- Table of Contents
-
- H3C WX3000 Series Unified Switches Switching Engine Configuration Guide-6W103
- 00-Preface
- 01-CLI Configuration
- 02-Login Configuration
- 03-Configuration File Management Configuration
- 04-VLAN Configuration
- 05-Auto Detect Configuration
- 06-Voice VLAN Configuration
- 07-GVRP Configuration
- 08-Basic Port Configuration
- 09-Link Aggregation Configuration
- 10-Port Isolation Configuration
- 11-Port Security-Port Binding Configuration
- 12-DLDP Configuration
- 13-MAC Address Table Management Configuration
- 14-MSTP Configuration
- 15-802.1x and System Guard Configuration
- 16-AAA Configuration
- 17-MAC Address Authentication Configuration
- 18-IP Address and Performance Configuration
- 19-DHCP Configuration
- 20-ACL Configuration
- 21-QoS-QoS Profile Configuration
- 22-Mirroring Configuration
- 23-ARP Configuration
- 24-SNMP-RMON Configuration
- 25-Multicast Configuration
- 26-NTP Configuration
- 27-SSH Configuration
- 28-File System Management Configuration
- 29-FTP-SFTP-TFTP Configuration
- 30-Information Center Configuration
- 31-System Maintenance and Debugging Configuration
- 32-VLAN-VPN Configuration
- 33-HWPing Configuration
- 34-DNS Configuration
- 35-Smart Link-Monitor Link Configuration
- 36-PoE-PoE Profile Configuration
- 37-Routing Protocol Configuration
- 38-UDP Helper Configuration
- 39-Acronyms
- 40-Index
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 11-Port Security-Port Binding Configuration | 152.65 KB |
Table of Contents
Setting the Maximum Number of MAC Addresses Allowed on a Port
Setting the Port Security Mode
Configuring Port Security Features
Ignoring the Authorization Information from the RADIUS Server
Configuring Security MAC Addresses
Displaying and Maintaining Port Security Configuration
Port Security Configuration Example
Displaying and Maintaining Port Binding Configuration
Port Binding Configuration Example
![]()
l The term switch used throughout this chapter refers to a switching device in a generic sense or the switching engine of a unified switch in the WX3000 series.
l The sample output information in this manual was created on the WX3024. The output information on your device may vary.
Port Security Overview
Introduction
Port security is a security mechanism for network access control. It is an expansion to the current 802.1x and MAC address authentication.
Port security allows you to define various security modes that enable devices to learn legal source MAC addresses, so that you can implement different network security management as needed.
With port security enabled, packets whose source MAC addresses cannot be learned by the device in the security mode are considered illegal packets. The events that cannot pass 802.1x authentication or MAC authentication are considered illegal.
With port security enabled, upon detecting an illegal packet or illegal event, the system triggers the corresponding port security features and takes pre-defined actions automatically. This reduces your maintenance workload and greatly enhances system security and manageability.
Port Security Features
The following port security features are provided:
l NTK (need to know) feature: By checking the destination MAC addresses in outbound data frames on the port, NTK ensures that the device sends data frames through the port only to successfully authenticated devices, thus preventing illegal devices from intercepting network data.
l Intrusion protection feature: By checking the source MAC addresses in inbound data frames or the username and password in 802.1x authentication requests on the port, intrusion protection detects illegal packets or events and takes a pre-set action accordingly. The actions you can set include: disconnecting the port temporarily/permanently, and blocking packets with the MAC address specified as illegal.
l Trap feature: When special data packets (generated from illegal intrusion, abnormal login/logout or other special activities) are passing through a port on the device, device tracking enables the switch to send Trap messages to help the network administrator monitor special activities.
Port Security Modes
Table 1-1 describes the available port security modes.
Table 1-1 Description of port security modes
|
Security mode |
Description |
Feature |
|
noRestriction |
Port security is disabled on the port and access to the port is not restricted. |
In this mode, neither the NTK nor the intrusion protection feature is triggered. |
|
autolearn |
In this mode, a port can learn a specified number of MAC addresses and save those addresses as secure MAC addresses. When the number of secure MAC addresses reaches the upper limit, the port changes to work in secure mode and permits only frames whose source MAC addresses are secure MAC addresses or static MAC addresses configured by using the mac-address static command. |
In either mode, the device will trigger NTK and intrusion protection upon detecting an illegal packet. |
|
secure |
In this mode, the port is disabled from learning MAC addresses. Only those packets whose source MAC addresses are security MAC addresses learned and static or dynamic MAC addresses can pass through the port. |
|
|
userlogin |
In this mode, port-based 802.1x authentication is performed for access users. |
In this mode, neither NTK nor intrusion protection will be triggered. |
|
userLoginSecure |
In this mode, a port performs 802.1x authentication of users and services only one user passing 802.1x authentication at a time. |
In any of these modes, the device triggers the NTK and Intrusion Protection features upon detecting an illegal packet or illegal event. |
|
userLoginSecureExt |
In this mode, a port performs 802.1x authentication of users and services users passing 802.1x authentication. |
|
|
userLoginWithOUI |
Similar to the userLoginSecure mode, a port in this mode performs 802.1x authentication of users and services only one user passing 802.1x authentication. The differences include: Such a port also permits frames from a wired user whose MAC address contains a specified OUI (organizationally unique identifier). For frames from a wireless user, such a port performs OUI check at first. If the OUI check fails, the port performs 802.1x authentication. |
|
|
macAddressWithRadius |
In this mode, a port performs RADIUS MAC authentication of users. |
|
|
macAddressOrUserLoginSecure |
This mode is the combination of the userLoginSecure and macAddressWithRadius modes, with 802.1x authentication having a higher priority than MAC authentication. For a user using a wired connection, the port performs MAC authentication upon receiving non-802.1x frames and performs 802.1x authentication first upon receiving 802.1x frames. If 802.1x authentication fails, the port performs MAC authentication. For a wireless user, 802.1x authentication is performed first. If 802.1x authentication fails, MAC authentication is performed. |
|
|
macAddressOrUserLoginSecureExt |
This mode is similar to the macAddressOrUserLoginSecure mode, except that there can be more than one 802.1x authenticated user on the port. |
|
|
macAddressElseUserLoginSecure |
This mode is the combination of the macAddressWithRadius and userLoginSecure modes, with MAC authentication having a higher priority than 802.1x authentication. Upon receiving a non-802.1x frame, a port in this mode performs only MAC authentication. Upon receiving an 802.1x frame, the port performs MAC authentication and then, if MAC authentication fails, 802.1x authentication. |
|
|
macAddressElseUserLoginSecureExt |
This mode is similar to the macAddressElseUserLoginSecure mode, except that there can be more than one 802.1x/MAC authenticated user on the port. |
|
|
macAddressAndUserLoginSecure |
To perform 802.1x authentication on the access user, MAC authentication must be performed first. 802.1x authentication can be performed on the access user only if MAC authentication succeeds. In this mode there can be only one authenticated user on the port. |
|
|
macAddressAndUserLoginSecureExt |
This mode is similar to the macAddressAndUserLoginSecure mode, except that there can be more than one authenticated user on the port. |
Port Security Configuration
Complete the following tasks to configure port security:
|
Task |
Remarks |
|
|
Required |
||
|
Setting the Maximum Number of MAC Addresses Allowed on a Port |
Optional |
|
|
Required |
||
|
Optional Choose one or more features as required. |
||
|
Ignoring the Authorization Information from the RADIUS Server |
Optional |
|
|
Optional |
||
Enabling Port Security
Follow these steps to enable port security:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable port security |
port-security enable |
Required Disabled by default |
![]()
Enabling port security resets the following configurations on the ports to the defaults (shown in parentheses below):
l 802.1x (disabled), port access control method (macbased), and port access control mode (auto)
l MAC authentication (disabled)
In addition, you cannot perform the above-mentioned configurations manually because these configurations change with the port security mode automatically.
![]()
l For details about 802.1x configuration, refer to 802.1x and System-Guard in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide.
l For details about MAC authentication configuration, refer to MAC Address Authentication in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide.
Setting the Maximum Number of MAC Addresses Allowed on a Port
Port security allows more than one user to be authenticated on a port. The number of authenticated users allowed, however, cannot exceed the configured upper limit.
By setting the maximum number of MAC addresses allowed on a port, you can
l Control the maximum number of users who are allowed to access the network through the port
l Control the number of Security MAC addresses that can be added with port security
This configuration is different from that of the maximum number of MAC addresses that can be leaned by a port in MAC address management.
Follow these steps to set the maximum number of MAC addresses allowed on a port:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Set the maximum number of MAC addresses allowed on the port |
port-security max-mac-count count-value |
Required Not limited by default |
![]()
l Assume that, in the macAddressOrUserLoginSecureExt port security mode, you have configured to allow up to n authenticated users to access the network. When all of these n authenticated users are connected to the network and one or more of them are MAC-authenticated, to perform 802.1x authentication on the MAC-authenticated user(s), the number of maximum MAC addresses allowed on the port must be set to n + 1. Similarly, in the case of the macAddressOrUserLoginSecure security mode, the maximum number of MAC addresses allowed on the port must be set to 2.
l In the macAddressAndUserLoginSecureExt port security mode, to allow up to n authenticated users to be connected to the network at the same time and the nth user to be 802.1x-authenticated, the maximum number of MAC addresses allowed on the port must be set to at least n + 1. Similarly, in the case of the macAddressAndUserLoginSecure security mode, the maximum number of MAC addresses allowed on the port must be set to 2.
Setting the Port Security Mode
Follow these steps to set the port security mode:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Set the OUI value for user authentication |
port-security oui OUI-value index index-value |
Optional In userLoginWithOUI mode, a port supports one 802.1x user plus one user whose source MAC address has a specified OUI value. |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Set the port security mode |
port-security port-mode { autolearn | mac-and-userlogin-secure | mac-and-userlogin-secure-ext | mac-authentication | mac-else-userlogin-secure | mac-else-userlogin-secure-ext | secure | userlogin | userlogin-secure | userlogin-secure-ext | userlogin-secure-or-mac | userlogin-secure-or-mac-ext | userlogin-withoui } |
Required By default, a port operates in noRestriction mode. In this mode, access to the port is not restricted. You can set a port security mode as needed. |
![]()
l Before setting the port security mode to autolearn, you need to set the maximum number of MAC addresses allowed on the port with the port-security max-mac-count command.
l After you set the port security mode to autolearn, you cannot configure any static or blackhole MAC addresses on the port.
l If the port is in a security mode other than noRestriction, before you can change the port security mode, you need to restore the port security mode to noRestriction with the undo port-security port-mode command.
If the port-security port-mode mode command has been executed on a port, none of the following can be configured on the same port:
l Maximum number of MAC addresses that the port can learn
l Reflector port for port mirroring
l Link aggregation
Configuring Port Security Features
Configuring the NTK feature
Follow these steps to configure the NTK feature:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Configure the NTK feature |
port-security ntk-mode { ntkonly | ntk-withbroadcasts | ntk-withmulticasts } |
Required Be default, NTK is disabled on a port, namely all frames are allowed to be sent. |
![]()
The WX3000 series devices do not support the ntkonly NTK feature.
Configuring intrusion protection
Follow these steps to configure the intrusion protection feature:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Set the corresponding action to be taken by the device when intrusion protection is triggered |
port-security intrusion-mode { disableport | disableport-temporarily | blockmac } |
Required By default, no action is taken when intrusion protection is triggered. |
|
Return to system view |
quit |
— |
|
Set the timer during which the port remains disabled |
port-security timer disableport timer |
Optional 20 seconds by default |
![]()
The port-security timer disableport command is used in conjunction with the port-security intrusion-mode disableport-temporarily command to set the length of time during which the port remains disabled.
![]()
If you configure the NTK feature and execute the port-security intrusion-mode blockmac command on the same port, the device will be unable to disable the packets whose destination MAC address is illegal from being sent out that port; that is, the NTK feature configured will not take effect on the packets whose destination MAC address is illegal.
Configuring the Trap feature
Follow these steps to configure port security trapping:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable sending traps for the specified type of event |
port-security trap { addresslearned | intrusion | dot1xlogon | dot1xlogoff | dot1xlogfailure | ralmlogon | ralmlogoff | ralmlogfailure } |
Required By default, no trap is sent. |
Ignoring the Authorization Information from the RADIUS Server
After an 802.1x user or MAC-authenticated user passes Remote Authentication Dial-In User Service (RADIUS) authentication, the RADIUS server delivers the authorization information to the device. You can configure a port to ignore the authorization information from the RADIUS server.
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Ignore the authorization information from the RADIUS server |
port-security authorization ignore |
Required By default, a port uses the authorization information from the RADIUS server. |
Configuring Security MAC Addresses
Security MAC addresses are special MAC addresses that never age out. One security MAC address can be added to only one port in the same VLAN so that you can bind a MAC address to one port in the same VLAN.
Security MAC addresses can be learned by the auto-learn function of port security or manually configured.
Before adding security MAC addresses to a port, you must configure the port security mode to autolearn. After this configuration, the port changes its way of learning MAC addresses as follows.
l The port deletes original dynamic MAC addresses;
l If the amount of security MAC addresses has not yet reach the maximum number, the port will learn new MAC addresses and turn them to security MAC addresses;
l If the amount of security MAC addresses reaches the maximum number, the port will not be able to learn new MAC addresses and the port mode will be changed from autolearn to secure.
![]()
The security MAC addresses manually configured are written to the configuration file; they will not get lost when the port is up or down. As long as the configuration file is saved, the security MAC addresses can be restored after the device reboots.
Configuration prerequisites
l Port security is enabled.
l The maximum number of security MAC addresses allowed on the port is set.
l The security mode of the port is set to autolearn.
Configuration procedure
Follow these steps to configure a security MAC address
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Add a security MAC address |
In system view |
mac-address security mac-address interface interface-type interface-number vlan vlan-id |
Either is required. By default, no security MAC address is configured. |
|
In Ethernet port view |
interface interface-type interface-number |
||
|
mac-address security mac-address vlan vlan-id |
|||
Displaying and Maintaining Port Security Configuration
|
To do… |
Use the command… |
Remarks |
|
Display information about port security configuration |
display port-security [ interface interface-list ] |
Available in any view |
|
Display information about security MAC address configuration |
display mac-address security [ interface interface-type interface-number ] [ vlan vlan-id ] [ count ] |
Port Security Configuration Example
Network requirements
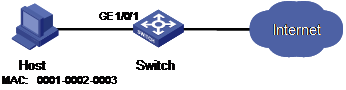
As shown in Figure 1-1, implement access user restrictions through the following configuration on GigabitEthernet 1/0/1 of the switch.
l Allow a maximum of 80 users to access the port without authentication and permit the port to learn and add the MAC addresses of the users as security MAC addresses.
l To ensure that Host can access the network, add the MAC address 0001-0002-0003 of Host as a security MAC address to the port in VLAN 1.
l After the number of security MAC addresses reaches 80, the port stops learning MAC addresses. If any frame with an unknown MAC address arrives, intrusion protection is triggered and the port will be disabled and stay silent for 30 seconds.
Figure 1-1 Network diagram for port security configuration
Configuration procedure
# Enter system view.
<device> system-view
# Enable port security.
[device] port-security enable
# Enter GigabitEthernet 1/0/1 port view.
[device] interface GigabitEthernet 1/0/1
# Set the maximum number of MAC addresses allowed on the port to 80.
[device-GigabitEthernet1/0/1] port-security max-mac-count 80
# Set the port security mode to autolearn.
[device-GigabitEthernet1/0/1] port-security port-mode autolearn
# Add the MAC address 0001-0002-0003 of Host as a security MAC address to the port in VLAN 1.
[device-GigabitEthernet1/0/1] mac-address security 0001-0002-0003 vlan 1
# Configure the port to be silent for 30 seconds after intrusion protection is triggered.
[device-GigabitEthernet1/0/1] port-security intrusion-mode disableport-temporarily
[device-GigabitEthernet1/0/1] quit
[device] port-security timer disableport 30
2 Port Binding Configuration
Port Binding Overview
Introduction
Port binding enables the network administrator to bind the MAC address and IP address of a user to a specific port. After the binding, the switch forwards only the packets received on the port whose MAC address and IP address are identical with the bound MAC address and IP address. This improves network security and enhances security monitoring.
Configuring Port Binding
Follow these steps to configure port binding:
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Bind the MAC address and IP address of a user to a specific port |
In system view |
am user-bind mac-addr mac-address ip-addr ip-address interface interface-type interface-number |
User either approach. By default, no user MAC address or IP address is bound to a port. |
|
In Ethernet port view |
interface interface-type interface-number |
||
|
am user-bind mac-addr mac-address ip-addr ip-address |
|||
![]()
l An IP address can be bound to only one port at a time.
l A MAC address can be bound to only one port at a time.
Displaying and Maintaining Port Binding Configuration
|
To do… |
Use the command… |
Remarks |
|
Display port binding information |
display am user-bind [ interface interface-type interface-number | ip-addr ip-addr | mac-addr mac-addr ] |
Available in any view |
Port Binding Configuration Example
Network requirements
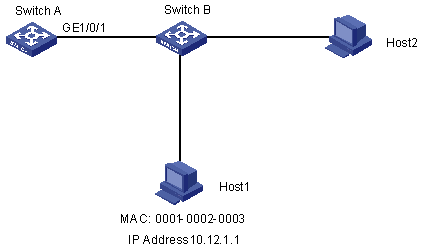
As shown in Figure 2-1, it is required to bind the MAC and IP addresses of Host 1 to GigabitEthernet 1/0/1 on switch A, so as to prevent malicious users from using the IP address they steal from Host 1 to access the network.
Figure 2-1 Network diagram for port binding configuration
Configuration procedure
Configure switch A as follows:
# Enter system view.
<device> system-view
# Enter GigabitEthernet 1/0/1 port view.
[device] interface GigabitEthernet 1/0/1
# Bind the MAC address and the IP address of Host 1 to GigabitEthernet 1/0/1.
[device-GigabitEthernet1/0/1] am user-bind mac-addr 0001-0002-0003 ip-addr 10.12.1.1
