- Table of Contents
-
- H3C WX3000 Series Unified Switches Switching Engine Configuration Guide-6W103
- 00-Preface
- 01-CLI Configuration
- 02-Login Configuration
- 03-Configuration File Management Configuration
- 04-VLAN Configuration
- 05-Auto Detect Configuration
- 06-Voice VLAN Configuration
- 07-GVRP Configuration
- 08-Basic Port Configuration
- 09-Link Aggregation Configuration
- 10-Port Isolation Configuration
- 11-Port Security-Port Binding Configuration
- 12-DLDP Configuration
- 13-MAC Address Table Management Configuration
- 14-MSTP Configuration
- 15-802.1x and System Guard Configuration
- 16-AAA Configuration
- 17-MAC Address Authentication Configuration
- 18-IP Address and Performance Configuration
- 19-DHCP Configuration
- 20-ACL Configuration
- 21-QoS-QoS Profile Configuration
- 22-Mirroring Configuration
- 23-ARP Configuration
- 24-SNMP-RMON Configuration
- 25-Multicast Configuration
- 26-NTP Configuration
- 27-SSH Configuration
- 28-File System Management Configuration
- 29-FTP-SFTP-TFTP Configuration
- 30-Information Center Configuration
- 31-System Maintenance and Debugging Configuration
- 32-VLAN-VPN Configuration
- 33-HWPing Configuration
- 34-DNS Configuration
- 35-Smart Link-Monitor Link Configuration
- 36-PoE-PoE Profile Configuration
- 37-Routing Protocol Configuration
- 38-UDP Helper Configuration
- 39-Acronyms
- 40-Index
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 21-QoS-QoS Profile Configuration | 362.68 KB |
Table of Contents
Traditional Packet Forwarding Service
New Applications and New Requirements
Major Traffic Control Techniques
Traffic Policing and Traffic Shaping
Configuring Priority Trust Mode
Setting the Priority of Protocol Packets·
Configuring Traffic Redirecting
Collecting/Clearing Traffic Statistics
Displaying and Maintaining QoS
Configuration Example of Traffic Policing
QoS Profile Configuration Task List
Displaying and Maintaining QoS Profile
QoS Profile Configuration Example
![]()
l The term switch used throughout this chapter refers to a switching device in a generic sense or the switching engine of the WX3000 series.
l The sample output information in this manual was created on the WX3024. The output information on your device may vary.
Overview
Introduction to QoS
Quality of service (QoS) is a concept generally existing in occasions with service supply and demand. It evaluates the ability to meet the need of the customers in service. Generally, the evaluation is not to grade precisely. Its purpose is to analyze the conditions where the service is the best and the conditions where the service still needs improvement and then to make improvements in the specified aspects.
Traditional Packet Forwarding Service
In traditional IP networks, packets are treated equally. That is, the FIFO (first in first out) policy is adopted for packet processing. Network resources required for packet forwarding is determined by the order in which packets arrive. All the packets share the resources of the network. Network resources available to the packets completely depend on the time they arrive. This service policy is known as Best-effort, which delivers the packets to their destination with the best effort, with no assurance and guarantee for delivery delay, jitter, packet loss ratio, reliability, and so on.
The traditional Best-Effort service policy is only suitable for applications insensitive to bandwidth and delay, such as WWW, file transfer and E-mail.
New Applications and New Requirements
With the expansion of computer network, more and more networks become part of the Internet. The Internet gains rapid development in terms of scale, coverage and user quantities. More and more users use the Internet as a platform for their services and for data transmission.
Besides the traditional applications such as WWW, E-mail, and FTP, new services are developed on the Internet, such as tele-education, telemedicine, video telephone, videoconference and Video-on-Demand (VoD). Enterprise users expect to connect their regional branches together using VPN techniques for coping with daily business, for instance, accessing databases or manage remote equipments through Telnet.
All these new applications have one thing in common, that is, they have special requirements for bandwidth, delay, and jitter. For instance, bandwidth, delay, and jitter are critical for videoconference and VoD. As for other applications, such as transaction processing and Telnet, although bandwidth is not as critical, a too long delay may cause unexpected results. That is, they need to get serviced in time even if congestion occurs.
Newly emerging applications demand higher service performance from IP networks. In addition to simply delivering packets to their destinations, better network services are demanded, such as allocating dedicated bandwidth, reducing packet loss ratio, avoiding congestion, regulating network traffic, and setting priority of the packets. To meet those requirements, the network should be provided with better service capability.
Major Traffic Control Techniques
Traffic classification, traffic policing, traffic shaping, congestion management, and congestion avoidance are the foundations for a network to provide differentiated services. Mainly they implement the following functions.
l Traffic classification identifies specific packets based on certain matching rules. It is a prerequisite for differentiated service.
l Traffic policing confines traffics to a specific specification. You can configure restriction or punishment measures against the traffics exceeding the specification to protect the benefits of carriers and to prevent network resources from being abused.
l Traffic shaping actively adjusts the output rate of traffics. It can enable the traffics to match the capacity of the downstream network devices, so as to prevent packets from being dropped and network congestion.
l Congestion management handles resource competition during network congestion. Generally, it adds packets to queues first, and then forwards the packets by using a scheduling algorithm.
l Congestion avoidance monitors the use of network resources and drops packets actively when congestion reaches certain degree. It relieves network load by adjusting traffics.
Traffic classification is the basis of all the above-mentioned traffic management technologies. It identifies packets using certain rules and makes differentiated services possible. Traffic policing, traffic shaping, congestion management, and congestion avoidance are methods for implementing network traffic control and network resource management. They are occurrences of differentiated services.
QoS Supported by Devices
Traffic Classification
Traffic here refers to service traffic; that is, all the packets passing the device.
Traffic classification means identifying packets that conform to certain characteristics according to certain rules. It is the foundation for providing differentiated services.
In traffic classification, the priority bit in the type of service (ToS) field in IP packet header can be used to identify packets of different priorities. The network administrator can also define traffic classification policies to identify packets by the combination of source address, destination address, MAC address, IP protocol or the port number of an application. Normally, traffic classification is done by checking the information carried in packet header. Packet payload is rarely adopted for traffic classification. The identifying rule is unlimited in range. It can be a quintuplet consisting of source address, source port number, protocol number, destination address, and destination port number. It can also be simply a network segment.
Precedence
IP precedence, ToS precedence, and DSCP precedence
Figure 1-1 DS field and ToS byte
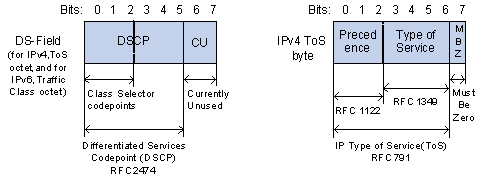
The ToS field in an IP header contains eight bits numbered 0 through 7, among which,
l The first three bits indicate IP precedence in the range 0 to 7.
l Bit 3 to bit 6 indicate ToS precedence in the range of 0 to 15.
l In RFC2474, the ToS field in IP packet header is also known as DS field. The first six bits (bit 0 through bit 5) of the DS field indicate differentiated service codepoint (DSCP) in the range of 0 to 63, and the last two bits (bit 6 and bit 7) are reserved.
Table 1-1 Description on IP precedence
|
IP Precedence (decimal) |
IP Precedence (binary) |
Description |
|
0 |
000 |
Routine |
|
1 |
001 |
priority |
|
2 |
010 |
immediate |
|
3 |
011 |
flash |
|
4 |
100 |
flash-override |
|
5 |
101 |
critical |
|
6 |
110 |
internet |
|
7 |
111 |
network |
In a network providing differentiated services, traffics are grouped into the following four classes, and packets are processed according to their DSCP values.
l Expedited Forwarding (EF) class: In this class, packets can be forwarded regardless of link share of other traffic. The class is suitable for preferential services with low delay, low packet loss ratio, low jitter, and assured bandwidth (such as virtual leased line);
l Assured forwarding (AF) class: This class is further divided into four subclasses (AF1/2/3/4) and a subclass is further divided into three drop priorities, so the AF service level can be segmented. The QoS rank of the AF class is lower than that of the EF class;
l Class selector (CS) class: This class comes from the IP ToS field and includes eight subclasses;
Table 1-2 Description on DSCP precedence values
|
DSCP value (decimal) |
DSCP value (binary) |
Description |
|
46 |
101110 |
ef |
|
10 |
001010 |
af11 |
|
12 |
001100 |
af12 |
|
14 |
001110 |
af13 |
|
18 |
010010 |
af21 |
|
20 |
010100 |
af22 |
|
22 |
010110 |
af23 |
|
26 |
011010 |
af31 |
|
28 |
011100 |
af32 |
|
30 |
011110 |
af33 |
|
34 |
100010 |
af41 |
|
36 |
100100 |
af42 |
|
38 |
100110 |
af43 |
|
8 |
001000 |
cs1 |
|
16 |
010000 |
cs2 |
|
24 |
011000 |
cs3 |
|
32 |
100000 |
cs4 |
|
40 |
101000 |
cs5 |
|
48 |
110000 |
cs6 |
|
56 |
111000 |
cs7 |
|
0 |
000000 |
be (default) |
802.1p priority
802.1p priority lies in Layer 2 packet headers and is applicable to occasions where the Layer 3 packet header does not need analysis but QoS must be assured at Layer 2.
Figure 1-2 An Ethernet frame with an 802.1Q tag header
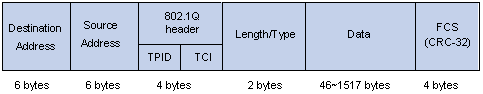
As shown in the figure above, each host supporting 802.1Q protocol adds a 4-byte 802.1Q tag header after the source address of the former Ethernet frame header when sending packets.
The 4-byte 802.1Q tag header consists of the tag protocol identifier (TPID, two bytes in length), whose value is 0x8100, and the tag control information (TCI, two bytes in length). Figure 1-3 describes the detailed contents of an 802.1Q tag header.
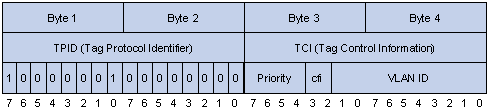
In the figure above, the priority field (three bits in length) in TCI is 802.1p priority (also known as CoS precedence), which ranges from 0 to 7.
Table 1-3 Description on 802.1p priority
|
802.1p priority (decimal) |
802.1p priority (binary) |
Description |
|
0 |
000 |
best-effort |
|
1 |
001 |
background |
|
2 |
010 |
spare |
|
3 |
011 |
excellent-effort |
|
4 |
100 |
controlled-load |
|
5 |
101 |
video |
|
6 |
110 |
voice |
|
7 |
111 |
network-management |
The precedence is called 802.1p priority because the related applications of this precedence are defined in detail in the 802.1p specifications.
Priority Trust Mode
A device can assign different types of precedence to the packets it receives as configured, such as 802.1p precedence, DSCP precedence, local precedence, and drop precedence.
Among the above-mentioned precedence types:
l The local precedence is only of local significance. A local precedence corresponds to a specific output queue. Packets with higher local precedence values take precedence over those with lower precedence values and will be processed preferentially.
l The drop precedence determines which packets are dropped preferentially. The higher the drop precedence, the more likely a packet is dropped.
![]()
The device does not support marking drop precedence for packets.
A device can operate in one of the following two priority trust modes when assigning precedence to received packets:
l Packet priority trusted mode
l Port priority trusted mode
In terms of priority trust mode, the priority mapping process is shown in Figure 1-4.
Figure 1-4 Assigning precedence to received packets in different trust modes
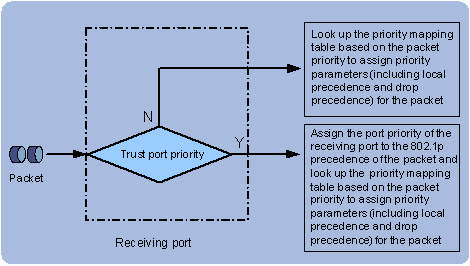
As for packet priority trusted mode, you can configure to trust the following packet priority:
l 802.1p precedence
l DSCP precedence
Trusting the 802.1p precedence
In this mode, you can specify to process the received packets in one of the following two ways.
l Keeping the original packet precedence unchanged (the default mode)
l Replacing the original packet precedence with the corresponding one (the automap mode).
If a packet does not carry 802.1p precedence, the device uses the priority of the receiving port as the 802.1p precedence of the packet and then looks up the COS-precedence-to-other-precedence mapping table for the corresponding precedence.
Trusting the DSCP precedence
In this mode, you can specify to process the received packets in one of the following ways.
l Keeping the original packet precedence unchanged (the default mode)
l Replacing the original packet precedence with the corresponding one (the automap mode)
l Looking up the DSCP-precedence-to-DSCP-precedence mapping table for the local DSCP precedence and then looking up the DSCP-precedence-to-other-precedence mapping table based on the new DSCP precedence for the one to be assigned to the packets (the remap mode)
The devices provide COS-precedence-to-other-precedence, DSCP-precedence-to-other-precedence, and DSCP-precedence-to-DSCP- precedence mapping tables for priority mapping. Table 1-4 through Table 1-6 list the default settings of these tables.
Table 1-4 The default COS-precedence-to-other-precedence mapping table of the devices
|
802.1p precedence |
Target local precedence |
Target drop precedence |
Target DSCP precedence |
|
0 |
2 |
0 |
16 |
|
1 |
0 |
0 |
0 |
|
2 |
1 |
0 |
8 |
|
3 |
3 |
0 |
24 |
|
4 |
4 |
0 |
32 |
|
5 |
5 |
0 |
40 |
|
6 |
6 |
0 |
48 |
|
7 |
7 |
0 |
56 |
Table 1-5 The default DSCP-precedence-to-other-precedence mapping table of the devices
|
DSCP precedence |
Target local precedence |
Target drop precedence |
Target 802.1p precedence |
|
0 to 7 |
0 |
1 |
1 |
|
8 to 15 |
1 |
1 |
2 |
|
16 to 23 |
2 |
1 |
0 |
|
24 to 31 |
3 |
1 |
3 |
|
32 to 39 |
4 |
0 |
4 |
|
40 to 47 |
5 |
0 |
5 |
|
48 to 55 |
6 |
0 |
6 |
|
56 to 63 |
7 |
0 |
7 |
Table 1-6 The default DSCP-precedence-to-DSCP-precedence mapping table of the devices
|
DSCP precedence |
Target DSCP precedence |
|
0 |
0 |
|
1 |
1 |
|
2 |
2 |
|
3 |
3 |
|
... |
... |
|
61 |
61 |
|
62 |
62 |
|
63 |
63 |
Protocol Priority
Protocol packets carry their own priority. You can modify the priority of a protocol packet to implement QoS.
Priority Marking
Traffic Policing and Traffic Shaping
The network will be made more congested by plenty of continuous burst packets if the traffic of each user is not limited. The traffic of each user must be limited in order to make better use of the limited network resources and provide better service for more users. For example, a traffic flow can be limited to get only its committed resources during a time period to avoid network congestion caused by excessive bursts.
Traffic policing and traffic shaping is each a kind of traffic control policy used to limit the traffic and the resource occupied by supervising the traffic. The regulation policy is implemented according to the evaluation result on the premise of knowing whether the traffic exceeds the specification when traffic policing or traffic shaping is performed. Normally, token bucket is used for traffic evaluation.
Token bucket
The token bucket can be considered as a container with a certain capacity to hold tokens. The system puts tokens into the bucket at the set rate. When the token bucket is full, the extra tokens will overflow and the number of tokens in the bucket stops increasing.
Figure 1-5 Evaluate the traffic with the token bucket
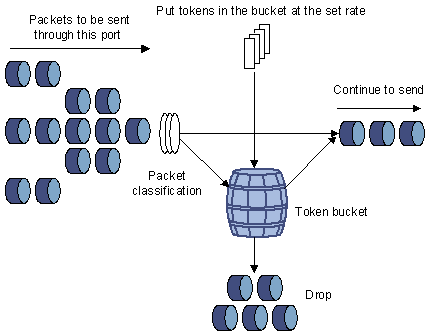
Evaluating the traffic with the token bucket
When token bucket is used for traffic evaluation, the number of the tokens in the token bucket determines the amount of the packets that can be forwarded. If the number of tokens in the bucket is enough to forward the packets, the traffic is conforming to the specification; otherwise, the traffic is nonconforming or excess.
Parameters concerning token bucket include:
l Average rate: The rate at which tokens are put into the bucket, namely, the permitted average rate of the traffic. It is generally set to committed information rate (CIR).
l Burst size: The capacity of the token bucket, namely, the maximum traffic size that is permitted in each burst. It is generally set to committed burst size (CBS). The set burst size must be greater than the maximum packet length.
One evaluation is performed on each arriving packet. In each evaluation, if the number of tokens in the bucket is enough, the traffic is conforming to the specification and you must take away some tokens whose number is corresponding to the packet forwarding authority; if the number of tokens in the bucket is not enough, it means that too many tokens have been used and the traffic is excess.
Traffic policing
The typical application of traffic policing is to supervise specific traffic into the network and limit it to a reasonable range, or to "discipline" the extra traffic. In this way, the network resources and the interests of the operators are protected. For example, you can limit HTTP packets to be within 50% of the network bandwidth. If the traffic of a certain connection is excess, traffic policing can choose to drop the packets or to reset the priority of the packets.
Traffic policing is widely used in policing the traffic into the network of internet service providers (ISPs). Traffic policing can identify the policed traffic and perform pre-defined policing actions based on different evaluation results. These actions include:
l Discarding the nonconforming packets.
l Forwarding the conforming packets or nonconforming packets.
l Marking the conforming packets or nonconforming packets with 802.1p precedence and then forwarding the packets.
l Marking the conforming packets or nonconforming packets with DSCP precedence and forwarding the packets.
Traffic shaping
Traffic shaping is a measure to regulate the output rate of traffic actively. Its typical application is to control local traffic output based on the traffic policing indexes of downstream network nodes.
The major difference between traffic shaping and traffic policing is that the packets to be dropped in traffic policing are cached in traffic shaping——usually in buffers or queues, as shown in Figure 1-6. When there are enough tokens in the token bucket, the cached packets are sent out evenly. Another difference between traffic policing and traffic shaping is that traffic shaping may increase the delay while traffic policing hardly increases the delay.
Figure 1-6 Diagram for traffic shaping
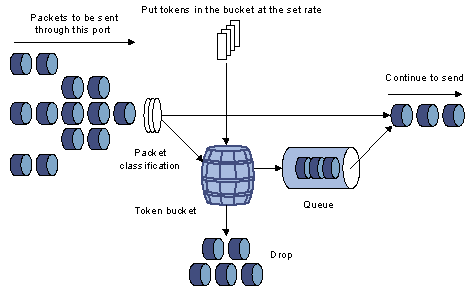
For example, if the device A sends packets to the device B. The device B will perform traffic policing on packets from the device A to drop the packets beyond the specification.
In order to avoid meaningless packet loss, you can perform traffic shaping on the packets on the egress of the device A and cache the packets beyond the traffic policing specification in the device A. When the next packets can be sent, the packets cached in the buffer queues will be taken out and sent. In this way, all the packets sent to the device B conforms to the traffic specification of the device B.
Traffic Redirecting
Traffic redirecting identifies traffic using ACLs and redirects the matched packets to specific ports. By traffic redirecting, you can change the way in which a packet is forwarded to achieve specific purposes.
VLAN Mapping
VLAN mapping identifies traffics using ACLs and maps the VLAN tags carrier in matched packets to specific VLAN tags. By employing VLAN mapping on a device connecting user networks to the carrier network, you can map the VLAN tags of specific user network packets to those of specific VLANs in the carrier network, thus meeting the requirements of the carrier network.
Queue Scheduling
When the network is congested, the problem that many packets compete for resources must be solved, usually through queue scheduling.
1) SP queuing
Figure 1-7 Diagram for SP queuing
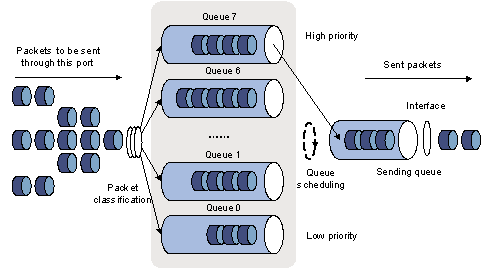
SP queue-scheduling algorithm is specially designed for critical service applications. An important feature of critical services is that they demand preferential service in congestion in order to reduce the response delay. Assume that there are eight output queues on the port and the preferential queue classifies the eight output queues on the port into eight classes, which are queue7, queue6, queue5, queue4, queue3, queue2, queue1, and queue0. Their priorities decrease in order.
In queue scheduling, SP sends packets in the queue with higher priority strictly following the priority order from high to low. When the queue with higher priority is empty, packets in the queue with lower priority are sent. You can put critical service packets into the queues with higher priority and put non-critical service (such as e-mail) packets into the queues with lower priority. In this case, critical service packets are sent preferentially and non-critical service packets are sent when critical service groups are not sent.
2) WRR queuing
Figure 1-8 Diagram for WRR queuing
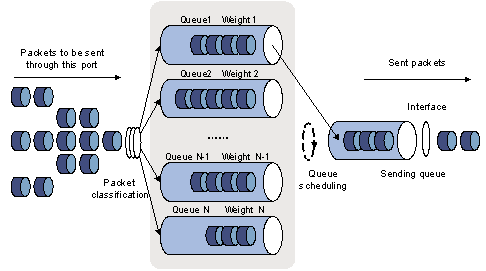
WRR queue-scheduling algorithm schedules all the queues in turn and every queue can be assured of a certain service time. Assume there are eight priority queues on a port. WRR configures a weight value for each queue, which is w7, w6, w5, w4, w3, w2, w1, and w0. The weight value indicates the proportion of obtaining resources. On a 100 M port, configure the weight value of WRR queue-scheduling algorithm to 50, 50, 30, 30, 10, 10, 10, and 10 (corresponding to w7, w6, w5, w4, w3, w2, w1, and w0 in order). In this way, the queue with the lowest priority can get 5 Mbps bandwidth at least, and the disadvantage of SP queue-scheduling that the packets in queues with lower priority may not get service for a long time is avoided. Another advantage of WRR queue is that: though the queues are scheduled in order, the service time for each queue is not fixed; that is to say, if a queue is empty, the next queue will be scheduled. In this way, the bandwidth resources are made full use.
3) SDWRR
Comparing with WRR queue, SDWRR queue further optimizes the delay and variation for different queues.
For example, configure the weight value of queue0 and queue1 to 5 and 3 respectively. The processing procedures of WRR and SDWRR are as follows:
l WRR: The packets whose weight value is 3 in queue1 are scheduled only after the packets whose weight value is 5 in the queue0 are scheduled. If there is a wide difference between the weight values of two queues, the queue with high weight value will cause great delay and variation for the queue with low weight value.
l SDWRR: Two queues are scheduled in turn. Packets whose weight value is 1 in queue0 are scheduled first, and then packets whose weight value is 1 in queue1 are scheduled. The procedure is repeated until the scheduling for one queue is over, and then SDWRR will schedule packets with the left weight values in the other queue. The detailed scheduling sequence is described in the Table 1-7.
Table 1-7 Queue-scheduling sequence of SDWRR
|
Scheduling algorithm |
Queue-scheduling sequence |
Description |
|
WRR |
0, 0, 0, 0, 0, 1, 1, 1, 0, 0, 0, 0, 0, 1, 1, 1 |
0 indicates packets in queue0 1 indicates packets in queue1 |
|
SDWRR |
0, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0 |
Flow-based Traffic Accounting
The function of flow-based traffic accounting is to use ACL rules in traffic classification and perform traffic accounting on the packets matching the ACL rules. You can get the statistics of the packets you are interested in through this function.
Burst
The Burst function can provide better packet cache function and traffic forwarding performance. It is suitable for networks where
l Large amount of broadcast/multicast packets and large burst traffic exist.
l Packets of high-rate links are forwarded to low-rate links or packets of multiple links with the equal rates are forwarded to a single link that is of the same rate as that of the incoming links.
Although the burst function helps reduce the packet loss ratio and improve packet processing capability in the networks mentioned above, it may affect QoS performance. So, use this function with caution.
Traffic mirroring
Traffic mirroring identifies traffic using ACLs and duplicates the matched packets to the destination port. For information about port mirroring, refer to Mirroring in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide.
QoS Configuration
QoS Configuration Task List
Complete the following tasks to configure QoS:
|
Task |
Remarks |
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
Configuring Priority Trust Mode
Refer to Priority Trust Mode for introduction to priority trust mode.
Configuration prerequisites
l The priority trust mode to be adopted is determined.
l The port where priority trust mode is to be configured is determined.
l The port priority value is determined.
Configuration procedure
Follow these steps to configure to trust port priority:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Configure the port priority |
priority priority-level |
Optional 0 by default |
Follow these steps to configure to trust 802.1p precedence:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Configure to trust 802.1p precedence |
priority-trust cos [ automap ] |
Required By default, port priority is trusted. |
Follow these steps to configure to trust DSCP precedence:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Configure to trust DSCP precedence |
priority-trust dscp [ automap | remap ] |
Required By default, port priority is trusted. |
Configuration example
l Configure to trust port priority on GigabitEthernet 1/0/1 and set the priority of GigabitEthernet 1/0/1 to 7.
Configuration procedure:
<device> system-view
[device] interface GigabitEthernet1/0/1
[device-GigabitEthernet1/0/1] priority 7
l Configure to trust 802.1p precedence on GigabitEthernet 1/0/1.
Configuration procedure:
<device> system-view
[device] interface GigabitEthernet1/0/1
[device-GigabitEthernet1/0/1] priority-trust cos
l Configure to trust DSCP precedence on GigabitEthernet 1/0/1.
Configuration procedure:
<device> system-view
[device] interface GigabitEthernet1/0/1
[device-GigabitEthernet1/0/1] priority-trust dscp
Configuring Priority Mapping
You can modify the COS-precedence-to-other-precedence, DSCP-precedence-to-other-precedence, and DSCP-precedence-to-DSCP-precedence mapping tables as required to mark packets with different priorities.
Configuration prerequisites
The target COS-precedence-to-other-precedence, DSCP-precedence-to-other-precedence, and DSCP-precedence-to-DSCP-precedence mapping tables are determined.
Configuration procedure
Follow these steps to configure the COS-precedence-to-other-precedence mapping table:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure COS-precedence-to-local-precedence mapping table |
qos cos-local-precedence-map cos0-map-local-prec cos1-map-local-prec cos2-map-local-prec cos3-map-local-prec cos4-map-local-prec cos5-map-local-prec cos6-map-local-prec cos7-map-local-prec |
Required |
|
Configure COS-precedence-to-drop-precedence mapping table |
qos cos-drop-precedence-map cos0-map-drop-prec cos1-map-drop-prec cos2-map-drop-prec cos3-map-drop-prec cos4-map-drop-prec cos5-map-drop-prec cos6-map-drop-prec cos7-map-drop-prec |
Required |
|
Configure COS-precedence-to-DSCP-precedence mapping table |
qos cos-dscp-map cos0-map-dscp cos1-map-dscp cos2-map-dscp cos3-map-dscp cos4-map-dscp cos5-map-dscp cos6-map-dscp cos7-map-dscp |
Required |
Follow these steps to configure the DSCP-precedence-to-other-precedence mapping table:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure DSCP-precedence-to-local-precedence mapping table |
qos dscp-local-precedence-map dscp-list : local-precedence |
Required |
|
Configure DSCP-precedence-to-drop-precedence mapping table |
qos dscp-drop-precedence-map dscp-list : drop-precedence |
Required |
|
Configure DSCP-precedence-to-COS-precedence mapping table |
qos dscp-cos-map dscp-list : cos-value |
Required |
Follow these steps to configure the DSCP-precedence-to-DSCP-precedence mapping table:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure DSCP-precedence-to-DSCP-precedence mapping table |
qos dscp-dscp-map dscp-list : dscp-value |
Required |
Configuration example
l Configure the COS-precedence-to-local-precedence mapping relationship for a device as follows: 0 to 2, 1 to 3, 2 to 4, 3 to 1, 4 to 7, 5 to 0, 6 to 5, and 7 to 6.
l Display the configuration.
Configuration procedure:
<device> system-view
[device] qos cos-local-precedence-map 2 3 4 1 7 0 5 6
[device] display qos cos-local-precedence-map
cos-local-precedence-map:
cos(802.1p) : 0 1 2 3 4 5 6 7
--------------------------------------------------------------------------
local precedence(queue) : 2 3 4 1 7 0 5 6
l Configure the DSCP-precedence-to-local-precedence mapping relationship for a device as follows: 0 through 7 to 2, 8 through 15 to 3, 16 through 23 to 4, 24 through 31 to 1, 32 through 39 to 7, 40 through 47 to 0, 48 through 55 to 5, and 56 through 63 to 6.
l Display the configuration.
<device> system-view
[device] qos dscp-local-precedence-map 0 1 2 3 4 5 6 7 : 2
[device] qos dscp-local-precedence-map 8 9 10 11 12 13 14 15 : 3
[device] qos dscp-local-precedence-map 16 17 18 19 20 21 22 23 : 4
[device] qos dscp-local-precedence-map 24 25 26 27 28 29 30 31 : 1
[device] qos dscp-local-precedence-map 32 33 34 35 36 37 38 39 : 7
[device] qos dscp-local-precedence-map 40 41 42 43 44 45 46 47 : 0
[device] qos dscp-local-precedence-map 48 49 50 51 52 53 54 55 : 5
[device] qos dscp-local-precedence-map 56 57 58 59 60 61 62 63 : 6
<device> display qos dscp-local-precedence-map
dscp-local-precedence-map:
dscp : local-precedence(queue)
----------------------------------------------
0 : 2
1 : 2
2 : 2
3 : 2
4 : 2
5 : 2
6 : 2
7 : 2
8 : 3
9 : 3
10 : 3
11 : 3
12 : 3
13 : 3
14 : 3
15 : 3
16 : 4
17 : 4
18 : 4
19 : 4
20 : 4
21 : 4
22 : 4
23 : 4
24 : 1
25 : 1
26 : 1
27 : 1
28 : 1
29 : 1
30 : 1
31 : 1
32 : 7
33 : 7
34 : 7
35 : 7
36 : 7
37 : 7
38 : 7
39 : 7
40 : 0
41 : 0
42 : 0
43 : 0
44 : 0
45 : 0
46 : 0
47 : 0
48 : 5
49 : 5
50 : 5
51 : 5
52 : 5
53 : 5
54 : 5
55 : 5
56 : 6
57 : 6
58 : 6
59 : 6
60 : 6
61 : 6
62 : 6
63 : 6
Setting the Priority of Protocol Packets
Refer to Protocol Priority for information about priority of protocol packets.
Configuration prerequisites
l The protocol type is determined.
l The priority value is determined.
Configuration procedure
Follow these steps to set the priority for specific protocol packets:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Set the priority for specific protocol packets |
protocol-priority protocol-type protocol-type { ip-precedence ip-precedence | dscp dscp-value } |
Required You can modify the IP precedence or DSCP precedence of the corresponding protocol packets. On a device, you can set the priority for protocol packets of Telnet, SNMP, and ICMP. |
Configuration example
l Set the IP precedence of ICMP packets to 3.
l Display the configuration.
Configuration procedure:
<device> system-view
[device] protocol-priority protocol-type icmp ip-precedence 3
[device] display protocol-priority
Protocol: icmp
IP-Precedence: flash(3)
Marking Packet Priority
Refer to Priority Marking for information about marking packet priority.
Marking packet priority can be implemented in the following two ways:
l Through traffic policing
When configuring traffic policing, you can define the action of marking the 802.1p priority and DSCP precedence for packets exceeding the traffic specification. Refer to Configuring Traffic Policing.
l Through the traffic-priority command
You can use the traffic priority command to mark the 802.1p priority and DSCP precedence of the packets.
Configuration prerequisites
The following items are defined or determined before the configuration:
l The ACL rules used for traffic classification are specified. Refer to the ACL module of this manual for related information.
l The type and value of the precedence to be marked for the packets matching the ACL rules are determined.
Configuration procedure
You can mark priority for all the packets matching specific ACL rules, or for packets that match specific ACL rules and are of a VLAN, of a port group, or pass a port.
Follow these steps to mark the priority for the packets matching specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Mark the priorities for packets matching specific ACL rules |
traffic-priority inbound acl-rule { dscp dscp-value | cos cos-value } |
Required |
Follow these steps to mark the priority for packets that are of a VLAN and match specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Mark the priorities for packets matching specific ACL rules |
traffic-priority vlan vlan-id inbound acl-rule { dscp dscp-value | cos cos-value } |
Required |
Follow these steps to mark the priority for packets that are of a port group and match specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter port group view |
port-group group-id |
— |
|
Mark the priorities for packets matching specific ACL rules |
traffic-priority inbound acl-rule { dscp dscp-value | cos cos-value } |
Required |
Follow these steps to mark the priority for packets passing a port and matching specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Mark the priorities for packets matching specific ACL rules |
traffic-priority inbound acl-rule { dscp dscp-value | cos cos-value } |
Required |
![]()
As the priority of traffic classification rules is higher than that of the default rules used for processing protocol packets, marking priority for all the packets or packets of a VLAN may affect device management that is implemented through Telnet and so on.
Configuration example
l GigabitEthernet 1/0/1 belongs to VLAN 2 and is connected to the 10.1.1.0/24 network segment.
l Mark the DSCP precedence as 56 for the packets from the 10.1.1.0/24 network segment.
1) Method I
<device> system-view
[device] acl number 2000
[device-acl-basic-2000] rule permit source 10.1.1.1 0.0.0.255
[device-acl-basic-2000] quit
[device] interface GigabitEthernet1/0/1
[device-GigabitEthernet1/0/1] traffic-priority inbound ip-group 2000 dscp 56
2) Method II
<device> system-view
[device] acl number 2000
[device-acl-basic-2000] rule permit source 10.1.1.1 0.0.0.255
[device-acl-basic-2000] quit
[device] traffic-priority vlan 2 inbound ip-group 2000 dscp 56
Configuring Traffic Policing
Refer to Traffic Policing and Traffic Shaping for information about traffic policing.
Configuration prerequisites
l The ACL rules used for traffic classification are defined. Refer to ACL in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide for information about defining ACL rules.
l The rate limit for traffic policing, and the actions for the packets exceeding the rate limit are determined.
Configuration procedure
You can configure traffic policing for all the packets matching specific ACL rules, or for the packets that match specific ACL rules and are of a VLAN, of a port group, or pass a port.
Follow these steps to configure traffic policing for all the packets matching specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure traffic policing |
traffic-limit inbound acl-rule target-rate [ conform con-action ] [ exceed exceed-action ] [ meter-statistic ] |
Required By default, traffic policing is disabled. |
|
Clear the traffic policing statistics |
reset traffic-limit inbound acl-rule |
Optional |
Follow these steps to configure traffic policing for packets that are of a VLAN and match specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure traffic policing |
traffic-limit vlan vlan-id inbound acl-rule target-rate [ conform con-action ] [ exceed exceed-action ] [ meter-statistic ] |
Required By default, traffic policing is disabled. |
|
Clear the traffic policing statistics |
reset traffic-limit vlan vlan-id inbound acl-rule |
Optional |
Follow these steps to configure traffic policing for packets that are of a port group and match specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter port group view |
port-group group-id |
— |
|
Configure traffic policing |
traffic-limit inbound acl-rule target-rate [ conform con-action ] [ exceed exceed-action ] [ meter-statistic ] |
Required By default, traffic policing is disabled. |
|
Clear the traffic policing statistics |
reset traffic-limit inbound acl-rule |
Optional |
Follow these steps to configure traffic policing for packets passing a port and matching specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Configure traffic policing |
traffic-limit inbound acl-rule target-rate [ conform con-action ] [ exceed exceed-action ] [ meter-statistic ] |
Required By default, traffic policing is disabled. |
|
Clear the traffic policing statistics |
reset traffic-limit inbound acl-rule |
Optional |
As the priority of traffic classification rules is higher than that of the default rules used for processing protocol packets, configuring traffic policing for all the packets or packets of a VLAN may affect device management that is implemented through Telnet and so on.
Configuration example
l GigabitEthernet 1/0/1 belongs to VLAN 2 and is connected to the 10.1.1.0/24 network segment
l Perform traffic policing on the packets from the 10.1.1.0/24 network segment, setting the rate to 128 kbps
l Mark the DSCP precedence as 56 for the inbound packets exceeding the rate limit.
1) Method I
<device> system-view
[device] acl number 2000
[device-acl-basic-2000] rule permit source 10.1.1.1 0.0.0.255
[device-acl-basic-2000] quit
[device] interface GigabitEthernet1/0/1
[device-GigabitEthernet1/0/1] traffic-limit inbound ip-group 2000 128 exceed remark-dscp 56
2) Method II
<device> system-view
[device] acl number 2000
[device-acl-basic-2000] rule permit source 10.1.1.1 0.0.0.255
[device-acl-basic-2000] quit
[device] traffic-limit vlan 2 inbound ip-group 2000 128 exceed remark-dscp 56
Configuring Traffic Shaping
Refer to Traffic Policing and Traffic Shaping for information about traffic shaping.
Configuration prerequisites
l The queue for which traffic shaping is to be performed is determined.
l The maximum traffic rate and the burst size are determined.
l The port where traffic shaping is to be configured is determined.
Configuration procedure
Follow these steps to configure traffic shaping:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Configure traffic shaping |
traffic-shape [ queue queue-id ] max-rate burst-size |
Required Traffic shaping is not enabled by default. Traffic shaping can be performed in one of the following two modes: l With the queue queue-id keyword and argument combination not specified, traffic shaping is performed for all the traffic. l With the queue queue-id keyword and argument combination specified, traffic shaping is performed for the traffic in the specific output queue. |
Configuration examples
# Perform traffic shaping for all the traffic to be transmitted through GigabitEthernet 1/0/1, with the maximum traffic rate being 640 kbps and the burst size being 16 kbytes.
<device> system-view
[device] interface GigabitEthernet1/0/1
[device-GigabitEthernet1/0/1] traffic-shape 640 16
Configuring Traffic Redirecting
Refer to Traffic Redirecting for information about traffic redirecting.
Configuration prerequisites
l The ACL rules used for traffic classification are defined. Refer to ACL in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide for information about defining ACL rules.
l The port which the packets matching the specified ACL rules are to be redirected to is determined.
Configuration procedure
You can redirect all the packets matching specific ACL rules, or packets that match specific ACL rules and are of a VLAN, of a port group, or pass a port.
Follow these steps to redirect all the packets matching specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure traffic redirecting |
traffic-redirect inbound acl-rule interface interface-type interface-number |
Required |
Follow these steps to redirect packets that are of a VLAN and match specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure traffic redirecting |
traffic-redirect vlan vlan-id inbound acl-rule interface interface-type interface-number |
Required |
Follow these steps to redirect packets that are of a port group and match specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter port group view |
port-group group-id |
— |
|
Configure traffic redirecting |
traffic-redirect inbound acl-rule interface interface-type interface-number |
Required |
Follow these steps to redirect packets passing a port and matching specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Configure traffic redirecting |
traffic-redirect inbound acl-rule interface interface-type interface-number |
Required |
![]()
If the traffic is redirected to a Combo port in down state, the system automatically redirects the traffic to the port corresponding to the Combo port in up state. Refer to Port Basic Configuration in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide for information about Combo ports.
![]()
As the priority of traffic classification rules is higher than that of the default rules used for processing protocol packets, redirecting all the packets or packets of a VLAN may affect device management that is implemented through Telnet and so on.
Configuration example
l GigabitEthernet 1/0/1 belongs to VLAN 2 and is connected to the 10.1.1.0/24 network segment.
l Redirect all the packets from the 10.1.1.0/24 network segment to GigabitEthernet 1/0/7.
1) Method I
<device> system-view
[device] acl number 2000
[device-acl-basic-2000] rule permit source 10.1.1.1 0.0.0.255
[device-acl-basic-2000] quit
[device] interface GigabitEthernet1/0/1
[device-GigabitEthernet1/0/1] traffic-redirect inbound ip-group 2000 interface GigabitEthernet1/0/7
2) Method II
<device> system-view
[device] acl number 2000
[device-acl-basic-2000] rule permit source 10.1.1.1 0.0.0.255
[device-acl-basic-2000] quit
[device] traffic-redirect vlan 2 inbound ip-group 2000 interface GigabitEthernet1/0/7
Configuring VLAN Mapping
Refer to VLAN Mapping for information about VLAN mapping.
Configuration prerequisites
l The ACL rules used for traffic classification are defined. Refer to ACL in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide for information about defining ACL rules.
l The VLAN ID to be marked is determined.
l The ports on which the configuration is to be performed are determined.
Configuration procedure
Follow these steps to configure VLAN mapping:
|
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Configure VLAN mapping |
traffic-remark-vlanid inbound acl-rule remark-vlan vlan-id untagged-packet |
Required By default, VLAN mapping is not configured. |
Configuration example
l GigabitEthernet 1/0/1 belongs to VLAN 2 and is connected to the 10.1.1.0/24 network segment.
l Configure VLAN mapping for all the packets sourced from the 10.1.1.0/24 network segment to map the VLAN IDs of these packets to 1001.
Configuration procedure :
<device> system-view
[device] acl number 2000
[device-acl-basic-2000] rule permit source 10.1.1.1 0.0.0.255
[device-acl-basic-2000] quit
[device] interface GigabitEthernet 1/0/1
[device-GigabitEthernet1/0/1] traffic-remark-vlanid inbound ip-group 2000 remark-vlan 1001
Configuring Queue Scheduling
Refer to Queue Scheduling for information about queue scheduling.
Configuration prerequisites
The algorithm for queue scheduling to be used and the related parameters are determined.
Configuration procedure
Follow these steps to configure SP queue scheduling algorithm:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure SP queue scheduling algorithm |
undo queue-scheduler [ queue-id ] &<1-8> |
Optional By default, SP queue scheduling algorithm is adopted on all the output queues of a port. |
Follow these steps to configure SDWRR queue scheduling algorithm:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure SDWRR queue scheduling algorithm |
queue-scheduler wrr { group1 { queue-id queue-weight } &<1-8> | group2 { queue-id queue-weight } &<1-8> }* |
Required By default, SP queue scheduling algorithm is adopted on all the output queues of a port. |
A port on a device can accommodate up to eight output queues. You can configure to use SP queue scheduling algorithm, SDWRR queue scheduling algorithm, or combine the two as required.
l With SDWRR queue scheduling algorithm adopted, the output queues of a port can be assigned to group 1 and group 2. The two groups are scheduled using SP algorithm. For example, you can assign queue 0, queue 1, queue 2, and queue 3 to group 1, and assign queue 4, queue 5, queue 6, and queue 7 to group 2. The queues in group 2 are scheduled preferentially using WRR queue scheduling algorithm. Queues in group 1 are scheduled using WRR queue scheduling algorithm only when all the queues in group 2 are empty.
l With both SP and SDWRR queue scheduling algorithms adopted, groups are scheduled using SP algorithm. Assume that queue 0 and queue 1 are scheduled using SP algorithm; queue 2, queue 3, and queue 4 are assigned to group 1; queue 5, queue 6, and queue 7 are assigned to group 2. The queues in group 2 are scheduled preferentially using WRR queue scheduling algorithm. When all the queues in group 2 are empty, queues in group 1 are scheduled using WRR queue scheduling algorithm. Then, queue 1 is scheduled, and then queue 0.
![]()
When using SDWRR or SP+SDWRR combination for queue scheduling, you are recommended to assign queues with successive queue numbers to the same scheduling group.
Configuration example
# Configure a device to adopt SP+SDWRR combination for queue scheduling, assigning queue 3, queue 4, and queue 5 to WRR scheduling group 1, with the weigh of 20, 20 and 30; assigning queue 0, queue 1, and queue 2 to WRR scheduling group 2, with the weight 20, 20, and 40; using SP for scheduling queue 6 and queue 7. Display the configuration information after configuration.
Configuration procedure:
<device> system-view
[device] queue-scheduler wrr group1 3 20 4 20 5 30 group2 0 20 1 20 2 40
[device] display queue-scheduler
QID: scheduling-group weight
-----------------------------------
0 : wrr , group2 20
1 : wrr , group2 20
2 : wrr , group2 40
3 : wrr , group1 20
4 : wrr , group1 20
5 : wrr , group1 30
6 : sp 0
7 : sp 0
Collecting/Clearing Traffic Statistics
Refer to Flow-based Traffic Accounting for information about traffic accounting.
Configuration prerequisites
The ACL rules for traffic classification are defined. Refer to ACL in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide for information about defining ACL rules.
Configuration procedure
You can collect traffic statistics or clear traffic statistics on all the packets matching specific ACL rules, or on packets that match specific ACL rules and are of a VLAN, of a port group, or pass a port.
Follow these steps to collect traffic statistics on all the packets matching specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Collect the statistics on the packets matching specific ACL rules |
traffic-statistic inbound acl-rule |
Required |
|
Clear the statistics on the packets matching specific ACL rules |
reset traffic-statistic inbound acl-rule |
Optional |
Follow these steps to collect traffic statistics on packets that are of a VLAN and match specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Collect the statistics on the packets matching specific ACL rules |
traffic-statistic vlan vlan-id inbound acl-rule |
Required |
|
Clear the statistics on the packets matching specific ACL rules |
reset traffic-statistic vlan vlan-id inbound acl-rule |
Optional |
Follow these steps to collect traffic statistics on packets that are of a port group and match specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter port group view |
port-group group-id |
— |
|
Collect the statistics on the packets matching specific ACL rules |
traffic-statistic inbound acl-rule |
Required |
|
Clear the statistics on the packets matching specific ACL rules |
reset traffic-statistic inbound acl-rule |
Optional |
Follow these steps to collect traffic statistics on packets passing a port and matching specific ACL rules:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Collect the statistics on the packets matching specific ACL rules |
traffic-statistic inbound acl-rule |
Required |
|
Clear the statistics on the packets matching specific ACL rules |
reset traffic-statistic inbound acl-rule |
Optional |
![]()
As the priority of traffic classification rules is higher than that of the default rules used for processing protocol packets, collecting traffic statistics on all the packets or packets of a VLAN may affect device management that is implemented through Telnet and so on
Configuration example
l GigabitEthernet 1/0/1 is connected to the 10.1.1.0/24 network segment.
l Collect statistics on the packets sourced from the 10.1.1.0/24 network segment.
l Clear the statistics.
1) Method I
<device> system-view
[device] acl number 2000
[device-acl-basic-2000] rule permit source 10.1.1.1 0.0.0.255
[device-acl-basic-2000] quit
[device] interface GigabitEthernet1/0/1
[device-GigabitEthernet1/0/1] traffic-statistic inbound ip-group 2000
[device-GigabitEthernet1/0/1] reset traffic-statistic inbound ip-group 2000
2) Method II
<device> system-view
[device] acl number 2000
[device-acl-basic-2000] rule permit source 10.1.1.1 0.0.0.255
[device-acl-basic-2000] quit
[device] traffic-statistic vlan 2 inbound ip-group 2000
[device] reset traffic-statistic vlan 2 inbound ip-group 2000
Enabling the Burst Function
Refer to Burst for information about the burst function.
Configuration prerequisites
The burst function is required.
Configuration procedure
Follow these steps to enable the burst function:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable the burst function |
burst-mode enable |
Required By default, the burst function is disabled. |
Configuration example
Enable the burst function on the devicees.
Configuration procedure:
<device> system-view
[device] burst-mode enable
Configuring Traffic Mirroring
Refer to Traffic mirroring for information about traffic mirroring.
Configuration prerequisites
l The ACL rules for traffic classification are defined. Refer to ACL in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide for information about defining ACL rules.
l The source mirroring ports and mirroring direction are determined.
l The destination mirroring port is determined.
Configuration procedure
You can configure traffic mirroring on all the packets matching specific ACL rules, or on packets that match specific ACL rules and are of a VLAN, of a port group, or pass a port.
Follow these steps to configure traffic mirroring globally:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view of the destination port |
interface interface-type interface-number |
— |
|
Define the current port as the destination port |
monitor-port |
Required |
|
Exit current view |
quit |
— |
|
Reference ACLs for identifying traffic flows and perform traffic mirroring for packets that match. |
mirrored-to inbound acl-rule monitor-interface |
Required |
Follow these steps to configure traffic mirroring for a VLAN:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view of the destination port |
interface interface-type interface-number |
— |
|
Define the current port as the destination port |
monitor-port |
Required |
|
Exit current view |
quit |
— |
|
Reference ACLs for identifying traffic flows and perform traffic mirroring for packets that match. |
mirrored-to vlan vlan-id inbound acl-rule monitor-interface |
Required |
Follow these steps to configure traffic mirroring for a port group:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view of the destination port |
interface interface-type interface-number |
— |
|
Define the current port as the destination port |
monitor-port |
Required |
|
Exit current view |
quit |
— |
|
Enter port group view |
port-group group-id |
— |
|
Reference ACLs for identifying traffic flows and perform traffic mirroring for packets that match. |
mirrored-to inbound acl-rule monitor-interface |
Required |
Follow these steps to configure traffic mirroring for a port:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view of the destination port |
interface interface-type interface-number |
— |
|
Define the current port as the destination port |
monitor-port |
Required |
|
Exit current view |
quit |
— |
|
Enter Ethernet port view of traffic mirroring configuration |
interface interface-type interface-number |
— |
|
Reference ACLs for identifying traffic flows and perform traffic mirroring for packets that match. |
mirrored-to inbound acl-rule monitor-interface |
Required |
![]()
As the priority of traffic classification rules is higher than that of the default rules used for processing protocol packets, traffic mirroring on all the packets or packets of a VLAN may affect device management that is implemented through Telnet and so on
Configuration example
Network requirements:
l GigabitEthernet 1/0/1 is connected to the 10.1.1.0/24 network segment.
l Duplicate the packets from network segment 10.1.1.0/24 to the destination mirroring port GigabitEthernet 1/0/4.
1) Method I
<device> system-view
[device] acl number 2000
[device-acl-basic-2000] rule permit source 10.1.1.0 0.0.0.255
[device-acl-basic-2000] quit
[device] interface GigabitEthernet 1/0/4
[device-GigabitEthernet1/0/4] monitor-port
[device-GigabitEthernet1/0/4] quit
[device] interface GigabitEthernet 1/0/1
[device-GigabitEthernet1/0/1] mirrored-to inbound ip-group 2000 monitor-interface
2) Method II
<device> system-view
[device] acl number 2000
[device-acl-basic-2000] rule permit source 10.1.1.0 0.0.0.255
[device-acl-basic-2000] quit
[device] interface GigabitEthernet 1/0/4
[device-GigabitEthernet1/0/4] monitor-port
[device-GigabitEthernet1/0/4] quit
[device] mirrored-to vlan 2 inbound ip-group 2000 monitor-interface
Displaying and Maintaining QoS
|
To do… |
Use the command… |
Remarks |
|
Display the protocol packet priority configuration |
display protocol-priority |
Available in any view |
|
Display the COS-precedence-to-Drop-precedence mapping relationship |
display qos cos-drop-precedence-map |
|
|
Display the COS-precedence-to-DSCP-precedence mapping relationship |
display qos cos-dscp-map |
|
|
Display the COS-precedence-to-local-precedence mapping relationship |
display qos cos-local-precedence-map |
|
|
Display the DSCP-precedence-to-COS-precedence mapping relationship |
display qos dscp-cos-map |
|
|
Display the DSCP-precedence-to-Drop-precedence mapping relationship |
display qos dscp-drop-precedence-map |
|
|
Display the DSCP-precedence-to-DSCP-precedence mapping relationship |
display qos dscp-dscp-map |
|
|
Display the DSCP-precedence-to-local-precedence mapping relationship |
display qos dscp-local-precedence-map |
|
|
Display queue scheduling algorithm and related parameters |
display queue-scheduler |
|
|
Display the QoS-related configuration of a port or all the ports |
display qos-interface { interface-type interface-number | unit-id } all |
|
|
Display the priority trust mode of a port or all the ports |
display qos-interface { interface-type interface-number | unit-id } priority-trust |
|
|
Display traffic shaping configuration of a port or all the ports |
display qos-interface { interface-type interface-number | unit-id } traffic-shape |
|
|
Display traffic policing configuration of a port or all the ports |
display qos-interface { interface-type interface-number | unit-id } traffic-limit |
|
|
Display priority marking configuration of a port or all the ports |
display qos-interface { interface-type interface-number | unit-id } traffic-priority |
|
|
Display traffic redirecting configuration of a port or all the ports |
display qos-interface { interface-type interface-number | unit-id } traffic-redirect |
|
|
Display traffic accounting configuration of a port or all the ports |
display qos-interface { interface-type interface-number | unit-id } traffic-statistic |
|
|
Display VLAN mapping configuration of a port or all the ports |
display qos-interface { interface-type interface-number | unit-id } traffic-remark-vlanid |
|
|
Display traffic mirroring configuration of a port or all the ports |
display qos-interface { interface-type interface-number | unit-id } mirrored-to |
|
|
Display the configuration of traffic mirroring, traffic policing, priority marking, traffic redirecting, or traffic accounting performed for all the packets |
display qos-global { all | mirrored-to | traffic-limit | traffic-priority | traffic-redirect | traffic-statistic } |
|
|
Display the configuration of traffic mirroring, traffic policing, priority marking, traffic redirecting, or traffic accounting performed for packets of a VLAN |
display qos-vlan [ vlan-id ] { all | mirrored-to | traffic-limit | traffic-priority | traffic-redirect | traffic-statistic } |
|
|
Display the configuration of traffic mirroring, traffic policing, priority marking, traffic redirecting, or traffic accounting performed for packets of a port group |
display qos-port-group [ group-id ] { all | mirrored-to | traffic-limit | traffic-priority | traffic-redirect | traffic-statistic } |
QoS Configuration Example
Configuration Example of Traffic Policing
Network requirement
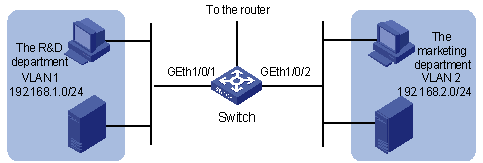
As shown in Figure 1-9, an enterprise network connects all the departments through a device. PC1, with the IP address 192.168.0.1 belongs to the R&D department and is connected to GigabitEthernet 1/0/1 of the switch. The marketing department is connected to GigabitEthernet 1/0/2 of the switch.
Configure traffic policing to satisfy the following requirements:
l Set the maximum rate of outbound IP packets sourced from the marketing department to 64 kbps. Drop the packets exceeding the rate limit.
l Set the maximum rate of outbound IP packets sourced from the R&D department to 128 kbps. Drop the packets exceeding the rate limit.
Figure 1-9 Network diagram for traffic policing and rate limiting configuration
Configuration procedure
1) Define an ACL for traffic classification.
# Create ACL 2000 and enter basic ACL view to classify packets sourced from the 192.168.1.0/24 network segment.
<device> system-view
[device] acl number 2000
[device-acl-basic-2000] rule permit source 192.168.1.0 0.0.0.255
[device-acl-basic-2000] quit
# Create ACL 2001 and enter basic ACL view to classify packets sourced from the 192.168.2.0/24 network segment.
[device] acl number 2001
[device-acl-basic-2001] rule permit source 192.168.2.0 0.0.0.255
[device-acl-basic-2001] quit
2) Configure traffic policing
# Set the maximum rate of outbound IP packets sourced from the marketing department to 64 kbps.
[device] traffic-limit vlan 2 inbound ip-group 2001 64 exceed drop
# Set the maximum rate of outbound IP packets sourced from the R&D department to 128 kbps.
[device] traffic-limit vlan 1 inbound ip-group 2000 128 exceed drop
Overview
Introduction to QoS Profile
QoS profile is a set of QoS configurations. It provides an easy way for performing and managing QoS configuration. A QoS profile can contain one or multiple QoS functions. In networks where hosts change their positions frequently, you can define QoS policies for the hosts and add the QoS policies to a QoS profile. When a host is connected to another port of a device, you can simply apply the corresponding QoS profile to the port to maintain the same QoS configuration performed for the host.
QoS Profile Application Mode
Dynamic application mode
A QoS profile can be applied dynamically to a user or a group of users passing 802.1x authentication. To apply QoS profiles dynamically, a user name-to-QoS profile mapping table is required on the AAA server. For a device operating in this mode, after a user passes the 802.1x authentication, the device looks up the user name-to-QoS profile mapping table for the QoS profile using the user name and then applies the QoS profile found to the port the user is connected to.
Corresponding to the 802.1x authentication modes, dynamic QoS profile application can be user-based and port-based.
l User-based QoS profile application
The device generates a new QoS profile by adding user source MAC address information to the identifying rule defined in the existing QoS profile and then applies the new QoS profile to the port the user is connected to.
l Port-based QoS profile application
The device directly applies the QoS profile to the port the user is connected to.
![]()
A user-based QoS profile application fails if the traffic classification rule defined in the QoS profile contains source address information (including source MAC address, source IP address, or both).
Manual application mode
You can use the apply command to manually apply a QoS profile to a port.
QoS Profile Configuration
QoS Profile Configuration Task List
Complete the following tasks to configure a QoS profile:
|
Task |
Remarks |
|
Required |
|
|
Optional |
|
|
Optional |
Configuring a QoS Profile
Configuration prerequisites
l The ACL rules used for traffic classification are defined. Refer to ACL in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide for information about defining ACL rules.
l The type and number of actions in the QoS profile are specified.
Configuration procedure
Follow these steps to configure a QoS profile:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Create a QoS profile and enter QoS profile view |
qos-profile profile-name |
— |
|
Configure traffic policing |
traffic-limit inbound acl-rule target-rate [ conform con-action ] [ exceed exceed-action ] [ meter-statistic ] |
Optional |
|
Configure packet filtering |
packet-filter inbound acl-rule |
Optional Refer to ACL in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide for information about packet filtering. |
|
Configure priority marking |
traffic-priority inbound acl-rule { dscp dscp-value | cos cos-value } |
Optional |
Applying a QoS Profile
You can configure to apply a QoS profile dynamically or simply apply a QoS profile manually.
Configuration prerequisites
l To configure to apply a QoS profile dynamically, make sure 802.1x is enabled both globally and on the port, and the authentication mode is determined. For information about 802.1x, refer to 802.1x and System Guard in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide.
l To apply a QoS profile manually, make sure the port to which the QoS profile is to be applied is determined.
l The QoS profile to be applied is determined.
Configuration procedure
Follow these steps to configure to apply a QoS profile dynamically:
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
|
Specify the mode to apply a QoS profile |
Configure the mode to apply a QoS profile as port-based |
qos-profile port-based |
Optional By default, the mode to apply a QoS profile is user-based. l If the 802.1x authentication mode is MAC address-based, the mode to apply a QoS profile must be configured user-based. l If the 802.1x authentication mode is port-based, the mode to apply a QoS profile must be configured as port-based. |
|
Configure the mode to apply a QoS profile as user-based |
undo qos-profile port-based |
||
Follow these steps to apply a QoS profile manually:
|
To do… |
Use the command… |
Remarks |
||
|
Enter system view |
system-view |
— |
||
|
Apply a QoS profile to specific ports |
In system view |
apply qos-profile profile-name interface interface-list |
Select either of the operations. By default, a port has no QoS profile applied to it. |
|
|
In Ethernet port view |
Enter Ethernet port view |
interface interface-type interface-number |
||
|
Apply a QoS profile to the current port |
apply qos-profile profile-name |
|||
Displaying and Maintaining QoS Profile
|
To do… |
Use the command… |
Remarks |
|
Display QoS profile configuration |
display qos-profile { all | name profile-name | interface interface-type interface-number | user user-name } |
Available in any view |
Configuration Example
QoS Profile Configuration Example
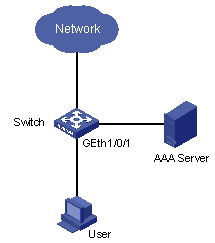
Network requirements
As shown in Figure 2-1, the user name is “someone”, and the authentication password is “hello”. It is connected to GigabitEthernet 1/0/1 of the switch and belongs to the test.net domain.
It is required to configure a QoS profile to limit the rate of all the outbound IP packets of the user to 128 kbps and configuring to drop the packets exceeding the target packet rate.
Figure 2-1 Network diagram for QoS profile configuration
Configuration procedure
1) Configuration on the AAA server
# Configure the user authentication information and the matching relationship between the user name and the QoS profile. Refer to the user manual of the AAA server for detailed configuration.
2) Configuration on the switch
# Configure IP addresses for the RADIUS server.
<device> system-view
[device] radius scheme radius1
[device-radius-radius1] primary authentication 10.11.1.1
[device-radius-radius1] primary accounting 10.11.1.2
[device-radius-radius1] secondary authentication 10.11.1.2
[device-radius-radius1] secondary accounting 10.11.1.1
# Set the encryption passwords for the device to exchange packets with the authentication RADIUS servers and accounting RADIUS servers.
[device-radius-radius1] key authentication money
[device-radius-radius1] key accounting money
# Configure the device to delete the user domain name from the user name and then send the user name to the RADIUS sever.
[device-radius-radius1] user-name-format without-domain
[device-radius-radius1] quit
# Create the user domain test.net and specify radius1 as your RADIUS server group.
[device] domain test.net
[device-isp-test.net] radius-scheme radius1
[device-isp-test.net] quit
# Create ACL 3000 to permit IP packets destined for any IP address.
[device] acl number 3000
[device-acl-adv-3000] rule 1 permit ip destination any
[device-acl-adv-3000] quit
# Define a QoS profile named “example” to limit the rate of matched packets to 128 kbps and configuring to drop the packets exceeding the target packet rate.
[device] qos-profile example
[device-qos-profile-example] traffic-limit inbound ip-group 3000 128 exceed drop
# Enable 802.1x.
[device] dot1x
[device] dot1x interface GigabitEthernet1/0/1
After the configuration, the QoS profile named “example” will be applied to the user with user name “someone” automatically after the user passes the authentication.
