- Table of Contents
-
- 07-Security Configuration Guide
- 00-Preface
- 01-Security Overview
- 02-AAA Configuration
- 03-802.1X Configuration
- 04-MAC Authentication Configuration
- 05-Portal Configuration
- 06-Port Security Configuration
- 07-User Profile Configuration
- 08-Password Control Configuration
- 09-Public Key Configuration
- 10-PKI Configuration
- 11-SSH Configuration
- 12-SSL Configuration
- 13-SSL VPN Configuration
- 14-TCP Attack Protection Configuration
- 15-ARP Attack Protection Configuration
- 16-IPsec Configuration
- 17-ALG Configuration
- 18-Firewall Configuration
- 19-Session Management Configuration
- 20-Web Filtering Configuration
- 21-User Isolation Configuration
- 22-Source IP Address Verification Configuration
- 23-FIPS Configuration
- 24-Protocol Packet Rate Limit Configuration
- 25-Attack detection and protection configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 22-Source IP Address Verification Configuration | 144.60 KB |
Configuring source IP address verification
Configuring source IP address verification
Displaying and maintaining source IP address verification
Source IP address verification configuration example
Source IPv4 address verification configuration example
Source IPv6 address verification configuration example (using DHCPv6 server)
Source IPv6 address verification configuration example (using ND)
Configuring source IP address verification
Overview
Source IP address verification is intended to improve wireless network security by blocking illegal packets. For example, it can prevent illegal hosts from using a valid IP address to access the network.
Source IP address verification can filter packets based on the IP-MAC binding entries.
For a client using an IPv4 address, the AP can obtain the IP address assigned to the client in the DHCPv4 packets exchanged between the DHCP server and the client, and bind the IP address with the MAC address of the client.
For a client using an IPv6 address, the AP can generate binding entries in either of the following ways:
· DHCPv6—The AP obtains the complete IPv6 address assigned to the client in the DHCPv6 packets exchanged between the DHCPv6 server and the client, and binds the IPv6 address with the MAC address of the client. If the AP obtains the IPv6 address prefix assigned to the client, it cannot generate the proper binding entry.
· ND—The AP obtains the broadcast IPv6 address prefix in the router advertisement packets exchanged between the router and the client, and binds the IPv6 address prefix with the MAC address of the client.
For more information about DHCP, DHCPv6, and ND, see Layer 3 Configuration Guide.
After source IP address verification is enabled, the AP looks up the binding entries for received packets. If the source MAC address and source IP address of a packet matches a binding entry, the AP forwards the packet. Otherwise, the AP discards it. Figure 1 shows how source IP address verification works.
Figure 1 Source IP address verification process
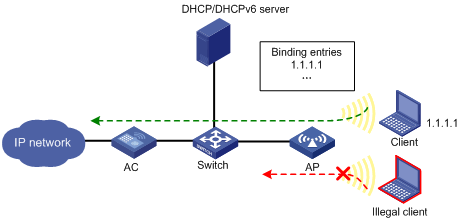
Configuring source IP address verification
Source IP address verification is effective on a per-SSID basis. After you enable this feature for an SSID, the AP only revivifies the source IP address of the clients using the SSID to access the network, but does not check the source IP addresses of the clients using other SSIDs.
For a client using an SSID configured with source IP address verification, if it accesses the network through AP local authentication, the source IP address verification feature is effective but the IP-MAC binding entry for the client cannot be displayed on the AC. If the client needs to roam to an AP of another AC in the roaming group, the AC to which the client roams must be configured with source IP address verification for the specified SSID. Otherwise, the client connection is lost. For more information about AP local authentication and WLAN roaming, see WLAN Configuration Guide.
To configure source IP address verification:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a WLAN service template. |
wlan service-template service-template-number { clear | crypto | wapi } |
N/A |
|
3. Enable source IP address verification for IPv4 clients. |
ip verify source |
By default, source IP address verification is disabled for IPv4 clients. |
|
4. Enable source IP address verification for IPv6 clients. |
ipv6 verify source |
By default, source IP address verification is disabled for IPv6 clients. |
Displaying and maintaining source IP address verification
|
Task |
Command |
|
Displaying IPv4/IPv6 binding entries. |
display wlan client { ip | ipv6 } source binding [ mac-address mac-address ] [ | { begin | exclude | include } regular-expression ] |
Source IP address verification configuration example
Source IPv4 address verification configuration example
Network requirements
As shown in Figure 2, the clients access the network using the SSID "service", and the DHCP server dynamically assigns IP addresses for the clients.
Enable source IP address verification for the clients using the SSID to prevent illegal access.
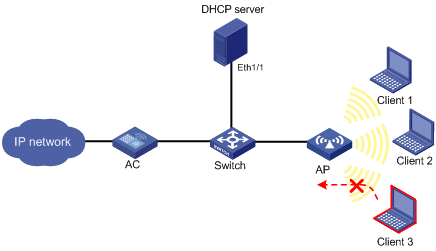
Configuration procedure
1. Configure the DHCP server:
# Enable DHCP.
<DHCP> system-view
[DHCP] dhcp enable
# Assign an IP address to interface Ethernet 1/1.
[DHCP] interface ethernet 1/1
[DHCP-Ethernet1/1] ip address 10.1.1.1 24
# Configure interface Ethernet 1/1 to operate in DHCP server mode.
[DHCP-Ethernet1/1] dhcp select server global-pool
[DHCP-Ethernet1/1] quit
# Create DHCP address pool 0, and assign network segment 10.1.1.0/24 to the address pool.
[DHCP] dhcp server ip-pool 0
[DHCP-dhcp-pool-0] network 10.1.1.0 mask 255.255.255.0
# Create a WLAN-ESS interface.
<AC> system-view
[AC] interface wlan-ess 1
[AC-WLAN-ESS1] quit
# Configure a WLAN service template, specify "service" as the SSID, and bind the WLAN-ESS interface with the service template.
[AC] wlan service-template 1 clear
[AC-wlan-st-1] ssid service
# Enable source IP address verification for IPv4 clients.
[AC-wlan-st-1] ip verify source
[AC-wlan-st-1] bind wlan-ess 1
[AC-wlan-st-1] authentication-method open-system
[AC-wlan-st-1] service-template enable
[AC-wlan-st-1] quit
# Create an AP template named "ap1".
[AC] wlan ap ap1 model WA3628i-AGN
[AC-wlan-ap-ap1] serial-id 210235A29G007C000020
# Configure 802.11gn radio.
[AC-wlan-ap-ap1] radio 2 type dot11gn
[AC-wlan-ap-ap1-radio-2] service-template 1
[AC-wlan-ap-ap1-radio-2] radio enable
Verifying the configuration
The MAC address of Client 1is 001d-0f31-87dd, and that of Client 2 is 001c-f08f-f7f1. They are legal clients but Client 3 is an illegal client. After they obtain IP addresses from the DHCP server, you can see the IPv4 binding entries for the two clients by using the display wlan client ip source binding command. The AP filters the received packets using the two binding entries. It forwards the packets from Client 1 and Client 2, but discards the packets from Client 3.
<Sysname> display wlan client ip source binding
Total Number of Clients: 2
IP Source Binding Information
------------------------------------------------------------
MAC Address APID/RID Type Binding IP Address
------------------------------------------------------------
001d-0f31-87dd 1/2 DHCP 10.1.1.1
001c-f08f-f7f1 1/2 DHCP 10.1.1.2
------------------------------------------------------------
Source IPv6 address verification configuration example (using DHCPv6 server)
Network requirements
· As shown in Figure 3, the clients access the network using the SSID "service", and the DHCPv6 server dynamically assigns IPv6 addresses for the clients.
· Enable source IP address verification for the IPv6 clients using the SSID to prevent illegal access.
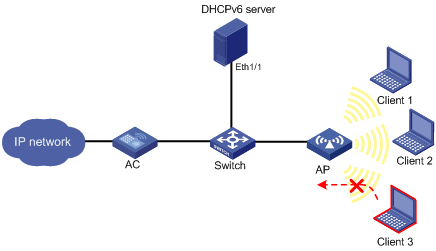
Configuration procedure
1. Configure the DHCPv6 server:
# Enable IPv6 forwarding and DHCPv6 server.
<DHCPv6> system-view
[DHCPv6] ipv6
[DHCPv6] ipv6 dhcp server enable
# Create DHCPv6 address pool 1, and assign network segment 2001:2::/64 to the address pool.
[DHCPv6] ipv6 dhcp pool 1
[DHCPv6-dhcp6-pool-1] network 2001:2::/64
[DHCPv6-dhcp6-pool-1] quit
# Assign an IPv6 address to interface Ethernet 1/1.
[DHCPv6] interface ethernet 1/1
[DHCPv6-Ethernet1/1] ipv6 address 2001:2::1/64
# Enable interface Ethernet 1/1 to send RA messages.
[DHCPv6-Ethernet1/1] undo ipv6 nd ra halt
# Configure interface Ethernet 1/1 to operate in DHCPv6 server mode, and reference address pool 1.
[DHCPv6-Ethernet1/1] ipv6 dhcp server apply pool 1
2. Configure the AC:
# Create a WLAN-ESS interface.
<AC> system-view
[AC] interface wlan-ess 1
[AC-WLAN-ESS1] quit
# Configure a WLAN service template, specify "service" as the SSID, and bind the WLAN-ESS interface with the service template.
[AC] wlan service-template 1 clear
[AC-wlan-st-1] ssid service
# Enable source IP address verification for IPv6 clients.
[AC-wlan-st-1] ipv6 verify source
[AC-wlan-st-1] bind wlan-ess 1
[AC-wlan-st-1] authentication-method open-system
[AC-wlan-st-1] service-template enable
[AC-wlan-st-1] quit
# Create an AP template named "ap1."
[AC] wlan ap ap1 model WA3628i-AGN
[AC-wlan-ap-ap1] serial-id 210235A29G007C000020
# Configure 802.11gn radio.
[AC-wlan-ap-ap1] radio 2 type dot11gn
[AC-wlan-ap-ap1-radio-2] service-template 1
[AC-wlan-ap-ap1-radio-2] radio enable
Verifying the configuration
The MAC address of Client 1is 001d-0f31-87dd, and that of Client 2 is 001c-f08f-f7f1. They are legal clients but Client 3 is an illegal client. After they obtain IPv6 addresses from the DHCPv6 server, you can see the IPv6 binding entries for the two clients by using the display wlan client ipv6 source binding command. The AP filters the received IPv6 packets using the two binding entries. It forwards the packets from Client 1 and Client 2, but discards the packets from Client 3.
<Sysname> display wlan client ipv6 source binding
Total Number of Clients: 2
IPv6 Source Binding Information
------------------------------------------------------------
MAC Address APID/RID Type Binding IP Address
------------------------------------------------------------
001d-0f31-87dd 1/2 DHCPv6 2001:2::2
001c-f08f-f7f1 1/2 DHCPv6 2001:2::3
------------------------------------------------------------
Source IPv6 address verification configuration example (using ND)
Network requirements
As shown in Figure 4, the clients access the network using the SSID "service", and the router dynamically assigns IPv6 address prefixes for the clients.
Enable source IP address verification for the IPv6 clients using the SSID to prevent illegal access.
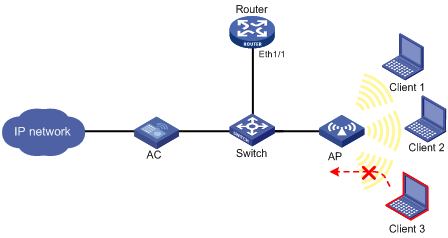
Configuration procedure
1. Configure the router:
# Enable IPv6 forwarding.
<Router> system-view
[Router] ipv6
# Assign an IPv6 address to interface Ethernet 1/1.
[Router] interface ethernet 1/1
[Router-Ethernet1/1] ipv6 address 2001::1/64
# Enable interface Ethernet 1/1 to send RA messages.
[Router-Ethernet1/1] undo ipv6 nd ra halt
# Specify the address prefix to distribute as 2001::/64, with life time being 86400 seconds. The preferred life time is 3600 seconds.
[Router-Ethernet1/1] ipv6 nd ra prefix 2001::/64 86400 3600
2. Configure the AC:
# Create a WLAN-ESS interface.
<AC> system-view
[AC] interface wlan-ess 1
[AC-WLAN-ESS1] quit
# Configure a WLAN service template, specify "service" as the SSID, and bind the WLAN-ESS interface with the service template.
[AC] wlan service-template 1 clear
[AC-wlan-st-1] ssid service
# Enable source IP address verification for IPv6 clients.
[AC-wlan-st-1] ipv6 verify source
[AC-wlan-st-1] bind wlan-ess 1
[AC-wlan-st-1] authentication-method open-system
[AC-wlan-st-1] service-template enable
[AC-wlan-st-1] quit
# Create an AP template named "ap1."
[AC] wlan ap ap1 model WA3628i-AGN
[AC-wlan-ap-ap1] serial-id 210235A29G007C000020
# Configure 802.11gn radio.
[AC-wlan-ap-ap1] radio 2 type dot11gn
[AC-wlan-ap-ap1-radio-2] service-template 1
[AC-wlan-ap-ap1-radio-2] radio enable
Verifying the configuration
The MAC address of Client 1is 001d-0f31-87dd, and that of Client 2 is 001c-f08f-f7f1. They are legal clients but Client 3 is an illegal client. After they obtain IPv6 address prefixes through ND, you can see the IPv6 binding entries for the two clients by using the display wlan client ipv6 source binding command. The AP filters the received IPv6 packets using the two binding entries. It forwards the packets from Client 1 and Client 2, but discards the packets from Client 3.
<Sysname> display wlan client ipv6 source binding
Total Number of Clients: 2
IPv6 Source Binding Information
------------------------------------------------------------
MAC Address APID/RID Type Binding IP Address
------------------------------------------------------------
001d-0f31-87dd 1/2 ND 2001::
001c-f08f-f7f1 1/2 ND 2001::
------------------------------------------------------------
