- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 09-Security | 244.16 KB |
WLAN security overview
802.11 networks are susceptible to a wide array of threats such as unauthorized access points and clients, ad hoc networks, and DoS attacks. To ensure security, the wireless intrusion detection system (WIDS) is introduced. WIDS provides early detection of malicious attacks and intrusions on a wireless network without affecting network performance, and provides real-time countermeasures.
WLAN security provides these features:
· WIDS attack detection
· Blacklist and white list
WIDS attack detection
The WIDS attack detection function detects intrusions or attacks on a WLAN network, and informs the network administrator of the attacks through recording information or sending logs. WIDS detection supports detection of the following attacks:
· Flood attack
· Spoofing attack
· Weak IV attack
Flood attack detection
A flood attack refers to the case where WLAN devices receive large volumes of frames of the same kind within a short span of time. When this occurs, the WLAN devices are overwhelmed with frames from this device and frames from authorized clients get dropped.
WIDS attacks detection counters this flood attack by constantly keeping track of the density of traffic generated by each device. When this density exceeds the tolerance limit, the device is considered to be flooding the network. Subsequent frames from this device are not processed. If the dynamic blacklist feature is enabled, the detected device is added to the blacklist, and is forbidden to access the WLAN for a period of time.
WIDS detects the following types of frames:
· Authentication requests and de-authentication requests
· Association requests, disassociation requests and reassociation requests
· Probe requests
· 802.11 null data frames
· 802.11 action frames.
Spoofing attack detection
In this kind of attack, a potential attacker can send frames in the air on behalf of another device. For instance, a client in a WLAN has been associated with an AP and is operating properly. In this case, a spoofed de-authentication frame can cause a client to get de-authenticated from the network and can affect the normal operation of the WLAN.
At present, spoofing attack detection counters this type of attack by detecting broadcast de-authentication and disassociation frames sent on behalf of an AP. When such a frame is received, it is identified as a spoofed frame, and the attack is immediately logged.
Weak IV detection
Wired Equivalent Privacy (WEP) uses an Initialization Vector (IV) to encrypt each frame. An IV and a key are used to generate a key stream, and thus encryptions using the same key have different results. When a WEP frame is sent, the IV used in encrypting the frame is also sent as part of the frame header.
However, if a WLAN device generates IVs in an insecure way (for example, if it uses a fixed IV for all frames), the shared secret key may be exposed to potential attackers. When the shared secret key is compromised, the attacker can access network resources.
Weak IV detection counters this attack by verifying the IVs in WEP frames. Whenever a frame with a weak IV is detected, it is immediately logged.
Blacklist and white list
Blacklist and white list
You can configure the blacklist and white list functions to filter frames from WLAN clients and thereby implement client access control.
The WLAN client access control is accomplished through the following three types of lists.
· White list—Contains the MAC addresses of all clients allowed to access the WLAN. If the white list is used, only permitted clients can access the WLAN, and all frames from other clients will be discarded.
· Static blacklist—Contains the MAC addresses of clients forbidden to access the WLAN. This list is manually configured.
· Dynamic blacklist—Contains MAC addresses of clients whose frames will be dropped. A client is dynamically added to the list if it is considered sending attacking frames until the timer of the entry expires.
Frame process procedure
When an AP receives an 802.11 frame, it checks the source MAC address of the frame and processes the frame as follows:
1. If the source MAC address does not match any entry in the white list, it is dropped. If there is a match, the frame is considered valid and will be further processed.
2. If no white list entries exist, the static and dynamic blacklists are searched.
¡ If the source MAC address matches an entry in any of the two lists, it is dropped.
¡ If there is no match, or no blacklist entries exist, the frame is considered valid and is further processed.
Configuring WIDS
Configuring WIDS
1. Select Security > WIDS from the navigation tree to enter the WIDS Setup tab.
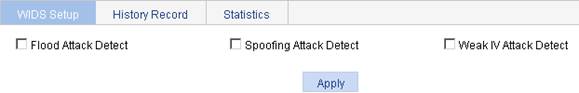
2. Configure WIDS as described in Table 1.
3. Click Apply.
|
Item |
Description |
|
Flood Attack Detect |
If you select the box, flood attack detection is enabled. It is disabled by default. |
|
Spoofing Attack Detect |
If you select the box, spoofing attack detection is enabled. It is disabled by default. |
|
Weak-IV Attack Detect |
If you select the box, Weak IV attack detection is enabled. It is disabled by default. |
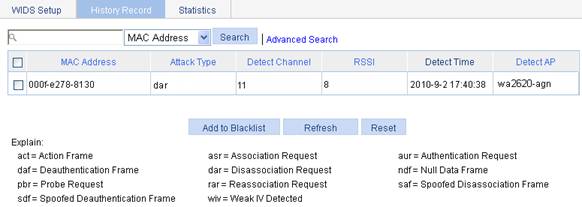
Displaying history record
1. Select Security > WIDS from the navigation tree.
2. Click the History Record tab to enter the history information page.
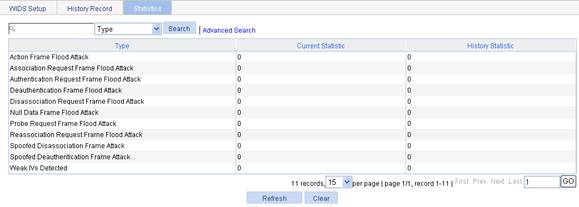
Displaying statistics information
1. Select Security > WIDS from the navigation tree.
2. Click the Statistics tab to enter the statistics information page.
Figure 3 Statistics information
Configuring the blacklist and white list functions
Configuring dynamic blacklist
1. Select Security > Filter from the navigation tree to enter the Blacklist tab.
Figure 4 Dynamic blacklist configuration page

2. Configure a dynamic blacklist as described in Table 2.
3. Click Apply.
|
Item |
Description |
|
Dynamic Blacklist |
Enable—Enable dynamic blacklist. Disable—Disable dynamic blacklist.
Before enabling the dynamic blacklist function, select the Flood Attack Detect check box in the WIDS Setup page. |
|
Blacklisted For |
Configure the lifetime of the entries in the blacklist. When the lifetime of an entry expires, the entry is removed from the blacklist. |
At present, these attacks can be detected through a dynamic blacklist: Assoc-Flood, Reassoc-Flood, Disassoc-Flood, ProbeReq-Flood, Action-Flood, Auth-Flood, Deauth-Flood and NullData-Flood.
Configuring static blacklist
1. Select Security > Filter from the navigation tree to enter the Blacklist tab.
2. Click the Static tab to enter the static blacklist configuration page.
3. Click Add Static to enter the page for adding a static blacklist.
Figure 5 Adding a static blacklist
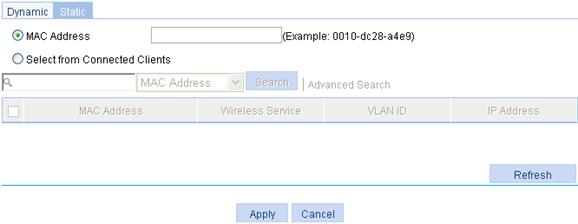
4. Add a static blacklist as described in Table 3.
5. Click Apply.
|
Item |
Description |
|
MAC Address |
Select the MAC Address box, and then add a MAC address to the static black list. |
|
Select from Connected Clients |
If you select the box, the table below lists the current existing clients. Select the boxes of the clients to add their MAC addresses to the static blacklist. |
Configuring white list
1. Select Security > Filter from the navigation tree.
2. Click the Whitelist tab.
3. Click Add to enter the white list configuration page.
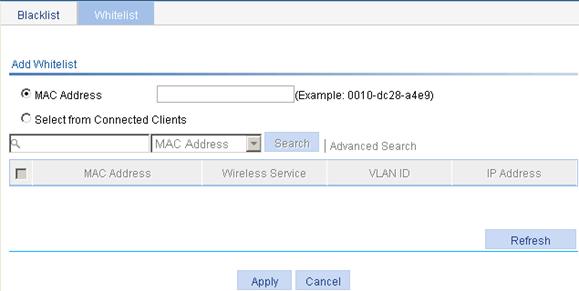
4. Add a white list as described in Table 4.
5. Click Apply.
|
Item |
Description |
|
MAC Address |
Select the MAC Address box and then add a MAC address to the white list. |
|
Select from Connected Clients |
If you select the box, the table below lists the current existing clients. Select the boxes of the clients to add their MAC addresses to the white list. |
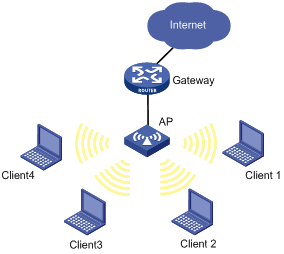
If an AP has the user isolation feature enabled, clients associated with it are isolated at Layer 2.
As shown in Figure 7, after user isolation is enabled on the AP, all the clients cannot ping each other or learn each other's MAC or IP addresses because they cannot exchange Layer 2 packets.
1. Select Security > User Isolation from the navigation tree to enter the user isolation configuration page.
Figure 8 Configuring user isolation
2. Configure user isolation as described in Table 5.
3. Click Apply.
|
Item |
Description |
|
User Isolate |
· Enable—Enable user isolation on the AP to isolate the clients associated with it at Layer 2. · Disable—Disable the user isolation. By default, wireless user isolation is disabled. |
