- Table of Contents
-
- H3C Low-End Ethernet Switches Configuration Guide(V1.01)
- 01-Login Configuration Guide
- 02-VLAN Configuration Guide
- 03-IP Address Configuration Guide
- 04-Voice VLAN Configuration Guide
- 05-GVRP Configuration Guide
- 06-Ethernet Interface Basic Configuration Guide
- 07-Link Aggregation Configuration Guide
- 08-Port Isolation Configuration Guide
- 09-Port Security Configuration Guide
- 10-Port Binding Configuration Guide
- 11-MAC Address Table Management Configuration Guide
- 12-DLDP Configuration Guide
- 13-Auto Detect Configuration Guide
- 14-MSTP Configuration Guide
- 15-Routing Configuration Guide
- 16-Multicast Configuration Guide
- 17-802.1x Configuration Guide
- 18-AAA Configuration Guide
- 19-MAC Authentication Configuration Guide
- 20-VRRP Configuration Guide
- 21-ARP Configuration Guide
- 22-DHCP Configuration Guide
- 23-ACL Configuration Guide
- 24-QoS-QoS Profile Configuration Guide
- 25-Web Cache Redirection Configuration Guide
- 26-Mirroring Configuration Guide
- 27-IRF Configuration Guide
- 28-Cluster Configuration Guide
- 29-PoE-PoE Profile Configuration Guide
- 30-UDP Helper Configuration Guide
- 31-SNMP-RMON Configuration Guide
- 32-NTP Configuration Guide
- 33-SSH Configuration Guide
- 34-FTP and TFTP Configuration Guide
- 35-Information Center Configuration Guide
- 36-VLAN-VPN Configuration Guide
- 37-HWPing Configuration Guide
- 38-DNS Configuration Guide
- 39-Access Management Configuration Guide
- 40-Web Authentication Configuration Guide
- 41-IPv6 Management Configuration Guide
- 42-Smart link - Monitor Link Configuration Guide
- 43-VLAN Mapping Configuration Guide
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 17-802.1x Configuration Guide | 91.77 KB |
Table of Contents
Configuring 802.1x Access Control
Networking and Configuration Requirements
Configuring Quick EAD Deployment
Networking and Configuration Requirements
![]()
The following configurations involve most AAA/RADIUS configuration commands. Refer to AAA Operation for information about the commands. Configurations on the user host and the RADIUS servers are omitted.
Configuring 802.1x Access Control
As a port-based access control protocol, 802.1x authenticates and controls access of users at the port level. A user host connected to an 802.1x-enabled port of an access control device can access the resources on the LAN only after passing authentication.
Network Diagram
Figure 1-1 Network diagram for configuring 802.1x access control
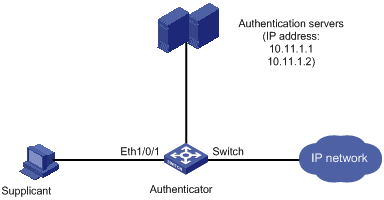
Networking and Configuration Requirements
l The switch authenticate supplicants on the port Ethernet 1/0/1 to control their access to the Internet by using the MAC-based access control method. That is, each user of a port must be authenticated separately, and when an authenticated user goes offline, no other users are affected.
l All supplicants belong to the default domain named aabbcc.net, which can accommodate up to 30 users. When authenticating a supplicant, the switch tries the RADIUS scheme first and then the local scheme if the RADIUS server is not available. A supplicant is disconnected by force if accounting fails. In addition, the username of a supplicant is not suffixed with the domain name. A connection is terminated if the total size of the data passes through it during a period of 20 minutes is less than 2000 bytes.
l The switch is connected to a server group comprising of two RADIUS servers whose IP addresses are 10.11.1.1 and 10.11.1.2 respectively. The former operates as the primary authentication server and the secondary accounting server, while the latter operates as the secondary authentication server and the primary accounting server. The shared key for authentication message exchange is name, and that for accounting message exchange is money. If the switch sends a packet to the RADIUS server but receives no response in 5 seconds, it retransmits the packet for up to 5 times. The switch sends real-time accounting packets at an interval of 15 minutes. A username is sent to the RADIUS server with the domain name truncated.
l The username and password for local 802.1x authentication are localuser and localpass (in plain text) respectively. The idle disconnecting function is enabled.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-SI/EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-C-SI series S3100-T-SI series |
Release 0011, Release 2102, Release 2107 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration Procedure
# Enable 802.1x globally.
<Sysname> system-view
[Sysname] dot1x
# Enable 802.1x on Ethernet 1/0/1.
[Sysname] dot1x interface Ethernet 1/0/1
# Set the access control method to MAC-based. This operation can be omitted because MAC-based is the default.
[Sysname] dot1x port-method macbased interface Ethernet 1/0/1
# Create a RADIUS scheme named radius1 and enter the RADIUS scheme view.
[Sysname] radius scheme radius1
# Assign IP addresses to the primary authentication and accounting RADIUS servers.
[Sysname-radius-radius1] primary authentication 10.11.1.1
[Sysname-radius-radius1] primary accounting 10.11.1.2
# Assign IP addresses to the secondary authentication and accounting RADIUS servers.
[Sysname-radius-radius1] secondary authentication 10.11.1.2
[Sysname-radius-radius1] secondary accounting 10.11.1.1
# Set the shared key for message exchange between the switch and the RADIUS authentication server.
[Sysname -radius-radius1] key authentication name
# Set the shared key for message exchange between the switch and the RADIUS accounting server.
[Sysname-radius-radius1] key accounting money
# Set the interval and the number of packet transmission attempts for the switch to send packets to the RADIUS server.
[Sysname-radius-radius1] timer 5
[Sysname-radius-radius1] retry 5
# Set the interval for the switch to send real-time accounting packets to the RADIUS server.
[Sysname-radius-radius1] timer realtime-accounting 15
# Configure the switch to send a username without the domain name to the RADIUS server.
[Sysname-radius-radius1] user-name-format without-domain
[Sysname-radius-radius1] quit
# Create a domain named aabbcc.net and enter its view.
[Sysname] domain aabbcc.net
# Specify radius1 as the RADIUS scheme of the user domain, and the local authentication scheme as the backup scheme when the RADIUS server is not available.
[Sysname-isp-aabbcc.net] scheme radius-scheme radius1 local
# Specify the maximum number of users of the user domain to 30.
[Sysname-isp-aabbcc.net] access-limit enable 30
# Enable the idle disconnecting function and set the related parameters.
[Sysname-isp-aabbcc.net] idle-cut enable 20 2000
[Sysname-isp-aabbcc.net] quit
# Set aabbcc.net as the default user domain.
[Sysname] domain default enable aabbcc.net
# Create a local user.
[Sysname] local-user localuser
[Sysname-luser-localuser] service-type lan-access
[Sysname-luser-localuser] password simple localpass
Complete Configuration
#
domain default enable aabbcc.net
#
dot1x
#
interface Ethernet1/0/1
dot1x
#
radius scheme system
radius scheme radius1
server-type standard
primary authentication 10.11.1.1
primary accounting 10.11.1.2
secondary authentication 10.11.1.2
secondary accounting 10.11.1.1
key authentication name
key accounting money
timer realtime-accounting 15
timer response-timeout 5
retry 5
user-name-format without-domain
#
domain aabbcc.net
scheme radius-scheme radius1 local
access-limit enable 30
idle-cut enable 20 2000
domain system
#
local-user localuser
password simple localpass
service-type lan-access
#
Precautions
1) 802.1x and the maximum number of MAC addresses that a port can learn are mutually exclusive. You cannot configure both of them on a port at the same time.
2) You can neither add an 802.1x-enabled port into an aggregation group nor enable 802.1x on a port which is a member of an aggregation group.
3) When a port uses the MAC-based access control method, users are authenticated individually and when a user goes offline, no other users are affected. When a port uses the port-based access control method, once a user passes authentication, all users on the port can access the network. But if the user gets offline, the port will be disabled and will log off all the other users.
4) If you use the dot1x port-method command to change the port access method, all online users will be logged off by force.
5) Handshake packet transmission needs the support of the H3C private client.
Configuring Quick EAD Deployment
As an integrated security scheme, an endpoint admission defense (EAD) scheme can improve the overall defense capability of a network. However, EAD deployment brings much workload in actual applications. To solve this problem, you can use 802.1x functions to implement fast deployment of EAD scheme.
To address the issue, the H3C series switches enable the user’s quick redirection to EAD client download server with 802.1x authentication, easing the work of EAD client deployment.
Network diagram
Figure 1-2 Network diagram for quick EAD deployment
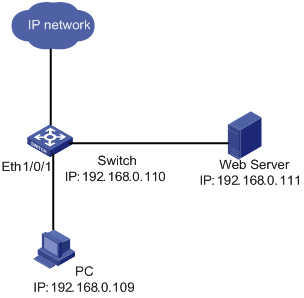
Networking and Configuration Requirements
A user connects to the switch directly. The switch connects to the Web server and the Internet. The user will be redirected to the Web server to download the authentication client and upgrade software when accessing the Internet through IE before passing authentication. After passing authentication, the user can access the Internet.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration procedure
![]()
Before enabling quick EAD deployment, be sure that:
l The Web server is configured properly.
l The default gateway of the user’s PC is configured as the IP address of the connected VLAN interface on the switch.
# Configure the URL for HTTP redirection.
<Sysname> system-view
[Sysname] dot1x url http://192.168.0.111
# Configure a free IP range.
[Sysname] dot1x free-ip 192.168.0.111 24
# Set the ACL timer to 10 minutes.
[Sysname] dot1x timer acl-timeout 10
# Enable dot1x globally.
[Sysname] dot1x
# Enable dot1x for Ethernet 1/0/1.
[Sysname] dot1x interface Ethernet 1/0/1
Complete Configuration
#
dot1x
dot1x url http://192.168.0.111
dot1x free-ip 192.168.0.0 255.255.255.0
dot1x timer acl-timeout 10
#
interface Ethernet1/0/1
dot1x
#
Precautions
1) You must configure the URL for HTTP redirection before configuring a free IP range. A URL must start with http:// and the segment where the URL resides must be in the free IP range. Otherwise, the redirection function cannot take effect.
2) You must disable the DHCP-triggered authentication function of 802.1x before configuring a free IP range.
3) The quick EAD deployment function applies to only ports with the access control mode set to auto through the dot1x port-control command.
4) At present, 802.1x is the only access approach that supports quick EAD deployment.
5) Currently, the quick EAD deployment function does not support port security. The configured free IP range cannot take effect if you enable port security.
