- Table of Contents
-
- H3C WX3000 Series Unified Switches Switching Engine Configuration Guide-6W103
- 00-Preface
- 01-CLI Configuration
- 02-Login Configuration
- 03-Configuration File Management Configuration
- 04-VLAN Configuration
- 05-Auto Detect Configuration
- 06-Voice VLAN Configuration
- 07-GVRP Configuration
- 08-Basic Port Configuration
- 09-Link Aggregation Configuration
- 10-Port Isolation Configuration
- 11-Port Security-Port Binding Configuration
- 12-DLDP Configuration
- 13-MAC Address Table Management Configuration
- 14-MSTP Configuration
- 15-802.1x and System Guard Configuration
- 16-AAA Configuration
- 17-MAC Address Authentication Configuration
- 18-IP Address and Performance Configuration
- 19-DHCP Configuration
- 20-ACL Configuration
- 21-QoS-QoS Profile Configuration
- 22-Mirroring Configuration
- 23-ARP Configuration
- 24-SNMP-RMON Configuration
- 25-Multicast Configuration
- 26-NTP Configuration
- 27-SSH Configuration
- 28-File System Management Configuration
- 29-FTP-SFTP-TFTP Configuration
- 30-Information Center Configuration
- 31-System Maintenance and Debugging Configuration
- 32-VLAN-VPN Configuration
- 33-HWPing Configuration
- 34-DNS Configuration
- 35-Smart Link-Monitor Link Configuration
- 36-PoE-PoE Profile Configuration
- 37-Routing Protocol Configuration
- 38-UDP Helper Configuration
- 39-Acronyms
- 40-Index
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 04-VLAN Configuration | 220.59 KB |
Introduction to Protocol-Based VLAN·
Encapsulation Format of Ethernet Data
Procedure for the Switch to Judge Packet Protocol
Implementation of Protocol-Based VLAN·
Basic VLAN Interface Configuration
Displaying and Maintaining VLAN
Protocol-Based VLAN Configuration Example
Configuring a Protocol-Based VLAN·
Configuring a Protocol Template for a Protocol-Based VLAN
Associating a Port with a Protocol-Based VLAN
Displaying and Maintaining Protocol-Based VLAN
Protocol-Based VLAN Configuration Example
![]()
l The term switch used throughout this chapter refers to a switching device in a generic sense or the switching engine of a unified switch in the WX3000 series.
l The sample output information in this manual was created on the WX3024. The output information on your device may vary.
VLAN Overview
Introduction to VLAN
The traditional Ethernet is a broadcast network, where all hosts are in the same broadcast domain and connected with each other through hubs or switches. Hubs and switches, which are the basic network connection devices, have limited forwarding functions.
l A hub is a physical layer device without the switching function, so it forwards the received packet to all ports except the inbound port of the packet.
l A switch is a link layer device which can forward a packet according to the MAC address of the packet. However, when the switch receives a broadcast packet or an unknown unicast packet whose MAC address is not included in the MAC address table of the switch, it will forward the packet to all the ports except the inbound port of the packet.
The above scenarios could result in the following network problems.
l Large quantity of broadcast packets or unknown unicast packets may exist in a network, wasting network resources.
l A host in the network receives a lot of packets whose destination is not the host itself, causing potential serious security problems.
Isolating broadcast domains is the solution for the above problems. The traditional way is to use routers, which forward packets according to the destination IP address and does not forward broadcast packets in the link layer. However, routers are expensive and provide few ports, so they cannot split the network efficiently. Therefore, using routers to isolate broadcast domains has many limitations.
The virtual local area network (VLAN) technology is developed for switches to control broadcasts in LANs.
A VLAN can span across physical spaces. This enables hosts in a VLAN to be located in different physical locations.
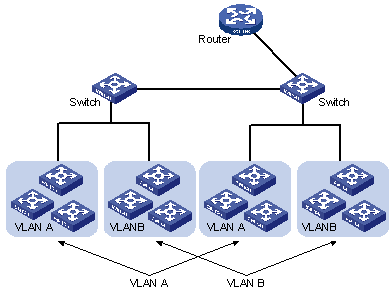
By creating VLANs in a physical LAN, you can divide the LAN into multiple logical LANs, each of which has a broadcast domain of its own. Hosts in the same VLAN communicate in the traditional Ethernet way. However, hosts in different VLANs cannot communicate with each other directly but need the help of network layer devices, such as routers and Layer 3 switches. Figure 1-1 illustrates a VLAN implementation.
Figure 1-1 A VLAN implementation
Advantages of VLANs
Compared with the traditional Ethernet, VLAN enjoys the following advantages.
l Broadcasts are confined to VLANs. This decreases bandwidth consumption and improves network performance.
l Network security is improved. Because each VLAN forms a broadcast domain, hosts in different VLANs cannot communicate with each other directly unless routers or Layer 3 switches are used.
l A more flexible way to establish virtual workgroups. VLAN can be used to create a virtual workgroup spanning physical network segments. When the physical position of a host changes within the range of the virtual workgroup, the host can access the network without changing its network configuration.
How VLAN Works
VLAN tag
VLAN tags in the packets are necessary for a switch to identify packets of different VLANs. A switch works at the data link layer of the OSI model (Layer 3 switches are not discussed in this chapter) and it can identify the data link layer encapsulation of the packet only, so you need to add the VLAN tag field into the data link layer encapsulation if necessary.
In 1999, IEEE issues the IEEE 802.1Q protocol to standardize VLAN implementation, defining the structure of VLAN-tagged packets.
In traditional Ethernet data frames, the type field of the upper layer protocol is encapsulated after the destination MAC address and source MAC address, as shown in Figure 1-2
Figure 1-2 Encapsulation format of traditional Ethernet frames
![]()
In Figure 1-2 DA refers to the destination MAC address, SA refers to the source MAC address, and Type refers to the upper layer protocol type of the packet. IEEE 802.1Q protocol defines that a 4-byte VLAN tag is encapsulated after the destination MAC address and source MAC address to show the information about VLAN.
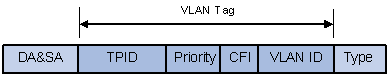
As shown in Figure 1-3, a VLAN tag contains four fields, including the tag protocol identifier (TPID), priority, canonical format indicator (CFI), and VLAN ID.
l TPID is a 16-bit field, indicating that this data frame is VLAN-tagged. By default, it is 0x8100 in the WX3000 series devices.
l Priority is a 3-bit field, referring to 802.1p priority. Refer to QoS-QoS profile in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide of this manual for details.
l CFI is a 1-bit field, indicating whether the MAC address is encapsulated in the standard format. 0 (the value of the CFI filed) indicates the MAC address is encapsulated in the standard format and 1 indicates the MAC address is not encapsulated in the standard format. The value is 0 by default.
l VLAN ID is a 12-bit field, indicating the ID of the VLAN to which this packet belongs. It is in the range of 0 to 4,095. Generally, 0 and 4,095 is not used, so the field is in the range of 1 to 4,094.
![]()
The frame format here takes the Ethernet II encapsulation as an example. Ethernet also supports 802.2/802.3 encapsulation, where VLAN tag is also encapsulated after the DA and SA field. Refer to Encapsulation Format of Ethernet Data for 802.2/802.3 encapsulation format.
VLAN ID identifies the VLAN to which a packet belongs. When a switch receives a packet carrying no VLAN tag, the switch encapsulates a VLAN tag with the default VLAN ID of the inbound port for the packet, and sends the packet to the default VLAN of the inbound port for transmission. For the details about setting the default VLAN of a port, refer to the default VLAN ID configuration of a port section in Port Basic Configuration in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide.
MAC address learning mechanism of VLANs
Switches forward packets according to the destination MAC addresses of the packets. So that switches maintain a table called MAC address forwarding table to record the source MAC addresses of the received packets and the corresponding ports receiving the packets for consequent packet forwarding. The process of recording is called MAC address learning.
After VLANs are configured on a switch, the MAC address learning of the switch has the following two modes.
l Shared VLAN learning (SVL): the switch records all the MAC address entries learnt by ports in all VLANs to a shared MAC address forwarding table. Packets received on any port of any VLAN are forwarded according to this table.
l Independent VLAN learning (IVL): the switch maintains an independent MAC address forwarding table for each VLAN. The source MAC address of a packet received on a port of a VLAN is recorded to the MAC address forwarding table of this VLAN only, and packets received on a port of a VLAN are forwarded according to the VLAN’s own MAC address forwarding table.
VLAN Interface
Hosts in different VLANs cannot communicate with each other directly unless routers or Layer 3 switches are used to do Layer 3 forwarding. The device supports VLAN interfaces configuration to forward packets in Layer 3.
VLAN interface is a virtual interface in Layer 3 mode, used to realize the layer 3 communication between different VLANs, and does not exist on a switch as a physical entity. Each VLAN has a VLAN interface, which can forward packets of the local VLAN to the destination IP addresses at the network layer. Normally, since VLANs can isolate broadcast domains, each VLAN corresponds to an IP network segment. And a VLAN interface serves as the gateway of the segment to forward packets in Layer 3 based on IP addresses.
![]()
The switching engine used in the device can be configured with a maximum number of eight VLAN interfaces.
VLAN Classification
Depending on how VLANs are established, VLANs fall into the following six categories.
l Port-based VLANs
l MAC address-based VLANs
l Protocol-based VLANs
l IP-subnet-based VLANs
l Policy-based VLANs
l Other types
Port-Based VLAN
Port-based VLAN technology introduces the simplest way to classify VLANs. You can assign the ports on the device to different VLANs. Thus packets received on a port will be transmitted through the corresponding VLAN only, so as to isolate hosts to different broadcast domains and divide them into different virtual workgroups.
The link type of a port on the device can be one of the following: access, trunk, and hybrid. For the three types of ports, the process of being added into a VLAN and the way of forwarding packets are different. For details, refer to Port Basic Configuration in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide.
Port-based VLANs are easy to implement and manage and applicable to hosts with relatively fixed positions.
Protocol-Based VLAN
Introduction to Protocol-Based VLAN
Protocol-based VLAN is also known as protocol VLAN, which is another way to classify VLANs. Through the protocol-based VLANs, the switch can analyze the received packets carrying no VLAN tag on the port and match the packets with the user-defined protocol template automatically according to different encapsulation formats and the values of specific fields. If a packet is matched, the switch will add a corresponding VLAN tag to it automatically. Thus, data of specific protocol is assigned automatically to the corresponding VLAN for transmission.
This feature is used for binding the types of services provided in the network to VLANs to facilitate management and maintenance.
Encapsulation Format of Ethernet Data
This section introduces the common encapsulation formats of Ethernet data for you to understand well the procedure for the switch to identify the packet protocols.
Ethernet II and 802.2/802.3 encapsulation
Mainly, there are two encapsulation types of Ethernet packets: Ethernet II and 802.2/802.3, defined by RFC 894 and RFC 1042 respectively. The two encapsulation formats are described in the following figures.
l Ethernet II packet:
Figure 1-4 Ethernet II encapsulation format
![]()
l 802.2/802.3 packet:
Figure 1-5 802.2/802.3 encapsulation format
![]()
In the two figures, DA and SA refer to the destination MAC address and source MAC address of the packet respectively. The number in the bracket indicates the field length in bytes.
The maximum length of an Ethernet packet is 1500 bytes, that is, 0x05DC in hexadecimal, so the length field in 802.2/802.3 encapsulation is in the range of 0x0000 to 0x05DC.
Whereas, the type field in Ethernet II encapsulation is in the range of 0x0600 to 0xFFFF.
Packets with the value of the type or length field being in the range 0x05DD to 0x05FF are regarded as illegal packets and thus discarded directly.
The switch identifies whether a packet is an Ethernet II packet or an 802.2/802.3 packet according to the ranges of the two fields.
Extended encapsulation formats of 802.2/802.3 packets
802.2/802.3 packets have the following three extended encapsulation formats:
l 802.3 raw encapsulation: only the length field is encapsulated after the source and destination address field, followed by the upper layer data. No other fields are included.
Figure 1-6 802.3 raw encapsulation format
![]()
Currently, only the IPX protocol supports 802.3 raw encapsulation, featuring with the value of the two bytes after the length field being 0xFFFF.
l 802.2 logical link control (LLC) encapsulation: the length field, the destination service access point (DSAP) field, the source service access point (SSAP) field and the control field are encapsulated after the source and destination address field. The value of the control field is always 3.
Figure 1-7 802.2 LLC encapsulation format
![]()
The DSAP field and the SSAP field in the 802.2 LLC encapsulation are used to identify the upper layer protocol. For example, if the two fields are both 0xE0, the upper layer protocol is IPX protocol.
l 802.2 sub-network access protocol (SNAP) encapsulation: encapsulates packets according to the 802.3 standard packet format, including the length, DSAP, SSAP, control, organizationally unique identifier (OUI), and protocol-ID (PID) fields.
Figure 1-8 802.2 SNAP encapsulation format
![]()
In 802.2 SNAP encapsulation format, the values of the DSAP field and the SSAP field are always 0xAA, and the value of the control field is always 3.
The switch differentiates between 802.2 LLC encapsulation and 802.2 SNAP encapsulation according to the values of the DSAP field and the SSAP field.
![]()
When the OUI is 00-00-00 in 802.2 SNAP encapsulation, the PID field has the same meaning as the type field in Ethernet II encapsulation, which both refer to globally unique protocol number. Such encapsulation is also known as SNAP RFC1042 encapsulation, which is standard SNAP encapsulation. The SNAP encapsulation mentioned in this chapter refers to SNAP RFC 1042 encapsulation.
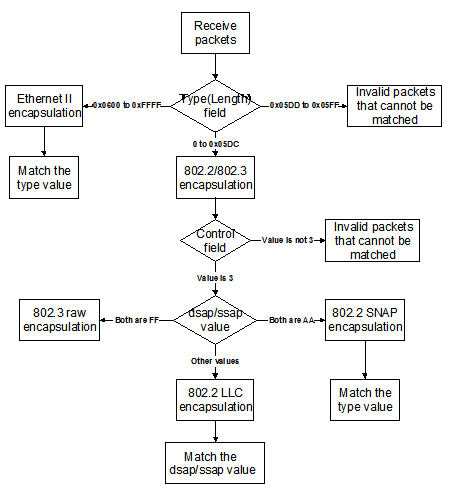
Procedure for the Switch to Judge Packet Protocol
Figure 1-9 Procedure for the switch to judge packet protocol
Encapsulation Formats
Table 1-1 lists the encapsulation formats supported by some protocols. In brackets are type values of these protocols.
Table 1-1 Encapsulation formats
|
Encapsulation |
Ethernet II |
802.3 raw |
802.2 LLC |
802.2 SNAP |
|
Protocol |
||||
|
IP (0x0800) |
Supported |
Not supported |
Not supported |
Supported |
|
IPX (0x8137) |
Supported |
Supported |
Supported |
Supported |
|
AppleTalk (0x809B) |
Supported |
Not supported |
Not supported |
Supported |
Implementation of Protocol-Based VLAN
The switching engines of the devices assign the packet to the specific VLAN by matching the packet with the protocol template.
The protocol template is the standard to determine the protocol to which a packet belongs. Protocol templates include standard templates and user-defined templates:
l The standard template adopts the RFC-defined packet encapsulation formats and values of some specific fields as the matching criteria.
l The user-defined template adopts the user-defined encapsulation formats and values of some specific fields as the matching criteria.
After configuring the protocol template, you must add a port to the protocol-based VLAN and associate this port with the protocol template. This port will add VLAN tags to the packets based on protocol types. The port in the protocol-based VLAN must be connected to a client. However, a common client cannot process VLAN-tagged packets. In order that the client can process the packets out of this port, you must configure the port in the protocol-based VLAN as a hybrid port and configure the port to remove VLAN tags when forwarding packets of all VLANs.
![]()
For the operation of removing VLAN tags when the hybrid port sends packets, refer to Port Basic Configuration in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide.
VLAN Configuration
Configuration Task List
Complete the following tasks to configure VLAN:
|
Task |
Remarks |
|
Required |
|
|
Optional |
|
|
Optional |
Basic VLAN Configuration
Follow these steps to make basic VLAN configuration:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Create multiple VLANs in batch |
vlan { vlan-id1 to vlan-id2 | all } |
Optional |
|
Create a VLAN and enter VLAN view |
vlan vlan-id |
Required By default, there is only one VLAN, that is, the default VLAN (VLAN 1). |
|
Assign a name for the current VLAN |
name text |
Optional By default, the name of a VLAN is its VLAN ID. “VLAN 0001” for example. |
|
Specify the description string of the current VLAN |
description text |
Optional By default, the description string of a VLAN is its VLAN ID. “VLAN 0001” for example. |
![]()
l VLAN 1 is the system default VLAN, which needs not to be created and cannot be removed, either.
l The VLAN you created in the way described above is a static VLAN. On the switch, there are dynamic VLANs which are registered through GVRP. For details, refer to GVRP in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide.
l When you use the vlan command to create VLANs, if the destination VLAN is an existing dynamic VLAN, it will be transformed into a static VLAN and the switch will output the prompt information.
Basic VLAN Interface Configuration
Configuration prerequisites
Before configuring a VLAN interface, create the corresponding VLAN.
Configuration procedure
Follow these steps to make basic VLAN interface configuration:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Create a VLAN interface and enter VLAN interface view |
interface Vlan-interface vlan-id |
Required By default, there is no VLAN interface on a switch. |
|
Specify the description string for the current VLAN interface |
description text |
Optional By default, the description string of a VLAN interface is the name of this VLAN interface. “Vlan-interface1 Interface” for example. |
|
Disable the VLAN interface |
shutdown |
Optional By default, the VLAN interface is enabled. In this case, the VLAN interface’s status is determined by the status of the ports in the VLAN, that is, if all ports of the VLAN are down, the VLAN interface is down (disabled); if one or more ports of the VLAN are up, the VLAN interface is up (enabled). If you disable the VLAN interface, the VLAN interface will always be down, regardless of the status of the ports in the VLAN. |
|
Enable the VLAN Interface |
undo shutdown |
![]()
The operation of enabling/disabling a VLAN’s VLAN interface does not influence the physical status of the Ethernet ports belonging to this VLAN.
Displaying and Maintaining VLAN
|
To do… |
Use the command… |
Remarks |
|
Display the VLAN interface information |
display interface Vlan-interface [ vlan-id ] |
Available in any view |
|
Display the VLAN information |
display vlan [ vlan-id [ to vlan-id ] | all | dynamic | static ] |
Configuring a Port-Based VLAN
Configuring a Port-Based VLAN
Configuration prerequisites
Create a VLAN before configuring a port-based VLAN.
Configuration procedure
Follow these steps to configure a port-based VLAN:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter VLAN view |
vlan vlan-id |
— |
|
Add Ethernet ports to the specific VLAN |
port interface-list |
Required By default, all the ports belong to the default VLAN (VLAN 1). |
![]()
The commands above are effective for access ports only. If you want to add trunk ports or hybrid ports to a VLAN, you need to use the port trunk permit vlan command or the port hybrid vlan command in Ethernet port view. For the configuration procedure, refer to the section of configuring Ethernet ports in Port Basic Configuration in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide.
Protocol-Based VLAN Configuration Example
Network requirements
l As shown in Figure 2-1, Switch A and Switch B each connect to a server and a workstation (PC).
l For data security concerns, the two servers are assigned to VLAN 101 with the descriptive string being “DMZ”, and the PCs are assigned to VLAN 201.
l The devices within each VLAN can communicate with each other but that in different VLANs cannot communicate with each other directly.
Figure 2-1 Network diagram for VLAN configuration

Configuration procedure
l Configure Switch A.
# Create VLAN 101, specify its descriptive string as “DMZ”, and add GigabitEthernet 1/0/1 to VLAN 101.
<SwitchA> system-view
[SwitchA] vlan 101
[SwitchA-vlan101] description DMZ
[SwitchA-vlan101] port GigabitEthernet 1/0/1
[SwitchA-vlan101] quit
# Create VLAN 201, and add GigabitEthernet 1/0/2 to VLAN 201.
[SwitchA] vlan 201
[SwitchA-vlan201] port GigabitEthernet 1/0/2
[SwitchA-vlan201] quit
l Configure Switch B.
# Create VLAN 101, specify its descriptive string as “DMZ”, and add GigabitEthernet 1/0/11 to VLAN 101.
<SwitchB> system-view
[SwitchB] vlan 101
[SwitchB-vlan101] description DMZ
[SwitchB-vlan101] port GigabitEthernet 1/0/11
[SwitchB-vlan101] quit
# Create VLAN 201, and add GigabitEthernet 1/0/12 to VLAN 201.
[SwitchB] vlan 201
[SwitchB-vlan201] port GigabitEthernet 1/0/12
[SwitchB-vlan201] quit
l Configure the link between Switch A and Switch B.
Because the link between Switch A and Switch B need to transmit data of both VLAN 101 and VLAN 102, you can configure the ports at the end of the link as trunk ports and permit packets of the two VLANs to pass through.
# Configure GigabitEthernet 1/0/3 of Switch A.
[SwitchA] interface GigabitEthernet 1/0/3
[SwitchA-GigabitEthernet1/0/3] port link-type trunk
[SwitchA-GigabitEthernet1/0/3] port trunk permit vlan 101
[SwitchA-GigabitEthernet1/0/3] port trunk permit vlan 201
# Configure GigabitEthernet 1/0/10 of Switch B.
[SwitchB] interface GigabitEthernet 1/0/10
[SwitchB-GigabitEthernet1/0/10] port link-type trunk
[SwitchB-GigabitEthernet1/0/10] port trunk permit vlan 101
[SwitchB-GigabitEthernet1/0/10] port trunk permit vlan 201
![]()
For the command of configuring a port link type (port link-type) and the command of allowing packets of certain VLANs to pass through a port (port trunk permit), refer to the section of configuring Ethernet ports in Port Basic Configuration in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide.
Configuring a Protocol-Based VLAN
Configuration Task List
Complete the following tasks to configure protocol-based VLAN:
|
Task |
Remarks |
|
Required |
|
|
Required |
|
|
Optional |
Configuring a Protocol Template for a Protocol-Based VLAN
Configuration prerequisites
Create a VLAN before configuring the VLAN as a protocol-based VLAN.
Configuration procedure
Follow these steps to configure the protocol template for a VLAN:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter VLAN view |
vlan vlan-id |
— |
|
Configure the protocol template for the VLAN |
protocol-vlan [ protocol-index ] { at | ip | ipx { ethernetii | llc | raw | snap } | mode { ethernetii etype etype-id | llc dsap dsap-id ssap ssap-id | snap etype etype-id } } |
Required By default, no protocol template is configured for the VLAN. |
When configuring a protocol template for a protocol-based VLAN, use the at, ip or ipx keyword to configure a standard template to match AppleTalk, IP, and IPX packets respectively, and use the mode keyword to configure a user-defined template.
![]()
l Because the IP protocol is closely associated with the ARP protocol, you are recommended to configure the ARP protocol type when configuring the IP protocol type and associate the two protocol types with the same port to avoid that ARP packets and IP packets are not assigned to the same VLAN, which will cause IP address resolution failure.
l If you specify some special values for both the dsap-id and ssap-id arguments when configuring the user-defined template for IIc encapsulation, the matching packets will take the same encapsulation format as some standard type of packets. For example, when both dsap-id and ssap-id have a value of 0xFF, the encapsulation format will be the same as that of ipx raw packets; if they both have a value of 0xE0, the packet encapsulation format will be the same as that of ipx llc packets; if they both have a value of 0xAA, the packet encapsulation format will be the same as that of snap packets. To prevent two commands from processing packets of the same protocol type in different ways, the system does not allow you to set both the dsap-id and ssap-id arguments to 0xFF, 0xE0, or 0xAA.
l When you use the mode keyword to configure a user-defined protocol template, if you set the etype-id argument for ethernetii or snap packets to 0x0800, 0x809B, or 0x8137, the matching packets will take the same format as that of the IP, IPX, and AppleTalk packets respectively. To prevent two commands from processing packets of the same protocol type in different ways, the switch will prompt that you cannot set the etype-id argument for Ethernet II or snap packets to 0x0800, 0x089B, or 0x8137.
Associating a Port with a Protocol-Based VLAN
Configuration prerequisites
l The protocol template for the protocol-based VLAN is configured.
l The port is configured as a hybrid port, and the port is configured to remove VLAN tags when it forwards the packets of the protocol-based VLANs.
Configuration procedure
Follow these steps to associate a port with the protocol-based VLAN:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter port view |
interface interface-type interface-number |
— |
|
Associate the port with the specified protocol-based VLAN |
port hybrid protocol-vlan vlan vlan-id { protocol-index [ to protocol-index-end ] | all } |
Required By default, a port is not associated with any protocol-based VLAN. |
![]()
For the operation of adding a hybrid port to a VLAN in the untagged way (when forwarding a packet, the port removes the VLAN tag of the packet), refer to the section of configuring Ethernet ports in Port Basic Configuration in H3C WX3000 Series Unified Switches Switching Engine Configuration Guide.
Displaying and Maintaining Protocol-Based VLAN
|
To do… |
Use the command… |
Remarks |
|
Display the information about the protocol-based VLAN |
display vlan [ vlan-id [ to vlan-id ] | all | dynamic | static] |
Available in any view |
|
Display the protocol information and protocol indexes configured on the specified VLAN |
display protocol-vlan vlan { vlan-id [ to vlan-id ] | all } |
|
|
Display the protocol information and protocol indexes configured on the specified port |
display protocol-vlan interface { interface-type interface-number [ to interface-type interface-number ] | all } |
Protocol-Based VLAN Configuration Example
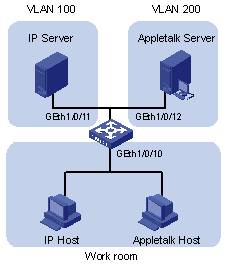
Network requirements
l As shown in Figure 2-2, Workroom connects to the LAN through port GigabitEthernet 1/0/10 on the switch.
l IP network and AppleTalk network workstations (hosts) coexist in the Workroom.
l The switch connects to VLAN 100 (using IP network) through GigabitEthernet 1/0/11 and to VLAN 200 (using AppleTalk network) through GigabitEthernet 1/0/12.
l Configure the switch to automatically assign the IP and AppleTalk packets to proper VLANs for transmission, so as to ensure the normal communication between the workstations and servers.
Figure 2-2 Network diagram for protocol-based VLAN configuration
Configuration procedure
# Create VLAN 100 and VLAN 200, and add GigabitEthernet 1/0/11 and GigabitEthernet 1/0/12 to VLAN 100 and VLAN 200 respectively.
<device> system-view
[device] vlan 100
[device-vlan100] port GigabitEthernet 1/0/11
[device-vlan100] quit
[device] vlan 200
[device-vlan200] port GigabitEthernet 1/0/12
# Configure protocol templates for VLAN 200 and VLAN 100, matching AppleTalk protocol and IP protocol respectively.
[device-vlan200] protocol-vlan at
[device-vlan200] quit
[device] vlan 100
[device-vlan100] protocol-vlan ip
# To ensure the normal operation of IP network, you need to configure a user-defined protocol template for VLAN 100 to match the ARP protocol (assume Ethernet II encapsulation is adopted here).
[device-vlan100] protocol-vlan mode ethernetii etype 0806
# Display the created protocol-based VLANs and the protocol templates.
[device-vlan100] display protocol-vlan vlan all
VLAN ID: 100
VLAN Type: Protocol-based VLAN
Protocol Index Protocol Type
0 ip
1 ethernetii etype 0x0806
VLAN ID: 200
VLAN Type: Protocol-based VLAN
Protocol Index Protocol Type
0 at
# Configure GigabitEthernet 1/0/10 as a hybrid port, which removes the VLAN tag of the packets of VLAN 100 and VLAN 200 before forwarding the packets.
[device-vlan100] quit
[device] interface GigabitEthernet 1/0/10
[device-GigabitEthernet1/0/10] port link-type hybrid
[device-GigabitEthernet1/0/10] port hybrid vlan 100 200 untagged
# Associate GigabitEthernet 1/0/10 with protocol template 0 and 1 of VLAN 100, and protocol template 0 of VLAN 200.
[device-GigabitEthernet1/0/10] port hybrid protocol-vlan vlan 100 0 to 1
[device-GigabitEthernet1/0/10] port hybrid protocol-vlan vlan 200 0
# Display the associations between GigabitEthernet 1/0/10 and the VLAN protocol templates to verify your configuration.
[device-GigabitEthernet1/0/10] display protocol-vlan interface GigabitEthernet 1/0/10
Interface:GigabitEthernet1/0/10
VLAN ID Protocol-Index Protocol-Type
100 0 ip
100 1 ethernetii etype 0x0806
200 0 at
The above output information indicates that GigabitEthernet 1/0/10 has already been associated with the corresponding protocol templates of VLAN 100 and VLAN 200. Thus, packets from the IP and AppleTalk workstations can be automatically assigned to VLAN 100 and VLAN 200 respectively for transmission by matching the corresponding protocol templates, so as to realize the normal communication between the workstations and the servers.
