- Table of Contents
-
- 03-IP Routing Volume
- 00-IP Routing Volume Organization
- 01-IP Routing Overview
- 02-Static Routing Configuration
- 03-RIP Configuration
- 04-OSPF Configuration
- 05-IS-IS Configuration
- 06-BGP Configuration
- 07-IPv6 Static Routing Configuration
- 08-IPv6 Ripng Configuration
- 09-IPv6 OSPFv3 Configuration
- 10-IPv6 IS-IS Configuration
- 11-IPv6 BGP Configuration
- 12-Routing Policy Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 02-Static Routing Configuration | 87.63 KB |
Table of Contents
1 Static Routing Configuration
Application Environment of Static Routing
Detecting Reachability of the Static Route’s Nexthop
Detecting Nexthop Reachability Through Track
Displaying and Maintaining Static Routes
When configuring a static route, go to these sections for information you are interested in:
l Detecting Reachability of the Static Route’s Nexthop
l Displaying and Maintaining Static Routes
![]()
The term “router” in this document refers to a router in a generic sense or a Layer 3 switch.
Introduction
Static Route
A static route is a manually configured. If a network’s topology is simple, you only need to configure static routes for the network to work normally. The proper configuration and usage of static routes can improve network performance and ensure bandwidth for important network applications.
The disadvantage of using static routes is that they cannot adapt to network topology changes. If a fault or a topological change occurs in the network, the routes will be unreachable and the network breaks. In this case, the network administrator has to modify the static routes manually.
Default Route
If the destination address of a packet fails to match any entry in the routing table, the packet will be discarded.
After a default route is configured on a router, any packet whose destination IP address matches no entry in the routing table can be forwarded to a designated upstream router.
A router selects the default route only when it cannot find any matching entry in the routing table.
l If there is no default route and the destination address of the packet fails to match any entry in the routing table, the packet will be discarded and an ICMP packet will be sent to the source to report that the destination or the network is unreachable.
Default routes can be configured in two ways:
l The network administrator can configure a default route with both destination and mask being 0.0.0.0. The router forwards any packet whose destination address fails to match any entry in the routing table to the next hop of the default static route.
l Some dynamic routing protocols, such as OSPF, RIP and IS-IS, can also generate a default route. For example, an upstream router running OSPF can generate a default route and advertise it to other routers, which install the default route with the next hop being the upstream router.
Application Environment of Static Routing
Before configuring a static route, you need to know the following concepts:
1) Destination address and mask
In the ip route-static command, an IPv4 address is in dotted decimal format and a mask can be either in dotted decimal format or in the form of mask length (the digits of consecutive 1s in the mask).
2) Output interface and next hop address
While configuring a static route, you can specify either the output interface or the next hop address depending on the specific occasion. For a Null0 interface, if the output interface has already been configured, there is no need to configure the next hop address
In fact, all the route entries must have a next hop address. When forwarding a packet, a router first searches the routing table for the route to the destination address of the packet. The system can find the corresponding link layer address and forward the packet only after the next hop address is specified. The next hop address can not be a local interface IP address; otherwise, the route configuration will not take effect.
3) Other attributes
You can configure different preferences for different static routes so that route management policies can be applied more flexibly. For example, specifying the same preference for different routes to the same destination enables load sharing, while specifying different preferences for these routes enables route backup.
Configuring a Static Route
Configuration Prerequisites
Before configuring a static route, you need to finish the following tasks:
l Configure the physical parameters for related interfaces
l Configure the link-layer attributes for related interfaces
l Configure the IP addresses for related interfaces
Configuration Procedure
Follow these steps to configure a static route:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure a static route |
ip route-static dest-address { mask | mask-length } { next-hop-address | interface-type interface-number next-hop-address | vpn-instance d-vpn-instance-name next-hop-address } [ preference preference-value ] [ tag tag-value ] [ description description-text ] |
Required By default, preference for static routes is 60, tag is 0, and no description information is configured. |
|
ip route-static vpn-instance s-vpn-instance-name&<1-6> dest-address { mask | mask-length } { next-hop-address [ public ] | interface-type interface-number next-hop-address | vpn-instance d-vpn-instance-name next-hop-address } [ preference preference-value ] [ tag tag-value ] [ description description-text ] |
||
|
Configure the default preference for static routes |
ip route-static default-preference default-preference-value |
Optional 60 by default |
![]()
l When configuring a static route, the static route does not take effect if you specify the next hop address first and then configure it as the IP address of a local interface.
l If you do not specify the preference when configuring a static route, the default preference will be used. Reconfiguring the default preference applies only to newly created static routes.
l You can flexibly control static routes by configuring tag values and using the tag values in the routing policy.
l If the destination IP address and mask are both configured as 0.0.0.0 with the ip route-static command, the route is the default route.
Detecting Reachability of the Static Route’s Nexthop
If a static route fails due to a topology change or a fault, the connection will be interrupted. To improve network stability, the system needs to detect reachability of the static route’s next hop and switch to a backup route once the next hop is unreachable.
Detecting Nexthop Reachability Through Track
If you specify the nexthop but not outgoing interface when configuring a static route, you can associate the static route with a track entry to check the static route validity:
l When the track entry is positive, the static route's nexthop is reachable and the static route takes effect.
l When the track entry is negative, the static route's nexthop is unreachable and the static route is invalid. For details about track, refer to Track Configuration in the System Volume.
Network requirements
To detect the reachability of a static route's nexthop through a Track entry, you need to create a Track first. For detailed Track configuration procedure, refer to Track Configuration in the System Volume.
Configuration procedure
Follow these steps to detect the reachability of a static route's nexthop through Track:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Associate the static route with a track entry |
ip route-static dest-address { mask | mask-length } { next-hop-address | vpn-instance d-vpn-instance-name next-hop-address } track track-entry-number [ preference preference-value ] [ tag tag-value ] [ description description-text ] |
Required Not configured by default |
|
ip route-static vpn-instance s-vpn-instance-name&<1-6> dest-address { mask | mask-length } { next-hop-address track track-entry-number [ public ] | vpn-instance d-vpn-instance-name next-hop-address track track-entry-number } [ preference preference-value ] [ tag tag-value ] [ description description-text ] |
![]()
l To configure this feature for an existing static route, simply associate the static route with a track entry. For a non-existent static route, configure it and associate it with a Track entry.
l If the track module uses NQA to detect the reachability of the private network static route's nexthop, the VPN instance number of the static route's nexthop must be identical to that configured in the NQA test group.
l If a static route needs route recursion, the associated track entry must monitor the nexthop of the recursive route instead of that of the static route; otherwise, a valid route may be mistakenly considered invalid.
Displaying and Maintaining Static Routes
|
To do… |
Use the command… |
Remarks |
|
Display the current configuration information |
display current-configuration |
Available in any view |
|
Display the brief information of the IP routing table |
display ip routing-table |
|
|
Display the detailed information of the IP routing table |
display ip routing-table verbose |
|
|
View information of static routes |
display ip routing-table protocol static [ inactive | verbose ] |
|
|
Delete all the static routes |
delete [ vpn-instance vpn-instance-name ] static-routes all |
Available In system view |
Configuration Example
Network requirements
The IP addresses and masks of the switches and hosts are shown in the following figure. Static routes are required for interconnection between any two hosts.
Network diagram
Figure 1-1 Network diagram for static route configuration
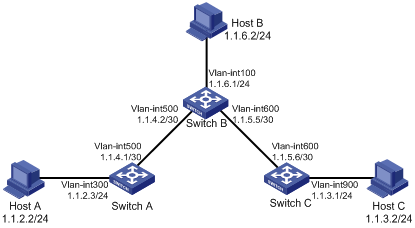
Configuration procedure
1) Configuring IP addresses for interfaces (omitted)
2) Configuring static routes
# Configure a default route on Switch A.
<SwitchA> system-view
[SwitchA] ip route-static 0.0.0.0 0.0.0.0 1.1.4.2
# Configure two static routes on Switch B.
<SwitchB> system-view
[SwitchB] ip route-static 1.1.2.0 255.255.255.0 1.1.4.1
[SwitchB] ip route-static 1.1.3.0 255.255.255.0 1.1.5.6
# Configure a default route on Switch C
<SwitchC> system-view
[SwitchC] ip route-static 0.0.0.0 0.0.0.0 1.1.5.5
3) Configure the hosts.
The default gateways for the three hosts A, B and C are 1.1.2.3, 1.1.6.1 and 1.1.3.1 respectively. The configuration procedure is omitted.
4) Display the configuration.
# Display the IP routing table of Switch A.
[SwitchA] display ip routing-table
Routing Tables: Public
Destinations : 7 Routes : 7
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/0 Static 60 0 1.1.4.2 Vlan500
1.1.2.0/24 Direct 0 0 1.1.2.3 Vlan300
1.1.2.3/32 Direct 0 0 127.0.0.1 InLoop0
1.1.4.0/30 Direct 0 0 1.1.4.1 Vlan500
1.1.4.1/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
# Display the IP routing table of Switch B.
[SwitchB] display ip routing-table
Routing Tables: Public
Destinations : 10 Routes : 10
Destination/Mask Proto Pre Cost NextHop Interface
1.1.2.0/24 Static 60 0 1.1.4.1 Vlan500
1.1.3.0/24 Static 60 0 1.1.5.6 Vlan600
1.1.4.0/30 Direct 0 0 1.1.4.2 Vlan500
1.1.4.2/32 Direct 0 0 127.0.0.1 InLoop0
1.1.5.4/30 Direct 0 0 1.1.5.5 Vlan600
1.1.5.5/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
1.1.6.0/24 Direct 0 0 192.168.1.47 Vlan100
1.1.6.1/32 Direct 0 0 127.0.0.1 InLoop0
# Use the ping command on Host B to check reachability to Host A, assuming Windows XP runs on the two hosts.
C:\Documents and Settings\Administrator>ping 1.1.2.2
Pinging 1.1.2.2 with 32 bytes of data:
Reply from 1.1.2.2: bytes=32 time=1ms TTL=255
Reply from 1.1.2.2: bytes=32 time=1ms TTL=255
Reply from 1.1.2.2: bytes=32 time=1ms TTL=255
Reply from 1.1.2.2: bytes=32 time=1ms TTL=255
Ping statistics for 1.1.2.2:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 1ms, Average = 1ms
# Use the tracert command on Host B to check reachability to Host A.
[HostB] tracert 1.1.2.2
Tracing route to 1.1.2.2 over a maximum of 30 hops
1 <1 ms <1 ms <1 ms 1.1.6.1
2 <1 ms <1 ms <1 ms 1.1.4.1
3 1 ms <1 ms <1 ms 1.1.2.2
Trace complete.

