- Table of Contents
-
- 03-Typical Configuration Example
- 01-H3C_AAA_Configuration_Examples
- 02-H3C_ACL_Configuration_Examples
- 03-H3C_ATM_Configuration_Examples
- 04-H3C_IGMP_Configuration_Examples
- 05-H3C_IP_Source_Guard_Configuration_Examples
- 06-H3C_Ethernet_OAM_Configuration_Examples
- 07-H3C_NQA_Configuration_Examples
- 08-H3C_QinQ_Configuration_Examples
- 09-H3C_OSPF_Configuration_Examples
- 10-H3C_MPLS_TE_Configuration_Examples
- 11-H3C_OpenFlow_Configuration_Examples
- 12-H3C_NAT_Configuration_Examples
- 13-H3C_RBAC_Configuration_Examples
- 14-H3C_IRF_Configuration_Examples
- 15-H3C_POS_Interface_Configuration_Examples
- 16-H3C_CPOS_Interface_Configuration_Examples
- 17-H3C_DHCP_Relay_Redundancy_Configuration_Examples
- 18-H3C_DLDP_Configuration_Examples
- 19-H3C_IS-IS_Configuration_Examples
- 20-H3C_MPLS_L3VPN_Configuration_Examples
- 21-H3C_SSH_Configuration_Examples
- 22-H3C_Login_Management_Configuration_Examples
- 23-H3C_SNMP_Configuration_Examples
- 24-H3C_Priority_Marking_and_Queue_Scheduling_Configuration_Examples
- 25-H3C_Multicast_VPN_Configuration_Examples
- 26-H3C_BGP_Configuration_Examples
- 27-H3C_HoVPN_Configuration_Examples
- 28-H3C_L2TP_Configuration_Examples
- 29-H3C_VRRP_Configuration_Examples
- 30-H3C_Traffic_Filtering_Configuration_Examples
- 31-H3C_Samplers_and_IPv4_NetStream_Configuration_Examples
- 32-H3C_Software_Upgrade_Examples
- 33-H3C_MPLS_L2VPN_Configuration_Examples
- 34-H3C_NetStream_Configuration_Examples
- 35-H3C_Policy-Based_Routing_Configuration_Examples
- 36-H3C_Traffic_Policing_Configuration_Examples
- 37-H3C_BFD_Configuration_Examples
- 38-H3C_OSPFv3_Configuration_Examples
- 39-H3C_VPLS_Configuration_Examples
- 40-H3C_GTS_and_Rate_Limiting_Configuration_Examples
- 41-H3C_IPv6_IS-IS_Configuration_Examples
- 42-H3C_MPLS OAM_Configuration_Examples
- 43-H3C_BGP_Route_Selection_Configuration_Examples
- 44-H3C_IS-IS_Route_Summarization_Configuration_Examples
- 45-H3C_SRv6 Configuration Examples
- 46-H3C_Attack_Protection_Configuration_Examples
- 47-H3C_OSPF_Multi-Process_Configuration_Examples
- 48-H3C_OSPF_with_Multi-Instance_Configuration_Examples
- 49-H3C_ARP_Attack_Protection_Configuration_Examples
- 50-H3C_DHCPv6_Server_and_DHCPv6_Prefix_Client_Configuration_Examples
- 51-Bidirectional NAT and NAT Server Configuration Examples
- 52-Bidirectional NAT and NAT Server With Easy IP Configuration Examples (Global NAT)
- 53-CE1 Interface Connection Configuration Examples
- 54-General QoS Configuration Examples
- 55-GRE Tunnel Establishment Using OSPF Configuration Examples
- 56-GRE Tunnel Establishment Using Static Routes Configuration Examples
- 57-Internal Users Accessing the External Network Configuration Examples
- 58-OSPF over IPsec for Overseas Branch Access Configuration Examples
- 59-QoS Configuration Examples for the Financial Industry
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 12-H3C_NAT_Configuration_Examples | 113.47 KB |
Contents
Example: Configuring basic NAT
Example: Configuring NAT Server for external-to-internal access
Introduction
This document provides NAT configuration examples.
Prerequisites
This document is not restricted to specific software or hardware versions.
The configuration examples in this document were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
The following information is provided based on the assumption that you have basic knowledge of NAT.
Restrictions and guidelines
NAT is available on service modules except CSPC-CP2LB.
A QoS policy is required on an interface to redirect the incoming traffic to the NAT-capable service module specified for the traffic outbound interface. For more information about QoS policies, see ACL and QoS Configuration Guide.
Example: Configuring basic NAT
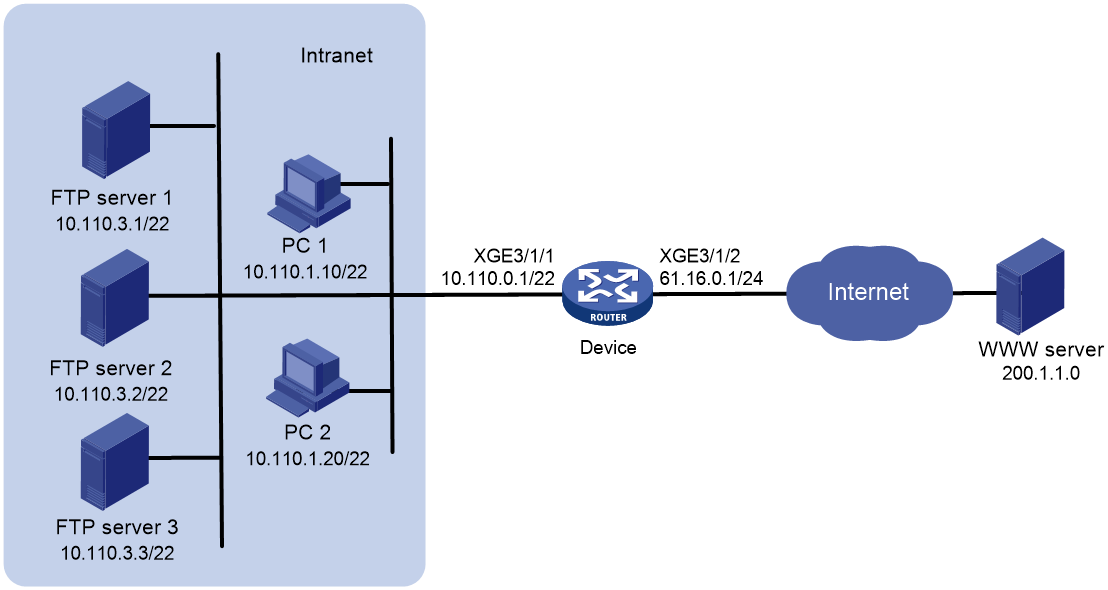
Network configuration
As shown in Figure 1, the internal users use the IP addresses in the range of 10.110.0.0 to 10.110.2.255. The private IP addresses of the FTP servers are from 10.110.3.1 to 10.110.3.3. These servers provide FTP services to external users. The company has three public IP addresses from 61.16.0.1 to 61.16.0.3.
Configure NAT on the device to implement the following:
· Allow the internal and external users to use the IP address 61.16.0.1 to access the FTP servers.
· Implement load sharing among the FTP servers and do not allow connections that are initiated by the FTP servers to the external network.
Analysis
· To translate IP addresses in the range of 10.110.0.0 to 10.110.2.255 into IP addresses in the range of 61.16.0.2 to 61.16.0.3, configure an ACL to identify these packets. Then configure outbound address translation on packets identified by the ACL on Ten-GigabitEthernet 3/1/2.
· To allow three FTP servers to load share services, configure NAT server group to implement load sharing.
· To allow internal hosts to access the internal FTP server by using a public IP address, enable AT hairpin on Ten-GigabitEthernet 3/1/1 of the device.
Procedures
Specifying IP addresses for the interfaces
# Specify IP addresses for Ten-GigabitEthernet 3/1/1 and Ten-GigabitEthernet 3/1/2.
<Device> system-view
[Device] interface Ten-GigabitEthernet 3/1/1
[Device-Ten-GigabitEthernet3/1/1] ip address 10.110.0.1 255.255.252.0
[Device-Ten-GigabitEthernet3/1/1] quit
[Device] interface Ten-GigabitEthernet 3/1/2
[Device-Ten-GigabitEthernet3/1/2] ip address 61.16.0.1 255.255.255.0
[Device-Ten-GigabitEthernet3/1/2] quit
Configuring outbound NAT for internal users
# Configure NAT address group 0, and add public IP address 61.16.0.2 and 61.16.0.3 to the group.
[Device-nat-address-group-0] address 61.16.0.2 61.16.0.3
[Device-nat-address-group-0] quit
# Configure ACL 2000 to identify packets only from subnet 10.110.0.0 to 10.110.2.255.
[Device-acl-ipv4-basic-2000] rule permit source 10.110.0.0 0.0.1.255
[Device-acl-ipv4-basic-2000] rule permit source 10.110.2.0 0.0.0.255
[Device-acl-ipv4-basic-2000] quit
[Device] interface Ten-GigabitEthernet 3/1/2
[Device-Ten-GigabitEthernet3/1/2] nat outbound 2000 address-group 0
[Device-Ten-GigabitEthernet3/1/2] quit
Implementing load sharing among FTP servers
# Create NAT server group 0, and add servers at 10.110.3.1, 10.110.3.2, 10.110.3.3 to the group.
[Device-nat-server-group-0] inside ip 10.110.3.1 port 21
[Device-nat-server-group-0] inside ip 10.110.3.2 port 21
[Device-nat-server-group-0] inside ip 10.110.3.3 port 21
[Device-nat-server-group-0] quit
[Device] interface Ten-GigabitEthernet 3/1/2
[Device-Ten-GigabitEthernet3/1/2] nat server protocol tcp global 61.16.0.1 ftp inside server-group 0
# Enable NAT hairpin on Ten-GigabitEthernet 3/1/1.
[Device] interface Ten-GigabitEthernet 3/1/1
[Device-Ten-GigabitEthernet3/1/1] nat hairpin enable
Specifying a NAT-capable service module to provide NAT service
# Specify the service module in slot 3 to provide the NAT service for Ten-GigabitEthernet 3/1/1.
[Device-Ten-GigabitEthernet3/1/1] nat service slot 3
[Device-Ten-GigabitEthernet3/1/1] quit
# Specify the service module in slot 3 to provide the NAT service for Ten-GigabitEthernet 3/1/2.
[Device] interface Ten-GigabitEthernet 3/1/2
[Device-Ten-GigabitEthernet3/1/2] nat service slot 3
[Device-Ten-GigabitEthernet3/1/2] quit
Configuring a QoS policy to redirect traffic to the NAT-capable service module
# Configure ACL 2001 to identify packets to be redirected to the NAT-capable service module. In this example, the packets are those to be translated, therefore, define the same ACL rules as those in ACL 2000.
[Device] acl basic 2001
[Device-acl-ipv4-basic-2001] rule permit source 10.110.0.0 0.0.1.255
[Device-acl-ipv4-basic-2001] rule permit source 10.110.2.0 0.0.0.255
[Device-acl-ipv4-basic-2001] quit
# Create traffic class 1 and define a match criterion for the traffic class to match ACL 2001.
[Device] traffic classifier 1
[Device-classifier-1] if-match acl 2001
[Device-classifier-1] quit
# Create traffic behavior 1 and configure redirecting traffic to the service module in slot 3 in the traffic behavior 1.
[Device] traffic behavior 1
[Device-behavior-1] redirect slot 3
[Device-behavior-1] quit
# Create QoS policy 1 and associate traffic class 1 with traffic behavior 1 in the QoS policy.
[Device] qos policy 1
[Device-qospolicy-1] classifier 1 behavior 1
[Device-qospolicy-1] quit
# Apply the QoS policy to the inbound direction of Ten-GigabitEthernet 3/1/1.
[Device] interface Ten-GigabitEthernet 3/1/1
[Device-Ten-GigabitEthernet3/1/1] qos apply policy 1 inbound
[Device-Ten-GigabitEthernet3/1/1] quit
Verifying the configuration
# Access the WWW server from PC 1. Verify that a NAT session is created on the device.
[Device] display nat session verbose
Initiator:
Source IP/port: 10.110.1.10/1024
Destination IP/port: 200.1.1.10/80
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Ten-GigabitEthernet3/1/1
Responder:
Source IP/port: 200.1.1.10/80
Destination IP/port: 61.16.0.2/1025
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Ten-GigabitEthernet3/1/2
State: TCP_CLOSE
Application: HTTP
Role: -
Failover group ID: -
Start time: 2014-07-08 13:30:47
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Total sessions found: 1
# Use two external hosts at the IP address of 61.16.0.10 and 61.16.0.11 to request FTP services at the same time. On the device, verify that two NAT sessions are created, and FTP server 1 and FTP server 2 provide FTP services for the two hosts, respectively.
[Device] display nat session verbose
Initiator:
Source IP/port: 61.16.0.11/1024
Destination IP/port: 61.16.0.1/21
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Ten-GigabitEthernet3/1/2
Responder:
Source IP/port: 10.110.3.1/21
Destination IP/port: 61.16.0.11/1024
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Ten-GigabitEthernet3/1/1
State: TCP_ESTABLISHED
Application: FTP
Role: -
Failover group ID: -
Start time: 2014-07-08 14:11:41
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Initiator:
Source IP/port: 61.16.0.10/1024
Destination IP/port: 61.16.0.1/21
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Ten-GigabitEthernet3/1/2
Responder:
Source IP/port: 10.110.3.2/21
Destination IP/port: 61.16.0.10/1024
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Ten-GigabitEthernet3/1/1
State: TCP_ESTABLISHED
Application: FTP
Role: -
Failover group ID: -
Start time: 2014-07-08 14:12:00
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Total sessions found: 2
# Access an FTP server through 61.16.0.1 from PC 1. Verify that a NAT session is created.
[Device] display nat session verbose
Initiator:
Source IP/port: 10.110.1.10/1024
Destination IP/port: 61.16.0.1/21
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Ten-GigabitEthernet3/1/1
Responder:
Source IP/port: 10.110.3.1/21
Destination IP/port: 61.16.0.2/1025
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Ten-GigabitEthernet3/1/1
State: TCP_ESTABLISHED
Application: FTP
Role: -
Failover group ID: -
Start time: 2014-07-08 14:24:15
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Total sessions found: 1
Configuration files
#
traffic classifier 1 operator and
if-match acl 2001
#
traffic behavior 1
redirect slot 3
#
qos policy 1
classifier 1 behavior 1
#
interface Ten-GigabitEthernet3/1/1
ip address 10.110.0.1 255.255.252.0
qos apply policy 1 inbound
nat hairpin enable
nat service slot 3
#
interface Ten-GigabitEthernet3/1/2
ip address 61.16.0.1 255.255.255.0
nat outbound 2000 address-group 0
nat server protocol tcp global 61.16.0.1 21 inside server-group 0
nat service slot 3
#
acl basic 2000
rule 0 permit source 10.110.0.0 0.0.1.255
rule 5 permit source 10.110.2.0 0.0.0.255
#
acl basic 2001
rule 0 permit source 10.110.0.0 0.0.1.255
rule 5 permit source 10.110.2.0 0.0.0.255
#
address 61.16.0.2 61.16.0.3
#
nat server-group 0
inside ip 10.110.3.1 port 21
inside ip 10.110.3.2 port 21
inside ip 10.110.3.3 port 21
#
Example: Configuring NAT Server for external-to-internal access
Network configuration
As shown in Figure 2, a company uses private IP addresses on network 10.110.10.1/16 and public IP address 202.38.1.1. Configure NAT dynamic port block mapping to allow external hosts to access the internal FTP server by IP address 202.38.1.1 and port number 21.
Procedures
Configuring the router
1. Specify IP addresses for the interfaces on the router.
<Router> system-view
[Router] interface Ten-GigabitEthernet 3/1/1
[Router-Ten-GigabitEthernet3/1/1] ip address 10.110.10.10 255.255.0.0
[Router-Ten-GigabitEthernet3/1/1] quit
[Router] interface Ten-GigabitEthernet 3/1/2
[Router-Ten-GigabitEthernet3/1/2] ip address 202.38.1.10 255.255.255.0
[Router-Ten-GigabitEthernet3/1/2] quit
2. Configure failover group cgn1.
# Specify the CGN card in slot 2 as the primary node in failover group cgn1.
[Router] failover group cgn1 id 1
[Router-failover-group-cgn] bind slot 2 primary
[Router-failover-group-cgn] quit
3. Configure ACL 3000.
# Configure ACL 3000 to identify packets from IP address 10.110.10.1.
[Router] acl advanced 3000
[Router-acl-ipv4-adv-3000] rule 5 permit ip source 10.110.10.1 0
[Router-acl-ipv4-adv-3000] quit
4. Configure a QoS policy to redirect IP packets to the NAT instance.
# Configure traffic class cgn to identify IP packets.
[Router] traffic classifier cgn
[Router-classifier-cgn] if-match acl 3000
[Router-classifier-cgn] quit
# Configure traffic behavior cgn to bind the matching traffic to NAT instance a.
[Router] traffic behavior cgn
[Router-behavior-cgn] bind nat-instance a
[Router-behavior-cgn] quit
# Create QoS policy cgn and associate the traffic class with the traffic behavior.
[Router] qos policy cgn
[Router-qospolicy-cgn] classifier cgn behavior cgn
[Router-qospolicy-cgn] quit
# Apply QoS policy to the inbound traffic on Ten-GigabitEthernet 3/1/1.
[Router] interface Ten-GigabitEthernet 3/1/1
[Router-Ten-GigabitEthernet3/1/1] qos apply policy cgn inbound
[Router-Ten-GigabitEthernet3/1/1] quit
5. Configure service instance group 1.
# Create service instance group 1 and associate it with failover group cgn1.
[Router] service-instance-group 1
[Router-service-instance-group-1] failover-group cgn1
[Router-service-instance-group-1] quit
6. Configure global NAT:
# Create a NAT instance named a with ID 1.
[Router] nat instance a id 1
# Associate NAT instance a with service instance group 1.
[Router-nat-instance-a] service-instance-group 1
# Configure NAT server to allow external hosts to access the internal FTP server by using address 202.38.1.1 and port number 21.
[Router-nat-instance-a] nat server protocol tcp global 202.38.1.1 21 inside 10.110.10.1 ftp
[Router-nat-instance-a] quit
Configuring the host
Configure 202.38.1.10 as the default gateway address for the host.
Verifying the configuration
# Verify that the host on the external network can access the internal server by using the public address. (Details not shown.)
# Display detailed information about NAT sessions.
<Router> display nat session verbose
Initiator:
Source IP/port: 202.38.1.20/53323
Destination IP/port: 202.38.1.1/21
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Ten-GigabitEthernet3/1/2
Responder:
Source IP/port: 10.110.10.1/21
Destination IP/port: 202.38.1.20/53323
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Ten-GigabitEthernet3/1/1
State: TCP_ESTABLISHED
Application: FTP
Role: Master
Failover group ID: 1
Start time: 2022-05-19 14:02:28
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Total sessions found: 1
Configuration files
#
failover group cgn1 id 1
bind slot 2 primary
#
traffic classifier cgn operator and
if-match acl 3000
#
traffic behavior cgn
bind nat-instance a
#
qos policy cgn
classifier cgn behavior cgn
#
interface Ten-GigabitEthernet3/1/1
ip address 10.110.10.10 255.255.0.0
qos apply policy cgn inbound
#
interface Ten-GigabitEthernet3/1/2
ip address 202.38.1.10 255.255.255.0
#
acl advanced 3000
rule 5 permit ip source 10.110.10.1 0
#
service-instance-group 1
failover-group cgn1
#
nat instance a id 1
service-instance-group 1
nat server protocol tcp global 202.38.1.1 21 inside 10.110.10.1 21
#
Related documentation
· H3C CR16000-F Routers NAT Configuration Guide-R8385P09
· H3C CR16000-F Routers NAT Command Reference-R8385P09
·