- Table of Contents
-
- 11-Segment Routing Configuration Guide
- 00-Preface
- 01-SR-MPLS configuration
- 02-SR-MPLS TE policy configuration
- 03-SRv6 configuration
- 04-SRv6 TE policy configuration
- 05-SRv6 VPN overview
- 06-IP L3VPN over SRv6 configuration
- 07-EVPN L3VPN over SRv6 configuration
- 08-EVPN VPWS over SRv6 configuration
- 09-EVPN VPLS over SRv6 configuration
- 10-Public network IP over SRv6 configuration
- 11-SRv6 OAM configuration
- 12-SRv6 network slicing configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 08-EVPN VPWS over SRv6 configuration | 812.16 KB |
Configuring EVPN VPWS over SRv6
EVPN VPWS over SRv6 network model
EVPN VPWS over SRv6 multihoming
LDP or static PW ACs for SRv6 PWs
Intercommunication between EVPN VPLS over SRv6 and EVPN VPWS over SRv6 networks
Restrictions and guidelines: EVPN VPWS over SRv6 configuration
Configuring EVPN VPWS over SRv6 with dynamic PWs
EVPN VPWS over SRv6 tasks at a glance (with dynamic PWs)
Applying a locator to a cross-connect
Configuring PEs to exchange BGP EVPN routes
Configuring the route recursion mode
Configuring SRv6 TE policy traffic steering
Restrictions and guidelines for SRv6 TE policy traffic steering
Configuring color-based traffic steering
Configuring tunnel policy-based traffic steering
Mapping an AC to a cross-connect
Mapping a Layer 3 interface to a cross-connect
Specifying a source address for the outer IPv6 header of SRv6-encapsulated EVPN VPWS packets
Configuring EVPN VPWS over SRv6 multihoming
Restrictions and guidelines for EVPN VPWS over SRv6 multihoming
Assigning an ESI to an interface
Setting the redundancy mode on an interface
Enabling cross-connects to ignore the state of ACs
Configuring FRR for EVPN VPWS over SRv6
Configuring LDP or static PWs as ACs for SRv6 PWs
About LDP or static PW AC configuration for SRv6 PWs
Restrictions and guidelines for LDP or static PW AC configuration for SRv6 PWs
Prerequisites for LDP or static PW AC configuration for SRv6 PWs
Configuring LDP PWs as ACs for SRv6 PWs
Configuring static PWs as ACs for SRv6 PWs
Configuring SRv6 PW packet statistics
Test the connectivity of an SRv6 PW
Using ping to test the connectivity of an SRv6 PW
Using tracert to test the connectivity of an SRv6 PW
Using a static BFD session to test the connectivity of an SRv6 PW
Display and maintenance commands for EVPN VPWS over SRv6
EVPN VPWS over SRv6 configuration examples
Example: Setting up an SRv6 tunnel between single-homed EVPN VPWS sites
Example: Configuring EVPN VPWS over SRv6 multihoming (S-Trunk dual-homed)
Example: Configuring LDP PWs as ACs for SRv6 PWs
Configuring EVPN VPWS over SRv6 with static PWs
EVPN VPWS over SRv6 tasks at a glance (with static PWs)
Configuring the static SRv6 PW establishment mode
Applying a locator to a cross-connect for SRv6 PW establishment
Configuring the route recursion mode
Configuring SRv6 TE policy traffic steering
Restrictions and guidelines for SRv6 TE policy traffic steering
Configuring color-based traffic steering
Configuring tunnel policy-based traffic steering
Mapping an AC to a cross-connect
Specifying a source address for the outer IPv6 header of SRv6-encapsulated EVPN VPWS packets
Configuring FRR for EVPN VPWS over SRv6
Configuring LDP or static PWs as ACs for SRv6 PWs
About LDP or static PW AC configuration for SRv6 PWs
Restrictions and guidelines for LDP or static PW AC configuration for SRv6 PWs
Prerequisites for LDP or static PW AC configuration for SRv6 PWs
Configuring LDP PWs as ACs for SRv6 PWs
Configuring static PWs as ACs for SRv6 PWs
Test the connectivity of an SRv6 PW
Using ping to test the connectivity of an SRv6 PW
Using tracert to test the connectivity of an SRv6 PW
Using a static BFD session to test the connectivity of an SRv6 PW
Display and maintenance commands for EVPN VPWS over SRv6
Configuring EVPN VPWS over SRv6
About EVPN VPWS over SRv6
EVPN VPWS over SRv6 uses SRv6 tunnels to carry EVPN VPWS services. This technology establishes point-to-point connections between customer sites over the IPv6 backbone network and transparently forwards Layer 2 customer traffic over the IPv6 backbone network. For more information about EVPN VPWS configuration, see EVPN Configuration Guide.
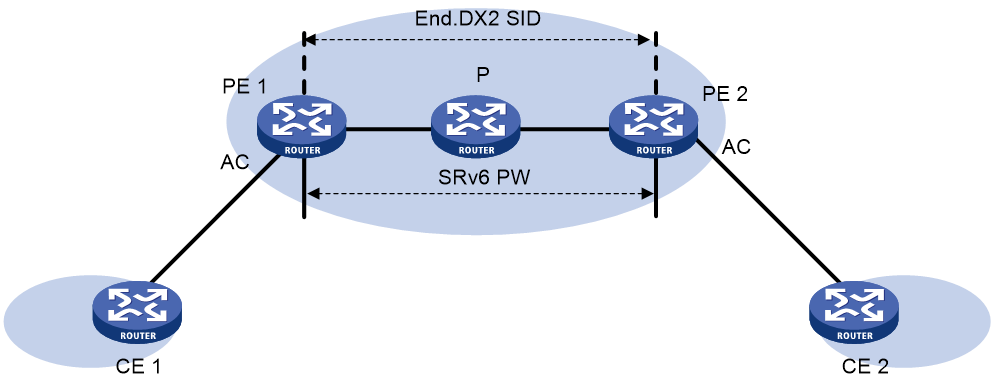
EVPN VPWS over SRv6 network model
As shown in Figure 1, the two PEs set up an SRv6 tunnel after assigning End.DX2 SIDs to the cross-connect. On a PE, this SRv6 tunnel is used as an SRv6 PW to encapsulate and forward Layer 2 data packets received from the local site and destined for a remote site. The devices on the IPv6 backbone transport network forward the SRv6-encapsulated packets according to the optimal routes calculated by an IGP. As a result, Layer 2 data packets of one customer site can be transparently forwarded to another site over the IPv6 backbone transport network.
Figure 1 Typical networking for EVPN VPWS over SRv6
SRv6 PW establishment
SRv6 PWs can be established dynamically or statically.
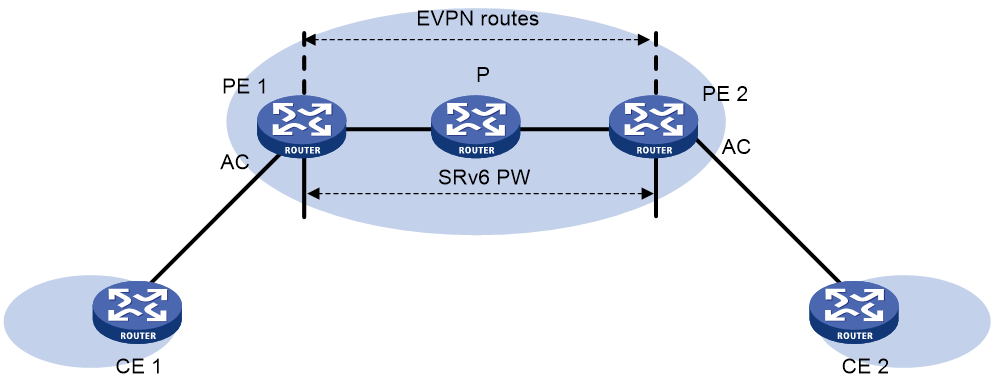
Dynamic SRv6 PW establishment
As shown in Figure 2, dynamic SRv6 PW establishment is implemented through End.DX2 SID advertisement in EVPN routes between PEs.
Figure 2 Dynamic SRv6 PW establishment
A pair of PEs use BGP EVPN routes to establish PWs as follows:
1. A PE adds the local service ID and End.DX2 SID of a local cross-connect to Ethernet auto-discovery routes and advertises the routes to the remote PE.
2. After receiving the routes, the remote PE checks the service ID carried in the routes. If the service ID is the same as the remote service ID configured locally for a cross-connect, the PE establishes an SRv6 tunnel to the other PE. The SID flag of the SRv6 tunnel is the End.DX2 SID in the routes.
The two PEs both advertise End.DX2 SIDs to each other and establish two SRv6 tunnels at two directions. The two SRv6 tunnels form a PW to carry Layer 2 customer traffic. The PW is called an SRv6 PW.
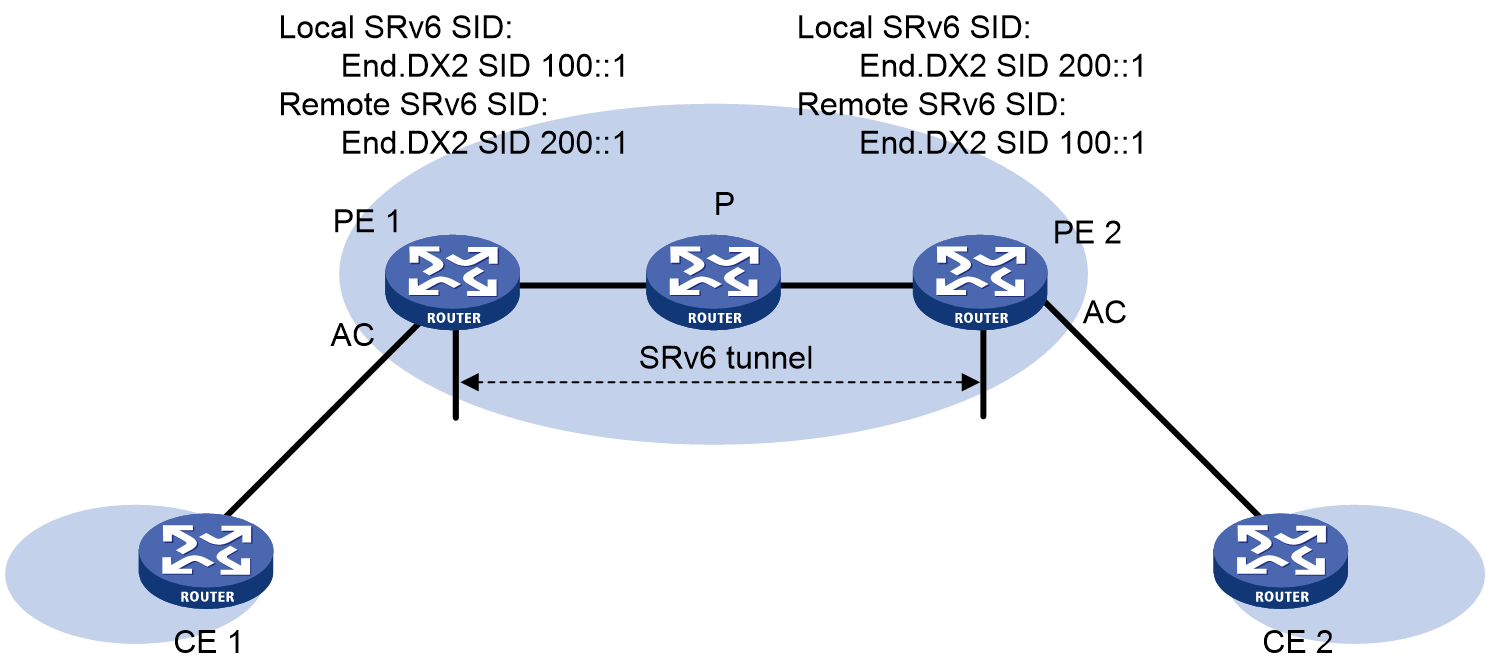
Static SRv6 PW establishment
As shown in Figure 3, static SRv6 PW establishment is implemented through configuring SRv6 SIDs to be assigned to the cross-connect by the local and remote ends.
Figure 3 Static SRv6 PW establishment
Traffic forwarding
EVPN VPWS over SRv6 supports the following packet forwarding modes:
· SRv6 BE mode.
· SRv6 TE mode.
· SRv6 TE and SRv6 BE hybrid mode.
The packet forwarding process differs by the packet forwarding mode in use.
SRv6 BE mode
This mode is also called SID-based forwarding mode. In this mode, a PE forwards an SRv6 packet by searching the IPv6 routing table based on the End.DX2 SID encapsulated in the packet. A layer 2 packet is forwarded from CE 1 to CE 2 as follows:
1. CE 1 sends the Layer 2 packet to PE 1.
2. After PE 1 receives the packet on the AC connected to CE 1, it searches for the SRv6 PW (SRv6 tunnel) associated with the AC and finds the End.DX2 SID to reach PE 2.
3. PE 1 encapsulates the outer IPv6 header and SRH header for the packet. The End.DX2 SID is encapsulated in the outer IPv6 header as the destination IPv6 address. The source IPv6 address is the source address specified for the outer IPv6 header of SRv6-encapsulated EVPN VPWS packets.
4. PE 1 searches the IPv6 routing table based on the End.DX2 SID for the optimal IGP route and forwards the packet to P through the optimal IGP route.
5. P searches the IPv6 routing table based on the End.DX2 SID for the optimal IGP route and forwards the packet to PE 2 through the optimal IGP route.
6. PE 2 searches the local SID forwarding table for the End.DX2 SID and performs the following operations:
a. Removes the outer IPv6 header.
b. Matches the packet to an AC based on the End.DX2 SID.
c. Forwards the packet to CE 2 through the AC.
SRv6 TE mode
This mode is also called SRv6 TE policy-based forwarding mode. In this mode, when a PE forwards a customer packet, it first searches for a matching SRv6 TE policy based on the packet attributes. Then, the PE adds an SRH to the packet. The SRH includes the destination End.DX2 SID and the SID list of the SRv6 TE policy. Finally, the PE forwards the encapsulated packet based on the SRv6 TE policy.
In a network where the SRv6 PWs are dynamically established, the following modes are available to steer traffic to an SRv6 TE policy:
· Color—The device searches for an SRv6 TE policy that has the same color and endpoint address as the color and nexthop address of a BGP EVPN route. If a matching SRv6 TE policy exists, the device recurses the BGP EVPN route to that SRv6 TE policy. When the device receives packets that match the BGP EVPN route, it forwards the packets through the SRv6 TE policy.
· Tunnel policy—The device searches the tunnel policies for a matching SRv6 TE policy based on the next hop of a matching route. Configure a preferred tunnel or load sharing tunnel policy that uses the SRv6 TE policy. In this way, the SRv6 TE policy will be used as the public tunnel to carry the SRv6 PW that forwards the packets of private network packets.
In a network where the SRv6 PWs are statically established, the following modes are available to steer traffic to an SRv6 TE policy:
· Color—The PE searches for an SRv6 TE policy that has the same color and endpoint address as the color and remote PE address of a static SRv6 PW. If a matching static SRv6 TE policy exists, the device recurses the forwarding path of the static SRv6 PW to that SRv6 TE policy. When the device receives packets that match the SRv6 PW, it forwards the packets through the SRv6 TE policy.
· Tunnel policy—The PE searches the tunnel policies for a matching SRv6 TE policy based on the remote PE address of a matching static SRv6 PW. Configure a preferred tunnel or load sharing tunnel policy that uses the SRv6 TE policy. In this way, the SRv6 TE policy will be used as the public tunnel to carry the SRv6 PW that forwards the packets of private network packets.
For more information about tunnel policies, see MPLS Configuration Guide. For more information about SRv6 TE policies, see "Configuring SRv6 TE policies."
SRv6 TE and SRv6 BE hybrid mode
In this mode, the PE preferentially uses the SRv6 TE mode to forward a packet. If no SRv6 TE policy is available for the packet, the PE forwards the packet in SRv6 BE mode.
EVPN VPWS over SRv6 multihoming
About EVPN VPWS over SRv6 multihoming
As shown in Figure 4, EVPN VPWS over SRv6 supports deploying multiple PEs at a site for redundancy and high availability. On the redundant PEs, Ethernet links connected to the site form an Ethernet segment (ES) that is uniquely identified by an ES identifier (ESI). EVPN VPWS over SRv6 supports only dualhoming.
Figure 4 EVPN VPWS over SRv6 multihoming
Redundancy mode
The device supports single-active redundancy mode and all-active redundancy mode of EVPN VPWS over SRv6 multihoming.
· All-active mode—This mode allows all redundant PWs to a multihomed site to load share traffic.
· Single-active mode—This mode allows one of the redundant PWs to forward traffic. When the main PW becomes unavailable because of device failure or link failure, traffic is switched to the secondary PW for forwarding. A designated forwarder (DF) is elected from the redundant PEs to determine the main PW. For more information about DF election, see EVPN VPWS configuration in EVPN Configuration Guide.
Route advertisement
The redundant PEs at a multihomed site both advertise End.DX2 SIDs to remote PEs. In addition, they advertise the redundancy mode of the multihomed site and their roles (primary or secondary) to remote PEs. A remote PE handles BGP EVPN routes advertised by the redundant PEs based on the redundancy mode.
· In all-active mode, the remote PE treats the routes advertised by the redundant PEs as ECMP routes that can load share traffic.
· In single-active mode, the remote PE treats the routes advertised by the primary PE as the optimal routes and only uses the optimal routes to forward traffic.
EVPN VPWS over SRv6 FRR
About FRR
EVPN VPWS over SRv6 Fast reroute (FRR) helps reduce the traffic loss caused by AC or PW failure on an EVPN VPWS over SRv6 network. FRR includes local FRR and remote FRR.
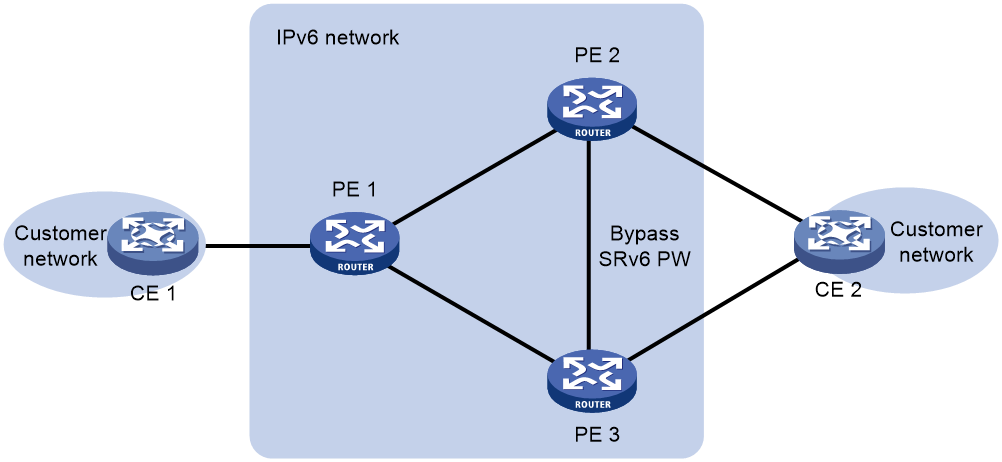
Local FRR
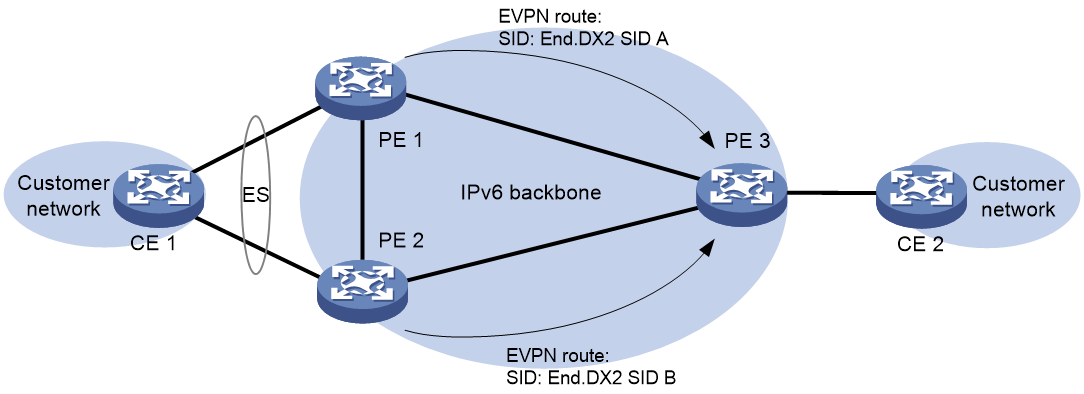
Local FRR enables two PEs at a multihomed EVPN VPWS over SRv6 network site or a primary/backup SRv6 PW site to set up a bypass SRv6 PW between them.
As shown in Figure 5, CE 2 is dualhomed to PE 2 and PE 3. When the AC on PE 2 fails, PE 2 advertises the local unreachable event to PE 1 and PE 3 for PE 1 to switch traffic to the PW to PE 3. In this situation, PE 3 drops the packets that PE 1 sends before it is notified of the local unreachable event. To resolve this issue, enable local FRR on PE 2 and PE 3. When receiving packets from PE 1 after PE 2's AC fails, PE 2 forwards the packets to PE 3 over the bypass SRv6 PW to prevent traffic loss.
A loop might exist if PE 2 and PE 3 establish a bypass SRv6 PW between them through End.DX2 SIDs. When the AC on PE 2 or PE 3 fails, PE 2 or PE 3 forwards the packets received from its peer back to its peer through the bypass SRv6 PW. To resolve this issue, use End.DX2L SIDs to establish a bypass SRv6 PW between PE 2 and PE 3. The packets from a bypass SRv6 PW carry an End.DX2L SID. A PE does not forward the packets back to the bypass SRv6 PW.
PEs preferentially use End.DX2L SIDs to establish a bypass SRv6 PW. If no End.DX2L SIDs are available, the PEs use End.DX2 SIDs to establish a bypass SRv6 PW.
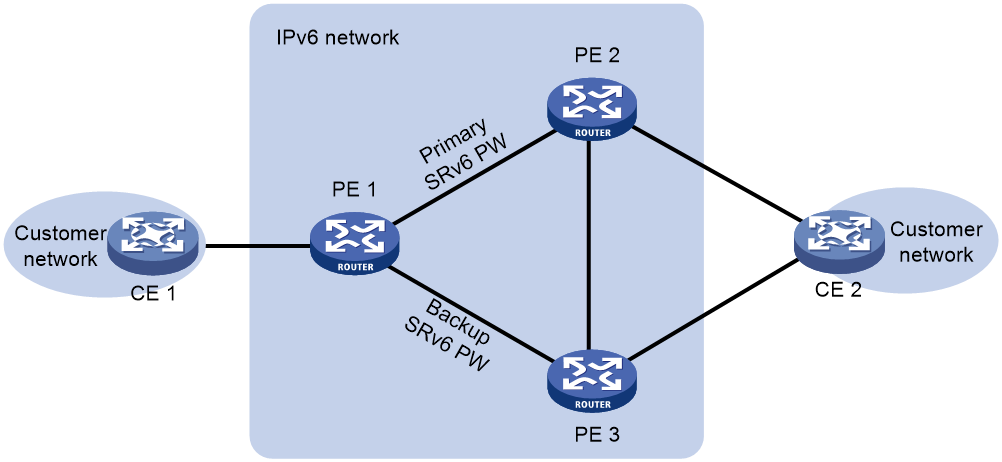
Remote FRR
Remote FRR enables two PEs on an EVPN VPWS over SRv6 network to set up a primary SRv6 PW and a backup SRv6 PW between them to ensure high availability. This feature is applicable to both multihoming and singlehoming scenarios.
As shown in Figure 6, PE 1 is connected to PE 2 and PE 3. For high availability, you can enable remote FRR on PE 1 for it to set up PWs to both PE 2 and PE 3. PE 1 uses the primary SRv6 PW to forward traffic as long as it is available. When the primary SRv6 PW fails, PE 1 switches traffic destined for CE 2 to the backup SRv6 PW. When PE 3 receives the traffic from the backup SRv6 PW, it forwards the traffic to CE 2. When CE 2 receives the traffic, it updates the MAC address table and switches the traffic destined for CE 1 to the link connected to PE 3. The switchover reduces packet loss.
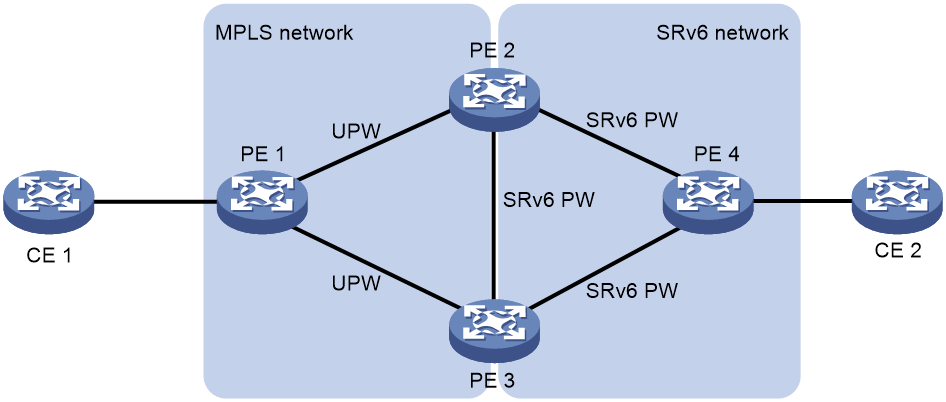
LDP or static PW ACs for SRv6 PWs
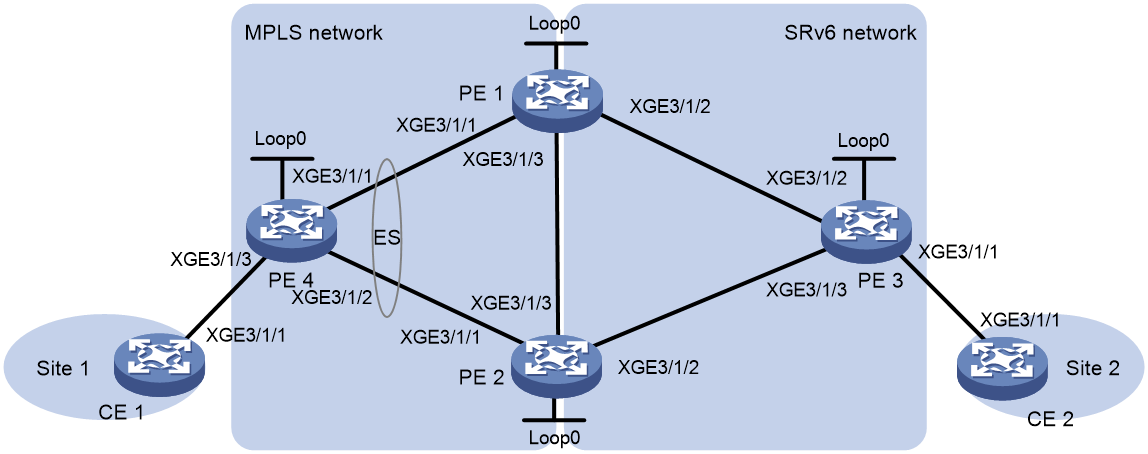
This feature ensures that a traditional MPLS L2VPN network (or VPWS network) and an EVPN VPWS over SRv6 network can communicate with each other. The LDP or static PWs in the MPLS L2VPN network are configured as ACs to the SRv6 PWs in the EVPN VPWS over SRv6 network. These ACs are referred to as UPWs in the EVPN VPWS over SRv6 network. Packets can be forwarded between SRv6 PWs and UPWs, so the MPLS L2VPN and EVPN VPWS over SRv6 networks can communicate with each other.
With this feature, an LDP or static PW can be single-homed to an SRv6 PW or two LDP or static PWs can be dual-homed to two SRv6 PWs.
As shown in Figure 7, in the MPLS L2VPN network, PE 1 is connected to PE 2 and PE 3 through LDP or static PWs. One of the PWs is the primary PW and the other PW is the backup PW. The PWs are UPWs. In the EVPN VPWS over SRv6 network, PE 4 is connected to PE 2 and PE 3 through SRv6 PWs. The UPWs in the MPLS L2VPN network act as ACs for the SRv6 network. When PE 2 or PE 3 receives packets from an UPW, it decapsulates MPLS encapsulation from the packets and searches for the SRv6 PW associated with the UPW. Then, the PE adds SRv6 encapsulation to the packets and forwards the packets to PE 4. When PE 2 or PE 3 receives packets from an SRv6 PW, it uses the same procedure to process the packets.
Figure 7 LDP or static PW ACs for SRv6 PWs
Intercommunication between EVPN VPLS over SRv6 and EVPN VPWS over SRv6 networks
In an EVPN VPWS over SRv6 network, an SRv6 PW can be associated only with one AC. If multiple ACs are attached to a PE, the PE cannot use the same SRv6 PW to forward traffic for the ACs. For the PE to use the same SRv6 PW to forward traffic for the ACs, configure intercommunication between EVPN VPLS over SRv6 and EVPN VPWS over SRv6 networks. With this feature, you can associate an SRv6 PW with multiple ACs on the PE without changing existing SRv6 PW and AC associations in the EVPN VPWS over SRv6 network. The PE where an SRv6 PW is associated with multiple ACs acts as a boundary PE between the EVPN VPWS over SRv6 and EVPN VPLS over SRv6 networks.
For more information about configuring intercommunication between EVPN VPLS over SRv6 and EVPN VPWS over SRv6 networks, see "Configuring EVPN VPLS over SRv6."
Restrictions and guidelines: EVPN VPWS over SRv6 configuration
In standard system operating mode, only the following cards support this feature:
|
Card category |
Cards |
|
CEPC |
CEPC-CQ8L, CEPC-CQ8LA, CEPC-CQ8L1A, CEPC-CQ16L1 |
|
CSPEX |
CSPEX-1802X, CSPEX-1802XA, CSPEX-2612XA, CSPEX-1812X-E, CSPEX-2304X-G, CSPEX-1502XA |
|
SPE |
RX-SPE200-E |
In SDN-WAN system operating mode, only the following cards support this feature:
|
Card category |
Cards |
|
CEPC |
CEPC-XP4LX, CEPC-XP24LX, CEPC-XP48RX, CEPC-CP4RX, CEPC-CP4RXA, CEPC-CP4RX-L, CEPC-CQ8L, CEPC-CQ8LA, CEPC-CQ8L1A, CEPC-CQ16L1 |
|
CSPEX |
CSPEX-1304X, CSPEX-1404X, CSPEX-1502X, CSPEX-1504X, CSPEX-1504XA, CSPEX-1602X, CSPEX-1602XA, CSPEX-1804X, CSPEX-1512X, CSPEX-1612X, CSPEX-1812X, CSPEX-1802X, CSPEX-1802XA, CSPEX-2612XA, CSPEX-1812X-E, CSPEX-2304X-G, CSPEX-1502XA |
|
SPE |
RX-SPE200, RX-SPE200-E |
Configuring EVPN VPWS over SRv6 with dynamic PWs
EVPN VPWS over SRv6 tasks at a glance (with dynamic PWs)
To configure EVPN VPWS over SRv6 with dynamic PWs, perform the following tasks:
1. Configuring a cross-connect
3. Applying a locator to a cross-connect
4. Configuring PEs to exchange BGP EVPN routes
5. Configuring packet forwarding methods
¡ Configuring the route recursion mode
¡ Configuring SRv6 TE policy traffic steering
This task is required if the route recursion mode is SRv6 TE mode or SRv6 TE and SRv6 BE hybrid mode.
6. Mapping an AC to a cross-connect
7. Specifying a source address for the outer IPv6 header of SRv6-encapsulated EVPN VPWS packets
8. (Optional.) Improving availability of the EVPN VPWS over SRv6 network
¡ Configuring EVPN VPWS over SRv6 multihoming
¡ Configuring FRR for EVPN VPWS over SRv6
9. (Optional.) Configuring LDP or static PWs as ACs for SRv6 PWs
10. (Optional.) Maintaining the EVPN VPWS over SRv6 network
¡ Configuring SRv6 PW packet statistics
¡ Test the connectivity of an SRv6 PW
Configuring a cross-connect
1. Enter system view.
system-view
2. Enable L2VPN.
system-view
l2vpn enable
By default, L2VPN is disabled.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
3. Create a cross-connect group and enter its view.
xconnect-group group-name
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
4. (Optional.) Configure a description for the cross-connect group.
description text
By default, no description is configured for a cross-connect group.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
5. (Optional.) Bring up the cross-connect group.
undo shutdown
By default, a cross-connect group is not administratively down.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
6. Create an EVPN instance for the cross-connect group and enter its view.
evpn encapsulation srv6
7. Configure an RD for the EVPN instance.
route-distinguisher route-distinguisher
By default, no RD is configured for the EVPN instance of a cross-connect group.
For more information about this command, see EVPN commands in EVPN Command Reference.
8. Configure route targets for the EVPN instance.
vpn-target { vpn-target&<1-8> } [ both | export-extcommunity | import-extcommunity ]
By default, no route targets are configured for the EVPN instance of a cross-connect group.
For more information about this command, see EVPN commands in EVPN Command Reference.
|
Parameter |
Description |
|
export-extcommunity |
Do not specify the same export targets for the EVPN instances of different cross-connect groups. Do not specify the same export targets for the EVPN instances of a cross-connect group and a VSI. As a best practice, the export targets of the EVPN instance of a cross-connect group do not match the import targets configured in VPN instance view, VPN instance EVPN view, public instance view, public instance EVPN view, or VSI EVPN instance view. |
|
import-extcommunity |
As a best practice, the import targets of the EVPN instance of a cross-connect group do not match the export targets configured in VPN instance view, VPN instance EVPN view, public instance view, public instance EVPN view, or VSI EVPN instance view. |
9. Return to cross-connect group view.
quit
10. Create a cross-connect and enter its view.
connection connection-name
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
Configuring SRv6 SIDs
Restrictions and guidelines
For more information about the commands in this section, see SRv6 commands in Segment Routing Command Reference.
Procedure
1. Enter system view.
system-view
2. Enable SRv6 and enter SRv6 view.
segment-routing ipv6
3. Configure a locator and enter SRv6 locator view.
locator locator-name [ ipv6-prefix ipv6-address prefix-length [ args args-length | static static-length ] * ]
4. Configure an opcode for End.DX2 SIDs.
opcode { opcode | hex hex-opcode } end-dx2 xconnect-group group-name connection connection-name
5. (Optional.) Configure an opcode for End.DX2L SIDs.
opcode { opcode | hex hex-opcode } end-dx2l xconnect-group group-name connection connection-name
Use this command only in the bypass PW network.
Applying a locator to a cross-connect
About this task
Perform this task to apply a locator to a cross-connect for the cross-connect to apply for End.DX2 and End.DX2L SIDs from the locator.
Procedure
1. Enter system view.
system-view
2. (Optional.) Configure a PW class.
a. Create a PW class and enter its view.
pw-class class-name
For more information about this command, see MPLS Command Reference.
b. Configure the SRv6 PW data encapsulation type for the PW class.
srv6-pw-type { ethernet | vlan }
By default, the SRv6 PW data encapsulation type for the PW class is Ethernet.
c. Return to system view.
quit
3. Enter cross-connect group view.
xconnect-group group-name
4. Enter cross-connect view.
connection connection-name
5. Apply a locator to the cross-connect.
segment-routing ipv6 locator locator-name [ dx2l-locator dx2l-locator-name ] [ auto-sid-disable ]
By default, no locator is applied to a cross-connect.
6. Create an SRv6 PW and enter SRv6 PW view.
evpn local-service-id local-service-id remote-service-id remote-service-id [ tunnel-policy tunnel-policy-name ]
For more information about this command, see EVPN commands in EVPN Command Reference.
Configuring PEs to exchange BGP EVPN routes
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Configure an IPv6 peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } as-number as-number
For more information about this command, see BGP commands in Layer 3—IP Routing Command Reference.
4. Specify the source interface of TCP connections to a peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } connect-interface interface-type interface-number
By default, BGP uses the IPv6 address of the output interface in the optimal route to the BGP peer or peer group as the source address of TCP connections to the peer or peer group.
For more information about this command, see BGP commands in Layer 3—IP Routing Command Reference.
5. Enter BGP EVPN address family view.
address-family l2vpn evpn
For more information about this command, see EVPN Command Reference.
6. Enable BGP to exchange EVPN routes with an IPv6 peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } enable
By default, BGP cannot exchange EVPN routes with an IPv6 peer or peer group.
For more information about this command, see BGP commands in Layer 3—IP Routing Command Reference.
7. Enable BGP to advertise SRv6-encapsulated BGP EVPN routes to a peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } advertise encap-type srv6
By default, BGP advertises VXLAN-encapsulated BGP EVPN routes to a peer or peer group.
Configuring the route recursion mode
About this task
After a PE receives a customer packet destined for an End.DX2 or End.DX2L SID, it forwards the packet according to the route recursion mode.
· SRv6 BE mode—This mode is also called SID-based forwarding mode. In this mode, the PE first encapsulates the End.DX2 or End.DX2L SID into the packet. Then, the PE searches the IPv6 routing table based on the End.DX2 or End.DX2L SID encapsulated in the packet to forward the packet.
· SRv6 TE mode—This mode is also called SRv6 TE policy-based forwarding mode. In this mode, the PE first searches for a matching SRv6 TE policy based on the packet attributes. Then, the PE adds an SRH to the packet. The SRH includes the End.DX2 or End.DX2L SID and the SID list of the SRv6 TE policy. Finally, the PE forwards the encapsulated packet through the SRv6 TE policy. For more information, see "Configuring SRv6 TE policies."
· SRv6 TE and SRv6 BE hybrid mode—In this mode, the PE preferentially uses the SRv6 TE mode to forward the packet. If no SRv6 TE policy is available for the packet, the PE forwards the packet in SRv6 BE mode.
In SRv6 TE mode, you can associate the SRv6 TE policy that contains paths between two PEs with the static BFD session specified for testing the IP connectivity between the PEs. For this purpose, you must execute the segment-routing ipv6 traffic-engineer command with the track-bfd keyword and create a static BFD session to test the IP connectivity between the two PEs. If the static BFD session goes down, the state of the SRv6 TE policy also changes to down. This mechanism avoids traffic forwarding failure caused by path disconnectivity. For more information about static BFD, see High Availability Configuration Guide. For more information about testing the IP connectivity between two PEs, see "Using a static BFD session to test the connectivity of an SRv6 PW."
Prerequisites
To use the SRv6 TE mode or the SRv6 TE and SRv6 BE hybrid mode, you must configure a tunnel policy and SRv6 TE policy. For more information, see tunnel policy configuration in MPLS Configuration Guide and "Configuring SRv6 TE policies."
Procedure
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect group EVPN instance view.
evpn encapsulation srv6
4. Configure the route recursion mode.
segment-routing ipv6 { best-effort | traffic-engineering [ track-bfd ] [ best-effort ] }
By default, a PE searches the IPv6 routing table based on the next hop of a matching route to forward traffic.
Configuring SRv6 TE policy traffic steering
Restrictions and guidelines for SRv6 TE policy traffic steering
This task is required if the route recursion mode is SRv6 TE mode or SRv6 TE and SRv6 BE hybrid mode.
If both color-based traffic steering and tunnel policy-based traffic steering are configured, the device performs traffic steering in the following sequence:
· Performs tunnel policy-based traffic steering.
· Performs color-based traffic steering.
· Performs traffic steering based on the preferred tunnel policy. (The tunnel policy does not take effect when color-based traffic steering is configured.)
· Performs traffic steering based on the load sharing tunnel policy. If this traffic steering method is not configured, the default tunnel policy applies.
Configuring color-based traffic steering
About this task
In a network where the SRv6 PWs are dynamically established, the PE searches for an SRv6 TE policy that has the same color and endpoint address as the color and next hop address of a BGP EVPN route. If a matching SRv6 TE policy exists, the device recurses the route to that SRv6 TE policy. When the device receives packets that match the route, it forwards the packets through the SRv6 TE policy.
Use one of the following methods to configure colors for BGP EVPN routes:
· Routing policy-based coloring—Configure a routing policy to add the color extended community attribute to BGP EVPN routes or modify the existing color extended community attribute in BGP EVPN routes.
· Default color—Specify a color as the default color for BGP EVPN routes. A BGP EVPN route uses the default color for color-based traffic steering if the route does not have the color extended community attribute or match a routing policy to obtain a color.
Restrictions and guidelines
Traffic steering is based on the greatest value among the color extended community attributes when the following conditions exist:
· You specify the additive keyword for the apply extcommunity color clause in a routing policy, and specify the routing policy for the import route-policy command.
· The received BGP EVPN routes carry the color extended community attribute.
Configuring routing policy-based coloring
1. Enter system view.
system-view
2. Enter routing policy node view.
route-policy route-policy-name { deny | permit } node node-number
For more information about this command, see routing policy commands in Layer 3—IP Routing Command Reference.
3. Set the color extended community attribute for BGP routes.
apply extcommunity color color [ additive ]
By default, no color extended community attribute is set for BGP routes.
For more information about this command, see routing policy commands in Layer 3—IP Routing Command Reference.
4. Return to system view.
quit
5. Enter cross-connect group view.
xconnect-group group-name
6. Enter EVPN instance view of the cross-connect group.
evpn encapsulation srv6
7. Apply the routing policy as an export policy to the EVPN instance.
export route-policy route-policy
By default, no export routing policy is applied to an EVPN instance. The EVPN instance does not filter advertised routes.
For more information about this command, see EVPN Command Reference.
8. Apply the routing policy as an import policy to the EVPN instance.
import route-policy route-policy
By default, no import routing policy is applied to an EVPN instance. The EVPN instance does not filter received routes.
For more information about this command, see EVPN Command Reference.
Configuring the default color for BGP EVPN routes
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter EVPN instance view of the cross-connect group.
evpn encapsulation srv6
4. Configure the default color for BGP EVPN routes.
default color color-value
By default, no default color is configured for BGP EVPN routes.
Configuring tunnel policy-based traffic steering
About this task
In a network where the SRv6 PWs are dynamically established, the PE searches the tunnel policies for a matching SRv6 TE policy based on the next hop of a matching route. Configure a preferred tunnel or load sharing tunnel policy that uses the SRv6 TE policy. In this way, the SRv6 TE policy will be used as the public tunnel to carry the SRv6 PW that forwards the packets of private network packets. For more information about tunnel policies, see MPLS Configuration Guide.
Configuring a tunnel policy
1. Enter system view.
system-view
2. Create a tunnel policy and enter tunnel policy view.
tunnel-policy tunnel-policy-name [ default ]
3. Configure the tunnel policy. Choose a minimum of one option:
¡ Specify an SRv6 TE policy as a preferred tunnel of the tunnel policy.
preferred-path srv6-policy { name srv6-policy-name | end-point ipv6 ipv6-address color color-value }
By default, no preferred tunnel is specified for a tunnel policy.
¡ Configuring SRv6 TE policy load sharing for the tunnel policy.
select-seq srv6-policy load-balance-number number
By default, no load sharing tunnel policy is configured.
For more information about the tunnel policy commands, see MPLS Command Reference.
Specifying the tunnel policy for a PW
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect view.
connection connection-name
4. Create an SRv6 PW and specify a tunnel policy for this PW.
evpn local-service-id local-service-id remote-service-id remote-service-id tunnel-policy tunnel-policy-name
Mapping an AC to a cross-connect
Mapping a Layer 3 interface to a cross-connect
Procedure
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect view.
connection connection-name
4. Map a Layer 3 interface to the cross-connect.
ac interface interface-type interface-number [ access-mode { ethernet | vlan } ] [ track track-entry-number&<1-15> ]
By default, no Layer 3 interface is bound to the cross-connect.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
Specifying a source address for the outer IPv6 header of SRv6-encapsulated EVPN VPWS packets
Restrictions and guidelines
To ensure correct traffic forwarding in an EVPN VPWS over SRv6 network, you must specify a source address for the outer IPv6 header of SRv6-encapsulated EVPN VPWS packets.
You cannot specify a loopback address, link-local address, multicast address, or unspecified address as the source IPv6 address. You must specify an IPv6 address of the local device as the source IPv6 address, and make sure the IPv6 address has been advertised by a routing protocol. As a best practice, specify a loopback interface address of the local device as the source IPv6 address.
Procedure
1. Enter system view.
system-view
2. Enter SRv6 view.
segment-routing ipv6
3. Specify a source address for the outer IPv6 header of SRv6-encapsulated EVPN VPWS packets.
encapsulation source-address ipv6-address [ ip-ttl ttl-value ]
By default, no source address is specified for the outer IPv6 header of SRv6-encapsulated EVPN VPWS packets.
Configuring EVPN VPWS over SRv6 multihoming
Restrictions and guidelines for EVPN VPWS over SRv6 multihoming
You must configure the same local and remote service IDs on the redundant PEs at a multihomed site.
As a best practice, set the same redundancy mode on the interfaces that act as ACs or are configured with ACs on the redundant PEs at a multihomed site.
You can assign an ESI to both a main interface and its subinterfaces:
· The ESI assigned to a subinterface takes precedence over the ESI assigned to the main interface. If you assign an ESI to a subinterface, the redundancy mode configured on the subinterface applies.
· If you assign an ESI only to the main interface, both the ESI and redundancy mode settings on the main interface apply to the associated subinterfaces. The redundancy mode configured on the subinterfaces will not take effect.
Assigning an ESI to an interface
About this task
An ESI uniquely identifies an ES. The links on interfaces with the same ESI belong to the same ES. Traffic of the ES can be distributed among the links for load sharing.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
¡ Enter Layer 2 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
¡ Enter Layer 3 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 3 aggregate interface view.
interface route-aggregation interface-number
¡ Enter FlexE physical interface view.
interface interface-type interface-number
¡ Enter FlexE logical interface view.
interface flexe interface-number
3. Assign an ESI to the interface.
esi esi-id
By default, no ESI is assigned to an interface.
For more information about this command, see EVPN commands in EVPN Command Reference.
Setting the redundancy mode on an interface
About this task
EVPN VPWS over SRv6 multihoming provides the single-active redundancy mode and all-active redundancy mode.
The redundant PEs at a dualhomed site each establish a PW to a remote PE. To use one PW as a backup of the other PW, use the single-active mode. To distribute traffic across the PWs for load sharing, use the all-active mode.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
¡ Enter Layer 2 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
¡ Enter Layer 3 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 3 aggregate interface view.
interface route-aggregation interface-number
¡ Enter FlexE physical interface view.
interface interface-type interface-number
¡ Enter FlexE logical interface view.
interface flexe interface-number
3. Set the redundancy mode.
evpn redundancy-mode { all-active | single-active }
By default, the all-active redundancy mode is used.
For more information about this command, see EVPN commands in EVPN Command Reference.
Enabling cross-connects to ignore the state of ACs
About this task
This task helps reduce the traffic loss caused by AC failure at a multihomed EVPN VPWS over SRv6 network site that uses single-active redundancy mode.
At a multihomed EVPN VPWS network site that uses single-active redundancy mode, CE 1 is dualhomed to PE 1 and PE 2 through a smart trunk. PE 1 is the primary PE, and PE 2 is the secondary PE. When the AC on PE 1 fails, PE 1 and PE 2 act as follows:
· PE 1 withdraws advertised Ethernet auto-discovery routes.
· PE 2 brings up its AC and advertises Ethernet auto-discovery routes to remote PEs.
The remote PEs switch traffic to the paths to PE 2 only after receiving the Ethernet auto-discovery routes advertised by PE 2, and traffic loss occurs during path switchover. To resolve this issue, enable cross-connects to ignore the state of ACs on PE 2. This feature allows PE 2 to advertise Ethernet auto-discovery routes to remote PEs regardless of the state of ACs and speeds up path switchover when the AC on PE 1 fails.
Restrictions and guidelines for AC state ignore configuration
On a cross-connect, cross-connect-specific AC state ignore configuration takes precedence over global AC state ignore configuration.
Enabling cross-connects to ignore the state of ACs globally
1. Enter system view.
system-view
2. Enable cross-connects to ignore the state of ACs globally.
l2vpn ignore-ac-state [ evpn-vpws ]
By default, cross-connects does not ignore the state of ACs.
Configuring a cross-connect to ignore the state of ACs
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect view.
connection connection-name
4. Enable the cross-connect to ignore the state of ACs or disable a cross-connect from ignoring the state of ACs.
ignore-ac-state { enable | disable }
By default, a cross-connect uses the global AC state ignore configuration.
Configuring FRR for EVPN VPWS over SRv6
Configuring local FRR
About this task
Local FRR enables two PEs at a multihomed EVPN VPWS over SRv6 network site to set up a dynamic bypass SRv6 PW between them. This feature helps reduce the traffic loss caused by AC failure.
Restrictions and guidelines
On an EVPN instance, EVPN instance-specific local FRR configuration takes precedence over global local FRR configuration.
If you have executed the evpn frr local enable command on an EVPN instance, the undo evpn multihoming vpws-frr local command does not delete the bypass SRv6 PW of the EVPN instance.
Perform this task on the redundant PEs at a multihomed site.
Enabling local FRR globally
1. Enter system view.
system-view
2. Enable local FRR globally for EVPN VPWS over SRv6.
evpn multihoming vpws-frr local
By default, local FRR is disabled globally for EVPN VPWS over SRv6.
For more information about this command, see EVPN Command Reference.
Configuring local FRR on an EVPN instance
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter EVPN instance view.
evpn encapsulation srv6
4. Configure local FRR for EVPN VPWS over SRv6.
evpn frr local { disable | enable }
By default, an EVPN instance uses the global local FRR configuration of EVPN VPWS over SRv6.
For more information about this command, see EVPN Command Reference.
Configuring remote FRR
About this task
Remote FRR enables two PEs on an EVPN VPWS over SRv6 network to set up a primary PW and a backup PW between them to ensure high availability. The PEs use the primary PW to forward traffic as long as it is available. When the primary PW fails, the PEs switch traffic to the backup PW.
Restrictions and guidelines
On an EVPN instance, EVPN instance-specific remote FRR configuration takes precedence over global remote FRR configuration.
If you have executed the evpn frr remote enable command on an EVPN instance, the undo evpn vpws-frr remote command does not delete the backup SRv6 PWs of the EVPN instance.
Enabling remote FRR globally
1. Enter system view.
system-view
2. Enable remote FRR globally for EVPN VPWS over SRv6.
evpn vpws-frr remote
By default, remote FRR is disabled globally for EVPN VPWS over SRv6.
For more information about this command, see EVPN Command Reference.
Configuring remote FRR on an EVPN instance
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter EVPN instance view.
evpn encapsulation srv6
4. Configure remote FRR for EVPN VPWS over SRv6.
evpn frr remote { disable | enable }
By default, an EVPN instance uses the global remote FRR configuration of EVPN VPWS over SRv6.
For more information about this command, see EVPN Command Reference.
Configuring LDP or static PWs as ACs for SRv6 PWs
About LDP or static PW AC configuration for SRv6 PWs
Use this feature to ensure that an MPLS L2VPN network and an EVPN VPWS over SRv6 network can communicate with each other.
Restrictions and guidelines for LDP or static PW AC configuration for SRv6 PWs
At a multihomed site, all PEs must use the same local service ID and remote service ID in the same ES.
As a best practice, set the same redundancy mode for the UPWs that use the same ESI at a multihomed site.
If the all-active redundancy mode is used at a multihomed site, you must enable the dual receive feature for PW redundancy on the multihomed PEs. To enable this feature, use the protection dual-receive command.
Prerequisites for LDP or static PW AC configuration for SRv6 PWs
Complete the following tasks:
· In the MPLS network, complete MPLS L2VPN settings on the PEs.
· In the SRv6 network, complete EVPN VPWS over SRv6 settings on the PEs.
Configuring LDP PWs as ACs for SRv6 PWs
Restrictions and guidelines
The data encapsulation type of an LDP PW must be the same as the access mode of the ACs mapped to the same cross-connect as the LDP PW. If they are different, perform one of the following tasks:
· Use the pw-type command on the PW class to which the LDP PW belongs to change the PW data encapsulation type.
· Use the ac interface command for the ACs and specify the access-mode parameter in the command to change the access mode of the ACs.
Procedure
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect group EVPN instance view.
evpn encapsulation srv6
4. Return to cross-connect group view.
quit
5. Enter cross-connect view.
connection connection-name
6. Create an LDP PW for the cross-connect and enter cross-connect PW view.
peer ip-address pw-id pw-id [ ignore-standby-state ] [ admin | pw-class class-name | tunnel-policy tunnel-policy-name ] *
The LDP PW configured by using this command is an UPW, which acts as an AC for the EVPN VPWS over SRv6 network.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
7. (Optional.) Assign an ESI to the UPW.
esi esi-id
By default, no ESI is assigned to an UPW.
At a multihomed site, use this command on the PEs in the MPLS L2VPN and EVPN VPWS over SRv6 networks.
For more information about this command, see EVPN commands in EVPN Command Reference.
8. (Optional.) Set the redundancy mode of the UPW.
evpn redundancy-mode { all-active | single-active }
By default, the redundancy mode is all-active.
At a multihomed site, use this command on the PEs in the MPLS L2VPN and EVPN VPWS over SRv6 networks.
For more information about this command, see EVPN commands in EVPN Command Reference.
9. Configure a backup LDP PW for the cross-connect and enter cross-connect backup PW view.
backup-peer ip-address pw-id pw-id [ pw-class class-name | tunnel-policy tunnel-policy-name ] *
At a multihomed site, use this command on the multihomed PEs.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
10. Return to cross-connect view.
quit
quit
11. Create an SRv6 PW and enter SRv6 PW view.
evpn local-service-id local-service-id remote-service-id remote-service-id [ tunnel-policy tunnel-policy-name ]
For more information about this command, see EVPN Command Reference.
Configuring static PWs as ACs for SRv6 PWs
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect group EVPN instance view.
evpn encapsulation srv6
4. Return to cross-connect group view.
quit
5. Enter cross-connect view.
connection connection-name
6. Create a static PW for the cross-connect and enter cross-connect PW view.
peer ip-address pw-id pw-id in-label label-value out-label label-value [ admin | pw-class class-name | tunnel-policy tunnel-policy-name ] *
The static PW configured by using this command is an UPW, which acts as an AC for the EVPN VPWS over SRv6 network.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
7. (Optional.) Assign an ESI to the UPW.
esi esi-id
By default, no ESI is assigned to an UPW.
At a multihomed site, use this command on the PEs in the MPLS L2VPN and EVPN VPWS over SRv6 networks.
For more information about this command, see EVPN commands in EVPN Command Reference.
8. (Optional.) Set the redundancy mode of the UPW.
evpn redundancy-mode { all-active | single-active }
By default, the redundancy mode is all-active.
At a multihomed site, use this command on the PEs in the MPLS L2VPN and EVPN VPWS over SRv6 networks.
For more information about this command, see EVPN commands in EVPN Command Reference.
9. Configure a backup static PW for the cross-connect and enter cross-connect backup PW view.
backup-peer ip-address pw-id pw-id in-label label-value out-label label-value [ pw-class class-name | tunnel-policy tunnel-policy-name ] *
At a multihomed site, use this command on the multihomed PEs.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
10. Return to cross-connect view.
quit
quit
11. Create an SRv6 PW and enter SRv6 PW view.
evpn local-service-id local-service-id remote-service-id remote-service-id [ tunnel-policy tunnel-policy-name ]
For more information about this command, see EVPN Command Reference.
Configuring SRv6 PW packet statistics
About this task
When SRv6 PW packet statistics is enabled, you can use the display l2vpn peer srv6 verbose command to display SRv6 PW packet statistics. To clear SRv6 PW packet statistics, use the reset l2vpn statistics srv6-pw command.
Procedure
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect view.
connection connection-name
4. Enter SRv6 PW view.
evpn local-service-id local-service-id remote-service-id remote-service-id [ tunnel-policy tunnel-policy-name ]
5. Enable SRv6 PW packet statistics.
statistics enable
By default, SRv6 PW packet statistics is disabled.
Test the connectivity of an SRv6 PW
Using ping to test the connectivity of an SRv6 PW
About this task
In an EVPN VPWS over SRv6 network, a PE transmits data packets to a remote PE over an SRv6 PW. Perform this task to test the connectivity of the SRv6 PW from the local PE to the remote PE when packet loss or traffic interruption occurs between the PEs.
The test process is as follows:
1. The local PE constructs an MPLS echo request packet and searches for the SRv6 tunnel that matches the specified cross-connect group name, local service ID, and remote service ID. After obtaining the End.DX2 SID of the SRv6 tunnel, the PE adds a UDP header and an IPv6 header to the packet and forwards the packet to the remote PE.
2. Upon receiving the MPLS echo request packet, the remote PE replies to the request.
3. The local PE identifies the connectivity of the SRv6 PW based on whether it has received MPLS echo replies from the remote PE and the reply response time. In addition, the local PE outputs statistics about the ping operation.
Procedure
To test the connectivity of an SRv6 PW from the local PE to the remote PE in an EVPN VPWS over SRv6 network, execute the following command in any view:
ping evpn vpws srv6 xconnect-group group-name local-service-id remote-service-id [ end-op endop ] [ -a source-ipv6 | -c count | -h hop-limit | -m interval | -r reply-mode | -s packet-size | -t time-out | -tc tc ] *
Using tracert to test the connectivity of an SRv6 PW
About this task
In an EVPN VPWS over SRv6 network, a PE transmits data packets to a remote PE over an SRv6 PW. Perform this task to trace the path of the SRv6 PW from the local PE to the remote PE when packet loss or traffic interruption occurs between the PEs. This task helps you locate the failed nodes on the path.
The test process is as follows:
1. The local PE constructs an MPLS echo request packet and searches for the SRv6 tunnel that matches the specified cross-connect group name, local service ID, and remote service ID. After obtaining the End.DX2 SID of the SRv6 tunnel, the PE adds a UDP header and an IPv6 header to the packet and forwards the packet to the remote PE. In the IPv6 header, the value of the Hop limit field is set to 1.
2. When the next node receives the packet, the value of the Hop limit field changes to 0. Then, the node sends an ICMPv6 timeout packet to the first node (the local PE).
3. When the local PE receives the ICMPv6 timeout packet, it increases the value of the Hop limit field by one in the MPLS echo request packet. Then, the local PE forwards the request packet to the remote PE. The value of the Hop limit field is 2.
4. The value of the Hop limit field decreases by one each time the request packet reaches a node. When the value of the Hop limit field decreases to 0, the node that receives the request packet responds to the first node with an ICMPv6 timeout packet. If the node that receives the request packet is the destination node, it sends an MPLS echo reply packet to the first node.
5. The local PE repeats the previous step until one of the following conditions exist:
¡ The local PE has not received any reply packets before the reply timeout time expires for all request packets.
¡ The local PE receives a reply packet from the remote PE.
6. The local PE identifies the connectivity of the SRv6 PW based on whether it has received MPLS echo reply packets from the remote PE and the reply response time. In addition, the local PE outputs statistics about the tracert operation.
Procedure
To trace the path of an SRv6 PW from the local PE to the remote PE in an EVPN VPWS over SRv6 network, execute the following command in any view:
tracert evpn vpws srv6 xconnect-group group-name local-service-id remote-service-id [ end-op endop ] [ -a source-ip | -h hop-limit | -r reply-mode | -t time-out | -tc tc ] *
Using a static BFD session to test the connectivity of an SRv6 PW
About this task
Enable BFD on both ends of an SRv6 PW for quick link connectivity detection. The PEs periodically send BFD control packets to each other out of the Layer 3 interfaces mapped to the cross-connect of the SRv6 PW. A PE sets the PW state to Down if it does not receive control packets from the remote end within a detection interval. To avoid packet forwarding failure, the PE switches packets to the backup SRv6 PW or an equal-cost SRv6 PW.
Restrictions and guidelines
Make sure the static BFD session is in Asynchronous mode.
Perform this task on both PEs at the two ends of an SRv6 PW.
In a primary/backup SRv6 PW scenario or an equal-cost SRv6 PW scenario, you must configure a static BFD session for each SRv6 PW to detect their connectivity.
If you do not specify the discriminator auto keywords when creating a static BFD session, you must configure the local and remote discriminators for the session by using the discriminator command. For more information about the discriminator command, see BFD commands in High Availability Command Reference.
Procedure
1. Enter system view.
system-view
2. Create a static BFD session for SRv6 PW connectivity detection and enter static BFD session view.
bfd static session-name evpn-vpws-srv6 interface interface-type interface-number remote-peer remote-ipv6-address [ discriminator auto ]
Display and maintenance commands for EVPN VPWS over SRv6
Execute display commands in any view and reset commands in user view.
For more information about the following commands, see BGP commands in Layer 3—IP Routing Command Reference:
· display bgp group.
· display bgp peer.
· display bgp update-group.
For more information about the display evpn route vpws command, see EVPN Command Reference.
|
Task |
Command |
|
Display BGP peer group information. |
display bgp [ instance instance-name ] group l2vpn evpn [ group-name group-name ] |
|
Display BGP EVPN route information. |
display bgp [ instance instance-name ] l2vpn evpn [ peer ipv6-address { advertised-routes | received-routes } [ statistics ] | [ route-distinguisher route-distinguisher ] [ route-type { auto-discovery | es | imet } ] [ { evpn-route route-length | evpn-prefix } [ advertise-info ] ] | [ ipv4-address | ipv6-address | mac-address ] ] | [ statistics ] ] |
|
Display BGP peer or peer group information. |
display bgp [ instance instance-name ] peer l2vpn evpn [ ipv6-address prefix-length | { ipv6-address | group-name group-name } log-info | [ ipv6-address ] verbose ] |
|
Display information about BGP update groups. |
display bgp [ instance instance-name ] update-group l2vpn evpn [ ipv6-address ] |
|
Display information about peers that are automatically discovered through BGP. |
display evpn auto-discovery { mac-ip [ srv6 ] [ peer peer-address ] | macip-prefix [ nexthop next-hop ] [ count ] } |
|
Display EVPN ES information. |
display evpn es { local [ count | [ xconnect-group group-name ] [ esi esi-id ] [ verbose ] ] | remote [ xconnect-group group-name] [ esi esi-id ] [ nexthop next-hop ] [ verbose ]} |
|
Display information about EVPN VPWS over SRv6. |
display evpn route vpws [ xconnect-group group-name [ connection connection-name ] ] [ count ] |
|
Display EVPN information about cross-connects. |
display evpn route xconnect-group [ name group-name [ connection connection-name ] ] [ count ] |
|
Display L2VPN SRv6 forwarding information. |
display l2vpn forwarding srv6 [ xconnect-group group-name ] [ verbose ] |
|
Display L2VPN information about Layer 3 interfaces mapped to cross-connects. |
display l2vpn interface [ xconnect-group group-name | interface-type interface-number ] [ verbose ] |
|
Display L2VPN SRv6 information. |
display l2vpn peer srv6 [ xconnect-group group-name ] [ state-machine | verbose ] |
|
Display information about Ethernet service instances. |
display l2vpn service-instance [ interface interface-type interface-number [ service-instance instance-id ] ] [ verbose ] |
|
Display information about cross-connect groups. |
display l2vpn xconnect-group [ evpn-srv6 | name group-name [ connection connection-name ] ] [ count | verbose ] |
|
Clear SRv6 PW packet statistics. |
reset l2vpn statistics srv6-pw [ xconnect-group group-name [ connection connection-name ] ] |
EVPN VPWS over SRv6 configuration examples
Example: Setting up an SRv6 tunnel between single-homed EVPN VPWS sites
Network configuration
As shown in Figure 8, set up an SRv6 tunnel between PE 1 and PE 2 for users in site 1 and site 2 to communicate through EVPN VPWS over the IPv6 backbone network.
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
XGE3/1/1 |
10::1/64 |
P |
Loop0 |
3::3/128 |
|
PE 1 |
Loop0 |
1::1/128 |
|
XGE3/1/1 |
20::2/64 |
|
|
XGE3/1/1 |
- |
|
XGE3/1/2 |
30::1/64 |
|
|
XGE3/1/2 |
20::1/64 |
PE 2 |
Loop0 |
2::2/128 |
|
CE 2 |
XGE3/1/1 |
10::2/64 |
|
XGE3/1/1 |
- |
|
|
|
|
|
XGE3/1/2 |
30::2/64 |
Procedure
1. Configure CE 1.
<CE1> system-view
[CE1] interface ten-gigabitethernet 3/1/1
[CE1-Ten-GigabitEthernet3/1/1] ipv6 address 10::1 64
[CE1-Ten-GigabitEthernet3/1/1] quit
2. Configure PE 1:
# Run OSPFv3 on PE 1 and use OSPFv3 to advertise SIDs.
<PE1> system-view
[PE1] ospfv3
[PE1-ospfv3-1] router-id 1.1.1.1
[PE1-ospfv3-1] segment-routing ipv6 locator aaa
[PE1-ospfv3-1] area 0.0.0.0
[PE1-ospfv3-1-area-0.0.0.0] quit
[PE1-ospfv3-1] quit
# Configure interface Loopback 0.
[PE1] interface loopback 0
[PE1-LoopBack0] ipv6 address 1::1 128
[PE1-LoopBack0] ospfv3 1 area 0
[PE1-LoopBack0] quit
# Enable L2VPN.
[PE1] l2vpn enable
# Configure Ten-GigabitEthernet 3/1/2, the interface connected to P.
[PE1] interface ten-gigabitethernet 3/1/2
[PE1-Ten-GigabitEthernet3/1/2] ipv6 address 20::1 64
[PE1-Ten-GigabitEthernet3/1/2] ospfv3 1 area 0
[PE1-Ten-GigabitEthernet3/1/2] undo shutdown
[PE1-Ten-GigabitEthernet3/1/2] quit
# Configure PE 1 to establish IBGP neighbor relationship with PE 2 and enable BGP EVPN to advertise routes in SRv6 encapsulation to PE 2.
[PE1] bgp 100
[PE1-bgp-default] router-id 1.1.1.1
[PE1-bgp-default] peer 2::2 as-number 100
[PE1-bgp-default] peer 2::2 connect-interface loopback 0
[PE1-bgp-default] address-family l2vpn evpn
[PE1-bgp-default-evpn] peer 2::2 enable
[PE1-bgp-default-evpn] peer 2::2 advertise encap-type srv6
[PE1-bgp-default-evpn] quit
[PE1-bgp-default] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable SRv6 encapsulation. Configure an RD and route targets for the EVPN instance and enable SRv6 BE route recursion mode.
[PE1] xconnect-group vpna
[PE1-xcg-vpna] evpn encapsulation srv6
[PE1-xcg-vpna-evpn-srv6] route-distinguisher 1:1
[PE1-xcg-vpna-evpn-srv6] vpn-target 1:1 export-extcommunity
[PE1-xcg-vpna-evpn-srv6] vpn-target 1:1 import-extcommunity
[PE1-xcg-vpna-evpn-srv6] segment-routing ipv6 best-effort
[PE1-xcg-vpna-evpn-srv6] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 3/1/1 to it. Create an SRv6 tunnel on the cross-connect.
[PE1-xcg-vpna] connection pw1
[PE1-xcg-vpna-pw1] ac interface ten-gigabitethernet 3/1/1
[PE1-xcg-vpna-pw1-Ten-GigabitEthernet3/1/1] quit
[PE1-xcg-vpna-pw1] evpn local-service-id 1 remote-service-id 2
[PE1-xcg-vpna-pw1-1-2] quit
[PE1-xcg-vpna-pw1] segment-routing ipv6 locator aaa
[PE1-xcg-vpna-pw1] quit
[PE1-xcg-vpna] quit
# Specify a source IP address for the outer IPv6 header of SRv6-encapsulated packets, and configure a locator to apply for End.DX2 SIDs.
[PE1] segment-routing ipv6
[PE1-segment-routing-ipv6] encapsulation source-address 1::1
[PE1-segment-routing-ipv6] locator aaa ipv6-prefix 100:: 64 static 32
[PE1-segment-routing-ipv6-locator-aaa] quit
[PE1-segment-routing-ipv6] quit
3. Configure PE 2:
# Run OSPFv3 on PE 2 and use OSPFv3 to advertise SIDs.
<PE2> system-view
[PE2] ospfv3
[PE2-ospfv3-1] router-id 2.2.2.2
[PE2-ospfv3-1] segment-routing ipv6 locator aaa
[PE2-ospfv3-1] area 0.0.0.0
[PE2-ospfv3-1-area-0.0.0.0] quit
[PE2-ospfv3-1] quit
# Configure interface Loopback 0.
[PE2] interface loopback 0
[PE2-LoopBack0] ipv6 address 2::2 128
[PE2-LoopBack0] ospfv3 1 area 0
[PE2-LoopBack0] quit
# Enable L2VPN.
[PE2] l2vpn enable
# Configure Ten-GigabitEthernet 3/1/2, the interface connected to P.
[PE2] interface ten-gigabitethernet 3/1/2
[PE2-Ten-GigabitEthernet3/1/2] ipv6 address 30::2 64
[PE2-Ten-GigabitEthernet3/1/2] ospfv3 1 area 0.0.0.0
[PE2-Ten-GigabitEthernet3/1/2] undo shutdown
[PE2-Ten-GigabitEthernet3/1/2] quit
# Configure PE 2 to establish IBGP neighbor relationship with PE 1, and enable BGP EVPN to advertise routes in SRv6 encapsulation to PE 1.
[PE2] bgp 100
[PE2-bgp-default] router-id 2.2.2.2
[PE2-bgp-default] peer 1::1 as-number 100
[PE2-bgp-default] peer 1::1 connect-interface loopback 0
[PE2-bgp-default] address-family l2vpn evpn
[PE2-bgp-default-evpn] peer 1::1 enable
[PE2-bgp-default-evpn] peer 1::1 advertise encap-type srv6
[PE2-bgp-default-evpn] quit
[PE2-bgp-default] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable SRv6 encapsulation. Configure an RD and route targets for the EVPN instance and enable SRv6 BE route recursion mode.
[PE2] xconnect-group vpna
[PE2-xcg-vpna] evpn encapsulation srv6
[PE2-xcg-vpna-evpn-srv6] route-distinguisher 1:1
[PE2-xcg-vpna-evpn-srv6] vpn-target 1:1 export-extcommunity
[PE2-xcg-vpna-evpn-srv6] vpn-target 1:1 import-extcommunity
[PE2-xcg-vpna-evpn-srv6] segment-routing ipv6 best-effort
[PE2-xcg-vpna-evpn-srv6] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 3/1/1 to it. Create an SRv6 tunnel on the cross-connect.
[PE2-xcg-vpna] connection pw1
[PE2-xcg-vpna-pw1] ac interface ten-gigabitethernet 3/1/1
[PE2-xcg-vpna-pw1-Ten-GigabitEthernet3/1/1] quit
[PE2-xcg-vpna-pw1] evpn local-service-id 2 remote-service-id 1
[PE2-xcg-vpna-pw1-2-1] quit
[PE2-xcg-vpna-pw1] segment-routing ipv6 locator aaa
[PE2-xcg-vpna-pw1] quit
[PE2-xcg-vpna] quit
# Specify a source IP address for the outer IPv6 header of SRv6-encapsulated packets, and configure a locator to apply for End.DX2 SIDs.
[PE2] segment-routing ipv6
[PE2-segment-routing-ipv6] encapsulation source-address 2::2
[PE2-segment-routing-ipv6] locator aaa ipv6-prefix 200:: 64 static 32
[PE2-segment-routing-ipv6-locator-aaa] quit
[PE2-segment-routing-ipv6] quit
4. Configure P:
# Run OSPFv3 on P.
<P> system-view
[P] ospfv3
[P-ospfv3-1] router-id 3.3.3.3
[P-ospfv3-1] area 0.0.0.0
[P-ospfv3-1-area-0.0.0.0] quit
[P-ospfv3-1] quit
# Configure IPv6 addresses for interfaces and run OSPFv3 on the interfaces.
[P] interface loopback 0
[P-LoopBack0] ipv6 address 3::3 128
[P-LoopBack0] ospfv3 1 area 0
[P-LoopBack0] quit
[P] interface ten-gigabitethernet 3/1/1
[P-Ten-GigabitEthernet3/1/1] ipv6 address 20::2 64
[P-Ten-GigabitEthernet3/1/1] ospfv3 1 area 0
[P-Ten-GigabitEthernet3/1/1] quit
[P] interface ten-gigabitethernet 3/1/2
[P-Ten-GigabitEthernet3/1/2] ipv6 address 30::1 64
[P-Ten-GigabitEthernet3/1/2] ospfv3 1 area 0
[P-Ten-GigabitEthernet3/1/2] quit
5. Configure CE 2.
<CE2> system-view
[CE2] interface ten-gigabitethernet 3/1/1
[CE2-Ten-GigabitEthernet3/1/1] ipv6 address 10::2 64
[CE2-Ten-GigabitEthernet3/1/1] quit
Verifying the configuration
# Verify that an SRv6 tunnel has been established between PE 1 and PE 2.
[PE1] display l2vpn peer srv6
Total number of SRv6 Tunnels: 1
1 up, 0 blocked, 0 down
Xconnect-group Name: vpna
Peer : 2::2
Flag : Main
State : Up
Remote SrvID : 2
# Verify that the SRv6 forwarding information on PE 1 is correct. You can see input and output SID information about the SRv6 tunnel.
[PE1] display l2vpn forwarding srv6
Total number of cross-connections: 1
Total number of SRv6 tunnels: 1, 1 up, 0 blocked, 0 down
Xconnect-group Name : vpna
Connection Name : pw1
Link ID : 0x1 Type: BE State: Up
In SID : 100::1:0:2
Out SID : 200::1:0:2
# Verify that CE 1 and CE 2 can ping each other. (Details not shown.)
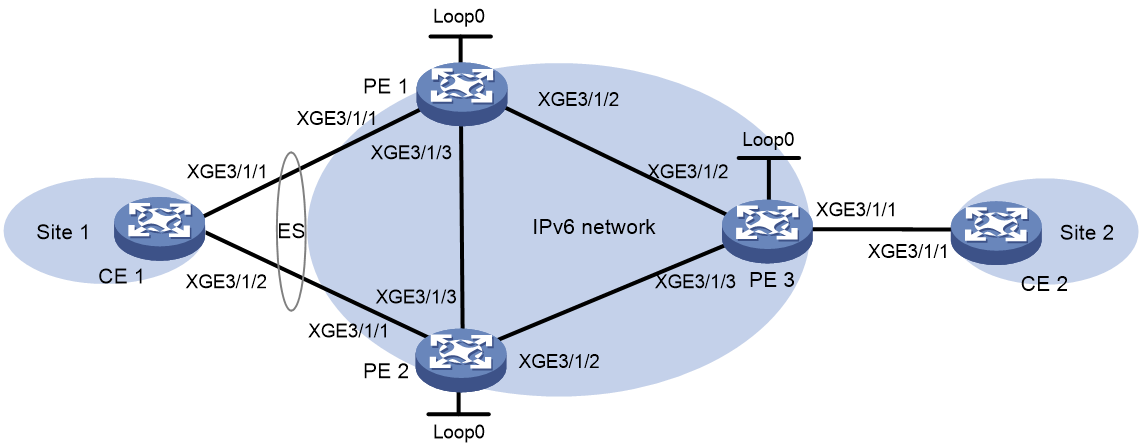
Example: Configuring EVPN VPWS over SRv6 multihoming (S-Trunk dual-homed)
Network configuration
As shown in Figure 9, CE 1 is dual-homed to PE 1 and PE 2 through S-Trunk. Configure EVPN VPWS over SRv6 for dual-homed site 1 and single-homed site 2 to communicate over the IPv6 backbone network through an SRv6 tunnel.
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
PE 1 |
Loop0 |
1::1/128 |
PE 2 |
Loop0 |
2::2/128 |
|
|
XGE3/1/1 |
N/A |
|
XGE3/1/1 |
N/A |
|
|
XGE3/1/2 |
10::1/64 |
|
XGE3/1/2 |
30::2/64 |
|
|
XGE3/1/3 |
20::1/64 |
|
XGE3/1/3 |
20::2/64 |
|
|
XGE3/1/3 |
10.1.2.1/24 |
|
XGE3/1/3 |
10.1.2.2/24 |
|
PE 3 |
Loop0 |
3::3/128 |
CE 1 |
RAGG1 |
100::1/64 |
|
|
XGE3/1/1 |
N/A |
CE 2 |
XGE3/1/1 |
100::2/64 |
|
|
XGE3/1/2 |
10::3/64 |
|
|
|
|
|
XGE3/1/3 |
30::3/64 |
|
|
|
Procedure
1. Configure CE 1:
# Create dynamic Layer 3 aggregate interface 1 and assign it an IPv6 address and prefix.
<CE1> system-view
[CE1] interface route-aggregation 1
[CE1-Route-Aggregation1] link-aggregation mode dynamic
[CE1-Route-Aggregation1] ipv6 address 100::1 64
[CE1-Route-Aggregation1] quit
# Assign Ten-GigabitEthernet 3/1/1 and Ten-GigabitEthernet 3/1/2 to aggregation group 1.
[CE1] interface ten-gigabitethernet 3/1/1
[CE1-Ten-GigabitEthernet3/1/1] port link-aggregation group 1
[CE1-Ten-GigabitEthernet3/1/1] quit
[CE1] interface ten-gigabitethernet 3/1/2
[CE1-Ten-GigabitEthernet3/1/2] port link-aggregation group 1
[CE1-Ten-GigabitEthernet3/1/2] quit
2. Configure PE 1:
# Run OSPFv3 on PE 1.
<PE1> system-view
[PE1] ospfv3
[PE1-ospfv3-1] router-id 1.1.1.1
[PE1-ospfv3-1] segment-routing ipv6 locator aaa
[PE1-ospfv3-1] area 0
[PE1-ospfv3-1-area-0.0.0.0] quit
[PE1-ospfv3-1] quit
# Configure interface Loopback 0.
[PE1] interface loopback 0
[PE1-LoopBack0] ipv6 address 1::1 128
[PE1-LoopBack0] ospfv3 1 area 0
[PE1-LoopBack0] quit
# Enable L2VPN.
[PE1] l2vpn enable
# Configure Ten-GigabitEthernet 3/1/2, the interface connected to PE 3.
[PE1] interface ten-gigabitethernet 3/1/2
[PE1-Ten-GigabitEthernet3/1/2] ipv6 address 10::1/64
[PE1-Ten-GigabitEthernet3/1/2] ospfv3 1 area 0
[PE1-Ten-GigabitEthernet3/1/2] undo shutdown
[PE1-Ten-GigabitEthernet3/1/2] quit
# Configure Ten-GigabitEthernet 3/1/3, the interface connected to PE 2.
[PE1] interface ten-gigabitethernet 3/1/3
[PE1-Ten-GigabitEthernet3/1/3] ipv6 address 20::1/64
[PE1-Ten-GigabitEthernet3/1/3] ospfv3 1 area 0
[PE1-Ten-GigabitEthernet3/1/3] undo shutdown
[PE1-Ten-GigabitEthernet3/1/3] quit
# Configure PE 1 to establish IBGP neighbor relationships with PE 2 and PE 3, and enable BGP EVPN to advertise routes in SRv6 encapsulation to PE 2 and PE 3.
[PE1] bgp 100
[PE1-bgp-default] router-id 1.1.1.1
[PE1-bgp-default] peer 2::2 as-number 100
[PE1-bgp-default] peer 2::2 connect-interface loopback 0
[PE1-bgp-default] peer 3::3 as-number 100
[PE1-bgp-default] peer 3::3 connect-interface loopback 0
[PE1-bgp-default] address-family l2vpn evpn
[PE1-bgp-default-evpn] peer 2::2 enable
[PE1-bgp-default-evpn] peer 3::3 enable
[PE1-bgp-default-evpn] peer 2::2 advertise encap-type srv6
[PE1-bgp-default-evpn] peer 3::3 advertise encap-type srv6
[PE1-bgp-default-evpn] quit
[PE1-bgp-default] quit
# Configure S-Trunk for CE 1 to be dual-homed to PE 1 and PE 2.
[PE1] lacp system-priority 10
[PE1] lacp system-mac 1-1-1
[PE1] lacp system-number 1
[PE1] s-trunk id 1
[PE1-s-trunk1] s-trunk ip destination 10.1.2.2 source 10.1.2.1
[PE1-s-trunk1] quit
[PE1] interface route-aggregation 1
[PE1-Route-Aggregation1] link-aggregation mode dynamic
[PE1-Route-Aggregation1] s-trunk 1
[PE1-Route-Aggregation1] s-trunk port-role primary
[PE1-Route-Aggregation1] quit
[PE1] interface ten-gigabitethernet 3/1/1
[PE1-Ten-GigabitEthernet3/1/1] port link-aggregation group 1
[PE1-Ten-GigabitEthernet3/1/1] quit
# Assign an ESI to site-facing interface Route-Aggregation 1 and set its redundancy mode to all-active.
[PE1] interface route-aggregation 1
[PE1-Route-Aggregation1] esi 1.1.1.1.1
[PE1-Route-Aggregation1] evpn redundancy-mode all-active
[PE1-Route-Aggregation1] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable SRv6 encapsulation. Configure an RD and route targets for the EVPN instance and enable SRv6 BE route recursion mode.
[PE1] xconnect-group vpna
[PE1-xcg-vpna] evpn encapsulation srv6
[PE1-xcg-vpna-evpn-srv6] route-distinguisher 1:1
[PE1-xcg-vpna-evpn-srv6] vpn-target 1:1 export-extcommunity
[PE1-xcg-vpna-evpn-srv6] vpn-target 1:1 import-extcommunity
[PE1-xcg-vpna-evpn-srv6] segment-routing ipv6 best-effort
[PE1-xcg-vpna-evpn-srv6] quit
# Create cross-connect pw1 and map Route-Aggregation 1 to it. Create an SRv6 tunnel on the cross-connect.
[PE1-xcg-vpna] connection pw1
[PE1-xcg-vpna-pw1] ac interface route-aggregation 1
[PE1-xcg-vpna-pw1-Route-Aggregation1] quit
[PE1-xcg-vpna-pw1] evpn local-service-id 1 remote-service-id 2
[PE1-xcg-vpna-pw1-1-2] quit
[PE1-xcg-vpna-pw1] segment-routing ipv6 locator aaa
[PE1-xcg-vpna-pw1] quit
[PE1-xcg-vpna] quit
# Specify a source IP address for the outer IPv6 header of SRv6-encapsulated packets, and configure a locator to apply for End.DX2 SIDs.
[PE1] segment-routing ipv6
[PE1-segment-routing-ipv6] encapsulation source-address 1::1
[PE1-segment-routing-ipv6] locator aaa ipv6-prefix 111:: 64 static 32
[PE1-segment-routing-ipv6-locator-aaa] quit
[PE1-segment-routing-ipv6] quit
3. Configure PE 2:
# Run OSPFv3 on PE 2.
<PE2> system-view
[PE2] ospfv3
[PE2-ospfv3-1] router-id 2.2.2.2
[PE2-ospfv3-1] segment-routing ipv6 locator aaa
[PE2-ospfv3-1] area 0.0.0.0
[PE2-ospfv3-1-area-0.0.0.0] quit
[PE2-ospfv3-1] quit
# Configure interface Loopback 0.
[PE2] interface loopback 0
[PE2-LoopBack0] ipv6 address 2::2 128
[PE2-LoopBack0] ospfv3 1 area 0
[PE2-LoopBack0] quit
# Enable L2VPN.
[PE2] l2vpn enable
# Configure Ten-GigabitEthernet 3/1/3, the interface connected to PE 1.
[PE2] interface ten-gigabitethernet 3/1/3
[PE2-Ten-GigabitEthernet3/1/3] ipv6 address 20::2 64
[PE2-Ten-GigabitEthernet3/1/3] ospfv3 1 area 0
[PE2-Ten-GigabitEthernet3/1/3] undo shutdown
[PE2-Ten-GigabitEthernet3/1/3] quit
# Configure Ten-GigabitEthernet 3/1/2, the interface connected to PE 3.
[PE2] interface ten-gigabitethernet 3/1/2
[PE2-Ten-GigabitEthernet3/1/2] ipv6 address 30::2 64
[PE2-Ten-GigabitEthernet3/1/2] ospfv3 1 area 0
[PE2-Ten-GigabitEthernet3/1/2] undo shutdown
[PE2-Ten-GigabitEthernet3/1/2] quit
# Configure PE 2 to establish IBGP neighbor relationships with PE 1 and PE 3, and enable BGP EVPN to advertise routes in SRv6 encapsulation to PE 1 and PE 3.
[PE2] bgp 100
[PE2-bgp-default] router-id 2.2.2.2
[PE2-bgp-default] peer 1::1 as-number 100
[PE2-bgp-default] peer 1::1 connect-interface loopback 0
[PE2-bgp-default] peer 3::3 as-number 100
[PE2-bgp-default] peer 3::3 connect-interface loopback 0
[PE2-bgp-default] address-family l2vpn evpn
[PE2-bgp-default-evpn] peer 1::1 enable
[PE2-bgp-default-evpn] peer 3::3 enable
[PE2-bgp-default-evpn] peer 1::1 advertise encap-type srv6
[PE2-bgp-default-evpn] peer 3::3 advertise encap-type srv6
[PE2-bgp-default-evpn] quit
[PE2-bgp-default] quit
# Configure S-Trunk for CE 1 to be dual-homed to PE 1 and PE 2.
[PE2] lacp system-priority 10
[PE2] lacp system-mac 1-1-1
[PE2] lacp system-number 2
[PE2] s-trunk id 1
[PE2-s-trunk1] s-trunk ip destination 10.1.2.1 source 10.1.2.2
[PE2-s-trunk1] quit
[PE2] interface route-aggregation 1
[PE2-Route-Aggregation1] link-aggregation mode dynamic
[PE2-Route-Aggregation1] s-trunk 1
[PE2-Route-Aggregation1] s-trunk port-role primary
[PE2-Route-Aggregation1] quit
[PE2] interface ten-gigabitethernet 3/1/1
[PE2-Ten-GigabitEthernet3/1/1] port link-aggregation group 1
[PE2-Ten-GigabitEthernet3/1/1] quit
# Assign an ESI to site-facing interface Route-Aggregation 1 and set its redundancy mode to all-active.
[PE2] interface route-aggregation 1
[PE2-Route-Aggregation1] esi 1.1.1.1.1
[PE2-Route-Aggregation1] evpn redundancy-mode all-active
[PE2-Route-Aggregation1] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable SRv6 encapsulation. Configure an RD and route targets for the EVPN instance and enable SRv6 BE route recursion mode.
[PE2] xconnect-group vpna
[PE2-xcg-vpna] evpn encapsulation srv6
[PE2-xcg-vpna-evpn-srv6] route-distinguisher 1:1
[PE2-xcg-vpna-evpn-srv6] vpn-target 1:1 export-extcommunity
[PE2-xcg-vpna-evpn-srv6] vpn-target 1:1 import-extcommunity
[PE2-xcg-vpna-evpn-srv6] segment-routing ipv6 best-effort
[PE2-xcg-vpna-evpn-srv6] quit
# Create cross-connect pw1 and map Route-Aggregation 1 to it. Create an SRv6 tunnel on the cross-connect.
[PE2-xcg-vpna] connection pw1
[PE2-xcg-vpna-pw1] ac interface route-aggregation 1
[PE2-xcg-vpna-pw1-Route-Aggregation1] quit
[PE2-xcg-vpna-pw1] evpn local-service-id 1 remote-service-id 2
[PE2-xcg-vpna-pw1-1-2] quit
[PE2-xcg-vpna-pw1] segment-routing ipv6 locator aaa
[PE2-xcg-vpna-pw1] quit
[PE2-xcg-vpna] quit
# Specify a source IP address for the outer IPv6 header of SRv6-encapsulated packets, and configure a locator to apply for End.DX2 SIDs.
[PE2] segment-routing ipv6
[PE2-segment-routing-ipv6] encapsulation source-address 2::2
[PE2-segment-routing-ipv6] locator aaa ipv6-prefix 222:: 64 static 32
[PE2-segment-routing-ipv6-locator-aaa] quit
[PE2-segment-routing-ipv6] quit
4. Configure PE 3:
# Run OSPFv3 on PE 3.
<PE3> system-view
[PE3] ospfv3
[PE3-ospfv3-1] router-id 3.3.3.3
[PE3-ospfv3-1] segment-routing ipv6 locator aaa
[PE3-ospfv3-1] area 0
[PE3-ospfv3-1-area-0.0.0.0] quit
[PE3-ospfv3-1] quit
# Configure interface Loopback 0.
[PE3] interface loopback 0
[PE3-LoopBack0] ipv6 address 3::3 128
[PE3-LoopBack0] ospfv3 1 area 0
[PE3-LoopBack0] quit
# Enable L2VPN.
[PE3] l2vpn enable
# Configure Ten-GigabitEthernet 3/1/2, the interface connected to PE 1.
[PE3] interface ten-gigabitethernet 3/1/2
[PE3-Ten-GigabitEthernet3/1/2] ipv6 address 10::3 64
[PE3-Ten-GigabitEthernet3/1/2] ospfv3 1 area 0
[PE3-Ten-GigabitEthernet3/1/2] undo shutdown
[PE3-Ten-GigabitEthernet3/1/2] quit
# Configure Ten-GigabitEthernet 3/1/3, the interface connected to PE 2.
[PE3] interface ten-gigabitethernet 3/1/3
[PE3-Ten-GigabitEthernet3/1/3] ipv6 address 30::3 64
[PE3-Ten-GigabitEthernet3/1/3] ospfv3 1 area 0
[PE3-Ten-GigabitEthernet3/1/3] undo shutdown
[PE3-Ten-GigabitEthernet3/1/3] quit
# Configure PE 3 to establish IBGP neighbor relationships with PE 1 and PE 2, and enable BGP EVPN to advertise routes in SRv6 encapsulation to PE 1 and PE 2.
[PE3] bgp 100
[PE3-bgp-default] router-id 3.3.3.3
[PE3-bgp-default] peer 1::1 as-number 100
[PE3-bgp-default] peer 1::1 connect-interface loopback 0
[PE3-bgp-default] peer 2::2 as-number 100
[PE3-bgp-default] peer 2::2 connect-interface loopback 0
[PE3-bgp-default] address-family l2vpn evpn
[PE3-bgp-default-evpn] peer 1::1 enable
[PE3-bgp-default-evpn] peer 2::2 enable
[PE3-bgp-default-evpn] peer 1::1 advertise encap-type srv6
[PE3-bgp-default-evpn] peer 2::2 advertise encap-type srv6
[PE3-bgp-default-evpn] quit
[PE3-bgp-default] quit
# Create a cross-connect group named vpna, create an EVPN instance for it, and enable SRv6 encapsulation. Configure an RD and route targets for the EVPN instance and enable SRv6 BE route recursion mode.
[PE3] xconnect-group vpna
[PE3-xcg-vpna] evpn encapsulation srv6
[PE3-xcg-vpna-evpn-srv6] route-distinguisher 1:1
[PE3-xcg-vpna-evpn-srv6] vpn-target 1:1 export-extcommunity
[PE3-xcg-vpna-evpn-srv6] vpn-target 1:1 import-extcommunity
[PE3-xcg-vpna-evpn-srv6] segment-routing ipv6 best-effort
[PE3-xcg-vpna-evpn-srv6] quit
# Create cross-connect pw1 and map Ten-GigabitEthernet 3/1/1 to it. Create an SRv6 tunnel on the cross-connect.
[PE3-xcg-vpna] connection pw1
[PE3-xcg-vpna-pw1] ac interface ten-gigabitethernet 3/1/1
[PE3-xcg-vpna-pw1-Ten-GigabitEthernet3/1/1] quit
[PE3-xcg-vpna-pw1] evpn local-service-id 2 remote-service-id 1
[PE3-xcg-vpna-pw1-2-1] quit
[PE3-xcg-vpna-pw1] segment-routing ipv6 locator aaa
[PE3-xcg-vpna-pw1] quit
[PE3-xcg-vpna] quit
# Specify a source IP address for the outer IPv6 header of SRv6-encapsulated packets, and configure a locator to apply for End.DX2 SIDs.
[PE3] segment-routing ipv6
[PE3-segment-routing-ipv6] encapsulation source-address 3::3
[PE3-segment-routing-ipv6] locator aaa ipv6-prefix 333:: 64 static 32
[PE3-segment-routing-ipv6-locator-aaa] quit
[PE3-segment-routing-ipv6] quit
5. Configure CE 2.
<CE2> system-view
[CE2] interface ten-gigabitethernet 3/1/1
[CE2-Ten-GigabitEthernet3/1/1] ipv6 address 100::2 64
[CE2-Ten-GigabitEthernet3/1/1] quit
Verifying the configuration
# Verify that PE 1 has established an SRv6 tunnel to PE 3.
[PE1] display l2vpn peer srv6
Total number of SRv6 Tunnels: 1
1 up, 0 blocked, 0 down
Xconnect-group Name: vpna
Peer : 3::3
Flag : Main
State : Up
Remote SrvID : 2
# Verify that PE 3 has established SRv6 tunnels to PE 1 and PE 2. The SRv6 tunnels are ECMP tunnels that load share traffic.
[PE3] display l2vpn peer srv6
Total number of SRv6 Tunnels: 2
2 up, 0 blocked, 0 down
Xconnect-group Name: vpna
Peer : 2::2
Flag : ECMP
State : Up
Remote SrvID : 1
Peer : 1::1
Flag : ECMP
State : Up
Remote SrvID : 1
# Verify that the SRv6 forwarding information on PE 1 and PE 3 is correct. You can see input and output SID information about the SRv6 tunnel.
[PE1] display l2vpn forwarding srv6
Total number of cross-connections: 1
Total number of SRv6 tunnels: 1, 1 up, 0 blocked, 0 down
Xconnect-group Name : vpna
Connection Name : pw1
Link ID : 0x1 Type: BE State: Up
In SID : 111::1:0:3
Out SID : 333::1:0:3
[PE3] display l2vpn forwarding srv6
Total number of cross-connections: 1
Total number of SRv6 tunnels: 2, 2 up, 0 blocked, 0 down
Xconnect-group Name : vpna
Connection Name : pw1
Link ID : 0x1 Type: BE State: Up
In SID : 333::1:0:3
Out SID : 111::1:0:3
Link ID : 0x1 Type: BE State: Up
In SID : 333::1:0:3
Out SID : 222::1:0:3
# Verify that CE 1 and CE 2 can ping each other. (Details not shown.)
# Verify that CE 1 and CE 2 can ping each other when the PW on PE 1 or PE 2 fails. (Details not shown.)
Example: Configuring LDP PWs as ACs for SRv6 PWs
Network configuration
As shown in Figure 10:
· PE 1 and PE 2 are edge devices on both the MPLS network and SRv6 network.
· Configure MPLS L2VPN on PE 1, PE 2, and PE 4, and configure the PEs to use LDP to establish LDP PWs.
· Configure EVPN VPWS over SRv6 on PE 1, PE 2, and PE 3.
· On PE 1 and PE 2, configure LDP PWs as UPWs (ACs) for SRv6 PWs to ensure that the MPLS L2VPN and EVPN VPWS over SRv6 networks can communicate with each other.
· PE 4 is dual-homed to PE 1 and PE 2 through two LDP PWs (UPWs).
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
PE 1 |
Loop0 |
1::1/128 |
PE 3 |
Loop0 |
3::3/128 |
|
|
Loop0 |
1.1.1.9/32 |
|
XGE3/1/1 |
- |
|
|
XGE3/1/1 |
10.1.1.1/24 |
|
XGE3/1/2 |
10::3/64 |
|
|
XGE3/1/2 |
10::1/64 |
|
XGE3/1/3 |
30::3/64 |
|
|
XGE3/1/3 |
20::1/64 |
PE 4 |
Loop0 |
4.4.4.9 |
|
PE 2 |
Loop0 |
2::2/128 |
|
XGE3/1/1 |
10.1.1.4/24 |
|
|
Loop0 |
2.2.2.9/32 |
|
XGE3/1/2 |
20.1.1.4/24 |
|
|
XGE3/1/1 |
20.1.1.2/24 |
|
XGE3/1/3 |
- |
|
|
XGE3/1/2 |
30::2/64 |
CE 1 |
XGE3/1/1 |
100::1/64 |
|
|
XGE3/1/3 |
20::2/64 |
CE2 |
XGE3/1/1 |
100::2/64 |
Procedure
1. Configure CE 1:
# Configure an IPv6 address and prefix length for Ten-GigabitEthernet 3/1/1.
<CE1> system-view
[CE1] interface ten-gigabitethernet 3/1/1
[CE1-Ten-GigabitEthernet3/1/1] ipv6 address 100::1 64
[CE1-Ten-GigabitEthernet3/1/1] quit
2. Configure PE 4:
# Configure MPLS basic capabilities.
<PE4> system-view
[PE4] interface loopback 0
[PE4-LoopBack0] ip address 4.4.4.9 32
[PE4-LoopBack0] ospf 1 area 0
[PE4-LoopBack0] quit
[PE4] mpls lsr-id 4.4.4.9
[PE4] mpls ldp
[PE4-ldp] quit
# Enable L2VPN.
[PE4] l2vpn enable
# Configure Ten-GigabitEthernet 3/1/1, the interface connected to PE 1.
[PE4] interface ten-gigabitethernet 3/1/1
[PE4-Ten-GigabitEthernet3/1/1] ip address 10.1.1.4 24
[PE4-Ten-GigabitEthernet3/1/1] ospf 1 area 0
[PE4-Ten-GigabitEthernet3/1/1] mpls enable
[PE4-Ten-GigabitEthernet3/1/1] mpls ldp enable
[PE4-Ten-GigabitEthernet3/1/1] undo shutdown
[PE4-Ten-GigabitEthernet3/1/1] quit
# Configure Ten-GigabitEthernet 3/1/2, the interface connected to PE 2.
[PE4] interface ten-gigabitethernet 3/1/2
[PE4-Ten-GigabitEthernet3/1/2] ip address 20.1.1.4 24
[PE4-Ten-GigabitEthernet3/1/2] ospf 1 area 0
[PE4-Ten-GigabitEthernet3/1/2] mpls enable
[PE4-Ten-GigabitEthernet3/1/2] mpls ldp enable
[PE4-Ten-GigabitEthernet3/1/2] undo shutdown
[PE4-Ten-GigabitEthernet3/1/2] quit
# Create cross-connect group vpna, create cross-connect pw1 in the group, and map Ten-GigabitEthernet 3/1/3 to the cross-connect. Create an LDP PW for the cross-connect to associate the AC with the PW. Configure a backup PW for the PW and enable the dual receive feature for PW redundancy.
[PE4] xconnect-group vpna
[PE4-xcg-vpna] connection pw1
[PE4-xcg-vpna-pw1] ac interface ten-gigabitethernet 3/1/3
[PE4-xcg-vpna-pw1-Ten-GigabitEthernet3/1/3] quit
[PE4-xcg-vpna-pw1] protection dual-receive
[PE4-xcg-vpna-pw1] peer 1.1.1.9 pw-id 500
[PE4-xcg-vpna-pw1-1.1.1.9-500] backup-peer 2.2.2.9 pw-id 500
[PE4-xcg-vpna-pw1-1.1.1.9-500-backup] quit
[PE4-xcg-vpna-pw1-1.1.1.9-500] quit
[PE4-xcg-vpna-pw1] quit
[PE4-xcg-vpna] quit
3. Configure PE 1:
# Run OSPF on PE 1.
<PE1> system-view
[PE1] ospf 1 router-id 1.1.1.9
[PE1-ospf-1] area 0
[PE1-ospf-1-area-0.0.0.0] network 1.1.1.9 0.0.0.0
[PE1-ospf-1-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[PE1-ospf-1-area-0.0.0.0] quit
[PE1-ospf-1] quit
# Run OSPFv3 on PE 1.
<PE1> system-view
[PE1] ospfv3
[PE1-ospfv3-1] router-id 1.1.1.9
[PE1-ospfv3-1] segment-routing ipv6 locator aaa
[PE1-ospfv3-1] area 0
[PE1-ospfv3-1-area-0.0.0.0] quit
[PE1-ospfv3-1] quit
# Configure interface Loopback 0.
[PE1] interface loopback 0
[PE1-LoopBack0] ip address 1.1.1.9 32
[PE1-LoopBack0] ipv6 address 1::1 128
[PE1-LoopBack0] ospfv3 1 area 0
[PE1-LoopBack0] quit
# Configure MPLS basic capabilities.
[PE1] mpls lsr-id 1.1.1.9
[PE1] mpls ldp
[PE1-ldp] quit
# Enable L2VPN.
[PE1] l2vpn enable
# Configure Ten-GigabitEthernet 3/1/1, the interface connected to PE 4.
[PE1] interface ten-gigabitethernet 3/1/1
[PE1-Ten-GigabitEthernet3/1/1] ip address 10.1.1.1 24
[PE1-Ten-GigabitEthernet3/1/1] mpls enable
[PE1-Ten-GigabitEthernet3/1/1] mpls ldp enable
[PE1-Ten-GigabitEthernet3/1/1] undo shutdown
[PE1-Ten-GigabitEthernet3/1/1] quit
# Configure Ten-GigabitEthernet 3/1/2, the interface connected to PE 3.
[PE1] interface ten-gigabitethernet 3/1/2
[PE1-Ten-GigabitEthernet3/1/2] ipv6 address 10::1 64
[PE1-Ten-GigabitEthernet3/1/2] ospfv3 1 area 0
[PE1-Ten-GigabitEthernet3/1/2] quit
# Configure Ten-GigabitEthernet 3/1/3, the interface connected to PE 2.
[PE1] interface ten-gigabitethernet 3/1/3
[PE1-Ten-GigabitEthernet3/1/3] ipv6 address 20::1 64
[PE1-Ten-GigabitEthernet3/1/3] ospfv3 1 area 0
[PE1-Ten-GigabitEthernet3/1/3] quit
# Establish IBGP connections to PE 2 and PE 3, and enable BGP EVPN to advertise route information to PE 2 and PE 3.
[PE1] bgp 100
[PE1-bgp-default] peer 2::2 as-number 100
[PE1-bgp-default] peer 2::2 connect-interface loopback 0
[PE1-bgp-default] peer 3::3 as-number 100
[PE1-bgp-default] peer 3::3 connect-interface loopback 0
[PE1-bgp-default] address-family l2vpn evpn
[PE1-bgp-default-evpn] peer 2::2 enable
[PE1-bgp-default-evpn] peer 3::3 enable
[PE1-bgp-default-evpn] peer 2::2 advertise encap-type srv6
[PE1-bgp-default-evpn] peer 3::3 advertise encap-type srv6
[PE1-bgp-default-evpn] quit
[PE1-bgp-default] quit
# Create cross-connect group vpna, create an EVPN instance for it, and enable SRv6 encapsulation. Configure an RD and route targets for the EVPN instance and enable SRv6 BE route recursion mode.
[PE1] xconnect-group vpna
[PE1-xcg-vpna] evpn encapsulation srv6
[PE1-xcg-vpna-evpn-srv6] route-distinguisher 1:1
[PE1-xcg-vpna-evpn-srv6] vpn-target 1:1 export-extcommunity
[PE1-xcg-vpna-evpn-srv6] vpn-target 1:1 import-extcommunity
[PE1-xcg-vpna-evpn-srv6] segment-routing ipv6 best-effort
[PE1-xcg-vpna-evpn-srv6] quit
# Create cross-connect pw1. Configure PE 1 to set up an UPW with PE 4, assign an ESI to the UPW, and set the redundancy mode of the UPW to all-active. Create an SRv6 PW for the cross-connect to associate the UPW with the SRv6 PW.
[PE1-xcg-vpna] connection pw1
[PE1-xcg-vpna-pw1] peer 4.4.4.9 pw-id 500
[PE1-xcg-vpna-pw1-4.4.4.9-500] esi 1.1.1.1.1
[PE1-xcg-vpna-pw1-4.4.4.9-500] evpn redundancy-mode all-active
[PE1-xcg-vpna-pw1-4.4.4.9-500] quit
[PE1-xcg-vpna-pw1] evpn local-service-id 1 remote-service-id 2
[PE1-xcg-vpna-pw1-1-2] quit
[PE1-xcg-vpna-pw1] segment-routing ipv6 locator aaa
[PE1-xcg-vpna-pw1] quit
[PE1-xcg-vpna] quit
# Configure a locator to apply for End.DX2 SIDs.
[PE1] segment-routing ipv6
[PE1-segment-routing-ipv6] encapsulation source-address 1::1
[PE1-segment-routing-ipv6] locator aaa ipv6-prefix 111:: 64 static 32
[PE1-segment-routing-ipv6-locator-aaa] quit
[PE1-segment-routing-ipv6] quit
4. Configure PE 2:
# Run OSPF on PE 2.
<PE2> system-view
[PE2] ospf 1 router-id 2.2.2.9
[PE2-ospf-1] area 0.0.0.0
[PE2-ospf-1-area-0.0.0.0] network 2.2.2.9 0.0.0.0
[PE2-ospf-1-area-0.0.0.0] network 20.1.1.0 0.0.0.255
[PE2-ospf-1-area-0.0.0.0] quit
[PE2-ospf-1] quit
# Run OSPFv3 on PE 2.
<PE2> system-view
[PE2] ospfv3
[PE2-ospfv3-1] router-id 2.2.2.9
[PE2-ospfv3-1] segment-routing ipv6 locator aaa
[PE2-ospfv3-1] area 0.0.0.0
[PE2-ospfv3-1-area-0.0.0.0] quit
[PE2-ospfv3-1] quit
# Configure interface Loopback 0.
[PE2] interface loopback 0
[PE2-LoopBack1] ip address 2.2.2.9 32
[PE2-LoopBack0] ipv6 address 2::2 128
[PE2-LoopBack0] ospfv3 1 area 0
[PE2-LoopBack0] quit
# Configure MPLS basic capabilities.
[PE2] mpls lsr-id 2.2.2.9
[PE2] mpls ldp
[PE2-ldp] quit
# Enable L2VPN.
[PE2] l2vpn enable
# Configure Ten-GigabitEthernet 3/1/3, the interface connected to PE 1.
[PE2] interface ten-gigabitethernet 3/1/3
[PE2-Ten-GigabitEthernet3/1/3] ipv6 address 20::2 64
[PE2-Ten-GigabitEthernet3/1/3] ospfv3 1 area 0
[PE2-Ten-GigabitEthernet3/1/3] undo shutdown
[PE2-Ten-GigabitEthernet3/1/3] quit
# Configure Ten-GigabitEthernet 3/1/2, the interface connected to PE 3.
[PE2] interface ten-gigabitethernet 3/1/2
[PE2-Ten-GigabitEthernet3/1/2] ipv6 address 30::2 64
[PE2-Ten-GigabitEthernet3/1/2] ospfv3 1 area 0
[PE2-Ten-GigabitEthernet3/1/2] undo shutdown
[PE2-Ten-GigabitEthernet3/1/2] quit
# Configure Ten-GigabitEthernet 3/1/1, the interface connected to PE 4.
[PE2] interface ten-gigabitethernet 3/1/1
[PE2-Ten-GigabitEthernet3/1/1] ip address 20.1.1.2 24
[PE2-Ten-GigabitEthernet3/1/1] mpls enable
[PE2-Ten-GigabitEthernet3/1/1] mpls ldp enable
[PE2-Ten-GigabitEthernet3/1/1] undo shutdown
[PE2-Ten-GigabitEthernet3/1/1] quit
# Establish IBGP connections to PE 1 and PE 3 and enable BGP EVPN to advertise route information to PE 1 and PE 3.
[PE2] bgp 100
[PE2-bgp-default] peer 1::1 as-number 100
[PE2-bgp-default] peer 1::1 connect-interface loopback 0
[PE2-bgp-default] peer 3::3 as-number 100
[PE2-bgp-default] peer 3::3 connect-interface loopback 0
[PE2-bgp-default] address-family l2vpn evpn
[PE2-bgp-default-evpn] peer 1::1 enable
[PE2-bgp-default-evpn] peer 3::3 enable
[PE2-bgp-default-evpn] peer 1::1 advertise encap-type srv6
[PE2-bgp-default-evpn] peer 3::3 advertise encap-type srv6
[PE2-bgp-default-evpn] quit
[PE2-bgp-default] quit
# Create cross-connect group vpna, create an EVPN instance for it, and enable SRv6 encapsulation. Configure an RD and route targets for the EVPN instance and enable SRv6 BE route recursion mode.
[PE2] xconnect-group vpna
[PE2-xcg-vpna] evpn encapsulation srv6
[PE2-xcg-vpna-evpn-srv6] route-distinguisher 1:1
[PE2-xcg-vpna-evpn-srv6] vpn-target 1:1 export-extcommunity
[PE2-xcg-vpna-evpn-srv6] vpn-target 1:1 import-extcommunity
[PE2-xcg-vpna-evpn-srv6] segment-routing ipv6 best-effort
[PE2-xcg-vpna-evpn-srv6] quit
# Create cross-connect pw1. Configure PE 2 to set up an UPW with PE 4, assign an ESI to the UPW, and set the redundancy mode of the UPW to all-active. Create an SRv6 PW for the cross-connect to associate the UPW with the SRv6 PW.
[PE2-xcg-vpna] connection pw1
[PE2-xcg-vpna-pw1] peer 4.4.4.9 pw-id 500
[PE2-xcg-vpna-pw1-4.4.4.9-500] esi 1.1.1.1.1
[PE2-xcg-vpna-pw1-4.4.4.9-500] evpn redundancy-mode all-active
[PE2-xcg-vpna-pw1-4.4.4.9-500] quit
[PE2-xcg-vpna-pw1] evpn local-service-id 1 remote-service-id 2
[PE2-xcg-vpna-pw1-1-2] quit
[PE2-xcg-vpna-pw1] segment-routing ipv6 locator aaa
[PE2-xcg-vpna-pw1] quit
[PE2-xcg-vpna] quit
# Configure a locator to apply for End.DX2 SIDs.
[PE2] segment-routing ipv6
[PE2-segment-routing-ipv6] encapsulation source-address 2::2
[PE2-segment-routing-ipv6] locator aaa ipv6-prefix 222:: 64 static 32
[PE2-segment-routing-ipv6-locator-aaa] quit
[PE2-segment-routing-ipv6] quit
5. Configure PE 3:
# Run OSPFv3 on PE 3.
<PE3> system-view
[PE3] ospfv3
[PE3-ospfv3-1] router-id 3.3.3.9
[PE3-ospfv3-1] segment-routing ipv6 locator aaa
[PE3-ospfv3-1] area 0
[PE3-ospfv3-1-area-0.0.0.0] quit
[PE3-ospfv3-1] quit
# Configure interface Loopback 0.
[PE3] interface loopback 0
[PE3-LoopBack0] ipv6 address 3::3 128
[PE3-LoopBack0] ospfv3 1 area 0
[PE3-LoopBack0] quit
# Enable L2VPN.
[PE3] l2vpn enable
# Configure Ten-GigabitEthernet 3/1/2, the interface connected to PE 1.
[PE3] interface ten-gigabitethernet 3/1/2
[PE3-Ten-GigabitEthernet3/1/2] ipv6 address 10::3 64
[PE3-Ten-GigabitEthernet3/1/2] ospfv3 1 area 0
[PE3-Ten-GigabitEthernet3/1/2] undo shutdown
[PE3-Ten-GigabitEthernet3/1/2] quit
# Configure Ten-GigabitEthernet 3/1/3, the interface connected to PE 2.
[PE3] interface ten-gigabitethernet 3/1/3
[PE3-Ten-GigabitEthernet3/1/3] ipv6 address 30::3 64
[PE3-Ten-GigabitEthernet3/1/3] ospfv3 1 area 0
[PE3-Ten-GigabitEthernet3/1/3] undo shutdown
[PE3-Ten-GigabitEthernet3/1/3] quit
# Establish IBGP connections to PE 1 and PE 2, and enable BGP EVPN to advertise route information to PE 1 and PE 2.
[PE3] bgp 100
[PE3-bgp-default] peer 1::1 as-number 100
[PE3-bgp-default] peer 1::1 connect-interface loopback 0
[PE3-bgp-default] peer 2::2 as-number 100
[PE3-bgp-default] peer 2::2 connect-interface loopback 0
[PE3-bgp-default] address-family l2vpn evpn
[PE3-bgp-default-evpn] peer 1::1 enable
[PE3-bgp-default-evpn] peer 2::2 enable
[PE3-bgp-default-evpn] peer 1::1 advertise encap-type srv6
[PE3-bgp-default-evpn] peer 2::2 advertise encap-type srv6
[PE3-bgp-default-evpn] quit
[PE3-bgp-default] quit
# Create cross-connect group vpna, create an EVPN instance for it, and enable SRv6 encapsulation. Configure an RD and route targets for the EVPN instance and enable SRv6 BE route recursion mode.
[PE3] xconnect-group vpna
[PE3-xcg-vpna] evpn encapsulation srv6
[PE3-xcg-vpna-evpn-srv6] route-distinguisher 1:1
[PE3-xcg-vpna-evpn-srv6] vpn-target 1:1 export-extcommunity
[PE3-xcg-vpna-evpn-srv6] vpn-target 1:1 import-extcommunity
[PE3-xcg-vpna-evpn-srv6] segment-routing ipv6 best-effort
[PE3-xcg-vpna-evpn-srv6] quit
# Create cross-connect pw1, map Ten-GigabitEthernet 3/1/1 to the cross-connect, and create an SRv6 PW on the cross-connect to associate the AC with the SRv6 PW.
[PE3-xcg-vpna] connection pw1
[PE3-xcg-vpna-pw1] ac interface ten-gigabitethernet 3/1/1
[PE3-xcg-vpna-pw1-Ten-GigabitEthernet3/1/1] quit
[PE3-xcg-vpna-pw1] evpn local-service-id 2 remote-service-id 1
[PE3-xcg-vpna-pw1-2-1] quit
[PE3-xcg-vpna-pw1] segment-routing ipv6 locator aaa
[PE3-xcg-vpna-pw1] quit
[PE3-xcg-vpna] quit
# Configure a locator to apply for End.DX2 SIDs.
[PE3] segment-routing ipv6
[PE3-segment-routing-ipv6] encapsulation source-address 3::3
[PE3-segment-routing-ipv6] locator aaa ipv6-prefix 333:: 64 static 32
[PE3-segment-routing-ipv6-locator-aaa] quit
[PE3-segment-routing-ipv6] quit
6. On CE 2, configure an IPv6 address for Ten-GigabitEthernet 3/1/1.
<CE2> system-view
[CE2] interface ten-gigabitethernet 3/1/1
[CE2-Ten-GigabitEthernet3/1/1] ipv6 address 100::2 64
[CE2-Ten-GigabitEthernet3/1/1] quit
Verifying the configuration
# On PE 1, view detailed cross-connect group information. Verify that PE 1 has established an LDP PW with PE 4 and an SRv6 PW with PE 3.
[PE1] display l2vpn xconnect-group verbose
Xconnect-group Name: vpna
Connection Name : pw1
Connection ID : 0
State : Up
MTU : 1500
PW Redundancy Mode : Slave
Diffserv Mode : -
LDP PWs:
Peer PW ID Link ID State Flag
4.4.4.9 500 0 Up Main
Create time: 2020-11-02 10:04:59
Last time status changed: 2020-11-02 10:04:59
Last time PW went down: 2020-11-02 10:04:59
SRv6 tunnels:
Peer : 3::3
Link ID : 0x1
State : Up
# On PE 1, display detailed local ES information. Verify that the LDP PW (UPW) has multihoming settings.
[PE1] display evpn es local verbose
Xconnect-group name : vpna
Connection name : pw1
ESI : 0001.0001.0001.0001.0001
Redundancy mode : All-active
State : Up
UPW Link ID : 0
Tag ID : 0
DF address : -
# On PE 2, display detailed cross-connect group information. Verify that PE 2 has established an LDP PW with PE 4 and an SRv6 PW with PE 3.
[PE2] display l2vpn xconnect-group verbose
Xconnect-group Name: vpna
Connection Name : pw1
Connection ID : 0
State : Up
MTU : 1500
PW Redundancy Mode : Slave
Diffserv Mode : -
LDP PWs:
Peer PW ID Link ID State Flag
4.4.4.9 500 0 Up Main
Create time: 2020-11-02 10:08:01
Last time status changed: 2020-11-02 10:08:01
Last time PW went down: 2020-11-02 10:08:01
SRv6 tunnels:
Peer : 3::3
Link ID : 0x1
State : Up
# On PE 2, display detailed local ES information. Verify that the LDP PW (UPW) has multihoming settings.
[PE2] display evpn es local verbose
Xconnect-group name : vpna
Connection name : pw1
ESI : 0001.0001.0001.0001.0001
Redundancy mode : All-active
State : Up
UPW Link ID : 0
Tag ID : 0
DF address : -
# Verify that CE 1 and CE 2 can ping each other. (Details not shown.)
Configuring EVPN VPWS over SRv6 with static PWs
EVPN VPWS over SRv6 tasks at a glance (with static PWs)
To configure EVPN VPWS over SRv6 with static PWs, perform the following tasks:
1. Configuring a cross-connect
2. Configuring the static SRv6 PW establishment mode
4. Applying a locator to a cross-connect for SRv6 PW establishment
5. Configuring packet forwarding methods
¡ Configuring the route recursion mode
¡ Configuring SRv6 TE policy traffic steering
This task is required if the route recursion mode is SRv6 TE mode or SRv6 TE and SRv6 BE hybrid mode.
6. Mapping an AC to a cross-connect
7. Specifying a source address for the outer IPv6 header of SRv6-encapsulated EVPN VPWS packets
8. (Optional.) Configuring FRR for EVPN VPWS over SRv6
9. (Optional.) Configuring LDP or static PWs as ACs for SRv6 PWs
10. (Optional.) Test the connectivity of an SRv6 PW
Configuring a cross-connect
1. Enter system view.
system-view
2. Enable L2VPN.
system-view
l2vpn enable
By default, L2VPN is disabled.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
3. (Optional.) Configure a PW class.
a. Create a PW class and enter its view.
pw-class class-name
For more information about this command, see MPLS Command Reference.
b. Configure the SRv6 PW data encapsulation type for the PW class.
srv6-pw-type { ethernet | vlan }
By default, the SRv6 PW data encapsulation type is Ethernet.
c. Return to system view.
quit
4. Create a cross-connect group and enter its view.
xconnect-group group-name
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
5. (Optional.) Configure a description for the cross-connect group.
description text
By default, no description is configured for a cross-connect group.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
6. (Optional.) Bring up the cross-connect group.
undo shutdown
By default, a cross-connect group is not administratively down.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
7. Create a cross-connect and enter its view.
connection connection-name
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
Configuring the static SRv6 PW establishment mode
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
3. Enter cross-connect view.
connection connection-name
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
4. Configure the static SRv6 PW establishment mode, and enter static SRv6 view of the cross-connect.
static-srv6 local-service-id local-service-id remote-service-id remote-service-id [ tunnel-policy tunnel-policy-name ]
By default, no SRv6 PW establishment mode is configured for the specified remote PE.
Configuring SRv6 SIDs
About this task
In the EVPN VPWS over SRv6 scenario, if the PEs cannot use BGP routes to establish SRv6 PW, you need to establish a static SRv6 PW between the PEs to ensure correct packet forwarding. Because the PEs cannot transmit SRv6 SID information through BGP routes, you need to configure the SRv6 SIDs assigned by the local and remote ends to the cross-connect. To configure the SRv6 SID assigned by the local end, configure the opcode command for the associated locator. To configure the SRv6 SID assigned by the remote end, configure the peer command for the remote locator in static SRv6 configuration view of the cross-connect.
The remote locator setting on the local PE must be the same as the locator setting on the remote PE. The local and remote PEs must use consistent locator, remote locator, and SRv6 SID settings. For example:
· Configuration on the local PE (PE 1):
locator pe1 ipv6-prefix 100:: 64 static 32
opcode 1 end-dx2 xconnect-group pe1 connection pe1
remote-locator pe2 ipv6-prefix 200:: 64 static 32
xconnect-group pe1
connection pe1
static-srv6 local-service-id 1 remote-service-id 2
peer 2::2 end-dx2-sid remote-locator pe2 opcode 1
The locator for the local PE is 100::/64. The SRv6 SID assigned by the local end to the cross-connect is End.DX2 SID 100::1. The remote locator is 200::/64. The SRv6 SID assigned by the remote end to the cross-connect is End.DX2 SID 200::1.
· Configuration on the remote PE (PE 2):
locator pe2 ipv6-prefix 200:: 64 static 32
opcode 1 end-dx2 xconnect-group pe2 connection pe2
remote-locator pe1 ipv6-prefix 100:: 64 static 32
xconnect-group pe2
connection pe2
static-srv6 local-service-id 1 remote-service-id 2
peer 1::1 end-dx2-sid remote-locator pe1 opcode 1
The locator for the local PE is 100::/64, and the remote locator is 200::/64. The locator for the remote PE is 200::/64, and the remote locator is 100::/64. The SRv6 SID assigned by the local PE to the cross-connect is End.DX2 SID 100::1. The SRv6 SID assigned by the remote PE to the cross-connect is End.DX2 SID 200::1.
When deploying an SRv6 PW in the EVPN VPWS over SRv6 scenario for packet forwarding, make sure the destination IPv6 address for packets is the SRv6 SID of the remote locator. Upon receiving the packets, the remote PE searches the local locator SID forwarding table, and perform one of the following operations:
· If a matching SRv6 SID is found in the local locator, the remote PE forwards the packets based on the SRv6 SID.
· If no matching SRv6 SID is found in the local locator, the remote PE discards the packets.
Restrictions and guidelines
When you create a remote locator, you must specify an IPv6 address prefix, prefix length, and static length for the remote locator. When you enter the view of an existing remote SRv6 locator, you only need to specify the remote locator name.
Each remote locator must have a unique name.
Do not specify the same IPv6 address prefix for different remote locators. In addition, the IPv6 address prefixes of different remote locators cannot overlap.
Do not specify the same IPv6 address prefix for the remote locator and local locator. In addition, the IPv6 address prefixes of the remote locator and local locator cannot overlap.
For more information about the commands in this section, see SRv6 commands in Segment Routing Command Reference.
Procedure
1. Enter system view.
system-view
2. Enable SRv6 and enter SRv6 view.
segment-routing ipv6
3. Configure a locator and enter SRv6 locator view.
locator locator-name [ ipv6-prefix ipv6-address prefix-length [ args args-length | static static-length ] * ]
4. Configure an opcode for End.DX2 SIDs.
opcode { opcode | hex hex-opcode } end-dx2 xconnect-group group-name connection connection-name
5. (Optional.) Configure an opcode for End.DX2L SIDs.
opcode { opcode | hex hex-opcode } end-dx2l xconnect-group group-name connection connection-name
Use this command only in the bypass PW network.
6. Configure a remote locator and enter remote SRv6 locator view.
remote-locator remote-locator-name [ ipv6-prefix ipv6-address prefix-length [ args args-length | static static-length ] * ]
Applying a locator to a cross-connect for SRv6 PW establishment
About this task
Perform this task to specify the SRv6 SID for the local and remote PEs to assign to the cross-connect. This task allows a static SRv6 PW to be established between the PEs.
Procedure
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect view.
connection connection-name
4. Apply a local locator to the cross-connect.
segment-routing ipv6 locator locator-name [ dx2l-locator dx2l-locator-name ] [ auto-sid-disable ]
By default, no locator is applied to a cross-connect.
5. Enter SRv6 PW view of the cross-connect.
static-srv6 local-service-id local-service-id remote-service-id remote-service-id [ tunnel-policy tunnel-policy-name ]
By default, no SRv6 PW establishment mode is configured for the specified remote PE.
6. Create a static SRv6 PW, and static SRv6 PW view of the cross-connect.
peer ipv6-address end-dx2-sid remote-locator locator-name opcode opcode [ color color-value | tunnel-policy tunnel-policy-name ]
By default, no static SRv6 PWs exist.
Configuring the route recursion mode
About this task
After a PE receives a customer packet destined for an End.DX2 or End.DX2L SID, it forwards the packet according to the route recursion mode.
· SRv6 BE mode—This mode is also called SID-based forwarding mode. In this mode, the PE first encapsulates the End.DX2 or End.DX2L SID into the packet. Then, the PE searches the IPv6 routing table based on the End.DX2 or End.DX2L SID encapsulated in the packet to forward the packet.
· SRv6 TE mode—This mode is also called SRv6 TE policy-based forwarding mode. In this mode, the PE first searches for a matching SRv6 TE policy based on the remote PE address. Then, the PE adds an SRH to the packet. The SRH includes the End.DX2 or End.DX2L SID and the SID list of the SRv6 TE policy. Finally, the PE forwards the encapsulated packet through the SRv6 TE policy. For more information, see "Configuring SRv6 TE policies."
· SRv6 TE and SRv6 BE hybrid mode—In this mode, the PE preferentially uses the SRv6 TE mode to forward the packet. If no SRv6 TE policy is available for the packet, the PE forwards the packet in SRv6 BE mode.
In SRv6 TE mode, you can associate the SRv6 TE policy that contains paths between two PEs with the static BFD session specified for testing the IP connectivity between the PEs. For this purpose, you must execute the segment-routing ipv6 traffic-engineer command with the track-bfd keyword and create a static BFD session to test the IP connectivity between the two PEs. If the static BFD session goes down, the state of the SRv6 TE policy also changes to down. This mechanism avoids traffic forwarding failure caused by path disconnectivity. For more information about static BFD, see High Availability Configuration Guide. For more information about testing the IP connectivity between two PEs, see "Using a static BFD session to test the connectivity of an SRv6 PW."
Prerequisites
To use the SRv6 TE mode or the SRv6 TE and SRv6 BE hybrid mode, you must configure a tunnel policy and SRv6 TE policy. For more information, see tunnel policy configuration in MPLS Configuration Guide and "Configuring SRv6 TE policies."
Procedure
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect view.
connection connection-name
4. Enter cross-connect static SRv6 view.
static-srv6 local-service-id local-service-id remote-service-id remote-service-id [ tunnel-policy tunnel-policy-name ]
5. Configure the route recursion mode.
segment-routing ipv6 { best-effort | traffic-engineering [ track-bfd ] [ best-effort ] }
By default, a PE searches the IPv6 routing table based on the next hop of a matching route to forward traffic.
Configuring SRv6 TE policy traffic steering
Restrictions and guidelines for SRv6 TE policy traffic steering
This task is required if the route recursion mode is SRv6 TE mode or SRv6 TE and SRv6 BE hybrid mode.
If both color-based traffic steering and tunnel policy-based traffic steering are configured, the device performs traffic steering in the following sequence:
· Performs tunnel policy-based traffic steering.
· Performs color-based traffic steering.
· Performs traffic steering based on the preferred tunnel policy. (The tunnel policy does not take effect when color-based traffic steering is configured.)
· Performs traffic steering based on the load sharing tunnel policy. If this traffic steering method is not configured, the default tunnel policy applies.
Configuring color-based traffic steering
About this task
In a network where the SRv6 PWs are statically established, you can configure the color attribute for the static SRv6 PW, static backup SRv6 PW, and bypass SRv6 PW. The PE searches for an SRv6 TE policy that has the same color and endpoint address as the color and remote PE address of a static SRv6 PE. If a matching SRv6 TE policy exists, the device recurses the static SRv6 PE to that SRv6 TE policy. When the device receives packets that match the static SRv6 PE, it forwards the packets through the SRv6 TE policy.
Use one of the following methods to configure colors for BGP EVPN routes:
· Static SRv6 PW-based coloring—Configure a color attribute for the SRv6 PW by specifying the color keyword for the backup-peer, bypass-peer, or peer command. This color attribute applies to only the specified SRv6 PW.
· Default color—Specify a color as the default color with the default color command in cross-connect static SRv6 view. This color attribute applies to all SRv6 PWs in static SRv6 view of the specified cross-connect.
Restrictions and guidelines
A static SRv6 PW preferentially uses the color attribute specified with the color keyword. If the color keyword is not specified, the SRv6 PW uses the color attribute configured with the default color command.
Configuring static SRv6 PW-based coloring
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect view.
connection connection-name
4. Enter static SRv6 view of the cross-connect.
static-srv6 local-service-id local-service-id remote-service-id remote-service-id [ tunnel-policy tunnel-policy-name ]
By default, no SRv6 PW establishment mode is configured for the specified remote PE.
5. Create a static SRv6 PW, and static SRv6 PW view of the cross-connect.
peer ipv6-address end-dx2-sid remote-locator locator-name opcode opcode color color-value [ tunnel-policy tunnel-policy-name ]
By default, no static SRv6 PWs exist.
Configuring the default color for the static SRv6 PW
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter static SRv6 view of the cross-connect.
static-srv6 local-service-id local-service-id remote-service-id remote-service-id [ tunnel-policy tunnel-policy-name ]
By default, no SRv6 PW establishment mode is configured for the specified remote PE.
4. Configure the default color for the static SRv6 PW.
default color color-value
By default, no default color is configured.
Configuring tunnel policy-based traffic steering
About this task
In a network where the SRv6 PWs are statically established, the PE searches the tunnel policies for a matching SRv6 TE policy based on the remote PE address of a matching static SRv6 PW. Configure a preferred tunnel or load sharing tunnel policy that uses the SRv6 TE policy. In this way, the SRv6 TE policy will be used as the public tunnel to carry the SRv6 PW that forwards the packets of private network packets.
Restrictions and guidelines
In a network where the SRv6 PWs are statically established, you can configure the tunnel policy for a static SRv6 PW by using the static-srv6 local-service-id remote-service-id or peer command. The configuration with the static-srv6 local-service-id remote-service-id command applies to all static SRv6 PWs in this view. The configuration with the peer command applies to the specified static SRv6 PW. A static SRv6 PW preferentially uses the configuration with the peer command. If the static SRv6 PW does not match the tunnel policy specified in the peer command, the tunnel policy specified in the static-srv6 local-service-id remote-service-id command applies.
Configuring a tunnel policy
1. Enter system view.
system-view
2. Create a tunnel policy and enter tunnel policy view.
tunnel-policy tunnel-policy-name [ default ]
3. Configure the tunnel policy. Choose a minimum of one option:
¡ Specify an SRv6 TE policy as a preferred tunnel of the tunnel policy.
preferred-path srv6-policy { name srv6-policy-name | end-point ipv6 ipv6-address color color-value }
By default, no preferred tunnel is specified for a tunnel policy.
¡ Configuring SRv6 TE policy load sharing for the tunnel policy.
select-seq srv6-policy load-balance-number number
By default, no load sharing tunnel policy is configured.
For more information about the tunnel policy commands, see MPLS Command Reference.
Specifying the tunnel policy for a static SRv6 PW
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect view.
connection connection-name
4. Configure the static SRv6 PW establishment mode, and enter static SRv6 view of the cross-connect.
static-srv6 local-service-id local-service-id remote-service-id remote-service-id tunnel-policy tunnel-policy-name
By default, no SRv6 PW establishment mode is configured for the specified remote PE.
5. Create a static SRv6 PW, and enter static SRv6 view of the cross-connect.
peer ipv6-address end-dx2-sid remote-locator locator-name opcode opcode [ color color-value ] tunnel-policy tunnel-policy-name
By default, no static SRv6 PWs exist.
Mapping an AC to a cross-connect
Specifying a source address for the outer IPv6 header of SRv6-encapsulated EVPN VPWS packets
Restrictions and guidelines
To ensure correct traffic forwarding in an EVPN VPWS over SRv6 network, you must specify a source address for the outer IPv6 header of SRv6-encapsulated EVPN VPWS packets.
You cannot specify a loopback address, link-local address, multicast address, or unspecified address as the source IPv6 address. You must specify an IPv6 address of the local device as the source IPv6 address, and make sure the IPv6 address has been advertised by a routing protocol. As a best practice, specify a loopback interface address of the local device as the source IPv6 address.
Procedure
1. Enter system view.
system-view
2. Enter SRv6 view.
segment-routing ipv6
3. Specify a source address for the outer IPv6 header of SRv6-encapsulated EVPN VPWS packets.
encapsulation source-address ipv6-address [ ip-ttl ttl-value ]
By default, no source address is specified for the outer IPv6 header of SRv6-encapsulated EVPN VPWS packets.
Configuring FRR for EVPN VPWS over SRv6
Configuring local FRR
About this task
In a static primary/backup SRv6 PW network, when an AC fails at the site, the remote PE cannot immediately detect the AC failure. Traffic forwarded to the PE will be dropped. This feature can establish a static bypass SRv6 PW to temporarily forward traffic for protecting the AC link between the PEs in the failover group, avoiding packet loss.
Restrictions and guidelines
The remote PE address and remote SID specified for the bypass SRv6 PW cannot be the same as those specified in any existing SRv6 PWs.
The SRv6 PW redundancy protection and bypass SRv6 PW features are mutually exclusive. You cannot configure both the bypass-peer command (in cross-connect AC view) and the backup-peer command (in cross-connect static SRv6 PW view).
Procedure
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect view.
connection connection-name
4. Enter cross-connect AC view.
ac interface interface-type interface-number [ access-mode { ethernet | vlan } ] [ track track-entry-number&<1-15> ]
By default, no interface is bound to a cross-connect.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
5. Configure a static bypass SRv6 PW for protecting the AC link, and enter cross-connect bypass SRv6 PW view.
bypass-peer ipv6-address end-dx2l-sid remote-locator locator-name opcode opcode [ color color-value | tunnel-policy tunnel-policy-name ] ac-bypass
By default, no cross-connect bypass SRv6 PW exists.
Configuring remote FRR
About this task
Remote FRR enables two PEs on an EVPN VPWS over SRv6 network to set up a primary static PW and a backup static PW between them to ensure high availability. The PEs use the primary static PW to forward traffic as long as it is available. When the primary static PW fails, the PEs switch traffic to the backup static PW.
Restrictions and guidelines
The remote PE address and remote SID specified for the backup SRv6 PW cannot be the same as those specified in any existing static or dynamic SRv6 PWs.
The SRv6 PW redundancy protection and bypass SRv6 PW features are mutually exclusive. If you execute backup-peer command on the primary SRv6 PW to configure a backup SRv6 PW, you cannot execute the bypass-peer command in cross-connect AC view to configure a static bypass SRv6 PW. If you execute the bypass-peer command in cross-connect AC view to configure a static bypass SRv6 PW, you cannot execute backup-peer command on the primary SRv6 PW to configure a backup SRv6 PW.
Procedure
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect view.
connection connection-name
4. Enter cross-connect static SRv6 view.
static-srv6 local-service-id local-service-id remote-service-id remote-service-id [ tunnel-policy tunnel-policy-name ]
By default, no SRv6 PW establishment mode is configured for the specified remote PE.
5. Enter cross-connect static SRv6 PW view.
peer ipv6-address end-dx2-sid remote-locator locator-name opcode opcode [ color color-value | tunnel-policy tunnel-policy-name ]
By default, no static SRv6 PWs exist.
6. Configure a static backup SRv6 PW for the cross-connect, and enter cross-connect static backup SRv6 PW view.
backup-peer ipv6-address end-dx2-sid remote-locator locator-name opcode opcode [ color color-value | tunnel-policy tunnel-policy-name ]
By default, no static SRv6 PW exists.
Configuring LDP or static PWs as ACs for SRv6 PWs
About LDP or static PW AC configuration for SRv6 PWs
Use this feature to ensure that an MPLS L2VPN network and an EVPN VPWS over SRv6 network can communicate with each other.
Restrictions and guidelines for LDP or static PW AC configuration for SRv6 PWs
At a multihomed site, all PEs must use the same local service ID and remote service ID in the same ES.
As a best practice, set the same redundancy mode for the UPWs that use the same ESI at a multihomed site.
If the all-active redundancy mode is used at a multihomed site, you must enable the dual receive feature for PW redundancy on the multihomed PEs. To enable this feature, use the protection dual-receive command.
Prerequisites for LDP or static PW AC configuration for SRv6 PWs
Complete the following tasks:
· In the MPLS network, complete MPLS L2VPN settings on the PEs.
· In the SRv6 network, complete EVPN VPWS over SRv6 settings on the PEs.
Configuring LDP PWs as ACs for SRv6 PWs
Restrictions and guidelines
The data encapsulation type of an LDP PW must be the same as the access mode of the ACs mapped to the same cross-connect as the LDP PW. If they are different, perform one of the following tasks:
· Use the pw-type command on the PW class to which the LDP PW belongs to change the PW data encapsulation type.
· Use the ac interface command for the ACs and specify the access-mode parameter in the command to change the access mode of the ACs.
Procedure
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect group EVPN instance view.
evpn encapsulation srv6
4. Return to cross-connect group view.
quit
5. Enter cross-connect view.
connection connection-name
6. Create an LDP PW for the cross-connect and enter cross-connect PW view.
peer ip-address pw-id pw-id [ ignore-standby-state ] [ admin | pw-class class-name | tunnel-policy tunnel-policy-name ] *
The LDP PW configured by using this command is an UPW, which acts as an AC for the EVPN VPWS over SRv6 network.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
7. (Optional.) Assign an ESI to the UPW.
esi esi-id
By default, no ESI is assigned to an UPW.
At a multihomed site, use this command on the PEs in the MPLS L2VPN and EVPN VPWS over SRv6 networks.
For more information about this command, see EVPN commands in EVPN Command Reference.
8. (Optional.) Set the redundancy mode of the UPW.
evpn redundancy-mode { all-active | single-active }
By default, the redundancy mode is all-active.
At a multihomed site, use this command on the PEs in the MPLS L2VPN and EVPN VPWS over SRv6 networks.
For more information about this command, see EVPN commands in EVPN Command Reference.
9. Configure a backup LDP PW for the cross-connect and enter cross-connect backup PW view.
backup-peer ip-address pw-id pw-id [ pw-class class-name | tunnel-policy tunnel-policy-name ] *
At a multihomed site, use this command on the multihomed PEs.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
10. Return to cross-connect view.
quit
quit
11. Enter cross-connect static SRv6 view.
static-srv6 local-service-id local-service-id remote-service-id remote-service-id [ tunnel-policy tunnel-policy-name ]
By default, no SRv6 PW establishment mode is configured for the specified remote PE.
12. Create a static SRv6 PW and enter cross-connect static SRv6 PW view.
peer ipv6-address end-dx2-sid remote-locator locator-name opcode opcode [ color color-value | tunnel-policy tunnel-policy-name ]
By default, no static SRv6 PW exists.
Configuring static PWs as ACs for SRv6 PWs
1. Enter system view.
system-view
2. Enter cross-connect group view.
xconnect-group group-name
3. Enter cross-connect group EVPN instance view.
evpn encapsulation srv6
4. Return to cross-connect group view.
quit
5. Enter cross-connect view.
connection connection-name
6. Create a static PW for the cross-connect and enter cross-connect PW view.
peer ip-address pw-id pw-id in-label label-value out-label label-value [ admin | pw-class class-name | tunnel-policy tunnel-policy-name ] *
The static PW configured by using this command is an UPW, which acts as an AC for the EVPN VPWS over SRv6 network.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
7. (Optional.) Assign an ESI to the UPW.
esi esi-id
By default, no ESI is assigned to an UPW.
At a multihomed site, use this command on the PEs in the MPLS L2VPN and EVPN VPWS over SRv6 networks.
For more information about this command, see EVPN commands in EVPN Command Reference.
8. (Optional.) Set the redundancy mode of the UPW.
evpn redundancy-mode { all-active | single-active }
By default, the redundancy mode is all-active.
At a multihomed site, use this command on the PEs in the MPLS L2VPN and EVPN VPWS over SRv6 networks.
For more information about this command, see EVPN commands in EVPN Command Reference.
9. Configure a backup static PW for the cross-connect and enter cross-connect backup PW view.
backup-peer ip-address pw-id pw-id in-label label-value out-label label-value [ pw-class class-name | tunnel-policy tunnel-policy-name ] *
At a multihomed site, use this command on the multihomed PEs.
For more information about this command, see MPLS L2VPN commands in MPLS Command Reference.
10. Return to cross-connect view.
quit
quit
11. Enter cross-connect static SRv6 view.
static-srv6 local-service-id local-service-id remote-service-id remote-service-id [ tunnel-policy tunnel-policy-name ]
By default, no SRv6 PW establishment mode is configured for the specified remote PE.
12. Create a static SRv6 PW and enter cross-connect static SRv6 PW view.
peer ipv6-address end-dx2-sid remote-locator locator-name opcode opcode [ color color-value | tunnel-policy tunnel-policy-name ]
By default, no static SRv6 PW exists.
Test the connectivity of an SRv6 PW
Using ping to test the connectivity of an SRv6 PW
About this task
In an EVPN VPWS over SRv6 network, a PE transmits data packets to a remote PE over an SRv6 PW. Perform this task to test the connectivity of the SRv6 PW from the local PE to the remote PE when packet loss or traffic interruption occurs between the PEs.
The test process is as follows:
1. The local PE constructs an MPLS echo request packet and searches for the SRv6 tunnel that matches the specified cross-connect group name, local service ID, and remote service ID. After obtaining the End.DX2 SID of the SRv6 tunnel, the PE adds a UDP header and an IPv6 header to the packet and forwards the packet to the remote PE.
2. Upon receiving the MPLS echo request packet, the remote PE replies to the request.
3. The local PE identifies the connectivity of the SRv6 PW based on whether it has received MPLS echo replies from the remote PE and the reply response time. In addition, the local PE outputs statistics about the ping operation.
Procedure
To test the connectivity of an SRv6 PW from the local PE to the remote PE in an EVPN VPWS over SRv6 network, execute the following command in any view:
ping static vpws srv6 xconnect-group group-name local-service-id remote-service-id [ end-op endop ] [ -a source-ipv6 | -c count | -h hop-limit | -m interval | -r reply-mode | -s packet-size | -t time-out | -tc tc ] *
Using tracert to test the connectivity of an SRv6 PW
About this task
In an EVPN VPWS over SRv6 network, a PE transmits data packets to a remote PE over an SRv6 PW. Perform this task to trace the path of the SRv6 PW from the local PE to the remote PE when packet loss or traffic interruption occurs between the PEs. This task helps you locate the failed nodes on the path.
The test process is as follows:
1. The local PE constructs an MPLS echo request packet and searches for the SRv6 tunnel that matches the specified cross-connect group name, local service ID, and remote service ID. After obtaining the End.DX2 SID of the SRv6 tunnel, the PE adds a UDP header and an IPv6 header to the packet and forwards the packet to the remote PE. In the IPv6 header, the value of the Hop limit field is set to 1.
2. When the next node receives the packet, the value of the Hop limit field changes to 0. Then, the node sends an ICMPv6 timeout packet to the first node (the local PE).
3. When the local PE receives the ICMPv6 timeout packet, it increases the value of the Hop limit field by one in the MPLS echo request packet. Then, the local PE forwards the request packet to the remote PE. The value of the Hop limit field is 2.
4. The value of the Hop limit field decreases by one each time the request packet reaches a node. When the value of the Hop limit field decreases to 0, the node that receives the request packet responds to the first node with an ICMPv6 timeout packet. If the node that receives the request packet is the destination node, it sends an MPLS echo reply packet to the first node.
5. The local PE repeats the previous step until one of the following conditions exist:
¡ The local PE has not received any reply packets before the reply timeout time expires for all request packets.
¡ The local PE receives a reply packet from the remote PE.
6. The local PE identifies the connectivity of the SRv6 PW based on whether it has received MPLS echo reply packets from the remote PE and the reply response time. In addition, the local PE outputs statistics about the tracert operation.
Procedure
To trace the path of an SRv6 PW from the local PE to the remote PE in an EVPN VPWS over SRv6 network, execute the following command in any view:
tracert static vpws srv6 xconnect-group group-name local-service-id remote-service-id [ end-op endop ] [ -a source-ip | -h hop-limit | -r reply-mode | -t time-out | -tc tc ] *
Using a static BFD session to test the connectivity of an SRv6 PW
About this task
Enable BFD on both ends of an SRv6 PW for quick link connectivity detection. The PEs periodically send BFD control packets to each other out of the Layer 3 interfaces mapped to the cross-connect of the SRv6 PW. A PE sets the PW state to Down if it does not receive control packets from the remote end within a detection interval. To avoid packet forwarding failure, the PE switches packets to the backup SRv6 PW or an equal-cost SRv6 PW.
Restrictions and guidelines
Make sure the static BFD session is in Asynchronous mode.
Perform this task on both PEs at the two ends of an SRv6 PW.
In a primary/backup SRv6 PW scenario or an equal-cost SRv6 PW scenario, you must configure a static BFD session for each SRv6 PW to detect their connectivity.
If you do not specify the discriminator auto keywords when creating a static BFD session, you must configure the local and remote discriminators for the session by using the discriminator command. For more information about the discriminator command, see BFD commands in High Availability Command Reference.
Procedure
1. Enter system view.
system-view
2. Create a static BFD session for SRv6 PW connectivity detection and enter static BFD session view.
bfd static session-name evpn-vpws-srv6 interface interface-type interface-number remote-peer remote-ipv6-address [ discriminator auto ]
Display and maintenance commands for EVPN VPWS over SRv6
Execute display commands in any view in user view.
|
Task |
Command |
|
Display L2VPN SRv6 forwarding information. |
display l2vpn forwarding srv6 [ xconnect-group group-name ] [ verbose ] |
|
Display L2VPN information about Layer 3 interfaces mapped to cross-connects. |
display l2vpn interface [ xconnect-group group-name | interface-type interface-number ] [ verbose ] |
|
Display L2VPN SRv6 information. |
display l2vpn peer srv6 [ xconnect-group group-name ] [ state-machine | verbose ] |
|
Display information about Ethernet service instances. |
display l2vpn service-instance [ interface interface-type interface-number [ service-instance instance-id ] ] [ verbose ] |
|
Display information about cross-connect groups. |
display l2vpn xconnect-group [ evpn-srv6 | name group-name [ connection connection-name ] | static-srv6 ] [ count | verbose ] |