- Table of Contents
-
- 02-WLAN Configuration Guide
- 00-Preface
- 01-WLAN Interface Configuration
- 02-WLAN Service Configuration
- 03-WLAN Security Configuration
- 04-WLAN Roaming Configuration
- 05-WLAN RRM Configuration
- 06-WLAN IDS Configuration
- 07-WLAN QoS Configuration
- 08-WLAN Mesh Link Configuration
- 09-WLAN Optimization Configuration
- 10-Advanced WLAN Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 03-WLAN Security Configuration | 483.87 KB |
Contents
Enabling an authentication method
Configuring the GTK rekey method
Displaying and maintaining WLAN security
WLAN security configuration examples
PSK authentication configuration example
MAC and PSK authentication configuration example
802.1X authentication configuration example
Dynamic WEP encryption-802.1X authentication configuration example
Supported combinations for ciphers
The wireless security capabilities incorporated in 802.11, though adequate to prevent the general public accessibility, do not offer sufficient protection from sophisticated network break-ins. To protect against any potential unauthorized access, advanced security mechanisms beyond the capabilities of 802.11 are necessary.
Authentication modes
To secure wireless links, the wireless clients must be authenticated before accessing the AP, and only wireless clients passing the authentication can be associated with the AP. 802.11 links define two authentication mechanisms: open system authentication and shared key authentication.
· Open system authentication
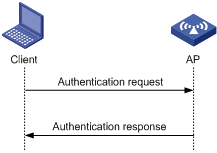
Open system authentication is the default authentication algorithm. This is the simplest of the available authentication algorithms. Essentially it is a null authentication algorithm. Any client that requests authentication with this algorithm can become authenticated. Open system authentication is not required to be successful as an AP may decline to authenticate the client. Open system authentication involves a two-step authentication process. In the first step, the wireless client sends a request for authentication. In the second step, the AP determines whether the wireless client passes the authentication and returns the result to the client.
Figure 1 Open system authentication process
· Shared key authentication
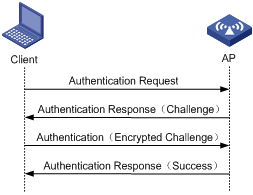
Figure 2 shows a shared key authentication process. The client and the AP have the same shared key configured.
a. The client sends an authentication request to the AP.
b. The AP randomly generates a challenge and sends it to the client.
c. The client uses the shared key to encrypt the challenge and sends it to the AP.
d. The AP uses the shared key to encrypt the challenge and compares the result with that received from the client. If they are identical, the client passes the authentication. If not, the authentication fails.
Figure 2 Shared key authentication process
WLAN data security
WLAN networks tend to be more susceptible to attacks than wired networks because WLAN devices share the same transmission medium. As a result, the potential exists for one a device to intercept data not intended for it. If no security is provided, plain-text data is at risk of being read by unintended recipients.
To secure data transmission, 802.11 protocols provide some encryption methods to make sure devices without the correct key cannot read encrypted data.
1. Plain-text data
All data packets are not encrypted. It is in fact a WLAN service without any security protection.
2. WEP encryption
Wired Equivalent Privacy (WEP) was developed to protect data exchanged among authorized users in a wireless LAN from casual eavesdropping. WEP uses RC4 encryption for confidentiality. WEP encryption falls into static and dynamic encryption according to how a WEP key is generated.
· Static WEP encryption
With Static WEP encryption, all clients using the same SSID must use the same encryption key. If the encryption key is deciphered or lost, attackers will get all encrypted data. In addition, periodical manual key update brings great management workload.
· Dynamic WEP encryption
Dynamic WEP encryption is a great improvement over static WEP encryption. With dynamic WEP encryption, WEP keys are negotiated between client and server through the 802.1X protocol so that each client is assigned a different WEP key, which can be updated periodically to further improve unicast frame transmission security.
Although WEP encryption increases the difficulty of network interception and session hijacking, it still has weaknesses due to limitations of RC4 encryption algorithm and static key configuration.
3. TKIP encryption
Temporal key integrity Protocol (TKIP) and WEP both use the RC4 algorithm, but TKIP has many advantages over WEP, and provides more secure protection for WLAN as follows:
¡ First, TKIP provides longer IVs to enhance encryption security. Compared with WEP encryption, TKIP encryption uses 128–bit RC4 encryption algorithm, and increases the length of IVs from 24 bits to 48 bits.
¡ Second, TKIP allows for dynamic key negotiation to avoid static key configuration. TKIP replaces a single static key with a base key generated by an authentication server. TKIP dynamic keys cannot be easily deciphered.
¡ Third, TKIP offers Message Integrity Check (MIC) and countermeasures. If a packet fails the MIC, the data may be tampered, and the system may be attacked. If two packets fail the MIC in a certain period, the AP automatically takes countermeasures. It will not provide services in a certain period to prevent attacks.
4. CCMP encryption
CTR with CBC-MAC protocol (CCMP) is based on the CCM of the AES encryption algorithm. CCM combines CTR for confidentiality and CBC-MAC for authentication and integrity. CCM protects the integrity of both the MPDU Data field and selected portions of the IEEE 802.11 MPDU header. The AES block algorithm in CCMP uses a 128-bit key and a 128-bit block size. Similarly, CCMP contains a dynamic key negotiation and management method, so that each wireless client can dynamically negotiate a key suite, which can be updated periodically to further enhance the security of the CCMP encryption mechanism. During the encryption process, CCMP uses a 48-bit packet number (PN) to make sure each encrypted packet uses a different PN, improving the security to a certain extent.
Client access authentication
1. PSK authentication
To implement pre-shared key (PSK) authentication, the client and the authenticator must have the same shared key configured. Otherwise, the client cannot pass pre-shared key (PSK) authentication.
2. 802.1X authentication
As a port-based access control protocol, 802.1X authenticates and controls accessing devices at the port level. A device connected to an 802.1X-enabled port of a WLAN access control device can access the resources on the WLAN only after passing authentication.
3. MAC authentication
MAC address authentication does not require any client software. The MAC address of a client is compared against a predefined list of allowed MAC addresses. If a match is found, the client can pass the authentication and access the WLAN; if not, the authentication fails and access is denied. The entire process does not require the user to enter a username or password. This type of authentication is suited to small networks (such as families and small offices) with fixed clients.
MAC address authentication can be done locally or through a RADIUS server.
¡ Local MAC address authentication—A list of usernames and passwords (the MAC addresses of allowed clients) is created on the wireless access device to authenticate the clients. Only clients whose MAC addresses are included in the list can pass the authentication and access the WLAN.
¡ MAC address authentication through RADIUS server—The wireless access device serves as the RADIUS client and sends the MAC address of each requesting client to the RADIUS server. If the client passes the authentication on the RADIUS server, the client can access the WLAN within the authorization assigned by the RADIUS server. In this authentication mode, if different domains are defined, authentication information of different SSIDs are sent to different RADIUS servers based on their domains.
|
|
NOTE: For more information about access authentication, see Security Configuration Guide. |
Protocols and standards
· IEEE Standard for Information technology—Telecommunications and information exchange between systems— Local and metropolitan area networks— Specific requirements -2004
· Wi-Fi Protected Access—Enhanced Security Implementation Based On IEEE P802.11i Standard-Aug 2004
· Information technology—Telecommunications and information exchange between systems—Local and metropolitan area networks—Specific requirements—802.11, 1999
· IEEE Standard for Local and metropolitan area networks "Port-Based Network Access Control" 802.1X™- 2004
· 802.11i IEEE Standard for Information technology—Telecommunications and information exchange between systems—Local and metropolitan area networks—Specific requirements
Configuring WLAN security
Configuration task list
To configure WLAN security in a service template, map the service template to a radio policy, and add radios to the radio policy. The SSID name, advertisement setting (beaconing), and encryption settings are configured in the service template. You can configure an SSID to support any combination of WPA, RSN, and Pre-RSN clients
Complete these tasks to configure WLAN security:
|
Task |
Remarks |
|
Required |
|
|
Optional |
|
|
Optional |
|
|
Required |
|
|
Required |
|
|
Optional |
Enabling an authentication method
You can enable open system or shared key authentication or both.
To enable an authentication method:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WLAN service template view. |
wlan service-template service-template-number crypto |
N/A |
|
3. Enable the authentication method. |
authentication-method { open-system | shared-key } |
Optional. Open system authentication method is used by default. · Shared key authentication is usable only when WEP encryption is adopted. In this case, you must configure the authentication-method shared-key command. · For RSN and WPA, open system authentication is required. |
Configuring the PTK lifetime
A pairwise transient key (PTK) is generated through a four-way handshake, during which, the pairwise master key (PMK), an AP random value (ANonce), a site random value (SNonce), the AP's MAC address and the client's MAC address are used.
To configure the PTK lifetime:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WLAN service template view. |
wlan service-template service-template-number crypto |
N/A |
|
3. Configure the PTK lifetime. |
ptk-lifetime time |
Optional. By default, the PTK lifetime is 43200 seconds. |
Configuring the GTK rekey method
An AC generates a group temporal key (GTK) and sends the GTK to a client during the authentication process between an AP and the client through group key handshake or the 4-way handshake. The client uses the GTK to decrypt broadcast and multicast packets. Robust Security Network (RSN) negotiates the GTK through the 4-way handshake or group key handshake, and Wi-Fi Protected Access (WPA) negotiates the GTK only through group key handshake.
Two GTK rekey methods can be configured:
· Time-based GTK rekey: After the specified interval elapses, GTK rekey occurs.
· Packet-based GTK rekey. After the specified number of packets is sent, GTK rekey occurs.
You can also configure the device to start GTK rekey when a client goes offline.
Configuring GTK rekey based on time
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WLAN service template view. |
wlan service-template service-template-number crypto |
N/A |
|
3. Enable GTK rekey. |
gtk-rekey enable |
By default, GTK rekey is enabled. |
|
4. Configure the GTK rekey interval. |
gtk-rekey method time-based [ time ] |
By default, the interval is 86400 seconds. |
|
5. Configure the device to start GTK rekey when a client goes offline. |
gtk-rekey client-offline enable |
Optional. Not configured by default. The command takes effect only when GTK rekey has been enabled with the gtk-rekey enable command. |
Configuring GTK rekey based on packet
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WLAN service template view. |
wlan service-template service-template-number crypto |
N/A |
|
3. Enable GTK rekey. |
gtk-rekey enable |
By default, GTK rekey is enabled. |
|
4. Configure GTK rekey based on packet. |
gtk-rekey method packet-based [ packet ] |
The default packet number is 10000000. |
|
5. Configure the device to start GTK rekey when a client goes offline. |
gtk-rekey client-offline enable |
Optional. Not configured by default. This command takes effect only when GTK rekey has been enabled with the gtk-rekey enable command. |
|
|
NOTE: · By default, time-based GTK rekey is adopted, and the rekey interval is 86400 seconds. · Configuring a new GTK rekey method overwrites the previous one. For example, if time-based GTK rekey is configured after packet-based GTK rekey is configured, time-based GTK rekey takes effect. |
Configuring security IE
Configuring WPA security IE
WPA ensures greater protection than WEP. WPA operates in either WPA-PSK (or Personal) mode or WPA-802.1X (or Enterprise) mode. In Personal mode, a pre-shared key or pass-phrase is used for authentication. In Enterprise mode, 802.1X and RADIUS servers and the Extensible Authentication Protocol (EAP) are used for authentication.
To configure the WPA security IE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WLAN service template view. |
wlan service-template service-template-number crypto |
N/A |
|
3. Enable the WPA-IE in the beacon and probe responses. |
security-ie wpa |
By default, WPA-IE is disabled. |
Configuring RSN security IE
An RSN is a security network that allows only the creation of robust security network associations (RSNAs). An RSN can be identified by the indication in the RSN Information Element (IE) of beacon frames. It provides greater protection than WEP and WPA.
To configure RSN security IE:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WLAN service template view. |
wlan service-template service-template-number crypto |
N/A |
|
3. Enable the RSN security IE in the beacon and probe responses. |
security-ie rsn |
By default, RSN-IE is disabled. |
Configuring cipher suite
A cipher suite is used for data encapsulation and de-encapsulation. It uses the following encryption methods:
· WEP40/WEP104/WEP128
· TKIP
· CCMP
Configuring WEP cipher suite
1. Configure static WEP encryption
The WEP encryption mechanism requires that the authenticator and clients on a WLAN have the same key configured. WEP adopts the RC4 algorithm (a stream encryption algorithm), supporting WEP40, WEP104 and WEP128 keys.
WEP can be used with either open system authentication mode or shared key authentication mode:
¡ In open system authentication mode, a WEP key is used for encryption only. A client can access the WLAN without having the same key as the authenticator. But, if the receiver has a different key from the sender, it discards the packets received from the sender.
¡ In shared key authentication mode, the WEP key is used for both encryption and authentication. If the key of a client is different from that of the authenticator, the client cannot pass the authentication and cannot access the WLAN.
To configure static WEP encryption:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WLAN service template view. |
wlan service-template service-template-number crypto |
N/A |
|
3. Enable the WEP cipher suite. |
cipher-suite { wep40 | wep104 | wep128 } * |
By default, no cipher suite is selected. |
|
4. Configure the WEP default key. |
wep default-key { 1 | 2 | 3 | 4 } { wep40 | wep104 | wep128 } { pass-phrase | raw-key } [ cipher | simple ] key |
By default, the WEP default key index number is 1. |
|
5. Specify a key index number. |
wep key-id { 1 | 2 | 3 | 4 } |
Optional. The default is 1. |
2. Configure dynamic WEP encryption
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WLAN service template view. |
wlan service-template service-template-number crypto |
N/A |
|
3. Enable dynamic WEP encryption. |
wep mode dynamic |
By default, static WEP encryption is adopted. Dynamic WEP encryption must be used together with 802.1X authentication. |
|
4. Enable the WEP cipher suite. |
cipher-suite { wep40 | wep104 | wep128 } |
Optional. With dynamic WEP encryption configured, the device automatically uses the WEP 104 cipher suite. To change the encryption method, use the cipher-suite command. |
|
5. Configure the WEP default key. |
wep default-key { 1 | 2 | 3 | 4 } { wep40 | wep104 | wep128 } { pass-phrase | raw-key } [ cipher | simple ] key |
Optional. No WEP default key is configured by default. If the WEP default key is configured, the WEP default key is used to encrypt multicast frames. If not, the device randomly generates a multicast WEP key. |
|
6. Specify a key index number. |
wep key-id { 1 | 2 | 3 } |
Optional. By default, the key index number is 1. For dynamic WEP encryption, the WEP key ID cannot be configured as 4. |
Configuring TKIP cipher suite
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WLAN service template view. |
wlan service-template service-template-number crypto |
N/A |
|
3. Enable the TKIP cipher suite. |
cipher-suite tkip |
By default, no cipher suite is selected. |
|
4. Configure the TKIP countermeasure interval. |
tkip-cm-time time |
Optional. The default countermeasure interval is 0 seconds. No countermeasures are taken. |
|
|
NOTE: Message integrity check (MIC) is used to prevent attackers from data modification. It ensures data security by using the Michael algorithm. When a fault occurs to the MIC, the device will consider that the data has been modified and the system is being attacked. Upon detecting the attack, TKIP will suspend within the countermeasure interval. No TKIP associations can be established within the interval. |
Configuring CCMP cipher suite
CCMP adopts the AES encryption algorithm.
To configure the CCMP cipher suite:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WLAN service template view. |
wlan service-template service-template-number crypto |
N/A |
|
3. Enable the CCMP cipher suite. |
cipher-suite ccmp |
By default, no cipher suite is selected. |
Configuring port security
The authentication type configuration includes the following options:
· PSK
· 802.1X
· MAC
· PSK and MAC
|
|
NOTE: This document describes only several common port security modes. For more information about other port security modes, see Security Configuration Guide. |
Before configuring port security, you must:
1. Create the wireless port.
2. Enable port security.
Configuring PSK authentication
|
Step |
Command |
Remarks |
|
1. Enter system view.. |
system-view |
N/A |
|
2. Enter WLAN-ESS interface view. |
interface wlan-ess interface-number |
N/A |
|
3. Enable 802.11 key negotiation. |
port-security tx-key-type 11key |
Not enabled by default. |
|
4. Configure the pre-shared key. |
port-security preshared-key { pass-phrase | raw-key } [ cipher | simple ] key |
Not configured by default. |
|
5. Enable the PSK port security mode. |
port-security port-mode psk |
N/A |
Configuring 802.1X authentication
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Enter WLAN-ESS interface view. |
interface wlan-ess interface-number |
|
3. Enable the 802.1X port security mode. |
port-security port-mode { userlogin-secure | userlogin-secure-ext } |
Configuring MAC authentication
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Enter WLAN-ESS interface view. |
interface wlan-ess interface-number |
|
3. Enable MAC port security mode. |
port-security port-mode mac-authentication |
|
|
NOTE: 802.11i does not support MAC authentication. |
Configuring PSK and MAC authentication
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WLAN-ESS interface view. |
interface wlan-ess interface-number |
N/A |
|
3. Enable 802.11 key negotiation. |
port-security tx-key-type 11key |
Not enabled by default. |
|
4. Enable the PSK and MAC port security mode. |
port-security port-mode mac-and-psk |
N/A |
|
5. Configure the pre-shared key. |
port-security preshared-key { pass-phrase | raw-key } key |
The key is a string of 8 to 63 characters, or a 64-digit hex number. |
|
|
NOTE: For more information about port security configuration commands, see Security Command Reference. |
Displaying and maintaining WLAN security
|
Task |
Command |
Remarks |
|
Display WLAN service template information. |
display wlan service-template [ service-template-number ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display client information. |
display wlan client { ap ap-name [ radio radio-number ] | mac-address mac-address | service-template service-template-number } [ verbose ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display MAC authentication information. |
display mac-authentication [ interface interface-list ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display the MAC address information of port security. |
display port-security mac-address security [ interface interface-type interface-number ] [ vlan vlan-id ] [ count ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display the PSK user information of port security. |
display port-security preshared-key user [ interface interface-type interface-number ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display the configuration information, running state and statistics of port security. |
display port-security [ interface interface-list ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display 802.1X session information or statistics. |
display dot1x [ sessions | statistics ] [ interface interface-list ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
|
NOTE: For more information about related display commands, see Security Command Reference. |
WLAN security configuration examples
PSK authentication configuration example
Network requirements
As shown in Figure 3, an AC is connected to an AP through a Layer 2 switch, and they are in the same network. Perform PSK authentication with key 12345678 on the client.
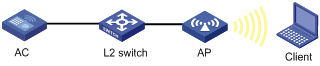
Configuration procedure
1. Configure the AC:
# Configure port security.
<AC> system-view
[AC] port-security enable
# Configure WLAN port security, configure the authentication mode as PSK, and the pre-shared key as 12345678.
[AC] interface wlan-ess 10
[AC-WLAN-ESS10] port-security port-mode psk
[AC-WLAN-ESS10] port-security preshared-key pass-phrase 12345678
[AC-WLAN-ESS10] port-security tx-key-type 11key
[AC-WLAN-ESS10] quit
# Create service template 10 of crypto type, configure its SSID as psktest, and bind WLAN-ESS10 to service template 10.
[AC] wlan service-template 10 crypto
[AC-wlan-st-10] ssid psktest
[AC-wlan-st-10] bind WLAN-ESS 10
[AC-wlan-st-10] security-ie rsn
[AC-wlan-st-10] cipher-suite ccmp
[AC-wlan-st-10] authentication-method open-system
[AC-wlan-st-10] service-template enable
[AC-wlan-st-10] quit
# Create an AP template named ap1 and its model is WA2100, and configure the serial ID of AP 1 as 210235A29G007C000020.
[AC] wlan ap ap1 model WA2100
[AC-wlan-ap-ap1] serial-id 210235A29G007C000020
# Bind service template 10 to radio 1.
[AC-wlan-ap-ap1] radio 1 type dot11g
[AC-wlan-ap-ap1-radio-1] service-template 10
[AC-wlan-ap-ap1-radio-1] radio enable
2. Verify the configuration:
¡ Configure the same PSK key on the client. After that, the client can associate with the AP and access the WLAN.
¡ You can use the display wlan client verbose command and display port-security preshared-key user command to view the online clients.
MAC and PSK authentication configuration example
Network requirements
· As shown in Figure 4, an AC with IP address 10.18.1.1, an AP, and a RADIUS server with IP address 10.18.1.88 are connected through a Layer 2 switch. Perform MAC and PSK authentication on the client.
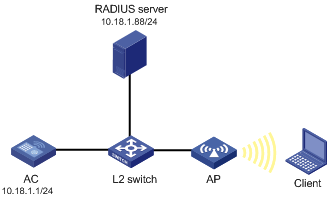
Configuration procedure
1. Configure the AC:
# Enable port security.
<AC> system-view
[AC] port-security enable
# Configure WLAN port security, using MAC and PSK authentication.
[AC] interface wlan-ess 2
[AC-WLAN-ESS2] port-security port-mode mac-and-psk
[AC-WLAN-ESS2] port-security tx-key-type 11key
[AC-WLAN-ESS2] port-security preshared-key pass-phrase 12345678
[AC-WLAN-ESS2] quit
# Create service template 2 of crypto type, configure its SSID as mactest, and bind WLAN-ESS2 to service template 2.
[AC] wlan service-template 2 crypto
[AC-wlan-st-2] ssid mactest
[AC-wlan-st-2] bind wlan-ess 2
[AC-wlan-st-2] authentication-method open-system
[AC-wlan-st-2] cipher-suite tkip
[AC-wlan-st-2] security-ie rsn
[AC-wlan-st-2] service-template enable
[AC-wlan-st-2] quit
# Create an AP template named ap1 and its model is WA2100, and configure the serial ID of AP 1 as 210235A29G007C000020.
[AC] wlan ap ap1 model WA2100
[AC-wlan-ap-ap1] serial-id 210235A29G007C000020
# Bind service template 2 to radio 1.
[AC-wlan-ap-ap1] radio 1 type dot11g
[AC-wlan-ap-ap1-radio-1] service-template 2
[AC-wlan-ap-ap1-radio-1] radio enable
[AC-wlan-ap-ap1-radio-1] quit
[AC-wlan-ap-ap1] quit
# Create a RADIUS scheme rad, and specify the extended RADIUS server type.
[AC] radius scheme rad
[AC-radius-rad] server-type extended
# Configure the IP addresses of the primary authentication server and accounting server as 10.18.1.88.
[AC-radius-rad] primary authentication 10.18.1.88
[AC-radius-rad] primary accounting 10.18.1.88
# Configure the shared key for RADIUS authentication/accounting packets as 12345678.
[AC-radius-rad] key authentication 12345678
[AC-radius-rad] key accounting 12345678
[AC-radius-rad] user-name-format without-domain
[AC-radius-rad] quit
# Configure AAA domain cams by referencing RADIUS scheme rad.
[AC] domain cams
[AC-isp-cams] authentication lan-access radius-scheme rad
[AC-isp-cams] authorization lan-access radius-scheme rad
[AC-isp-cams] accounting lan-access radius-scheme rad
[AC-isp-cams] quit
# Configure the MAC authentication domain by referencing AAA domain cams.
[AC] mac-authentication domain cams
# Configure MAC authentication user name format, using MAC addresses without hyphen as username and password (consistent with the format on the server).
[AC] mac-authentication user-name-format mac-address without-hyphen
2. Configure the RADIUS server (IMCv3):
|
|
NOTE: The following takes the IMC (the IMC versions are IMC PLAT 3.20-R2602 and IMC UAM 3.60-E6102) as an example to illustrate the basic configurations of the RADIUS server. |
# Add access device.
a. Log in to the IMC Platform.
b. Click the Service tab, and then select Access Service > Access Device from the navigation tree to enter the access device configuration page.
c. Click Add on the page to enter the configuration page shown in Figure 5:
d. Add 12345678 for Shared Key.
e. Add ports 1812, and 1813 for Authentication Port and Accounting Port respectively.
f. Select LAN Access Service for Service Type.
g. Select H3C for Access Device Type.
h. Select or manually add an access device with the IP address 10.18.1.1.

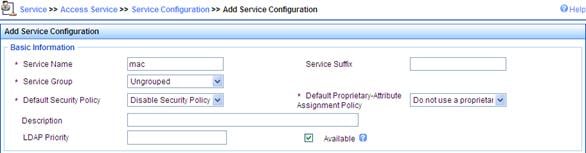
# Add service.
a. Click the Service tab, and then select Access Service > Access Device from the navigation tree to enter the add service page.
b. Click Add on the page to enter the following configuration page.
c. Set the service name to mac, and the others keep the default values.
Figure 6 Adding service
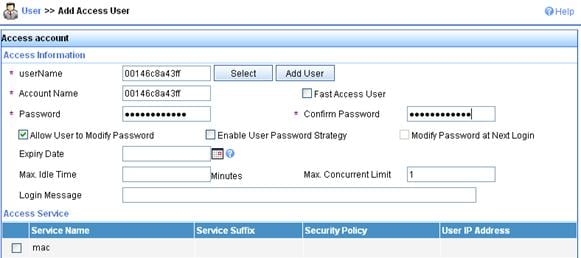
# Add account.
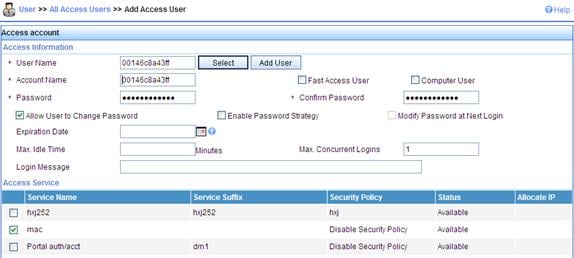
a. Click the User tab, and then select User > All Access Users from the navigation tree to enter the user page.
b. Click Add on the page to enter the page shown in Figure 7.
c. Enter a username 00146c8a43ff.
d. Add an account and password 00146c8a43ff.
e. Select the service mac.
3. Configure the RADIUS server (IMCv5):
|
|
NOTE: The following takes the IMC (the IMC versions are IMC PLAT 5.0 and IMC UAM 5.0) as an example to illustrate the basic configurations of the RADIUS server. |
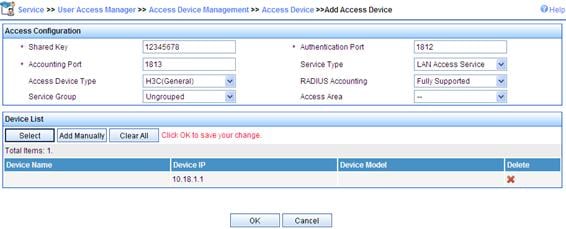
# Add an access device.
a. Log in to the IMC Platform.
b. Click the Service tab, and then select User Access Manager > Access Device Management > Access Device from the navigation tree to enter the access device configuration page.
c. Click Add on the page to enter the configuration page as shown in Figure 8:
d. Input 12345678 as the Shared Key. Keep the default values for other parameters.
e. Select or manually add the access device with the IP address 10.18.1.1.
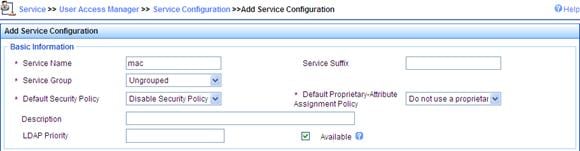
# Add service.
a. Click the Service tab, and then select User Access Manager > Service Configuration from the navigation tree to enter the add service page.
b. Click Add on the page to enter the following configuration page.
c. Set the service name as mac, and keep the default values for other parameters.
Figure 9 Adding service
# Add an account.
a. Click the User tab, and then select User > All Access Users from the navigation tree to enter the user page.
b. Click Add on the page to enter the page as shown in Figure 10.
c. Enter username 00146c8a43ff.
d. Set the account name and password both as 00146c8a43ff.
e. Select the service mac.
4. Verify the configuration:
¡ After the client passes the MAC authentication, the client can associate with the AP and access the WLAN.
¡ You can use the display wlan client verbose command, display connection command, and display mac-authentication command to view the online clients.
802.1X authentication configuration example
Network requirements
As shown in Figure 11, an AC with IP address 10.18.1.1, an AP and a RADIUS server with IP address 10.18.1.88 are connected through a Layer 2 switch. Perform 802.1X authentication on the client.
Configuration procedure
1. Configure the AC:
# Enable port security.
<AC> system-view
[AC] port-security enable
# Configure the 802.1X authentication mode as EAP.
[AC] dot1x authentication-method eap
# Create a RADIUS scheme rad, and specify the extended RADIUS server type.
[AC] radius scheme rad
[AC-radius-rad] server-type extended
# Configure the IP addresses of the primary authentication server and accounting server as 10.18.1.88.
[AC-radius-rad] primary authentication 10.18.1.88
[AC-radius-rad] primary accounting 10.18.1.88
# Configure the shared key for RADIUS authentication/accounting packets as 12345678.
[AC-radius-rad] key authentication 12345678
[AC-radius-rad] key accounting 12345678
[AC-radius-rad] user-name-format without-domain
[AC-radius-rad] quit
# Configure AAA domain cams by referencing RADIUS scheme rad.
[AC] domain cams
[AC-isp-cams] authentication lan-access radius-scheme rad
[AC-isp-cams] authorization lan-access radius-scheme rad
[AC-isp-cams] accounting lan-access radius-scheme rad
[AC-isp-cams] quit
# Specify the mandatory domain as cams.
[AC] interface WLAN-ESS 1
[AC-WLAN-ESS1] dot1x mandatory-domain cams
# Configure the port security mode as userlogin-secure-ext, and enable 802.11 key negotiation.
[AC-WLAN-ESS1] port-security port-mode userlogin-secure-ext
[AC-WLAN-ESS1] port-security tx-key-type 11key
# Disable the multicast trigger function and the online user handshake function.
[AC-WLAN-ESS1] undo dot1x multicast-trigger
[AC-WLAN-ESS1] undo dot1x handshake
[AC-WLAN-ESS1] quit
# Create service template 1 of crypto type, configure its SSID as dot1x, and configure the tkip and ccmp cipher suite.
[AC] wlan service-template 1 crypto
[AC-wlan-st-1] ssid dot1x
[AC-wlan-st-1] bind WLAN-ESS 1
[AC-wlan-st-1] authentication-method open-system
[AC-wlan-st-1] cipher-suite tkip
[AC-wlan-st-1] cipher-suite ccmp
[AC-wlan-st-1] security-ie rsn
[AC-wlan-st-1] service-template enable
[AC-wlan-st-1] quit
# Create an AP template named ap1 and its model is WA2100, and configure the serial ID of AP 1 as 210235A29G007C000020.
[AC] wlan ap ap1 model WA2100
[AC-wlan-ap-ap1] serial-id 210235A29G007C000020
# Bind service template 1 to radio 1.
[AC-wlan-ap-ap1] radio 1 type dot11g
[AC-wlan-ap-ap1-radio-1] service-template 1
[AC-wlan-ap-ap1-radio-1] radio enable
2. Configure the RADIUS server (IMCv3):
|
|
NOTE: The following takes the IMC (the IMC versions are IMC PLAT 3.20-R2602 and IMC UAM 3.60-E6102) as an example to illustrate the basic configurations of the RADIUS server. |
# Add access device.
a. Log in to the IMC Platform.
b. Click the Service tab, and then select Access Service > Access Device from the navigation tree to enter the access device configuration page.
c. Click Add on the page to enter the configuration page shown in Figure 12:
d. Add 12345678 for Shared Key.
e. Add ports 1812, and 1813 for Authentication Port and Accounting Port respectively.
f. Select LAN Access Service for Service Type.
g. Select H3C for Access Device Type.
h. Select or manually add an access device with the IP address 10.18.1.1.
Figure 12 Adding access device

# Add service.
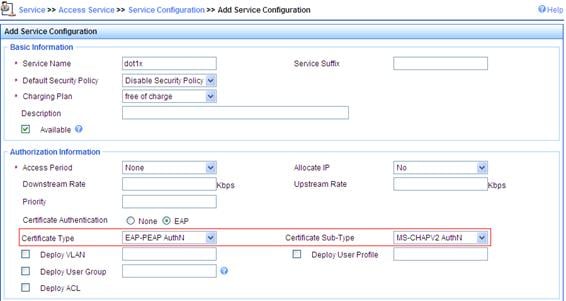
a. Click the Service tab, and then select Access Service > Service Configuration from the navigation tree to enter the add service page.
b. Click Add on the page to enter the configuration page shown in Figure 13.
c. Set the service name to dot1x.
d. Select EAP-PEAP AuthN from the Certificate Type drop-down list, and MS-CHAPV2 AuthN from the Certificate Sub-Type list.
# Add account.
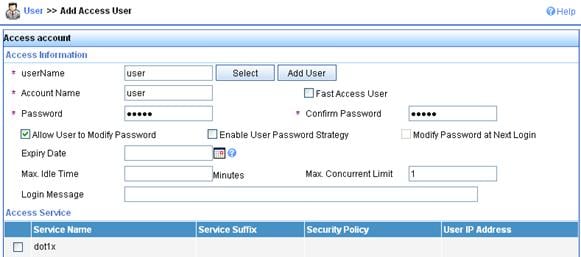
a. Click the User tab, and then select Users > All Access Users from the navigation tree to enter the user page.
b. Click Add on the page to enter the page shown in Figure 14.
c. Enter a username user.
d. Add an account user and password dot1x.
e. Select the previously configured service dot1x.
3. Configure the RADIUS server (IMCv5):
|
|
NOTE: The following takes the IMC (the IMC versions are IMC PLAT 5.0 and IMC UAM 5.0) as an example to illustrate the basic configurations of the RADIUS server. |
# Add an access device.
a. Log in to the IMC Platform.
b. Click the Service tab, and then select User Access Manager > Access Device Management from the navigation tree to enter the access device configuration page.
c. Click Add on the page to enter the configuration page as shown in Figure 15:
d. Input 12345678 as the Shared Key. Keep the default values for other parameters.
e. Select or manually add the access device with the IP address 10.18.1.1.
Figure 15 Adding access device

# Add service.
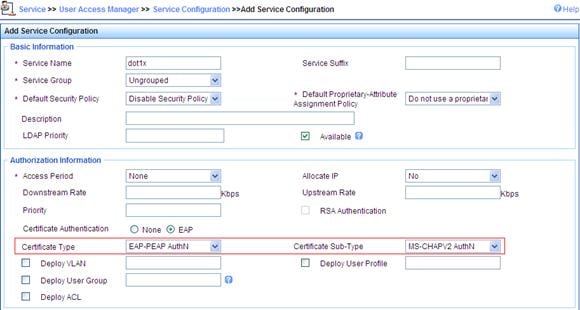
a. Click the Service tab, and then select User Access Manager > Service Configuration from the navigation tree to enter the add service page.
b. Click Add on the page to enter the following configuration page.
c. Set the service name to dot1x, select EAP-PEAP AuthN as the Certificate Type, and MS-CHAPV2 AuthN as the Certificate Sub-Type.
Figure 16 Adding service
# Add an account.
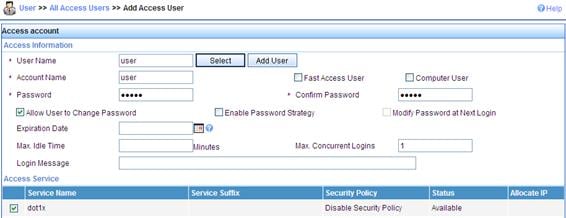
a. Click the User tab, and then select User > All Access Users from the navigation tree to enter the user page.
b. Click Add on the page to enter the page as shown in Figure 17.
c. Enter username user.
d. Set the account name user and password dot1x.
e. Select the service dot1x.
4. Configure the wireless card:
a. Double click the ![]() icon at the bottom right corner of your desktop.
icon at the bottom right corner of your desktop.
The Wireless Network Connection Status window appears.
b. Click the Properties button in the General tab.
The Wireless Network Connection Properties window appears.
c. On the Wireless Networks tab, select wireless network with the SSID dot1x, and then click Properties.
The dot1x Properties window appears.
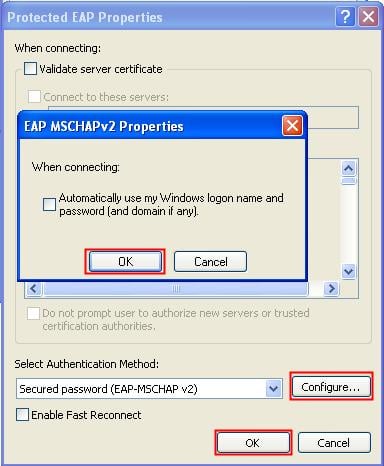
d. On the Authentication tab, select Protected EAP (PEAP) from the EAP type list, and click Properties.
e. On the popup window, clear Validate server certificate, and click Configure.
f. In the popup dialog box, clear Automatically use my Windows logon name and password (and domain if any).
The configuration procedure is as shown in Figure 22 through Figure 24.
Figure 18 Configuring the wireless card (I)
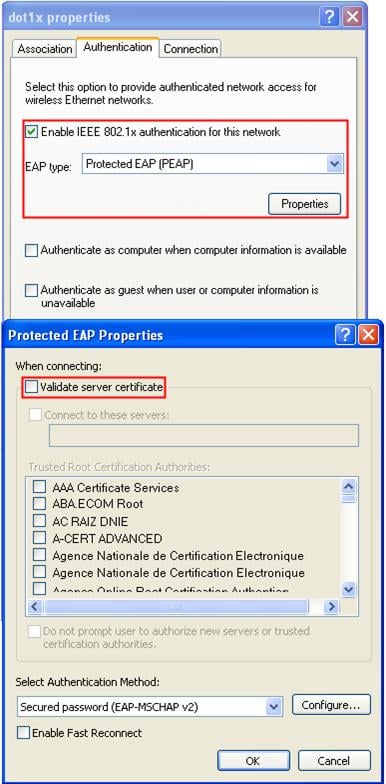
Figure 19 Configuring the wireless card (II)
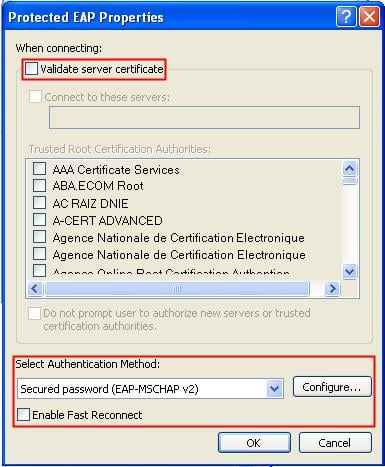
Figure 20 Configuring the wireless card (III)
5. Verify the configuration:
¡ The client can pass 802.1X authentication and associate with the AP.
¡ You can use the display wlan client verbose command, display connection command, and display dot1x command to view the online clients.
Dynamic WEP encryption-802.1X authentication configuration example
Network requirements
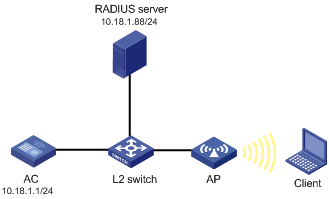
As shown in Figure 21, an AC with IP address 10.18.1.1, an AP, and a RADIUS server with IP address 10.18.1.88 are connected through a Layer 2 switch. Perform dynamic WEP encryption.
Configuration procedure
1. Configure the AC:
# Enable port security.
<AC> system-view
[AC] port-security enable
# Configure the 802.1X authentication mode as EAP.
[AC] dot1x authentication-method eap
# Create a RADIUS scheme rad, and specify the extended RADIUS server type.
[AC] radius scheme rad
[AC-radius-rad] server-type extended
# Configure the IP addresses of the primary authentication and accounting servers as 10.18.1.88.
[AC-radius-rad] primary authentication 10.18.1.88
[AC-radius-rad] primary accounting 10.18.1.88
# Configure the shared key for RADIUS authentication/accounting as 12345678.
[AC-radius-rad] key authentication 12345678
[AC-radius-rad] key accounting 12345678
[AC-radius-rad] user-name-format without-domain
[AC-radius-rad] quit
# Configure AAA domain bbb by referencing RADIUS scheme rad.
[AC] domain bbb
[AC-isp-bbb] authentication lan-access radius-scheme rad
[AC-isp-bbb] authorization lan-access radius-scheme rad
[AC-isp-bbb] accounting lan-access radius-scheme rad
[AC-isp-bbb] quit
# Specify the mandatory domain as bbb.
[AC] interface WLAN-ESS 1
[AC-WLAN-ESS1] dot1x mandatory-domain bbb
# Configure the port security mode as userlogin-secure-ext.
[AC-WLAN-ESS1] port-security port-mode userlogin-secure-ext
# Disable the multicast trigger function and the online user handshake function.
[AC-WLAN-ESS1] undo dot1x multicast-trigger
[AC-WLAN-ESS1] undo dot1x handshake
[AC-WLAN-ESS1] quit
# Create service template 1 of crypto type, configure its SSID as dot1x, and enable dynamic WEP encryption.
[AC] wlan service-template 1 crypto
[AC-wlan-st-1] ssid dot1x
[AC-wlan-st-1] wep mode dynamic
[AC-wlan-st-1] authentication-method open-system
[AC-wlan-st-1] bind WLAN-ESS 1
[AC-wlan-st-1] service-template enable
[AC-wlan-st-1] quit
# Create an AP template named ap1, and specify its model as WA2100, and serial ID as 210235A29G007C000020.
[AC] wlan ap ap1 model WA2100
[AC-wlan-ap-ap1] serial-id 210235A29G007C000020
# Bind service template 1 to radio 1.
[AC-wlan-ap-ap1] radio 1 type dot11g
[AC-wlan-ap-ap1-radio-1] service-template 1
[AC-wlan-ap-ap1-radio-1] radio enable
2. Configure the RADIUS server (IMCv3):
See "Configure the RADIUS server (IMCv3):."
3. Configure the RADIUS server (IMCv5):
See "Configure the RADIUS server (IMCv5):."
4. Configure the wireless card:
a. Double click the ![]() icon at the bottom right corner of your desktop.
icon at the bottom right corner of your desktop.
The Wireless Network Connection Status window appears.
b. Click the Properties button on the General tab.
The Wireless Network Connection Properties window appears.
c. On the Wireless Networks tab, select wireless network with the SSID dot1x, and then click Properties.
The dot1x Properties window appears.
d. On the Authentication tab, select Protected EAP (PEAP) from the EAP type list, and click Properties.
e. On the popup window, clear Validate server certificate, and click Configure.
f. In the popup dialog box, clear Automatically use my Windows logon name and password (and domain if any).
The configuration procedure is as shown in Figure 22 through Figure 24.
Figure 22 Configuring the wireless card (I)
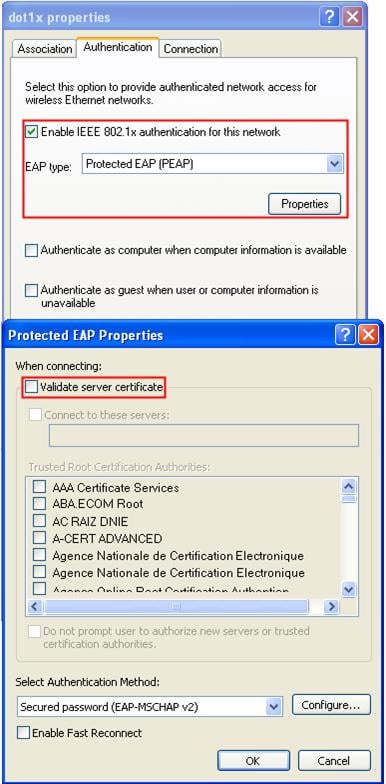
Figure 23 Configuring the wireless card (II)

Figure 24 Configuring the wireless card (III)

Verifying the configuration
· After inputting username user and password dot1x in the popup dialog box, the client can associate with the AP and access the WLAN.
· You can use the display wlan client verbose command, display connection command, and display dot1x command to view online client information.
Supported combinations for ciphers
This section introduces the combinations that can be used during the cipher suite configuration.
RSN
For RSN, the WLAN-WSEC module supports only CCMP and TKIP ciphers as the pair wise ciphers and WEP cipher suites will only be used as group cipher suites. Below are the RSN cipher suite combinations. (WEP40, WEP104 and WEP128 are mutually exclusive).
|
Unicast cipher |
Broadcast cipher |
Authentication method |
Security Type |
|
CCMP |
WEP40 |
PSK |
RSN |
|
CCMP |
WEP104 |
PSK |
RSN |
|
CCMP |
WEP128 |
PSK |
RSN |
|
CCMP |
TKIP |
PSK |
RSN |
|
CCMP |
CCMP |
PSK |
RSN |
|
TKIP |
WEP40 |
PSK |
RSN |
|
TKIP |
WEP104 |
PSK |
RSN |
|
TKIP |
WEP128 |
PSK |
RSN |
|
TKIP |
TKIP |
PSK |
RSN |
|
CCMP |
WEP40 |
802.1X |
RSN |
|
CCMP |
WEP104 |
802.1X |
RSN |
|
CCMP |
WEP128 |
802.1X |
RSN |
|
CCMP |
TKIP |
802.1X |
RSN |
|
CCMP |
CCMP |
802.1X |
RSN |
|
TKIP |
WEP40 |
802.1X |
RSN |
|
TKIP |
WEP104 |
802.1X |
RSN |
|
TKIP |
WEP128 |
802.1X |
RSN |
|
TKIP |
TKIP |
802.1X |
RSN |
WPA
For WPA, the WLAN-WSEC module supports the CCMP and TKIP ciphers as the pair wise ciphers and WEP cipher suites will only be used as group cipher suites. Below are the WPA cipher suite combinations (WEP40, WEP104 and WEP128 are mutually exclusive).
|
Unicast cipher |
Broadcast cipher |
Authentication method |
Security Type |
|
CCMP |
WEP40 |
PSK |
WPA |
|
CCMP |
WEP104 |
PSK |
WPA |
|
CCMP |
WEP128 |
PSK |
WPA |
|
CCMP |
TKIP |
PSK |
WPA |
|
CCMP |
CCMP |
PSK |
WPA |
|
TKIP |
WEP40 |
PSK |
WPA |
|
TKIP |
WEP104 |
PSK |
WPA |
|
TKIP |
WEP128 |
PSK |
WPA |
|
TKIP |
TKIP |
PSK |
WPA |
|
CCMP |
WEP40 |
802.1X |
WPA |
|
CCMP |
WEP104 |
802.1X |
WPA |
|
CCMP |
WEP128 |
802.1X |
WPA |
|
CCMP |
TKIP |
802.1X |
WPA |
|
CCMP |
CCMP |
802.1X |
WPA |
|
TKIP |
WEP40 |
802.1X |
WPA |
|
TKIP |
WEP104 |
802.1X |
WPA |
|
TKIP |
WEP128 |
802.1X |
WPA |
|
TKIP |
TKIP |
802.1X |
WPA |
Pre-RSN
For Pre-RSN stations, the WLAN-WSEC module supports only WEP cipher suites. (WEP40, WEP104, and WEP128 are mutually exclusive).
|
Unicast cipher |
Broadcast cipher |
Authentication method |
Security Type |
|
WEP40 |
WEP40 |
Open system |
no Sec Type |
|
WEP104 |
WEP104 |
Open system |
no Sec Type |
|
WEP128 |
WEP128 |
Open system |
no Sec Type |
|
WEP40 |
WEP40 |
Shared key |
no Sec Type |
|
WEP104 |
WEP104 |
Shared key |
no Sec Type |
|
WEP128 |
WEP128 |
Shared key |
no Sec Type |
