- Table of Contents
-
- H3C Low-End Ethernet Switches Configuration Guide(V1.01)
- 01-Login Configuration Guide
- 02-VLAN Configuration Guide
- 03-IP Address Configuration Guide
- 04-Voice VLAN Configuration Guide
- 05-GVRP Configuration Guide
- 06-Ethernet Interface Basic Configuration Guide
- 07-Link Aggregation Configuration Guide
- 08-Port Isolation Configuration Guide
- 09-Port Security Configuration Guide
- 10-Port Binding Configuration Guide
- 11-MAC Address Table Management Configuration Guide
- 12-DLDP Configuration Guide
- 13-Auto Detect Configuration Guide
- 14-MSTP Configuration Guide
- 15-Routing Configuration Guide
- 16-Multicast Configuration Guide
- 17-802.1x Configuration Guide
- 18-AAA Configuration Guide
- 19-MAC Authentication Configuration Guide
- 20-VRRP Configuration Guide
- 21-ARP Configuration Guide
- 22-DHCP Configuration Guide
- 23-ACL Configuration Guide
- 24-QoS-QoS Profile Configuration Guide
- 25-Web Cache Redirection Configuration Guide
- 26-Mirroring Configuration Guide
- 27-IRF Configuration Guide
- 28-Cluster Configuration Guide
- 29-PoE-PoE Profile Configuration Guide
- 30-UDP Helper Configuration Guide
- 31-SNMP-RMON Configuration Guide
- 32-NTP Configuration Guide
- 33-SSH Configuration Guide
- 34-FTP and TFTP Configuration Guide
- 35-Information Center Configuration Guide
- 36-VLAN-VPN Configuration Guide
- 37-HWPing Configuration Guide
- 38-DNS Configuration Guide
- 39-Access Management Configuration Guide
- 40-Web Authentication Configuration Guide
- 41-IPv6 Management Configuration Guide
- 42-Smart link - Monitor Link Configuration Guide
- 43-VLAN Mapping Configuration Guide
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-Login Configuration Guide | 86.1 KB |
Logging In from the Console Port
Networking and Configuration Requirements
Networking and Configuration Requirements
Configuring Login Access Control
Networking and Configuration Requirements
![]()
Unless otherwise specified, all the switches used in the following configuration examples and configuration procedures are S3600 series switches (release 1510).
Logging In from the Console Port
You can log in locally from the console port to configure and maintain your switch, including configuring other login modes. The default login mode on the S3600 series is local console login.
Network Diagram
Figure 1-1 Logging in from the console port to configure Telnet login

Networking and Configuration Requirements
As shown in Figure 1-1, use a console cable to connect the serial port of your PC/terminal to the console port of the switch. Log into the switch from the AUX user interface on the console port to configure Telnet login. The current user level is manage level (level 3).
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-SI/EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-C-SI series S3100-T-SI series |
Release 0011, Release 2102, Release 2107 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration Procedure
l Configure common attributes for Telnet login
# Set the level of commands accessible to the VTY 0 user to 2.
[Sysname] user-interface vty 0
[Sysname-ui-vty0] user privilege level 2
# Enable the Telnet service on VTY 0.
[Sysname-ui-vty0] protocol inbound telnet
# Set the number of lines that can be viewed on the screen of the VTY 0 user to 30.
[Sysname-ui-vty0] screen-length 30
# Set the history command buffer size to 20 for VTY 0.
[Sysname-ui-vty0] history-command max-size 20
# Set the idle-timeout time of VTY 0 to 6 minutes.
[Sysname-ui-vty0] idle-timeout 6
l Configure an authentication mode for Telnet login
The following three authentication modes are available for Telnet login: none, password, and scheme.
The configuration procedures for the three authentication modes are described below:
1) Configure not to authenticate Telnet users on VTY 0.
[Sysname] user-interface vty 0
[Sysname-ui-vty0] authentication-mode none
2) Configure password authentication for Telnet login on VTY 0, and set the password to 123456 in plain text.
[Sysname] user-interface vty 0
[Sysname-ui-vty0] authentication-mode password
[Sysname-ui-vty0] set authentication password simple 123456
3) Configure local authentication in scheme mode for login users.
# Create a local user named guest and enter local user view.
[Sysname] local-user guest
# Set the authentication password to 123456 in plain text.
[Sysname-luser-guest] password simple 123456
# Set the service type to Telnet and the user level to 2 for the user guest.
[Sysname-luser-guest] service-type telnet level 2
[Sysname-luser-guest] quit
# Enter VTY 0 user interface view.
[Sysname] user-interface vty 0
# Set the authentication mode to scheme for Telnet login on VTY 0.
[Sysname-ui-vty0] authentication-mode scheme
[Sysname-ui-vty0] quit
# Specify the domain system as the default domain, and configure the domain to adopt local authentication in scheme mode.
[Sysname] domain default enable system
[Sysname] domain system
[Sysname-isp-system] scheme local
Complete Configuration
l Telnet login configuration with the authentication mode being none
user-interface vty 0
authentication-mode none
user privilege level 2
history-command max-size 20
idle-timeout 6 0
screen-length 30
protocol inbound telnet
l Telnet login configuration with the authentication mode being password
user-interface vty 0
user privilege level 2
set authentication password simple 123456
history-command max-size 20
idle-timeout 6 0
screen-length 30
protocol inbound telnet
l Telnet login configuration with the authentication mode being scheme
#
domain system
#
local-user guest
password simple 123456
level 2
#
user-interface vty 0
authentication-mode scheme
user privilege level 2
history-command max-size 20
idle-timeout 6 0
screen-length 30
protocol inbound telnet
Precautions
Logging In Through Telnet
You can telnet to your switch to manage and maintain it remotely.
Network Diagram
Figure 1-2 Telneting to the switch to configure console login
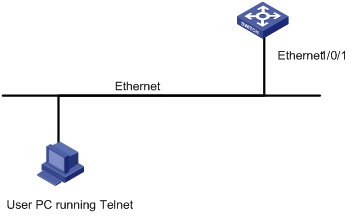
Networking and Configuration Requirements
As shown in Figure 1-2, telnet to the switch to configure console login. The current user level is manage level (level 3).
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-SI/EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-C-SI series S3100-T-SI series |
Release 0011, Release 2102, Release 2107 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration Procedure
l Common configuration for console login
# Specify the level of commands accessible to the AUX 0 user interface to 2.
[Sysname] user-interface aux 0
[Sysname-ui-aux0] user privilege level 2
# Set the baud rate of the console port to 19200 bps.
[Sysname-ui-aux0] speed 19200
# Set the number of lines that can be viewed on the screen of the AUX 0 user to 30.
[Sysname-ui-aux0] screen-length 30
# Set the history command buffer size to 20 for AUX 0.
[Sysname-ui-aux0] history-command max-size 20
# Set the idle-timeout time of AUX 0 to 6 minutes.
[Sysname-ui-aux0] idle-timeout 6
l Configure the authentication mode for console login
The following three authentication modes are available for console login: none, password, and scheme. The configuration procedures for the three authentication modes are described below:
1) Configure not to authenticate console login users.
[Sysname] user-interface aux 0
[Sysname-ui-aux0] authentication-mode none
2) Configure password authentication for console login, and set the password to 123456 in plain text.
[Sysname] user-interface aux 0
[Sysname-ui-aux0] authentication-mode password
[Sysname-ui-aux0] set authentication password simple 123456
3) Configure local authentication in scheme mode for console login.
# Create a local user named guest and enter local user view.
[Sysname] local-user guest
# Set the authentication password to 123456 in plain text.
[Sysname-luser-guest] password simple 123456
# Set the service type to Terminal and the user level to 2 for the user guest.
[Sysname-luser-guest] service-type terminal level 2
[Sysname-luser-guest] quit
# Enter AUX 0 user interface view.
[Sysname] user-interface aux 0
# Set the authentication mode to scheme for console login.
[Sysname-ui-aux0] authentication-mode scheme
Complete Configuration
l Console login configuration with the authentication mode being none
#
user-interface aux 0
user privilege level 2
history-command max-size 20
idle-timeout 6 0
speed 19200
screen-length 30
l Console login configuration with the authentication mode being password
#
user-interface aux 0
authentication-mode password
user privilege level 2
set authentication password simple 123456
history-command max-size 20
idle-timeout 6 0
speed 19200
screen-length 30
l Console login configuration with the authentication mode being scheme
#
local-user guest
password simple 123456
service-type terminal
level 2
#
user-interface aux 0
authentication-mode scheme
user privilege level 2
history-command max-size 20
idle-timeout 6 0
speed 19200
screen-length 30
Precautions
Configuring Login Access Control
Network Diagram
Figure 1-3 Network diagram for login access control
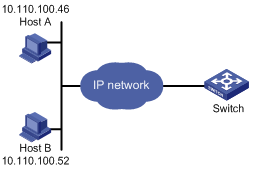
Networking and Configuration Requirements
As shown in Figure 1-3, configure the switch to allow only Telnet/SNMP/WEB users at 10.110.100.52 and 10.110.100.46 to log in.
Applicable Product Matrix
|
Product series |
Software version |
Hardware version |
|
S5600 series |
Release 1510, Release1602 |
All versions |
|
S5100-SI/EI series |
Release 2200, Release2201 |
All versions |
|
S3600-SI/EI series |
Release 1510, Release1602 |
All versions |
|
S3100-EI series |
Release 2104, Release 2107 |
All versions |
|
S3100-C-SI series S3100-T-SI series |
Release 0011, Release 2102, Release 2107 |
All versions |
|
S3100-52P |
Release 1500, Release 1602 |
S3100-52P |
Configuration Procedure
# Create basic ACL 2000 and enter basic ACL view.
[Sysname] acl number 2000 match-order config
[Sysname-acl-basic-2000]
# Define ACL rules to allow only Telnet/SNMP/WEB users at 10.110.100.52 and 10.110.100.46 to log into the switch.
[Sysname-acl-basic-2000] rule 1 permit source 10.110.100.52 0
[Sysname-acl-basic-2000] rule 2 permit source 10.110.100.46 0
[Sysname-acl-basic-2000] rule 3 deny source any
[Sysname-acl-basic-2000] quit
# Reference ACL 2000 to control Telnet login by source IP address.
[Sysname] user-interface vty 0 4
[Sysname-ui-vty0-4] acl 2000 inbound
# Reference ACL 2000 to control SNMP login by source IP address.
[Sysname] snmp-agent community read aaa acl 2000
[Sysname] snmp-agent group v2c groupa acl 2000
[Sysname] snmp-agent usm-user v2c usera groupa acl 2000
# Reference ACL 2000 to control WEB login by source IP address.
[Sysname] ip http acl 2000
Complete Configuration
l Configuration for Telnet login control by source IP address
#
acl number 2000
rule 1 permit source 10.110.100.52 0
rule 2 permit source 10.110.100.46 0
rule 3 deny
#
user-interface vty 0 4
acl 2000 inbound
l Configuration for SNMP login control by source IP address
#
acl number 2000
rule 1 permit source 10.110.100.52 0
rule 2 permit source 10.110.100.46 0
rule 3 deny
#
snmp-agent community read aaa acl 2000
snmp-agent group v2c groupa acl 2000
snmp-agent usm-user v2c usera groupa acl 2000
l Configuration for WEB login control by source IP address
#
ip http acl 2000
#
acl number 2000
rule 1 permit source 10.110.100.52 0
rule 2 permit source 10.110.100.46 0
rule 3 deny
Precautions
None
