- Table of Contents
-
- 02-WLAN Configuration Guide
- 00-Preface
- 01-WLAN Interface Configuration
- 02-WLAN Service Configuration
- 03-WLAN Security Configuration
- 04-WLAN Roaming Configuration
- 05-WLAN RRM Configuration
- 06-WLAN IDS Configuration
- 07-WLAN QoS Configuration
- 08-WLAN Mesh Link Configuration
- 09-WLAN Optimization Configuration
- 10-Advanced WLAN Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 04-WLAN Roaming Configuration | 356.20 KB |
Contents
Configuring an IACTP mobility group
Displaying and maintaining WLAN roaming
WLAN roaming configuration examples
Intra-AC roaming configuration example
Inter-AC roaming configuration example
WLAN roaming overview
Inter AC Tunneling Protocol (IACTP) is a proprietary protocol of H3C which defines how access controllers (ACs) communicate with each other. Based on the standard TCP client/server model, this protocol generically encapsulates and transports communications securely between ACs.
You can use IACTP to create and maintain AC groups, termed mobility groups, which can include up to 8 ACs. IACTP provides a secure control tunnel for applications such as roaming that allow sharing and exchanging messages. IACTP can be used with either IPv4 or with IPv6.
When a station first associates with an AC in a mobility group, that AC becomes the station's Home-AC (HA). The connection request goes through 802.1X authentication followed by 11 Key exchange, and the station information is then synchronized across the other ACs in the mobility group.
When the station roams to another AC in the mobility group (a Foreign-AC (FA)), the HA information is used to fast-forward station authentication by skipping 802.1X authentication and performing only 802.11 key exchange. This method facilitates seamless roaming within a mobility group.
Terminology
· HA—The AC to which a wireless station is connected by associating with an AP for the first time is the HA of the station.
· FA—An AC that is other than the HA and to which a station is currently connected is an FA of the station.
· Fast-roam capable station—A wireless station that associates to an AC in the mobility-group and supports fast roaming (only key caching is supported).
· Roam-out station—A wireless station that has associated with an AC other than the HA in the mobility-group is a roam-out station at its HA.
· Roam-in station—A wireless station that has associated with an AC other than the HA in the mobility-group is a roam-in station at the FA.
· Intra-AC roaming—A procedure where a wireless station roams from one AP to another AP, which are connected to the same AC.
· Inter-AC roaming—A procedure where a wireless station roams from one AP to another AP, which are connected to different ACs.
· Inter-AC fast roaming capability—If a station uses 802.1X (RSN) authentication through negotiation and supports key caching, this station has inter-AC fast roaming capability.
WLAN roaming topologies
WLAN Roaming topologies consist of:
· Intra-AC roaming topology
· Inter-AC roaming topology
· Intra-FA roaming topology
· Inter-FA roaming topology
· Roam-back topology
Intra-AC roaming
The figure below illustrates how a station can roam from one AP to another AP, through a connection to the same AC.
Figure 1 Intra-AC roaming
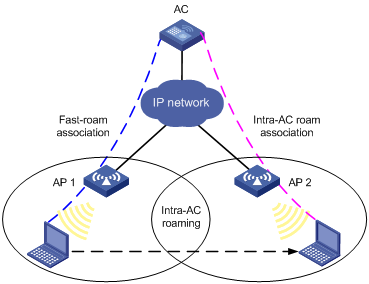
1. A station is associated with AP 1, which is connected to an AC.
2. The station disassociates with AP 1 and roams to AP 2 connected to the same AC.
3. The station is associated with AP 2 through intra-AC roam association.
Inter-AC roaming
The figure below illustrates how a station can roam from one AP to another AP, through a connection to different ACs.
Figure 2 Inter-AC roaming
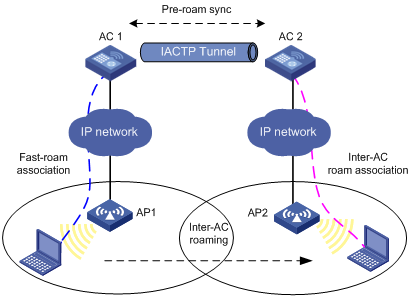
1. A station is associated with AP 1, which is connected to AC 1.
2. The station disassociates with AP 1 and roams to AP 2 connected to AC 2.
3. The station is associated with AP 2 through inter-AC roam association. Prior to inter-AC roaming, AC 1 should synchronize the station information with AC 2 through an IACTP tunnel.
Intra-FA roaming
Figure 3 Intra-FA roaming
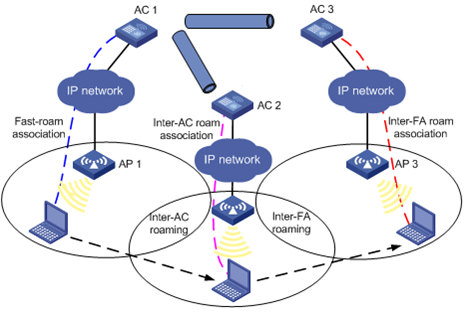
1. A station is associated with AP 1, which is connected to AC 1.
2. The station disassociates with AP 1 and roams to AP 2 connected to AC 2. Now AC 2 is the FA for the station.
3. The station is associated with AP 2 through inter-AC roam association. Prior to inter-AC roaming, AC 1 should synchronize the station information with AC 2 through an IACTP tunnel.
4. The station then disassociates with AP 2 and roams to AP 3 which is also connected to AC 2. The station is associated with AP 3 through intra-FA roam association.
Inter-FA roaming
Figure 4 Inter-FA roaming
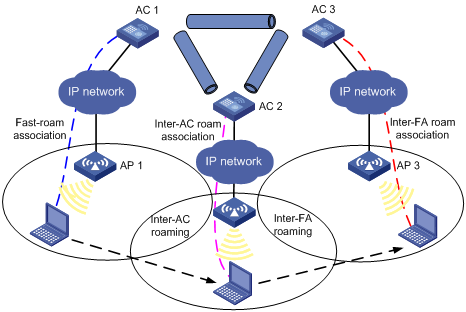
1. A station is associated with AP 1, which is connected to AC 1.
2. The station disassociates with AP 1 and roams to AP 2 connected to AC 2. Now AC 2 is the FA for the station.
3. The station is associated with AP 2 through inter-AC roam association.
4. The station then disassociates with AP 2 and roams to AP 3 which is connected to AC 3, which now is its FA. Prior to inter-AC roaming, AC 1 should synchronize the station information with AC 2 and AC 3 through IACTP tunnels.
Roam-back
Figure 5 Roam-back
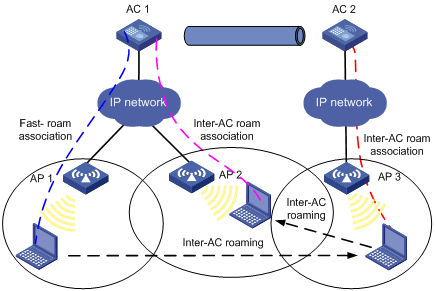
1. A station is associated with AP 1, which is connected to AC 1.
2. The station disassociates with AP 1 and roams to AP 3 connected to AC 2. Now AC 2 is the FA for the station.
3. The station is associated with AP 3 through inter-AC roam association. Prior to inter-AC roaming, AC 1 should synchronize the station information with AC 2 through an IACTP tunnel.
4. The station then disassociates with AP 3 and roams back to AP 2 or AP 1 connected to AC 1, which is its HA.
Configuring an IACTP mobility group
The IACTP service is part of the WLAN system, and can be enabled only after a mobility group and the tunnel source IP address are configured.
An IACTP mobility group includes attributes such as the mobility tunnel protocol type, source IP address, authentication mode, and member IP addresses.
To configure a mobility group and enable IACTP service for it:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a mobility group with the specified name. |
wlan mobility-group name |
ACs in the same mobility group should have the same mobility group name. |
|
3. Specify the mobility tunnel protocol type. |
mobility-tunnel { iactp | iactp6 } |
Optional. By default, the mobility tunnel protocol type is IPv4. |
|
4. Specify the tunnel source IP address. |
source { ip ipv4-address | ipv6 ipv6-address } |
Not configured by default |
|
5. Add a member. |
member { ip ipv4-address | ipv6 ipv6-address } [ vlan vlan-id-list ] |
By default, no member exists in a mobility group. Members can be added dynamically irrespective of whether IACTP service is enabled or not. |
|
6. Specify an IACTP control message integrity authentication mode. |
authentication-mode authentication-method [ cipher | simple ] authentication-key |
Optional. By default, IACTP control message integrity authentication is disabled. |
|
7. Enable the IACTP service for the group. |
mobility-group enable |
By default, IACTP service is disabled. |
|
|
NOTE: · Do not configure ACs in a mobility group to back up each other. · ACs in a mobility group must have the same user profile configurations. |
Displaying and maintaining WLAN roaming
|
Task |
Command |
Remarks |
|
Display mobility group information. |
display wlan mobility-group [ member { ip IPv4-address | ipv6 IPv6-address } ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display the roam-track information of a client on the HA. |
display wlan client roam-track mac-address mac-address [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display the WLAN client roaming information. |
display wlan client { roam-in | roam-out } [ member { ip IPv4-address | ipv6 IPv6-address } ] [ verbose ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
WLAN roaming configuration examples
Intra-AC roaming configuration example
Network requirements
As shown in Figure 6, an AC has two APs associated and all of them are in VLAN 1. A client is associated with AP 1. Configure intra-AC roaming so that the client can associate with AP 2 when roaming to AP 2.
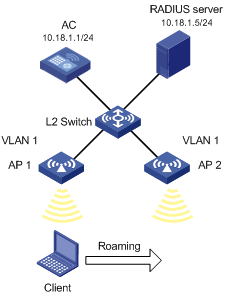
Configuration procedure
|
|
NOTE: · For wireless service configuration, see "Configuring WLAN services." A client has inter-AC fast roaming capability only if it uses 802.1X (RSN) authentication. · If you select an authentication mode involving remote authentication, you need to configure the corresponding RADIUS server. For more information, see "Configuring WLAN security." |
1. Configure the AC:
# On interface WLAN-ESS 1, configure port security mode as userlogin-secure-ext, and enable key negotiation of the 11key type.
<AC> system-view
[AC] interface wlan-ess 1
[AC-WLAN-ESS1] port-security port-mode userlogin-secure-ext
[AC-WLAN-ESS1] port-security tx-key-type 11key
# Disable the multicast trigger function and the online user handshake function.
[AC-WLAN-ESS1] undo dot1x multicast-trigger
[AC-WLAN-ESS1] undo dot1x handshake
[AC-WLAN-ESS1] quit
# Create service template 1 of crypto type, configure its SSID as intra-roam, and bind WLAN-ESS1 to intra-roam.
[AC] wlan service-template 1 crypto
[AC-wlan-st-1] ssid intra-roam
[AC-wlan-st-1] bind wlan-ess 1
# Configure the authentication method as open-system, and use the CCMP cipher suite for frame encryption.
[AC-wlan-st-1] authentication-method open-system
[AC-wlan-st-1] cipher-suite ccmp
[AC-wlan-st-1] security-ie rsn
# Enable service template 1.
[AC-wlan-st-1] service-template enable
[AC-wlan-st-1] quit
# Enable port security.
[AC] port-security enable
# Configure the 802.1X authentication method as EAP.
[AC] dot1x authentication-method eap
# Create a RADIUS scheme rad, and specify the extended RADIUS server type.
[AC] radius scheme rad
[AC-radius-rad] server-type extended
# Configure the IP addresses of the primary authentication server and accounting server as 10.18.1.5.
[AC-radius-rad] primary authentication 10.18.1.5
[AC-radius-rad] primary accounting 10.18.1.5
# Configure the shared key for RADIUS authentication/accounting packets as 12345678.
[AC-radius-rad] key authentication 12345678
[AC-radius-rad] key accounting 12345678
# Configure the source IP address of RADIUS packets sent by the AC as 10.18.1.1.
[AC-radius-rad] nas-ip 10.18.1.1
[AC-radius-rad] quit
# Create ISP domain cams and configure the ISP domain cams to use RADIUS scheme rad to implement authentication, authorization, and accounting for all types of users.
[AC] domain cams
[AC-isp-cams] authentication default radius-scheme rad
[AC-isp-cams] authorization default radius-scheme rad
[AC-isp-cams] accounting default radius-scheme rad
[AC-isp-cams] quit
#Configure the 802.1X mandatory authentication domain as cams on interface WLAN-ESS 1.
[AC] interface WLAN-ESS 1
[AC-WLAN-ESS1] dot1x mandatory-domain cams
[AC-WLAN-ESS1] quit
# Configure AP 1: Create an AP template named ap1 and its model is WA2100, and configure the serial ID of AP 1 as 210235A045B05B1236548.
[AC] wlan ap ap1 model WA2100
[AC-wlan-ap-ap1] serial-id 210235A045B05B1236548
[AC-wlan-ap-ap1] radio 1 type dot11g
# Bind service template 1 to radio 1.
[AC-wlan-ap-ap1-radio-1] service-template 1
[AC-wlan-ap-ap1-radio-1] radio enable
[AC-wlan-ap-ap1-radio-1] quit
[AC-wlan-ap-ap1] quit
# Configure AP 2: Create an AP template named ap2 and its model is WA2100, and configure the serial ID of AP 2 as 2210235A22W0076000103.
[AC] wlan ap ap2 model WA2100
[AC-wlan-ap-ap2] serial-id 210235A22W0076000103
[AC-wlan-ap-ap2] radio 1 type dot11g
# Bind service template 1 to radio 1 of AP 2 (Intra-AC roaming requires consistent SSIDs of different APs. Therefore, radio 1 of AP 2 should be bound to service template 1.).
[AC-wlan-ap-ap2-radio-1] service-template 1
[AC-wlan-ap-ap2-radio-1] radio enable
[AC-wlan-ap-ap2-radio-1] return
2. Verify the configuration:
After the client roams to AP2, use the display wlan client verbose command to display detailed client information. You should find that the AP name and BSSID fields have been changed to those of AP2. You can also use the display wlan client roam-track mac-address command to view client roaming track information.
Inter-AC roaming configuration example
Network requirements
As shown in Figure 7, a client associates with AP 1. Configure inter-AC roaming so that the client can associate with AP2 when roaming to it.
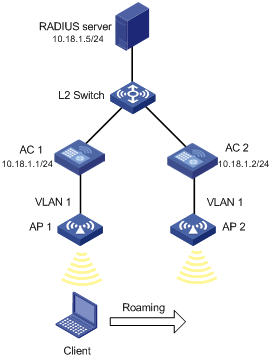
Configuration procedure
|
|
NOTE: · For wireless service configuration, see "WLAN service configuration." A client has inter-AC fast roaming capability only if it uses 802.1X (RSN) authentication through negotiation. · If you select an authentication mode involving remote authentication, you need to configure the corresponding RADIUS server. For more information, see "WLAN security configuration." |
1. Configure AC 1:
# On interface WLAN-ESS 1, configure port security mode as userlogin-secure-ext, and enable key negotiation of the 11key type.
<AC1> system-view
[AC1] interface wlan-ess 1
[AC1-WLAN-ESS1] port-security port-mode userlogin-secure-ext
[AC1-WLAN-ESS1] port-security tx-key-type 11key
# Disable the multicast trigger function and the online user handshake function.
[AC1-WLAN-ESS1] undo dot1x multicast-trigger
[AC1-WLAN-ESS1] undo dot1x handshake
[AC1-WLAN-ESS1] quit
# Create service template 1 of crypto type, configure its SSID as inter-roam, and bind WLAN-ESS1 to inter-roam.
[AC1] wlan service-template 1 crypto
[AC1-wlan-st-1] ssid inter-roam
[AC1-wlan-st-1] bind wlan-ess 1
# Configure the authentication method as open-system, and use the CCMP cipher suite for frame encryption.
[AC1-wlan-st-1] authentication-method open-system
[AC1-wlan-st-1] cipher-suite ccmp
[AC1-wlan-st-1] security-ie rsn
# Enable service template 1.
[AC1-wlan-st-1] service-template enable
[AC1-wlan-st-1] quit
# Enable port security.
[AC1] port-security enable
# Configure the 802.1X authentication method as EAP.
[AC1] dot1x authentication-method eap
# Create a RADIUS scheme rad, and specify the extended RADIUS server type.
[AC1] radius scheme rad
[AC1-radius-rad] server-type extended
# Configure the IP addresses of the primary authentication server and accounting server as 10.18.1.5.
[AC1-radius-rad] primary authentication 10.18.1.5
[AC1-radius-rad] primary accounting 10.18.1.5
# Configure the shared key for RADIUS authentication/accounting packets as 12345678.
[AC1-radius-rad] key authentication 12345678
[AC1-radius-rad] key accounting 12345678
# Configure the source IP address of RADIUS packets sent by the AC as 10.18.1.1.
[AC1-radius-rad] nas-ip 10.18.1.1
[AC1-radius-rad] quit
# Configure ISP domain cams to use RADIUS scheme rad to implement authentication, authorization, and accounting for all types of users.
[AC1] domain cams
[AC1-isp-cams] authentication default radius-scheme rad
[AC1-isp-cams] authorization default radius-scheme rad
[AC1-isp-cams] accounting default radius-scheme rad
[AC1-isp-cams] quit
#Configure the 802.1X mandatory authentication domain as cams on interface WLAN-ESS 1.
[AC1] interface WLAN-ESS 1
[AC1-WLAN-ESS1] dot1x mandatory-domain cams
[AC1-WLAN-ESS1] quit
# Configure AP 1: Create an AP template named ap1 and its model is WA2100, and configure the serial ID of AP 1 as 210235A045B05B1236548.
[AC1] wlan ap ap1 model WA2100
[AC1-wlan-ap-ap1] serial-id 210235A045B05B1236548
[AC1-wlan-ap-ap1] radio 1 type dot11g
# Bind service template inter-roam to radio 1.
[AC1-wlan-ap-ap1-radio-1] service-template 1
[AC1-wlan-ap-ap1-radio-1] radio enable
[AC1-wlan-ap-ap1-radio-1] quit
[AC1-wlan-ap-ap1] quit
# Create mobility group roam, specify the tunnel source IP as 10.18.1.1, and specify a member with IP address 10.18.1.2.
[AC1] wlan mobility-group roam
[AC1-wlan-mg-roam] source ip 10.18.1.1
[AC1-wlan-mg-roam] member ip 10.18.1.2
[AC1-wlan-mg-roam] mobility-group enable
2. Configure AC 2:
# On interface WLAN-ESS 1, configure port security mode as userlogin-secure-ext, and enable key negotiation of the 11key type.
<AC2> system-view
[AC2] interface wlan-ess 1
[AC2-WLAN-ESS1] port-security port-mode userlogin-secure-ext
[AC2-WLAN-ESS1] port-security tx-key-type 11key
# Disable the multicast trigger function and the online user handshake function.
[AC2-WLAN-ESS1] undo dot1x multicast-trigger
[AC2-WLAN-ESS1] undo dot1x handshake
[AC2-WLAN-ESS1] quit
# Create service template 1 of crypto type, configure its SSID as inter-roam, and bind WLAN-ESS1 to intra-roam.
[AC2] wlan service-template 1 crypto
[AC2-wlan-st-1] ssid inter-roam
[AC2-wlan-st-1] bind wlan-ess 1
# Configure the authentication method as open-system, use the CCMP cipher suite for frame encryption, and enable the RSN security IE to be carried in beacon and reply frames. .
[AC2-wlan-st-1] authentication-method open-system
[AC2-wlan-st-1] cipher-suite ccmp
[AC2-wlan-st-1] security-ie rsn
# Enable service template 1.
[AC2-wlan-st-1] service-template enable
[AC2-wlan-st-1] quit
# Enable port security.
[AC2] port-security enable
# Configure the 802.1X authentication method as EAP.
[AC2] dot1x authentication-method eap
# Create RADIUS scheme rad, and specify the server type as extended to exchange extended messages with the server.
[AC2] radius scheme rad
[AC2-radius-rad] server-type extended
# Specify the IP addresses of the primary authentication and accounting servers as 10.18.1.5.
[AC2-radius-rad] primary authentication 10.18.1.5
[AC2-radius-rad] primary accounting 10.18.1.5
# Configure the authentication and accounting keys as 12345678.
[AC2-radius-rad] key authentication 12345678
[AC2-radius-rad] key accounting 12345678
# Configure the source IP address of RADIUS packets as 10.18.1.2.
[AC2-radius-rad] nas-ip 10.18.1.2
[AC2-radius-rad] quit
# Create ISP domain cams, and use RADIUS scheme rad as the AAA methods.
[AC2] domain cams
[AC2-isp-cams] authentication default radius-scheme rad
[AC2-isp-cams] authorization default radius-scheme rad
[AC2-isp-cams] accounting default radius-scheme rad
[AC2-isp-cams] quit
# On interface WLAN-ESS 1, configure the 802.1X mandatory authentication domain as cams.
[AC1] interface WLAN-ESS 1
[AC1-WLAN-ESS1] dot1x mandatory-domain cams
[AC1-WLAN-ESS1] quit
# Configure AP 2: Create an AP template named ap2 and its model is WA2100, and configure the serial ID of AP 2 as 2210235A22W0076000103.
[AC2] wlan ap ap2 model WA2100
[AC2-wlan-ap-ap2] serial-id 210235A22W0076000103
[AC2-wlan-ap-ap2] radio 1 type dot11g
# Bind service template inter-roam to radio 1 of AP 2 (Inter-AC roaming requires consistent SSIDs of APs. Therefore, radio 1 of AP 2 should be bound to service template inter-roam.).
[AC2-wlan-ap-ap2-radio-1] service-template 1
[AC2-wlan-ap-ap2-radio-1] radio enable
[AC2-wlan-ap-ap2-radio-1] quit
[AC2-wlan-ap-ap2] quit
# Create mobility group roam, specify the tunnel source IP as 10.18.1.2, and specify a member with IP address 10.18.1.1.
[AC2] wlan mobility-group roam
[AC2-wlan-mg-roam] source ip 10.18.1.2
[AC2-wlan-mg-roam] member ip 10.18.1.1
[AC2-wlan-mg-roam] mobility-group enable
3. Verify the configuration:
You can use the display wlan client roam-out command on AC 1 to display roamed out client information, and use the display wlan client roam-in command on AC 2 to display roamed in client information. You can also use the display wlan client roam-track mac-address command to view client roaming track information on AC 1.
