- Table of Contents
-
- 08-Configuration Examples
- 01-Web Login Configuration Examples
- 02-Internet Access Through a Static IP Address Configuration Examples
- 03-Internet access through PPPoE configuration examples
- 04-Signature Library Upgrade Configuration Examples
- 04-Software Upgrade Examples(only for F50X0-D and F5000-AK5X5 firewalls)
- 05-Software Upgrade Examples
- 06-Static routing configuration examples
- 07-OSPF configuration examples
- 08-BGP configuration examples
- 09-RIP configuration examples
- 10-DHCP configuration examples
- 11-DNS configuration examples
- 12-Object Group Configuration Examples
- 13-Public key management configuration examples
- 14-Security Policy Configuration Examples
- 15-Attack defense configuration examples
- 16-Connection Limit Configuration Examples
- 17-IPS Configuration Examples
- 18-URL Filtering Configuration Examples
- 19-Anti-Virus Configuration Examples
- 20-Data Filtering Configuration Examples
- 21-File Filtering Configuration Examples
- 22-APR-Based Security Policy Configuration Examples
- 23-Bandwidth Management Configuration Examples
- 24-NAT configuration examples
- 25-NAT hairpin configuration examples
- 26-IPsec configuration examples
- 27-SSL VPN configuration examples
- 28-Server Load Balancing Configuration Examples
- 29-Outbound Link Load Balancing Configuration Examples
- 30-Inbound Link Load Balancing Configuration Examples
- 31-Transparent DNS Proxy Configuration Examples
- 32-Context Configuration Examples
- 32-Context Configuration Examples(only for F50X0-D and F5000-AK5X5 firewalls)
- 33-IRF configuration examples
- 34-High Availability Group Configuration Examples
- 35-NAT Flow Logging Configuration Examples
- 36-User identification configuration examples
- 37-Server Connection Detection Configuration Examples
- 38-IP Reputation Configuration Examples
- 39-NPTv6 Configuration Examples
- 40-SSL Decryption Configuration Examples
- 41-MAC Address Learning Through a Layer 3 Device Configuration Examples
- 42-WAF Configuration Examples
- 43-NetShare Control Configuration Examples
- 44-4G Configuration Examples
- 45-WLAN Configuration Examples
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 26-IPsec configuration examples | 259.92 KB |
Introduction
The following information provides IPsec configuration examples.
This document is not restricted to specific software or hardware versions. Procedures and information in the examples might be slightly different depending on the software or hardware version of the device.
The configuration examples were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
The following information is provided based on the assumption that you have basic knowledge of the IPsec feature.
Restrictions and guidelines
· When you specify the remote host name in an IPsec policy, follow these restrictions and guidelines:
¡ If the remote host name is resolved by a DNS server, the local device gets the latest IP address corresponding to the host name by sending a query to the DNS server when the cached DNS entry ages. The DNS entry aging information is obtained from the DNS server.
¡ If the remote host name is resolved by a locally configured static DNS entry and the IP address in the entry is changed, you must respecify the remote host name in the IPsec policy to get the new IP address.
· To make sure SAs can be set up and the traffic protected by IPsec can be processed correctly between two IPsec peers, create mirror image ACLs on the IPsec peers. If the ACL rules on IPsec peers do not form mirror images of each other, SAs can be set up only when both of the following requirements are met:
¡ The range specified by an ACL rule on one peer is covered by its counterpart ACL rule on the other peer.
¡ The peer with the narrower rule initiates SA negotiation.
If a wider ACL rule is used by the SA initiator, the negotiation request might be rejected because the matching traffic is beyond the scope of the responder.
· If you do not configure the local identity in an IPsec policy, the policy uses the global local identity settings configured in the advanced settings.
· Modifications to the following settings in an IPsec policy take effect only on IPsec SAs set up after the modifications:
¡ Encapsulation mode.
¡ Security protocol.
¡ Security algorithms.
¡ PFS.
¡ IPsec SA lifetimes.
¡ IPsec SA idle timeout.
For the modifications to take effect on existing IPsec SAs, you must reset the IPsec SAs.
· The IPsec peers of an IPsec tunnel must have IPsec policies that use the same security protocols, security algorithms, and encapsulation mode.
· When IKE negotiates IPsec SAs, it uses the IPsec SA lifetime settings configured in the IPsec policy to negotiate the IPsec SA lifetime with the peer. If the IPsec SA lifetime settings are not configured in the IPsec policy, the global IPsec SA lifetime settings are used. IKE uses the local lifetime settings or those proposed by the peer, whichever are smaller.
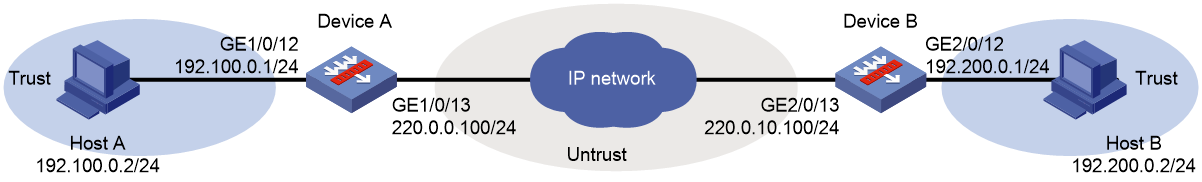
Network configuration
As shown in Figure 1, establish an IPsec tunnel between Device A and Device B to protect data flows between the subnets of Host A and Host B. Configure the tunnel as follows:
· Set up SAs through IKE negotiation.
· Configure IKE to use the 3DES-CBC encryption algorithm, the SHA256 authentication algorithm, and the preshared key authentication method.
· Specify the IPsec encapsulation mode as tunnel and the security protocol as ESP
Software versions used
This configuration example was created and verified on F9345 of the F1060 device.
Procedure
Configuring Device A
1. Assign IP addresses to interfaces and add the interfaces to security zones:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/13.
# In the dialog box that opens, configure the interface:
a. Select the Untrust security zone.
b. Click the IPv4 Address tab. Enter the IP address and mask of the interface. In this example, enter 220.0.0.100/24.
c. Click OK.
# Add GE 1/0/12 to the Trust security zone and set its IP address to 192.100.0.1/24 in the same way you configure GE 1/0/13.
2. Configure settings for routing:
This example configures static routes.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > Static Routing.
# On the IPv4 Static Routing tab, click Create.
# In the dialog box that opens, configure a static route to reach 220.0.10.100:
a. Set the destination IP address to 220.0.10.100.
b. Set the mask length to 24.
c. Set the next hop address to 220.0.0.2.
d. Use the default settings for other parameters.
e. Click OK.
# On the IPv4 Static Routing tab, click Create.
# In the dialog box that opens, configure a static route to reach 192.200.0.2:
a. Set the destination IP address to 192.200.0.2.
b. Set the mask length to 24.
c. Set the next hop address to 220.0.0.2.
d. Use the default settings for other parameters.
e. Click OK.
3. Configure security policies:
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Click Create.
# Configure a security policy named trust-untrust to permit specific traffic from the Trust to Untrust security zones:
a. Set the security policy name to trust-untrust.
b. Select source zone Trust.
c. Select destination zone Untrust.
d. Select IPv4 as the type.
e. Select action Permit.
f. Enter source IPv4 address 192.100.0.0/24.
g. Enter destination IPv4 address 192.200.0.0/24.
h. Use the default settings for other parameters.
i. Click OK.
# On the Security Policies page, click Create.
# Configure a security policy named untrust-trust to permit specific traffic from the Untrust to Trust security zones:
a. Set the security policy name to untrust-trust.
b. Select source zone Untrust.
c. Select destination zone Trust.
d. Select IPv4 as the type.
e. Select action Permit.
f. Enter source IPv4 address 192.200.0.0/24.
g. Enter destination IPv4 address 192.100.0.0/24.
h. Use the default settings for other parameters.
i. Click OK.
# On the Security Policies page, click Create.
# Configure a security policy named local-untrust to permit specific traffic from the Local to Untrust security zones:
a. Set the security policy name to local-untrust.
b. Select source zone Local.
c. Select destination zone Untrust.
d. Select IPv4 as the type.
e. Select action Permit.
f. Enter source IPv4 address 220.0.0.100.
g. Enter destination IPv4 address 220.0.10.100.
h. Use the default settings for other parameters.
i. Click OK.
# On the Security Policies page, click Create.
# Configure a security policy named untrust-local to permit specific traffic from the Untrust to Local security zones:
a. Set the security policy name to untrust-local.
b. Select source zone Untrust.
c. Select destination zone Local.
d. Select IPv4 as the type.
e. Select action Permit.
f. Enter source IPv4 address 220.0.10.100.
g. Enter destination IPv4 address 220.0.0.100.
h. Use the default settings for other parameters.
i. Click OK.
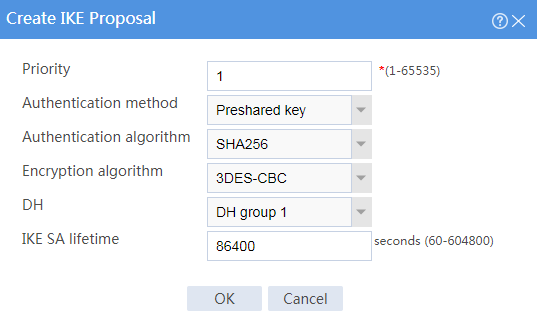
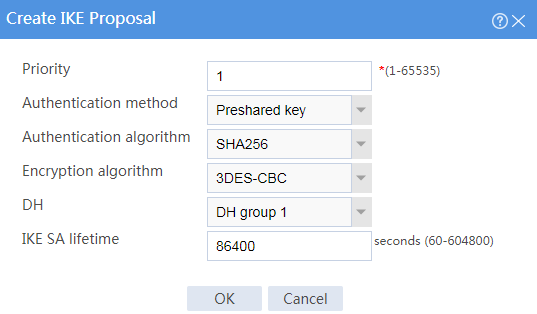
4. Create an IKE proposal:
# On the top navigation bar, click Network.
# From the navigation pane, select VPN > IPsec > IKE Proposals.
# Click Create.
¡ Set the priority to 1.
¡ Select the preshared key authentication method.
¡ Select the SHA256 authentication algorithm.
¡ Select the 3DES-CBC encryption algorithm.
# Click OK.
Figure 2 Creating an IKE proposal
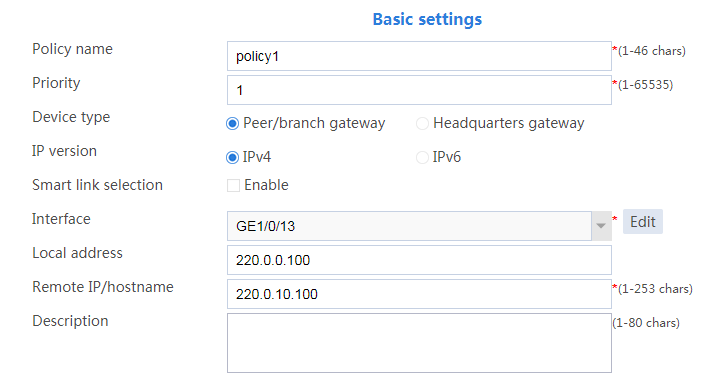
5. Configure the IPsec policy:
# On the top navigation bar, click Network.
# From the navigation pane, select VPN > IPsec > IPsec Policies.
# Click Create.
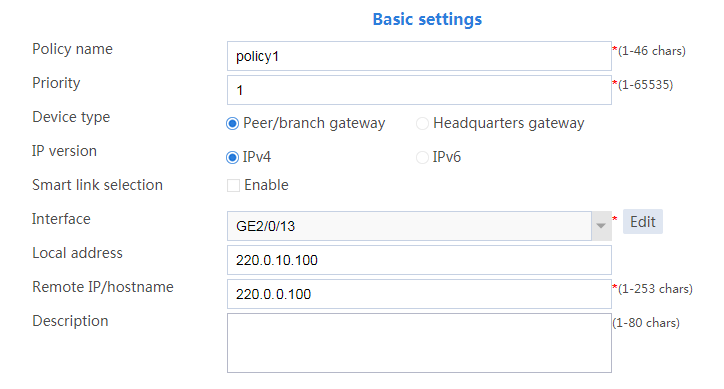
# Configure the basic settings as follows:
¡ Set the policy name to policy1.
¡ Set the priority to 1.
¡ Set the device type to Peer/branch gateway.
¡ Set the IP version to IPv4.
¡ Select interface GE1/0/13.
¡ Configure the local address as 220.0.0.100.
¡ Configure the remote address/host name as 220.0.10.100.
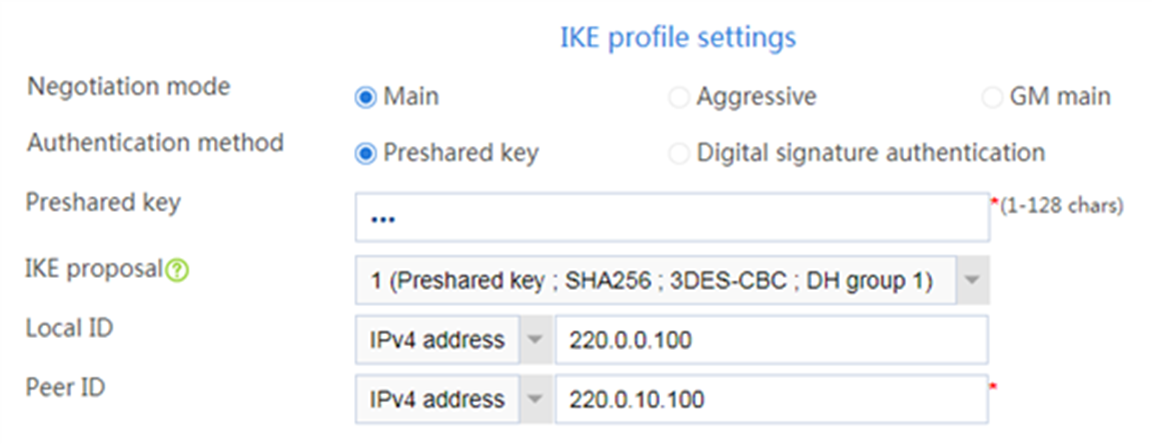
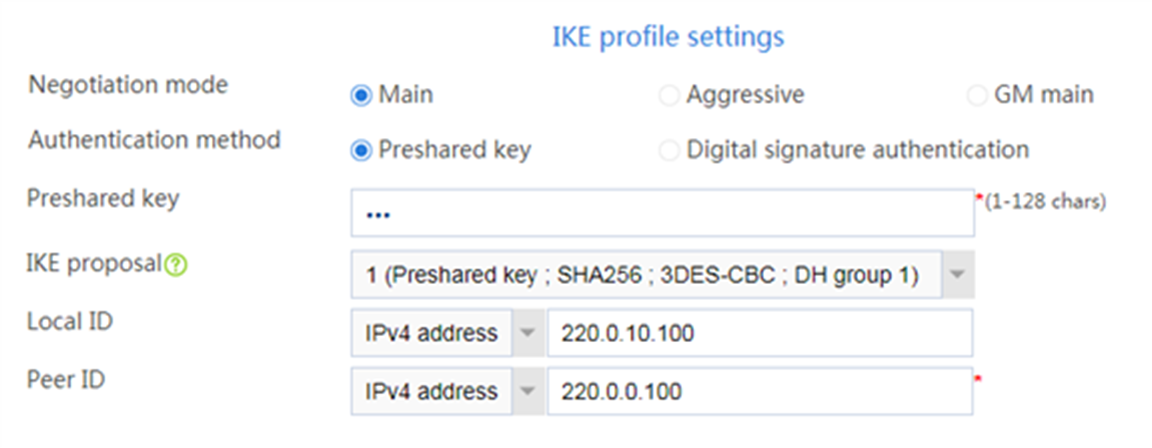
# Configure the IKE profile settings as follows:
¡ Set the negotiation mode as Main.
¡ Set the authentication method as Preshared key.
¡ Enter the preshared key string.
¡ Select IKE proposal 1 (Preshared key; SHA256; 3DES-CBC; DH group 1).
¡ Set the local ID as IPv4 address 220.0.0.100.
¡ Set the peer ID as IPv4 address 220.0.10.100.
Figure 4 IKE profile settings
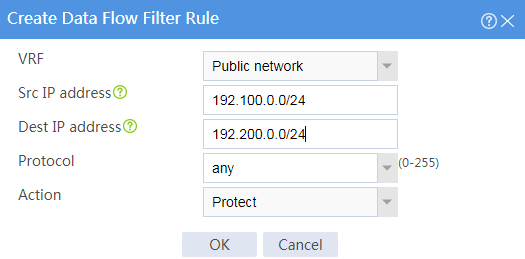
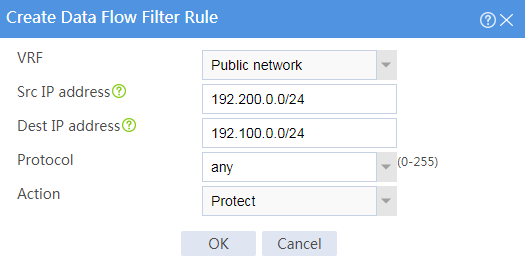
# Configure the data flow filter rules as follows:
¡ Click Create.
¡ Set the source IP address as 192.100.0.0/24.
¡ Set the destination IP address as 192.200.0.0/24.
# Click OK.
Figure 5 Creating a data flow filter rule
# Set the IPsec SA triggering mode to Traffic-based.
# Configure the IPsec advanced settings as follows:
¡ Select the Tunnel encapsulation mode.
¡ Select the ESP security protocol.
# Click OK.
Configuring Device B
1. Assign IP addresses to interfaces and add the interfaces to security zones:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 2/0/13.
# In the dialog box that opens, configure the interface:
a. Select the Untrust security zone.
b. Click the IPv4 Address tab, and then enter the IP address and mask of the interface. In this example, enter 220.0.10.100/24.
c. Click OK.
# Add GE 2/0/12 to the Trust security zone and set its IP address to 192.200.0.2/24 in the same way you configure GE 2/0/13.
2. Configure settings for routing:
This example configures static routes.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > Static Routing.
# On the IPv4 Static Routing tab, click Create.
# In the dialog box that opens, configure a static route to reach 220.0.0.100:
a. Set the destination IP address to 220.0.0.100.
b. Set the mask length to 24.
c. Set the next hop address to 220.0.10.2.
d. Use the default settings for other parameters.
e. Click OK.
# On the IPv4 Static Routing tab, click Create.
# Configure a static route to reach 192.100.0.2:
a. Set the destination IP address to 192.100.0.2.
b. Set the mask length to 24.
c. Set the next hop address to 220.0.10.2.
d. Use the default settings for other parameters.
e. Click OK.
3. Configure security policies:
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Click Create.
# Configure a security policy named trust-untrust to permit specific traffic from the Trust to Untrust security zones:
a. Set the security policy name to trust-untrust.
b. Select source zone Trust.
c. Select destination zone Untrust.
d. Select IPv4 as the type.
e. Select action Permit.
f. Enter source IPv4 address 192.200.0.0/24.
g. Enter destination IPv4 address 192.100.0.0/24.
h. Use the default settings for other parameters.
i. Click OK.
# On the Security Policies page, click Create.
# Configure a security policy named untrust-trust to permit specific traffic from the Untrust to Trust security zones:
a. Set the security policy name to untrust-trust.
b. Select source zone Untrust.
c. Select destination zone Trust.
d. Select IPv4 as the type.
e. Select action Permit.
f. Enter source IPv4 address 192.100.0.0/24.
g. Enter destination IPv4 address 192.200.0.0/24.
h. Use the default settings for other parameters.
i. Click OK.
# On the Security Policies page, click Create.
# Configure a security policy named local-untrust to permit specific traffic from the Local to Untrust security zones:
a. Set the security policy name to local-untrust.
b. Select source zone Local.
c. Select destination zone Untrust.
d. Select IPv4 as the type.
e. Select action Permit.
f. Enter source IPv4 address 220.0.10.100.
g. Enter destination IPv4 address 220.0.0.100.
h. Use the default settings for other parameters.
i. Click OK.
# On the Security Policies page, click Create.
# Configure a security policy named untrust-local to permit specific traffic from the Untrust to Local security zones:
a. Set the security policy name to untrust-local.
b. Select source zone Untrust.
c. Select destination zone Local.
d. Select IPv4 as the type.
e. Select action Permit.
f. Enter source IPv4 address 220.0.0.100.
g. Enter destination IPv4 address 220.0.10.100.
h. Use the default settings for other parameters.
i. Click OK.
4. Create an IKE proposal:
# On the top navigation bar, click Network.
# From the navigation pane, select VPN > IPsec > IKE Proposals.
# Click Create.
¡ Set the priority to 1.
¡ Select the preshared key authentication method.
¡ Select the SHA256 authentication algorithm.
¡ Select the 3DES-CBC encryption algorithm.
# Click OK.
Figure 6 Creating an IKE proposal
5. Configure the IPsec policy:
# On the top navigation bar, click Network.
# From the navigation pane, select VPN > IPsec > IPsec Policies.
# Click Create.
# Configure the basic settings as follows:
¡ Set the policy name to policy1.
¡ Set the priority to 1.
¡ Set the device type to Peer/branch gateway.
¡ Set the IP version to IPv4.
¡ Select interface GE2/0/13.
¡ Configure the local address as 220.0.10.100.
¡ Configure the remote address/host name as 220.0.0.100.
Figure 7 Basic settings
# Configure the IKE profile settings as follows:
¡ Set the negotiation mode as Main.
¡ Set the authentication method as Preshared key.
¡ Enter the preshared key string.
¡ Select IKE proposal 1 (Preshared key; SHA256; 3DES-CBC; DH group 1).
¡ Set the local ID as IPv4 address 220.0.10.100.
¡ Set the peer ID as IPv4 address 220.0.0.100.
Figure 8 IKE profile settings
# Configure the data flow filter rules as follows:
¡ Click Create.
¡ Set the source IP address as 192.200.0.0/24.
¡ Set the destination IP address as 192.100.0.0/24.
# Click OK.
Figure 9 Creating a data flow filter rule
# Set the IPsec SA triggering mode to Traffic-based.
# Configure the IPsec advanced settings as follows:
¡ Select the Tunnel encapsulation mode.
¡ Select the ESP security protocol.
# Click OK.
Verifying the configuration
1. Verify that Device A and Device B can communicate with each other.
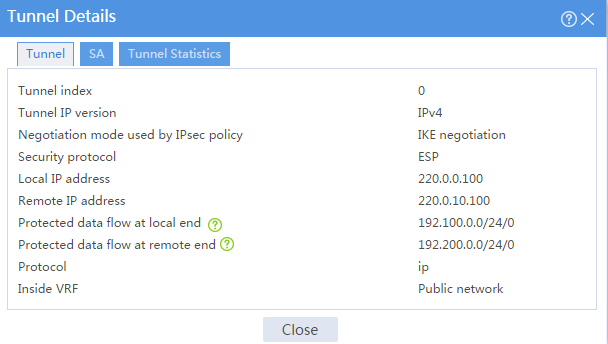
2. On Device A, display IPsec tunnel information:
# On the top navigation bar, click Network.
# From the navigation pane, select VPN > IPsec > IPsec Tunnels. The established IPsec tunnel is displayed.
# Click the Details icon for the IPsec tunnel. The Tunnel Details page displays tunnel information, SA information, and tunnel statistics.
Figure 10 Details of the IPsec tunnel on Device A
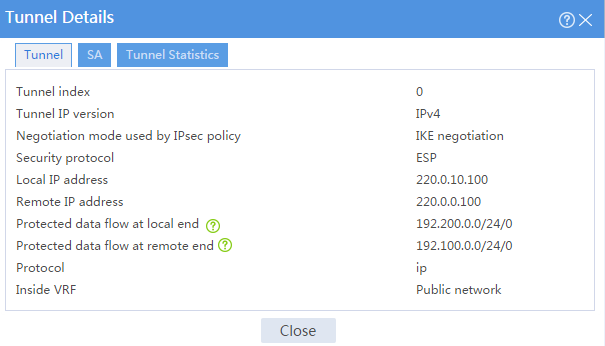
3. On Device B, display IPsec tunnel information:
# On the top navigation bar, click Network.
# From the navigation pane, select VPN > IPsec > IPsec Tunnels. The established IPsec tunnel is displayed.
# Click the Details icon for the IPsec tunnel. The Tunnel Details page displays tunnel information, SA information, and tunnel statistics.
Figure 11 Details of the IPsec tunnel on Device B