- Table of Contents
-
- 02-Typical configuration example
- 01-AAA_Configuration_Examples
- 02-ACL_Configuration_Examples
- 03-ATM_Configuration_Examples
- 04-IGMP_Configuration_Examples
- 05-IP_Source_Guard_Configuration_Examples
- 06-Ethernet_OAM_Configuration_Examples
- 07-NQA_Configuration_Examples
- 08-QinQ_Configuration_Examples
- 09-OSPF_Configuration_Examples
- 10-MPLS_TE_Configuration_Examples
- 11-OpenFlow_Configuration_Examples
- 12-NAT_Configuration_Examples
- 13-RBAC_Configuration_Examples
- 14-IRF_Configuration_Examples
- 15-POS_Interface_Configuration_Examples
- 16-CPOS_Interface_Configuration_Examples
- 17-DLDP_Configuration_Examples
- 18-IS-IS_Configuration_Examples
- 19-MPLS_L3VPN_Configuration_Examples
- 20-SSH_Configuration_Examples
- 21-Login_Management_Configuration_Examples
- 22-SNMP_Configuration_Examples
- 23-Priority_Marking_and_Queue_Scheduling_Configuration_Examples
- 24-Multicast_VPN_Configuration_Examples
- 25-BGP_Configuration_Examples
- 26-HoVPN_Configuration_Examples
- 27-L2TP_Configuration_Examples
- 28-VRRP_Configuration_Examples
- 29-Traffic_Filtering_Configuration_Examples
- 30-Samplers_and_IPv4_NetStream_Configuration_Examples
- 31-Software_Upgrade_Examples
- 32-MPLS_L2VPN_Configuration_Examples
- 33-NetStream_Configuration_Examples
- 34-Policy-Based_Routing_Configuration_Examples
- 35-Traffic_Policing_Configuration_Examples
- 36-BFD_Configuration_Examples
- 37-OSPFv3_Configuration_Examples
- 38-VPLS_Configuration_Examples
- 39-GTS_and_Rate_Limiting_Configuration_Examples
- 40-IPv6_IS-IS_Configuration_Examples
- 41-MPLS OAM_Configuration_Examples
- 42-BGP_Route_Selection_Configuration_Examples
- 43-IS-IS_Route_Summarization_Configuration_Examples
- 44-Attack_Protection_Configuration_Examples
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 02-ACL_Configuration_Examples | 125.32 KB |
Example: Filtering packets by MAC address
Example: Filtering packets by IP address
Configuration restrictions and guidelines
Denying the Administration department to access the R&D department
Configuring access control for the R&D department
Example: Filtering TCP packets
Configuring access control for the Administration department
Configuring access control for the R&D department
Introduction
This document provides ACL configuration examples.
Prerequisites
The configuration examples in this document were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
This document assumes that you have basic knowledge of ACL.
Example: Filtering packets by MAC address
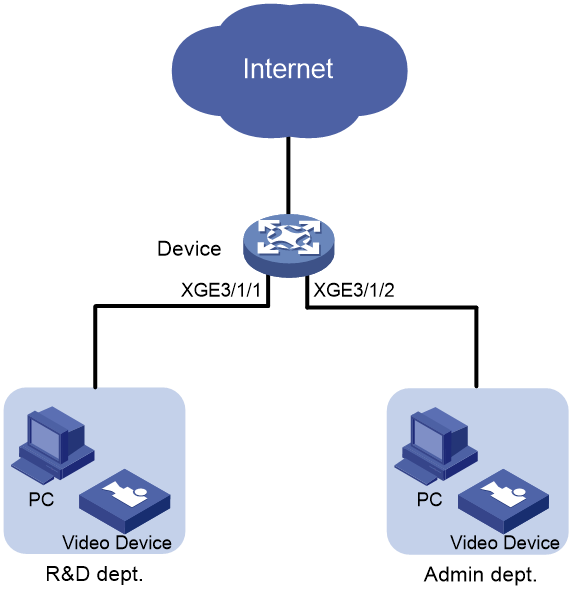
Network configuration
As shown in Figure 1, the R&D department and the Administration department have video devices deployed. The video devices use MAC addresses prefixed with 000f-e2. Configure packet filtering on the device to allow outgoing video data to pass through only from 8:30 to 18:00 every day.
Analysis
Because the MAC addresses of the video devices are fixed, you can use an Ethernet frame header ACL to filter packets by MAC address. In the ACL, specify a MAC address and a mask to match the MAC addresses that have the same prefix.
Procedures
# Create a time range time1 for the time range from 8:30 to 18:00 every day.
<Device> system-view
[Device] time-range time1 8:30 to 18:00 daily
# Configure Ethernet frame header ACL 4000 to allow packets with source MAC addresses prefixed with 000f-e2 to pass through only during time1.
[Device] acl mac 4000
[Device-acl-mac-4000] rule permit source-mac 000f-e200-0000 ffff-ff00-0000 time-range time1
[Device-acl-mac-4000] rule deny source-mac 000f-e200-0000 ffff-ff00-0000
[Device-acl-mac-4000] quit
# Apply ACL 4000 to filter incoming packets on Ten-GigabitEthernet 3/1/1 and Ten-GigabitEthernet 3/1/2.
[Device] interface ten-gigabitethernet 3/1/1
[Device-Ten-GigabitEthernet3/1/1] packet-filter mac 4000 inbound
[Device-Ten-GigabitEthernet3/1/1] quit
[Device] interface ten-gigabitethernet 3/1/2
[Device-Ten-GigabitEthernet3/1/2] packet-filter mac 4000 inbound
[Device-Ten-GigabitEthernet3/1/2] quit
Verifying the configuration
# Verify that the ACL is successfully applied for packet filtering.
[Device] display packet-filter interface inbound
Interface: Ten-GigabitEthernet3/1/1
Inbound policy:
MAC ACL 4000
Interface: Ten-GigabitEthernet3/1/2
Inbound policy:
MAC ACL 4000
# Verify that the video devices can communicate with the external network during the time range time1. (Details not shown.)
# Verify that the video devices cannot communicate with the external network beyond the time range time1. (Details not shown.)
Configuration files
#
interface Ten-GigabitEthernet3/1/1
port link-mode route
packet-filter mac 4000 inbound
#
interface Ten-GigabitEthernet3/1/2
port link-mode route
packet-filter mac 4000 inbound
#
time-range time1 08:30 to 18:00 daily
#
acl mac 4000
rule 0 permit source-mac 000f-e200-0000 ffff-ff00-0000 time-range time1
rule 5 deny source-mac 000f-e200-0000 ffff-ff00-0000
Example: Filtering packets by IP address
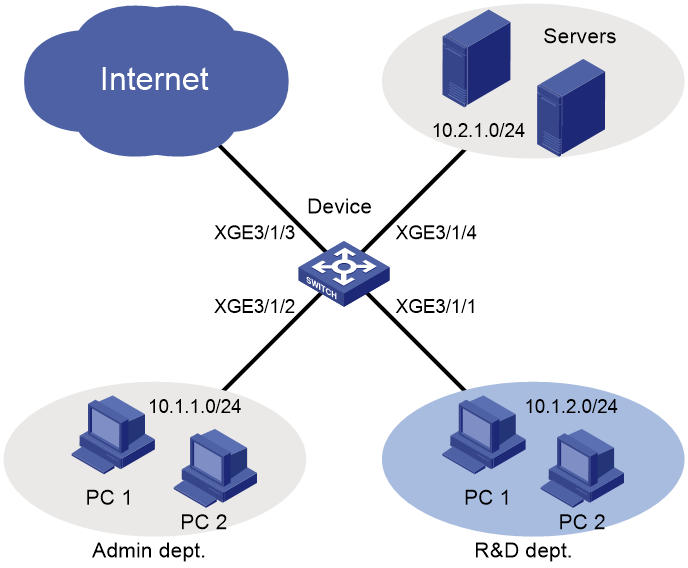
Network configuration
As shown in Figure 2, a company's internal network connects to the Internet through the device. The R&D department, Administration department, and servers are on different subnets.
Configure packet filtering to meet the following requirements:
· The Administration department can access the Internet and servers at any time, but cannot access the R&D department at any time.
· The R&D department can access only the servers during working hours (8:30 to 18:00) on working days (Monday to Friday). It can access the Internet and servers, but cannot access the Administration department outside working hours.
Analysis
To meet the network requirements, you must perform the following tasks:
· To deny the Administration department to access the R&D department, perform the following tasks:
¡ Configure an advanced ACL to deny packets destined for subnet 10.1.2.0/24.
¡ Apply the ACL to filter incoming packets on Ten-GigabitEthernet 3/1/2.
· To implement access control for the R&D department, perform the following tasks:
¡ Create a time range for the working hours (8:30 to 18:00) on working days (Monday to Friday).
¡ Create an advanced ACL and configure the following rules:
- Configure rules to allow only packets destined for subnet 10.2.1.0/24 to pass through. Set the rules to be active during the time range.
- To deny the R&D department to access the Administration department, configure a rule to deny packets destined for subnet 10.1.1.0/24.
¡ Apply the ACL to filter incoming packets on Ten-GigabitEthernet 3/1/1.
Configuration restrictions and guidelines
When you configure ACL rules to allow the R&D department to access only the servers during working hours on working days, configure the permit rule before the deny rule. Otherwise, the interface denies all packets during working hours on working days.
Procedures
Denying the Administration department to access the R&D department
# Create IPv4 advanced ACL 3000.
<Device> system-view
[Device] acl advanced 3000
# Configure a rule to deny packets destined for subnet 10.1.2.0/24 to pass through.
[Device-acl-ipv4-adv-3000] rule deny ip destination 10.1.2.0 0.0.0.255
[Device-acl-ipv4-adv-3000] quit
# Apply ACL 3000 to filter incoming packets on Ten-GigabitEthernet 3/1/2.
[Device] interface ten-gigabitethernet 3/1/2
[Device-Ten-GigabitEthernet3/1/2] packet-filter 3000 inbound
[Device-Ten-GigabitEthernet3/1/2] quit
Configuring access control for the R&D department
# Configure a time range worktime for the time range of 8:30 to 18:00 from Monday to Friday.
[Device] time-range worktime 8:30 to 18:00 working-day
# Create IPv4 advanced ACL 3001.
[Device] acl advanced 3001
# Configure a rule to allow packets destined for subnet 10.2.1.0/24 to pass through during worktime.
[Device-acl-ipv4-adv-3001] rule permit ip destination 10.2.1.0 0.0.0.255 time-range worktime
# Configure a rule to deny all IP packets to pass through during worktime.
[Device-acl-ipv4-adv-3001] rule deny ip time-range worktime
# Configure a rule to deny packets destined for subnet 10.1.1.0/24 to pass through.
[Device-acl-ipv4-adv-3001] rule deny ip destination 10.1.1.0 0.0.0.255
[Device-acl-ipv4-adv-3001] quit
# Apply ACL 3001 to filter incoming packets on Ten-GigabitEthernet 3/1/1.
[Device] interface ten-gigabitethernet 3/1/1
[Device-Ten-GigabitEthernet3/1/1] packet-filter 3001 inbound
[Device-Ten-GigabitEthernet3/1/1] quit
Verifying the configuration
# Verify that the ACLs are successfully applied for packet filtering.
[Device] display packet-filter interface inbound
Interface: Ten-GigabitEthernet3/1/1
Inbound policy:
IPv4 ACL 3001
Interface: Ten-GigabitEthernet3/1/2
Inbound policy:
IPv4 ACL 3000
# Verify that you cannot ping through a website on the Internet from the R&D department at 9:30 on Monday.
C:\>ping www.google.com
Pinging www.google.com [173.194.127.242] with 32 bytes of data:
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Ping statistics for 173.194.127.242:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 30ms, Maximum = 30ms, Average = 30ms
C:\>
# Verify that you can ping through a website on the Internet from the Administration department at 9:30 on Monday.
C:\>ping www.google.com
Pinging www.google.com [173.194.127.242] with 32 bytes of data:
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Ping statistics for 173.194.127.242:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 30ms, Maximum = 30ms, Average = 30ms
C:\>
# Verify that you can ping through a website on the Internet from the R&D department at 19:30 on Monday.
C:\>ping www.google.com
Pinging www.google.com [173.194.127.242] with 32 bytes of data:
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Ping statistics for 173.194.127.242:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 30ms, Maximum = 30ms, Average = 30ms
C:\>
Configuration files
#
interface Ten-GigabitEthernet3/1/1
port link-mode route
packet-filter 3001 inbound
#
interface Ten-GigabitEthernet3/1/2
port link-mode route
packet-filter 3000 inbound
#
time-range worktime 08:30 to 18:00 working-day
#
acl advanced 3000
rule 0 deny ip destination 10.1.2.0 0.0.0.255
#
acl advanced 3001
rule 0 permit ip destination 10.2.1.0 0.0.0.255 time-range worktime
rule 5 deny ip time-range worktime
rule 10 deny ip destination 10.1.1.0 0.0.0.255
Example: Filtering TCP packets
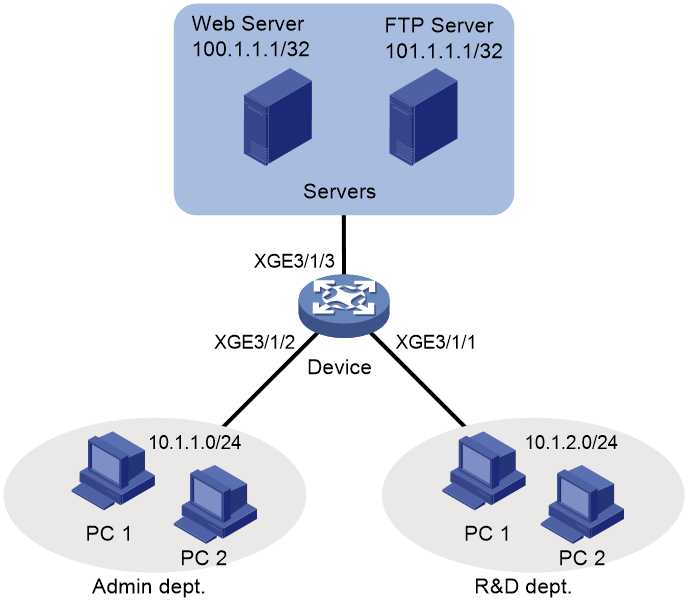
Network configuration
As shown in Figure 3, the R&D department, Administration department, and servers are on different networks, and they are connected through the device.
Configure packet filtering to meet the following requirements:
· The Web server provides HTTP services to only the Administration department.
· The FTP server provides FTP services to only the R&D department.
· The TCP connections between hosts and the Web server can only be initiated by the hosts. The TCP connections between hosts and the FTP server can be initiated by either the hosts or the FTP server.
Analysis
To meet the network requirements, you must perform the following tasks:
· To allow TCP connections initiated by the hosts to the Web server, perform the following tasks:
¡ Configure an advanced ACL rule as follows to allow packets sent by the Web server through established TCP connections to pass through:
- Specify the established keyword (the ACK or RST flag bit set) in the rule to match established TCP connections.
- Because a TCP initiator typically uses a TCP port number higher than 1023, specify a port number range higher than 1023 to match established TCP connections.
¡ Configure an advanced ACL rule to deny packets sent from the subnet where the Web server resides to the subnet where the hosts reside.
· FTP uses TCP port 20 for data transfer and port 21 for FTP control. To identify FTP traffic, you must specify TCP ports 20 and 21 in ACL rules.
· To identify HTTP packets, specify TCP port 80 in ACL rules.
Procedures
Configuring access control for the Administration department
# Create IPv4 advanced ACL 3000.
<Device> system-view
[Device] acl advanced 3000
# Configure a rule to allow TCP packets from the Web server to the hosts on subnet 10.1.1.0/24, with TCP port number higher than 1023 and the ACK or RST flag set.
[Device-acl-ipv4-adv-3000] rule permit tcp established source 100.1.1.1 0 destination 10.1.1.0 0.0.0.255 destination-port gt 1023
# Configure a rule to deny TCP packets from subnet 100.1.1.1/32 to subnet 10.1.1.0/24 to pass through.
[Device-acl-ipv4-adv-3000] rule deny tcp source 100.1.1.1 0 destination 10.1.1.0 0.0.0.255
# Configure a rule to deny FTP packets sourced from 101.1.1.1/32 to pass through.
[Device-acl-ipv4-adv-3000] rule deny tcp source 101.1.1.1 0 source-port range 20 21
[Device-acl-ipv4-adv-3000] quit
# Apply ACL 3000 to filter outgoing packets on Ten-GigabitEthernet 3/1/2.
[Device] interface ten-gigabitethernet 3/1/2
[Device-Ten-GigabitEthernet3/1/2] packet-filter 3000 outbound
[Device-Ten-GigabitEthernet3/1/2] quit
Configuring access control for the R&D department
# Create IPv4 advanced ACL 3001.
[Device] acl advanced 3001
# Configure a rule to deny HTTP packets sourced from 100.1.1.1/32 to pass through.
[Device-acl-ipv4-adv-3001] rule deny tcp source 100.1.1.1 0 source-port eq 80
[Device-acl-ipv4-adv-3001] quit
# Apply ACL 3001 to filter outgoing packets on Ten-GigabitEthernet 3/1/1.
[Device] interface ten-gigabitethernet 3/1/1
[Device-Ten-GigabitEthernet3/1/1] packet-filter 3001 outbound
[Device-Ten-GigabitEthernet3/1/1] quit
Verifying the configuration
1. Verify that the ACLs are successfully applied for packet filtering.
[Device] display packet-filter interface outbound
Interface: Ten-GigabitEthernet3/1/1
Out-bound policy:
IPv4 ACL 3001
Interface: Ten-GigabitEthernet3/1/2
Out-bound policy:
IPv4 ACL 3000
2. Verify that you cannot Telnet to the FTP server from the Administration department.
C:\>telnet 101.1.1.1 21
Connecting To 101.1.1.1...Could not open connection to the host, on port 21:
Connect failed
C:\>
3. Verify that from the Web server, you can ping a host in the Administration department, but cannot access a shared folder on the host:
# Set a shared folder on a host in the Administration department. (Details not shown.)
# Ping the host from the Web server. The ping operation succeeds.
C:\>ping 10.1.1.110
Pinging 10.1.1.110 with 32 bytes of data:
Reply from 10.1.1.110: bytes=32 time=2ms TTL=128
Reply from 10.1.1.110: bytes=32 time=14ms TTL=128
Reply from 10.1.1.110: bytes=32 time=1ms TTL=128
Reply from 10.1.1.110: bytes=32 time=1ms TTL=128
Ping statistics for 10.1.1.110:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 14ms, Average = 4ms
C:\>
# Verify that you cannot access the share folder from the Web server. (Details not shown.)
4. Verify that you cannot Telnet to the Web server from the R&D department.
C:\>telnet 100.1.1.1 80
Connecting To 100.1.1.1...Could not open connection to the host, on port 80:
Connect failed
C:\>
Configuration files
#
interface Ten-GigabitEthernet3/1/1
port link-mode route
packet-filter 3001 outbound
#
interface Ten-GigabitEthernet3/1/2
port link-mode route
packet-filter 3000 outbound
#
acl advanced 3000
rule 0 permit tcp source 100.1.1.1 0 destination 10.1.1.0 0.0.0.255 destination
-port gt 1023 established
rule 5 deny tcp source 100.1.1.1 0 destination 10.1.1.0 0.0.0.255
rule 10 deny tcp source 101.1.1.1 0 source-port range ftp-data ftp
#
acl advanced 3001
rule 0 deny tcp source 100.1.1.1 0 source-port eq www
Related documentation
· H3C CR16000-F Routers ACL and QoS Configuration Guide-R8385P09
· H3C CR16000-F Routers ACL and QoS Command Reference-R8385P09
·