- Table of Contents
-
- 08-Configuration Examples
- 01-Web Login Configuration Examples
- 02-Internet Access Through a Static IP Address Configuration Examples
- 03-Internet access through PPPoE configuration examples
- 04-Signature Library Upgrade Configuration Examples
- 04-Software Upgrade Examples(only for F50X0-D and F5000-AK5X5 firewalls)
- 05-Software Upgrade Examples
- 06-Static routing configuration examples
- 07-OSPF configuration examples
- 08-BGP configuration examples
- 09-RIP configuration examples
- 10-DHCP configuration examples
- 11-DNS configuration examples
- 12-Object Group Configuration Examples
- 13-Public key management configuration examples
- 14-Security Policy Configuration Examples
- 15-Attack defense configuration examples
- 16-Connection Limit Configuration Examples
- 17-IPS Configuration Examples
- 18-URL Filtering Configuration Examples
- 19-Anti-Virus Configuration Examples
- 20-Data Filtering Configuration Examples
- 21-File Filtering Configuration Examples
- 22-APR-Based Security Policy Configuration Examples
- 23-Bandwidth Management Configuration Examples
- 24-NAT configuration examples
- 25-NAT hairpin configuration examples
- 26-IPsec configuration examples
- 27-SSL VPN configuration examples
- 28-Server Load Balancing Configuration Examples
- 29-Outbound Link Load Balancing Configuration Examples
- 30-Inbound Link Load Balancing Configuration Examples
- 31-Transparent DNS Proxy Configuration Examples
- 32-Context Configuration Examples
- 32-Context Configuration Examples(only for F50X0-D and F5000-AK5X5 firewalls)
- 33-IRF configuration examples
- 34-High Availability Group Configuration Examples
- 35-NAT Flow Logging Configuration Examples
- 36-User identification configuration examples
- 37-Server Connection Detection Configuration Examples
- 38-IP Reputation Configuration Examples
- 39-NPTv6 Configuration Examples
- 40-SSL Decryption Configuration Examples
- 41-MAC Address Learning Through a Layer 3 Device Configuration Examples
- 42-WAF Configuration Examples
- 43-NetShare Control Configuration Examples
- 44-4G Configuration Examples
- 45-WLAN Configuration Examples
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 34-High Availability Group Configuration Examples | 807.91 KB |
High availability group configuration examples
Introduction
The following information provides high availability (HA) group configuration examples.
This document is not restricted to specific software or hardware versions. Procedures and information in the examples might be slightly different depending on the software or hardware version of the device.
The configuration examples were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
The following information is provided based on the assumption that you have basic knowledge of the HA group, VRRP, and Track features.
Verify that the devices to be assigned to the HA group meet the hardware and software environment consistency requirements in this section.
Hardware environment consistency
Before you configure the HA group, verify that the following hardware settings are the same on the devices to be assigned to the HA group:
· Device model.
· Location, number, and type of MPUs.
· Location, number, and type of service modules.
· Location, number, and type of switching fabric modules.
· Location, number, and type of interface modules.
· Number and type of management interfaces, service interfaces, interfaces for setting up the control channel, and interfaces for setting up the data channel. Do not use one interface for multiple purposes.
· Location, number, and type of disks. A device without disks installed has small log storage and does not support some types of logs or reports.
Software environment consistency
Before you configure the HA group, verify that the following software settings are the same on the devices to be assigned to the HA group:
· Software environment and version, including boot packages, system packages, feature packages, and patches.
· Licensed signature libraries and features, such as signature library types, signature library version, validation time, and number of licensed resources.
· Interface numbers.
· Type, speed, and number of the interfaces for setting up the control channel. As a best practice, use aggregate interfaces.
· Type, speed, and number of the interfaces for setting up the data channel. As a best practice, use aggregate interfaces.
· Aggregate interface numbers and aggregation member port numbers.
· Security zone configuration on the interfaces at the same location.
Feature compatibility restrictions
Compatibility with NAT
If you configure both VRRP and NAT on the HA group, you must associate NAT configuration with VRRP groups, such as NAT rules, source translation methods, and NAT server mappings. If you fail to do so, NAT cannot operate correctly.
Compatibility with SSL VPN
For SSL VPN to operate correctly on the HA group, you must configure the port used for transmitting user data for the HA group on the global setting configuration page of SSL VPN.
You can use SSL VPN only when the HA group is operating in active/standby mode.
Compatibility with application security
If asymmetric-path traffic exists on the transparent in-path HA group operating in dual-active mode, enable DPI services to support the HA group feature on the advanced setting configuration page of application security. If you fail to do so, application security services cannot identify or process traffic correctly.
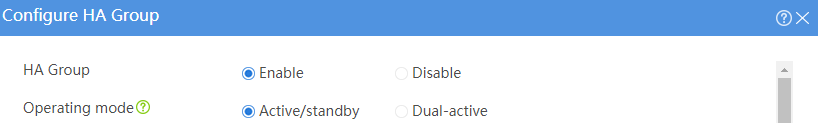
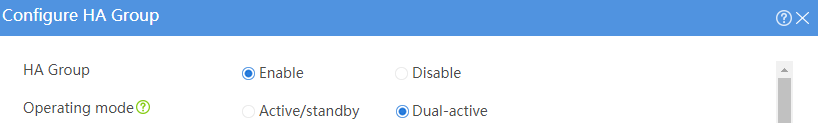
Example: Configuring the HA group in active/standby mode in collaboration with VRRP (IPv4)
Network configuration
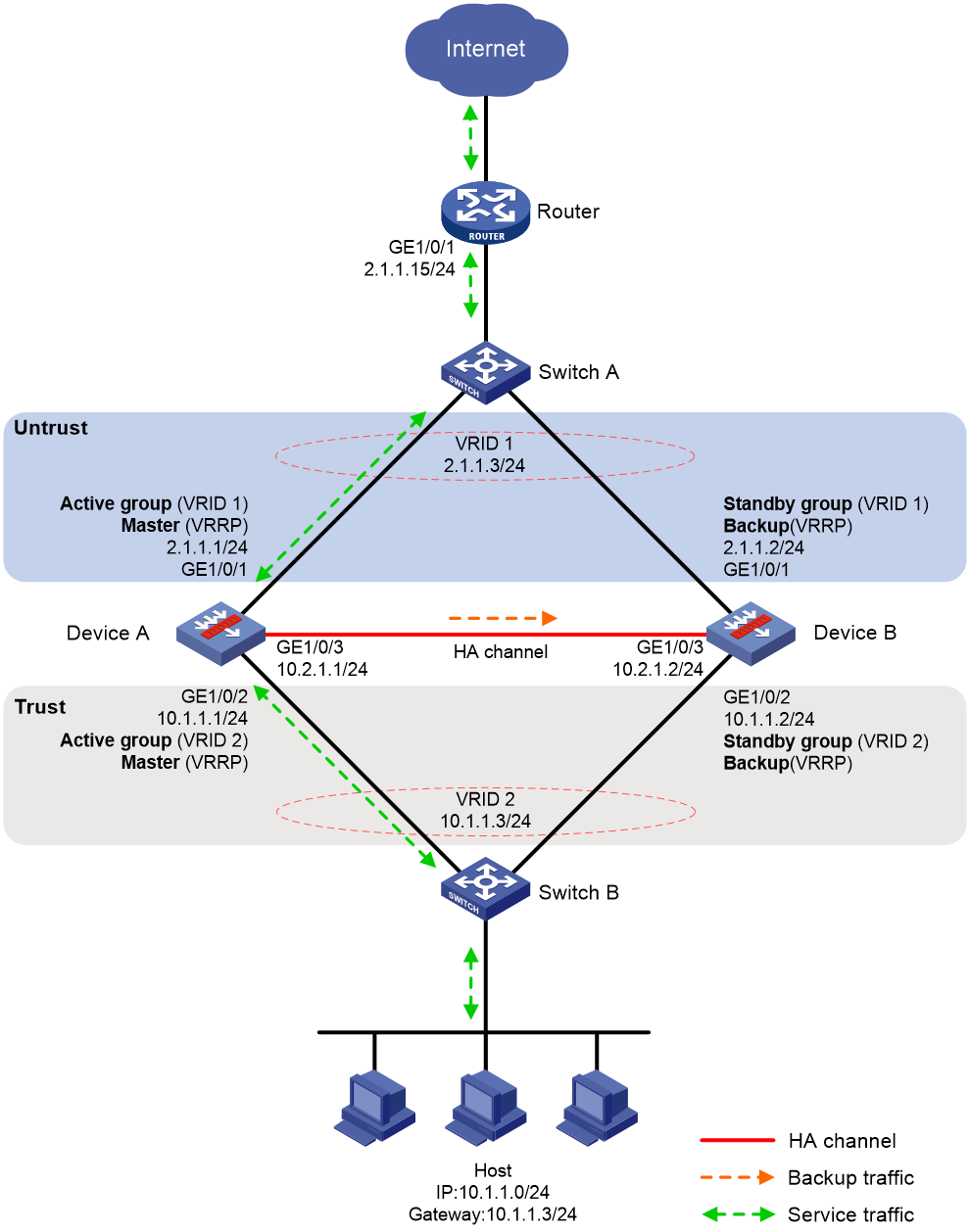
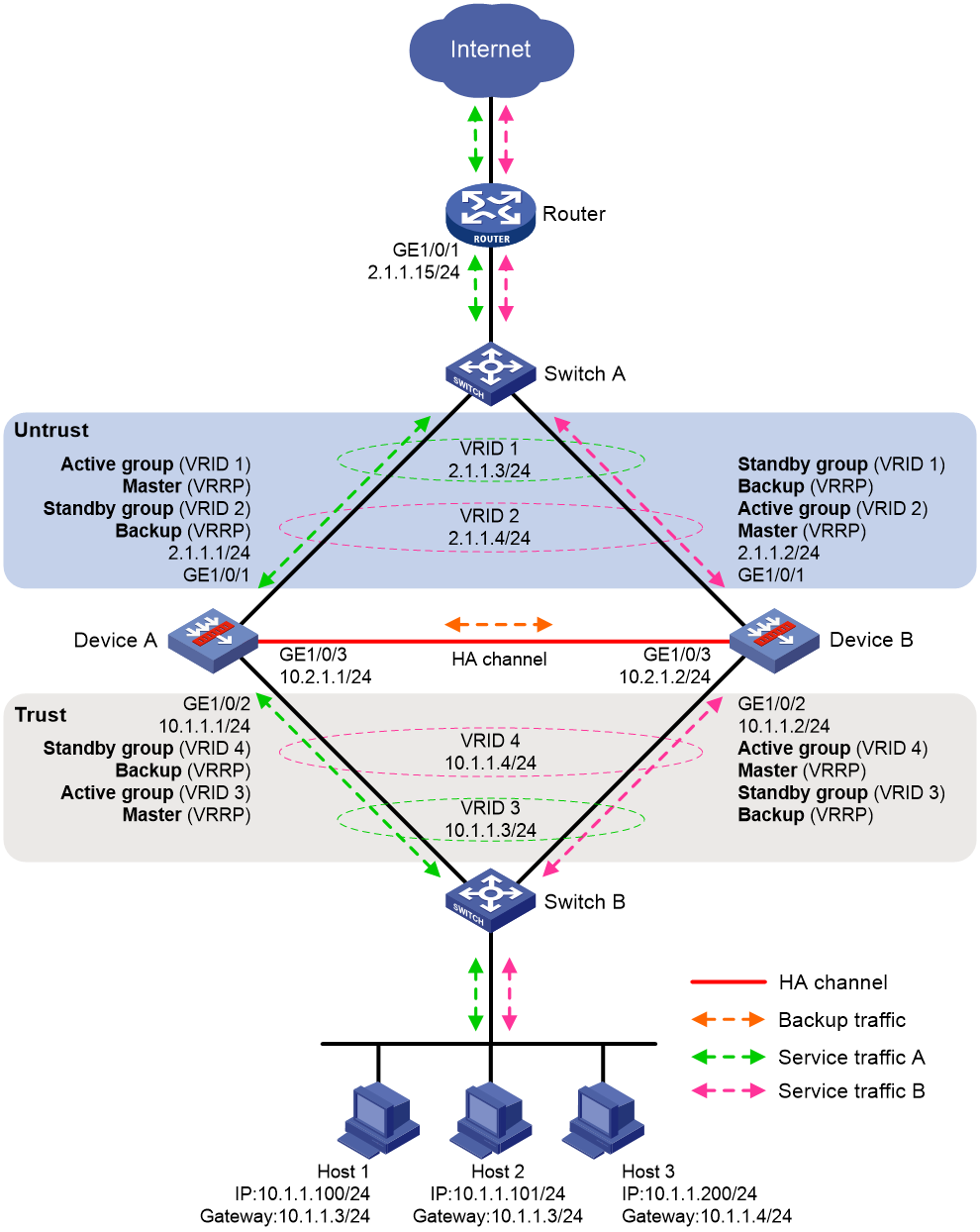
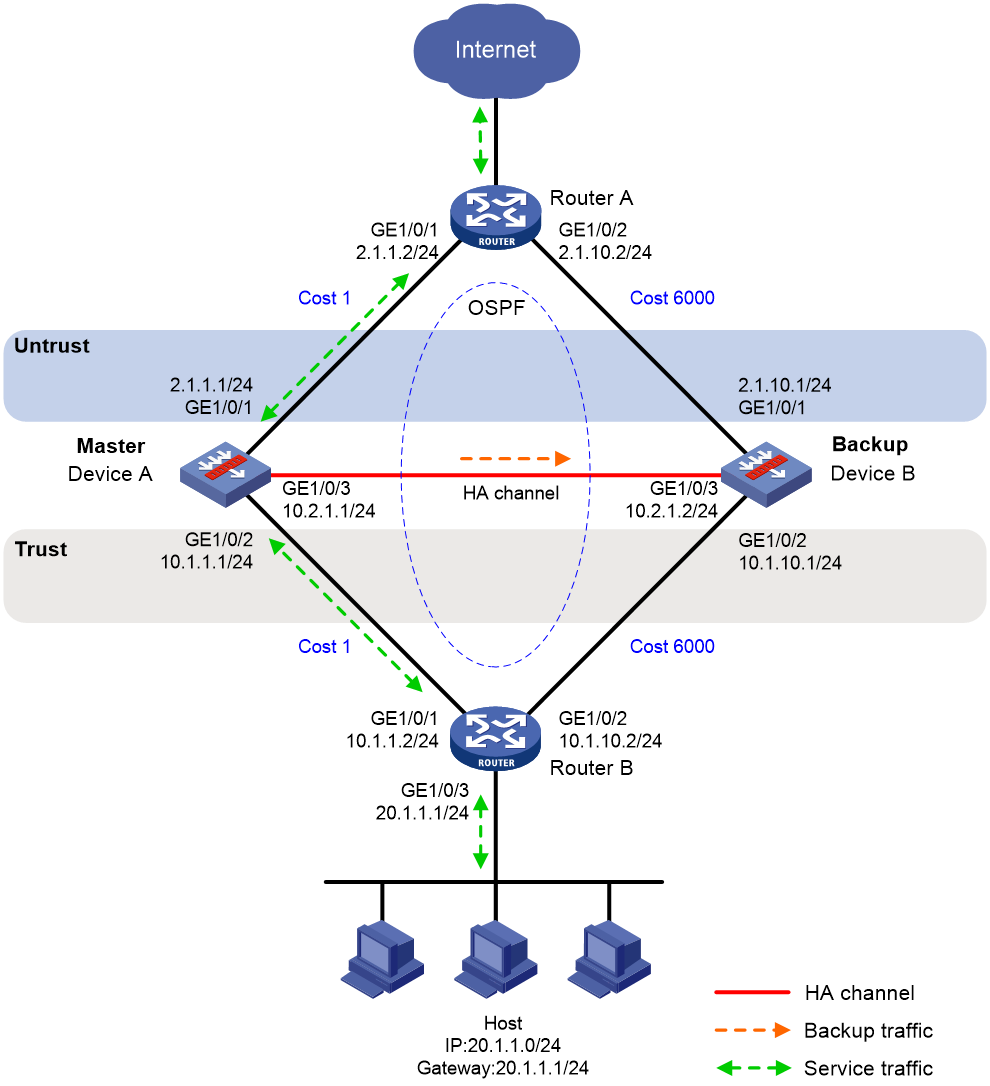
As shown in Figure 1, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with VRRP.
· Configure the HA group to operate in active/standby mode.
· Configure Device A and Device B as the primary device and the secondary device, respectively.
Software versions used
This configuration example was created and verified on F9345 of the F1060 device.
Procedure
Configuring Switch A
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the router to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
Configuring Switch B
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the host to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
Configuring the router
# Assign 2.1.1.15/24 to GigabitEthernet 1/0/1.
# Configure routes as follows:
· Specify 2.1.1.3 (virtual IP address of VRRP group 1) as the next hop of the routes to the internal network.
· Specify the IP address of the peer interface attached to the traffic outgoing interface as the next hop of the route to the Internet.
Configuring Device A
Configuring basic network settings
1. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Untrust security zone.
b. On the IPv4 Address tab, enter the IP address and mask of the interface. In this example, enter 2.1.1.1/24.
c. Use the default settings for other parameters.
d. Click OK.
# Add GE 1/0/2 to the Trust security zone and assign 10.1.1.1/24 to it in the same way you configure GE 1/0/1.
# Assign 10.2.1.1/24 to GE 1/0/3 in the same way you configure GE 1/0/1.
2. Configure routing:
This step uses static routing as an example. To use dynamic routing, configure a dynamic routing protocol.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > Static Routing.
# On the IPv4 Static Routing tab, click Create.
# In the dialog box that opens, configure an IPv4 static route:
a. Enter destination IP address 0.0.0.0.
b. Enter mask length 0.
c. Enter next hop address 2.1.1.15.
d. Use the default settings for other parameters.
e. Click OK.
3. Configure a security policy to permit service traffic:
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Untrust:
a. Enter security policy name Trust-Untrust.
b. Select source zone Trust.
c. Select destination zone Untrust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Enter source IP address 10.1.1.0/24.
g. Use the default settings for other parameters.
h. Click OK.
4. Configure security policies to permit VRRP protocol packets:
This task allows Device A and Device B to exchange VRRP packets and elect a VRRP master when the HA channels are disconnected.
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Local:
a. Enter security policy name vrrp1.
b. Select source zone Trust.
c. Select destination zone Local.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group vrrp.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Local to zone Trust:
a. Enter security policy name vrrp2.
b. Select source zone Local.
c. Select destination zone Trust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group vrrp.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Untrust to zone Local:
a. Enter security policy name vrrp3.
b. Select source zone Untrust.
c. Select destination zone Local.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group vrrp.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Local to zone Untrust:
a. Enter security policy name vrrp4.
b. Select source zone Local.
c. Select destination zone Untrust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group vrrp.
g. Use the default settings for other parameters.
h. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
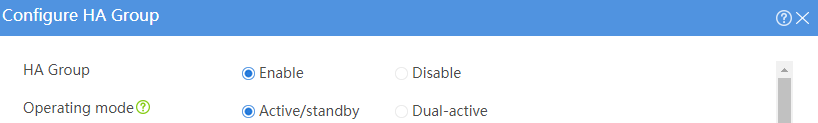
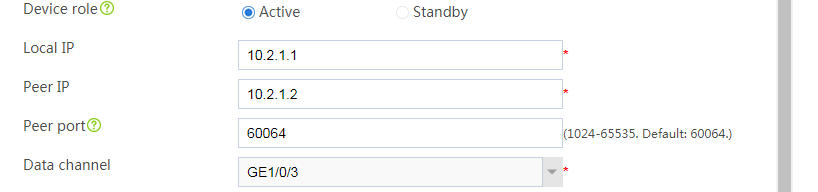
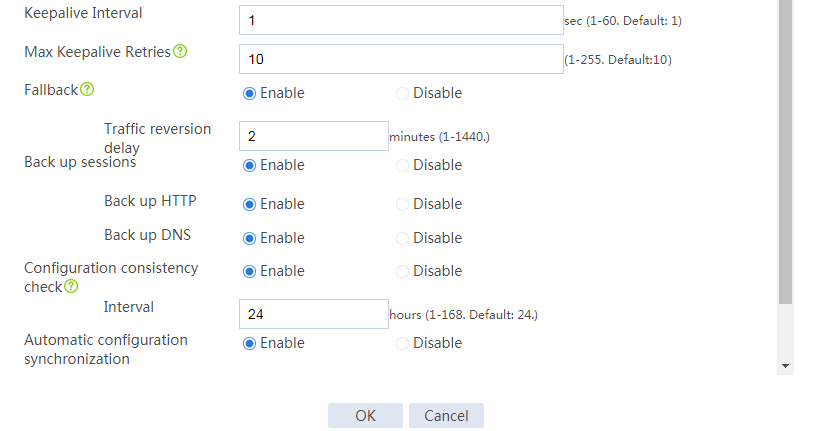
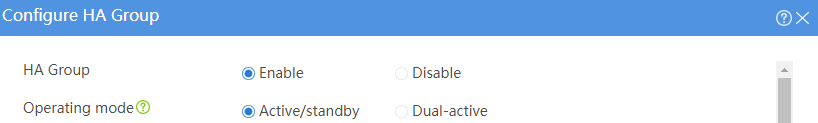
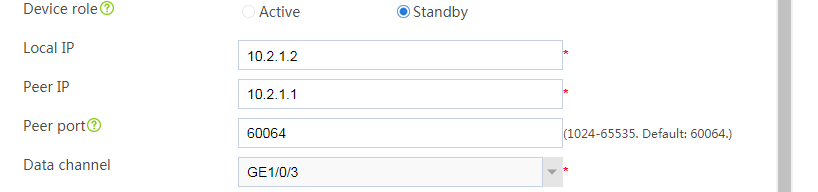
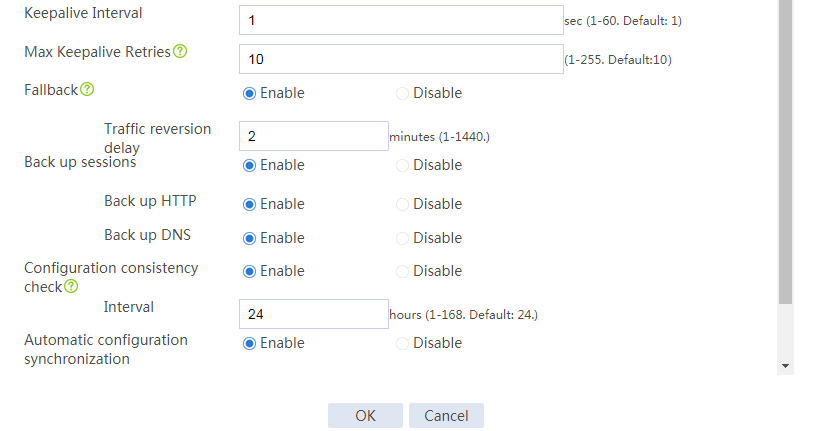
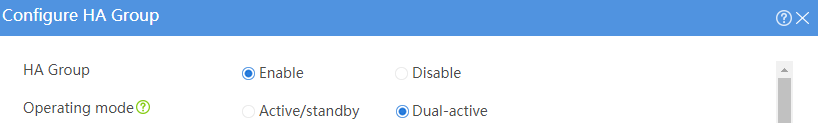
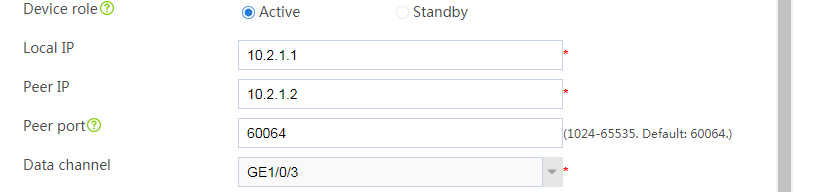
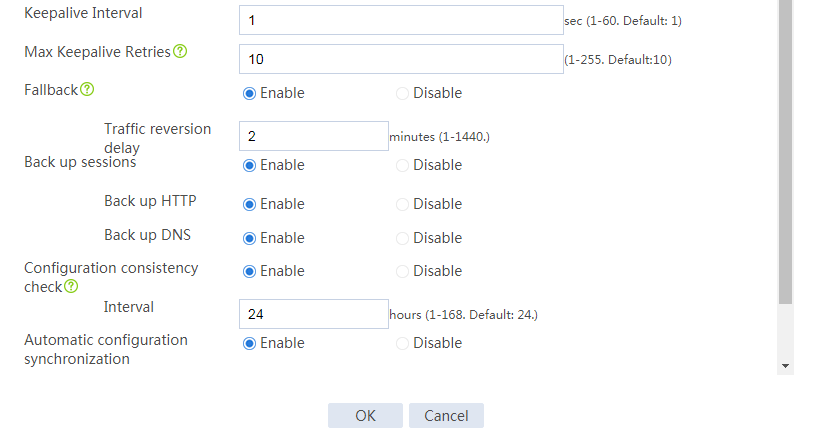
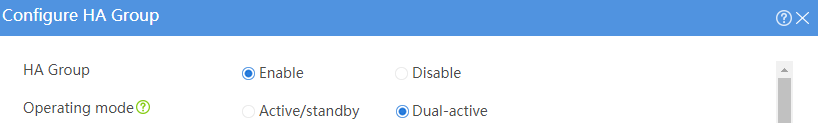
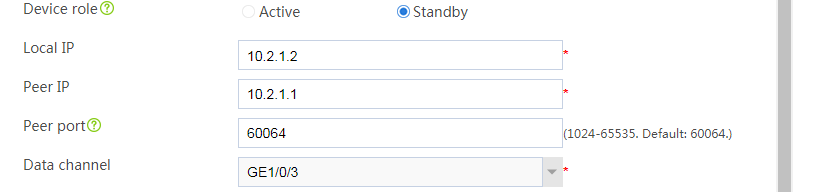
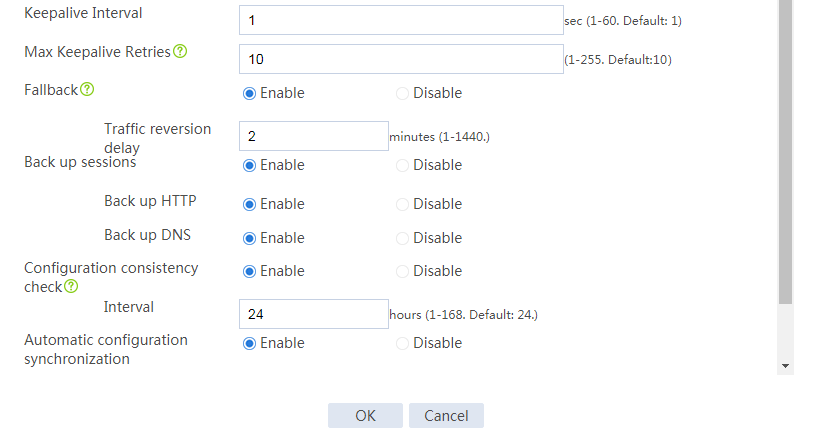
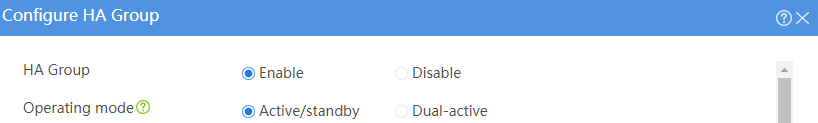
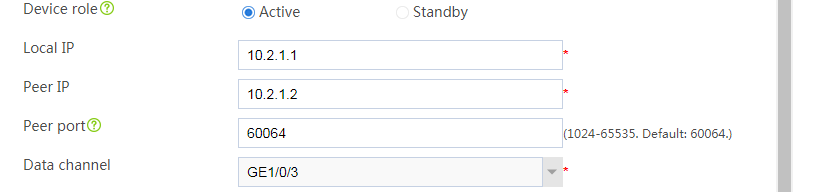
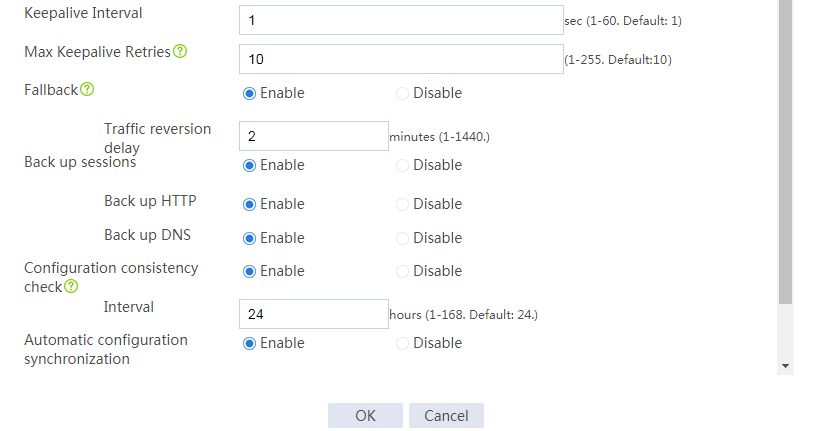
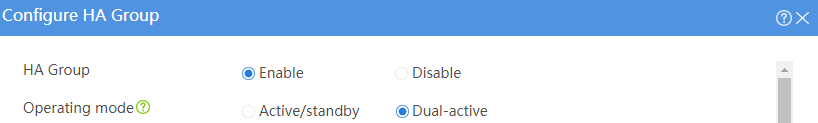
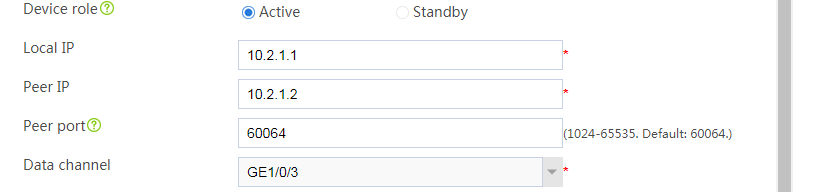
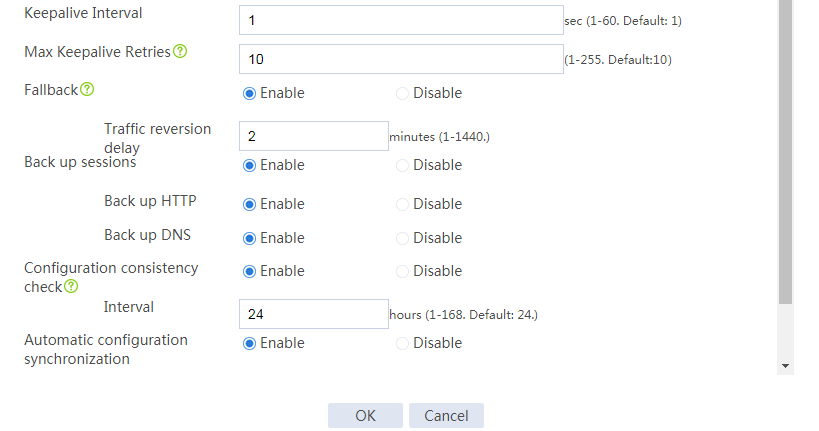
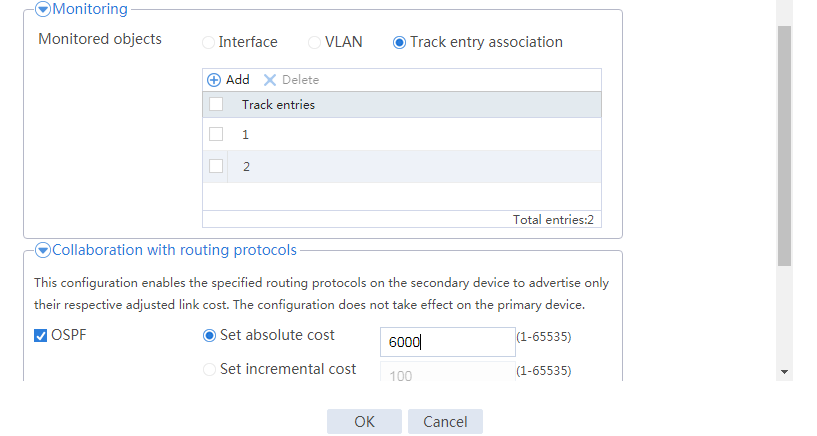
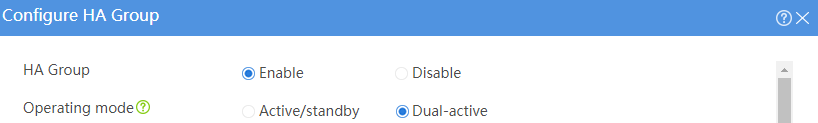
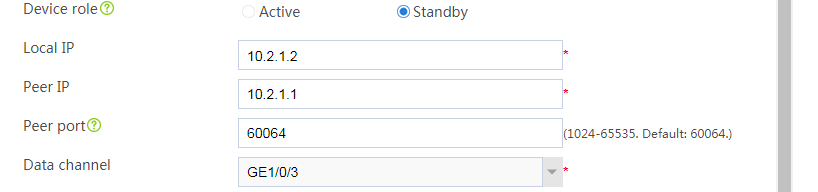
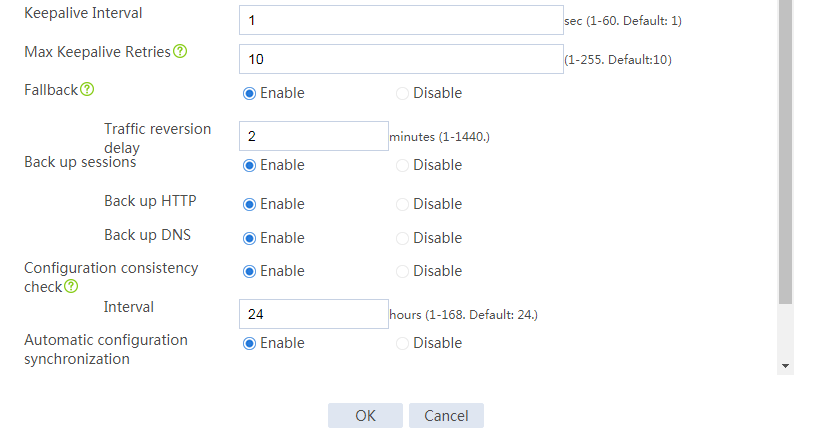
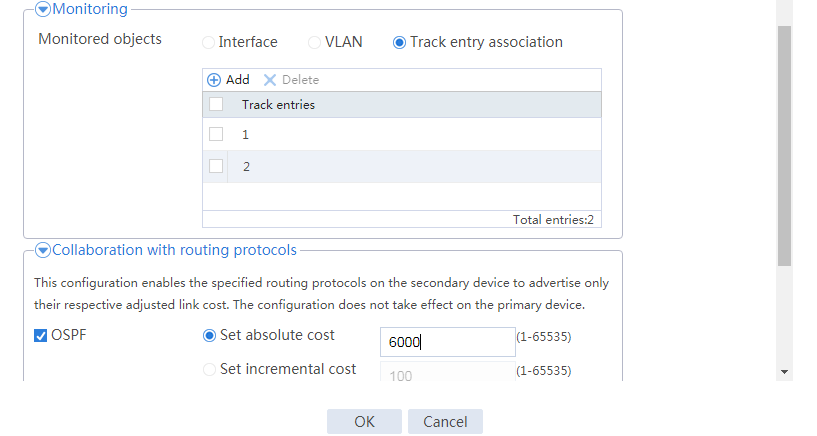
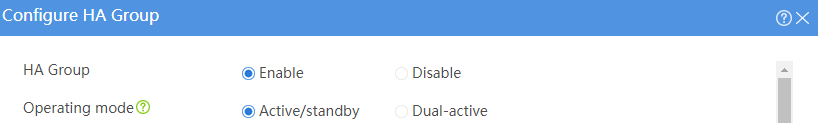
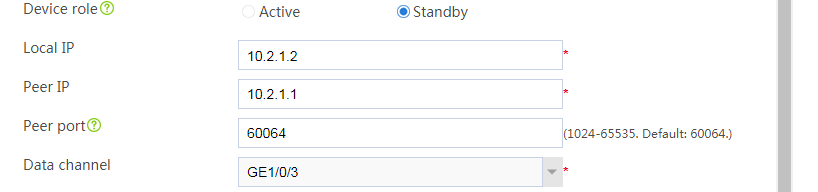
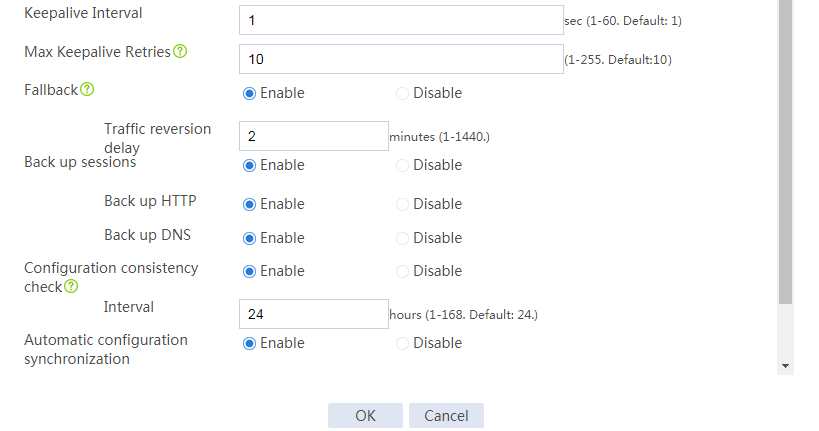
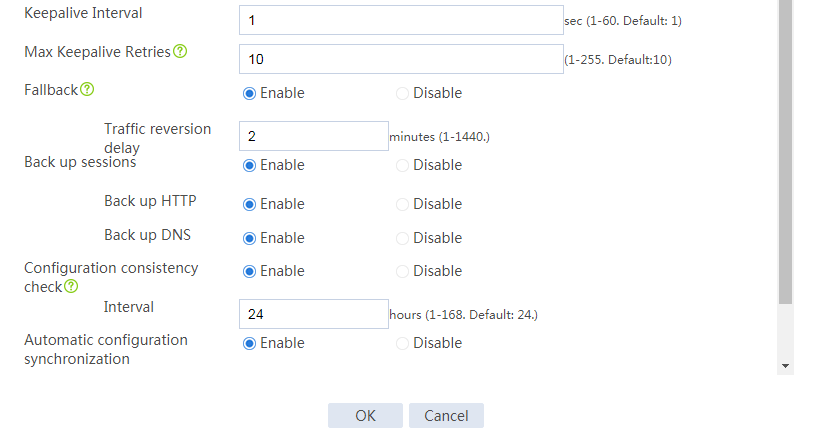
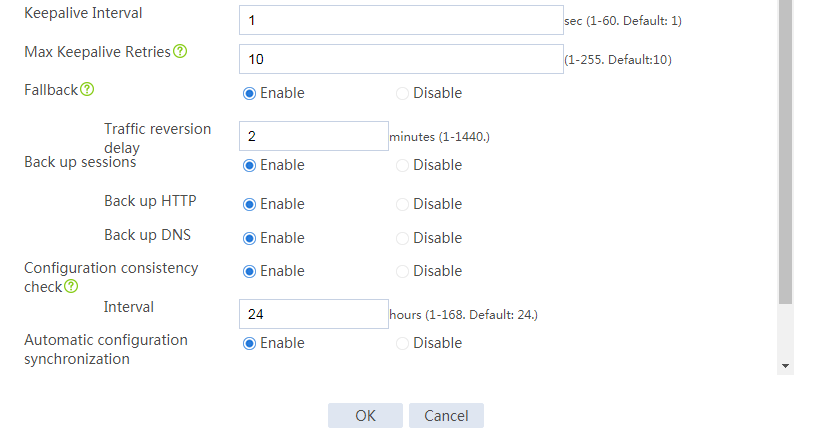
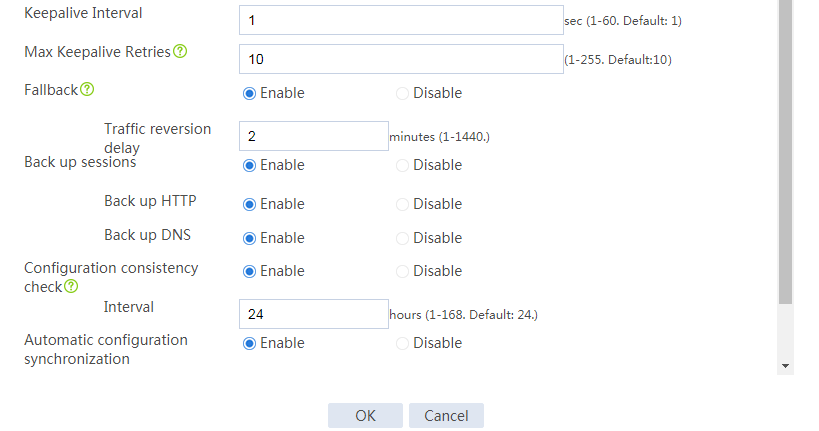
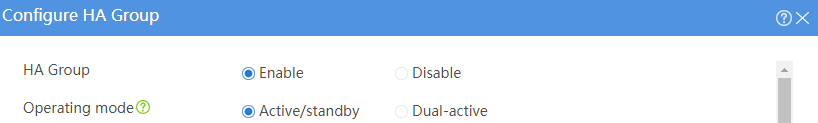
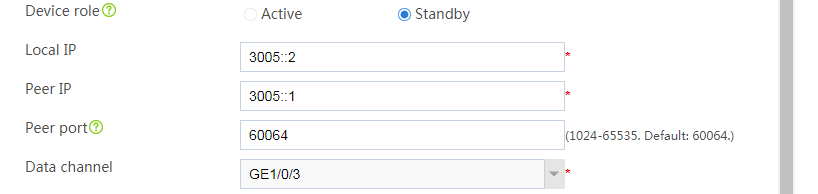
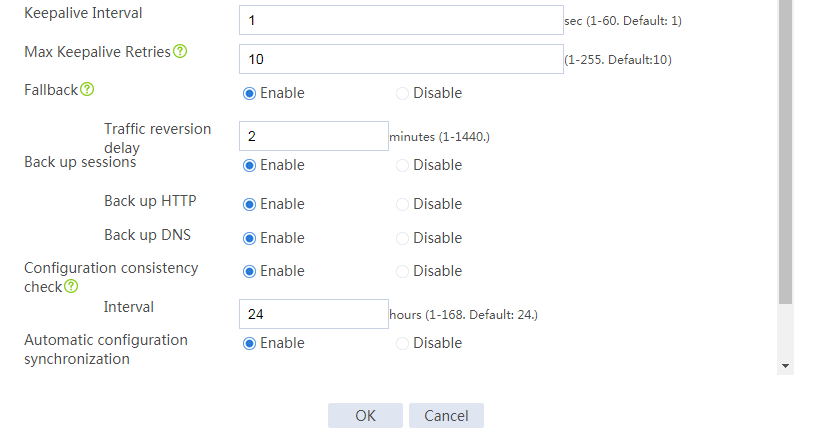
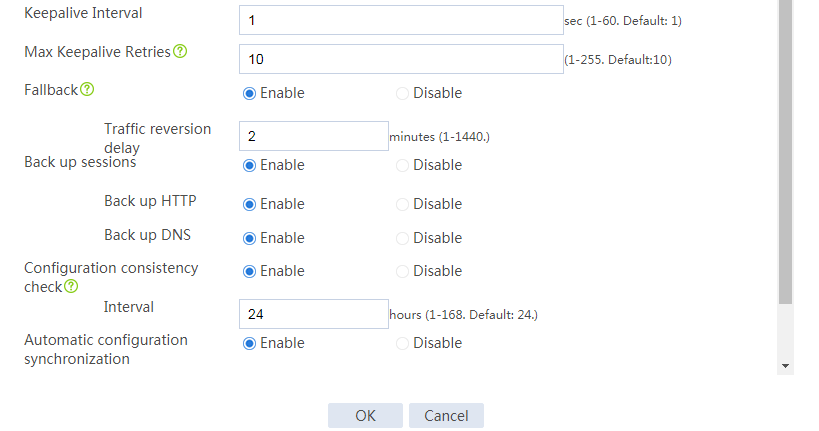
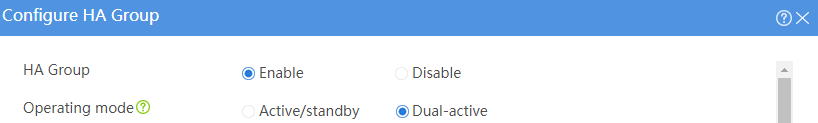
# Configure the HA group parameters as shown in Figure 2.
Figure 2 Configuring HA group parameters
# Click OK.
Associating the HA group with VRRP
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > VRRP.
# Click Create.
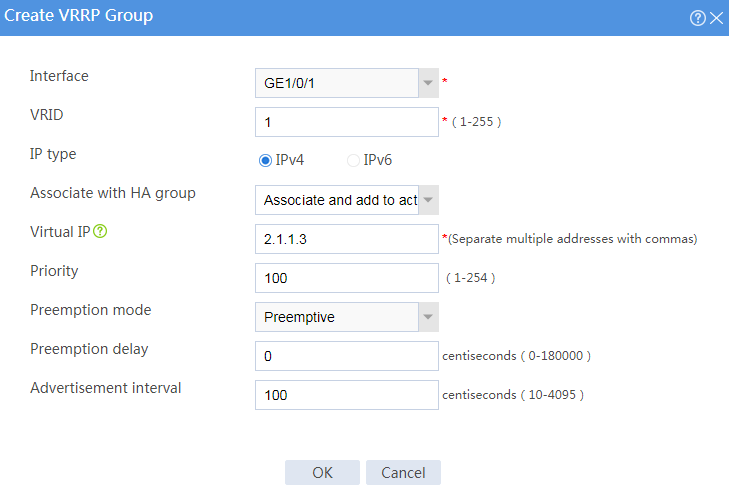
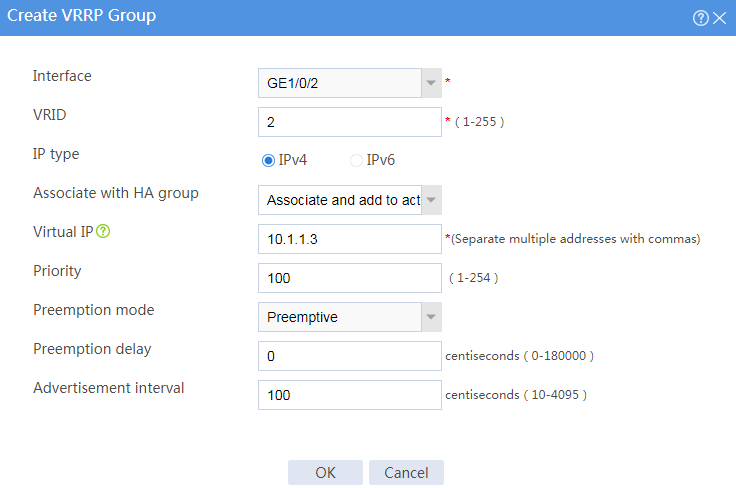
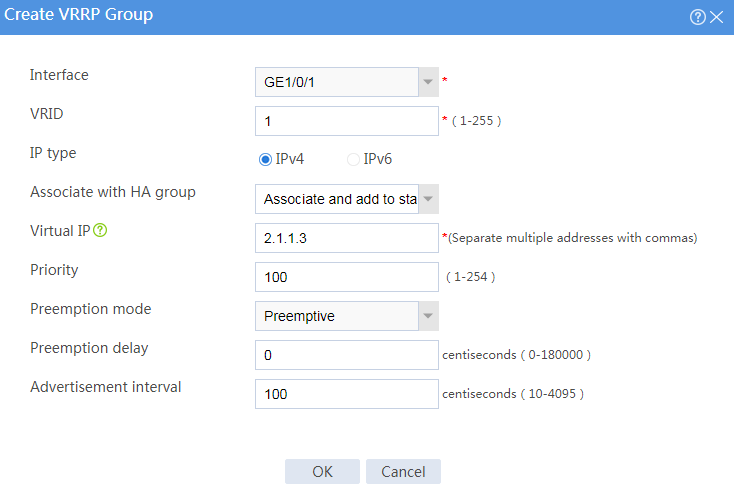
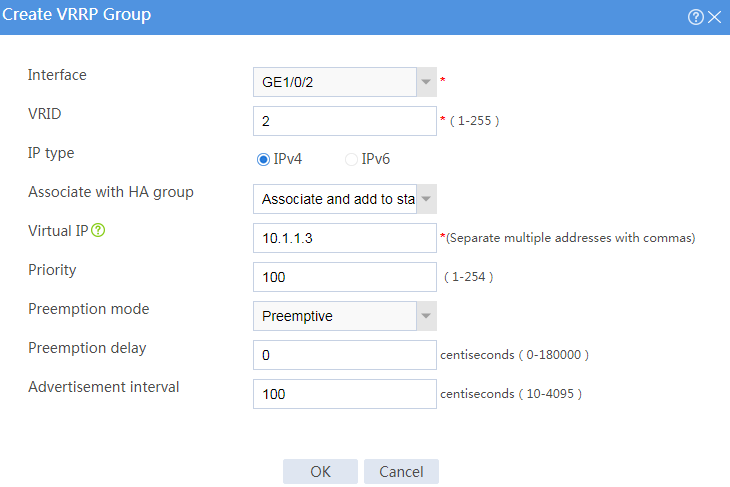
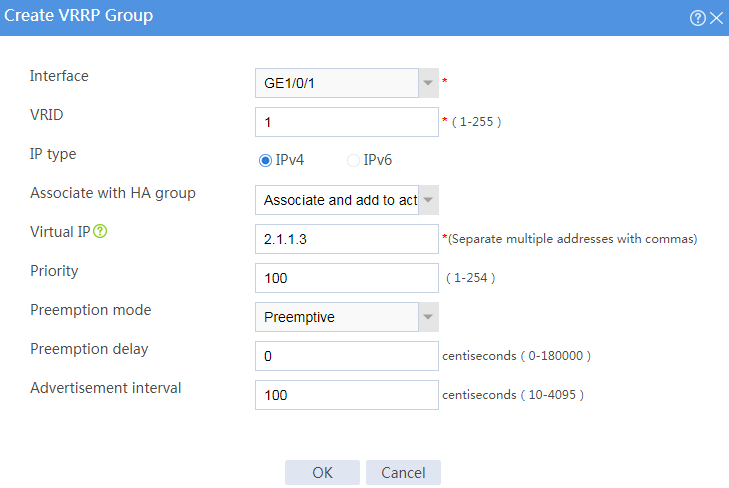
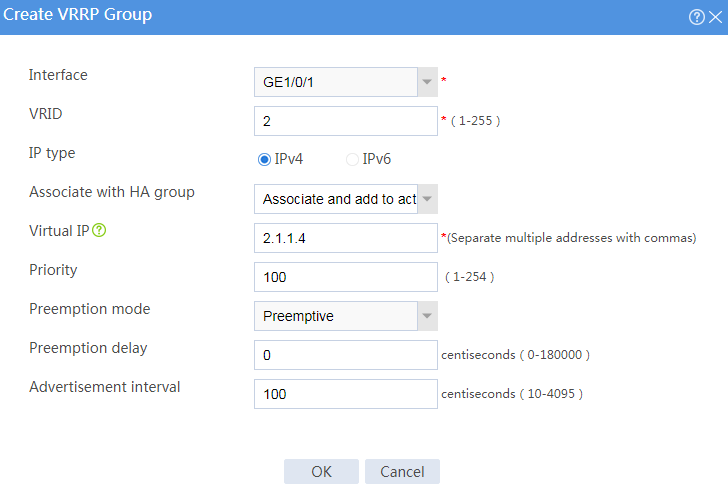
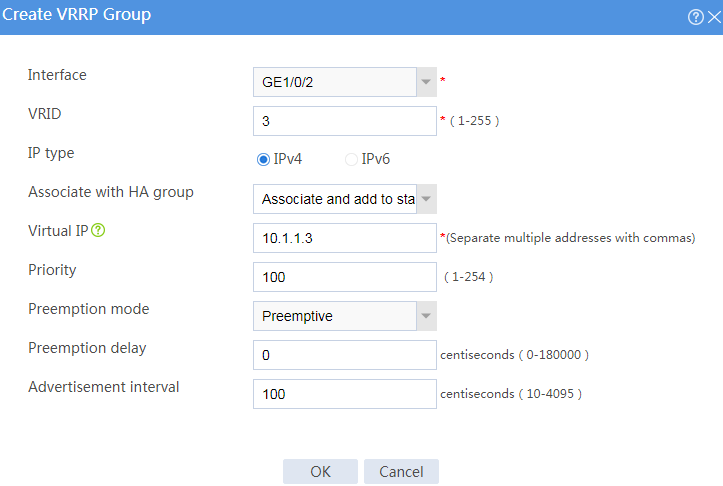
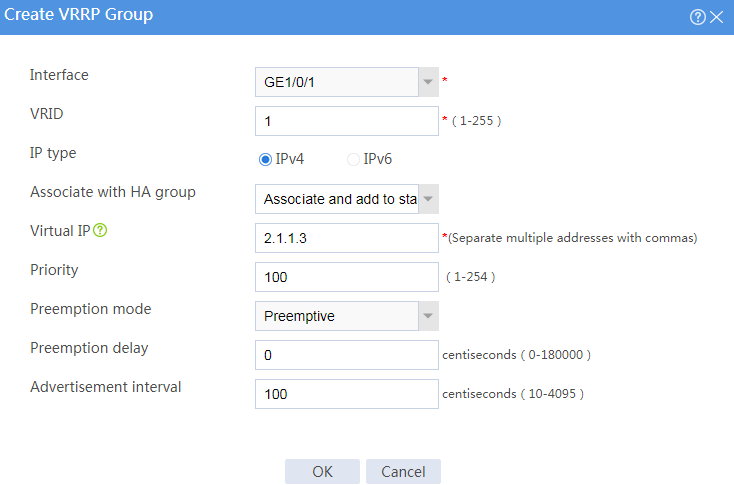
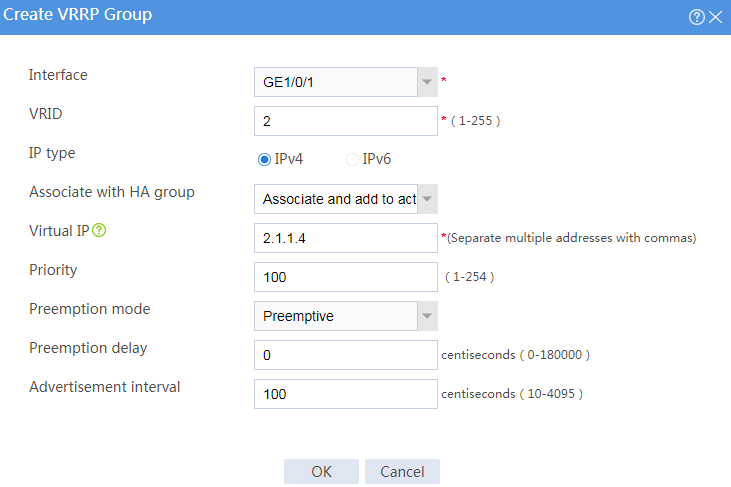
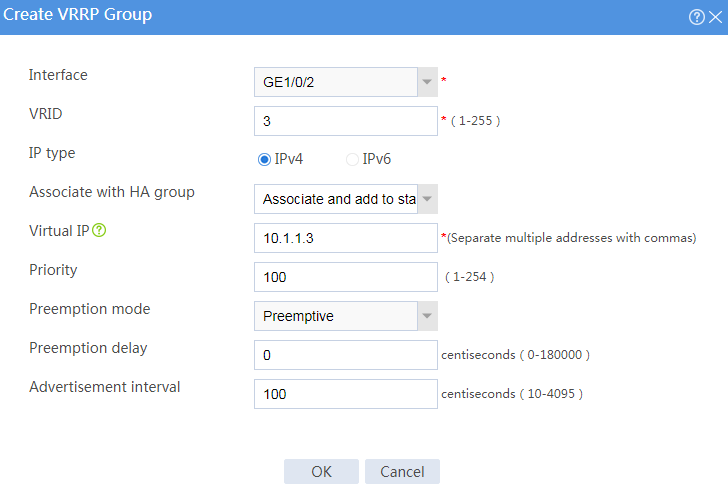
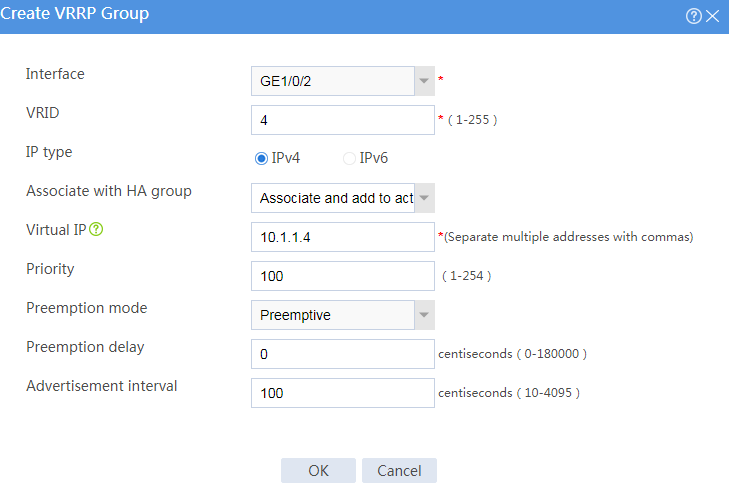
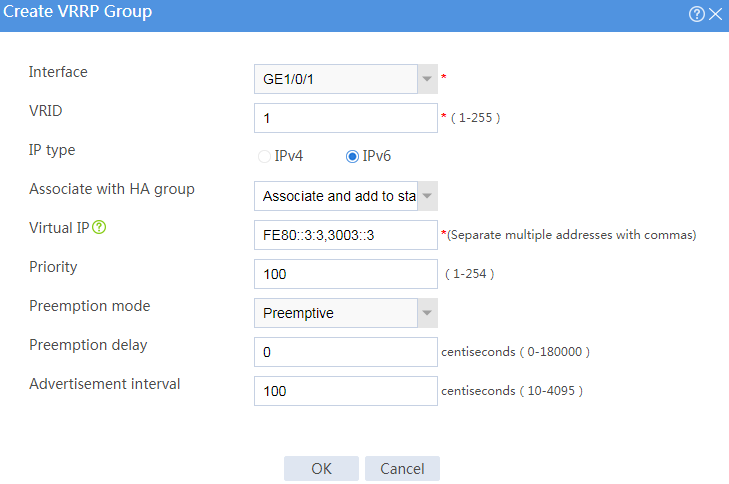
# Configure VRRP groups as shown in the follow figures.
Figure 3 Creating VRRP group 1
Figure 4 Creating VRRP group 2
# Click OK.
Configuring security services
# Configure security devices on the HA group member devices. If the HA group can back up configuration for a module, configure the module only on the primary device (Device A).
Configuring Device B
Configuring basic network settings
1. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Untrust security zone.
b. On the IPv4 Address tab, enter the IP address and mask of the interface. In this example, enter 2.1.1.2/24.
c. Use the default settings for other parameters.
d. Click OK.
# Add GE 1/0/2 to the Trust security zone and assign 10.1.1.2/24 to it in the same way you configure GE 1/0/1.
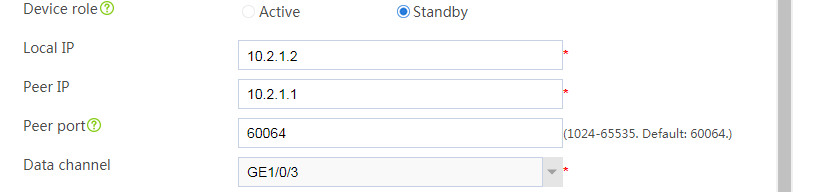
# Assign 10.2.1.2/24 to GE 1/0/3 in the same way you configure GE 1/0/1.
2. Configure routing:
This step uses static routing as an example. To use dynamic routing, configure a dynamic routing protocol.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > Static Routing.
# On the IPv4 Static Routing tab, click Create.
# In the dialog box that opens, configure an IPv4 static route:
a. Enter destination IP address 0.0.0.0.
b. Enter mask length 0.
c. Enter next hop address 2.1.1.15.
d. Use the default settings for other parameters.
e. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
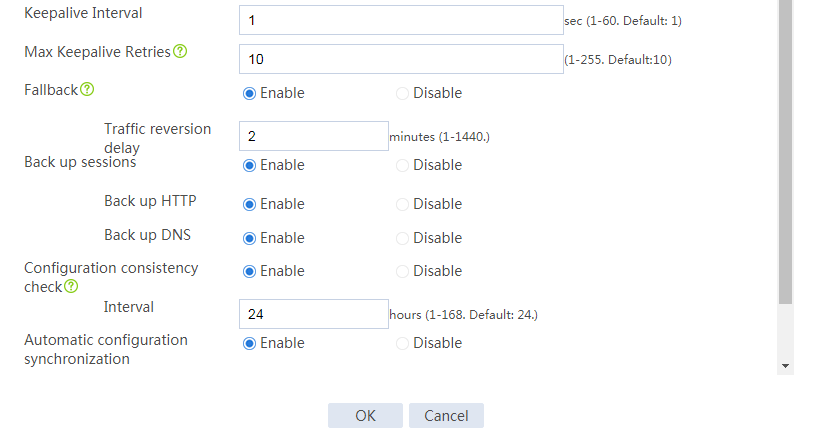
# Configure the HA group parameters as shown in Figure 5.
Figure 5 Configuring HA group parameters
# Click OK.
Associating the HA group with VRRP
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > VRRP.
# Click Create.
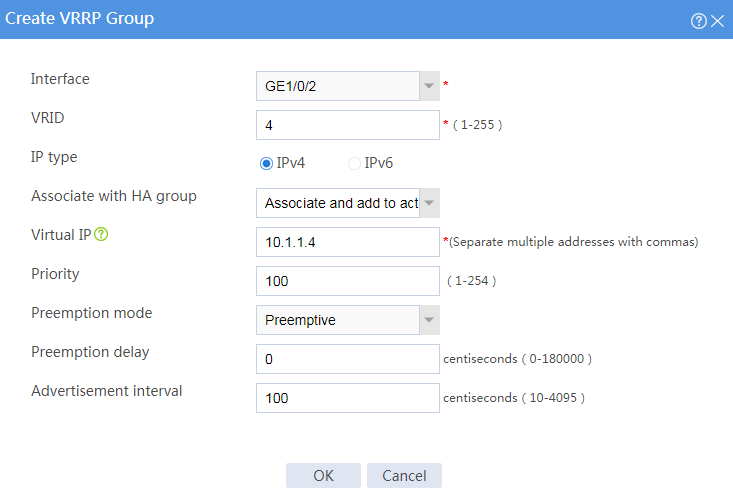
# Configure VRRP groups as shown in the follow figures.
Figure 6 Creating VRRP group 1
Figure 7 Creating VRRP group 2
# Click OK.
Configuring the host
# On the host, specify 10.1.1.3 (virtual IP address of VRRP group 2) as the default gateway.
Verifying the configuration
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that only Device A generates log messages when the host communicates with the Internet.
Network configuration
As shown in Figure 8, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with VRRP.
· Configure the HA group to operate in dual-active mode.
· Configure Device A and Device B to load share traffic.
Software versions used
This configuration example was created and verified on F9345 of the F1060 device.
Procedure
Configuring Switch A
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the router to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
Configuring Switch B
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the host to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
Configuring the router
# Assign 2.1.1.15/24 to GigabitEthernet 1/0/1.
# Specify 2.1.1.3 (virtual IP address of VRRP group 1) as the next hop of the routes to some subnets of the internal network. Specify 2.1.1.4 (virtual IP address of VRRP group 2) as the next hop of the routes to the other subnets of the internal network.
# Specify the IP address of the peer interface attached to the traffic outgoing interface as the next hop of the route to the Internet.
Configuring Device A
Configuring basic network settings
1. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Untrust security zone.
b. On the IPv4 Address tab, enter the IP address and mask of the interface. In this example, enter 2.1.1.1/24.
c. Use the default settings for other parameters.
d. Click OK.
# Add GE 1/0/2 to the Trust security zone and assign 10.1.1.1/24 to it in the same way you configure GE 1/0/1.
# Assign 10.2.1.1/24 to GE 1/0/3 in the same way you configure GE 1/0/1.
2. Configure routing:
This step uses static routing as an example. To use dynamic routing, configure a dynamic routing protocol.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > Static Routing.
# On the IPv4 Static Routing tab, click Create.
# In the dialog box that opens, configure an IPv4 static route:
a. Enter destination IP address 0.0.0.0.
b. Enter mask length 0.
c. Enter next hop address 2.1.1.15.
d. Use the default settings for other parameters.
e. Click OK.
3. Configure a security policy to permit service traffic:
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Untrust:
a. Enter security policy name Trust-Untrust.
b. Select source zone Trust.
c. Select destination zone Untrust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Enter source IP address 10.1.1.0/24.
g. Use the default settings for other parameters.
h. Click OK.
4. Configure security policies to permit VRRP protocol packets:
This task allows Device A and Device B to exchange VRRP packets and elect a VRRP master when the HA channels are disconnected.
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Local:
a. Enter security policy name vrrp1.
b. Select source zone Trust.
c. Select destination zone Local.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group vrrp.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Local to zone Trust:
a. Enter security policy name vrrp2.
b. Select source zone Local.
c. Select destination zone Trust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group vrrp.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Untrust to zone Local:
a. Enter security policy name vrrp3.
b. Select source zone Untrust.
c. Select destination zone Local.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group vrrp.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Local to zone Untrust:
a. Enter security policy name vrrp4.
b. Select source zone Local.
c. Select destination zone Untrust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group vrrp.
g. Use the default settings for other parameters.
h. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
# Configure the HA group parameters as shown in Figure 9.
Figure 9 Configuring HA group parameters
# Click OK.
Associating the HA group with VRRP
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > VRRP.
# Click Create.
# Configure VRRP groups as shown in the follow figures.
Figure 10 Creating VRRP group 1
Figure 11 Creating VRRP group 2
Figure 12 Creating VRRP group 3
Figure 13 Creating VRRP group 4
# Click OK.
Configuring security services
# Configure security devices on the HA group member devices. If the HA group can back up configuration for a module, configure the module only on the primary device (Device A).
Configuring Device B
Configuring basic network settings
1. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Untrust security zone.
b. On the IPv4 Address tab, enter the IP address and mask of the interface. In this example, enter 2.1.1.2/24.
c. Use the default settings for other parameters.
d. Click OK.
# Add GE 1/0/2 to the Trust security zone and assign 10.1.1.2/24 to it in the same way you configure GE 1/0/1.
# Assign 10.2.1.2/24 to GE 1/0/3 in the same way you configure GE 1/0/1.
2. Configure routing:
This step uses static routing as an example. To use dynamic routing, configure a dynamic routing protocol.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > Static Routing.
# On the IPv4 Static Routing tab, click Create.
# In the dialog box that opens, configure an IPv4 static route:
a. Enter destination IP address 0.0.0.0.
b. Enter mask length 0.
c. Enter next hop address 2.1.1.15.
d. Use the default settings for other parameters.
e. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
# Configure the HA group parameters as shown in Figure 14.
Figure 14 Configuring HA group parameters
# Click OK.
Associating the HA group with VRRP
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > VRRP.
# Click Create.
# Configure VRRP groups as shown in the follow figures.
Figure 15 Creating VRRP group 1
Figure 16 Creating VRRP group 2
Figure 17 Creating VRRP group 3
Figure 18 Creating VRRP group 4
# Click OK.
Configuring the hosts
# On some hosts, specify 10.1.1.3 (virtual IP address of VRRP group 3) as the default gateway. On the other hosts, specify 10.1.1.4 (virtual IP address of VRRP group 4) as the default gateway.
Verifying the configuration
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that only Device A generates log messages when a host for which Device A forwards traffic communicates with the Internet. Verity that only Device B generates log messages when a host for which Device B forwards traffic communicates with the Internet.
Example: Configuring the HA group in active/standby mode in collaboration with a routing protocol (IPv4)
Network configuration
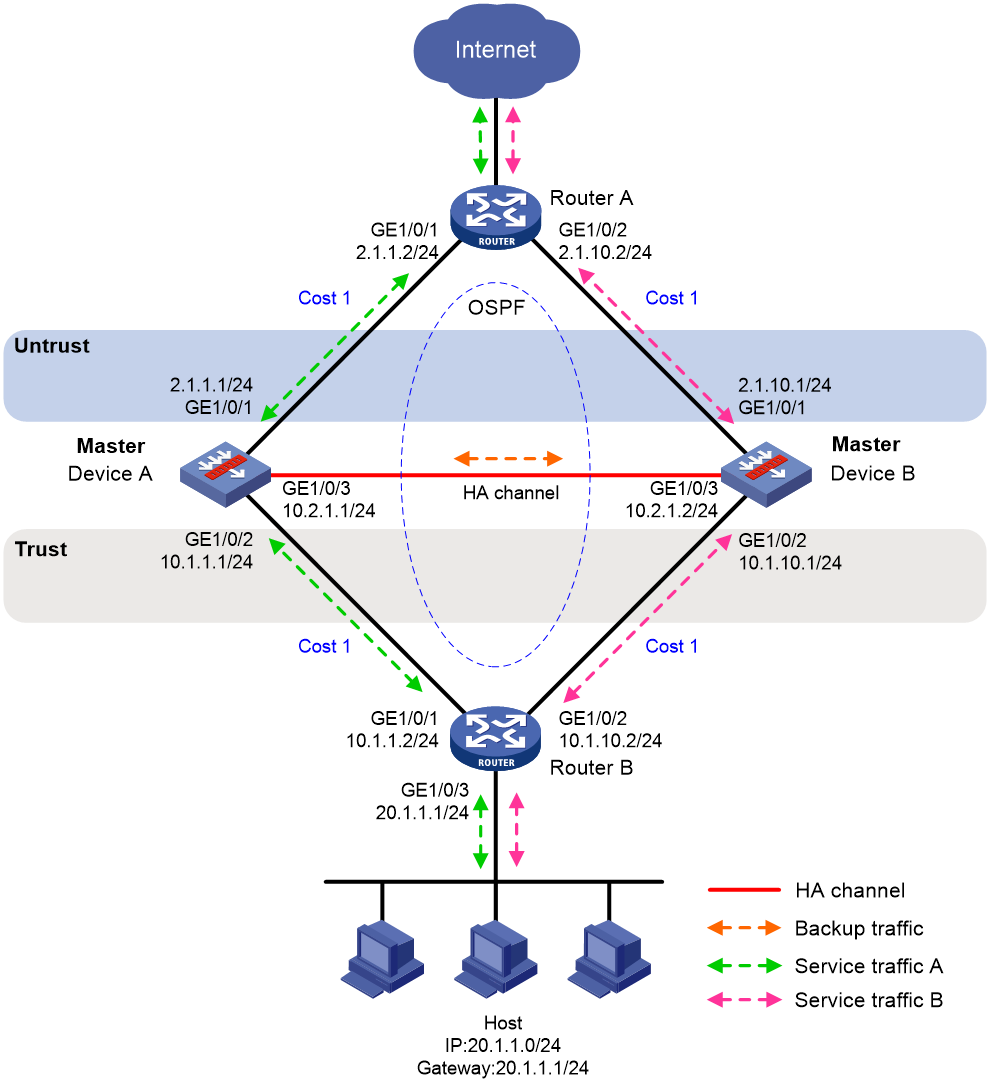
As shown in Figure 19, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with OSPF.
· Configure the HA group to operate in active/standby mode.
· Configure Device A and Device B as the primary device and the secondary device, respectively.
Software versions used
This configuration example was created and verified on F9345 of the F1060 device.
Procedure
Configuring Router A
# Assign 2.1.1.2/24 to GigabitEthernet 1/0/1.
# Assign 2.1.10.2/24 to GigabitEthernet 1/0/2.
# Configure OSPF for Router A to have Layer 3 reachability to other devices.
Configuring Router B
# Assign 10.1.1.2/24 to GigabitEthernet 1/0/1.
# Assign 10.1.10.2/24 to GigabitEthernet 1/0/2.
# Configure OSPF for Router B to have Layer 3 reachability to other devices.
Configuring Device A
Configuring basic network settings
1. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Untrust security zone.
b. On the IPv4 Address tab, enter the IP address and mask of the interface. In this example, enter 2.1.1.1/24.
c. Use the default settings for other parameters.
d. Click OK.
# Add GE 1/0/2 to the Trust security zone and assign 10.1.1.1/24 to it in the same way you configure GE 1/0/1.
# Assign 10.2.1.1/24 to GE 1/0/3 in the same way you configure GE 1/0/1.
2. Configure routing:
This step uses OSPF as an example. You can configure another dynamic routing protocol as needed.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > OSPF.
# Click Create.
# In the dialog box that opens, configure an OSPF instance:
a. Select version OSPFv2.
b. Enter instance name 1.
c. Enter router ID 2.1.1.1.
d. Use the default settings for other parameters.
e. Click OK.
# Click 0 in the Number of OSPF areas column for the created OSPF instance.
# On the OSPF area configuration page that opens, click Create.
# In the dialog box that opens, configure an area:
a. Enter area ID 0.0.0.0.
b. Add subnets 2.1.1.0/24 and 10.1.1.0/24.
c. Use the default settings for other parameters.
d. Click OK.
3. Configure a security policy to permit service traffic:
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Untrust:
a. Enter security policy name Trust-Untrust.
b. Select source zone Trust.
c. Select destination zone Untrust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Enter source IP address 20.1.1.0/24.
g. Use the default settings for other parameters.
h. Click OK.
4. Configure security policies to permit OSPF protocol packets:
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Local:
a. Enter security policy name ospf1.
b. Select source zone Trust.
c. Select destination zone Local.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Local to zone Trust:
a. Enter security policy name ospf2.
b. Select source zone Local.
c. Select destination zone Trust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Untrust to zone Local:
a. Enter security policy name ospf3.
b. Select source zone Untrust.
c. Select destination zone Local.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Local to zone Untrust:
a. Enter security policy name ospf4.
b. Select source zone Local.
c. Select destination zone Untrust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > Track.
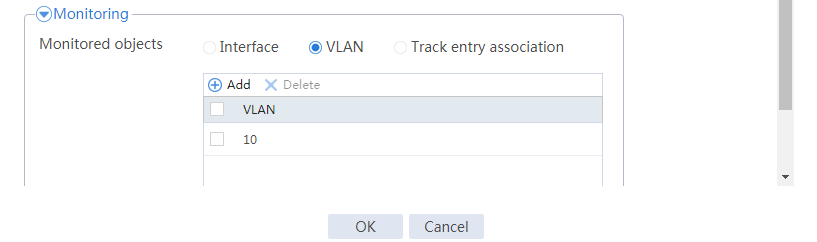
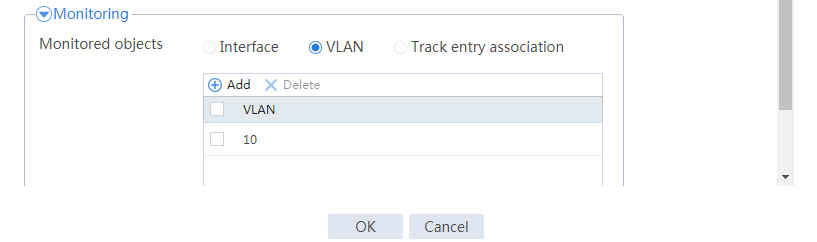
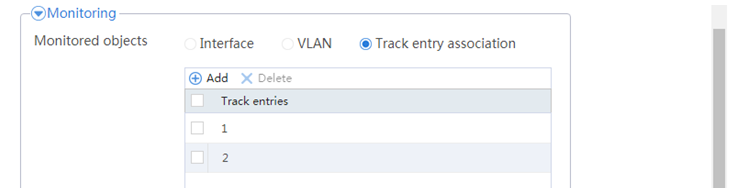
# Click Add.
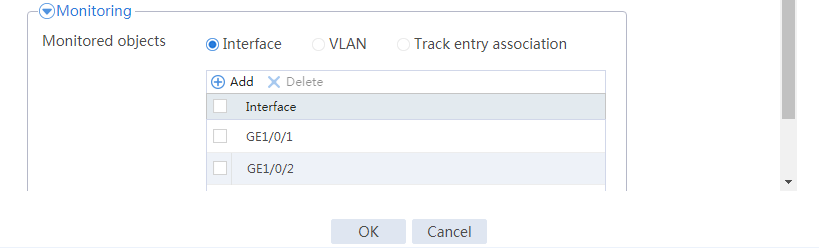
# Configure a track entry:
1. Enter track entry ID 1.
2. Select the interface module.
3. Select GE 1/0/1 as the monitored interface.
4. Use the default settings for other parameters.
# Configure track entry 2 to monitor the state of GE 1/0/2. (Details not shown.)
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
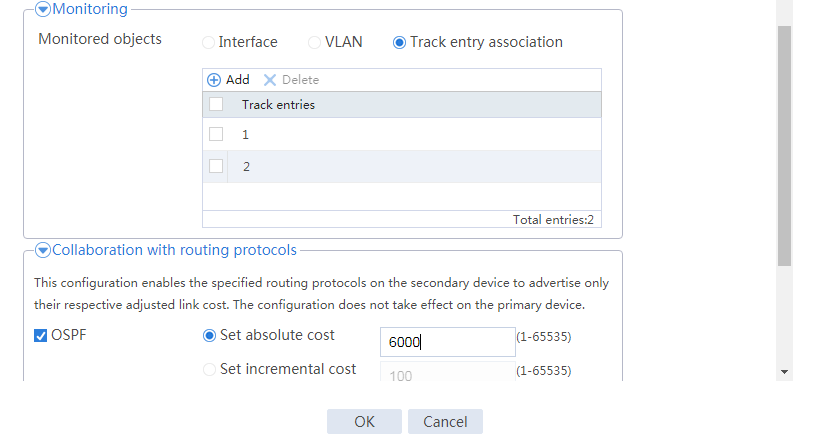
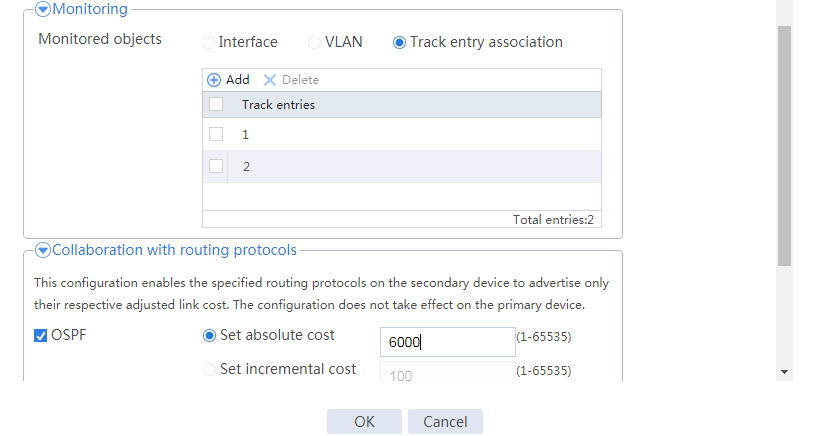
# Configure the HA group parameters as shown in Figure 20.
Figure 20 Configuring HA group parameters
# Click OK.
Configuring security services
# Configure security devices on the HA group member devices. If the HA group can back up configuration for a module, configure the module only on the primary device (Device A).
Configuring Device B
Configuring basic network settings
1. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Untrust security zone.
b. On the IPv4 Address tab, enter the IP address and mask of the interface. In this example, enter 2.1.10.1/24.
c. Use the default settings for other parameters.
d. Click OK.
# Add GE 1/0/2 to the Trust security zone and assign 10.1.10.1/24 to it in the same way you configure GE 1/0/1.
# Assign 10.2.1.2/24 to GE 1/0/3 in the same way you configure GE 1/0/1.
2. Configure routing:
This step uses OSPF as an example. You can configure another dynamic routing protocol as needed.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > OSPF.
# Click Create.
# In the dialog box that opens, configure an OSPF instance:
a. Select version OSPFv2.
b. Enter instance name 1.
c. Enter router ID 2.1.10.1.
d. Use the default settings for other parameters.
e. Click OK.
# Click 0 in the Number of OSPF areas column for the created OSPF instance.
# On the OSPF area configuration page that opens, click Create.
# In the dialog box that opens, configure an area:
a. Enter area ID 0.0.0.0.
b. Add subnets 2.1.10.0/24 and 10.1.10.0/24.
c. Use the default settings for other parameters.
d. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > Track.
# Click Add.
# Configure a track entry:
1. Enter track entry ID 1.
2. Select the interface module.
3. Select GE 1/0/1 as the monitored interface.
4. Use the default settings for other parameters.
# Configure track entry 2 to monitor the state of GE 1/0/2. (Details not shown.)
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
# Configure the HA group parameters as shown in Figure 21.
Figure 21 Configuring HA group parameters
# Click OK.
Configuring the host
# On the host, specify 20.1.1.1 as the default gateway.
Verifying the configuration
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that only Device A generates log messages when the host communicates with the Internet.
Example: Configuring the HA group in dual-active mode in collaboration with a routing protocol (IPv4)
Network configuration
As shown in Figure 22, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with OSPF.
· Configure the HA group to operate in dual-active mode.
· Configure Device A and Device B to load share traffic.
Software versions used
This configuration example was created and verified on F9345 of the F1060 device.
Procedure
Configuring Router A
# Assign 2.1.1.2/24 to GigabitEthernet 1/0/1.
# Assign 2.1.10.2/24 to GigabitEthernet 1/0/2.
# Configure OSPF for Router A to have Layer 3 reachability to other devices.
# Configure per-flow load sharing for IP forwarding.
Configuring Router B
# Assign 10.1.1.2/24 to GigabitEthernet 1/0/1.
# Assign 10.1.10.2/24 to GigabitEthernet 1/0/2.
# Configure OSPF for Router B to have Layer 3 reachability to other devices.
# Configure per-flow load sharing for IP forwarding.
Configuring Device A
Configuring basic network settings
1. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Untrust security zone.
b. On the IPv4 Address tab, enter the IP address and mask of the interface. In this example, enter 2.1.1.1/24.
c. Use the default settings for other parameters.
d. Click OK.
# Add GE 1/0/2 to the Trust security zone and assign 10.1.1.1/24 to it in the same way you configure GE 1/0/1.
# Assign 10.2.1.1/24 to GE 1/0/3 in the same way you configure GE 1/0/1.
2. Configure routing:
This step uses OSPF as an example. You can configure another dynamic routing protocol as needed.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > OSPF.
# Click Create.
# In the dialog box that opens, configure an OSPF instance:
a. Select version OSPFv2.
b. Enter instance name 1.
c. Enter router ID 2.1.1.1.
d. Use the default settings for other parameters.
e. Click OK.
# Click 0 in the Number of OSPF areas column for the created OSPF instance.
# On the OSPF area configuration page that opens, click Create.
# In the dialog box that opens, configure an area:
a. Enter area ID 0.0.0.0.
b. Add subnets 2.1.1.0/24 and 10.1.1.0/24.
c. Use the default settings for other parameters.
d. Click OK.
3. Configure a security policy to permit service traffic:
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Untrust:
a. Enter security policy name Trust-Untrust.
b. Select source zone Trust.
c. Select destination zone Untrust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Enter source IP address 20.1.1.0/24.
g. Use the default settings for other parameters.
h. Click OK.
4. Configure security policies to permit OSPF protocol packets:
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Local:
a. Enter security policy name ospf1.
b. Select source zone Trust.
c. Select destination zone Local.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Local to zone Trust:
a. Enter security policy name ospf2.
b. Select source zone Local.
c. Select destination zone Trust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Untrust to zone Local:
a. Enter security policy name ospf3.
b. Select source zone Untrust.
c. Select destination zone Local.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Local to zone Untrust:
a. Enter security policy name ospf4.
b. Select source zone Local.
c. Select destination zone Untrust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > Track.
# Click Add.
# Configure a track entry:
1. Enter track entry ID 1.
2. Select the interface module.
3. Select GE 1/0/1 as the monitored interface.
4. Use the default settings for other parameters.
# Configure track entry 2 to monitor the state of GE 1/0/2. (Details not shown.)
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
# Configure the HA group parameters as shown in Figure 23.
Figure 23 Configuring HA group parameters
# Click OK.
Configuring security services
# Configure security devices on the HA group member devices. If the HA group can back up configuration for a module, configure the module only on the primary device (Device A).
Configuring Device B
Configuring basic network settings
1. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Untrust security zone.
b. On the IPv4 Address tab, enter the IP address and mask of the interface. In this example, enter 2.1.10.1/24.
c. Use the default settings for other parameters.
d. Click OK.
# Add GE 1/0/2 to the Trust security zone and assign 10.1.10.1/24 to it in the same way you configure GE 1/0/1.
# Assign 10.2.1.2/24 to GE 1/0/3 in the same way you configure GE 1/0/1.
2. Configure routing:
This step uses OSPF as an example. You can configure another dynamic routing protocol as needed.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > OSPF.
# Click Create.
# In the dialog box that opens, configure an OSPF instance:
a. Select version OSPFv2.
b. Enter instance name 1.
c. Enter router ID 2.1.10.1.
d. Use the default settings for other parameters.
e. Click OK.
# Click 0 in the Number of OSPF areas column for the created OSPF instance.
# On the OSPF area configuration page that opens, click Create.
# In the dialog box that opens, configure an area:
a. Enter area ID 0.0.0.0.
b. Add subnets 2.1.10.0/24 and 10.1.10.0/24.
c. Use the default settings for other parameters.
d. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > Track.
# Click Add.
# Configure a track entry:
1. Enter track entry ID 1.
2. Select the interface module.
3. Select GE 1/0/1 as the monitored interface.
4. Use the default settings for other parameters.
# Configure track entry 2 to monitor the state of GE 1/0/2. (Details not shown.)
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
# Configure the HA group parameters as shown in Figure 24.
Figure 24 Configuring HA group parameters
# Click OK.
Configuring the hosts
# On the hosts, specify 20.1.1.1 as the default gateway.
Verifying the configuration
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that both Device A and Device B generate log messages when the hosts communicate with the Internet.
Network configuration
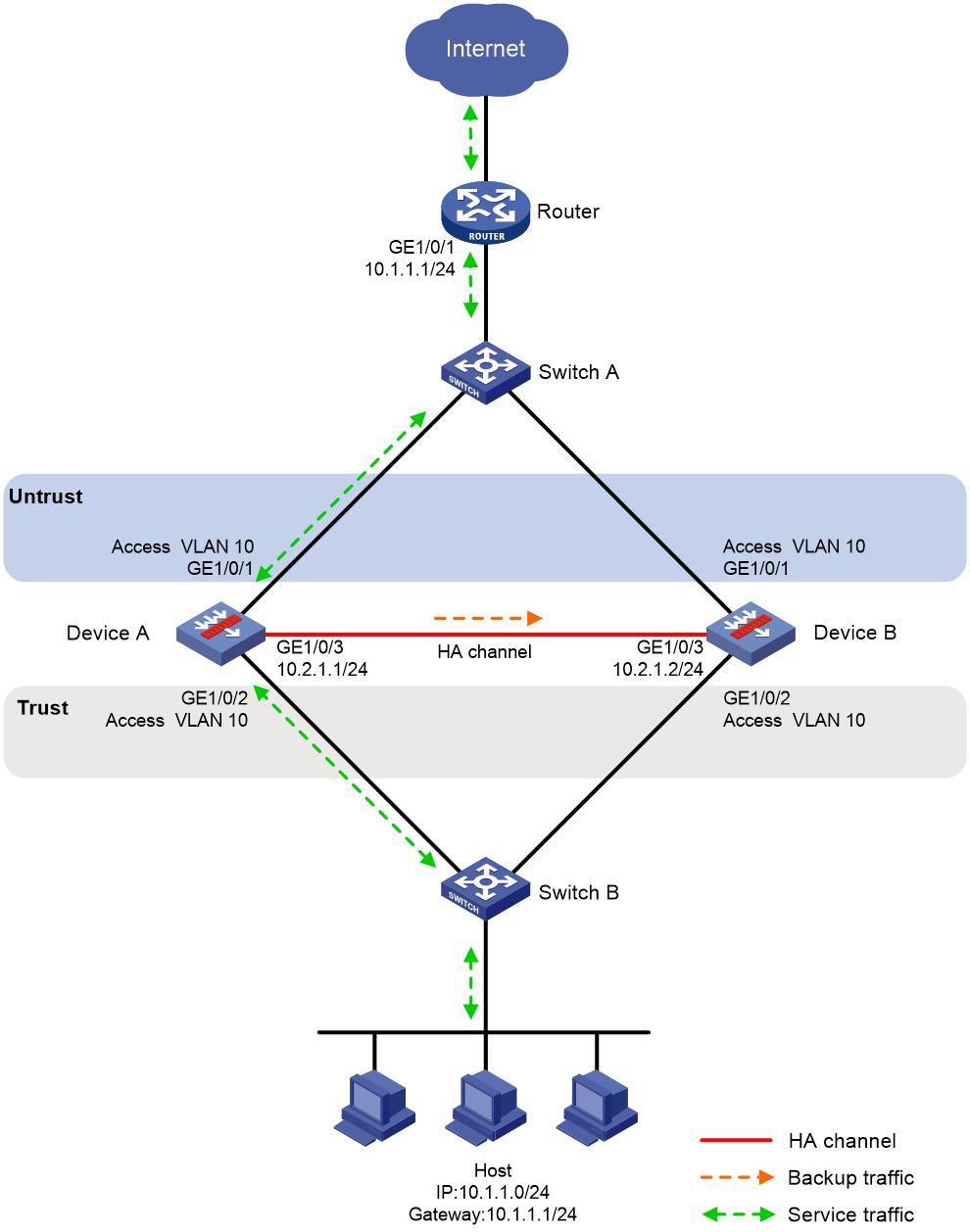
As shown in Figure 25, set up a transparent in-path HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to operate in active/standby mode.
· Connect Switch A and Switch B to Layer 2 interfaces of the HA group.
· Configure Device A and Device B as the primary device and the secondary device, respectively.
Software versions used
This configuration example was created and verified on F9345 of the F1060 device.
Procedure
Configuring Switch A
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the router to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
Configuring Switch B
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the host to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
Configuring Device A
Configuring basic network settings
1. Configure Layer 2 service interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Link > VLANs.
# Click Create.
a. Enter VLAN ID 10.
b. Click OK.
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. Select the Layer 2 link mode.
b. Select security zone Untrust.
c. On the VLAN tab, set the link type to Access and enter PVID 10.
d. Use the default settings for other parameters.
e. Click OK.
# Click the Edit icon for GE 1/0/2.
# In the dialog box that opens, configure the interface:
a. Select the Layer 2 link mode.
b. Select security zone Trust.
c. On the VLAN tab, set the link type to Access and enter PVID 10.
d. Use the default settings for other parameters.
e. Click OK.
2. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/3.
# In the dialog box that opens, configure the interface:
a. On the IPv4 Address tab, enter the IP address and mask of the interface. In this example, enter 10.2.1.1/24.
b. Use the default settings for other parameters.
c. Click OK.
3. Configure a security policy to permit service traffic:
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Untrust:
a. Enter security policy name Trust-Untrust.
b. Select source zone Trust.
c. Select destination zone Untrust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Enter source IP address 10.1.1.0/24.
g. Use the default settings for other parameters.
h. Click OK.
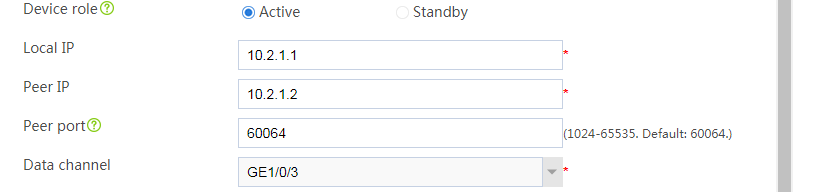
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
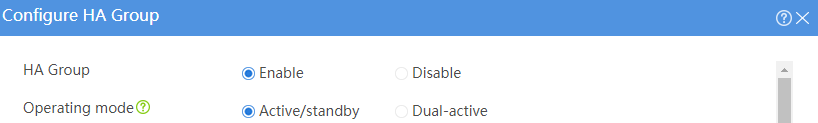
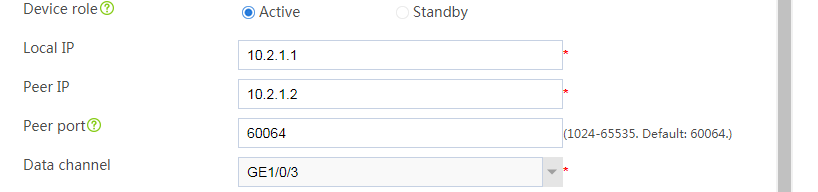
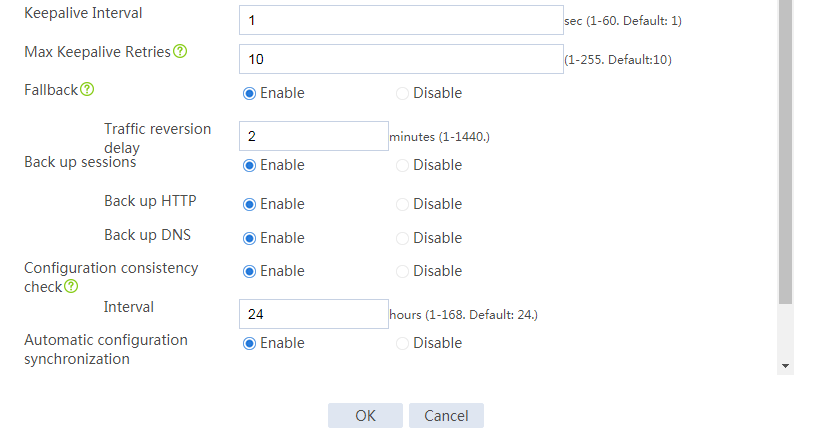
# Configure the HA group parameters as shown in Figure 26.
Figure 26 Configuring HA group parameters
# Click OK.
Configuring security services
# Configure security devices on the HA group member devices. If the HA group can back up configuration for a module, configure the module only on the primary device (Device A).
Configuring Device B
Configuring basic network settings
1. Configure Layer 2 service interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Link > VLANs.
# Click Create.
a. Enter VLAN ID 10.
b. Click OK.
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. Select the Layer 2 link mode.
b. Select security zone Untrust.
c. On the VLAN tab, set the link type to Access and enter PVID 10.
d. Use the default settings for other parameters.
e. Click OK.
# Click the Edit icon for GE 1/0/2.
# In the dialog box that opens, configure the interface:
a. Select the Layer 2 link mode.
b. Select security zone Trust.
c. On the VLAN tab, set the link type to Access and enter PVID 10.
d. Use the default settings for other parameters.
e. Click OK.
2. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/3.
# In the dialog box that opens, configure the interface:
a. On the IPv4 Address tab, enter the IP address and mask of the interface. In this example, enter 10.2.1.2/24.
b. Use the default settings for other parameters.
c. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
# Configure the HA group parameters as shown in Figure 27.
Figure 27 Configuring HA group parameters
# Click OK.
Configuring the host
# On the host, specify 10.1.1.1 as the default gateway.
Verifying the configuration
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that only Device A generates log messages when the host communicates with the Internet.
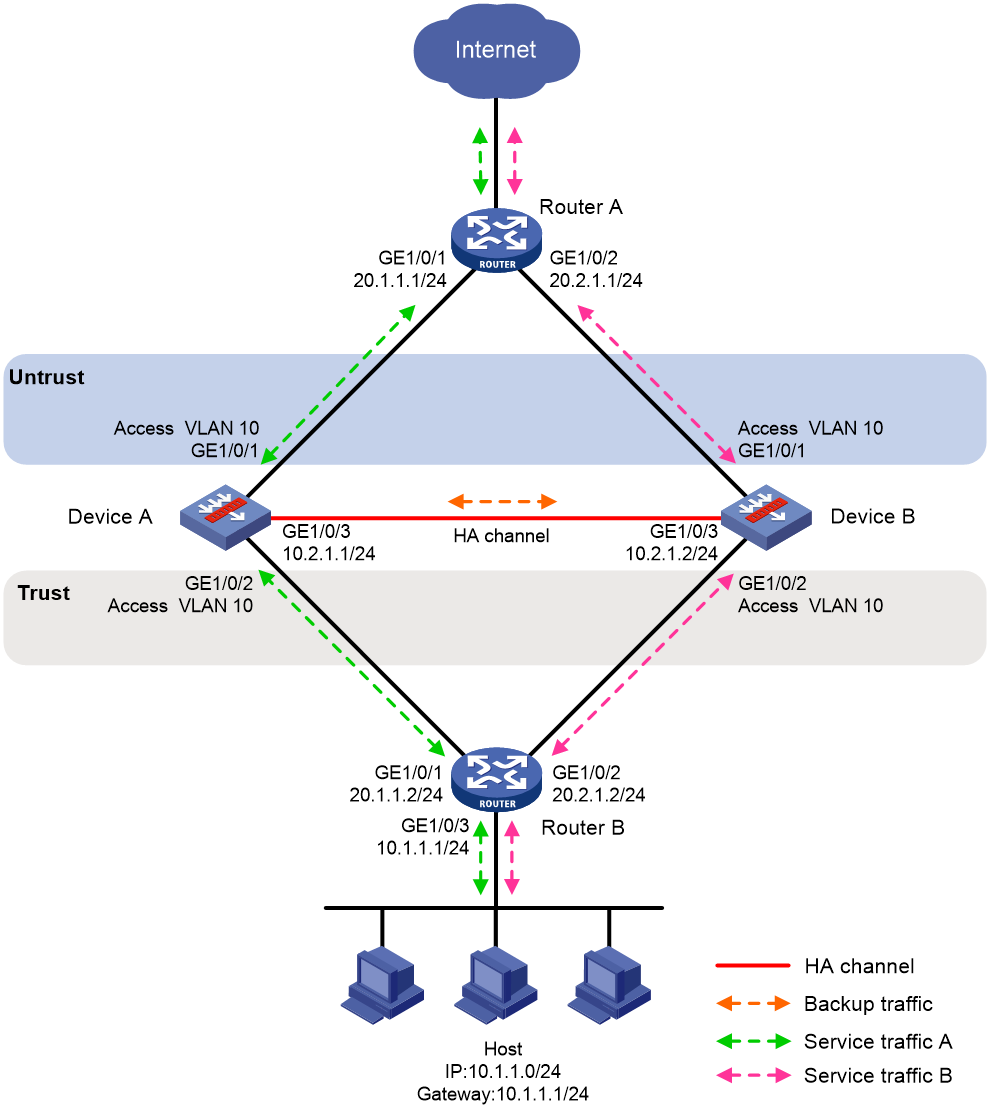
Network configuration
As shown in Figure 28, set up a transparent in-path HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to operate in dual-active mode.
· Connect Router A and Router B to Layer 2 interfaces of the HA group.
· Configure Device A and Device B to load share traffic.
Software versions used
This configuration example was created and verified on F9345 of the F1060 device.
Procedure
Configuring Router A
# Configure OSPF for the hosts to access the Internet and for Device A and Device B to load share the traffic sent to the hosts.
Configuring Router B
# Configure OSPF for the hosts to access the Internet and for Device A and Device B to load share the traffic sent to the hosts.
Configuring Device A
Configuring basic network settings
1. Configure Layer 2 service interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Link > VLANs.
# Click Create.
a. Enter VLAN ID 10.
b. Click OK.
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. Select the Layer 2 link mode.
b. Select security zone Untrust.
c. On the VLAN tab, set the link type to Access and enter PVID 10.
d. Use the default settings for other parameters.
e. Click OK.
# Click the Edit icon for GE 1/0/2.
# In the dialog box that opens, configure the interface:
a. Select the Layer 2 link mode.
b. Select security zone Trust.
c. On the VLAN tab, set the link type to Access and enter PVID 10.
d. Use the default settings for other parameters.
e. Click OK.
2. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/3.
# In the dialog box that opens, configure the interface:
a. On the IPv4 Address tab, enter the IP address and mask of the interface. In this example, enter 10.2.1.1/24.
b. Use the default settings for other parameters.
c. Click OK.
3. Configure a security policy to permit service traffic:
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Untrust:
a. Enter security policy name Trust-Untrust.
b. Select source zone Trust.
c. Select destination zone Untrust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Enter source IP address 10.1.1.0/24.
g. Use the default settings for other parameters.
h. Click OK.
4. Configure security policies to permit OSPF protocol packets:
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Untrust:
a. Enter security policy name ospf1.
b. Select source zone Untrust.
c. Select destination zone Local.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Untrust to zone Trust:
a. Enter security policy name ospf2.
b. Select source zone Untrust.
c. Select destination zone Trust.
d. Select IP version IPv4.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
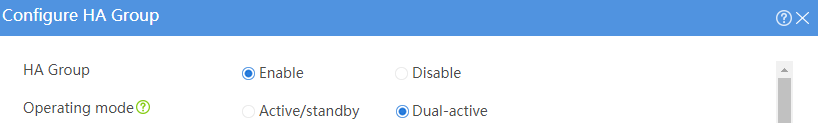
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
# Configure the HA group parameters as shown in Figure 29.
Figure 29 Configuring HA group parameters
# Click OK.
Configuring security services
# Configure security devices on the HA group member devices. If the HA group can back up configuration for a module, configure the module only on the primary device (Device A).
Configuring Device B
Configuring basic network settings
1. Configure Layer 2 service interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Link > VLANs.
# Click Create.
a. Enter VLAN ID 10.
b. Click OK.
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. Select the Layer 2 link mode.
b. Select security zone Untrust.
c. On the VLAN tab, set the link type to Access and enter PVID 10.
d. Use the default settings for other parameters.
e. Click OK.
# Click the Edit icon for GE 1/0/2.
# In the dialog box that opens, configure the interface:
a. Select the Layer 2 link mode.
b. Select security zone Trust.
c. On the VLAN tab, set the link type to Access and enter PVID 10.
d. Use the default settings for other parameters.
e. Click OK.
2. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/3.
# In the dialog box that opens, configure the interface:
a. On the IPv4 Address tab, enter the IP address and mask of the interface. In this example, enter 10.2.1.2/24.
b. Use the default settings for other parameters.
c. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
# Configure the HA group parameters as shown in Figure 30.
Figure 30 Configuring HA group parameters
# Click OK.
Configuring the hosts
# On the hosts, specify 10.1.1.1 as the default gateway.
Verifying the configuration
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that both Device A and Device B generate log messages when the hosts communicate with the Internet.
Network configuration
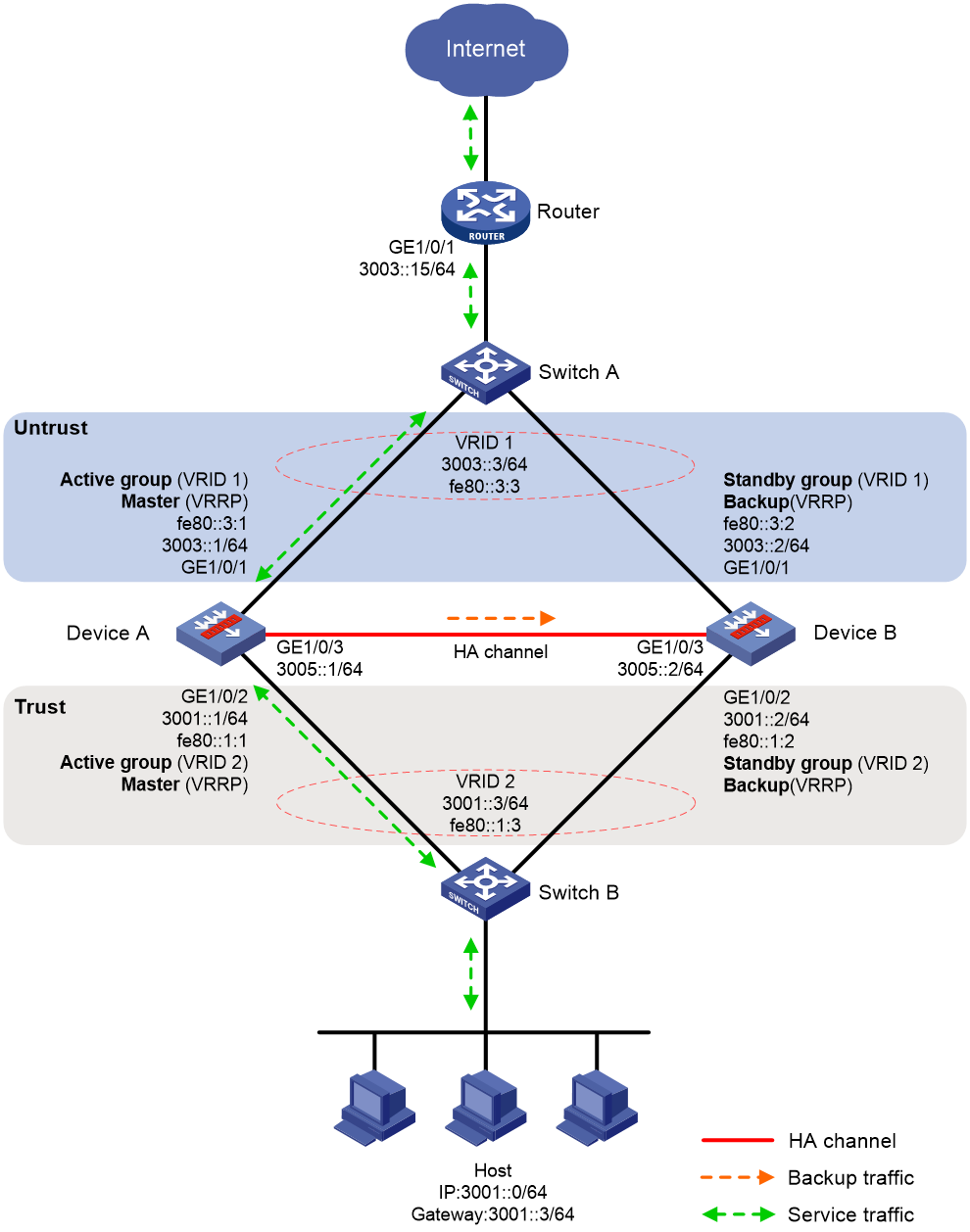
As shown in Figure 31, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with VRRP.
· Configure the HA group to operate in active/standby mode.
· Configure Device A and Device B as the primary device and the secondary device, respectively.
Software versions used
This configuration example was created and verified on F9345 of the F1060 device.
Procedure
Configuring Switch A
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the router to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
Configuring Switch B
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the host to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
Configuring the router
# Assign 3003::15/64 to GigabitEthernet 1/0/1.
# Configure routes as follows:
· Specify 3003::3/64 (virtual IP address of VRRP group 1) as the next hop of the routes to the internal network.
· Specify the IP address of the peer interface attached to the traffic outgoing interface as the next hop of the route to the Internet.
Configuring Device A
Configuring basic network settings
1. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Untrust security zone.
b. On the IPv6 Address tab, enter global unicast address 3003::1/64 and link local address fe80::3:1.
c. Use the default settings for other parameters.
d. Click OK.
# Click the Edit icon for GE 1/0/2.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Trust security zone.
b. On the IPv6 Address tab, enter global unicast address 3001::1/64 and link local address fe80::1:1.
c. Use the default settings for other parameters.
d. Click OK.
# Click the Edit icon for GE 1/0/3.
# In the dialog box that opens, configure the interface:
a. On the IPv6 Address tab, enter global unicast address 3005::1/64 and configure the interface to use a link local address generated automatically.
b. Use the default settings for other parameters.
c. Click OK.
2. Configure routing:
This step uses static routing as an example. To use dynamic routing, configure a dynamic routing protocol.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > Static Routing.
# On the IPv6 Static Routing tab, click Create.
# In the dialog box that opens, configure an IPv6 static route:
a. Enter destination IP address 0::0.
b. Enter mask length 0.
c. Enter next hop address 3003::15.
d. Use the default settings for other parameters.
e. Click OK.
3. Configure a security policy to permit service traffic:
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Untrust:
a. Enter security policy name Trust-Untrust.
b. Select source zone Trust.
c. Select destination zone Untrust.
d. Select IP version IPv6.
e. Set the action to Permit.
f. Enter source IP address 3001::0/64.
g. Use the default settings for other parameters.
h. Click OK.
4. Configure security policies to permit VRRP protocol packets:
This task allows Device A and Device B to exchange VRRP packets and elect a VRRP master when the HA channels are disconnected.
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Local:
a. Enter security policy name vrrp1.
b. Select source zone Trust.
c. Select destination zone Local.
d. Select IP version IPv6.
e. Set the action to Permit.
f. Select policy group vrrp.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Local to zone Trust:
a. Enter security policy name vrrp2.
b. Select source zone Local.
c. Select destination zone Trust.
d. Select IP version IPv6.
e. Set the action to Permit.
f. Select policy group vrrp.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Untrust to zone Local:
a. Enter security policy name vrrp3.
b. Select source zone Untrust.
c. Select destination zone Local.
d. Select IP version IPv6.
e. Set the action to Permit.
f. Select policy group vrrp.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Local to zone Untrust:
a. Enter security policy name vrrp4.
b. Select source zone Local.
c. Select destination zone Untrust.
d. Select IP version IPv6.
e. Set the action to Permit.
f. Select policy group vrrp.
g. Use the default settings for other parameters.
h. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
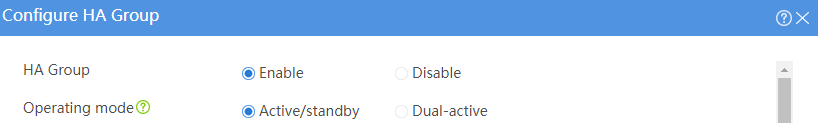
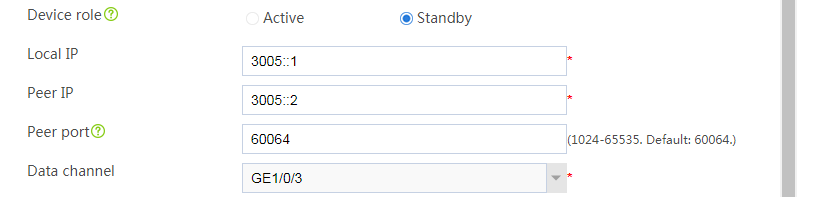
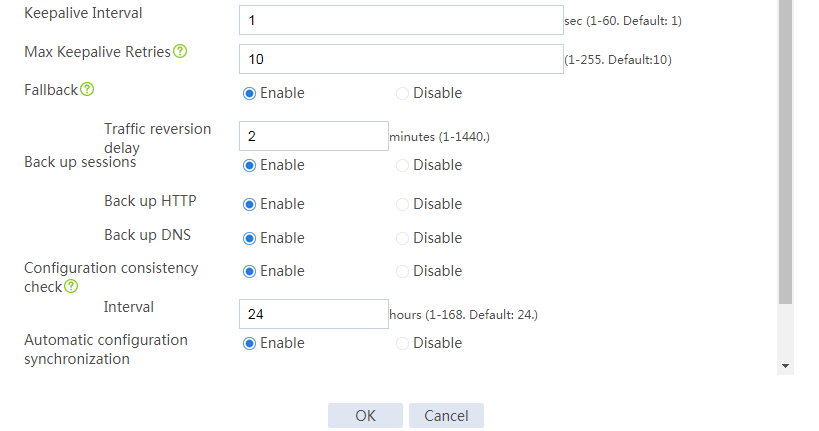
# Configure the HA group parameters as shown in Figure 32.
Figure 32 Configuring HA group parameters
# Click OK.
Associating the HA group with VRRP
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > VRRP.
# Click Create.
# Configure VRRP groups as shown in the follow figures.
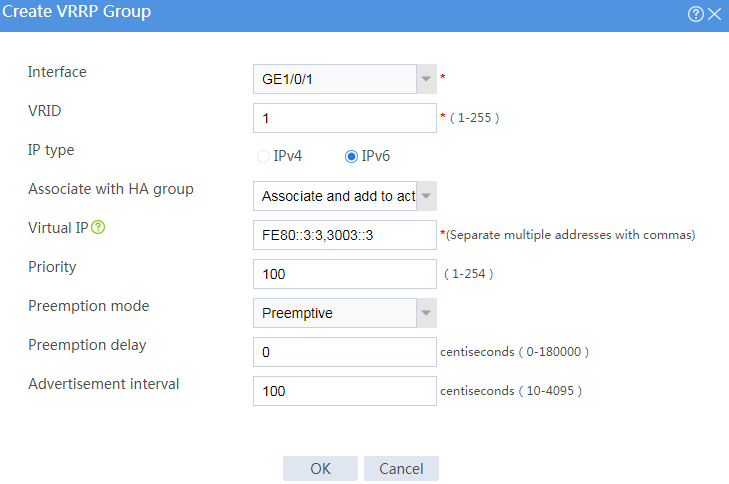
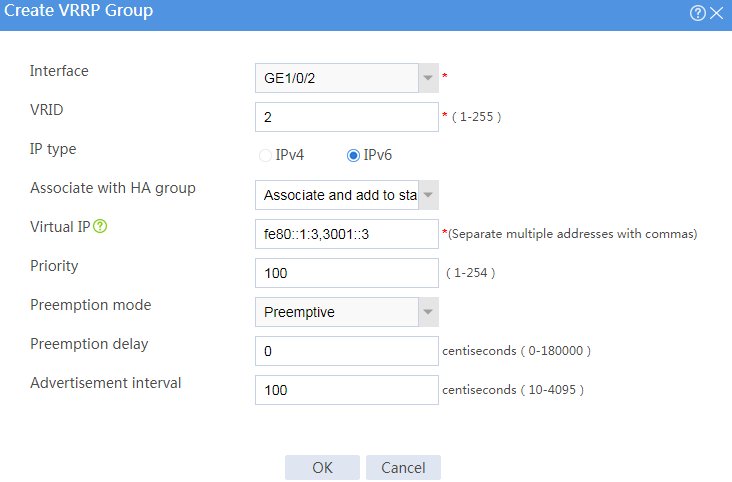
Figure 33 Creating VRRP group 1
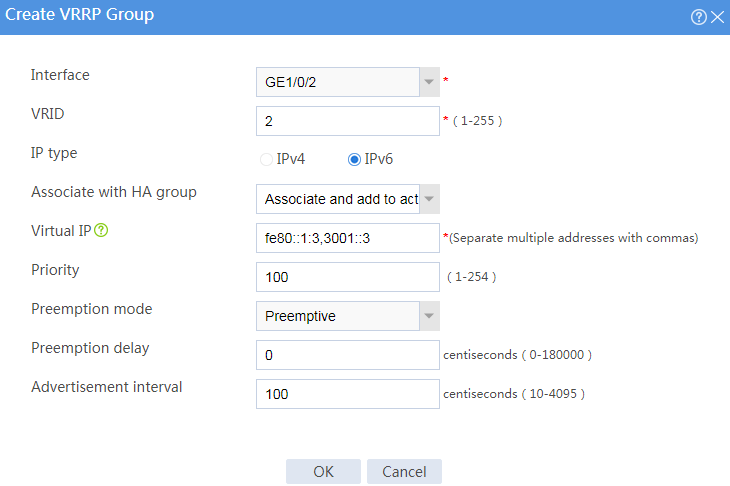
Figure 34 Creating VRRP group 2
# Click OK.
Configuring security services
# Configure security devices on the HA group member devices. If the HA group can back up configuration for a module, configure the module only on the primary device (Device A).
Configuring Device B
Configuring basic network settings
1. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Untrust security zone.
b. On the IPv6 Address tab, enter global unicast address 3003::2/64 and link local address fe80::3:2.
c. Use the default settings for other parameters.
d. Click OK.
# Click the Edit icon for GE 1/0/2.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Trust security zone.
b. On the IPv6 Address tab, enter global unicast address 3001::2/64 and link local address fe80::1:2.
c. Use the default settings for other parameters.
d. Click OK.
# Click the Edit icon for GE 1/0/3.
# In the dialog box that opens, configure the interface:
a. On the IPv6 Address tab, enter global unicast address 3005::2/64 and configure the interface to use a link local address generated automatically.
b. Use the default settings for other parameters.
c. Click OK.
2. Configure routing:
This step uses static routing as an example. To use dynamic routing, configure a dynamic routing protocol.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > Static Routing.
# On the IPv6 Static Routing tab, click Create.
# In the dialog box that opens, configure an IPv6 static route:
a. Enter destination IP address 0::0.
b. Enter mask length 0.
c. Enter next hop address 3003::15.
d. Use the default settings for other parameters.
e. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
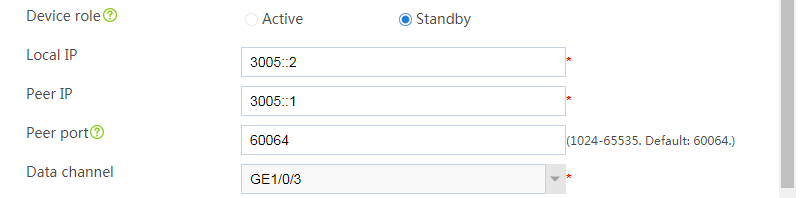
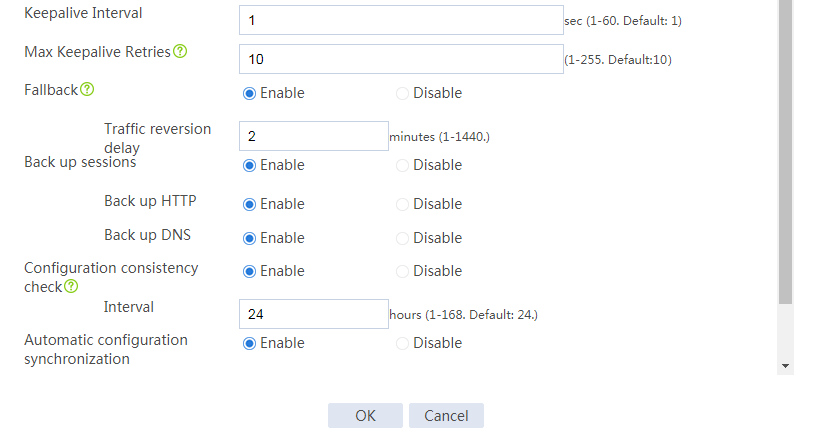
# Configure the HA group parameters as shown in Figure 35.
Figure 35 Configuring HA group parameters
# Click OK.
Associating the HA group with VRRP
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > VRRP.
# Click Create.
# Configure VRRP groups as shown in the follow figures.
Figure 36 Creating VRRP group 1
Figure 37 Creating VRRP group 2
# Click OK.
Configuring the host
# On the host, specify 3001::3 (virtual IP address of VRRP group 2) as the default gateway.
Verifying the configuration
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that only Device A generates log messages when the host communicates with the Internet.
Example: Configuring the HA group in dual-active mode in collaboration with a routing protocol (IPv6)
Network configuration
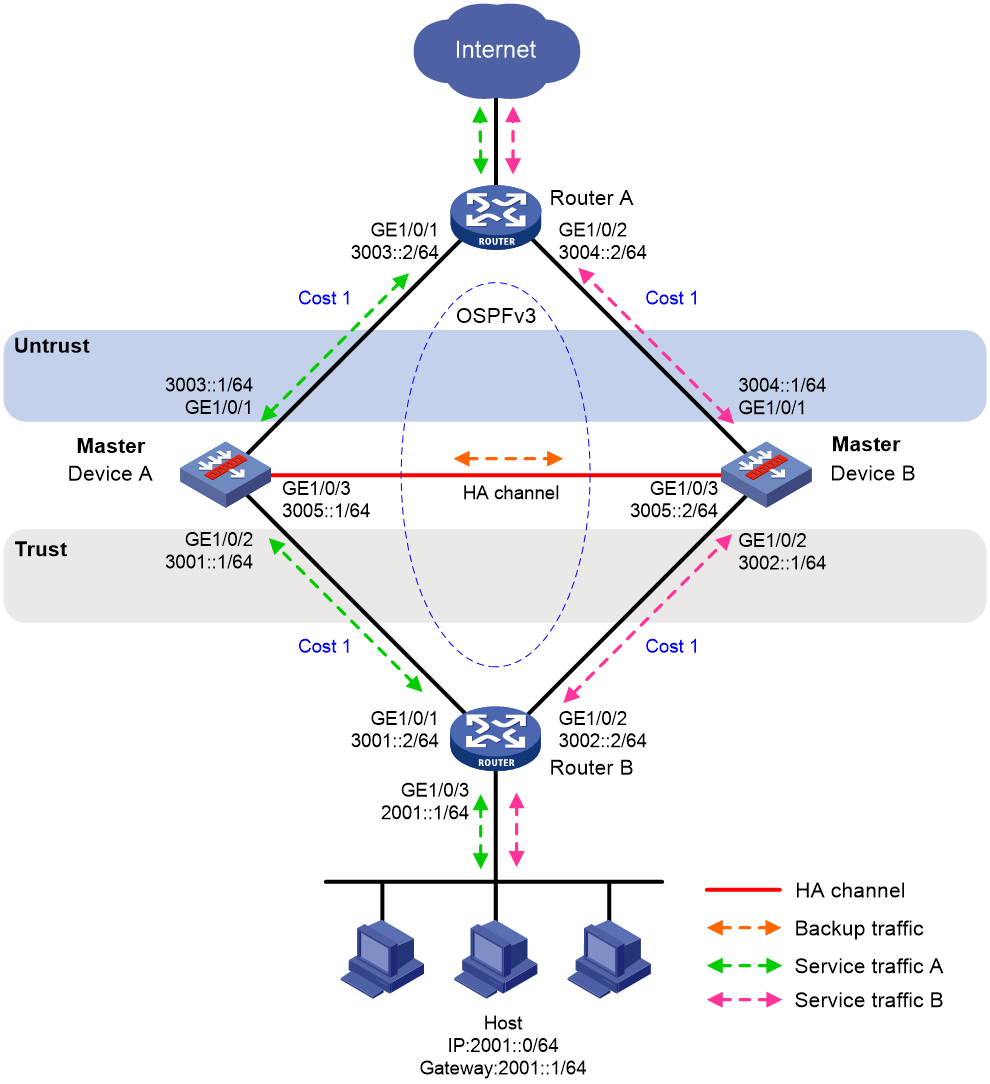
As shown in Figure 38, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with OSPFv3.
· Configure the HA group to operate in dual-active mode.
· Configure Device A and Device B to load share traffic.
Software versions used
This configuration example was created and verified on F9345 of the F1060 device.
Procedure
Configuring Router A
# Assign 3003::2/64 to GigabitEthernet 1/0/1.
# Assign 3004::2/64 to GigabitEthernet 1/0/2.
# Configure OSPFv3 for Router A to have Layer 3 reachability to other devices.
# Configure per-flow load sharing for IP forwarding.
Configuring Router B
# Assign 3001::2/64 to GigabitEthernet 1/0/1.
# Assign 3002::2/64 to GigabitEthernet 1/0/2.
# Configure OSPFv3 for Router B to have Layer 3 reachability to other devices.
# Configure per-flow load sharing for IP forwarding.
Configuring Device A
Configuring basic network settings
1. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Untrust security zone.
b. On the IPv6 Address tab, enter global unicast address 3003::1/64 and configure the interface to use a link local address generated automatically.
c. Use the default settings for other parameters.
d. Click OK.
# Click the Edit icon for GE 1/0/2.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Trust security zone.
b. On the IPv6 Address tab, enter global unicast address 3001::1/64 and configure the interface to use a link local address generated automatically.
c. Use the default settings for other parameters.
d. Click OK.
# Click the Edit icon for GE 1/0/3.
# In the dialog box that opens, configure the interface:
a. On the IPv6 Address tab, enter global unicast address 3005::1/64 and configure the interface to use a link local address generated automatically.
b. Use the default settings for other parameters.
c. Click OK.
2. Configure routing:
This step uses OSPF as an example. You can configure another dynamic routing protocol as needed.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > OSPF.
# Click Create.
# In the dialog box that opens, configure an OSPF instance:
a. Select version OSPFv3.
b. Enter instance name 1.
c. Enter router ID 2.1.1.1.
d. Use the default settings for other parameters.
e. Click OK.
# Click 0 in the Number of OSPF areas column for the created OSPF instance.
# On the OSPF area configuration page that opens, click Create.
# In the dialog box that opens, configure an area:
a. Enter area ID 0.0.0.0.
b. Click OK.
# Click 0 in the Number of OSPF interfaces column for the created OSPF instance.
# On the OSPF interface configuration page that opens, click Create.
# In the dialog box that opens, configure an area:
a. Enter area ID 0.0.0.0.
b. Select interface GE 1/0/1.
c. Enter interface instance ID 1.
d. Click OK.
# Click 1 in the Number of OSPF interfaces column for the created OSPF instance.
# On the OSPF interface configuration page that opens, click Create.
# In the dialog box that opens, configure an area:
a. Enter area ID 0.0.0.0.
b. Select interface GE 1/0/2.
c. Enter interface instance ID 1.
d. Click OK.
3. Configure a security policy to permit service traffic:
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Untrust:
a. Enter security policy name Trust-Untrust.
b. Select source zone Trust.
c. Select destination zone Untrust.
d. Select IP version IPv6.
e. Set the action to Permit.
f. Enter source IP address 2001::0/64.
g. Use the default settings for other parameters.
h. Click OK.
4. Configure security policies to permit OSPF protocol packets:
Perform this task only on the primary device. The secondary device will synchronize security policy configuration with the primary device after the HA group is set up.
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Select Create > Create a policy.
# In the dialog box that opens, configure a security policy to permit traffic from zone Trust to zone Local:
a. Enter security policy name ospf1.
b. Select source zone Trust.
c. Select destination zone Local.
d. Select IP version IPv6.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Local to zone Trust:
a. Enter security policy name ospf2.
b. Select source zone Local.
c. Select destination zone Trust.
d. Select IP version IPv6.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Untrust to zone Local:
a. Enter security policy name ospf3.
b. Select source zone Untrust.
c. Select destination zone Local.
d. Select IP version IPv6.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
# Configure a security policy to permit traffic from zone Local to zone Untrust:
a. Enter security policy name ospf4.
b. Select source zone Local.
c. Select destination zone Untrust.
d. Select IP version IPv6.
e. Set the action to Permit.
f. Select policy group ospf.
g. Use the default settings for other parameters.
h. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > Track.
# Click Add.
# Configure a track entry:
1. Enter track entry ID 1.
2. Select the interface module.
3. Select GE 1/0/1 as the monitored interface.
4. Use the default settings for other parameters.
# Configure track entry 2 to monitor the state of GE 1/0/2. (Details not shown.)
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
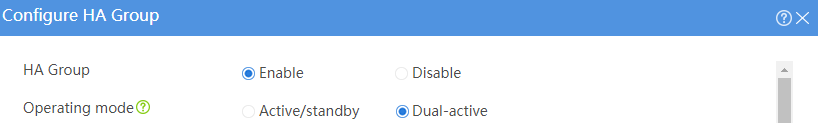
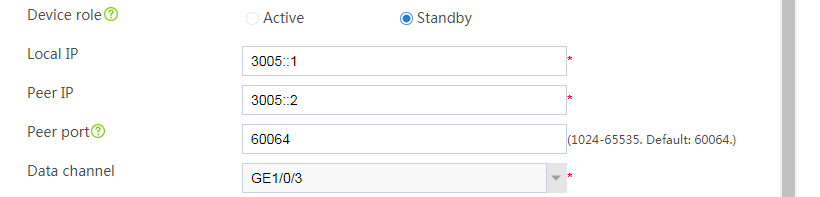
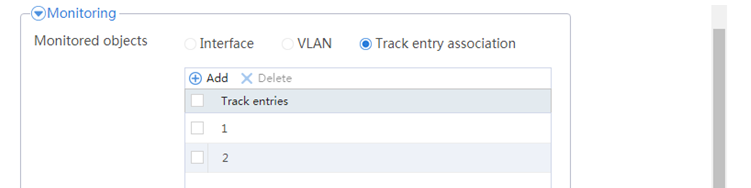
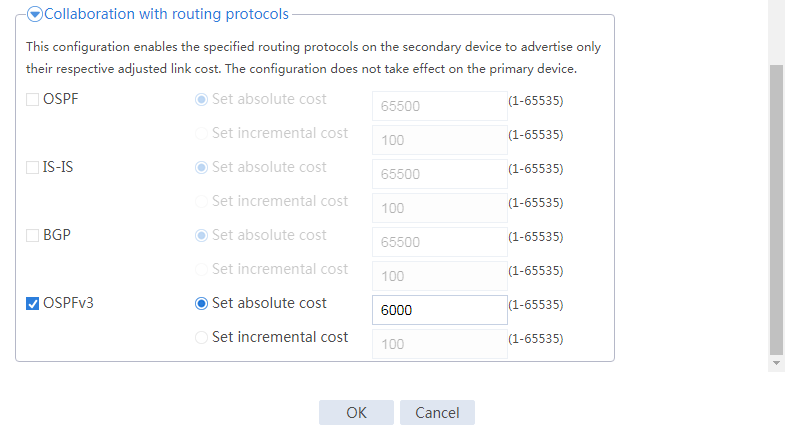
# Configure the HA group parameters as shown in Figure 39.
Figure 39 Configuring HA group parameters
# Click OK.
Configuring security services
# Configure security devices on the HA group member devices. If the HA group can back up configuration for a module, configure the module only on the primary device (Device A).
Configuring Device B
Configuring basic network settings
1. Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Untrust security zone.
b. On the IPv6 Address tab, enter global unicast address 3002::1/64 and configure the interface to use a link local address generated automatically.
c. Use the default settings for other parameters.
d. Click OK.
# Click the Edit icon for GE 1/0/2.
# In the dialog box that opens, configure the interface:
a. On the Basic Configuration tab, select the Trust security zone.
b. On the IPv6 Address tab, enter global unicast address 3004::1/64 and configure the interface to use a link local address generated automatically.
c. Use the default settings for other parameters.
d. Click OK.
# Click the Edit icon for GE 1/0/3.
# In the dialog box that opens, configure the interface:
a. On the IPv6 Address tab, enter global unicast address 3005::2/64 and configure the interface to use a link local address generated automatically.
b. Use the default settings for other parameters.
c. Click OK.
2. Configure routing:
This step uses OSPF as an example. You can configure another dynamic routing protocol as needed.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > OSPF.
# Click Create.
# In the dialog box that opens, configure an OSPF instance:
a. Select version OSPFv3.
b. Enter instance name 1.
c. Enter router ID 2.1.10.1.
d. Use the default settings for other parameters.
e. Click OK.
# Click 0 in the Number of OSPF areas column for the created OSPF instance.
# On the OSPF area configuration page that opens, click Create.
# In the dialog box that opens, configure an area:
a. Enter area ID 0.0.0.0.
b. Click OK.
# Click 0 in the Number of OSPF interfaces column for the created OSPF instance.
# On the OSPF interface configuration page that opens, click Create.
# In the dialog box that opens, configure an area:
a. Enter area ID 0.0.0.0.
b. Select interface GE 1/0/1.
c. Enter interface instance ID 1.
d. Click OK.
# Click 1 in the Number of OSPF interfaces column for the created OSPF instance.
# On the OSPF interface configuration page that opens, click Create.
# In the dialog box that opens, configure an area:
a. Enter area ID 0.0.0.0.
b. Select interface GE 1/0/2.
c. Enter interface instance ID 1.
d. Click OK.
Configuring HA group settings
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > Track.
# Click Add.
# Configure a track entry:
1. Enter track entry ID 1.
2. Select the interface module.
3. Select GE 1/0/1 as the monitored interface.
4. Use the default settings for other parameters.
# Configure track entry 2 to monitor the state of GE 1/0/2. (Details not shown.)
# On the top navigation bar, click System.
# From the navigation pane, select High Availability > HA Group.
# Click Configure.
# Configure the HA group parameters as shown in Figure 40.
Figure 40 Configuring HA group parameters
# Click OK.
Configuring the hosts
# On the hosts, specify 2002::1 as the default gateway.
Verifying the configuration
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that both Device A and Device B generate log messages when the hosts communicate with the Internet.