- Table of Contents
-
- 07-Security Configuration Guide
- 00-Preface
- 01-Security Overview
- 02-AAA Configuration
- 03-802.1X Configuration
- 04-MAC Authentication Configuration
- 05-Portal Configuration
- 06-Port Security Configuration
- 07-User Profile Configuration
- 08-Password Control Configuration
- 09-Public Key Configuration
- 10-PKI Configuration
- 11-SSH Configuration
- 12-SSL Configuration
- 13-SSL VPN Configuration
- 14-TCP Attack Protection Configuration
- 15-ARP Attack Protection Configuration
- 16-IPsec Configuration
- 17-ALG Configuration
- 18-Firewall Configuration
- 19-Session Management Configuration
- 20-Web Filtering Configuration
- 21-User Isolation Configuration
- 22-Source IP Address Verification Configuration
- 23-FIPS Configuration
- 24-Protocol Packet Rate Limit Configuration
- 25-Attack detection and protection configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 13-SSL VPN Configuration | 62.99 KB |
Configuring SSL VPN
Overview
SSL VPN is a VPN technology based on Secure Sockets Layer (SSL). It works between the transport layer and the application layer. Using the certificate-based identity authentication, data encryption, and integrity verification mechanisms that the SSL protocol provides, SSL VPN can establish secure connections for communications at the application layer.
SSL VPN has been widely used for secure, remote Web-based access. For example, it can allow remote users to access the corporate network securely. Figure 1 shows a typical SSL VPN network. On the SSL VPN gateway, the network administrator creates resources corresponding to the servers in the internal network. To access an internal server, a remote user first needs to establish a Hypertext Transfer Protocol Secure (HTTPS) connection with the SSL VPN gateway and selects the resources to be accessed. Then, the SSL VPN gateway forwards the resource access request to the internal server. In the SSL VPN deployed network, the SSL VPN gateway will establish an SSL connection with a remote user and then will authenticate the user before allowing the user to access an internal server, and therefore the internal servers are well protected.
Figure 1 Network diagram for SSL VPN configuration
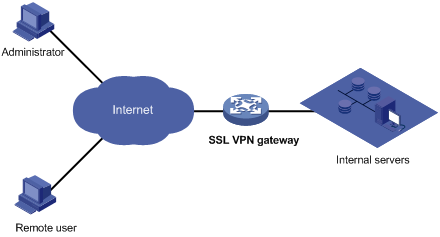
The following is how SSL VPN operates:
1. The administrator logs in to the Web interface of the SSL VPN gateway, and then creates resources corresponding to the internal servers.
2. The remote user establishes an HTTPS connection with the SSL VPN gateway. The SSL VPN gateway and the remote user authenticate each other using the certificate-based authentication function provided by SSL.
3. After the HTTPS connection is established, the user can try to log in to the Web interface of the SSL VPN gateway by entering the username, password, and authentication method (RADIUS authentication, for example). The SSL VPN gateway will verify the user information.
4. After logging in to the Web interface, the user finds the resources to access on the Web interface and then sends an access request to the SSL VPN gateway through an SSL connection.
5. The SSL VPN gateway resolves the request, interacts with the corresponding server, and then forwards the server’s reply to the user.
Configuration procedure
Complete the following tasks to configure SSL VPN:
· Specify the SSL server policy to be used by the SSL VPN service. To access the SSL VPN gateway or the internal resources, remote users need to log in to the Web interface of the SSL VPN gateway through HTTPS. Therefore, you must specify an SSL server policy on the SSL VPN gateway so that the gateway can determine the SSL parameters to be used for providing the SSL VPN service.
· Specify the TCP port number to be used by the SSL VPN service. The SSL VPN gateway acts as the HTTPS server to provide the Web interface for remote users to log in.
· Enable the SSL VPN service. Remote users can access the Web interface of the SSL VPN gateway only after the SSL VPN service is enabled on the gateway.
Follow these guidelines when you configure SSL VPN:
· If the HTTPS service and the SSL VPN service use the same port number, the two services must use the same SSL server policy. Otherwise, you cannot enable both the services.
· When both the HTTPS service and the SSL VPN service are enabled and they use the same port number, to modify the SSL server policy that the services use, you must first disable the two services, modify the SSL server policy, and then enable the services again.
· When the SSL VPN service is enabled, your change to the port number or SSL server policy for the service does not take effect. To make your change take effect, disable the SSL VPN service and then enable it again.
Before you configure SSL VPN, create an SSL server policy. For information about SSL server policy configuration, see "Configuring SSL."
To configure SSL VPN:
|
Step |
Command |
|
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify the SSL server policy and port to be used by the SSL VPN service. |
ssl-vpn server-policy server-policy-name [ port port-number ] |
By default, no SSL server policy is specified for the SSL VPN service and the SSL VPN service uses TCP port 443. |
|
3. Enable the SSL VPN service. |
ssl-vpn enable |
Disabled by default. |
SSL VPN configuration example
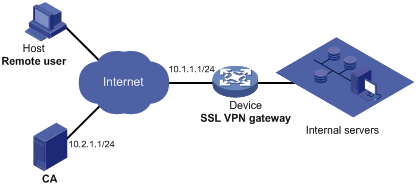
Network requirements
As shown in Figure 2, configure SSL and enable SSL VPN service on the SSL VPN gateway, so that users can log in to the Web interface of the SSL VPN gateway through HTTPS and then access the internal resources of the corporate network through the SSL VPN gateway.
In this configuration example:
· The IP address of the SSL VPN gateway is 10.1.1.1/24.
· The IP address of the Certificate Authority (CA) is 10.2.1.1/24. The name of the CA is CA server, which is used to issue certificates to the SSL VPN gateway and remote users.
Configuration procedure
In this example, the Windows Server is used as the CA. Install the SCEP plugin on the CA.
Before the following configurations, make sure the intended SSL VPN gateway, the CA, and the host used by the remote user can reach each other, and the CA is enabled with the CA service and can issue certificates to the device (SSL VPN gateway) and the host.
1. Apply for a certificate for the SSL VPN gateway:
# Configure a PKI entity named en and specify the common name of the entity as http-server.
<Device> system-view
[Device] pki entity en
[Device-pki-entity-en] common-name http-server
[Device-pki-entity-en] quit
# Configure a PKI domain named sslvpn, and specify the trusted CA as ca server, the URL of the RA server as http://10.2.1.1/certsrv/mscep/mscep.dll, registration authority for certificate requesting as RA, and the entity as en.
[Device] pki domain sslvpn
[Device-pki-domain-sslvpn] ca identifier ca server
[Device-pki-domain-sslvpn] certificate request url http://10.2.1.1/certsrv/mscep/mscep.dll
[Device-pki-domain-sslvpn] certificate request from ra
[Device-pki-domain-sslvpn] certificate request entity en
[Device-pki-domain-sslvpn] quit
# Generate the local RSA key pair.
[Device] public-key local create rsa
# Retrieve the CA certificate.
[Device] pki retrieval-certificate ca domain sslvpn
# Apply for a certificate for the device.
[Device] pki request-certificate domain sslvpn
2. Configure an SSL server policy for the SSL VPN service:
# Configure an SSL server policy named myssl, and specify the policy to use PKI domain sslvpn.
[Device] ssl server-policy myssl
[Device-ssl-server-policy-myssl] pki-domain sslvpn
[Device-ssl-server-policy-myssl] quit
3. Configure SSL VPN:
# Specify the SSL server policy myssl and port 443 (default) for the SSL VPN service.
[Device] ssl-vpn server-policy myssl
# Enable the SSL VPN service.
[Device] ssl-vpn enable
4. Verify the configuration.
On the user host, launch the IE browser and input https://10.1.1.1/svpn in the address bar. You can open the Web login interface of the SSL VPN gateway.
For more information about PKI configuration commands, SSL configuration commands, and the public-key local create rsa command, see Security Command Reference.
