- Table of Contents
-
- 07-Security Configuration Guide
- 00-Preface
- 01-Security Overview
- 02-AAA Configuration
- 03-802.1X Configuration
- 04-MAC Authentication Configuration
- 05-Portal Configuration
- 06-Port Security Configuration
- 07-User Profile Configuration
- 08-Password Control Configuration
- 09-Public Key Configuration
- 10-PKI Configuration
- 11-SSH Configuration
- 12-SSL Configuration
- 13-SSL VPN Configuration
- 14-TCP Attack Protection Configuration
- 15-ARP Attack Protection Configuration
- 16-IPsec Configuration
- 17-ALG Configuration
- 18-Firewall Configuration
- 19-Session Management Configuration
- 20-Web Filtering Configuration
- 21-User Isolation Configuration
- 22-Source IP Address Verification Configuration
- 23-FIPS Configuration
- 24-Protocol Packet Rate Limit Configuration
- 25-Attack detection and protection configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 18-Firewall Configuration | 232.40 KB |
Configuring a packet-filter firewall
Packet-filter firewall configuration task list
Enabling the firewall function
Configuring the default filtering action of the firewall
Applying an ACL packet-filter firewall to an interface
Applying an ACL packet-filter firewall to a user profile
Displaying and maintaining a packet-filter firewall
Packet-filter firewall configuration example
Enabling the firewall function
Applying an ASPF policy to an interface
Applying an ASPF policy to a user profile
Displaying and maintaining ASPF
Configuring firewall
The term "router" in this document refers to both routers and routing-capable H3C access controllers.
Overview
A firewall blocks unauthorized Internet access to a protected network while allowing internal network users to access the Internet through WWW, or to send and receive e-mails. A firewall can also be used to control access to the Internet, for example, to permit only specific hosts within the organization to access the Internet. Many of today's firewalls offer additional features, such as identity authentication and encryption.
Another application of firewall is to protect the mainframe and important resources (such as data) on internal networks. Any access to protected data is filtered by the firewall, even if the access is initiated by a user within the internal network.
The device mainly implements three categories of firewalls:
· ACL based packet filter
· Application Specific Packet Filter (ASPF)
· Address translation
This chapter focuses on ACL packet-filter firewall and ASPF. For more information about address translation, see "Configuring NAT."
ACL based packet filter
An ACL packet-filter firewall implements IP packet specific filtering.
Before an IP packet can be forwarded, the firewall obtains the header information of the packet, including the following:
· Number of the upper layer protocol carried by the IP layer
· Source address
· Destination address
· Source port number
· Destination port number
The firewall compares the head information against the preset ACL rules and processes the packet based on the comparison result.
An ACL packet-filter is a static firewall. It cannot solve the following issues:
· For multi-channel application layer protocols, such as FTP and H.323, the values of some security policy parameters are unpredictable.
· ICMP attacks cannot be prevented because not all faked ICMP error messages from the network can be recognized.
· For a TCP connection, the first packet must be a SYN packet. Any non-SYN packet that is the first packet over the TCP connection is dropped. If a packet-filter firewall is deployed in a network, the non-SYN packets of existing TCP connections passing the firewall for the first time are dropped, breaking the existing TCP connections.
ASPF
ASPF was proposed to address the issues that a static firewall cannot solve. An ASPF implements application layer and transport specific, namely status-based, packet filtering. An ASPF can detect application layer protocols including FTP, GTP, HTTP, SMTP, Real RTSP, SCCP, SIP, and H.323 (Q.931, H.245, and RTP/RTCP), and transport layer protocols TCP and UDP.
ASPF functions
An ASPF provides the following functions:
· Application layer protocol inspection—ASPF checks the application layer information of packets, such as the protocol type and port number, and monitors the application layer protocol status for each connection. ASPF maintains the status information of each connection, and based on the status information, determines whether to permit a packet to pass through the firewall into the internal network, thus defending the internal network against attacks.
· Transport layer protocol inspection (generic TCP and UDP inspection)—ASPF checks a TCP/UDP packet's source and destination addresses and port numbers to determine whether to permit the packet to pass through the firewall into the internal network.
· Connection status inspection—ASPF can filter packets according to connection status.
· Port to Application Mapping (PAM)—Allows you to specify port numbers other than the standard ones for application layer protocols.
· ICMP error message inspection—ASPF checks the connection information carried in an ICMP error message. If the information does not match the connection, the ASPF processes the packet as configured, for example, it discards the packet.
· First packet inspection for TCP connection—ASPF checks the first packet over a TCP connection. If the first packet over a TCP connection is not a SYN packet, the ASPF will discard the packet.
At the border of a network, an ASPF can work in coordination with a packet-filter firewall to provide the network with a security policy that is more comprehensive and better satisfies the actual needs.
ASPF basic concepts
· PAM
While application layer protocols use the standard port numbers for communication, PAM allows you to define a set of new port numbers for different applications, and provides mechanisms to maintain and use the configuration information of user-defined ports.
PAM supports two types of port mapping mechanisms: general port mapping and host port mapping.
¡ General port mapping—A mapping of a user-defined port number to an application layer protocol. If port 8080 is mapped to HTTP, for example, all TCP packets to port 8080 are regarded as HTTP packets.
¡ Host port mapping—A mapping of a user-defined port number to an application layer protocol for packets to/from specific hosts. For example, you can establish a host port mapping so that all TCP packets using 8080 as the destination port and 10.110.0.0/16 as the destination network segment are regarded as HTTP packets. The hosts can be specified by means of a basic ACL.
· Single-channel protocol and multi-channel protocol
¡ Single-channel protocol—A single-channel protocol establishes only one channel to exchange both control messages and data for a user. SMTP and HTTP are examples of single-channel protocols.
¡ Multi-channel protocol—A multi-channel protocol establishes more than one channel for a user and transfers control messages and user data through different channels. FTP and RTSP are examples of multi-channel protocols.
· Internal interface and external interface
On an edge device configured with ASPF to protect servers on the internal network, interfaces connected with the internal network are internal interfaces and the interface connected with the Internet is the external interface.
When an ASPF is applied on the outbound direction of the external interface of a device, a temporary channel can be opened on the firewall for return packets to internal network users accessing the Internet.
Application layer protocol inspection
As shown in Figure 1, to protect the internal network, an ACL is usually required on the router to permit internal hosts to access external networks while prohibiting hosts on external networks from accessing the internal network. However, the ACL will also filter out the return packets to internal users, thus failing the connection setup attempts.
Figure 1 Application layer protocol inspection
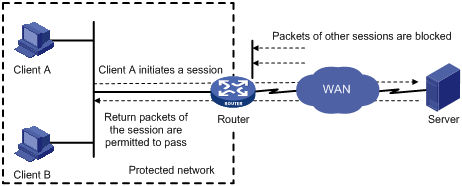
ASPF implements the application layer protocol inspection function in cooperation with the session management and ALG features. After detecting the first packet of a session, ASPF matches the packet with the configured policy and sends the result to the session management feature, which is responsible for session information database establishment and session status maintenance. Then, the ASPF processes subsequent packets of the session based on session status information returned by the session management feature.
For information about session management, see "Managing sessions." For information about ALG, see "Configuring ALG."
Transport layer protocol inspection
Configuring a packet-filter firewall
WLAN-ESS interfaces do not support IPv6 packet-filter firewall.
User profiles do not support IPv6 packet-filter firewall.
Packet-filter firewall configuration task list
|
Task |
Remarks |
|
Required. |
|
|
Optional. |
|
|
Perform at least one of the tasks. |
|
Enabling the firewall function
To enable IPv4 firewall:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the IPv4 firewall function. |
firewall enable |
Disabled by default. |
To enable IPv6 firewall:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the IPv6 firewall function. |
firewall ipv6 enable |
Disabled by default. |
Configuring the default filtering action of the firewall
The default filtering action configuration is used for the firewall to determine whether to permit a data packet to pass or deny the packet when there is no appropriate criterion for judgment.
To configure the default filtering action of the IPv4 firewall:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify the default filtering action of the IPv4 firewall. |
firewall default { deny | permit } |
Optional. By default, the firewall permits packets to pass. |
To configure the default filtering action of the IPv6 firewall:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify the default filtering action of the IPv6 firewall. |
firewall ipv6 default { deny | permit } |
Optional. By default, the firewall permits packets to pass. |
Applying an ACL packet-filter firewall to an interface
When an ACL is applied to an interface, the time range-based filtering will also work at the same time. In addition, you can specify separate access rules for inbound and outbound packets.
A basic ACL defines rules based only on the Layer 3 source IP addresses to analyze and process data packets.
An advanced ACL defines rules according to the source and destination IP addresses of packets, the type of protocol over IP, TCP/UDP source and destination ports.
To apply an IPv4 ACL-based packet-filter firewall to an interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Apply an IPv4 ACL to the interface. |
firewall packet-filter { acl-number | name acl-name } { inbound | outbound } |
By default, no ACL-based packet-filter firewall is applied to filter IPv4 packets on an interface. You can apply only one IPv4 ACL to filter packets in one direction of an interface. |
To apply an IPv6 ACL-based packet-filter firewall to an interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Apply an IPv6 ACL to the interface. |
firewall packet-filter ipv6 { acl6-number | name acl6-name } { inbound | outbound } |
By default, no ACL-based packet-filter firewall is applied to filter IPv6 packets on an interface. You can apply only one IPv6 ACL to filter packets in one direction of an interface. |
Applying an ACL packet-filter firewall to a user profile
Perform this task to implement user-based packet filtering. After a user passes authentication, if the user is authorized with a user profile and the user profile is configured with a packet-filter firewall, the packets received or sent by the user are filtered by the firewall as configured.
To apply an ACL-based packet-filter firewall to a user profile:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter user profile view. |
user-profile user-profile-name |
N/A |
|
3. Apply an ACL to the user profile. |
firewall packet-filter { acl-number | name acl-name } { inbound | outbound } |
By default, packet filtering is not configured for any user profile. You can apply only one ACL to filter packets in one direction of a user profile. |
Displaying and maintaining a packet-filter firewall
|
Task |
Command |
Remarks |
|
Display the packet filtering statistics of the IPv4 firewall. |
display firewall-statistics { all | interface interface-type interface-number | user-profile user-profile-name } [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display the packet filtering statistics of the IPv6 firewall. |
display firewall ipv6 statistics { all | interface interface-type interface-number } [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Clear the packet filtering statistics of the IPv4 firewall. |
reset firewall-statistics { all | interface interface-type interface-number | user-profile user-profile-name } |
Available in user view. |
|
Clear the packet filtering statistics of the IPv6 firewall. |
reset firewall ipv6 statistics { all | interface interface-type interface-number } |
Available in user view. |
Packet-filter firewall configuration example
Network requirements
As shown in Figure 2, the internal network of a company is connected to VLAN-interface 2 of the AC, and the internal users access the Internet through VLAN-interface 3 of the AC.
The company provides WWW, FTP and Telnet services to the outside. The internal subnet of the company is 129.1.1.0/24, on which the internal FTP server address is 129.1.1.1, the Telnet server address is 129.1.1.2, and the internal WWW server address is 129.1.1.3. The public address of the company is 20.1.1.1. NAT is enabled on the AC so that hosts on the internal network can access the Internet and external hosts can access the internal servers.
Configure the firewall feature to achieve the following aims:
· Only specific users on the external network are allowed access to the internal servers.
This example assumes the specific external user is at 20.3.3.3.
· Only specific hosts on the internal network are permitted access to the external network.
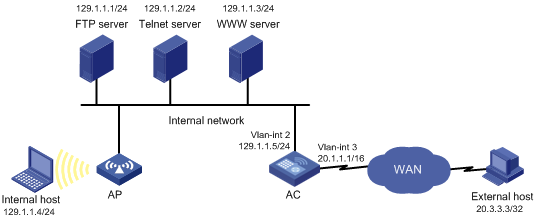
Configuration procedure
# Enable the firewall function on the AC.
<AC> system-view
[AC] firewall enable
# Create advanced ACL 3001.
[AC] acl number 3001
# Configure rules to permit specific hosts to access external networks and permit internal servers to access external networks.
[AC-acl-adv-3001] rule permit ip source 129.1.1.1 0
[AC-acl-adv-3001] rule permit ip source 129.1.1.2 0
[AC-acl-adv-3001] rule permit ip source 129.1.1.3 0
[AC-acl-adv-3001] rule permit ip source 129.1.1.4 0
# Configure a rule to prohibit all IP packets from passing the firewall.
[AC-acl-adv-3001] rule deny ip
[AC-acl-adv-3001] quit
# Create advanced ACL 3002.
[AC] acl number 3002
# Configure a rule to allow a specific external user to access internal servers.
[AC-acl-adv-3002] rule permit tcp source 20.3.3.3 0 destination 129.1.1.0 0.0.0.255
# Configure a rule to permit specific data (only packets of which the port number is greater than 1024) to get access to the internal network.
[AC-acl-adv-3002] rule permit tcp destination 20.1.1.1 0 destination-port gt 1024
[AC-acl-adv-3002] rule deny ip
[AC-acl-adv-3002] quit
# Apply ACL 3001 to packets that come in through VLAN-interface 2.
[AC] interface vlan-interface 2
[AC-Vlan-interface2] firewall packet-filter 3001 inbound
[AC-Vlan-interface2] quit
# Apply ACL 3002 to packets that come in through VLAN-interface 3.
[AC] interface vlan-interface 3
[AC-Vlan-interface3] firewall packet-filter 3002 inbound
Configuring an ASPF
ASPF configuration task list
|
Task |
Remarks |
|
Required. |
|
|
Required. |
|
|
Perform at least one of the tasks. |
|
|
Optional. |
Enabling the firewall function
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the IPv4 firewall function. |
firewall enable |
Disabled by default. |
Configuring an ASPF policy
Note the following guidelines when you configure an ASPF policy:
· If you enable TCP or UDP inspection without configuring application layer protocol inspection, some packets may fail to get a response. Therefore, enable application layer protocol inspection together with TCP/UDP inspection.
· In the case of a Telnet application, you only need to configure TCP inspection.
To configure an ASPF policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an ASPF policy and enter its view. |
aspf-policy aspf-policy-number |
N/A |
|
3. Drop ICMP error messages. |
icmp-error drop |
Optional. By default, ICMP error messages are not dropped. |
|
4. Drop non-SYN packet that is the first packet over a TCP connection. |
tcp syn-check |
Optional. By default, a non-SYN packet that is the first packet over a TCP connection is not dropped. |
Applying an ASPF policy to an interface
Two concepts are distinguished in ASPF policy: internal interface and external interface.
If the device is connected to both the internal network and the Internet, and employs ASPF to protect the internal servers, the interface connected to the internal network is the internal interface and the one connected to the Internet is the external interface.
IF both ASPF and packet-filter firewall are applied to the external interface, access to the internal network from the Internet is denied. The response packet can pass ASPF when internal network users access the Internet.
To monitor the traffic through an interface, you must apply the configured ASPF policy to that interface.
Make sure a connection initiation packet and the corresponding return packet are based on the same interface, because it is based on interfaces that an ASPF stores and maintains the application layer protocol status.
To apply an ASPF policy on an Interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Apply an ASPF policy to the interface. |
firewall aspf aspf-policy-number { inbound | outbound } |
Not applied by default. |
Applying an ASPF policy to a user profile
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter user profile view. |
user-profile user-profile-name |
N/A |
|
3. Apply an ASPF policy to the user profile. |
firewall aspf aspf-policy-number { inbound | outbound } |
By default, no ASPF policy is applied to any user profile. |
Configuring port mapping
Two mapping mechanisms exist: general port mapping and basic ACL–based host port mapping.
· General port mapping—Refers to a mapping of a user-defined port number to an application layer protocol. If port 8080 is mapped to HTTP, for example, all TCP packets the destination port of which is port 8080 are regarded as HTTP packets.
· Host port mapping—Refers to a mapping of a user-defined port number to an application layer protocol for packets to some specific hosts. For example, you can establish a host port mapping so that all TCP packets using port 8080 sent to the network segment 10.110.0.0 are regarded as HTTP packets. The address range of hosts can be specified by means of a basic ACL.
To configure port mapping:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure mapping between the port and the application protocol. |
port-mapping application-name port port-number [ acl acl-number ] |
Not configured by default. The application layer protocols supported by this function include FTP, GTP, H323, HTTP, RTSP, SCCP, SIP, SMTP, and SQLNET. |
Displaying and maintaining ASPF
|
Task |
Command |
Remarks |
|
Display all ASPF policy and session information. |
display aspf all [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display the ASPF policy configuration applied to the interface. |
display aspf interface [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display the configuration information of a specific ASPF policy. |
display aspf policy aspf-policy-number [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display the port mapping information. |
display port-mapping [ application-name | port port-number ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
ASPF configuration example
Network requirements
Configure an ASPF policy on the AC to drop ICMP error messages and non-SYN packets that are the first packets over TCP connections.
This example applies to scenarios where local users need to access remote network services.
Figure 3 Network diagram
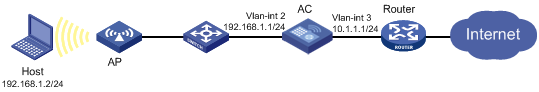
Configuration procedure
# Enable the firewall function on the AC.
<AC> system-view
[AC] firewall enable
# Configure ACL 3111 to prohibit all IP packets from entering the internal network. The ASPF will create a TACL for packets permitted to pass the firewall.
[AC] acl number 3111
[AC-acl-adv-3111] rule deny ip
[AC-acl-adv-3111] quit
# Create an ASPF policy.
[AC] aspf-policy 1
[AC-aspf-policy-1] icmp-error drop
[AC-aspf-policy-1] tcp syn-check
[AC-aspf-policy-1] quit
# Apply ACL 3111 and the ASPF policy to interface VLAN-interface 3.
[AC] interface vlan-interface 3
[AC-Vlan-interface3] firewall aspf 1 outbound
[AC-Vlan-interface3] firewall packet-filter 3111 inbound
