- Table of Contents
-
- 07-Security Configuration Guide
- 00-Preface
- 01-Security Overview
- 02-AAA Configuration
- 03-802.1X Configuration
- 04-MAC Authentication Configuration
- 05-Portal Configuration
- 06-Port Security Configuration
- 07-User Profile Configuration
- 08-Password Control Configuration
- 09-Public Key Configuration
- 10-PKI Configuration
- 11-SSH Configuration
- 12-SSL Configuration
- 13-SSL VPN Configuration
- 14-TCP Attack Protection Configuration
- 15-ARP Attack Protection Configuration
- 16-IPsec Configuration
- 17-ALG Configuration
- 18-Firewall Configuration
- 19-Session Management Configuration
- 20-Web Filtering Configuration
- 21-User Isolation Configuration
- 22-Source IP Address Verification Configuration
- 23-FIPS Configuration
- 24-Protocol Packet Rate Limit Configuration
- 25-Attack detection and protection configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 20-Web Filtering Configuration | 195.57 KB |
IP address-supported URL address filtering
Configuring URL address filtering
Configuring IP address-supported URL address filtering
Configuring URL parameter filtering
Displaying and maintaining Web filtering
URL address filtering configuration example
URL parameter filtering configuration example
Java blocking configuration example
Failed to add filtering entry or suffix keyword due to upper limit
Invalid characters are present in the configured parameter
Unable to access the HTTP server by IP address
Configuring Web filtering
Support for this feature depends on the device model. For more information, see About the H3C Access Controllers Configuration Guides.
Overview
In legacy network security solutions, network protection mainly targets external attacks. With the popularity of network applications in every walk of life, however, the internal network also faces security threats caused by internal user access to illegal networks. To protect the internal network against such threats, the network devices must be able to filter illegal access requests from internal users.
Web filtering can help devices prevent internal users from accessing unauthorized websites and block Java applets and ActiveX objects from Web pages. Web filtering provides the following functions:
· IP address-supported URL address filtering
URL address filtering
URL address filtering helps prevent internal users from accessing prohibited websites or restrict them to specific websites by checking URL addresses contained in Web requests.
Processing procedure
1. After receiving a Web request, the device resolves the URL address in the request.
2. The device matches the URL address against the configured filtering entries.
3. If a match is found and the filtering action of the matched entry is permit, the device forwards the request.
4. If a match is found and the filtering action of the matched entry is deny, the device drops the Web request and sends a TCP reset packet to both the client that sent the request and the server.
5. If no match is found, the device forwards or drops the request, depending on the default filtering action configured for URL address filtering.
IP address-supported URL address filtering
Once the URL address filtering function is enabled, the system denies all Web requests that use IP addresses by default. By enabling support for IP address in URL address filtering, you can configure the device to allow internal users to access specified or all websites based on the website IP addresses.
Processing procedure
After the device receives a Web request that uses an IP address, it processes the request as follows:
· If URL address filtering supports IP addresses, the device forwards the request. The device permits all Web requests that use the websites' IP addresses to pass.
· If URL address filtering does not support IP addresses, the device checks the ACL rules for URL address filtering. If the ACL permits the IP address, the device forwards the request. Otherwise, the device drops the request.
URL parameter filtering
Many Web pages are dynamic, connected with databases, and support data query and modification through Web requests. This makes it possible to fabricate special SQL statements in Web requests to obtain confidential data from databases or break down databases by repeatedly modifying database information. This kind of attack is called SQL injection attack.
To address this problem, the device compares the URL parameters in a Web request against SQL statement keywords and some other characters that may constitute SQL statements. If a match is found, the device regards the request as an SQL injection attack and denies it. This protection mechanism is called URL parameter filtering.
Web requests transmit parameters mainly by using GET and POST methods. The method used for transmitting parameters determines the positions of the URL parameters. The device obtains parameters based on the parameter transmission method and performs filtering. The device supports URL parameter filtering of Web requests with the GET, POST or PUT method.
Processing procedure
After receiving a Web request containing URL parameters, the device obtains the parameters according to the parameter transmission method and processes the request accordingly:
· If the parameters are transmitted by the method of GET, POST or PUT, the device obtains the URL parameters from the Web request and compares the URL parameters against the configured filtering entries. If a match is found, the device denies the request. Otherwise, the device forwards the request.
Java blocking
Java blocking protects networks from Java applets attacks.
After the Java blocking function is enabled, all requests for Java applets of Web pages are filtered. If Java applets in some Web pages are expected, configure ACL rules to permit requests to Java applets of these Web pages.
Processing procedure
· If the Java blocking function is enabled but no ACL is configured for it, the device replaces suffixes .class and .jar with .block in all Web requests and then forwards the requests.
· If the Java blocking function is enabled and an ACL is configured for it, the device uses ACL rules to determine whether to replaces suffixes .class and .jar with .block in Web requests. If the destination server in a Web request is a server permitted by the ACL, no replacement occurs and the request is forwarded; otherwise, the suffix in the request is replaced with .block before the request is forwarded.
ActiveX blocking
ActiveX blocking protects networks from being attacked by malicious ActiveX plugins.
After the ActiveX blocking function is enabled, requests for ActiveX plugins to all Web pages will be filtered. If the ActiveX plugins in some Web pages are expected, you can configure ACL rules to permit requests to the ActiveX plugins of these Web pages.
Processing procedure
· If the ActiveX blocking function is enabled but no ACL is configured for it, the device replaces the suffix .ocx with .block in all Web requests before forwarding the requests.
· If the ActiveX blocking function is enabled and an ACL is configured for it, the device determines whether to replaces suffix .ocx with .block in Web requests according to the ACL rules. If the destination server in a Web request is a server permitted by the ACL, no replacement occurs and the request is forwarded; otherwise, the suffix is replaced with .block and then the request is forwarded.
· In addition to the default suffix .ocx, you can add ActiveX blocking suffixes (that is, the filename suffixes to be replaced in Web requests) through command lines.
Configuring Web filtering
IP address-supported URL filtering can take effect only after the URL address filtering is enabled, while URL parameter filtering, Java blocking, and ActiveX blocking can be enabled independently.
Configuring URL address filtering
|
Step |
Command |
|
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the URL address filtering function. |
firewall http url-filter host enable |
Disabled by default. |
|
3. Specify the default filtering action. |
firewall http url-filter host default { deny | permit } |
Optional. The default is deny. |
|
4. Add a URL address filtering entry. |
firewall http url-filter host url-address { deny | permit } url-address |
N/A |
|
5. Display information about URL address filtering. |
display firewall http url-filter host [ all | item keywords | verbose ] [ | { begin | exclude | include } regular-expression ] |
Optional. |
Configuring IP address-supported URL address filtering
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the URL address filtering function. |
firewall http url-filter host enable |
Disabled by default. |
|
3. Configure IP address-supported URL address filtering. |
firewall http url-filter host ip-address { deny | permit } |
Deny by default. |
|
4. Specify an ACL for URL address filtering. |
firewall http url-filter host acl acl-number |
Optional. By default, no ACL is specified for URL address filtering. |
|
5. Display information about URL address filtering. |
display firewall http url-filter host [ all | item keywords | verbose ] [ | { begin | exclude | include } regular-expression ] |
Optional. |
The source IP addresses specified in the ACL for URL address filtering must be the IP addresses of the websites allowed to be accessed by using their IP addresses.
Configuring URL parameter filtering
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the URL parameter filtering function. |
firewall http url-filter parameter enable |
Disabled by default. |
|
3. Add a URL parameter filtering entry. |
firewall http url-filter parameter { default | keywords keywords } |
N/A |
|
4. Display information about URL parameter filtering. |
display firewall http url-filter parameter [ all | item keywords | verbose ] [ | { begin | exclude | include } regular-expression ] |
Optional. |
Configuring Java blocking
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the Java blocking function. |
firewall http java-blocking enable |
Disabled by default. |
|
3. Add a Java blocking suffix keyword. |
firewall http java-blocking suffix keywords |
Optional. |
|
4. Specify an ACL for Java blocking. |
firewall http java-blocking acl acl-number |
Optional. By default, no ACL is specified for Java blocking. |
|
5. Display information about Java blocking. |
display firewall http java-blocking [ all | item keywords | verbose ] [ | { begin | exclude | include } regular-expression ] |
Optional. |
In the ACL for Java blocking, you need to configure the source IP addresses as the IP addresses of the HTTP servers allowed to be accessed, and set the action to permit.
Configuring ActiveX blocking
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the ActiveX blocking function. |
firewall http activex-blocking enable |
Disabled by default. |
|
3. Add an ActiveX blocking suffix keyword. |
firewall http activex-blocking suffix keywords |
Optional. |
|
4. Specify an ACL for ActiveX blocking. |
firewall http activex-blocking acl acl-number |
Optional. By default, no ACL is specified for ActiveX blocking. |
|
5. Display information about ActiveX blocking. |
display firewall http activex-blocking [ all | item keywords | verbose ] [ | { begin | exclude | include } regular-expression ] |
Optional. |
In the ACL for ActiveX blocking, you need to configure the source IP addresses as the IP addresses of the HTTP servers allowed to be accessed and set the action to permit.
Displaying and maintaining Web filtering
|
Task |
Command |
Remarks |
|
Display information about URL address filtering. |
display firewall http url-filter host [ all | item keywords | verbose ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display information about URL parameter filtering. |
display firewall http url-filter parameter [ all | item keywords | verbose ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display information about Java blocking. |
display firewall http java-blocking [ all | item keywords | verbose ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display information about ActiveX blocking. |
display firewall http activex-blocking [ all | item keywords | verbose ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Clear Web filtering statistics. |
reset firewall http { activex-blocking | java-blocking | url-filter host | url-filter parameter } counter |
Available in user view. |
URL address filtering configuration example
Network requirements
Figure 1 Network diagram
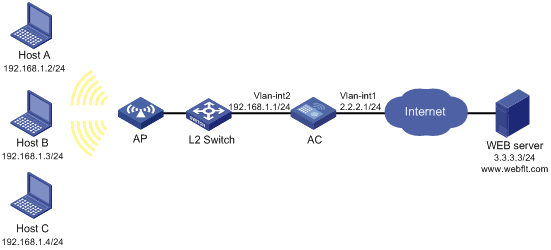
Configuration procedure
# Configure IP addresses for the interfaces. (Details not shown.)
# Configure a NAT policy for the outbound interface.
<AC> system-view
[AC] acl number 2200
[AC-acl-basic-2200] rule 0 permit source 192.168.1.0 0.0.0.255
[AC-acl-basic-2200] rule 1 deny source any
[AC-acl-basic-2200] quit
[AC] nat address-group 1 2.2.2.10 2.2.2.11
[AC] interface Vlan-interface 1
[AC-Vlan-interface1] nat outbound 2200 address-group 1
[AC-Vlan-interface1] quit
# Enable the URL address filtering function.
[AC] firewall http url-filter host enable
# Allow users to access only website www.webfit.com, and set the default filtering action to deny.
[AC] firewall http url-filter host url-address permit www.webflt.com
[AC] firewall http url-filter host default deny
# Configure an ACL for URL address filtering.
[AC] acl number 2000
[AC-acl-basic-2000] rule 0 permit source 3.3.3.3 0.0.0.0
[AC-acl-basic-2000] rule 1 deny source any
[AC-acl-basic-2000] quit
# Allow users to use IP addresses to access websites.
[AC] firewall http url-filter host ip-address permit
[AC] firewall http url-filter host acl 2000
After the configurations are completed, open a Web browser on a host in the LAN, enter website http://www.webflt.com or http://3.3.3.3, and you can access this website correctly. Enter other website addresses, and you are not allowed to access the corresponding websites.
# Display detailed information about URL address filtering.
[AC] display firewall http url-filter host verbose
URL-filter host is enabled.
Default method: deny.
The support for IP address: permit.
The configured ACL group is 2000.
There are 1 packet(s) being filtered.
There are 1 packet(s) being passed.
# Display URL address filtering information for all filtering entries.
[AC] display firewall http url-filter host all
SN Match-Times Keywords
------------------------------------
1 1 www.webflt.com
URL parameter filtering configuration example
Network requirements
The hosts in the network segment 192.168.1.0/24 access the Internet through the AC. The AC is enabled with the URL parameter filtering function, which uses the user-defined filtering entry group to filter Web requests.
Figure 2 Network diagram
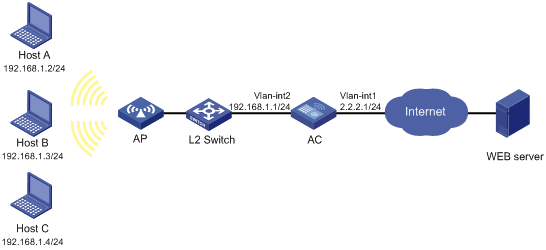
Configuration procedure
# Configure IP addresses for the interfaces. (Details not shown.)
# Configure a NAT policy for the outbound interface.
<AC> system-view
[AC] acl number 2200
[AC-acl-basic-2200] rule 0 permit source 192.168.1.0 0.0.0.255
[AC-acl-basic-2200] rule 1 deny source any
[AC-acl-basic-2200] quit
[AC] nat address-group 1 2.2.2.10 2.2.2.11
[AC] interface Vlan-interface 1
[AC-Vlan-interface1] nat outbound 2200 address-group 1
[AC-Vlan-interface1] quit
# Enable the URL parameter filtering function, and add URL parameter filtering entry group.
[AC] firewall http url-filter parameter enable
[AC] firewall http url-filter parameter keywords group
# Use the display firewall http url-filter parameter verbose command to display detailed URL parameter filtering information.
[AC] display firewall http url-filter parameter verbose
URL-filter parameter is enabled.
There are 1 packet(s) being filtered.
There are 2 packet(s) being passed.
# Use the display firewall http url-filter parameter all command to display URL parameter filtering information for all filtering entries.
[AC] display firewall http url-filter parameter all
SN Match-Times Keywords
------------------------------------
1 1 group
Java blocking configuration example
Network requirements
The hosts in the network segment 192.168.1.0/24 access the Internet through the AC. Enable Java blocking on the AC, add suffix keyword .js, and configure the device to allow only Java applet requests to the website at 5.5.5.5.
Figure 3 Network diagram
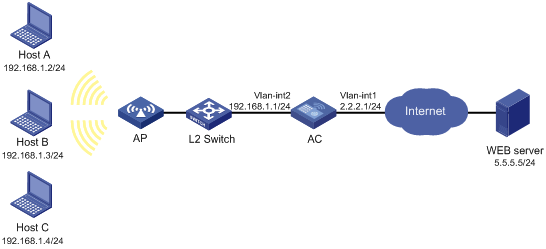
Configuration procedure
# Configure IP addresses for the interfaces. (Details not shown.)
# Configure a NAT policy for the outbound interface.
<AC> system-view
[AC] acl number 2200
[AC-acl-basic-2200] rule 0 permit source 192.168.1.0 0.0.0.255
[AC-acl-basic-2200] rule 1 deny source any
[AC-acl-basic-2200] quit
[AC] nat address-group 1 2.2.2.10 2.2.2.11
[AC] interface Vlan-interface 1
[AC-Vlan-interface1] nat outbound 2200 address-group 1
[AC-Vlan-interface1] quit
# Configure an ACL numbered 2100 for Java blocking.
[AC] acl number 2100
[AC-acl-basic-2100] rule 0 permit source 5.5.5.5 0.0.0.0
[AC-acl-basic-2100] rule 1 deny source any
[AC-acl-basic-2100] quit
# Enable the Java blocking function, add blocking suffix keyword .js, and specify ACL 2100 for Java blocking.
[AC] firewall http java-blocking enable
[AC] firewall http java-blocking suffix .js
[AC] firewall http java-blocking acl 2100
# Use the display firewall http java-blocking verbose command to display detailed Java blocking information.
[AC] display firewall http java-blocking verbose
Java blocking is enabled.
The configured ACL group is 2100.
There are 0 packet(s) being filtered.
There are 1 packet(s) being passed.
# Use the display firewall http java-blocking all command to display Java blocking information for all blocking suffix keywords.
[AC] display firewall http java-blocking all
SN Match-Times Keywords
------------------------------------
1 0 .CLASS
2 0 .JAR
3 1 .js
The output shows that there are three Java blocking suffix keywords, of which .CLASS and .JAR are the default ones, and .js is a user-defined one and has been matched once.
Troubleshooting Web filtering
Failed to add filtering entry or suffix keyword due to upper limit
Symptom
· When you try to add a URL address filtering entry or URL parameter filtering entry, the system prompts you that no more entry can be added.
· When you add a Java blocking or ActiveX blocking suffix keyword, the system prompts you that no more keyword can be added.
Analysis
The number of URL address filtering entries, URL parameter filtering entries, Java blocking suffix keywords, or ActiveX blocking suffix keywords has reached the upper limit.
Solution
If necessary, remove some configured entries or keywords before adding new ones.
Invalid characters are present in the configured parameter
Symptom
When you configure a URL address filtering entry or URL parameter filtering entry, the system displays a character error message.
Analysis
A URL address filtering entry can contain only 0 to 9, a to z, A to Z, dot (.), hyphen (-), underline (_), and wildcards caret (^), dollar sign ($), ampersand (&), and asterisk (*). A URL parameter filtering entry can contain only 0 to 9, a to z, A to Z, wildcards caret (^), dollar sign ($), ampersand (&), and asterisk (*), and other ASCII characters with values between 31 and 127.
Solution
Make sure that all entered characters are valid.
Invalid use of wildcard
Symptom
When you configure a URL address filtering entry or URL parameter filtering entry, the system prompts you that the wildcards are not used correctly.
Analysis
The wildcards for URL address filtering entries and those for URL parameter filtering entries have different usage restrictions:
Table 1 Wildcards for URL address filtering entries
|
Wildcard |
Meaning |
Usage guidelines |
|
^ |
Matches website addresses starting with the keyword |
It can be present once at the beginning of a filtering entry. |
|
$ |
Matches website addresses ending with the keyword |
It can be present once at the end of a filtering entry. |
|
& |
Stands for a valid character other than a dot (.) |
It can be present multiple times at any position of a filtering entry, consecutively or inconsecutively, but cannot be used together with an asterisk (*). |
|
* |
Stands for any number of valid characters and spaces excluding a dot (.) |
It can be present once at the beginning or in the middle of a filtering entry. It cannot be at the end and cannot be used next to a caret (^) or a dollar sign ($). |
Table 2 Wildcards for URL parameter filtering entries
|
Wildcard |
Meaning |
Usage guidelines |
|
^ |
Matches parameters starting with the keyword |
Can be present once at the beginning of a filtering entry. |
|
$ |
Matches parameters ending with the keyword |
It can be present once at the end of a filtering entry. |
|
& |
Stands for one valid character |
It can be present multiple times at any position of a filtering entry, consecutively or inconsecutively, and cannot be used next to an asterisk (*). If it is present at the beginning or end of a filtering entry, it must be next to a caret (^) or a dollar sign ($). |
|
* |
Stands for a string of up to 4 valid characters, including spaces |
It can be present once in the middle of a filtering entry. |
Solution
Use the wildcards correctly according to the above principles.
Invalid blocking suffix
Symptom
When you configure a Java blocking suffix keyword or ActiveX blocking suffix keyword, the system prompts you that there are invalid suffix keywords.
Analysis
A blocking suffix requires a dot (.) as part of it. If no dot or multiple dots are configured, the configuration fails.
Solution
Configure a suffix keyword according to the description in the analysis.
ACL configuration failed
Symptom
An ACL rule uses the IP address of a host in the internal network as the source address and permits requests from the host. The ACL is referenced for URL address filtering, Java blocking or ActiveX blocking, but it does not work.
Analysis
For URL address filtering, Java blocking and ActiveX blocking, ACLs permit access to servers in external networks rather than hosts in the internal network. This is because the internal network is assumed to be trusted.
Solution
Specify the IP address of the server in the external network as the source IP address in the ACL rule.
Unable to access the HTTP server by IP address
Symptom
After the URL address filtering function is enabled, you cannot access the HTTP server by its IP address.
Analysis
By default, the URL address filtering function disables access by IP address. Web requests that use the IP address to access the HTTP server will be filtered.
Solution
Configure an ACL to permit Web requests to the IP address of the HTTP server.
