- Table of Contents
-
- 03-IP Routing Volume
- 00-IP Routing Volume Organization
- 01-IP Routing Overview
- 02-Static Routing Configuration
- 03-RIP Configuration
- 04-OSPF Configuration
- 05-IS-IS Configuration
- 06-BGP Configuration
- 07-IPv6 Static Routing Configuration
- 08-IPv6 Ripng Configuration
- 09-IPv6 OSPFv3 Configuration
- 10-IPv6 IS-IS Configuration
- 11-IPv6 BGP Configuration
- 12-Routing Policy Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 05-IS-IS Configuration | 682.62 KB |
Table of Contents
Configuring IS-IS Basic Functions
Configuring the IS Level and Circuit Level
Configuring the Network Type of an Interface as P2P
Configuring IS-IS Routing Information Control
Specifying a Priority for IS-IS
Configuring the Maximum Number of Equal Cost Routes
Configuring IS-IS Route Summarization
Configuring IS-IS Route Redistribution
Configuring IS-IS Route Filtering
Configuring IS-IS Route Leaking
Tuning and Optimizing IS-IS Networks
Specifying Intervals for Sending IS-IS Hello and CSNP Packets
Specifying the IS-IS Hello Multiplier
Configuring a DIS Priority for an Interface
Disabling an Interface from Sending/Receiving IS-IS Packets
Enabling an Interface to Send Small Hello Packets
Configuring IS-IS Authentication
Configuring Neighbor Relationship Authentication
Configuring Area Authentication
Configuring Routing Domain Authentication
Configuring System ID to Host Name Mappings
Configuring a Static System ID to Host Name Mapping
Configuring Dynamic System ID to Host Name Mapping
Enabling the Logging of Neighbor State Changes
Displaying and Maintaining IS-IS
Configuring IS-IS Route Redistribution
IS-IS-based Graceful Restart Configuration Example
IS-IS Authentication Configuration Example
1 IS-IS Configuration
When configuring IS-IS, go to these sections for information you are interested in:
l IS-IS Configuration Task List
l Configuring IS-IS Basic Functions
l Configuring IS-IS Routing Information Control
l Tuning and Optimizing IS-IS Networks
l Configuring IS-IS Authentication
l Configuring System ID to Host Name Mappings
l Enabling the Logging of Neighbor State Changes
l Displaying and Maintaining IS-IS
![]()
The term “router” in this document refers to a router in a generic sense or a Layer 3 switch.
IS-IS Overview
Intermediate System-to-Intermediate System (IS-IS) is a dynamic routing protocol designed by the International Organization for Standardization (ISO) to operate on the connectionless network protocol (CLNP).
The IS-IS routing protocol was modified and extended in RFC 1195 by the International Engineer Task Force (IETF) for application in both TCP/IP and OSI reference models, and the new one is called Integrated IS-IS or Dual IS-IS.
IS-IS is an Interior Gateway Protocol (IGP) used within an Autonomous System. It adopts the Shortest Path First (SPF) algorithm for route calculation.
Basic Concepts
IS-IS terminology
l Intermediate system (IS). An IS, similar to a router in TCP/IP, is the basic unit in IS-IS to generate and propagate routing information. In the following text, an IS refers to a router.
l End system (ES). An ES refers to a host system in TCP/IP. ISO defines the ES-IS protocol for communication between an ES and an IS, and therefore an ES does not participate in the IS-IS processing.
l Routing domain (RD). A group of ISs exchanges routing information with each other using the same routing protocol in a routing domain.
l Area. An area is a unit in a routing domain. The IS-IS protocol allows a routing domain to be divided into multiple areas.
l Link State Database (LSDB). All link states in the network forms the LSDB. There is at least one LSDB in each IS. The IS uses the SPF algorithm and LSDB to generate its own routes.
l Link State Protocol Data Unit (LSPDU) or Link State Packet (LSP). Each IS can generate an LSP which contains all the link state information of the IS.
l Network Protocol Data Unit (NPDU). An NPDU is a network layer protocol packet in OSI, which is equivalent to an IP packet in TCP/IP.
l Designated IS. On a broadcast network, the designated router is also known as the designated IS.
l Network service access point (NSAP). An NSAP is an OSI network layer address. It identifies an abstract network service access point and describes the network address in the OSI reference model.
IS-IS address format
1) NSAP
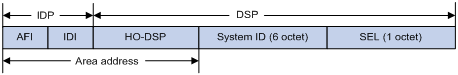
As shown in Figure 1-1, an NSAP address consists of the Initial Domain Part (IDP) and the Domain Specific Part (DSP). The IDP is equal to the network ID of an IP address, and the DSP is equal to the subnet and host ID.
The IDP includes the Authority and Format Identifier (AFI) and the Initial Domain Identifier (IDI).
The DSP includes the High Order Part of DSP (HO-DSP), System ID and SEL, where the HO-DSP identifies the area, the System ID identifies the host, and the SEL identifies the type of service.
The IDP and DSP are variable in length. The length of an NSAP address varies from 8 bytes to 20 bytes.
Figure 1-1 NSAP address format
2) Area address
The area address comprises the IDP and the HODSP of the DSP, which identify the area and the routing domain. Different routing domains cannot have the same area address.
Generally, a router only needs one area address, and all nodes in the same routing domain must share the same area address. However, a router can have three area addresses at most to support smooth area merging, partitioning and switching.
3) System ID
A system ID identifies a host or router uniquely. It has a fixed length of 48 bits (6 bytes).
The system ID of a device can be generated from the Router ID. For example, a router uses the IP address 168.10.1.1 of Loopback 0 as the Router ID, and the system ID in IS-IS can be obtained in the following way:
l Extend each decimal number of the IP address to 3 digits by adding 0s from the left, like 168.010.001.001;
l Divide the extended IP address into 3 sections with 4 digits in each section to get the system ID 1680.1000.1001.
There are other methods to define a system ID. The principle is to make sure it can uniquely identify a host or router.
4) SEL
The NSAP Selector (SEL), or the N-SEL, is similar to the protocol identifier in IP. Different transport layer protocols correspond to different SELs. All SELs in IP are 00.
NET
A network entity title (NET) indicates the network layer information of an IS and does not include transport layer information. It is a special NSAP address with the SEL being 0. Therefore, the length of the NET is equal to the NSAP and is in the range 8 bytes to 20 bytes.
Generally, a router only needs one NET, but it can have three NETs at most for smooth area merging and partitioning. When you configure multiple NETs, make sure their system IDs are the same.
For example, a NET is ab.cdef.1234.5678.9abc.00, where,
Area = ab.cdef, System ID = 1234.5678.9abc, and SEL = 00.
IS-IS Area
Two-level hierarchy
IS-IS has a two-level hierarchy to support large scale networks. A large scale routing domain is divided into multiple Areas. Typically, a Level-1 router is deployed within an area, a Level-2 router is deployed between areas, and a Level-1-2 router is deployed between Level-1 and Level-2 routers.
Level-1 and Level-2
1) Level-1 router
A Level-1 router establishes neighbor relationships with Level-1 and Level-1-2 routers in the same area. The LSDB maintained by the Level-1 router contains the local area routing information. It directs the packets destined for an outside area to the nearest Level-1-2 router.
2) Level-2 router
A Level-2 router establishes neighbor relationships with the Level-2 and Level-1-2 routers in the same or in different areas. It maintains a Level-2 LSDB which contains inter-area routing information. All the Level-2 and Level-1-2 routers must be contiguous to form the backbone of a routing domain.
3) Level-1-2 router
A router with both Level-1 and Level-2 router functions is a Level-1-2 router. It can establish Level-1 neighbor relationships with the Level-1 and Level-1-2 routers in the same area, or establish Level-2 neighbor relationships with the Level-2 and Level-1-2 routers in different areas. A Level-1 router must be connected to other areas through a Level-1-2 router. The Level-1-2 router maintains two LSDBs, where the Level-1 LSDB is for routing within the area, and the Level-2 LSDB is for routing between areas.
![]()
l The Level-1 routers in different areas can not establish neighbor relationships.
l The neighbor relationship establishment of Level-2 routers has nothing to do with area.
Figure 1-2 shows an IS-IS network topology. Area 1 comprises a set of Level-2 routers and is the backbone. The other four areas are non-backbone areas connected to the backbone through Level-1-2 routers.
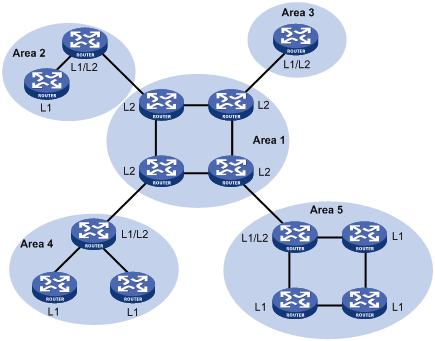
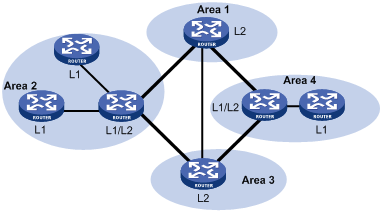
Figure 1-3 shows another IS-IS topology. The Level-1-2 routers connect to the Level-1 and Level-2 routers, and form the IS-IS backbone together with the Level-2 routers. There is no area defined as the backbone in this topology. The backbone comprises all contiguous Level-2 and Level-1-2 routers which can reside in different areas.
![]()
The IS-IS backbone does not need to be a specific Area.
Both the IS-IS Level-1 and Level-2 routers use the SPF algorithm to generate the shortest path tree (SPT).
Routing method
A Level-1 router makes routing decisions based on the system ID. If the destination is not in the area, the packet is forwarded to the nearest Level-1-2 router.
A Level-2 router routes packets across areas according to the area address.
Route leaking
An IS-IS routing domain is comprised of only one Level-2 area and multiple Level-1 areas. A Level-1 area consists of a group of Level-1 routers and is connected with a Level-2 area rather than other Level-1 areas.
The routing information of a Level-1 area is sent to the Level-2 area through the Level-1-2 router. Therefore, the Level-2 router knows the routing information of the entire IS-IS routing domain but does not share the information of other Level-1 areas and the Level-2 area with the Level-1 area by default.
Since a Level-1 router simply sends packets destined for other areas to the nearest Level-1-2 router, this may cause that the best paths cannot be selected.
To solve this problem, route leaking was introduced. A Level-2 router can advertise Level-2 routing information to a specified Level-1 area. By having the routing information of other areas, a Level-1 router in the area can make a better routing decision for a packet to another area.
IS-IS Network Type
Network type
IS-IS supports two network types:
l Broadcast network, such as Ethernet, Token-Ring.
l Point-to-point network, such as PPP, HDLC.
![]()
For a Non-Broadcast Multi-Access (NBMA) interface, such as an ATM interface, you need to configure subinterfaces for it and configure the interface type for the subinterfaces as point-to-point or broadcast. IS-IS cannot run on point to multipoint (P2MP) links.
DIS and pseudonodes
On an IS-IS broadcast network, a router is elected as the Designated Intermediate System (DIS).
The Level-1 and Level-2 DISs are elected respectively. You can assign different priorities for different level DIS elections. The higher a router’s priority is, the more likelihood the router becomes the DIS. If there are multiple routers with the same highest DIS priority, the one with the highest SNPA (Subnetwork Point of Attachment) address (MAC address on a broadcast network) will be elected. A router can be the DIS for different levels.
As shown in Figure 1-4, the same level routers on a network including non-DIS routers establish adjacencies with each other.
Figure 1-4 DIS in the IS-IS broadcast network
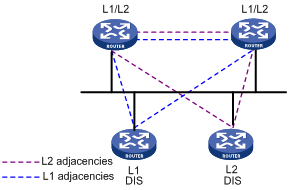
The DIS creates and updates pseudonodes as well as generates their LSPs to describe all routers on the network.
A pseudonode represents a virtual node on the broadcast network. It is not a real router. In IS-IS, it is identified by the system ID of the DIS and a one-byte Circuit ID (a non zero value).
Using pseudonodes can reduce the resources consumed by SPF and simplify network topology.
![]()
On IS-IS broadcast networks, all routers are adjacent with each other. However, the DIS is responsible for the synchronization of their LSDBs.
IS-IS PDU Format
PDU header format
IS-IS packets are encapsulated into link layer frames. The Protocol Data Unit (PDU) consists of two parts, the headers and the variable length fields, where the headers comprise the PDU common header and the PDU specific header. All PDUs have the same PDU common header, while the specific headers vary by PDU type. The following figure shows the PDU format.
Figure 1-5 PDU format
![]()
Common header format
Figure 1-6 shows the PDU common header format.
Figure 1-6 PDU common header format
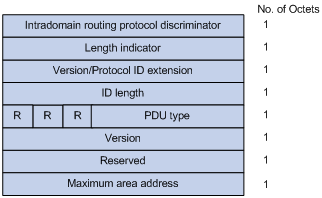
l Intradomain Routing Protocol Discriminator: Set to 0x83.
l Length Indicator: Length of the PDU header in bytes, including both common and specific headers.
l Version/Protocol ID Extension: Set to 1(0x01).
l ID Length: Length of the NSAP address and NET ID.
l R(Reserved): Set to 0.
l PDU Type: For details, refer to Table 1-1.
l Version: Set to 1(0x01).
l Maximum Area Address: Maximum number of area addresses supported.
Table 1-1 PDU type
|
Type |
PDU Type |
Acronym |
|
15 |
Level-1 LAN IS-IS hello PDU |
L1 LAN IIH |
|
16 |
Level-2 LAN IS-IS hello PDU |
L2 LAN IIH |
|
17 |
Point-to-Point IS-IS hello PDU |
P2P IIH |
|
18 |
Level-1 Link State PDU |
L1 LSP |
|
20 |
Level-2 Link State PDU |
L2 LSP |
|
24 |
Level-1 Complete Sequence Numbers PDU |
L1 CSNP |
|
25 |
Level-2 Complete Sequence Numbers PDU |
L2 CSNP |
|
26 |
Level-1 Partial Sequence Numbers PDU |
L1 PSNP |
|
27 |
Level-2 Partial Sequence Numbers PDU |
L2 PSNP |
Hello
Hello packets are used by routers to establish and maintain neighbor relationships. A hello packet is also called an IS-to-IS hello PDU (IIH). For broadcast networks, the Level-1 routers use the Level-1 LAN IIHs; and the Level-2 routers use the Level-2 LAN IIHs. The P2P IIHs are used on point-to-point networks.
Figure 1-7 illustrates the hello packet format in broadcast networks, where the blue fields are the common header.
Figure 1-7 L1/L2 LAN IIH format
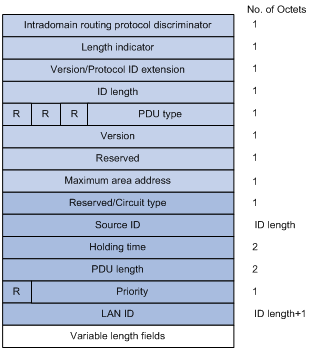
l Reserved/Circuit Type: The first 6 bits are reserved with a value of 0. The last 2 bits indicate the router type. 00 means reserved, 01 indicates L1, 10 indicates L2, and 11 indicates L1/2.
l Source ID: System ID of the router advertising the hello packet.
l Holding Time: If no hello packets are received from the neighbor within the holding time, the neighbor is considered down.
l PDU Length: Total length of the PDU in bytes.
l Priority: DIS priority.
l LAN ID: Includes the system ID and a one-byte pseudonode ID.
Figure 1-8 shows the hello packet format on the point-to-point networks.
Figure 1-8 P2P IIH format
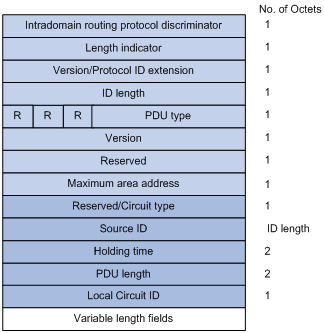
Instead of the priority and LAN ID fields in the LAN IIH, the P2P IIH has a Local Circuit ID field.
LSP packet format
The Link State PDUs (LSP) carry link state information. LSP involves two types: Level-1 LSP and Level-2 LSP. The Level-2 LSPs are sent by the Level-2 routers, and the Level-1 LSPs are sent by the Level-1 routers. The level-1-2 router can send both types of LSPs.
The two types of LSPs have the same format, as shown in Figure 1-9.
Figure 1-9 L1/L2 LSP format
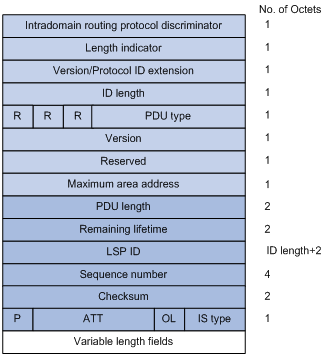
l PDU Length: Total length of the PDU in bytes.
l Remaining Lifetime: LSP remaining lifetime in seconds.
l LSP ID: Consists of the system ID, the pseudonode ID (one byte) and the LSP fragment number (one byte).
l Sequence Number: LSP sequence number.
l Checksum: LSP checksum.
l P (Partition Repair): Only for L2 LSPs. It indicates whether the router supports partition repair.
l ATT (Attachment): Generated by a L1/L1 router for L1 LSPs only. It indicates that the router generating the LSP is connected to multiple areas.
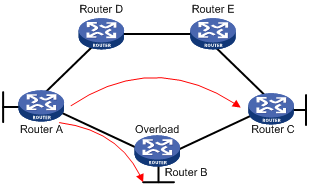
l OL (LSDB Overload): Indicates that the LSDB is not complete because the router runs out of memory. In this case, other routers will not send packets to the overloaded router, except packets destined to the networks directly connected to the router. For example, in Figure 1-10, Router A forwards packets to Router C through Router B. Once other routers know the OL field of LSPs from Router B is set to 1, Router A will send packets to Router C via Router D and Router E, but still send to Router B packets destined to the network directly connected to Router B.
l IS Type: Type of the router generating the LSP.
SNP format
A sequence number PDU (SNP) acknowledges the latest received LSPs. It is similar to an Acknowledge packet, but more efficient.
SNP involves Complete SNP (CSNP) and Partial SNP (PSNP), which are further divided into Level-1 CSNP, Level-2 CSNP, Level-1 PSNP and Leval-2 PSNP.
CSNP covers the summary of all LSPs in the LSDB to synchronize the LSDB between neighboring routers. On broadcast networks, CSNP is sent by the DIS periodically (10s by default). On point-to-point networks, CSNP is only sent during the first adjacency establishment.
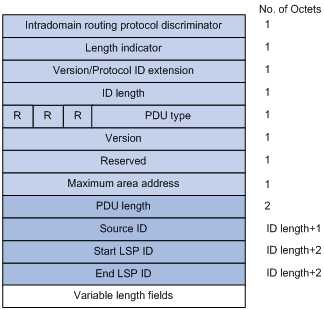
The CSNP packet format is shown in Figure 1-11.
Figure 1-11 L1/L2 CSNP format
PSNP only contains the sequence numbers of one or multiple latest received LSPs. It can acknowledge multiple LSPs at one time. When LSDBs are not synchronized, a PSNP is used to request new LSPs from neighbors.
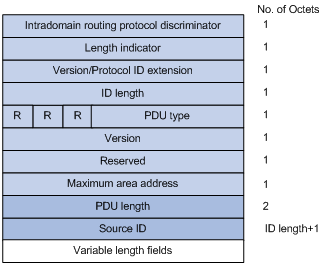
Figure 1-12 shows the PSNP packet format.
Figure 1-12 L1/L2 PSNP format
CLV
The variable fields of PDU comprise multiple Code-Length-Value (CLV) triplets. Figure 1-13 shows the CLV format.
Figure 1-13 CLV format
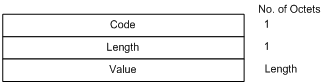
Table 1-2 shows that different PDUs contain different CLVs.
Table 1-2 CLV name and the corresponding PDU type
|
CLV Code |
Name |
PDU Type |
|
1 |
Area Addresses |
IIH, LSP |
|
2 |
IS Neighbors (LSP) |
LSP |
|
4 |
Partition Designated Level2 IS |
L2 LSP |
|
6 |
IS Neighbors (MAC Address) |
LAN IIH |
|
7 |
IS Neighbors (SNPA Address) |
LAN IIH |
|
8 |
Padding |
IIH |
|
9 |
LSP Entries |
SNP |
|
10 |
Authentication Information |
IIH, LSP, SNP |
|
128 |
IP Internal Reachability Information |
LSP |
|
129 |
Protocols Supported |
IIH, LSP |
|
130 |
IP External Reachability Information |
L2 LSP |
|
131 |
Inter-Domain Routing Protocol Information |
L2 LSP |
|
132 |
IP Interface Address |
IIH, LSP |
Code 1 to 10 of CLV are defined in ISO 10589 (code 3 and 5 are not shown in the table), and others are defined in RFC 1195.
Supported IS-IS Features
Multiple instances and processes
IS-IS supports multiple instances and processes. Multiple processes allow a IS-IS process to work in concert with a group of interfaces. This means that a router can run multiple IS-IS processes, and each process corresponds to a unique group of interfaces.
For routers supporting VPN, each IS-IS process is associated with a VPN instance. Thus, the VPN instance is also associated with interfaces corresponding to the process.
Hot standby
![]()
For detailed information about IS-IS hot standby, refer to HA configuration in the System Volume.
A distributed router supports IS-IS Hot Standby (HSB). The data is copied from the Active Main Board (AMB) to the Standby Main Board (SMB). Whenever the AMB is down, the SMB can switch to the active status to run IS-IS.
There are two kinds of IS-IS HSB. One is IS-IS data synchronization backup. After switching from AMB to SMB, IS-IS can work immediately.
The other HSB is to backup only the configuration information of IS-IS during the switching from AMB to SMB. After the graceful restart (GR), the IS-IS router will send requests to neighbors to synchronize the LSDB.
IS-IS Graceful Restart
![]()
For detailed GR information , refer to GR Configuration in the System Volume.
After an IS-IS GR Restarter restarts IS-IS, it needs to complete the following two tasks to synchronize the LSDB with its neighbors.
l To obtain effective IS-IS neighbor information without changing adjacencies.
l To obtain the LSDB contents.
After the restart, the GR Restarter will send an OSPF GR signal to its neighbors to keep the adjacencies. After receiving the responses from neighbors, the GR Restarter can restore the neighbor table.
After reestablishing neighborships, the GR Restarter will synchronize the LSDB and exchange routing information with all adjacent GR capable neighbors. After that, the GR Restarter will update its own routing table and forwarding table based on the new routing information and remove the stale routes. In this way, the IS-IS routing convergence is complete.
Management tag
Management tag simplifies routing information management by carrying the management information of the IP address prefixes (to control route redistribution from other routing protocols) and BGP community and extended community attributes.
LSP fragment extension
IS-IS advertises link state information by flooding LSPs. One LSP carries a limited amount of link state information; therefore, IS-IS fragments LSPs. Each LSP fragment is uniquely identified by a combination of the System ID, Pseudonode ID (0 for a common LSP or a non-zero value for a Pseudonode LSP), and LSP Number (LSP fragment number) of the node or pseudo node that generated the LSP. The one-byte LSP Number field, allowing a maximum of only 256 fragments to be generated by an IS-IS router, limits the amount of link information that the IS-IS router can advertise.
The LSP fragment extension feature allows an IS-IS router to generate more LSP fragments. Up to 50 additional virtual systems can be configured on the router, and each virtual system is capable of generating 256 LSP fragments to enable the IS-IS router to generate up to 13056 LSP fragments.
1) Terms
l Originating System
It is the router actually running IS-IS. After LSP fragment extension is enabled, additional virtual systems can be configured for the router. Originating system is the actual IS-IS process that originally runs.
l System ID: System ID of the originating system.
l Additional System ID
Additional virtual system IDs are configured for the IS-IS router after LSP fragment extension is enabled. Each additional system ID can generate 256 LSP fragments. Both the additional system ID and the system ID must be unique in the entire routing domain.
l Virtual System
A virtual system is identified by an additional system ID and generates extended LSP fragments.
l Original LSP
It is the LSP generated by the originating system. The system ID in its LSP ID field is the system ID of the originating system.
l Extended LSP
Extended LSPs are generated by virtual systems. The system ID in its LSP ID field is the virtual system ID.
After additional system IDs are configured, an IS-IS router can advertise more link state information in extended LSP fragments. Each virtual system can be considered a virtual router. An extended LSP fragment is advertised by a virtual system identified by an additional system ID.
2) Operation modes
The LSP fragment extension feature operates in two modes:
l Mode-1: Applicable to a network where some routers do not support LSP fragment extension. In this mode, adjacencies are formed between the originating system and virtual systems, with the link cost from the originating system to each virtual system as 0. Thus, each virtual system acts as a router connected to the originating system in the network, but the virtual systems are reachable through the originating system only. Therefore, the IS-IS routers not supporting LSP fragment extension can operate normally without modifying the extended LSP fragments received, but some limitation is imposed on the link state information in the extended LSP fragments advertised by the virtual systems.
l Mode-2: Applicable to a network where all the routers support LSP fragment extension. In this mode, all the IS-IS routers know which virtual system belongs to which originating system; therefore, no limitation is imposed on the link state information of the extended LSP fragments advertised by the virtual systems.
The operation mode of LSP fragment extension is configured based on area and routing level. Mode-1 allows the routers supporting and not supporting LSP fragment extension to interoperate with each other, but it restricts the link state information in the extended fragments. Mode-2 does not restrict the link state information in the extended fragments, and is recommended for an area where all the routers are at the same routing level and support LSP fragment extension.
Dynamic host name mapping mechanism
The dynamic host name mapping mechanism provides the mappings between the host names and the system IDs for the IS-IS routers. The dynamic host name information is announced in the dynamic host name CLV of an LSP.
This mechanism also provides the mapping between a host name and the DIS of a broadcast network, which is announced in the dynamic host name TLV of a pseudonode LSP.
A host name is easier to remember than a system ID. After enabling this feature on the router, you can see the host names instead of system IDs using the display command.
Protocols and Standards
l ISO 10589 ISO IS-IS Routing Protocol
l ISO 9542 ES-IS Routing Protocol
l ISO 8348/Ad2 Network Services Access Points
l RFC 1195 - Use of OSI IS-IS for Routing in TCP/IP and Dual Environments
l RFC 2763 - Dynamic Hostname Exchange Mechanism for IS-IS
l RFC 2966 - Domain-wide Prefix Distribution with Two-Level IS-IS
l RFC 2973 - IS-IS Mesh Groups
l RFC 3277 - IS-IS Transient Blackhole Avoidance
l RFC 3358 - Optional Checksums in ISIS
l RFC 3373 - Three-Way Handshake for IS-IS Point-to-Point Adjacencies
l RFC 3567 - Intermediate System to Intermediate System (IS-IS) Cryptographic Authentication
l RFC 3719 - Recommendations for Interoperable Networks using IS-IS
l RFC 3786 - Extending the Number of IS-IS LSP Fragments Beyond the 256 Limit
l RFC 3787 - Recommendations for Interoperable IP Networks using IS-IS
l RFC 3847 - Restart signaling for IS-IS
IS-IS Configuration Task List
Complete the following tasks to configure IS-IS:
|
Task |
Remarks |
|
|
Required |
||
|
Optional |
||
|
Required |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Specifying Intervals for Sending IS-IS Hello and CSNP Packets |
Optional |
|
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
|
Optional |
||
Configuring IS-IS Basic Functions
Configuration Prerequisites
Before the configuration, accomplish the following tasks:
l Configure the link layer protocol.
l Configure an IP address for each interface, and make sure all neighboring nodes are reachable to each other at the network layer.
Enabling IS-IS
Follow these steps to enable IS-IS:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enable the IS-IS routing process and enter its view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
Required Not enabled by default |
|
Assign a network entity title (NET) |
network-entity net |
Required Not assigned by default |
|
Return to system view |
quit |
–– |
|
Enter interface view |
interface interface-type interface-number |
–– |
|
Enable an IS-IS process on the interface |
isis enable [ process-id ] |
Required Disabled by default |
Configuring the IS Level and Circuit Level
If only one area is available, it is recommended that:
l Configure the IS level of all routers as Level-1 or Level-2 and don’t configure different levels in this case because there is no need for all routers to maintain two identical LSDBs;
l Configure the IS level as Level-2 on all routers in an IP network for scalability.
For an interface of a Level-1 (or Level-2) router, the circuit level can only be Level-1 (or Level-2). For an interface of a Level-1-2 router, the default circuit level is Level-1-2; if the router only needs to form Level-1 (or Level-2) neighbor relationships, you can configure the circuit level for its interfaces as Level-1 (or Level-2) to limit neighbor relationship establishment.
Follow these steps to configure the IS level and circuit level:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Specify the IS level |
is-level { level-1 | level-1-2 | level-2 } |
Optional The default is Level-1-2. |
|
Return to system view |
quit |
–– |
|
Enter interface view |
interface interface-type interface-number |
–– |
|
Specify the circuit level |
isis circuit-level [ level-1 | level-1-2 | level-2 ] |
Optional The default is Level-1-2. |
Configuring the Network Type of an Interface as P2P
Interfaces with different network types operate differently. For example, broadcast interfaces on a network need to elect the DIS and flood CSNP packets to synchronize the LSDBs, while P2P interfaces on a network need not elect the DIS and have a different LSDP synchronization mechanism.
If there are only two routers on a broadcast network, you can configure the network type of attached interfaces as P2P to avoid DIS election and CSNP flooding, saving network bandwidth and speeding up network convergence.
Follow these steps to configure the network type of an interface:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter interface view |
interface interface-type interface-number |
–– |
|
Configure the network type for the interface as P2P |
isis circuit-type p2p |
Optional By default, The network type of a VLAN interface is broadcast. |
![]()
You can only perform this configuration for a broadcast network with only two attached routers.
Configuring IS-IS Routing Information Control
Configuration Prerequisites
Before the configuration, accomplish the following tasks:
l Configure network layer addresses for interfaces, and make sure adjacent nodes are reachable to each other at the network layer.
l Enable IS-IS.
Configuring IS-IS Link Cost
The IS-IS cost of an interface is determined in the following order:
l ISIS cost specified in interface view.
l ISIS cost specified in system view. The cost is applied to the interfaces associated to the IS-IS process.
l Automatically calculated cost: When the cost style is wide or wide-compatible, IS-IS automatically calculates the cost using the formula: interface cost= (bandwidth reference value/interface bandwidth) ×10.
If none of the above costs is used, a default cost of 10 applies.
Configuring an IS-IS cost for an interface
Follow these steps to configure a cost for an interface:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Specify an IS-IS cost style |
cost-style { narrow | wide | wide-compatible | { compatible | narrow-compatible } [ relax-spf-limit ] } |
Optional narrow by default |
|
Return to system view |
quit |
–– |
|
Enter interface view |
interface interface-type interface-number |
–– |
|
Specify a cost for the interface |
isis cost value [ level-1 | level-2 ] |
Optional No cost is specified for the interface by default. |
Configuring a global IS-IS cost
Follow these steps to configure a global IS-IS cost:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Specify an IS-IS cost style |
cost-style { narrow | wide | wide-compatible | { compatible | narrow-compatible } [ relax-spf-limit ] } |
Optional narrow by default |
|
Specify a global IS-IS cost |
circuit-cost value [ level-1 | level-2 ] |
Required No global cost is specified by default. |
Enable automatic IS-IS cost calculation
Follow these steps to enable automatic IS-IS cost calculation:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
— |
|
Specify an IS-IS cost style |
cost-style { wide | wide-compatible } |
Required narrow by default |
|
Enable automatic IS-IS cost calculation |
auto-cost enable |
Required Disabled by default |
|
Configure a bandwidth reference value for automatic IS-IS cost calculation |
bandwidth-reference value |
Optional 100 Mbps by default |
Specifying a Priority for IS-IS
A router may run multiple routing protocols. When routes to the same destination are found by multiple routing protocols, the route learned by the protocol with the highest priority wins. You can reference a routing policy to specify a priority for specific routes. For information about routing policy, refer to Routing Policy Configuration in the IP Routing Volume.
Follow these steps to configure the priority of IS-IS.
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Specify a priority for IS-IS |
preference { route-policy route-policy-name | preference } * |
Required 15 by default |
Configuring the Maximum Number of Equal Cost Routes
If there are multiple equal cost routes to the same destination, the traffic can be load balanced to enhance efficiency.
Follow these steps to configure the maximum number of equal cost routes:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Specify the maximum number of equal cost routes for load balancing |
maximum load-balancing number |
Required The default number is 4. |
Configuring IS-IS Route Summarization
This task is to configure a summary route, so routes falling into the network range of the summary route are summarized into one route for advertisement. Doing so can reduce the size of routing tables, as well as the scale of LSP and LSDB. Both IS-IS routes and redistributed routes can be summarized.
Follow these steps to configure route summarization:
|
To do… |
Use the command... |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Configure IS-IS route summarization |
summary ip-address { mask | mask-length } [ avoid-feedback | generate_null0_route | tag tag | [ level-1 | level-1-2 | level-2 ] ] * |
Required No route summarization is configured by default. |
![]()
l The cost of the summary route is the lowest one among the costs of summarized routes.
l The router summarizes only the routes in the locally generated LSPs.
Advertising a Default Route
A router running IS-IS cannot redistribute any default route and thus cannot advertise a default route to other neighbors. You can use the following commands to advertise a default route of 0.0.0.0/0 to the same level neighbors.
Follow these steps to advertise a default route:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
— |
|
Advertise a default route |
default-route-advertise [ route-policy route-policy-name | [ level-1 | level-2 | level-1-2 ] ] * |
Required The function is disabled by default. |
![]()
The default route is only advertised to routers at the same level. You can use a routing policy to generate the default route only when a local routing entry is matched by the policy.
Configuring IS-IS Route Redistribution
Redistribution of large numbers of routes on a device may affect the performance of other devices in the network. In that case, you can configure a limit on the number of redistributed routes to limit the number of routes to be advertised.
Follow these steps to configure IS-IS route redistribution from other routing protocols:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Redistribute routes from another routing protocol |
import-route protocol [ process-id | all-processes | allow-ibgp ] [ cost cost | cost-type { external | internal } | [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] * |
Required No route is redistributed by default. If no level is specified, routes are redistributed into the Level-2 routing table by default. |
|
Configure the maximum number of redistributed Level 1/Level 2 IPv4 routes |
import-route limit number |
Optional The default number is 128000. |
![]()
Only active routes can be redistributed. You can use the display ip routing-table protocol command to display route state information.
Configuring IS-IS Route Filtering
You can reference a configured ACL, IP prefix list or routing policy to filter routes calculated from the received LSPs and the routes redistributed from other routing protocols.
Filtering routes calculated from received LSPs
IS-IS saves the LSPs received from neighbors in the LSDB, uses the SPF algorithm to calculate the shortest path tree with itself as the root and installs the routes into the IS-IS routing table.
By reference a configured ACL, IP prefix list or routing policy, you can filter the calculated routes and only the routes matching the filter can be added into the IS-IS routing table.
Follow these steps to filter routes calculated from received LSPs:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Filter routes calculated from received LSPs |
filter-policy { acl-number | ip-prefix ip-prefix-name | route-policy route-policy-name } import |
Required No filtering is configured by default. |
Filtering redistributed routes
IS-IS can redistribute routes from other routing protocols or other IS-IS processes, add them into the IS-IS routing table and advertise them in LSPs.
By reference a configured ACL, IP prefix list or routing policy, you can filter redistributed routes and only the routes matching the filter can be added into the IS-IS routing table and advertised to neighbors.
Follow these steps to configure the filtering of redistributed routes:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Configure the filtering of routes redistributed from another routing protocol or IS-IS process |
filter-policy { acl-number | ip-prefix ip-prefix-name | route-policy route-policy-name } export [ protocol [ process-id ] ] |
Required Not configured by default |
Configuring IS-IS Route Leaking
With IS-IS route leaking enabled, the Level-1-2 router can advertise the routing information of other Level-1 areas and Level-2 area routing information to Level-1 routers.
Follow these steps to configure IS-IS route leaking:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Enable IS-IS route leaking |
import-route isis level-2 into level-1 [ filter-policy { acl-number | ip-prefix ip-prefix-name | route-policy route-policy-name } | tag tag ] * |
Required Disabled by default |
![]()
l If a filter policy is specified, only routes passing it can be advertised into Level-1 area.
l You can specify a routing policy in the import-route isis level-2 into level-1 command to filter routes from Level-2 to Level-1. Other routing policies specified for route reception and redistribution does not affect the route leaking.
Tuning and Optimizing IS-IS Networks
Configuration Prerequisites
Before the configuration, accomplish the following tasks:
l Configure IP addresses for interfaces, and make adjacent nodes reachable to each other at the network layer.
l Enable IS-IS.
Specifying Intervals for Sending IS-IS Hello and CSNP Packets
Follow these steps to configure intervals for sending IS-IS hello and CSNP packets:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter interface view |
interface interface-type interface-number |
–– |
|
Specify the interval for sending hello packets |
isis timer hello seconds [ level-1 | level-2 ] |
Optional 10 seconds by default |
|
Specify the interval for sending CSNP packets on the DIS of a broadcast network |
isis timer csnp seconds [ level-1 | level-2 ] |
Optional 10 seconds by default |
![]()
The interval between hello packets sent by the DIS is 1/3 the hello interval set with the isis timer hello command.
Specifying the IS-IS Hello Multiplier
If a neighbor receives no hello packets from the router within the advertised hold time, it considers the router down and recalculates the routes. The hold time is the hello multiplier times the hello interval.
Follow these steps to specify the IS-IS hello multiplier:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter interface view |
interface interface-type interface-number |
–– |
|
Specify the number of hello packets a neighbor must miss before declaring the router is down |
isis timer holding-multiplier value [ level-1 | level-2 ] |
Optional 3 by default |
![]()
On a broadcast link, Level-1 and Level-2 hello packets are advertised separately and therefore you need to set a hello multiplier for each level. On a P2P link, Level-1 and Level-2 hello packets are advertised in P2P hello packets, and you need not specify Level-1 or Level-2.
Configuring a DIS Priority for an Interface
On an IS-IS broadcast network, a router should be elected as the DIS at a routing level. You can specify a DIS priority at a level for an interface. The greater the interface’s priority is, the more likely it becomes the DIS. If multiple routers in the broadcast network have the same highest DIS priority, the router with the highest MAC address becomes the DIS.
Follow these steps to specify a DIS priority for an interface:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter interface view |
interface interface-type interface-number |
–– |
|
Specify a DIS priority for the interface |
isis dis-priority value [ level-1 | level-2 ] |
Optional 64 by default |
Disabling an Interface from Sending/Receiving IS-IS Packets
After disabled from sending and receiving hello packets, an interface cannot form any neighbor relationship, but can advertise directly connected networks in LSPs through other interfaces. By doing so, you can save bandwidth and CPU resources while ensuring other routers know networks directly connected to the interface.
Follow these steps to disable an interface from sending and receiving IS-IS packets:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter interface view |
interface interface-type interface-number |
–– |
|
Disable the interface from sending and receiving IS-IS packets |
isis silent |
Required Not disabled by default |
Enabling an Interface to Send Small Hello Packets
IS-IS messages cannot be fragmented at the IP layer because they are directly encapsulated into frames. Therefore, any two IS-IS neighboring routers need to negotiate a common MTU. To avoid sending big hellos for saving bandwidth, you can enable the interface to send small hello packets without CLVs.
Follow these steps to enable an interface to send small hello packets:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter interface view |
interface interface-type interface-number |
–– |
|
Enable the interface to send small hello packets without CLVs |
isis small-hello |
Required Standard hello packets are sent by default. |
Configuring LSP Parameters
Configuring LSP timers
1) Specify the maximum age of LSPs
Each LSP has an age that decreases in the LSDB. Any LSP with an age of 0 is deleted from the LSDB. You can adjust the age value based on the scale of a network.
Follow these steps to specify the maximum age of LSPs:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Specify the maximum LSP age |
timer lsp-max-age seconds |
Optional 1200 seconds by default |
2) Specify the LSP refresh interval and generation interval
Each router needs to refresh LSPs generated by itself at a configurable interval and send them to other routers to prevent valid routes from being aged out. A smaller refresh interval speeds up network convergence but consumes more bandwidth.
When the network topology changes, for example, a neighbor is down/up, or the interface metric, system ID or area ID is changed, the router generates an LSP after a configurable interval. If such changes occur frequently, excessive LSPs are generated, consuming a large amount of router resources and bandwidth; in this case, you can adjust the LSP generation interval.
Follow these steps to specify the LSP refresh interval and generation interval:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Specify the LSP refresh interval |
timer lsp-refresh seconds |
Optional 900 seconds by default |
|
Specify the LSP generation interval |
timer lsp-generation maximum-interval [ initial-interval [ second-wait-interval ] ] [ level-1 | level-2 ] |
Optional 2 seconds by default |
3) Specify LSP sending intervals
If a change occurs in the LSDB, IS-IS advertises the changed LSP to neighbors. You can specify the minimum interval for sending such LSPs.
On a P2P link, IS-IS requires an advertised LSP be acknowledged. If no acknowledgement is received within a configurable interval, IS-IS will retransmit the LSP.
Follow these steps to configure LSP sending intervals:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter interface view |
interface interface-type interface-number |
–– |
|
Specify the minimum interval for sending LSPs and the maximum LSP number that can be sent at a time |
isis timer lsp time [ count count ] |
Optional By default, the minimum interval is 33 milliseconds, and the maximum LSP number that can be sent at a time is 5. |
|
Specify the LSP retransmission interval on a P2P link |
isis timer retransmit seconds |
Optional 5 seconds by default |
![]()
Configure a proper LSP retransmission interval to avoid unnecessary retransmissions.
Specifying LSP lengths
IS-IS messages cannot be fragmented at the IP layer because they are directly encapsulated in frames. Therefore, IS-IS routers in an area need to send LSPs smaller than the smallest interface MTU in this area.
If the IS-IS routers have different interface MTUs, it is recommended to configure the maximum size of generated LSP packets to be smaller than the smallest interface MTU in this area. Otherwise, the routers have to dynamically adjust the LSP packet size to fit the smallest interface MTU, which takes time and affects other services.
Follow these steps to specify LSP lengths:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Specify the maximum length of generated Level-1 LSPs or Level-2 LSPs |
lsp-length originate size [ level-1 | level-2 ] |
1497 bytes by default |
|
Specify the maximum length of received LSPs |
lsp-length receive size |
1497 bytes by default |
Enabling LSP flash flooding
Since changed LSPs may trigger SPF recalculation, you can enable LSP flash flooding to advertise the changed LSPs before the router recalculates routes. Doing so can speed up network convergence.
Follow these steps to enable LSP flash flooding:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Enable LSP flash flooding |
flash-flood [ flood-count flooding-count | max-timer-interval flooding-interval | [ level-1 | level-2 ] ] * |
Required Not enabled by default |
Enabling LSP fragment extension
Follow these steps to enable LSP fragment extension:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Enable LSP fragment extension and specify the working mode |
lsp-fragments-extend [ [ level-1 | level-2 | level-1-2 ] | [ mode-1 | mode-2 ] ] * |
Required Not enabled by default |
|
Configure a virtual system ID |
virtual-system virtual-system-id |
Required Not configured by default |
![]()
l After LSP fragment extension is enabled for an IS-IS process, the MTUs of all the interfaces running the IS-IS process must not be less than 512; otherwise, LSP fragment extension will not take effect.
l At least one virtual system needs to be configured for the router to generate extended LSP fragments. An IS-IS process allows 50 virtual systems at most.
Limiting LSP flooding
In well connected NBMA networks, many P2P links exist. The following figure shows a fully meshed network, where Switchs A, B, C and D run IS-IS. When Switch A generates an LSP, it floods the LSP out VLAN-interface 100, VLAN-interface 200 and VLAN-interface 300. After receiving the LSP from VLAN-interface 100, Switch D floods it out VLAN-interface 200 and VLAN-interface 300 to Switch B and Switch C, which however has received the LSP from Router A. In this case, LSP flooding consumes extra bandwidth.
Figure 1-14 Network diagram of a fully meshed network
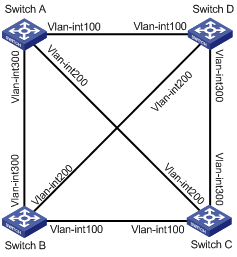
To avoid this, you can configure some interfaces as a mesh group or/and configure the blocked interfaces.
l After receiving an LSP, a member interface in a mesh group floods it out the interfaces that does not belong to the mesh group.
l If an interface is blocked, it does not send LSPs unless the neighbor sends LSP requests to it.
Before configuring this task, you need to consider redundancy for interfaces to avoid the fact that LSP packets cannot be flooded due to link failures.
Follow these steps to add an interface into a mesh group and block an interface:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter interface view |
interface interface-type interface-number |
–– |
|
Add the interface to a mesh group |
isis mesh-group mesh-group-number |
Required to choose either. By default, the interface neither belongs to any mesh group nor is blocked. |
|
Block the interface |
isis mesh-group mesh-blocked |
![]()
The mesh group feature takes effect only on P2P interfaces.
Configuring SPF Parameters
When the LSDB changes on a router, a route calculation starts. Frequent route calculations consume a lot of system resources, while route calculations at a proper interval improve efficiency. You can set an appropriate interval for SPF calculations as needed.
Follow these steps to configure the SPF parameters:
|
To do… |
Use the command... |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Configure the SPF calculation interval |
timer spf maximum-interval [ initial-interval [ second-wait-interval ] ] |
Optional The default SPF calculation interval is 10 seconds. |
Setting the LSDB Overload Bit
By setting the overload bit in sent LSPs, a router informs other routers of a failure that makes it incapable of routing and forwarding packets.
When an IS-IS router cannot record the complete LSDP due to running out of memory or some other reasons, it will calculate wrong routes. To make troubleshooting easier in this case, you can temporarily isolate the router from the IS-IS network by setting the overload bit.
Follow these steps to set the LSDB overload bit:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Set the overload bit |
set-overload [ on-startup [ [ start-from-nbr system-id [ timeout1 [ nbr-timeout ] ] ] | timeout2 ] [ allow { interlevel | external } * ] |
Required Not set by default |
Configuring IS-IS Authentication
Configuration Prerequisites
Complete the following tasks before this configuration:
l Configure network layer addresses for interfaces to make neighboring nodes accessible to each other at the network layer.
l Enable IS-IS.
Configuring Neighbor Relationship Authentication
With neighbor relationship authentication configured, an interface adds the password in the specified mode into hello packets to the peer and checks the password in the received hello packets. If the authentication succeeds, it forms the neighbor relationship with the peer.
The authentication mode and password at both ends must be identical.
Follow these steps to configure neighbor relationship authentication:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter interface view |
interface interface-type interface-number |
–– |
|
Specify the authentication mode and password |
isis authentication-mode { simple | md5 } password [ level-1 | level-2 ] [ ip | osi ] |
Required Not authentication is configured by default. |
![]()
The level-1 and level-2 keywords in the isis authentication-mode command are only supported on VLAN interfaces of switches, and the interfaces must be configured with the isis enable command first.
Configuring Area Authentication
Area authentication enables a router not to install routing information from untrusted routers into the Level-1 LSDB. The router encapsulates the authentication password in the specified mode into Level-1 packets (LSP, CSNP, PSNP) and check the password in received Level-1 packets.
Routers in a common area must have the same authentication mode and password.
Follow these steps to configure area authentication:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Specify the area authentication mode and password |
area-authentication-mode { simple | md5 } password [ ip | osi ] |
Required No area authentication is configured by default. |
Configuring Routing Domain Authentication
Routing domain authentication prevents untrusted routing information from entering into a routing domain. A router with the authentication configured encapsulates the password in the specified mode into Level-2 packets (LSP, CSNP, PSNP) and check the password in received Level-2 packets.
All the routers in the backbone must have the same authentication mode and password.
Follow these steps to configure routing domain authentication:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Specify the routing domain authentication mode and password |
domain-authentication-mode { simple | md5 } password [ ip | osi ] |
Required No routing domain authentication is configured by default. |
Configuring System ID to Host Name Mappings
In IS-IS, a system ID identifies a router or host uniquely. A system ID has a fixed length of 6 bytes. When an administrator needs to view IS-IS neighbor information, routing table or LSDB information, using the system IDs in dotted decimal notation is not convenient. To solve it, you can configure the mappings between system IDs and host names since host names are easier to remember and use.
Such mappings can be configured manually or dynamically. Note that:
l Using the display isis lsdb command on a router configured with dynamic system ID to host name mapping displays router names rather than system IDs.
l If you configure both dynamic and static system ID to host name mappings on a router, the host name for dynamic system ID to host name mapping applies.
Configuring a Static System ID to Host Name Mapping
Follow these steps to configure a static system ID to host name mapping:
|
To do… |
Use the command... |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Configure a system ID to host name mapping for a remote IS |
is-name map sys-id map-sys-name |
Required A system ID can only correspond to a host name. |
Configuring Dynamic System ID to Host Name Mapping
You need to configure a static system ID to host name mapping for any other router in a network. When a new router is added into the network or a mapping needs to be modified, you need to perform configuration on all routers.
In this case, you can configure dynamic system ID to host name mapping. To do so, you need to configure a host name for each router in the network. Each router advertises the host name in dynamic host name CLVs to other routers. At last, all routers in the network have all the mappings to generate a mapping table.
In addition, you can configure a name for the DIS in a broadcast network to help check the origin of LSPs in the LSDB.
Follow these steps to configure dynamic system ID to host name mapping:
|
To do… |
Use the command... |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Specify a host name for the router |
is-name sys-name |
Required No specified by default. |
|
Return to system view |
quit |
–– |
|
Enter interface view |
interface interface-type interface-number |
–– |
|
Configure a DIS name |
isis dis-name symbolic-name |
Optional Not configured by default. This command takes effect only on a router with dynamic system ID to host name mapping configured. This command is not supported on P2P interfaces. |
Configuring IS-IS GR
Restarting ISIS on a router causes transient network disconnection and route re-convergence.
With the Graceful Restart (GR) feature, the restarting router, known as the GR restarter, can notify the event to its GR capable neighbors, which, known as the GR helpers, will keep their adjacencies with the router within a configurable GR interval. After the restart, the router contacts its neighbors to retrieve its routing table.
During the whole process, the network keeps stable.
You can enable the GR Restarter to suppress the Suppress-Advertisement (SA) bit in the hello PDUs. In this way, its neighbors will still advertise the adjacencies within the specified period.
Follow these steps to configure GR on the GR Restarter and GR Helper respectively:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable IS-IS, and enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
Required Disabled by default |
|
Enable the GR capability for IS-IS |
graceful-restart |
Required Disabled by default |
|
Set the Graceful Restart interval |
graceful-restart interval timer |
Required 300 seconds by default |
|
Suppress the SA bit during restart |
graceful-restart suppress-sa |
Optional By default, the SA bit is not suppressed. |
Enabling the Logging of Neighbor State Changes
Follow these steps to enable the logging of neighbor state changes:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Enable the logging of neighbor state changes |
log-peer-change |
Required Enabled by default |
![]()
With this feature enabled, the router delivers information about neighbor state changes to the terminal for display.
Enabling IS-IS SNMP Trap
Follow these steps to enable IS-IS SNMP trap:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
–– |
|
Enter IS-IS view |
isis [ process-id ] [ vpn-instance vpn-instance-name ] |
–– |
|
Enable SNMP trap |
is-snmp-traps enable |
Required Enabled by default |
Displaying and Maintaining IS-IS
|
To do… |
Use the command… |
Remarks |
|
Display brief IS-IS configuration information |
display isis brief [ process-id | vpn-instance vpn-instance-name ] |
Available in any view |
|
Display the status of IS-IS debug switches |
display isis debug-switches { process-id | vpn-instance vpn-instance-name } |
Available in any view |
|
Display the IS-IS Graceful Restart state |
display isis graceful-restart status [ level-1 | level-2 ] [ process-id | vpn-instance vpn-instance-name ] |
Available in any view |
|
Display information about IS-IS enabled interfaces |
display isis interface [ statistics | [ interface-type interface-number ] [ verbose ] ] [ process-id | vpn-instance vpn-instance-name ] |
Available in any view |
|
Display IS-IS license information |
display isis license |
Available in any view |
|
Display IS-IS LSDB information |
display isis lsdb [ [ l1 | l2 | level-1 | level-2 ] | [ lsp-id LSPID | lsp-name lspname ] | local | verbose ] * [ process-id | vpn-instance vpn-instance-name ] |
Available in any view |
|
Display IS-IS mesh group information |
display isis mesh-group [ process-id | vpn-instance vpn-instance-name ] |
Available in any view |
|
Display the host-name-to-system-ID mapping table |
display isis name-table [ process-id | vpn-instance vpn-instance-name ] |
Available in any view |
|
Display IS-IS neighbor information |
display isis peer [ verbose | statistics ] [ process-id | vpn-instance vpn-instance-name ] |
Available in any view |
|
Display IS-IS IPv4 routing information |
display isis route [ ipv4 ] [ [ level-1 | level-2 ] | verbose ] * [ process-id | vpn-instance vpn-instance-name ] |
Available in any view |
|
Display IS-IS SPF calculation log information |
display isis spf-log [ process-id | vpn-instance vpn-instance-name ] |
Available in any view |
|
Display IS-IS statistics |
display isis statistics [ level-1 | level-2 | level-1-2 ] [ process-id | vpn-instance vpn-instance-name ] |
Available in any view |
|
Clear ISIS process data structure information |
reset isis all [ process-id | vpn-instance vpn-instance-name ] |
Available in user view |
|
Clear the data structure information of an IS-IS neighbor |
reset isis peer system-id [ process-id | vpn-instance vpn-instance-name ] |
Available in user view |
IS-IS Configuration Example
IS-IS Basic Configuration
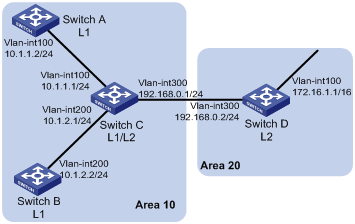
Network requirements
As shown in Figure 1-15, Switch A, B, C and Switch D reside in an IS-IS AS. Switch A and B are Level-1 switches, Switch D is a Level-2 switch and Switch C is a Level-1-2 switch. Switch A, B and C are in Area 10, while Switch D is in Area 20.
Network diagram
Figure 1-15 Network diagram for IS-IS basic configuration
Configuration procedure
1) Configure IP addresses for interfaces (omitted)
2) Configure IS-IS
# Configure Switch A.
<SwitchA> system-view
[SwitchA] isis 1
[SwitchA-isis-1] is-level level-1
[SwitchA-isis-1] network-entity 10.0000.0000.0001.00
[SwitchA-isis-1] quit
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] isis enable 1
[SwitchA-Vlan-interface100] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] isis 1
[SwitchB-isis-1] is-level level-1
[SwitchB-isis-1] network-entity 10.0000.0000.0002.00
[SwitchB-isis-1] quit
[SwitchB] interface vlan-interface 200
[SwitchB-Vlan-interface200] isis enable 1
[SwitchB-Vlan-interface200] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] isis 1
[SwitchC-isis-1] network-entity 10.0000.0000.0003.00
[SwitchC-isis-1] quit
[SwitchC] interface vlan-interface 100
[SwitchC-Vlan-interface100] isis enable 1
[SwitchC-Vlan-interface100] quit
[SwitchC] interface vlan-interface 200
[SwitchC-Vlan-interface200] isis enable 1
[SwitchC-Vlan-interface200] quit
[SwitchC] interface vlan-interface 300
[SwitchC-Vlan-interface300] isis enable 1
[SwitchC-Vlan-interface300] quit
# Configure Switch D.
<SwitchD> system-view
[SwitchD] isis 1
[SwitchD-isis-1] is-level level-2
[SwitchD-isis-1] network-entity 20.0000.0000.0004.00
[SwitchD-isis-1] quit
[SwitchD] interface vlan-interface 100
[SwitchD-Vlan-interface100] isis enable 1
[SwitchD-Vlan-interface100] quit
[SwitchD] interface vlan-interface 300
[SwitchD-Vlan-interface300] isis enable 1
[SwitchD-Vlan-interface300] quit
3) Verify the configuration
# Display the IS-IS LSDB of each switch to check the LSP integrity.
[SwitchA] display isis lsdb
Database information for ISIS(1)
--------------------------------
Level-1 Link State Database
LSPID Seq Num Checksum Holdtime Length ATT/P/OL
--------------------------------------------------------------------------
0000.0000.0001.00-00* 0x00000004 0xdf5e 1096 68 0/0/0
0000.0000.0002.00-00 0x00000004 0xee4d 1102 68 0/0/0
0000.0000.0002.01-00 0x00000001 0xdaaf 1102 55 0/0/0
0000.0000.0003.00-00 0x00000009 0xcaa3 1161 111 1/0/0
0000.0000.0003.01-00 0x00000001 0xadda 1112 55 0/0/0
*-Self LSP, +-Self LSP(Extended), ATT-Attached, P-Partition, OL-Overload
[SwitchB] display isis lsdb
Database information for ISIS(1)
--------------------------------
Level-1 Link State Database
LSPID Seq Num Checksum Holdtime Length ATT/P/OL
--------------------------------------------------------------------------
0000.0000.0001.00-00 0x00000006 0xdb60 988 68 0/0/0
0000.0000.0002.00-00* 0x00000008 0xe651 1189 68 0/0/0
0000.0000.0002.01-00* 0x00000005 0xd2b3 1188 55 0/0/0
0000.0000.0003.00-00 0x00000014 0x194a 1190 111 1/0/0
0000.0000.0003.01-00 0x00000002 0xabdb 995 55 0/0/0
*-Self LSP, +-Self LSP(Extended), ATT-Attached, P-Partition, OL-Overload
[SwitchC] display isis lsdb
Database information for ISIS(1)
--------------------------------
Level-1 Link State Database
LSPID Seq Num Checksum Holdtime Length ATT/P/OL
--------------------------------------------------------------------------
0000.0000.0001.00-00 0x00000006 0xdb60 847 68 0/0/0
0000.0000.0002.00-00 0x00000008 0xe651 1053 68 0/0/0
0000.0000.0002.01-00 0x00000005 0xd2b3 1052 55 0/0/0
0000.0000.0003.00-00* 0x00000014 0x194a 1051 111 1/0/0
0000.0000.0003.01-00* 0x00000002 0xabdb 854 55 0/0/0
*-Self LSP, +-Self LSP(Extended), ATT-Attached, P-Partition, OL-Overload
Level-2 Link State Database
LSPID Seq Num Checksum Holdtime Length ATT/P/OL
--------------------------------------------------------------------------
0000.0000.0003.00-00* 0x00000012 0xc93c 842 100 0/0/0
0000.0000.0004.00-00 0x00000026 0x331 1173 84 0/0/0
0000.0000.0004.01-00 0x00000001 0xee95 668 55 0/0/0
*-Self LSP, +-Self LSP(Extended), ATT-Attached, P-Partition, OL-Overload
[SwitchD] display isis lsdb
Database information for ISIS(1)
--------------------------------
Level-2 Link State Database
LSPID Seq Num Checksum Holdtime Length ATT/P/OL
-------------------------------------------------------------------------------
0000.0000.0003.00-00 0x00000013 0xc73d 1003 100 0/0/0
0000.0000.0004.00-00* 0x0000003c 0xd647 1194 84 0/0/0
0000.0000.0004.01-00* 0x00000002 0xec96 1007 55 0/0/0
*-Self LSP, +-Self LSP(Extended), ATT-Attached, P-Partition, OL-Overload
# Display the IS-IS routing information of each switch. Level-1 switches should have a default route with the next hop being the Level-1-2 switch. The Level-2 switch should have both routing information of Level-1 and Level-2.
[SwitchA] display isis route
Route information for ISIS(1)
-----------------------------
ISIS(1) IPv4 Level-1 Forwarding Table
-------------------------------------
IPV4 Destination IntCost ExtCost ExitInterface NextHop Flags
--------------------------------------------------------------------------
10.1.1.0/24 10 NULL Vlan100 Direct D/L/-
10.1.2.0/24 20 NULL Vlan100 10.1.1.1 R/-/-
192.168.0.0/24 20 NULL Vlan100 10.1.1.1 R/-/-
0.0.0.0/0 10 NULL Vlan100 10.1.1.1 R/-/-
Flags: D-Direct, R-Added to RM, L-Advertised in LSPs, U-Up/Down Bit Set
[SwitchC] display isis route
Route information for ISIS(1)
-----------------------------
ISIS(1) IPv4 Level-1 Forwarding Table
-------------------------------------
IPV4 Destination IntCost ExtCost ExitInterface NextHop Flags
--------------------------------------------------------------------------
192.168.0.0/24 10 NULL Vlan300 Direct D/L/-
10.1.1.0/24 10 NULL Vlan100 Direct D/L/-
10.1.2.0/24 10 NULL Vlan200 Direct D/L/-
Flags: D-Direct, R-Added to RM, L-Advertised in LSPs, U-Up/Down Bit Set
ISIS(1) IPv4 Level-2 Forwarding Table
-------------------------------------
IPV4 Destination IntCost ExtCost ExitInterface NextHop Flags
--------------------------------------------------------------------------
192.168.0.0/24 10 NULL Vlan300 Direct D/L/-
10.1.1.0/24 10 NULL Vlan100 Direct D/L/-
10.1.2.0/24 10 NULL Vlan200 Direct D/L/-
172.16.0.0/16 20 NULL Vlan300 192.168.0.2 R/-/-
Flags: D-Direct, R-Added to RM, L-Advertised in LSPs, U-Up/Down Bit Set
[SwitchD] display isis route
Route information for ISIS(1)
-----------------------------
ISIS(1) IPv4 Level-2 Forwarding Table
-------------------------------------
IPV4 Destination IntCost ExtCost ExitInterface NextHop Flags
--------------------------------------------------------------------------
192.168.0.0/24 10 NULL Vlan300 Direct D/L/-
10.1.1.0/24 20 NULL Vlan300 192.168.0.1 R/-/-
10.1.2.0/24 20 NULL Vlan300 192.168.0.1 R/-/-
172.16.0.0/16 10 NULL Vlan100 Direct D/L/-
Flags: D-Direct, R-Added to RM, L-Advertised in LSPs, U-Up/Down Bit Set
DIS Election Configuration
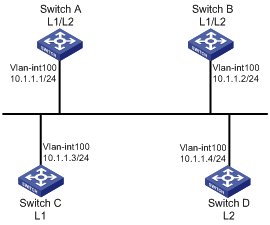
Network requirements
As shown in Figure 1-16, Switch A, B, C and Switch D reside in IS-IS area 10 on a broadcast network (Ethernet). Switch A and Switch B are Level-1-2 switches, Switch C is a Level-1 switch, and Switch D is a Level-2 switch.
Change the DIS priority of Switch A to make it elected as the Level-1-2 DIS router.
Network diagram
Figure 1-16 Network diagram for DIS selection
Configuration procedure
1) Configure an IP address for each interface (omitted)
2) Enable IS-IS
# Configure Switch A.
<SwitchA> system-view
[SwitchA] isis 1
[SwitchA-isis-1] network-entity 10.0000.0000.0001.00
[SwitchA-isis-1] quit
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] isis enable 1
[SwitchA-Vlan-interface100] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] isis 1
[SwitchB-isis-1] network-entity 10.0000.0000.0002.00
[SwitchB-isis-1] quit
[SwitchB] interface vlan-interface 100
[SwitchB-Vlan-interface100] isis enable 1
[SwitchB-Vlan-interface100] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] isis 1
[SwitchC-isis-1] network-entity 10.0000.0000.0003.00
[SwitchC-isis-1] is-level level-1
[SwitchC-isis-1] quit
[SwitchC] interface vlan-interface 100
[SwitchC-Vlan-interface100] isis enable 1
[SwitchC-Vlan-interface100] quit
# Configure Switch D.
<SwitchD> system-view
[SwitchD] isis 1
[SwitchD-isis-1] network-entity 10.0000.0000.0004.00
[SwitchD-isis-1] is-level level-2
[SwitchD-isis-1] quit
[SwitchD] interface vlan-interface 100
[SwitchD-Vlan-interface100] isis enable 1
[SwitchD-Vlan-interface100] quit
# Display information about IS-IS neighbors of Switch A.
[SwitchA] display isis peer
Peer information for ISIS(1)
----------------------------
System Id: 0000.0000.0002
Interface: Vlan-interface100 Circuit Id: 0000.0000.0003.01
State: Up HoldTime: 21s Type: L1(L1L2) PRI: 64
System Id: 0000.0000.0003
Interface: Vlan-interface100 Circuit Id: 0000.0000.0003.01
State: Up HoldTime: 27s Type: L1 PRI: 64
System Id: 0000.0000.0002
Interface: Vlan-interface100 Circuit Id: 0000.0000.0004.01
State: Up HoldTime: 28s Type: L2(L1L2) PRI: 64
System Id: 0000.0000.0004
Interface: Vlan-interface100 Circuit Id: 0000.0000.0004.01
State: Up HoldTime: 30s Type: L2 PRI: 64
# Display information about IS-IS interfaces of Switch A.
[SwitchA] display isis interface
Interface information for ISIS(1)
---------------------------------
Interface: Vlan-interface100
Id IPV4.State IPV6.State MTU Type DIS
001 Up Down 1497 L1/L2 No/No
# Display information about IS-IS interfaces of Switch C.
[SwitchC] display isis interface
Interface information for ISIS(1)
---------------------------------
Interface: Vlan-interface100
Id IPV4.State IPV6.State MTU Type DIS
001 Up Down 1497 L1/L2 Yes/No
# Display information about IS-IS interfaces of Switch D.
[SwitchD] display isis interface
Interface information for ISIS(1)
---------------------------------
Interface: Vlan-interface100
Id IPV4.State IPV6.State MTU Type DIS
001 Up Down 1497 L1/L2 No/Yes
![]()
By using the default DIS priority, Switch C is the Level-1 DIS, and Switch D is the Level-2 DIS. The pseudonodes of Level-1 and Level-2 are 0000.0000.0003.01 and 0000.0000.0004.01 respectively.
3) Configure the DIS priority of Switch A.
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] isis dis-priority 100
[SwitchA-Vlan-interface100] quit
# Display IS-IS neighbors of Switch A.
[SwitchA] display isis peer
Peer information for ISIS(1)
----------------------------
System Id: 0000.0000.0002
Interface: Vlan-interface100 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 21s Type: L1(L1L2) PRI: 64
System Id: 0000.0000.0003
Interface: Vlan-interface100 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 27s Type: L1 PRI: 64
System Id: 0000.0000.0002
Interface: Vlan-interface100 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 28s Type: L2(L1L2) PRI: 64
System Id: 0000.0000.0004
Interface: Vlan-interface100 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 30s Type: L2 PRI: 64
# Display information about IS-IS interfaces of Switch A.
[SwitchA] display isis interface
Interface information for ISIS(1)
---------------------------------
Interface: Vlan-interface100
Id IPV4.State IPV6.State MTU Type DIS
001 Up Down 1497 L1/L2 Yes/Yes
![]()
After the DIS priority configuration, Switch A becomes the Level-1-2 DIS, and the pseudonode is 0000.0000.0001.01.
# Display information about IS-IS neighbors and interfaces of Switch C.
[SwitchC] display isis peer
Peer information for ISIS(1)
----------------------------
System Id: 0000.0000.0002
Interface: Vlan-interface100 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 25s Type: L1 PRI: 64
System Id: 0000.0000.0001
Interface: Vlan-interface100 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 7s Type: L1 PRI: 100
[SwitchC] display isis interface
Interface information for ISIS(1)
---------------------------------
Interface: Vlan-interface100
Id IPV4.State IPV6.State MTU Type DIS
001 Up Down 1497 L1/L2 No/No
# Display information about IS-IS neighbors and interfaces of Switch D.
[SwitchD] display isis peer
Peer information for ISIS(1)
----------------------------
System Id: 0000.0000.0001
Interface: Vlan-interface100 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 9s Type: L2 PRI: 100
System Id: 0000.0000.0002
Interface: Vlan-interface100 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 28s Type: L2 PRI: 64
[SwitchD] display isis interface
Interface information for ISIS(1)
---------------------------------
Interface: Vlan-interface100
Id IPV4.State IPV6.State MTU Type DIS
001 Up Down 1497 L1/L2 No/No
Configuring IS-IS Route Redistribution
Network requirements
As shown in the following figure, Switch A, Switch B, Switch C and Switch D reside in the same AS. They use IS-IS to interconnect. Switch A and Switch B are Level-1 routers, Switch D is a Level-2 router, and Switch C is a Level-1-2 router.
It is required to redistribute RIP routes into IS-IS on Switch D.
Network diagram
Figure 1-17 IS-IS route redistribution
Configuration procedure
1) Configure IP addresses for interfaces (omitted)
2) Configure IS-IS basic functions
# Configure Switch A.
<SwitchA> system-view
[SwitchA] isis 1
[SwitchA-isis-1] is-level level-1
[SwitchA-isis-1] network-entity 10.0000.0000.0001.00
[SwitchA-isis-1] quit
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] isis enable 1
[SwitchA-Vlan-interface100] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] isis 1
[SwitchB-isis-1] is-level level-1
[SwitchB-isis-1] network-entity 10.0000.0000.0002.00
[SwitchB-isis-1] quit
[SwitchB] interface vlan-interface 200
[SwitchB-Vlan-interface200] isis enable 1
[SwitchB-Vlan-interface200] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] isis 1
[SwitchC-isis-1] network-entity 10.0000.0000.0003.00
[SwitchC-isis-1] quit
[SwitchC] interface vlan-interface 200
[SwitchC-Vlan-interface200] isis enable 1
[SwitchC-Vlan-interface200] quit
[SwitchC] interface vlan-interface 100
[SwitchC-Vlan-interface100] isis enable 1
[SwitchC-Vlan-interface100] quit
[SwitchC] interface vlan-interface 300
[SwitchC-Vlan-interface300] isis enable 1
[SwitchC-Vlan-interface300] quit
# Configure Switch D.
<SwitchD> system-view
[SwitchD] isis 1
[SwitchD-isis-1] is-level level-2
[SwitchD-isis-1] network-entity 20.0000.0000.0004.00
[SwitchD-isis-1] quit
[SwitchD] interface interface vlan-interface 300
[SwitchD-Vlan-interface300] isis enable 1
[SwitchD-Vlan-interface300] quit
# Display IS-IS routing information on each switch.
[SwitchA] display isis route
Route information for ISIS(1)
-----------------------------
ISIS(1) IPv4 Level-1 Forwarding Table
-------------------------------------
IPV4 Destination IntCost ExtCost ExitInterface NextHop Flags
--------------------------------------------------------------------------
10.1.1.0/24 10 NULL VLAN100 Direct D/L/-
10.1.2.0/24 20 NULL VLAN100 10.1.1.1 R/-/-
192.168.0.0/24 20 NULL VLAN100 10.1.1.1 R/-/-
0.0.0.0/0 10 NULL VLAN100 10.1.1.1 R/-/-
Flags: D-Direct, R-Added to RM, L-Advertised in LSPs, U-Up/Down Bit Set
[SwitchC] display isis route
Route information for ISIS(1)
-----------------------------
ISIS(1) IPv4 Level-1 Forwarding Table
-------------------------------------
IPV4 Destination IntCost ExtCost ExitInterface NextHop Flags
--------------------------------------------------------------------------
10.1.1.0/24 10 NULL VLAN100 Direct D/L/-
10.1.2.0/24 10 NULL VLAN200 Direct D/L/-
192.168.0.0/24 10 NULL VLAN300 Direct D/L/-
Flags: D-Direct, R-Added to RM, L-Advertised in LSPs, U-Up/Down Bit Set
ISIS(1) IPv4 Level-2 Forwarding Table
-------------------------------------
IPV4 Destination IntCost ExtCost ExitInterface NextHop Flags
--------------------------------------------------------------------------
10.1.1.0/24 10 NULL VLAN100 Direct D/L/-
10.1.2.0/24 10 NULL VLAN200 Direct D/L/-
192.168.0.0/24 10 NULL VLAN300 Direct D/L/-
Flags: D-Direct, R-Added to RM, L-Advertised in LSPs, U-Up/Down Bit Set
[SwitchD] display isis route
Route information for ISIS(1)
-----------------------------
ISIS(1) IPv4 Level-2 Forwarding Table
-------------------------------------
IPV4 Destination IntCost ExtCost ExitInterface NextHop Flags
--------------------------------------------------------------------------
192.168.0.0/24 10 NULL VLAN300 Direct D/L/-
10.1.1.0/24 20 NULL VLAN300 192.168.0.1 R/-/-
10.1.2.0/24 20 NULL VLAN300 192.168.0.1 R/-/-
Flags: D-Direct, R-Added to RM, L-Advertised in LSPs, U-Up/Down Bit Set
3) Configure RIPv2 on Switch D and Switch E, and configure route redistribution from RIP to IS-IS on Switch D.
# Configure RIPv2 on Switch D.
[SwitchD] rip 1
[SwitchD-rip-1] network 10.0.0.0
[SwitchD-rip-1] version 2
[SwitchD-rip-1] undo summary
# Configure RIPv2 on Switch E.
[SwitchE] rip 1
[SwitchE-rip-1] network 10.0.0.0
[SwitchE-rip-1] version 2
[SwitchE-rip-1] undo summary
# Configure route redistribution from RIP to IS-IS on Switch D.
[SwitchD-rip-1] quit
[SwitchD] isis 1
[SwitchD–isis] import-route rip level-2
# Display IS-IS routing information on Switch C.
[SwitchC] display isis route
Route information for ISIS(1)
-----------------------------
ISIS(1) IPv4 Level-1 Forwarding Table
-------------------------------------
IPV4 Destination IntCost ExtCost ExitInterface NextHop Flags
--------------------------------------------------------------------------
10.1.1.0/24 10 NULL VLAN100 Direct D/L/-
10.1.2.0/24 10 NULL VLAN200 Direct D/L/-
192.168.0.0/24 10 NULL VLAN300 Direct D/L/-
Flags: D-Direct, R-Added to RM, L-Advertised in LSPs, U-Up/Down Bit Set
ISIS(1) IPv4 Level-2 Forwarding Table
-------------------------------------
IPV4 Destination IntCost ExtCost ExitInterface NextHop Flags
--------------------------------------------------------------------------
10.1.1.0/24 10 NULL VLAN100 Direct D/L/-
10.1.2.0/24 10 NULL VLAN200 Direct D/L/-
192.168.0.0/24 10 NULL VLAN300 Direct D/L/-
10.1.4.0/24 10 NULL VLAN300 192.168.0.2 R/L/-
10.1.5.0/24 20 NULL VLAN300 192.168.0.2 R/L/-
10.1.6.0/24 20 NULL VLAN300 192.168.0.2 R/L/-
Flags: D-Direct, R-Added to RM, L-Advertised in LSPs, U-Up/Down Bit Set
IS-IS-based Graceful Restart Configuration Example
Network requirements
Switch A, Switch B, and Switch C belong to the same IS-IS routing domain, as illustrated in Figure 1-18.
Network diagram
Figure 1-18 Network diagram for IS-IS-based GR configuration
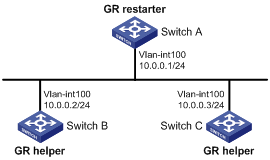
Configuration procedure
1) Configure IP addresses of the interfaces on each switch and configure IS-IS.
Follow Figure 1-18 to configure the IP address and subnet mask of each interface. The configuration procedure is omitted.
Configure IS-IS on the switches, ensuring that Switch A, Switch B and Switch C can communicate with each other at layer 3 and dynamic route update can be implemented among them with IS-IS. The configuration procedure is omitted here.
2) Configure IS-IS Graceful Restart.
# Enable IS-IS Graceful Restart on Switch A and configure the Graceful Restart Interval.
<SwitchA> system-view
[SwitchA] isis 1
[SwitchA-isis-1] graceful-restart
[SwitchA-isis-1] graceful-restart interval 150
[SwitchA-isis-1] return
Configurations for Switch B and Switch C are similar and therefore are omitted here.
3) Verify the configuration.
After Router A establishes adjacencies with Router B and Router C, they begin to exchange routing information. Restart IS-IS on Router A, which enters into the restart state and sends connection requests to its neighbors through the Graceful Restart mechanism to synchronize the LSDB. Using the display isis graceful-restart status command can display the IS-IS GR status on Router A.
# Restart the IS-IS process on Switch A.
<SwitchA> reset isis all 1
Warning : Reset ISIS process? [Y/N]:y
# Check the Graceful Restart status of IS-IS on Switch A.
<SwitchA> display isis graceful-restart status
Restart information for IS-IS(1)
--------------------------------------------------------------------
IS-IS(1) Level-1 Restart Status
Restart Interval: 150
SA Bit Supported
Total Number of Interfaces = 1
Restart Status: RESTARTING
Number of LSPs Awaited: 3
T3 Timer Status:
Remaining Time: 140
T2 Timer Status:
Remaining Time: 59
IS-IS(1) Level-2 Restart Status
Restart Interval: 150
SA Bit Supported
Total Number of Interfaces = 1
Restart Status: RESTARTING
Number of LSPs Awaited: 3
T3 Timer Status:
Remaining Time: 140
T2 Timer Status:
Remaining Time: 59
IS-IS Authentication Configuration Example
Network requirements
As shown in the following figure, Switch A, Switch B, Switch C and Switch D reside in the same IS-IS routing domain.
Switch A, Switch B, and Switch C belong to Area 10, and Switch D belongs to Area 20.
Configure neighbor relationship authentication between neighbors. Configure area authentication in Area 10 to prevent untrusted routes from entering into the area. Configure routing domain authentication on Switch C and Switch D to prevent untrusted routes from entering the routing domain.
Network diagram
Figure 1-19 IS-IS authentication configuration
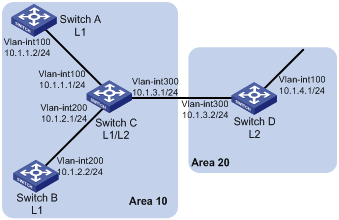
Configuration procedure
1) Configure IP addresses for interfaces (Omitted).
2) Configure IS-IS basic functions.
# Configure Switch A.
<SwitchA> system-view
[SwitchA] isis 1
[SwitchA-isis-1] network-entity 10.0000.0000.0001.00
[SwitchA-isis-1] quit
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] isis enable 1
[SwitchA-Vlan-interface100] quit
# Configure Switch B.
<SwitchB> system-view
[SwitchB] isis 1
[SwitchB-isis-1] network-entity 10.0000.0000.0002.00
[SwitchB-isis-1] quit
[SwitchB] interface vlan-interface 200
[SwitchB-Vlan-interface200] isis enable 1
[RouterB--Vlan-interface200] quit
# Configure Switch C.
<SwitchC> system-view
[SwitchC] isis 1
[SwitchC-isis-1] network-entity 10.0000.0000.0003.00
[SwitchC-isis-1] quit
[SwitchC] interface vlan-interface 200
[SwitchC-Vlan-interface200] isis enable 1
[SwitchC-Vlan-interface200] quit
[SwitchC] interface vlan-interface 300
[SwitchC-Vlan-interface300] isis enable 1
[SwitchC-Vlan-interface300] quit
[SwitchC] interface vlan-interface 300
[SwitchC-Vlan-interface300] isis enable 1
[SwitchC-Vlan-interface300] quit
# Configure Switch D.
<SwitchD> system-view
[SwitchD] isis 1
[SwitchD-isis-1] network-entity 20.0000.0000.0001.00
[SwitchD-isis-1] quit
[SwitchD] interface vlan-interface 300
[SwitchD-Vlan-interface300] isis enable 1
[SwitchD-Vlan-interface300] quit
3) Configure neighbor relationship authentication between neighbors.
# Specify the MD5 authentication mode and password eRq on VLAN-interface 100 of Switch A and on VLAN-interface 100 of Switch C.
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] isis authentication-mode md5 eRg
[SwitchA-Vlan-interface100] quit
[SwitchC] interface vlan-interface 100
[SwitchC-Vlan-interface100] isis authentication-mode md5 eRg
[SwitchC-Vlan-interface100] quit
# Specify the MD5 authentication mode and password t5Hr on VLAN-interface 200 of Switch B and on VLAN-interface 200 of Switch C.
[SwitchB] interface vlan-interface 200
[SwitchB-Vlan-interface200] isis authentication-mode md5 t5Hr
[SwitchB-Vlan-interface200] quit
[SwitchC] interface vlan-interface 200
[SwitchC-Vlan-interface200] isis authentication-mode md5 t5Hr
[SwitchC-Vlan-interface200] quit
# Specify the MD5 authentication mode and password hSec on VLAN-interface 300 of Switch D and on VLAN-interface 300 of Switch C.
[SwitchC] interface vlan-interface 300
[SwitchC-Vlan-interface300] isis authentication-mode md5 hSec
[SwitchC-Vlan-interface300] quit
[SwitchD] interface vlan-interface 300
[SwitchD-Vlan-interface300] isis authentication-mode md5 hSec
[SwitchD-Vlan-interface300] quit
4) Configure area authentication. Specify the MD5 authentication mode and password 10Sec on Switch A, Switch B and Switch C.
[SwitchA] isis 1
[SwitchA-isis-1] area-authentication-mode md5 10Sec
[SwitchA-isis-1] quit
[SwitchB] isis 1
[SwitchB-isis-1] area-authentication-mode md5 10Sec
[SwitchB-isis-1] quit
[SwitchC] isis 1
[SwitchC-isis-1] area-authentication-mode md5 10Sec
[SwitchC-isis-1] quit
5) Configure routing domain authentication. Specify the MD5 authentication mode and password 1020Sec on Switch C and Switch D.
[SwitchC] isis 1
[SwitchC-isis-1] domain-authentication-mode md5 1020Sec
[SwitchC-isis-1] quit
[SwitchD] isis 1
[SwitchD-isis-1] domain-authentication-mode md5 1020Sec

