- Table of Contents
-
- H3C Low-End Ethernet Switches Configuration Guide(V1.01)
- 01-Login Configuration Guide
- 02-VLAN Configuration Guide
- 03-IP Address Configuration Guide
- 04-Voice VLAN Configuration Guide
- 05-GVRP Configuration Guide
- 06-Ethernet Interface Basic Configuration Guide
- 07-Link Aggregation Configuration Guide
- 08-Port Isolation Configuration Guide
- 09-Port Security Configuration Guide
- 10-Port Binding Configuration Guide
- 11-MAC Address Table Management Configuration Guide
- 12-DLDP Configuration Guide
- 13-Auto Detect Configuration Guide
- 14-MSTP Configuration Guide
- 15-Routing Configuration Guide
- 16-Multicast Configuration Guide
- 17-802.1x Configuration Guide
- 18-AAA Configuration Guide
- 19-MAC Authentication Configuration Guide
- 20-VRRP Configuration Guide
- 21-ARP Configuration Guide
- 22-DHCP Configuration Guide
- 23-ACL Configuration Guide
- 24-QoS-QoS Profile Configuration Guide
- 25-Web Cache Redirection Configuration Guide
- 26-Mirroring Configuration Guide
- 27-IRF Configuration Guide
- 28-Cluster Configuration Guide
- 29-PoE-PoE Profile Configuration Guide
- 30-UDP Helper Configuration Guide
- 31-SNMP-RMON Configuration Guide
- 32-NTP Configuration Guide
- 33-SSH Configuration Guide
- 34-FTP and TFTP Configuration Guide
- 35-Information Center Configuration Guide
- 36-VLAN-VPN Configuration Guide
- 37-HWPing Configuration Guide
- 38-DNS Configuration Guide
- 39-Access Management Configuration Guide
- 40-Web Authentication Configuration Guide
- 41-IPv6 Management Configuration Guide
- 42-Smart link - Monitor Link Configuration Guide
- 43-VLAN Mapping Configuration Guide
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 23-ACL Configuration Guide | 107.43 KB |
Networking and Configuration Requirements
Networking and Configuration Requirements
Configuring Ethernet Frame Header ACLs
Networking and Configuration Requirements
Networking and Configuration Requirements
Configuring Basic ACLs
Basic ACLs filter packets based on only source IP address.
The numbers of basic ACLs range from 2000 to 2999.
Network Diagram
Figure 1-1 Network diagram for basic ACL configuration
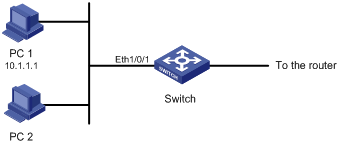
Networking and Configuration Requirements
PC 1 and PC 2 connect to the switch through Ethernet 1/0/1 (assuming that the switch is an S3600 one). PC 1’s IP address is 10.1.1.1. Apply an ACL on Ethernet 1/0/1 to deny packets with the source IP address of 10.1.1.1 from 8:00 to 18:00 everyday.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration Procedure
# Define a periodic time range that is from 8:00 to 18:00 everyday.
<H3C> system-view
[H3C] time-range test 8:00 to 18:00 daily
# Define basic ACL 2000 to filter packets with the source IP address of 10.1.1.1.
[H3C] acl number 2000
[H3C-acl-basic-2000] rule 1 deny source 10.1.1.1 0 time-range test
[H3C-acl-basic-2000] quit
# Apply ACL 2000 to Ethernet 1/0/1.
[H3C] interface Ethernet 1/0/1
[H3C-Ethernet1/0/1] packet-filter inbound ip-group 2000
Complete Configuration
#
acl number 2000
rule 1 deny source 10.1.1.1 0 time-range test
#
interface Ethernet1/0/1
packet-filter inbound ip-group 2000 rule 1
#
time-range test 08:00 to 18:00 daily
#
Precautions
l If a packet matches multiple ACL rules at the same time and some actions of the rules conflict, the last assigned rule takes effective.
l When applying multiple rules, you are recommended to apply rules in the ascending order of their mask ranges and apply rues with the same mask range at the same time. This is to ensure that the actual operation of the rules is consistent with the requirements.
l Some functions and protocols configured on the device may occupy ACL rule resources. The actual occupation varies with functions and protocols.
Configuring Advanced ACLs
Advanced ACLs filter packets based on Layer 3 and Layer 4 header information such as the source and destination IP addresses, type of the protocols carried by IP, protocol-specific features (such as TCP or UDP source port and destination port, ICMP message type and message code).
The numbers of advanced ACLs range from 3000 to 3999.
Network Diagram
Figure 1-2 Network diagram for advanced ACL configuration
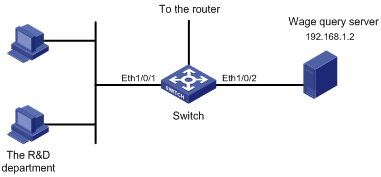
Networking and Configuration Requirements
Different departments of an enterprise are interconnected through a switch (assuming that the switch is an S3600 one).The IP address of the wage query server is 192.168.1.2. The R&D department is connected to Ethernet 1/0/1 of the switch. Apply an advanced ACL on the interface to deny access requests that are sourced from the R&D department and destined for the wage server during working hours (8:00 to 18:00).
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration Procedure
# Define a periodic time range that is from 8:00 to 18:00 on working days.
<H3C> system-view
[H3C] time-range test 8:00 to 18:00 working-day
# Define advanced ACL 3000 to filter packets destined for the wage query server.
[H3C] acl number 3000
[H3C-acl-adv-3000] rule 1 deny ip destination 192.168.1.2 0 time-range test
[H3C-acl-adv-3000] quit
# Apply ACL 3000 to Ethernet 1/0/1.
[H3C] interface Ethernet 1/0/1
[H3C-Ethernet1/0/1] packet-filter inbound ip-group 3000
Complete Configuration
#
acl number 3000
rule 1 deny IP destination 192.168.1.2 0 time-range test
#
interface Ethernet1/0/1
packet-filter inbound ip-group 3000 rule 1
#
time-range test 08:00 to 18:00 working-day
#
Precautions
l ACL 3998 and ACL 3999 are reserved for cluster management.
l If a packet matches multiple ACL rules at the same time and some actions of the rules conflict, the last assigned rule takes effective.
l For an advanced ACL applied to a port, if a rule defines the TCP/UDP port information, the operator argument can only be eq.
l When applying multiple rules, you are recommended to apply rules in the ascending order of their mask ranges and apply rues with the same mask range at the same time. This is to ensure that the actual operation of the rules is consistent with the requirements.
l Some functions and protocols configured on the device may occupy ACL rule resources. The actual occupation varies with functions and protocols.
Configuring Ethernet Frame Header ACLs
Ethernet frame header ACLs filter packets based on Layer 2 header information such as source and destination MAC addresses, 802.1p priority and type of the Layer 2 protocol.
The numbers of Ethernet frame header ACLs range from 4000 to 4999.
Network Diagram
Figure 1-3 Network diagram for Ethernet frame header ACL configuration
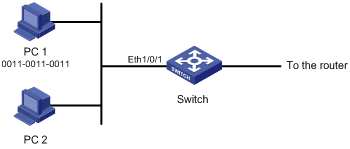
Networking and Configuration Requirements
PC 1 and PC 2 connect to the switch through Ethernet 1/0/1 (assuming that the switch is an S3600 one). PC 1’s MAC address is 0011-0011-0011. Apply an Ethernet frame header ACL on the interface to filter packets with the source MAC address of 0011-0011-0011 and the destination MAC address of 0011-0011-0012 from 8:00 to 18:00 everyday.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration Procedure
# Define a periodic time range that is from 8:00 to 18:00 everyday.
<H3C> system-view
[H3C] time-range test 8:00 to 18:00 daily
# Define ACL 4000 to filter packets with the source MAC address of 0011-0011-0011 and the destination MAC address of 0011-0011-0012.
[H3C] acl number 4000
[H3C-acl-ethernetframe-4000] rule 1 deny source 0011-0011-0011 ffff-ffff-ffff dest 0011-0011-0012 ffff-ffff-ffff time-range test
[H3C-acl-ethernetframe-4000] quit
# Apply ACL 4000 to Ethernet 1/0/1.
[H3C] interface Ethernet 1/0/1
[H3C-Ethernet1/0/1] packet-filter inbound link-group 4000
Complete Configuration
#
acl number 4000
rule 1 deny source 0011-0011-0011 ffff-ffff-ffff dest 0011-0011-0012 ffff-ffff-ffff time-range test
#
interface Ethernet1/0/1
packet-filter inbound link-group 4000 rule 1
#
time-range test 08:00 to 18:00 daily
#
Precautions
l If a packet matches multiple ACL rules at the same time and some actions of the rules conflict, the last assigned rule takes effective. For an Ethernet frame header ACL applied to a port, you cannot configure the format-type argument as 802.3/802.2, 802.3, ether_ii or snap.
l When applying multiple rules, you are recommended to apply rules in the ascending order of their mask ranges and apply rues with the same mask range at the same time. This is to ensure that the actual operation of the rules is consistent with the requirements.
l Some functions and protocols configured on the device may occupy ACL rule resources. The actual occupation varies with functions and protocols.
Configuring User-Defined ACLs
A user-defined ACL filters packets by comparing the strings retrieved from the packets with specified strings. It defines the byte it begins to perform the “and” operation with the mask on the basis of packet headers.
The numbers of user-defined ACLs range from 5000 to 5999.
Network Diagram
Figure 1-4 Network diagram for user-defined ACL configuration
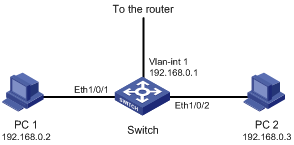
Networking and Configuration Requirements
l PC 1 and PC 2 are connected to the switch through Ethernet 1/0/1 and Ethernet 1/0/2 respectively (assuming that the switch is an S3600 one). The IP addresses of PC 1 and PC 2 are 192.168.0.2 and 192.168.0.3.
l PC 1 and PC 2 belong to VLAN 1 and access the Internet through the same gateway, which has an IP address of 192.168.0.1 (the IP address of VLAN-interface 1).
Configure a user-defined ACL to deny all ARP packets from PC 1 that use the gateway IP address as the source address from 8:00 to 18:00 everyday.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration Procedure
# Define a periodic time range that is from 8:00 to 18:00 everyday.
<H3C> system-view
[H3C] time-range test 8:00 to 18:00 daily
# Define ACL 5000 to deny any ARP packet whose source IP address is 192.168.0.1 from 8:00 to 18:00 everyday (provided that VLAN-VPN is not enabled on any port).In the ACL rule, 0806 is the ARP protocol number, 16 is the protocol type field offset of the internally processed Ethernet frame, c0a80001 is the hexadecimal form of 192.168.0.1, and 32 is the source IP address field offset of the internally processed ARP packet.
[H3C] acl number 5000
[H3C-acl-user-5000] rule 1 deny 0806 ffff 16 c0a80001 ffffffff 32 time-range test
# Apply ACL 5000 to Ethernet 1/0/1.
[H3C] interface Ethernet 1/0/1
[H3C-Ethernet1/0/1] packet-filter inbound user-group 5000
Complete Configuration
#
acl number 5000
rule 1 deny 0806 ffff 16 c0a80001 ffffffff 32 time-range test
#
interface Ethernet1/0/1
packet-filter inbound user-group 5000 rule 1
#
time-range test 08:00 to 18:00 daily
#
Precautions
l Some functions and protocols configured on the device may occupy ACL rule resources. The actual occupation varies with functions and protocols.
l For an S3600 series Ethernet switch, if VLAN-VPN is not enabled, each packet in the switch carries one VLAN tag which is 4 bytes long; If VLAN-VPN is enabled on a port, each packet in the switch carries two VLAN tags, which are 8 bytes long. Pay attention to the above information when configuring a rule that matches specific fields of packets.
l For an S5600 series Ethernet switch, each packet in the switch carries two VLAN tags, which are 8 bytes long. Pay attention to the above information when configuring a rule that matches specific fields of packets.
l The command for defining a user-defined ACL rule is rule [ rule-id ] { deny | permit } [ rule-string rule-mask offset ] &<1-8> [ time-range time-name ], where, rule-id refers to the ACL number, rule-string the user-defined rule string, rule-mask the user-defined rule mask, and offset the rule mask offset.
l If you specify multiple rule strings in an ACL rule, the valid length of the rule mask is 128 hexadecimal numerals (64 bytes).For example, assume that you specify a rule string of aa and set its offset to 2. If you continue to specify a rule string of bb, its offset must be in the range from 3 to 65 bytes. If you set the offset of the rule string aa to 3, the offset of the rule string bb must be in the range of 4 to 66 bytes, and so on. Note that the offset of the rule string bb cannot be greater than 79 bytes.
l As shown in Table 1-1, the hardware rule of the S3600/S5600 series logically divides the rule mask offset of a user-defined string into multiple offset units, each of which is 4-byte long. Available offset units fall into eight groups, which are numbered from Offset1 to Offset8
l With the S3600/S5600 series, for a user-defined ACL to be assigned successfully, the maximum length of a user-defined rule string is 32 bytes. The string may or may not contain spaces, and can occupy up to eight mask offset units. Besides, any two offset units cannot belong to the same offset group.
Table 1-1 Offset units of a user-defined rule string
|
Offset unit |
|||||||
|
Offset1 |
Offset2 |
Offset3 |
Offset4 |
Offset5 |
Offset6 |
Offset7 |
Offset8 |
|
0 to 3 |
4 to 7 |
8 to 11 |
12 to 15 |
16 to 19 |
20 to 23 |
24 to 27 |
28 to 31 |
|
2 to 5 |
6 to 9 |
10 to 13 |
14 to 17 |
18 to 21 |
22 to 25 |
26 to 29 |
30 to 33 |
|
6 to 9 |
10 to 13 |
14 to 17 |
18 to 21 |
22 to 25 |
26 to 29 |
30 to 33 |
34 to 37 |
|
12 to 15 |
16 to 19 |
20 to 23 |
24 to 27 |
28 to 31 |
32 to 35 |
36 to 39 |
40 to 43 |
|
20 to 23 |
24 to 27 |
28 to 31 |
32 to 35 |
36 to 39 |
40 to 43 |
44 to 47 |
48 to 51 |
|
30 to 33 |
34 to 37 |
38 to 41 |
42 to 45 |
46 to 49 |
50 to 53 |
54 to 57 |
58 to 61 |
|
42 to 45 |
46 to 49 |
50 to 53 |
54 to 57 |
58 to 61 |
62 to 65 |
66 to 69 |
70 to 73 |
|
56 to 59 |
60 to 63 |
64 to 67 |
68 to 71 |
72 to 75 |
76 to 79 |
0 to 3 |
4 to 7 |
l For example, assuming that you configure ACL 5000, specifying a 32-byte rule string, a rule mask of all Fs, and an offset of 4 and then apply the ACL to Ethernet 1/0/1. In this case, the 32-byte rule string occupies eight offset units: 4 to 7 (Offset2), 8 to 11 (Offset3), 12 to 15 (Offset4), 16 to 19 (Offset5), 20 to 23 (Offset1), 24 to 27 (Offset7), 28 to 31 (Offset8), and 32 to 35 (Offset6), as shown in Table 1-1. The rule can be assigned successfully.
l If you configure ACL 5001, specifying a 32-byte rule string, a rule mask of all Fs, and an offset of 24 and then apply the ACL to Ethernet 1/0/1: In this case, the 32-byte rule string does not comply with the rule that a user-defined rule string can contain up to eight mask offset units and any two offset units cannot belong to the same offset. The ACL cannot be assigned.
Table 1-2 The common protocol types and their offsets are listed in the following table.
|
Protocol type |
Protocol number (hexadecimal) |
Offset for S3600 series Ethernet switches with VLAN-VPN function disabled |
Offset for S3600 series Ethernet switches with VLAN-VPN function enabled |
Offset for S5600 series Ethernet switches |
|
ARP |
0x0806 |
16 |
20 |
20 |
|
RARP |
0x8035 |
16 |
20 |
20 |
|
IP |
0x0800 |
16 |
20 |
20 |
|
IPX |
0x8137 |
16 |
20 |
20 |
|
AppleTalk |
0x809B |
16 |
20 |
20 |
|
ICMP |
0x01 |
27 |
31 |
31 |
|
IGMP |
0x02 |
27 |
31 |
31 |
|
TCP |
0x06 |
27 |
31 |
31 |
