- Table of Contents
-
- 03-IP Routing Volume
- 00-IP Routing Volume Organization
- 01-IP Routing Overview
- 02-Static Routing Configuration
- 03-RIP Configuration
- 04-OSPF Configuration
- 05-IS-IS Configuration
- 06-BGP Configuration
- 07-IPv6 Static Routing Configuration
- 08-IPv6 Ripng Configuration
- 09-IPv6 OSPFv3 Configuration
- 10-IPv6 IS-IS Configuration
- 11-IPv6 BGP Configuration
- 12-Routing Policy Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 12-Routing Policy Configuration | 159.94 KB |
Table of Contents
Route Policy Configuration Task List
Defining an Extended Community List
Displaying and Maintaining the Route Policy
Route Policy Configuration Example
Applying a Route Policy to IPv4 Route Redistribution
Applying a Route Policy to IPv6 Route Redistribution
Applying a Route Policy to Filter Received BGP Routes
Troubleshooting Route Policy Configuration
IPv4 Routing Information Filtering Failure
IPv6 Routing Information Filtering Failure
A route policy is used on a router for route filtering and attributes modification when routes are received, advertised, or redistributed.
When configuring route policy, go to these sections for information you are interested in:
l Introduction to Route Policy
l Route Policy Configuration Task List
l Displaying and Maintaining the Route Policy
l Route Policy Configuration Example
l Troubleshooting Route Policy Configuration
l The term “router” in this document refers to a router in a generic sense or a Layer 3 switch.
l Route policy in this chapter involves both IPv4 route policy and IPv6 route policy.
l EA boards (such as LSQ1GP12EA and LSQ1TGX1EA) do not support IPv6 features.
Introduction to Route Policy
Route Policy
A route policy is used on a router for route filtering and attributes modification when routes are received, advertised, or redistributed.
To configure a route policy, you need to define some filters based on the attributes of routing information, such as destination address, advertising router’s address and so on. The filters can be set beforehand and then applied to the route policy.
Filters
There are six types of filters: ACL, IP prefix list, AS path ACL, community list, extended community list and route policy.
ACL
ACL involves IPv4 ACL and IPv6 ACL. An ACL is configured to match the destinations or next hops of routing information.
For ACL configuration, refer to ACL configuration in the Security Volume.
IP prefix list
IP prefix list involves IPv4 and IPv6 prefix list.
An IP prefix list is configured to match the destination address of routing information. Moreover, you can use the gateway option to allow only routing information from certain routers to be received. For gateway option information, refer to RIP Commands and OSPF Commands in the IP Routing Volume.
An IP prefix list, identified by name, can comprise multiple items. Each item, identified by an index number, can specify a prefix range to match. An item with a smaller index number is matched first. If one item is matched, the IP prefix list is passed, and the packet will not go to the next item.
AS-PATH list
An AS-PATH list, configured based on the BGP AS PATH attribute, can only be used to match BGP routing information.
Community list
A community list, configured based on the BGP community attribute, can only be used to match BGP routing information.
Extended community list
An extended community list, configured based on the BGP extended community attribute (Route-Target for VPN, and Source of Origin), can only be used to match BGP routing information.
Route policy
A route policy is used to match routing information and modify the attributes of permitted routes. It can reference the above mentioned filters to define its own match criteria.
A route policy can comprise multiple nodes, which are in logic OR relationship. Each route policy node is a match unit, and a node with a smaller number is matched first. Once a node is matched, the route policy is passed and the packet will not go to the next node.
A route policy node comprises a set of if-match and apply clauses. The if-match clauses define the match criteria. The matching objects are some attributes of routing information. The if-match clauses of a route policy node is in logical AND relationship. That is, a packet must match all the if-match clauses of the node to pass it. The apply clauses of the node specify the actions to be taken on the permitted packets, such as route attribute modification.
Route Policy Application
A route policy is applied on a router to filter routes when they are received, advertised or redistributed and to modify some attributes of permitted routes.
Route Policy Configuration Task List
Complete the following tasks to configure a route policy:
|
Task |
|
Defining Filters
Prerequisites
Before configuring this task, you need to decide on:
l IP-prefix list name
l Matching address range
l Extcommunity list sequence number
Defining an IP-prefix List
Define an IPv4 prefix list
Identified by name, an IPv4 prefix list can comprise multiple items. Each item specifies a prefix range to match and is identified by an index number.
An item with a smaller index number is matched first. If one item is matched, the IP prefix list is passed, and the routing information will not go to the next item.
Follow these steps to define an IPv4 prefix list:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Define an IPv4 prefix list |
ip ip-prefix ip-prefix-name [ index index-number ] { permit | deny } ip-address mask-length [ greater-equal min-mask-length ] [ less-equal max-mask-length ] |
Required Not defined by default. |
![]()
If all the items are set to the deny mode, no routes can pass the IPv4 prefix list. Therefore, you need to define the permit 0.0.0.0 0 less-equal 32 item following multiple deny items to allow other IPv4 routing information to pass.
For example, the following configuration filters routes 10.1.0.0/16, 10.2.0.0/16 and 10.3.0.0/16, but allows other routes to pass.
<Sysname> system-view
[Sysname] ip ip-prefix abc index 10 deny 10.1.0.0 16
[Sysname] ip ip-prefix abc index 20 deny 10.2.0.0 16
[Sysname] ip ip-prefix abc index 30 deny 10.3.0.0 16
[Sysname] ip ip-prefix abc index 40 permit 0.0.0.0 0 less-equal 32
Define an IPv6 prefix list
Identified by name, each IPv6 prefix list can comprise multiple items. Each item specifies a prefix range to match and is identified by an index number.
An item with a smaller index number is matched first. If one item is matched, the IPv6 prefix list is passed, and the routing information will not go to the next item.
Follow these steps to define an IPv6 prefix list:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Define an IPv6 prefix list |
ip ipv6-prefix ipv6-prefix-name [ index index-number ] { deny | permit } ipv6-address prefix-length [ greater-equal min-prefix-length ] [ less-equal max-prefix-length ] |
Required Not defined by default. |
![]()
If all items are set to the deny mode, no routes can pass the IPv6 prefix list. Therefore, you need to define the permit :: 0 less-equal 128 item following multiple deny items to allow other IPv6 routing information to pass.
For example, the following configuration filters routes 2000:1::/48, 2000:2::/48 and 2000:3::/48, but allows other routes to pass.
<Sysname> system-view
[Sysname] ip ipv6-prefix abc index 10 deny 2000:1:: 48
[Sysname] ip ipv6-prefix abc index 20 deny 2000:2:: 48
[Sysname] ip ipv6-prefix abc index 30 deny 2000:3:: 16
[Sysname] ip ipv6-prefix abc index 40 permit :: 0 less-equal 128
Defining an AS Path List
You can define multiple items for an AS path list that is identified by number. The relation between items is logical OR, that is, if a route matches one of these items, it passes the AS path list.
Follow these steps to define an AS path list:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Define an AS path ACL |
ip as-path as-path-number { deny | permit } regular-expression |
Required Not defined by default. |
Defining a Community List
You can define multiple items for a community list that is identified by number. During matching, the relation between items is logic OR, that is, if routing information matches one of these items, it passes the community list.
Follow these steps to define a community list:
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Define a community list |
Define a basic community list |
ip community-list basic-comm-list-num { deny | permit } [ community-number-list ] [ internet | no-advertise | no-export | no-export-subconfed ] * |
Required to define either; Not defined by default. |
|
Define an advanced community list |
ip community-list adv-comm-list-num { deny | permit } regular-expression |
||
Defining an Extended Community List
You can define multiple items for an extended community list that is identified by number. During matching, the relation between items is logic OR, that is, if routing information matches one of these items, it passes the extended community list.
Follow these steps to define an extended community list:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Define an extended community list |
ip extcommunity-list ext-comm-list-number { deny | permit } { rt route-target }&<1-16> |
Required Not defined by default |
Configuring a Route Policy
A route policy is used to filter routing information, and modify attributes of matching routing information. The match criteria of a route policy can be configured by referencing filters above mentioned.
A route policy can comprise multiple nodes, and each route policy node contains:
l if-match clauses: Define the match criteria that routing information must satisfy. The matching objects are some attributes of routing information.
l apply clauses: Specify the actions to be taken on routing informaiton that has satisfied the match criteria, such as route attibute modification.
Prerequisites
Before configuring this task, you need to configure:
l Filters
l Routing protocols
You also need to decide on:
l Name of the route policy, and node numbers
l Match criteria
l Attributes to be modified
Creating a Route Policy
Follow these steps to create a route policy:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Create a route policy, specify a node for it and enter route policy node view |
route-policy route-policy-name { permit | deny } node node-number |
Required |
![]()
l If a route policy node has the permit keyword specified, routing information matching all the if-match clauses of the node will be handled using the apply clauses of this node, without needing to match against the next node. If routing information does not match the node, it will go to the next node for a match.
l If a route policy node has the deny keyword specified, the apply clauses of the node will not be executed. When routing information matches all the if-match clauses of the node, it cannot pass the node, or go to the next node. If route information cannot match all the if-match clauses of the node, it will go to the next node for a match.
l When a route policy has more than one node, at least one node should be configured with the permit keyword. If the route policy is used to filter routing information, routing information that does not meet any node cannot pass the route policy. If all nodes of the route policy are set with the deny keyword, no routing information can pass it.
Defining if-match Clauses
Follow these steps to define if-match clauses for a route-policy node:
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enter route policy node view |
route-policy route-policy-name { permit | deny } node node-number |
Required |
|
|
Define match criteria for IPv4 routes |
Match IPv4 routing information specified in the ACL |
if-match acl acl-number |
Optional Not configured by default. |
|
Match IPv4 routing information specified in the IP prefix list |
if-match ip-prefix ip-prefix-name |
||
|
Match IPv4 routing information whose next hop or source is specified in the ACL or IP prefix list |
if-match ip { next-hop | route-source } { acl acl-number | ip-prefix ip-prefix-name } |
Optional Not configured by default. |
|
|
Match IPv6 routing information whose next hop or source is specified in the ACL or IP prefix list |
if-match ipv6 { address | next-hop | route-source } { acl acl-number | prefix-list ipv6-prefix-name } |
Optional Not configured by default. |
|
|
Match BGP routing information whose AS path attribute is specified in the AS path list (s) |
if-match as-path AS-PATH-number&<1-16> |
Optional Not configured by default. |
|
|
Match BGP routing information whose community attribute is specified in the community list(s) |
if-match community { basic-community-list-number [ whole-match ] | adv-community-list-number }&<1-16> |
Optional Not configured by default. |
|
|
Match routes having the specifed cost |
if-match cost value |
Optional Not configured by default. |
|
|
Match BGP routing information whose extended community attribute is specified in the extended community list(s) |
if-match extcommunity ext-comm-list-number&<1-16> |
Optional Not configured by default. |
|
|
Match routing information having specified outbound interface(s) |
if-match interface { interface-type interface-number }&<1-16> |
Optional Not configured by default. |
|
|
Match routing information having MPLS labels |
if-match mpls-label |
Optional Not configured by default. |
|
|
Match routing information having the specified route type |
if-match route-type { internal | external-type1 | external-type2 | external-type1or2 | is-is-level-1 | is-is-level-2 | nssa-external-type1 | nssa-external-type2 | nssa-external-type1or2 } * |
Optional Not configured by default. |
|
|
Match RIP, OSPF, and IS-IS routing information having the specified tag value |
if-match tag value |
Optional Not configured by default. |
|
![]()
l The if-match clauses of a route policy node are in logic AND relationship, namely, routing information has to satisfy all its if-match clauses before being executed with its apply clauses.
l You can specify no or multiple if-match clauses for a route policy node. If no if-match clause is specified, and the route policy node is in permit mode, all routing information can pass the node. If it is in deny mode, no routing information can pass it.
l An ACL specified in an if-match clause should be a non-VPN ACL.
l The if-match commands for matching IPv4 destination, next hop and source address are different from those for matching IPv6 ones.
l BGP does not support the route policy that specifies the outbound interface as the matching criteria.
Defining apply Clauses
Follow these steps to define apply clauses for a route policy:
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enter route policy node view |
route-policy route-policy-name { permit | deny } node node-number |
Required Not created by default. |
|
|
Set the AS-PATH attribute for BGP routing information |
Optional Not set by default. |
||
|
Delete the community attribute of BGP routing information using the community list |
apply comm-list comm-list-number delete |
Optional Not configured by default. |
|
|
Set the community attribute for BGP routing information |
apply community { none | additive | { community-number&<1-16> | aa:nn&<1-16> | internet | no-export-subconfed | no-export | no-advertise } * [ additive ] } |
Optional Not set by default. |
|
|
Set a cost for routing information |
apply cost [ + | - ] value |
Optional Not set by default. |
|
|
Set a cost type for routing information |
apply cost-type [ external | internal | type-1 | type-2 ] |
Optional Not set by default. |
|
|
Set the extended community attribute for BGP routing |
apply extcommunity { rt { as-number:nn | ip-address:nn } }&<1-16> [ additive ] |
Optional Not set by default. |
|
|
Set the next hop |
for IPv4 routes |
apply ip-address next-hop ip-address |
Optional Not set by default. The setting does not apply to redistributed routing information. |
|
for IPv6 routes |
apply ipv6 next-hop ipv6-address |
Optional Not set by default. The setting does not apply to redistributed routing information. |
|
|
Inject routing information to a specified ISIS level |
apply isis { level-1 | level-1-2 | level-2 } |
Optional Not configured by default. |
|
|
Set the local preference for BGP routing information |
apply local-preference preference |
Optional Not set by default. |
|
|
Set MPLS label |
apply mpls-label |
Optional Not set by default. |
|
|
Set the origin attribute for BGP routing information |
apply origin { igp | egp as-number | incomplete } |
Optional Not set by default. |
|
|
Set the preference for the routing protocol |
apply preference preference |
Optional Not set by default. |
|
|
Set a preferred value for BGP routing information |
apply preferred-value preferred-value |
Optional Not set by default. |
|
|
Set a tag value for RIP, OSPF or IS-IS routing information |
apply tag value |
Optional Not set by default. |
|
![]()
l The difference between IPv4 and IPv6 apply clauses is the command for setting the next hop for routing information.
l The apply ip-address next-hop and apply ipv6 next-hop commands do not apply to redistributed IPv4 and IPv6 routes respectively.
Displaying and Maintaining the Route Policy
|
To do… |
Use the command… |
Remarks |
|
Display BGP AS-PATH list information |
display ip as-path [ as-path-number ] |
Available in any view |
|
Display BGP community list information |
display ip community-list [ basic-community-list-number | adv-community-list-number ] |
|
|
Display BGP extended community list information |
display ip extcommunity-list [ ext-comm-list-number ] |
|
|
Display IPv4 prefix list statistics |
display ip ip-prefix [ ip-prefix-name ] |
|
|
Display IPv6 prefix list statistics |
display ip ipv6-prefix [ ipv6-prefix-name ] |
|
|
Display route policy information |
display route-policy [ route-policy-name ] |
|
|
Clear IPv4 prefix list statistics |
reset ip ip-prefix [ ip-prefix-name ] |
Available in user view |
|
Clear IPv6 prefix list statistics |
reset ip ipv6-prefix [ ipv6-prefix-name ] |
Route Policy Configuration Example
Applying a Route Policy to IPv4 Route Redistribution
Network Requirements
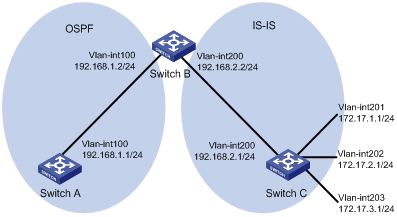
l As shown in the following figure, Switch B exchanges routing information with Switch A using OSPF, and with Switch C using IS-IS.
l On Switch B, enable route redistribution from IS-IS to OSPF and apply a route policy to set the cost of route 172.17.1.0/24 to 100, and the tag of route 172.17.2.0/24 to 20.
Network diagram
Figure 1-1 Network diagram for route policy application to route redistribution
Configuration procedure
1) Specify IP addresses for interfaces (omitted).
2) Configure IS-IS.
# Configure Switch C.
<SwitchC> system-view
[SwitchC] isis
[SwitchC-isis-1] is-level level-2
[SwitchC-isis-1] network-entity 10.0000.0000.0001.00
[SwitchC-isis-1] quit
[SwitchC] interface vlan-interface 200
[SwitchC-Vlan-interface200] isis enable
[SwitchC-Vlan-interface200] quit
[SwitchC] interface vlan-interface 201
[SwitchC-Vlan-interface201] isis enable
[SwitchC-Vlan-interface201] quit
[SwitchC] interface vlan-interface 202
[SwitchC-Vlan-interface202] isis enable
[SwitchC-Vlan-interface202] quit
[SwitchC] interface vlan-interface 203
[SwitchC-Vlan-interface203] isis enable
[SwitchC-Vlan-interface203] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] isis
[SwitchB-isis-1] is-level level-2
[SwitchB-isis-1] network-entity 10.0000.0000.0002.00
[SwitchB-isis-1] quit
[SwitchB] interface vlan-interface 200
[SwitchB-Vlan-interface200] isis enable
[SwitchB-Vlan-interface200] quit
3) Configure OSPF and route redistribution
# Configure OSPF on Switch A.
<SwitchA> system-view
[SwitchA] ospf
[SwitchA-ospf-1] area 0
[SwitchA-ospf-1-area-0.0.0.0] network 192.168.1.0 0.0.0.255
[SwitchA-ospf-1-area-0.0.0.0] quit
[SwitchA-ospf-1] quit
# On Switch B, configure OSPF and enable route redistribution from IS-IS.
[SwitchB] ospf
[SwitchB-ospf-1] area 0
[SwitchB-ospf-1-area-0.0.0.0] network 192.168.1.0 0.0.0.255
[SwitchB-ospf-1-area-0.0.0.0] quit
[SwitchB-ospf-1] import-route isis 1
[SwitchB-ospf-1] quit
# Display the OSPF routing table on Switch A to view redistributed routes.
[SwitchA] display ospf routing
OSPF Process 1 with Router ID 192.168.1.1
Routing Tables
Routing for Network
Destination Cost Type NextHop AdvRouter Area
192.168.1.0/24 1562 Stub 192.168.1.1 192.168.1.1 0.0.0.0
Routing for ASEs
Destination Cost Type Tag NextHop AdvRouter
172.17.1.0/24 1 Type2 1 192.168.1.2 192.168.2.2
172.17.2.0/24 1 Type2 1 192.168.1.2 192.168.2.2
172.17.3.0/24 1 Type2 1 192.168.1.2 192.168.2.2
192.168.2.0/24 1 Type2 1 192.168.1.2 192.168.2.2
Total Nets: 5
Intra Area: 1 Inter Area: 0 ASE: 4 NSSA: 0
4) Configure filtering lists
# Configure ACL 2002 to permit route 172.17.2.0/24.
[SwitchB] acl number 2002
[SwitchB-acl-basic-2002] rule permit source 172.17.2.0 0.0.0.255
[SwitchB-acl-basic-2002] quit
# Configure IP prefix list prefix-a to permit route 172.17.1.0/24.
[SwitchB] ip ip-prefix prefix-a index 10 permit 172.17.1.0 24
5) Configure a route policy.
[SwitchB] route-policy isis2ospf permit node 10
[SwitchB-route-policy] if-match ip-prefix prefix-a
[SwitchB-route-policy] apply cost 100
[SwitchB-route-policy] quit
[SwitchB] route-policy isis2ospf permit node 20
[SwitchB-route-policy] if-match acl 2002
[SwitchB-route-policy] apply tag 20
[SwitchB-route-policy] quit
[SwitchB] route-policy isis2ospf permit node 30
[SwitchB-route-policy] quit
6) Apply the route policy to route redistribution.
# On Switch B, apply the route policy when redistributing routes.
[SwitchB] ospf
[SwitchB-ospf-1] import-route isis 1 route-policy isis2ospf
[SwitchB-ospf-1] quit
# Display the OSPF routing table on Switch A. The cost of route 172.17.1.0/24 is 100, the tag of route 172.17.1.0/24 is 20.
[SwitchA] display ospf routing
OSPF Process 1 with Router ID 192.168.1.1
Routing Tables
Routing for Network
Destination Cost Type NextHop AdvRouter Area
192.168.1.0/24 1 Transit 192.168.1.1 192.168.1.1 0.0.0.0
Routing for ASEs
Destination Cost Type Tag NextHop AdvRouter
172.17.1.0/24 100 Type2 1 192.168.1.2 192.168.2.2
172.17.2.0/24 1 Type2 20 192.168.1.2 192.168.2.2
172.17.3.0/24 1 Type2 1 192.168.1.2 192.168.2.2
192.168.2.0/24 1 Type2 1 192.168.1.2 192.168.2.2
Total Nets: 5
Intra Area: 1 Inter Area: 0 ASE: 4 NSSA: 0
Applying a Route Policy to IPv6 Route Redistribution
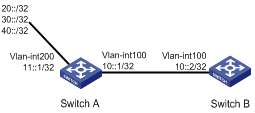
Network requirements
l Enable RIPng on Switch A and Switch B.
l On Switch A, configure three static routes, and apply a route policy to static route redistribution to permit routes 20::0/32 and 40::0/32, and deny route 30::0/32.
l Display RIPng routing table information on Switch B to verify the configuration.
Network diagram
Figure 1-2 Network diagram for route policy application to route redistribution
Configuration procedure
1) Configure Switch A.
# Configure IPv6 addresses for VLAN-interface 100 and VLAN-interface 200.
<SwitchA> system-view
[SwitchA] ipv6
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] ipv6 address 10::1 32
[SwitchA-Vlan-interface100] quit
[SwitchA] interface vlan-interface 200
[SwitchA-Vlan-interface200] ipv6 address 11::1 32
[SwitchA-Vlan-interface200] quit
# Enable RIPng on VLAN-interface 100.
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] ripng 1 enable
[SwitchA-Vlan-interface100] quit
# Configure three static routes.
[SwitchA] ipv6 route-static 20:: 32 11::2
[SwitchA] ipv6 route-static 30:: 32 11::2
[SwitchA] ipv6 route-static 40:: 32 11::2
# Configure a route policy.
[SwitchA] ip ipv6-prefix a index 10 permit 30:: 32
[SwitchA] route-policy static2ripng deny node 0
[SwitchA-route-policy] if-match ipv6 address prefix-list a
[SwitchA-route-policy] quit
[SwitchA] route-policy static2ripng permit node 10
[SwitchA-route-policy] quit
# Enable RIPng and and apply the route policy to static route redistribution.
[SwitchA] ripng
[SwitchA-ripng-1] import-route static route-policy static2ripng
2) Configure Switch B.
# Configure the IPv6 address for VLAN-interface 100.
[SwitchB] ipv6
[SwitchB] interface vlan-interface 100
[SwitchB-Vlan-interface100] ipv6 address 10::2 32
# Enable RIPng on VLAN-interface 100.
[SwitchB-Vlan-interface100] ripng 1 enable
[SwitchB-Vlan-interface100] quit
# Enable RIPng.
[SwitchB] ripng
# Display RIPng routing table information.
[SwitchB-ripng-1] display ripng 1 route
Route Flags: A - Aging, S - Suppressed, G - Garbage-collect
----------------------------------------------------------------
Peer FE80::7D58:0:CA03:1 on Vlan-interface 100
Dest 10::/32,
via FE80::7D58:0:CA03:1, cost 1, tag 0, A, 18 Sec
Dest 20::/32,
via FE80::7D58:0:CA03:1, cost 1, tag 0, A, 8 Sec
Dest 40::/32,
via FE80::7D58:0:CA03:1, cost 1, tag 0, A, 3 Sec
Applying a Route Policy to Filter Received BGP Routes
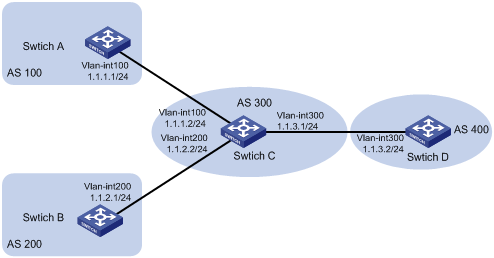
Network requirements
l All the switches run BGP. Switch C establishes eBGP connections with other switches.
l Configure a route policy on Switch D to reject routes from AS 200.
Network diagram
Figure 1-3 Route policy configuration to filter received BGP routes
Configuration procedure
1) Configure IP addresses for the interfaces (omitted).
2) Configure BGP.
# Configure Switch A.
<SwitchA> system-view
[SwitchA] bgp 100
[SwitchA-bgp] router-id 1.1.1.1
[SwitchA-bgp] peer 1.1.1.2 as-number 300
# Configure Switch B.
<SwitchB> system-view
[SwitchB] bgp 200
[SwitchB-bgp] router-id 2.2.2.2
[SwitchB-bgp] peer 1.1.2.2 as-number 300
# Configure Switch C.
<SwitchC> system-view
[SwitchC] bgp 300
[SwitchC-bgp] router-id 3.3.3.3
[SwitchC-bgp] peer 1.1.1.1 as-number 100
[SwitchC-bgp] peer 1.1.2.1 as-number 200
[SwitchC-bgp] peer 1.1.3.2 as-number 400
# Configure Switch D.
<SwitchD> system-view
[SwitchD] bgp 400
[SwitchD-bgp] router-id 4.4.4.4
[SwitchD-bgp] peer 1.1.3.1 as-number 300
[SwitchD-bgp] quit
# On Switch A, inject routes 4.4.4.4/24, 5.5.5.5/24, and 6.6.6.6/24 to BGP.
[SwitchA-bgp] network 4.4.4.4 24
[SwitchA-bgp] network 5.5.5.5 24
[SwitchA-bgp] network 6.6.6.6 24
# On Switch B, inject routes 7.7.7.7/24, 8.8.8.8/24, and 9.9.9.9/24 to BGP.
[SwitchB-bgp] network 7.7.7.7 24
[SwitchB-bgp] network 8.8.8.8 24
[SwitchB-bgp] network 9.9.9.9 24
# Display the BGP routing table information of Switch D.
[SwitchD-bgp] display bgp routing-table
Total Number of Routes: 6
BGP Local router ID is 4.4.4.4
Status codes: * - valid, > - best, d - damped,
h - history, i - internal, s - suppressed, S - Stale
Origin : i - IGP, e - EGP, ? - incomplete
Network NextHop MED LocPrf PrefVal Path/Ogn
*> 4.4.4.0/24 1.1.3.1 0 300 100i
*> 5.5.5.0/24 1.1.3.1 0 300 100i
*> 6.6.6.0/24 1.1.3.1 0 300 100i
*> 7.7.7.0/24 1.1.3.1 0 300 200i
*> 8.8.8.0/24 1.1.3.1 0 300 200i
*> 9.9.9.0/24 1.1.3.1 0 300 200i
The display above shows that Switch D has learned routes 4.4.4.0/24, 5.5.5.0/24, and 6.6.6.0/24 from AS 100 and 7.7.7.0/24, 8.8.8.0/24, and 9.9.9.0/24 from AS 200.
3) Configure Switch D to reject routes from AS 200.
# Configure AS_PATH list 1 on Switch D.
[SwitchD] ip as-path 1 permit .*200.*
# Configure a route policy named rt1 on Switch D.
[SwitchD] route-policy rt1 deny node 1
[SwitchD] if-match as-path 1
[SwitchD] route-policy rt2 permit node 2
# On Switch D, specify route policy rt1 to filter routes received from peer 1.1.3.1.
[SwitchD] bgp 400
[SwitchD] peer 1.1.3.1 route-policy rt1 import
# Display the BGP routing table information of Switch D.
[SwitchD] display bgp routing-table
Total Number of Routes: 3
BGP Local router ID is 4.4.4.4
Status codes: * - valid, > - best, d - damped,
h - history, i - internal, s - suppressed, S - Stale
Origin : i - IGP, e - EGP, ? - incomplete
Network NextHop MED LocPrf PrefVal Path/Ogn
*> 4.4.4.0/24 1.1.3.1 0 300 100i
*> 5.5.5.0/24 1.1.3.1 0 300 100i
*> 6.6.6.0/24 1.1.3.1 0 300 100i
The display above shows that Switch D has learned only routes 4.4.4.0/24, 5.5.5.0/24, and 6.6.6.0/24 from AS 100.
Troubleshooting Route Policy Configuration
IPv4 Routing Information Filtering Failure
Symptom
Filtering routing information failed, while the routing protocol runs normally.
Analysis
At least one item of the IP prefix list should be configured as permit mode, and at least one node in the Route policy should be configured as permit mode.
Solution
1) Use the display ip ip-prefix command to display IP prefix list information.
2) Use the display route-policy command to display route policy information.
IPv6 Routing Information Filtering Failure
Symptom
Filtering routing information failed, while the routing protocol runs normally.
Analysis
At least one item of the IPv6 prefix list should be configured as permit mode, and at least one node of the Route policy should be configured as permit mode.
Solution
1) Use the display ip ipv6-prefix command to display IP prefix list information.
2) Use the display route-policy command to display route policy information.

