNet switch series |
Not supported |
|
WS5820-WiNet switch series WS5810-WiNet switch series |
Not supported |
|
WAS6000 switch series |
Not supported |
|
IE4300-12P-AC switch IE4300-12P-PWR switch IE4300-M switch series IE4320 switch series |
Not supported |
Restrictions and guidelines
· To avoid valid users from being blocked, do not enable MAC authentication globally before you finish all settings.
· When you add an access user on IMC, make sure the user account on IMC matches the MAC authentication user account policy on the device. If MAC-based accounts are used, make sure the username and password of each user account are the same as the MAC address of the corresponding MAC authentication user.
· In standard RADIUS protocol, the authentication port on RADIUS servers is UDP port 1812. If an H3C device is used as a RADIUS server, the authentication port on the RADIUS server is UDP port 1645.
Procedures
If an ADCAM server is used for authentication and authorization, configure VSIs on the server. The server will assign these VSIs to the device. You do not need to configure VSIs on the device.
Configuring the RADIUS server
This example uses IMC PLAT 7.3 (E0506), IMC EIA 7.3 (E0503), and IMC EIP 7.3 (E0503) to describe the procedure.
Adding the device to the IMC Platform as an access device
1. Log in to IMC.
2. Click the User tab.
3. From the navigation pane, select User Access Policy > Access Device Management > Access Device.
4. Click Add.
5. On the page that opens, configure access device parameters.
a. Set the ports for authentication and accounting to 1812 and 1813, respectively.
b. Select H3C (General) from the Access Device Type list.
c. Set the shared key to expert for secure authentication and accounting communication.
d. Select an access device from the device list or manually add an access device. In this example, the IP address of the access device is 10.1.1.2.
e. Use the default values for other parameters.
f. Click OK.
The IP address of the access device specified on IMC must be the same as the source IP address of the RADIUS packets sent from the device. On the device, the source IP address is chosen in the following order:
a. IP address specified by using the nas-ip command.
b. IP address specified by using the radius nas-ip command.
c. IP address of the outbound interface (the default).
In this example, the device uses the IP address of the outbound interface as the source IP address of RADIUS packets.
Figure 3 Adding an access device
Adding an access policy
1. Click the User tab.
2. From the navigation pane, select User Access Policy > Access Policy.
3. Click Add.
4. On the page that opens, configure access policy parameters.
a. Enter access policy name MACauth.
b. Set the name of the VSI to be deployed to bbb.
c. Configure other parameters as needed.
d. Click OK.
Figure 4 Adding an access policy
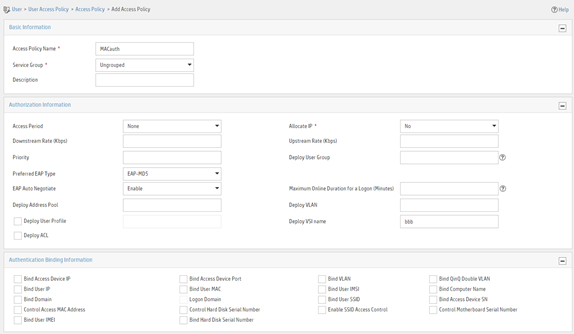
Adding an access service
1. Click the User tab.
2. From the navigation pane, select User Access Policy > Access Service.
3. Click Add.
4. On the page that opens, configure access service parameters.
a. Enter service name MACauth Service and set the service suffix to 2000. The service suffix is the authentication domain for the MAC authentication user.
|
IMPORTANT: With the service suffix configured, you must configure the device to send usernames that include the domain name to the RADIUS servers. |
b. Select MACauth from the Default Access Policy list.
c. Configure other parameters as needed.
d. Click OK.
Figure 5 Adding an access service
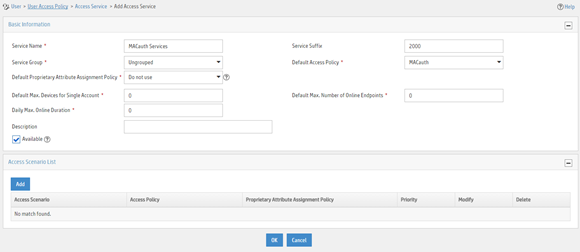
Adding an access user
1. Click the User tab.
2. From the navigation pane, select Access User > Access User.
3. Click Add.
4. On the page that opens, configure access user parameters.
a. Select the user or add a user named test.
b. Enter account name d4-85-64-be-c6-3e and password d4-85-64-be-c6-3e.
c. Select MACauth Service in the Access Service area.
d. Configure other parameters as needed.
e. Click OK.
Figure 6 Adding an access user
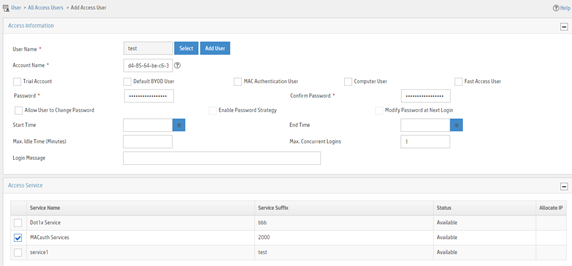
Configuring the device
# Configure a RADIUS scheme.
|
IMPORTANT: With the service suffix configured on IMC, you must configure the device to send usernames that include the domain name to the RADIUS servers. By default, the device includes the domain name in the usernames sent to a RADIUS server. |
<Device> system-view
[Device] radius scheme bbb
[Device-radius-bbb] primary authentication 10.1.1.1
[Device-radius-bbb] primary accounting 10.1.1.2
[Device-radius-bbb] key authentication simple expert
[Device-radius-bbb] key accounting simple expert
[Device-radius-bbb] user-name-format with-domain
[Device-radius-bbb] quit
# Configure ISP domain 2000.
[Device] domain 2000
[Device-isp-2000] authentication lan-access radius-scheme bbb
[Device-isp-2000] authorization lan-access radius-scheme bbb
[Device-isp-2000] accounting lan-access radius-scheme bbb
[Device-isp-2000] quit
# Enable MAC authentication on interface GigabitEthernet 1/0/1.
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] mac-authentication
# Enable MAC-based traffic match mode for dynamic Ethernet service instances on interface GigabitEthernet 1/0/1.
[Device-GigabitEthernet1/0/1] mac-based ac
[Device-GigabitEthernet1/0/1] quit
# Enable L2VPN.
[Device] l2vpn enable
# Create a VSI named bbb and the associated VXLAN.
[Device] vsi bbb
[Device-vsi-bbb] vxlan 5
[Device-vsi-bbb-vxlan-5] quit
[Device-vsi-bbb] quit
# Specify ISP domain 2000 as the global MAC authentication domain.
[Device] mac-authentication domain 2000
# Use the MAC address of each user as both the username and password for MAC authentication. The MAC addresses are in hexadecimal notation with hyphens, and letters are in lower case.
[Device] mac-authentication user-name-format mac-address with-hyphen lowercase
# Enable MAC authentication globally.
[Device] mac-authentication
Verifying the configuration
# Verify that VSI bbb is assigned to the MAC authentication user after the user passes authentication.
[Device] display mac-authentication connection
Total connections: 1
Slot ID: 1
User MAC address: d485-64be-c63e
Access interface: GigabitEthernet1/0/1
Username: d4-85-64-be-c6-3e
User access state: Successful
Authentication domain: 2000
IPv4 address: 192.168.1.1
IPv6 address: 2000:0:0:0:1:2345:6789:abcd
Initial VLAN: 1
Authorization untagged VLAN: N/A
Authorization tagged VLAN: N/A
Authorization VSI: bbb
Authorization microsegment ID: N/A
Authorization ACL ID: N/A
Authorization user profile: N/A
Authorization CAR:
Average input rate: 102400 bps
Peak input rate: 204800 bps
Average output rate: 102400 bps
Peak output rate: 204800 bps
Authorization URL: N/A
Termination action: N/A
Session timeout period: N/A
Offline detection: 100 sec (server-assigned)
Online from: 2016/06/13 09:06:37
Online duration: 0h 0m 35s
# Verify that a dynamic AC is created for MAC address d485-64be-c63e.
[Device] display l2vpn forwarding ac verbose
VSI Name: bbb
Interface: GE1/0/1 Service Instance: 1
Link ID : 0
Access Mode : VLAN
Encapsulation: untagged
Type : Dynamic (MAC-based)
MAC address : d485-64be-c63e
Configuration files
#
radius scheme bbb
primary authentication 10.1.1.1
primary accounting 10.1.1.2
key authentication cipher $c$3$+zuETC3Y0LHiW3bxzBb+UNEuWlxHkQ==
key accounting cipher $c$3$2b8hx6mbWlnMMQY82TeUzgh0VnWXbg==
#
domain 2000
authentication lan-access radius-scheme bbb
accounting lan-access radius-scheme bbb
#
interface GigabitEthernet1/0/1
mac-authentication
mac-based ac
#
vsi bbb
vxlan 5
#
l2vpn enable
#
mac-authentication domain 2000
#
mac-authentication user-name-format mac-address with-hyphen lowercase
#
mac-authentication
#
Example: Configuring MAC authentication with ACL assignment
Network configuration
As shown in Figure 7:
· Configure the device to use the RADIUS servers to perform authentication, authorization, and accounting for the user on the host that is connected to GigabitEthernet 1/0/1.
· Enable MAC authentication on GigabitEthernet 1/0/1 to control Internet access.
· Use the MAC address of the host as both the username and password for MAC authentication. The MAC address is in hexadecimal notation with hyphens, and letters are in lower case.
· Use an ACL to deny the user to access the FTP server at 10.0.0.1 after the user passes authentication.
IMC acts as the RADIUS servers.
Analysis
· For the device to use IMC as the RADIUS servers for user authentication, authorization, and accounting, perform the following tasks on IMC:
a. Add the device to IMC as an access device.
b. Add an access policy.
c. Add an access service and specify the access policy in the access service.
d. Add an access user and specify the access service for the access user.
· For the device to perform RADIUS-based authentication, authorization, and accounting for the MAC authentication access user, configure AAA settings on the device, including ISP domain settings and RADIUS scheme settings.
· To use an ACL to restrict the user's network access behaviors after the user passes authentication, perform the following tasks:
¡ On IMC, specify the ACL number for the user when you add an access policy for the user.
¡ On the device, create the ACL and configure its rules.
Applicable hardware and software versions
The following matrix shows the hardware and software versions to which this configuration example is applicable:
|
Hardware |
Software version |
|
S6812 switch series S6813 switch series |
Release 66xx |
|
S6550XE-HI switch series |
Release 6008 and later |
|
S6525XE-HI switch series |
Release 6008 and later |
|
S5850 switch series |
Release 8005 and later |
|
S5570S-EI switch series |
Release 11xx |
|
S5560X-EI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S5560X-HI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S5500V2-EI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
MS4520V2-30F switch |
Release 63xx, Release 65xx, Release 66xx |
|
MS4520V2-30C switch MS4520V2-54C switch |
Release 65xx, Release 66xx |
|
MS4520V2-28S switch MS4520V2-24TP switch |
Release 63xx |
|
S6520X-HI switch series S6520X-EI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S6520X-SI switch series S6520-SI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S5000-EI switch series |
Release 63xx, Release 65xx, Release 66xx |
|
MS4600 switch series |
Release 63xx, Release 65xx, Release 66xx |
|
ES5500 switch series |
Release 63xx, Release 65xx, Release 66xx |
|
S5560S-EI switch series S5560S-SI switch series |
Release 63xx |
|
S5500V3-24P-SI switch S5500V3-48P-SI switch |
Release 63xx |
|
S5500V3-SI switch series (except the S5500V3-24P-SI and S5500V3-48P-SI switches) |
Release 11xx |
|
S5170-EI switch series |
Release 11xx |
|
S5130S-HI switch series S5130S-EI switch series S5130S-SI switch series S5130S-LI switch series |
Release 63xx |
|
S5120V2-SI switch series S5120V2-LI switch series |
Release 63xx |
|
S5120V3-EI switch series |
Release 11xx |
|
S5120V3-36F-SI switch S5120V3-28P-HPWR-SI switch S5120V3-54P-PWR-SI switch |
Release 11xx |
|
S5120V3-SI switch series (except the S5120V3-36F-SI, S5120V3-28P-HPWR-SI, and S5120V3-54P-PWR-SI switches) |
Release 63xx |
|
S5120V3-LI switch series |
Release 63xx |
|
S3600V3-EI switch series |
Release 11xx |
|
S3600V3-SI switch series |
Release 11xx |
|
S3100V3-EI switch series S3100V3-SI switch series |
Release 63xx |
|
S5110V2 switch series |
Release 63xx |
|
S5110V2-SI switch series |
Release 63xx |
|
S5000V3-EI switch series S5000V5-EI switch series |
Release 63xx |
|
S5000E-X switch series S5000X-EI switch series |
Release 63xx |
|
E128C switch E152C switch E500C switch series E500D switch series |
Release 63xx |
|
MS4320V2 switch series MS4320V3 switch series MS4300V2 switch series MS4320 switch series MS4200 switch series |
Release 63xx |
|
WS5850-WiNet switch series |
Release 63xx |
|
WS5820-WiNet switch series WS5810-WiNet switch series |
Release 63xx |
|
WAS6000 switch series |
Release 63xx |
|
IE4300-12P-AC switch IE4300-12P-PWR switch IE4300-M switch series IE4320 switch series |
Release 63xx |
Restrictions and guidelines
· To avoid valid users from being blocked, do not enable MAC authentication globally before you finish all settings.
· When you add an access user on IMC, make sure the user account on IMC matches the MAC authentication user account policy on the device. If MAC-based accounts are used, make sure the username and password of each user account are the same as the MAC address of the corresponding MAC authentication user.
· In standard RADIUS protocol, the authentication port on RADIUS servers is UDP port 1812. If an H3C device is used as a RADIUS server, the authentication port on the RADIUS server is UDP port 1645.
Procedures
Configuring the RADIUS server
This example uses IMC PLAT 7.3 (E0506), IMC EIA 7.3 (E0503), and IMC EIP 7.3 (E0503) to describe the procedure.
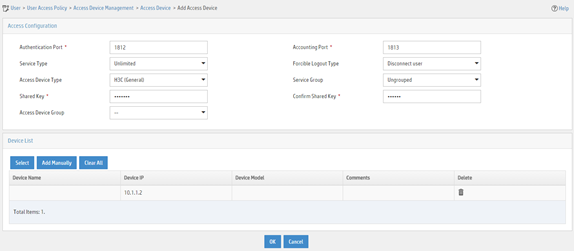
Adding the device to the IMC Platform as an access device
1. Log in to IMC.
2. Click the User tab.
3. From the navigation pane, select User Access Policy > Access Device Management > Access Device.
4. Click Add.
5. On the page that opens, configure access device parameters.
a. Set the ports for authentication and accounting to 1812 and 1813, respectively.
b. Select H3C (General) from the Access Device Type list.
c. Set the shared key to expert for secure authentication and accounting communication.
d. Select an access device from the device list or manually add an access device. In this example, the IP address of the access device is 10.1.1.2.
e. Use the default values for other parameters.
f. Click OK.
The IP address of the access device specified on IMC must be the same as the source IP address of the RADIUS packets sent from the device. On the device, the source IP address is chosen in the following order:
a. IP address specified by using the nas-ip command.
b. IP address specified by using the radius nas-ip command.
c. IP address of the outbound interface (the default).
In this example, the device uses the IP address of the outbound interface as the source IP address of RADIUS packets.
Figure 8 Adding an access device
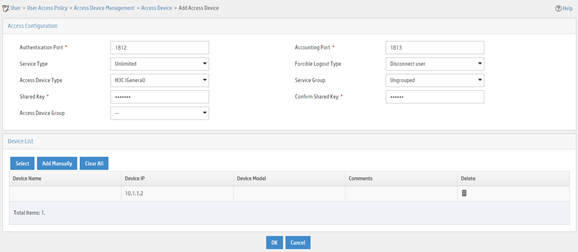
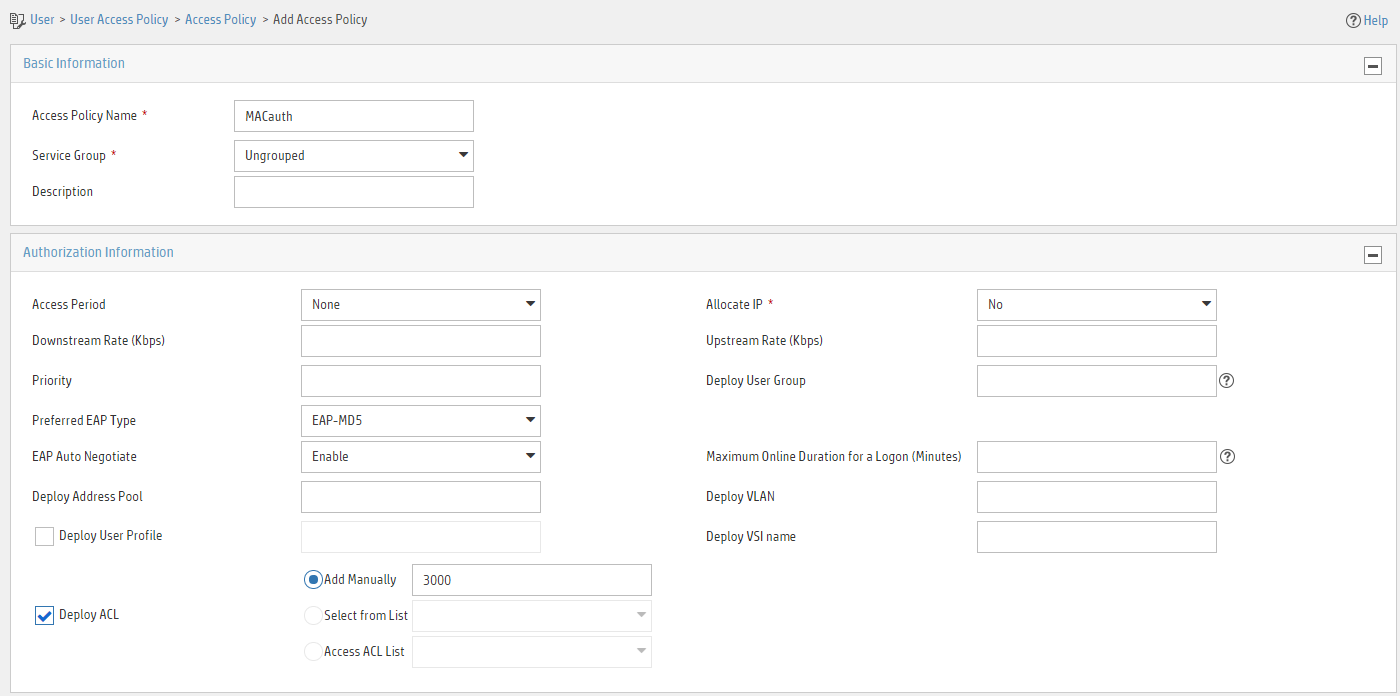
Adding an access policy
1. Click the User tab.
2. From the navigation pane, select User Access Policy > Access Policy.
3. Click Add.
4. On the page that opens, configure access policy parameters.
a. Enter access policy name MACauth.
b. Select Deploy ACL and manually enter ACL number 3000.
c. Configure other parameters as needed.
d. Click OK.
Figure 9 Adding an access policy
Adding an access service
1. Click the User tab.
2. From the navigation pane, select User Access Policy > Access Service.
3. Click Add.
4. On the page that opens, configure access service parameters.
a. Enter service name MACauth Services and set the service suffix to bbb. The service suffix is the authentication domain for the MAC authentication user.
|
IMPORTANT: With the service suffix configured, you must configure the device to send usernames that include the domain name to the RADIUS servers. |
b. Select MACauth from the Default Access Policy list.
c. Configure other parameters as needed.
d. Click OK.
Figure 10 Adding an access service
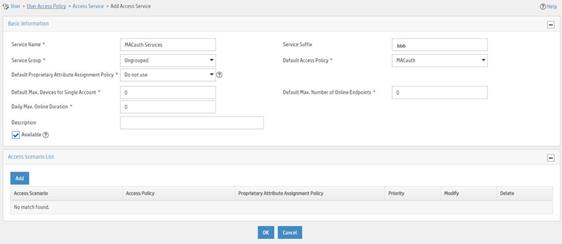
Adding an access user
1. Click the User tab.
2. From the navigation pane, select Access User > Access User.
3. Click Add.
4. On the page that opens, configure access user parameters.
a. Select the user or add a user named test.
b. Enter account name d4-85-64-be-c6-3e and password d4-85-64-be-c6-3e.
c. Select MACauth Services in the Access Service area.
d. Configure other parameters as needed.
e. Click OK.
Figure 11 Adding an access user
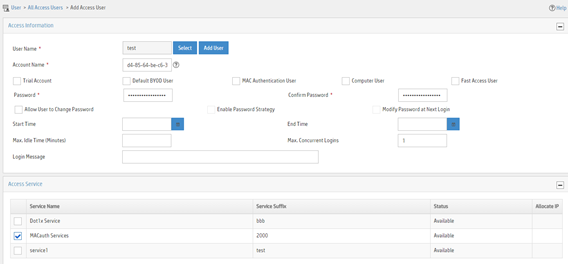
Configuring the device
1. Configure advanced ACL 3000 to deny packets destined for 10.0.0.1.
<Device> system-view
[Device] acl advanced 3000
[Device-acl-ipv4-adv-3000] rule 0 deny ip destination 10.0.0.1 0
[Device-acl-ipv4-adv-3000] quit
2. Configure RADIUS-based MAC authentication:
# Configure a RADIUS scheme.
|
IMPORTANT: With the service suffix configured on IMC, you must configure the device to send usernames that include the domain name to the RADIUS servers. By default, the device includes the domain name in the usernames sent to a RADIUS server. |
[Device] radius scheme 2000
[Device-radius-2000] primary authentication 10.1.1.1 1812
[Device-radius-2000] primary accounting 10.1.1.2 1813
[Device-radius-2000] key authentication simple expert
[Device-radius-2000] key accounting simple expert
[Device-radius-2000] user-name-format with-domain
[Device-radius-2000] quit
# Create ISP domain bbb and configure the ISP domain to use RADIUS scheme 2000 for user authentication, authorization, and accounting.
[Device] domain bbb
[Device-isp-bbb] authentication default radius-scheme 2000
[Device-isp-bbb] authorization default radius-scheme 2000
[Device-isp-bbb] accounting default radius-scheme 2000
[Device-isp-bbb] quit
# Specify ISP domain bbb as the global MAC authentication domain.
[Device] mac-authentication domain bbb
# Use the MAC address of each user as both the username and password for MAC authentication. The MAC addresses are in hexadecimal notation with hyphens, and letters are in lower case.
[Device] mac-authentication user-name-format mac-address with-hyphen lowercase
# Enable MAC authentication on interface GigabitEthernet 1/0/1.
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] mac-authentication
[Device-GigabitEthernet1/0/1] quit
# Enable MAC authentication globally.
[Device] mac-authentication
Verifying the configuration
|
IMPORTANT: Support for VSI- and microsegment-related fields depends on the device model. |
# Display MAC authentication settings and statistics.
<Device> display mac-authentication
Global MAC authentication parameters:
MAC authentication : Enable
Authentication method : PAP
DR member configuration conflict : Unknown
Username format : MAC address in lowercase(xx-xx-xx-xx-xx-xx)
Username : mac
Password : Not configured
MAC range accounts : 0
MAC address Mask Username
Offline detect period : 300 s
Quiet period : 60 s
Server timeout : 100 s
Reauth period : 3600 s
User aging period for critical VLAN : 1000 s
User aging period for critical VSI : 1000 s
User aging period for guest VLAN : 1000 s
User aging period for guest VSI : 1000 s
User aging period for critical microsegment: 1000 s
Temporary user aging period : 60 s
Authentication domain : bbb
HTTP proxy port list : Not configured
HTTPS proxy port list : Not configured
Online MAC-auth wired users : 1
Silent MAC users:
MAC address VLAN ID From port Port index
GigabitEthernet1/0/1 is link-up
MAC authentication : Enabled
Carry User-IP : Disabled
Authentication domain : Not configured
Auth-delay timer : Disabled
Periodic reauth : Disabled
Re-auth server-unreachable : Logoff
Guest VLAN : Not configured
Guest VLAN reauthentication : Enabled
Guest VLAN auth-period : 30 s
Critical VLAN : Not configured
Critical voice VLAN : Disabled
Host mode : Single VLAN
Offline detection : Enabled
Authentication order : Default
User aging : Enabled
Server-recovery online-user-sync : Enabled
Guest VSI : Not configured
Guest VSI reauthentication : Enabled
Guest VSI auth-period : 30 s
Critical VSI : Not configured
Critical microsegment ID : Not configured
URL user logoff : No
Auto-tag feature : Disabled
VLAN tag configuration ignoring : Disabled
Max online users : 4294967295
Authentication attempts : successful 1, failed 0
Current online users : 1
MAC address Auth state
0800-2712-3456 Authenticated
# Verify that you cannot ping the FTP server from the host.
C:\>ping 10.0.0.1
Pinging 10.0.0.1 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 10.0.0.1:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
The output shows that ACL 3000 has been assigned to GigabitEthernet 1/0/1 to deny access to the FTP server.
Configuration files
#
acl advanced 3000
rule 0 deny ip destination 10.0.0.1 0
#
radius scheme 2000
primary authentication 10.1.1.1
primary accounting 10.1.1.2
key authentication cipher $c$3$PJM7Px3rbC96Kvh8RyFWHMLatExagQ==
key accounting cipher $c$3$rr7AO7ZuSNZ+b+deWrfb/Qg1JPc97g==
#
domain bbb
authentication default radius-scheme 2000
authorization default radius-scheme 2000
accounting default radius-scheme 2000
#
mac-authentication domain bbb
#
mac-authentication user-name-format mac-address with-hyphen lowercase
#
interface GigabitEthernet1/0/1
mac-authentication
#
mac-authentication
#