- Table of Contents
-
- H3C Access Controllers Web-Based Configuration Guide(E3703P61 R2509P61 R3709P61 R2609P61 R3509P61)-6W103
- 00-Preface
- 01-About
- 02-Web overview
- 03-Login
- 04-Quick Start
- 05-Summary
- 06-Device
- 07-Network
- 08-AP Configuration
- 09-Wireless Service
- 10-WLAN Roaming Configuration
- 11-Radio Configuration
- 12-Authentication
- 13-Security
- 14-QoS Configuration
- 15-Advanced Settings
- 16-Stateful Failover Configuration
- 17-VPN
- 18-SSL VPN Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 06-Device | 986.72 KB |
Contents
Registering an enhanced license
Displaying registered enhanced licenses
Configuring basic device settings
Generating the diagnostic information file
Configuring the time zone and daylight saving time
System time configuration example
Setting buffer capacity and refresh interval
Initializing the configuration
Displaying interface information and statistics
Configuring a WAN subinterface
Interface management configuration example
Recommended configuration procedure
Configuring ports for a mirroring group
Port mirroring configuration example
Switching the user access level to the management level
Configuring SNMP trap function
Displaying SNMP packet statistics
SNMPv1/SNMPv2c configuration example
Configuring a management IP address
Managing licenses
A license controls the maximum number of online APs. You can add a license on a device to increase the maximum number of online APs that the device supports.
Support for licenses depends on the device model. Meanwhile, the upper limit of online APs that a device supports varies with device models. For more information, see "About the H3C Access Controllers Web-Based Configuration Guide."
Adding a license
|
|
IMPORTANT: After adding a license successfully, you must reboot the device to validate the newly added license. |
Support for adding licenses depends on the device model. For more information, see "About the H3C Access Controllers Web-Based Configuration Guide."
You can also increase the number of allowed APs by registering an enhanced license. For more information about enhanced licenses, see "Configuring enhanced licenses."
To add a license:
1. Select Device > License from the navigation tree.
The License tab appears.

2. Configure license information as described in Table 1.
3. Click Add.
|
Item |
Description |
|
License Key |
License key of the license |
|
Activation Key |
Activation key of the license. |
Displaying a license
1. Select Device > License from the navigation tree.
The page in Figure 1 appears.
2. View license information as described in Table 2.
|
Field |
Description |
|
default AP number |
Default number of APs that the device can support. |
|
max AP number |
Maximum number of APs that the device can support. |
|
current AP number |
Current number of APs that the device supports. |
|
License Key |
License key of the license. |
|
Activation Key |
Activation key of the license. |
|
AP number |
Number of allowed APs that are added by the license. |
Configuring enhanced licenses
Support for enhanced licenses depends on the device model. For more information, see "About the H3C Access Controllers Web-Based Configuration Guide."
Features including WIPS, IAA, RPF, and HACC and the number of manageable APs require licenses and registration before they can be used. For more information about the registration, see H3C Access Controllers License Activation and Registration Guide.
Registering an enhanced license
|
|
IMPORTANT: After registering an enhanced license, you must reboot the device to validate the newly added features. |
You can also increase the number of allowed APs by adding a license. For more information about license, see "Managing licenses."
To register an enhanced license:
1. Select Device > License from the navigation tree.
2. Click the Enhanced License tab.
The page in Figure 2 appears.
3. Configure enhanced license information as described in Table 3.
4. Click Add.
|
Item |
Description |
|
Feature Name |
Select the name of the feature to be registered. For example: · IAA—Enables intelligent application aware (IAA) on the device. · RFP—Enables radio frequency prevention (RFP) on the device. · WIPS—Enables wireless intrusion prevention system (WIPS) on the device. · HACC—Enables access controller hardware acceleration (HACC) on the device. · AP—Increases the number of allowed APs. |
|
Activation Key |
Activation key of the license. The activation key is in the format of XXXXX-XXXXX-XXXXX-XXXXX-XXXXX-XXXXX-XXXXX, where X represents a character, including case-sensitive letters, digits, plus sign (+), and slash (/).The activation key must conform to this format to ensure a successful register. You can register on www.h3c.com.hk to obtain the activation key by using the License Key, the device serial number, and verification code contained in New H3C Technologies Co., Ltd. Software License Certificate. |
Displaying registered enhanced licenses
1. Select Device > License from the navigation tree.
2. Click the Enhanced License tab.
The page in Figure 2 appears.
3. View the registered enhanced licenses at the lower part of the page.
Table 4 Field description
|
Field |
Description |
|
Feature Name |
Name of the feature registered. |
|
Activation Key |
Activation key of the license. The activation key is in the format of XXXXX-XXXXX-XXXXX-XXXXX-XXXXX-XXXXX-XXXXX, where X represents a character, including case-sensitive letters, digits, plus sign (+), and slash (/).The activation key must conform to this format to ensure a successful register. You can register on www.h3c.com to obtain the activation key by using the License Key, the device serial number, and verification code contained in New H3C Technologies Co., Ltd. Software License Certificate. |
|
Available Time Left |
Time left for the license. After the time elapses, the license expires. The value Forever means that the license is an official license. |
|
AP Number |
Number of APs that the license supports. |
Configuring basic device settings
The device basic information feature allows you to:
· Set the system name of the device. The configured system name will be displayed at the top of the navigation bar.
· Set the idle timeout period for a logged-in user. The system logs an idle user off the Web for security purposes after the configured period.
Configuring system name
1. Select Device > Basic from the navigation tree
The page for configuring the system name appears.
Figure 3 Configuring the system name

2. Set the system name for the device.
3. Click Apply.
Configuring Web idle timeout
1. Select Device > Basic from the navigation tree.
2. Click the Web Idle Timeout tab.
The page for configuring Web idle timeout period appears.
Figure 4 Configuring Web idle timeout
3. Set the Web idle timeout for a logged-in user.
4. Click Apply.
Maintaining devices
Upgrading software
|
IMPORTANT: During a software upgrade, avoid performing any operation on the Web interface. Otherwise, the upgrade operation might be interrupted. |
A boot file, also known as the system software or device software, is an application file used to boot the device. Software upgrade allows you to obtain a target application file from the local host and set the file as the boot file to be used at the next reboot. You can keep the original filename after you obtain the target application file from the local host. In addition, you can select whether to reboot the device to make the upgrade software take effect.
To upgrade software:
1. Select Device > Device Maintenance from the navigation tree.
The software upgrade configuration page appears.
Figure 5 Software upgrade configuration page

2. Configure the software upgrade parameters as described in Table 5.
3. Click Apply.
|
Item |
Description |
|
File |
Specify the path of the local application file, which must be with the extension .app or .bin. |
|
File Type |
Specify the type of the boot file for the next boot: · Main—Boots the device. · Backup—Boots the device when the main boot file is unavailable. |
|
If a file with the same name already exists, overwrite it without any prompt |
Specify whether to overwrite the file with the same name. If you do not select the option, when you rename a file with the same name, the system prompts "The file has existed.", and you cannot upgrade the software. |
|
Reboot after the upgrade is finished. |
Specify whether to reboot the device to make the upgraded software take effect after the application file is uploaded. |
Rebooting the device
|
|
CAUTION: Before rebooting the device, save the configuration. Otherwise, all unsaved configurations are lost after device reboot. |
1. Select Device > Device Maintenance from the navigation tree.
2. Click the Reboot tab.
The reboot tab page appears.
Figure 6 Device reboot page
3. Clear the box before "Check whether the current configuration is saved in the next startup configuration file" or keep it selected.
4. Click Apply.
A confirmation dialog box appears.
5. Click OK.
¡ If you select the box next to Check whether the current configuration is saved in the next startup configuration file, the system checks the configuration before rebooting the device. If the check succeeds, the system reboots the device. If the check fails, the system displays a dialog box to inform you that the current configuration and the saved configuration are inconsistent, and does not reboot the device. You must save the current configuration manually before you can reboot the device.
¡ If you do not select the box next to Check whether the current configuration is saved in the next startup configuration file, the system reboots the device automatically.
6. Log in again in to the Web interface after the device reboots.
Generating the diagnostic information file
Each functional module has its own running information. Typically, you need to view the output information for each individual module. You can generate the diagnostic information file to receive as much information as possible in one operation during daily maintenance or when system failure occurs. When you perform the diagnostic information generation operation, the system saves the running statistics of multiple functional modules to a file named default.diag, and use the file to locate problems.
To generate the diagnostic information file:
1. Select Device > Device Maintenance from the navigation tree.
2. Click the Diagnostic Information tab.
The diagnostic information tab page appears.
Figure 7 Diagnostic information

3. Click Create Diagnostic Information File.
The system begins to generate the diagnostic information file, and after the file is generated, the page in Figure 8 appears.
Figure 8 The diagnostic information file is created
4. Click Click to Download.
The File Download dialog box appears. You can select to open this file or save this file to the local host.
|
|
NOTE: · During the generation of the diagnostic file, do not perform any operation on the Web interface. · To view this file after the diagnostic file is generated successfully, select Device > File Management, or download this file to the local host. For more information, see "Managing files." |
Configuring the system time
Configure a correct system time so that the device can work with other devices correctly. System time allows you to display and set the device system time, system time zone, and daylight saving time on the Web interface.
You can set the system time using manual configuration or automatic synchronization of NTP server time.
Changing the system clock on each device within a network is time-consuming and does not guarantee clock precision.
Defined in RFC 1305, the Network Time Protocol (NTP) synchronizes timekeeping among distributed time servers and clients.
NTP can keep consistent timekeeping among all clock-dependent devices within the network so that the devices can provide diverse applications based on consistent time. For a local system running NTP, it can synchronize, be synchronized by, or mutually synchronize with other clocks.
Configuration guidelines
· A device can act as a server to synchronize the clock of other devices only after its clock has been synchronized. If the clock of a server has a stratum level higher than or equal to that of a client's clock, the client will not synchronize its clock to the server's clock.
· Because the synchronization process takes a period of time, the clock status may be displayed as unsynchronized after your configuration. Refresh the page to update the clock status.
· If the system time of the NTP server is ahead of the system time of the device, and the difference between them exceeds the Web idle time specified on the device, all online Web users are logged out because of timeout.
Displaying the system time
1. Select Device > System Time from the navigation tree.
The page for configuring system time appears.
Figure 9 Displaying the system time
2. View the current system time on the top of the page.
Configuring the system time
1. Select Device > System Time from the navigation tree.
The page in Figure 9 appears.
2. Click the System Time Configuration calendar button.
The calendar page appears.
Figure 10 Configuring the system time
3. Modify the system time either in the System Time Configuration field, or through the calendar page.
You can perform the following operations on the calendar page:
a. Click Today to set the current date on the calendar to the current system date of the local host. The time is not changed.
b. Set the year, month, date and time, and then click OK.
4. Click Apply in the system time configuration page to save your configuration.
Configuring the network time
1. Select Device > System Time from the navigation tree.
2. Click Net Time.
The network time page appears.
Figure 11 Configuring the network time
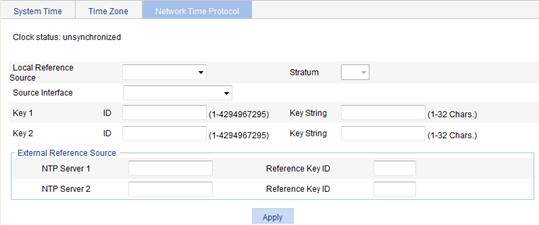
3. Configure system time parameters as described in Table 6.
4. Click Apply.
|
Item |
Description |
|
|
Clock status |
Display the synchronization status of the system clock. |
|
|
Local Reference Source |
Set the IP address of the local clock source to 127.127.1.u, where u is in the range of 0 to 3, representing the NTP process ID. · If the IP address of the local clock source is specified, the local clock is used as the reference clock, and can provide time for other devices. · If the IP address of the local clock source is not specified, the local clock is not used as the reference clock. |
|
|
Stratum |
Set the stratum level of the local clock. The stratum level of the local clock determines the precision of the local clock. A higher value indicates a lower precision. A stratum 1 clock has the highest precision, and a stratum 16 clock is not synchronized and cannot be used as a reference clock. |
|
|
Source Interface |
Set the source interface for an NTP message. If you do not want the IP address of a specific interface on the local device to become the destination address of response messages, you can specify the source interface for NTP messages so that the source IP address in the NTP messages becomes the primary IP address of this interface. If the specified source interface is down, the source IP address of the NTP messages sent is the primary IP address of the outbound interface. |
|
|
Key 1 |
Set NTP authentication key. The NTP authentication feature should be enabled for a system running NTP in a network where there is a high security demand. This feature enhances the network security by means of client-server key authentication, which prohibits a client from synchronizing with a device that has failed authentication. You can set two authentication keys, each of which is composed of a key ID and key string. · ID is the ID of a key. · Key string is a character string for MD5 authentication key. |
|
|
Key 2 |
||
|
External Reference Source |
NTP Server 1/Reference Key ID |
Specify the IP address of an NTP server, and configure the authentication key ID used for the association with the NTP server. The device synchronizes its time to the NTP server only if the key provided by the server is the same with the specified key. You can configure two NTP servers. The clients will choose the optimal reference source.
The IP address of an NTP server is a unicast address, and cannot be a broadcast or a multicast address, or the IP address of the local clock source. |
|
NTP Server 2/Reference Key ID |
||
Configuring the time zone and daylight saving time
1. Select Device > System Time from the navigation tree.
2. Click Time Zone.
The time zone page appears.
Figure 12 Configuring the time zone
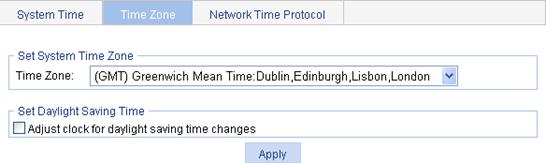
3. Configure the time zone and daylight saving time as described in Table 7.
4. Click Apply.
|
Item |
Description |
|
Time Zone |
Set the time zone for the system. |
|
Adjust clock for daylight saving time changes |
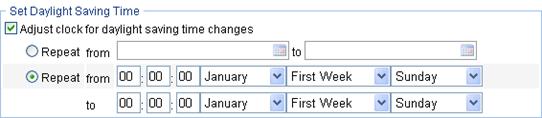
Adjust the system clock for daylight saving time changes, which means adding one hour to the current system time. Click Adjust clock for daylight saving time changes to expand the option, as shown in Figure 13. You can configure the daylight saving time changes in either of the following ways: 1. Specify that the daylight saving time starts on a specific date and ends on a specific date. The time range must be greater than one day and smaller than one year. For example, configure the daylight saving time to start on August 1st, 2006 at 06:00:00 a.m., and end on September 1st, 2006 at 06:00:00 a.m. 2. Specify that the daylight saving time starts and ends on the corresponding specified days every year. The time range must be greater than one day and smaller than one year. For example, configure the daylight saving time to start on the first Monday in August at 06:00:00 a.m., and end on the last Sunday in September at 06:00:00 a.m. |
Figure 13 Configuring the daylight saving time
System time configuration example
Network requirements
· As shown in Figure 14, the local clock of the switch is set as the reference clock.
· The AC operates in client mode, and uses the switch as the NTP server.
· NTP authentication is configured on both the AC and switch.

Configuring the switch
Configure the local clock as the reference clock, with the stratum of 2, configure authentication, with the key ID of 24, and trusted key as aNiceKey. (Details not shown.)
Configuring the AC
To configure the switch as the NTP server of the AC:
1. Select Device > System Time from the navigation tree.
2. Click the Net Time tab.
The Net Time tab page appears.
Figure 15 Configuring the switch as the NTP server of the AC
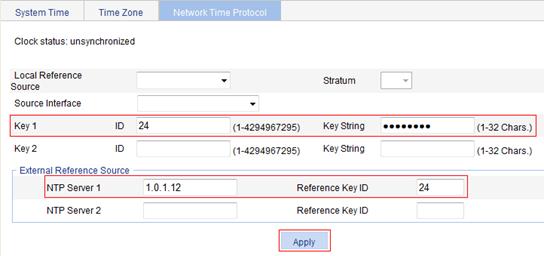
3. Enter 24 for the ID of key 1, and aNiceKey for the key string. Enter 1.0.1.12 in the NTP Server 1 box and 24 in the Reference Key ID box.
4. Click Apply.
Verifying the configuration
After you complete the configuration, the current system time displayed on the System Time page is the same for AC and Switch.
Managing logs
System logs contain a large amount of network and device information, including running status and configuration changes. System logs allow administrators to monitor network and device operation. With system logs, administrators can take corresponding actions against network and security problems.
The system sends system logs to the following destinations:
· Console.
· Monitor terminal, which is a user terminal that has login connections through the AUX, VTY, or TTY user interface.
· Log buffer.
· Loghost.
Displaying syslog
The Web interface provides abundant search and sorting functions for viewing logs.
To display syslog:
1. Select Device > Syslog from the navigation tree.
The page for displaying syslog appears.
|
|
TIP: · You can click Reset to clear all system logs saved in the log buffer on the Web interface. · You can click Refresh to manually refresh the page, or you can set the refresh interval on the Log Setup page to enable the system to automatically refresh the page. For more information, see "Setting buffer capacity and refresh interval." |
2. View system logs.
Table 8 Field description
|
Field |
Description |
|
Time/Date |
Display the time/date when system logs are generated. |
|
Source |
Display the module that generates system logs. |
|
Level |
Display the system information levels. The information is classified into eight levels depending on severity: · Emergency—The system is unusable. · Alert—Action must be taken immediately. · Critical—Critical conditions. · Error—Error conditions. · Warning—Warning conditions. · Notification—Normal but significant condition. · Information—Informational messages. · Debug—Debug-level messages. |
|
Digest |
Display the brief description of system logs. |
|
Description |
Display the contents of system logs. |
Setting the log host
You can set the loghost on the Web interface to enable the system to output syslogs to the log host. You can specify a maximum of four different log hosts.
To set the log host:
1. Select Device > Syslog from the navigation tree.
2. Click the Loghost tab.
The loghost configuration page appears.

3. Configure the log host as described in Table 9.
4. Click Apply.
|
Item |
Description |
|
IPv4/Domain |
Set the IPv4 address, domain name, or IPv6 address of the log host. You can specify up to four log hosts. |
|
IPv6 |
|
|
Loghost IP/Domain |
Setting buffer capacity and refresh interval
1. Select Device > Syslog from the navigation tree.
2. Click the Log Setup tab.
The syslog configuration page appears.
Figure 18 Syslog configuration page
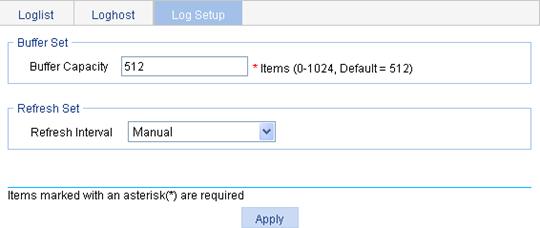
3. Configure buffer capacity and refresh interval as described in Table 10.
4. Click Apply.
|
Item |
Description |
|
Buffer Capacity |
Set the number of logs that can be stored in the log buffer of the Web interface. |
|
Refresh Interval |
Set the refresh period on the log information displayed on the Web interface. You can select manual refresh or automatic refresh: · Manual—Click Refresh to refresh the Web interface when displaying log information. · Automatic—You can select to refresh the Web interface every 1, 5, or 10 minutes. |
Managing the configuration
Support for configuration management depends on the device model. For more information, see "About the H3C Access Controllers Web-Based Configuration Guide."
Backing up the configuration
|
|
IMPORTANT: When you back up configuration files, back up both the .cfg configuration files and .xml configuration files. Otherwise, some configuration information might fail to be restored if the configuration is deleted accidentally. |
Configuration backup allows you to perform the following operations:
· Open and view the configuration file for the next startup.
· Back up the configuration file for the next startup to the host of the current user.
To back up the configuration:
1. Select Device > Configuration from the navigation tree.
The page for backing up configuration appears.
Figure 19 Backing up the configuration

2. Click the Backup button after Backup the configuration file with the extension ".cfg."
A file download dialog box appears. You can select to view the .cfg file or to save the file locally.
3. Click the Backup button after Backup the configuration file with the extension ".xml."
A file download dialog box appears. You can select to view the .xml file or to save the file locally.
Restoring the configuration
|
|
IMPORTANT: The restored configuration file takes effect at the next device reboot. |
Configuration restoration allows you to perform the following tasks:
· Upload the .cfg file on the host of the current user to the device for the next startup.
· Upload the .xml file on the host of the current user to the device for the next startup, and delete the previous next-startup .xml file.
To restore the configuration:
1. Select Device > Configuration from the navigation tree.
2. Click the Restore tab.
The page for restoring configuration appears.
Figure 20 Restoring the configuration
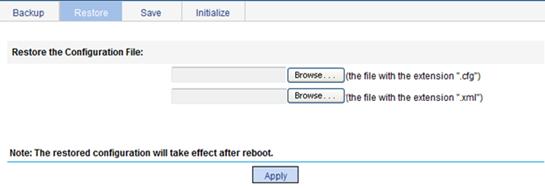
3. Click the Browse button before (the file with the extension ".cfg.")
The file upload dialog box appears. You can select the .cfg file to be uploaded.
4. Click the Browse button before (the file with the extension ".xml.")
The file upload dialog box appears. You can select the .xml file to be uploaded.
5. Click Apply.
Saving the configuration
|
IMPORTANT: · H3C recommends that you do not perform any operation on the Web interface while the configuration is being saved. · The system does not support saving the configuration of two or more consecutive users. The system prompts the users to try again if one user's configuration is being saved. |
The save configuration module provides the function to save the current configuration to the configuration file (.cfg file) to be used at the next startup. You can save the configuration by using one of the following ways: fast or common.
Fast
Click the Save button at the upper right of the auxiliary area, and you can save the configuration to the configuration file.
Figure 21 Saving the configuration
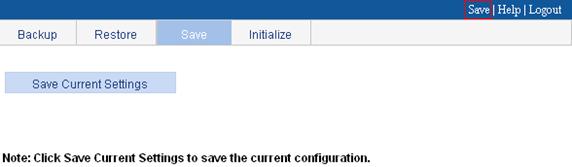
Common
1. Select Device > Configuration from the navigation tree.
2. Click the Save tab.
The page in Figure 21 appears.
3. Click Save Current Settings to save the current configuration to the configuration file.
Initializing the configuration
This operation restores the system to factory defaults, delete the current configuration file, and reboot the device.
To initialize the configuration:
1. Select Device > Configuration from the navigation tree.
2. Click the Initialize tab.
The initialize confirmation page appears.
Figure 22 Initializing the configuration

3. Click Restore Factory-Default Settings to restore the system to factory defaults.
Managing files
The device saves critical files, such as host, software and configuration files, into the storage device, and the system provides the file management function for the users to manage those files.
There are different types of storage media, such as flash and compact flash (CF). Different devices support different types of storage devices. For more information, see "About the H3C Access Controllers Web-Based Configuration Guide."
Displaying file list
1. Select Device > File Management from the navigation tree.
The file management page appears.
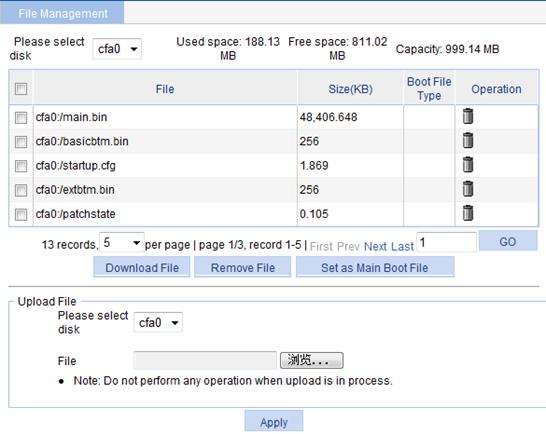
2. Select a disk from the Please select disk list on the top of the page.
3. View the used space, free space and capacity of the disk at the right of the list.
4. View all files saved in this disk (in the format of path + filename), file sizes, and the boot file types (Main or Backup is displayed if the file is an application file, with the extension of .bin or .app).
Downloading a file
1. Select Device > File Management from the navigation tree.
The page in Figure 23 appears.
2. Select a file from the list.
You can select one file at a time.
3. Click Download File.
The File Download dialog box appears. You can select to open the file or to save the file to a specified path.
Uploading a file
|
|
IMPORTANT: H3C recommends that you do not perform any operation on the Web interface during the upgrade procedure. |
1. Select Device > File Management from the navigation tree.
The page in Figure 23 appears.
2. Select the disk to save the file in the Upload File box.
3. Click Browse to set the path and name of the file.
4. Click Apply.
Removing a file
1. Select Device > File Management from the navigation tree.
The page in Figure 23 appears.
2. Select one or multiple files from the file list,
3. Click Remove File.
|
|
NOTE: You can also remove a file by clicking the |
Specifying the main boot file
1. Select Device > File Management from the navigation tree.
The page in Figure 23 appears.
2. Select the box to the left of an application file (with the extension of .bin or .app).
You can set one file at a time.
3. Click Set as Main Boot File to set the main boot file to be used at the next startup.
Managing interfaces
Interface management overview
An interface is the point of interaction for exchanging data between entities. There are two types of interfaces: physical and logical. A physical interface refers to an interface that physically exists as a hardware component, for example, Ethernet interfaces. A logical interface is an interface that can implement data switching but does not exist physically, and must be created manually, for example, VLAN interfaces.
You can use the interface management feature on the Web-based configuration interface to manage the following types of interfaces:
· Layer 2 Ethernet interface—Physical interface operating on the data link layer for forwarding Layer 2 protocol packets.
· Management Ethernet interface—Physical interface operating on the network layer. You can configure IP addresses for a management Ethernet interface. To manage the device, you can log in to the device through a management Ethernet interface.
· Loopback interface—A loopback interface is a software-only virtual interface. The physical layer state and link layer protocols of a loopback interface are always up unless the loopback interface is manually shut down. You can enable routing protocols on a loopback interface, and a loopback interface can send and receive routing protocol packets. When you assign an IPv4 address whose mask is not 32-bit, the system automatically changes the mask into a 32-bit mask.
· Null interface—A null interface is a completely software-based logical interface, and is always up. However, you cannot use it to forward data packets or configure an IP address or link layer protocol. With a null interface specified as the next hop of a static route to a specific network segment, any packets routed to the network segment are dropped. The null interface provides a method to filter packets than ACL. You can filter uninteresting traffic by transmitting it to a null interface instead of applying an ACL.
· VLAN interface—Virtual Layer 3 interface used for Layer 3 communications between VLANs. A VLAN interface corresponds to a VLAN. You can assign an IP address to a VLAN interface and specify it as the gateway of the corresponding VLAN to forward traffic destined for an IP network segment different from that of the VLAN.
· Virtual template (VT) interface—Template used for configuring virtual access (VA) interfaces.
· Bridge-Aggregation interface (BAGG)—Multiple Layer 2 Ethernet interfaces can be combined to form a Layer 2 aggregation group. The logical interface created for the group is called an aggregate interface.
Displaying interface information and statistics
1. Select Device > Interface from the navigation tree.
The interface management page appears. The page displays the interfaces' names, IP addresses, masks, and status.
Figure 24 Displaying interface information

2. Click an interface name in the Name column to display the statistics of that interface.
The page for displaying interface statistics appears.
Figure 25 Displaying interface statistics

Creating an interface
1. Select Device > Interface from the navigation tree.
The page in Figure 24 appears.
2. Click Add.
The page for creating an interface appears.
Figure 26 Creating an interface
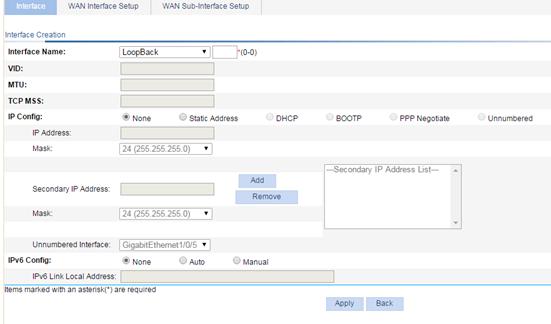
3. Configure the interface as described in Table 11.
4. Click Apply.
|
Item |
Description |
|
Interface Name |
Set the type and number of a logical interface. |
|
VID |
If you are creating a Layer 3 Ethernet subinterface, set the VLANs associated with the subinterface. This parameter is available only for Layer 3 Ethernet subinterfaces.
This configuration item is not configurable because the device does not support Layer 3 Ethernet subinterfaces. |
|
Set the maximum transmit unit (MTU) that is allowed to pass the interface. The MTU value affects fragmentation and reassembly of IP packets. Support for this configuration item depends on the interface type. All Layer 3 interfaces support MTU. |
|
|
TCP MSS |
Set the maximum segment size (MSS) for IP packets on the interface. Support for this configuration item depends on the interface type. All Layer 3 interfaces support MTU |
|
IP Config |
Set the way for the interface to obtain an IP address, include: · None—Select this option if you do not want to assign an IP address for the interface. · Static Address—Select the option to manually assign an IP address and mask for the interface. If this option is selected, you must set the IP Address and Mask fields. · DHCP—Select the option for the interface to obtain an IP address through DHCP automatically. · BOOTP—Select the option for the interface to obtain an IP address through BOOTP automatically. · PPP Negotiate—Select the option for the interface to obtain an IP address through PPP negotiation. · Unnumbered—Select this option to borrow the IP address of another interface on the same device for the interface. If this option is selected, you must select the interface whose IP address you want to borrow in the Unnumbered Interfaces list. Support for the way of obtaining an IP address depends on the device model and the interface type. |
|
IP Address/Mask |
After selecting the Static Address option for the IP Config configuration item, you need to set the primary IP address and mask, and secondary IP addresses and masks for the interface.
· The primary and secondary IP addresses cannot be 0.0.0.0. · For a loopback interface, the mask is fixed to 32 bits and is not configurable. · The number of secondary IP addresses supported by the device depends on the device model. |
|
Secondary IP Address/Mask |
|
|
Unnumbered Interface |
If the Unnumbered option is selected as the way for the interface to obtain an IP address, you must set the interface whose IP address is to be borrowed. |
|
IPv6 Config |
Set the option for the interface to obtain an IPv6 link-local address, include. · None—Select this option if you do not want to assign an IPv6 link-local address to the interface. · Auto—Select this option for the system to automatically assign an IPv6 link-local address to the interface. · Manual—Select this option to manually assign an IPv6 link-local address to the interface. If this option is selected, you must set the IPv6 Link Local Address field. |
|
IPv6 Link Local Address |
If the Manual option is selected for the interface to obtain an IPv6 link-local address, you must set an IPv6 link-local address for the interface. |
Modifying a Layer 2 interface
1. Select Device > Interface from the navigation tree.
The page in Figure 24 appears.
2. Click the ![]() icon
corresponding to a Layer 2 interface.
icon
corresponding to a Layer 2 interface.
The page for modifying a Layer 2 interface appears.
Figure 27 Modifying a Layer 2 physical interface

3. Modify the information about the Layer 2 physical interface as described in Table 12.
4. Click Apply.
|
Item |
Description |
|
Port State |
Enable or disable the interface. In some cases, modification to the interface parameters does not take effect immediately. You need to shut down and then bring up the interface to make the modification take effect. |
|
Speed |
Set the transmission rate of the interface. Available options include: · 10—10 Mbps. · 100—100 Mbps. · 1000—1000 Mbps. · Auto—Auto-negotiation. · Auto 10—The auto-negotiation rate of the interface is 10 Mbps. · Auto 100—The auto-negotiation rate of the interface is 100 Mbps. · Auto 1000—The auto-negotiation rate of the interface is 1000 Mbps. · Auto 10 100—The auto-negotiation rate of the interface is 10 Mbps or 100 Mbps. · Auto 10 1000—The auto-negotiation rate of the interface is 10 Mbps or 1000 Mbps. · Auto 100 1000—The auto-negotiation rate of the interface is 100 Mbps or 1000 Mbps. · Auto 10 100 1000—The auto-negotiation rate of the interface is 10 Mbps, 100 Mbps or 1000 Mbps. |
|
Duplex |
Set the duplex mode of the interface. · Auto—Auto-negotiation. · Full—Full duplex. · Half—Half duplex. |
|
Link Type |
Set the link type of the current interface, which can be access, hybrid, or trunk. For more information, see Table 13.
To change the link type of a port from trunk to hybrid or vice versa, you must first set its link type to access. |
|
PVID |
Set the default VLAN ID of the hybrid or trunk port.
The trunk ports at the two ends of a link must have the same PVID. |
|
MDI |
Set the Medium Dependent Interface (MDI) mode for the interface. Two types of Ethernet cables can be used to connect Ethernet devices: crossover and straight-through. To accommodate these two types of cables, an Ethernet interface on the device can operate in one of the following MDI modes: · Across mode. · Normal mode. · Auto mode. An Ethernet interface is composed of eight pins. By default, each pin has its particular role. For example, pin 1 and pin 2 are used for transmitting signals; pin 3 and pin 6 are used for receiving signals. Pin roles are set as a result of how you set the MDI mode: · In across mode, pin 1 and pin 2 are used for transmitting signals, and pin 3 and pin 6 are used for receiving signals. · In auto mode, the pin roles are determined through auto negotiation. · In normal mode, pin 1 and pin 2 are used for receiving signals while pin 3 and pin 6 are used for transmitting signals. Configure the MDI mode depending on the cable types: · Typically, the auto mode is recommended. The other two modes are useful only when the device cannot determine the cable types. · When straight-through cables are used, the local MDI mode must be different from the remote MDI mode. · When crossover cables are used, the local MDI mode must be the same as the remote MDI mode, or the MDI mode of at least one end must be set to auto. |
|
Flow Control |
Enable or disable flow control on the interface. If there is traffic congestion on the device on the local end after flow control is enabled on both ends, the device sends information to notify the peer end to stop sending packets temporarily. To avoid packet loss, the peer end and the device stop sending packets when the device receives the information.
Flow control can be realized only when it is enabled on both ends. |
|
Jumbo Frame Forwarding |
Enable or disable the forwarding of jumbo frames. |
|
Max MAC Count |
Set the maximum number of MAC addresses the interface can learn. Available options include: · User Defined—Select this option to set the limit manually. · No Limited—Select this option to set no limit. |
|
Broadcast Suppression |
Set broadcast suppression. You can suppress broadcast traffic by percentage or by PPS: · ratio—Sets the maximum percentage of broadcast traffic to the total transmission capability of an Ethernet interface. When this option is selected, you need to enter a percentage in the box below this option. · pps—Sets the maximum number of broadcast packets that can be forwarded on an Ethernet interface every second. When this option is selected, you need to enter a number in the box below this option. |
|
Multicast Suppression |
Set multicast suppression. You can suppress multicast traffic by percentage or by PPS: · ratio—Sets the maximum percentage of multicast traffic to the total transmission capability of an Ethernet interface. When this option is selected, you need to enter a percentage in the box below this option. · pps—Sets the maximum number of multicast packets that can be forwarded on an Ethernet interface per second. When this option is selected, you need to enter a number in the box below this option. |
|
Unicast Suppression |
Set unicast suppression. You can suppress unicast traffic by percentage or by PPS: · ratio—Sets the maximum percentage of unicast traffic to the total transmission capability of an Ethernet interface. When this option is selected, you need to enter a percentage in the box below this option. · pps—Sets the maximum number of unicast packets that can be forwarded on an Ethernet interface every second. When this option is selected, you need to enter a number in the box below this option. |
Table 13 Link type description
|
Link type |
Description |
|
Access |
An access port can belong to only one VLAN and is typically used to connect a user device. |
|
Hybrid |
A hybrid port can be assigned to multiple VLANs to receive and send packets for the VLANs. A hybrid port allows packets of multiple VLANs to pass through untagged. Hybrid ports can be used to connect network devices and user devices. |
|
Trunk |
A trunk port can be assigned to multiple VLANs to receive and send packets for the VLANS. A trunk port allows only packets of the default VLAN to pass through untagged. Trunk ports are typically used to connect network devices. |
Modifying a Layer 3 interface
1. Select Device > Interface from the navigation tree.
The page in Figure 24 appears.
2. Click the ![]() icon
corresponding to a Layer 3 interface.
icon
corresponding to a Layer 3 interface.
The page for modifying a Layer 3 interface appears.
Figure 28 Modifying a Layer 3 physical interface
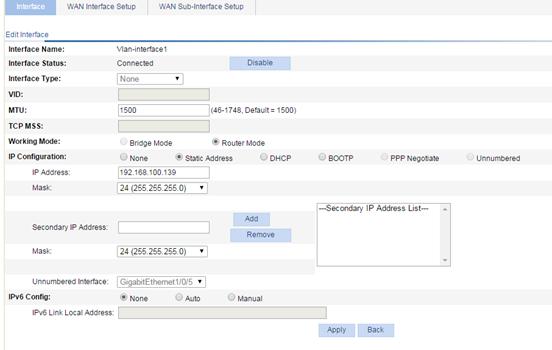
3. Modify the information about the Layer 3 interface.
The configuration items of modifying the Layer 3 interface are similar to those for creating an interface. Table 14 describes configuration items that apply to modifying a Layer 3 interface.
4. Click Apply.
|
Item |
Description |
|
Interface Type |
Set the interface type, which can be Electrical port, Optical port, or None. |
|
Interface Status |
Display and set the interface status. · Connected indicates that the current status of the interface is up and connected. You can click Disable to shut down the interface. · Not connected indicates that the current status of the interface is up but not connected. You can click Disable to shut down the interface. · Administratively Down indicates that the interface is shut down by the administrator. You can click Enable to bring up the interface. After you click Enable or Disable, the page displaying interface information appears.
For an interface whose status cannot be changed, the Enable or Disable button is not available. |
|
Working Mode |
Set the interface to work in bridge mode or router mode. |
Configuring a WAN interface
1. Select Device > Interface from the navigation tree, and click the WAN Interface Setup tab.
The page in Figure 29 appears.
Figure 29 Configuring a WAN interface

2. Configure the information about the WAN interface as described in Table 15.
3. Click Apply.
|
Item |
Description |
|
WAN Interface |
Display the name of the Ethernet interface to be configured. |
|
Connection Mode |
Set the connection mode of the WAN interface. |
|
PVC |
Set the VPI/VCI values of the PVC. |
|
TCP-MSS |
Set the maximum segment size (MSS) for TCP packets on the interface. |
|
MTU |
Set the maximum transmit unit (MTU) that is allowed to pass the interface. |
|
IP Address |
Configure an IP address for the interface. This field is required only when the connection mode is set to IPoA or IPoEoA. |
|
IP Mask |
Configure the subnet mask for the interface. This field is required only when the connection mode is set to IPoA or IPoEoA. |
|
Map IP |
Set the remote IP address mapped to the PVC in an IPoA mapping. This field is required only when the connection mode is set to IPoA. |
|
User Name |
Configure the username for authentication. This field is required only when the connection mode is set to PPPoA or PPPoEoA. |
|
Password |
Display whether a password is configured for authentication. This field is required only when the connection mode is set to PPPoA or PPPoEoA. If the field displays null, no password is configured for authentication. |
|
New Password |
Set or modify the password for authentication. This field is required only when the connection mode is set to PPPoA or PPPoEoA. |
|
Idle Timeout |
Set the idle timeout time for a connection: · Online for all time—The connection is maintained until being disconnected manually or upon an anomaly. · Online according to the Idle Timeout value—The connection is disconnected automatically if no traffic is exchanged on the link for a period of time. The connection will be re-set up when an access to the Internet request is received. If you select Online according to the Idle Timeout value, you must set the idle timeout value. This field is required only when the connection mode is set to PPPoEoA. |
Configuring a WAN subinterface
1. Select Device > Interface from the navigation tree, and click the WAN Sub-Interface Setup tab.
The page in Figure 30 appears.
Figure 30 Configuring a WAN subinterface

2. Click Add.
The page for creating a WAN subinterface appears, as shown in Figure 31.
Figure 31 Creating a WAN subinterface
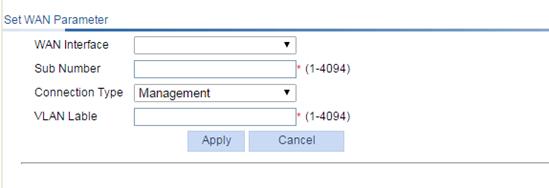
3. Configure the WAN subinterface as described in Table 16.
4. Click Apply.
|
Item |
Description |
|
WAN Interface |
Select the WAN interface based on which a subinterface is created. |
|
Sub Number |
Set the number of the WAN subinterface. |
|
Connection Type |
Set the connection type. · Management—The connection is used for management only. · Internet—The connection is used for Internet access only. · Management_Internet—The connection is used for both management and Internet access. · Other—The connection is used for other purposes. |
|
VLAN Label |
Set the ID of the VLAN associated with the WAN subinterface belongs. |
Interface management configuration example
Network requirements
Create VLAN-interface 100 and specify its IP address as 10.1.1.2.
Configuration procedure
1. Create VLAN 100:
a. Select Network > VLAN from the navigation tree.
The VLAN tab page appears.
b. Click Add.
The page for creating VLANs appears.
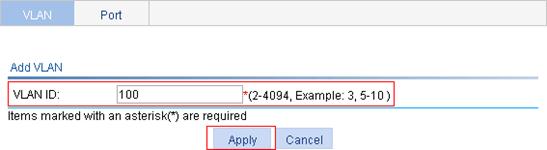
c. Enter VLAN ID 100.
d. Click Apply.
2. Create VLAN-interface 100 and assign an IP address for it:
a. Select Device > Interface from the navigation tree.
b. Click Add.
The page for creating an interface appears.
Figure 33 Creating VLAN-interface 100

c. Select Vlan-interface from the Interface Name list, enter the interface ID 100, select the Static Address option in the IP Config area, enter the IP address 10.1.1.2, and select 24 (255.255.255.0) from the Mask list.
d. Click Apply.
Configuring port mirroring
Port mirroring includes local port mirroring and remote port mirroring. Unless otherwise specified, port mirroring described in this chapter refers to local port mirroring.
Support for port mirroring varies by device model. For more information, see "About the H3C Access Controllers Web-Based Configuration Guide."
Overview
Port mirroring copies the packets passing through one or multiple ports (called mirroring ports) to a port (called the monitor port) on the local device. The monitor port is connected to a monitoring device. By analyzing on the monitoring device the packets mirrored to the monitor port, you can monitor the network and troubleshoot possible network problems.
Figure 34 A port mirroring implementation

Port mirroring is implemented through mirroring groups. The mirroring ports and the monitor port are in the same mirroring group. With port mirroring enabled, the device copies packets passing through the mirroring ports to the monitor port.
Configuration guidelines
When you configure port mirroring, follow these guidelines:
· Depending on the device model, you can assign these types of ports to a mirroring group as mirroring ports:
¡ Layer 2 Ethernet
¡ Layer 3 Ethernet
¡ POS
¡ CPOS
¡ Serial
¡ MP-group
· Depending on the device model, you can configure these types of ports as the monitor port:
¡ Layer 2 Ethernet
¡ Layer 3 Ethernet
¡ Tunnel
· To ensure correct operation of your device, do not enable STP, MSTP, or RSTP on the monitor port.
· On some types of devices, you can configure a member port in link aggregation as the monitor port.
· Other restrictions on the monitor port depend on your device model.
· You can configure multiple mirroring ports, but only one monitor port for a mirroring group.
· A port can be assigned to only one mirroring group.
Recommended configuration procedure
|
Task |
Remarks |
|
Add a mirroring group |
Required. Select the mirroring group type Local from the Type list. |
|
Configure the mirroring ports |
Required. During configuration, select the port type Mirror Port. For more information, see "Configuring ports for a mirroring group." |
|
Configure the monitor port |
Required. During configuration, select the port type Monitor Port. For more information, see "Configuring ports for a mirroring group." |
Adding a mirroring group
1. Select Device > Port Mirroring from the navigation tree.
2. Click the Add tab.
The page for adding a mirroring group appears.
Figure 35 Adding a mirroring group
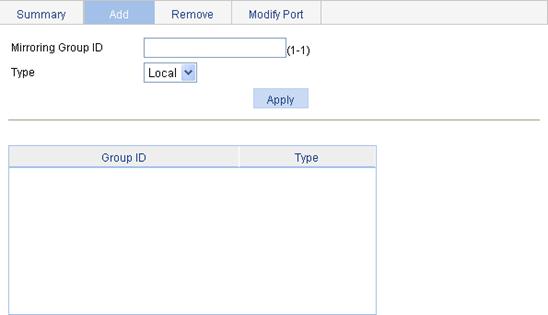
3. Configure the mirroring group, as described in Table 17.
4. Click Apply.
|
Item |
Description |
|
Mirroring Group ID |
ID of the mirroring group. |
|
Type |
Specify the type of the mirroring group. Local means adding a local mirroring group. |
Configuring ports for a mirroring group
1. Select Device > Port Mirroring from the navigation tree
2. Click the Modify Port tab.
The page for configuring ports for a mirroring group appears.
Figure 36 Configuring ports for a mirroring group
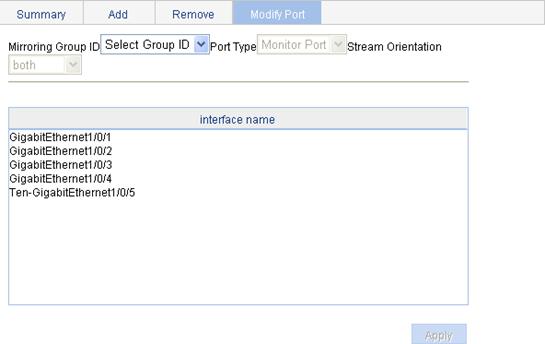
3. Configure the port information for the mirroring group, as described in Table 18.
4. Click Apply.
The progress bar appears.
5. Click Close when the progress bar prompts that the configuration is complete.
|
Item |
Description |
|
Mirroring Group ID |
ID of the mirroring group to be configured. |
|
Port Type |
Set the type of the ports to be configured: · Monitor Port—Configures the monitor port for the mirroring group. · Mirror Port—Configures mirroring ports for the mirroring group. |
|
Stream Orientation |
Set the direction of the traffic mirrored by the mirroring ports of the mirroring group. This configuration item is available when Mirror Port is selected in the Port Type list: · both—Mirrors both received and sent packets on mirroring ports. · inbound—Mirrors only packets received by mirroring ports. · outbound—Mirrors only packets sent by mirroring ports. |
|
interface name |
Select the ports to be configured from the interface name list. |
Port mirroring configuration example
Network requirements
As shown in Figure 37:
· GigabitEthernet 1/0/1 on the AC receives packets from the AP.
· The server is connected to GigabitEthernet 1/0/2 of the AC.
Configure port mirroring to monitor the bidirectional traffic on GigabitEthernet 1/0/1 of the AC on the server.

Requirement analysis
To implement port mirroring, perform the following configurations on the AC:
· Configure GigabitEthernet 1/0/1 of the AC as a mirroring port.
· Configure GigabitEthernet 1/0/2 of the AC as the monitor port.
Configuration procedure
1. Add a mirroring group:
a. Select Device > Port Mirroring from the navigation tree.
b. Click the Add tab.
c. Enter 1 for Mirroring Group ID, and select Local from the Type list.
d. Click Apply.
Figure 38 Adding a mirroring group

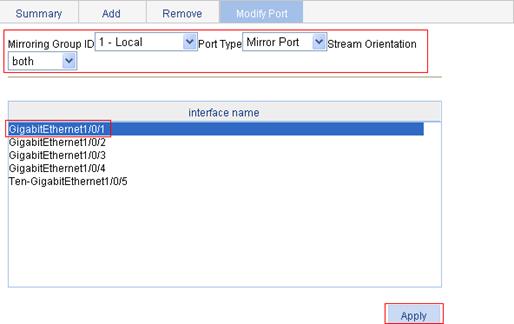
2. Configure the mirroring ports:
3. Click the Modify Port tab.
a. Select 1 – Local for Mirroring Group ID, Mirror Port for Port Type, both for Stream Orientation, and GigabitEthernet 1/0/1 from the interface name list.
b. Click Apply.
The progress bar appears.
c. Click Close when the progress bar prompts that the configuration is complete.
Figure 39 Configuring a mirroring port
4. Configure the monitor port:
a. Click the Modify Port tab.
b. Select 1 – Local for Mirroring Group ID, Monitor Port for Port Type, and GigabitEthernet 1/0/2 from the interface name list.
c. Click Apply.
A progress bar appears.
d. Click Close when the progress bar prompts that the configuration is complete.
Figure 40 Configuring the monitor port

Managing users
In the user management part, you can perform the following configuration:
· Create a local user, and set the password, access level, and service type for the user.
· Set the super password for switching the current Web user level to the management level.
· Switch the current Web user access level to the management level.
Creating a user
1. Select Device > Users from the navigation tree.
2. Click the Create tab.
The page for creating local users appears.
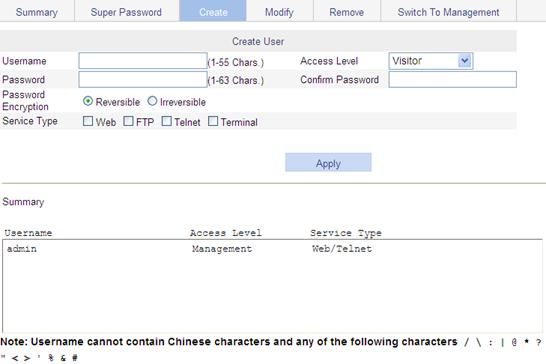
3. Configure the user information as described in Table 19.
4. Click Apply.
|
Item |
Description |
|
Username |
Set the username for a user. |
|
Access Level |
Set the access level for a user. Users of different levels can perform different operations. The following Web user levels, from low to high, are available:. · Visitor—Users of this level can perform the ping and traceroute operations, but they cannot access the device data or configure the device. · Monitor—Users of this level can only access the device data but cannot configure the device. · Configure—Users of this level can access data on the device and configure the device, but they cannot upgrade the host software, add/delete/modify users, or back up/restore the application file. · Management—Users of this level can perform any operations on the device. |
|
Password |
Set the password for a user. |
|
Confirm Password |
Enter the same password again. Otherwise, the system prompts that the two passwords are not consistent when you apply the configuration. |
|
Password Encryption |
Set the encryption method for storing users' passwords: · Reversible—The device stores passwords by using reversible encryption. · Irreversible—The device stores passwords by using irreversible encryption. |
|
Service Type |
Set the service type, including Web, FTP, and Telnet services. You must select at least one service type. |
Setting the super password
Management level users can specify the password for a lower-level user to switch from the current access level to the management level. If this password is not configured, the switchover will fail.
To set the super password:
1. Select Device > Users from the navigation tree.
2. Click the Super Password tab.
The super password configuration page appears.
Figure 42 Setting the super password

3. Set the super password as described in Table 20.
4. Click Apply.
|
Item |
Description |
|
Create/Remove |
Set the operation type: · Create—Configure or modify the super password. · Remove—Remove the current super password. |
|
Password |
Set the password for a user to switch to the management level. |
|
Confirm Password |
Enter the same password again. Otherwise, the system prompts that the two passwords are not consistent when you apply the configuration. |
|
Password Encryption |
Set the encryption method for storing users' passwords: · Reversible—The device stores passwords by using reversible encryption. · Irreversible—The device stores passwords by using irreversible encryption. |
Switching the user access level to the management level
This function is provided for a user to switch the current user level to the management level. Note the following:
· Before switching, make sure that the super password is already configured. A user cannot switch to the management level without a super password.
· The access level switchover of a user is valid for the current login only. The access level configured for the user is not changed. When the user logs in again to the Web interface, the access level of the user is still the original level.
To switch the user access level to the management level:
1. Select Device > Users from the navigation tree.
2. Click the Switch To Management tab.
The access level switching page appears.
Figure 43 Switching to the management level
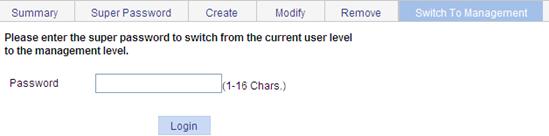
3. Enter the super password.
4. Click Login.
Configuring SNMP
SNMP overview
Simple Network Management Protocol (SNMP) is an Internet standard protocol widely used for a management station to access and manage the devices on a network. SNMP shields the physical differences between various devices and realizes automatic management of products from different manufacturers.
An SNMP enabled network comprises the network management system (NMS) and agents.
The NMS manages agents by exchanging management information through SNMP. The NMS and managed agents must use the same SNMP version to communicate with each other.
SNMP agents support SNMPv1, SNMPv2c, and SNMPv3.
· SNMPv1—Uses community names for authentication. Like the password, a community name is used to restrict the communication between the NMS and the Agent. To access an SNMP agent, an NMS must use the same community name as the one that is set on the SNMP agent. If the community name used by the NMS is different from that set on the agent, the NMS cannot establish an SNMP session to access the agent or receive traps and notifications from the agent.
· SNMPv2c—Uses community names for authentication. SNMPv2c is compatible with SNMPv1 and supports more operation modes, data types, and error codes.
· SNMPv3—Uses a user-based security model (USM) to secure SNMP communication. You can configure authentication and privacy mechanisms to authenticate and encrypt SNMP packets for integrity, authenticity, and confidentiality.
For more information about SNMP, see "About the H3C Access Controllers Web-Based Configuration Guide."
SNMP configuration task list
SNMPv3 differs from SNMPv1 and SNMPv2c in configurations. The following describes their configuration procedures separately.
SNMPv1 or SNMPv2c configuration task list
Perform the tasks in Table 21 to configure SNMPv1 or SNMPv2c.
Table 21 SNMPv1 or SNMPv2c configuration task list
|
Task |
Remarks |
|
Required. The SNMP agent function is disabled by default.
If SNMP agent is disabled, all SNMP agent-related configurations are removed. |
|
|
Optional. After creating SNMP views, you can specify an SNMP view for an SNMP group to limit the MIB objects that can be accessed by the SNMP group. |
|
|
Required. |
|
|
Optional. Allows you to configure that the agent can send SNMP traps to the NMS, and configure information about the target host of the SNMP traps. By default, an agent is allowed to send SNMP traps to the NMS. |
|
|
Optional. |
SNMPv3 configuration task list
Perform the tasks in Table 22 to configure SNMPv3.
Table 22 SNMPv3 configuration task list
|
Task |
Remarks |
|
Required. The SNMP agent function is disabled by default.
If SNMP agent is disabled, all SNMP agent-related configurations are removed. |
|
|
Optional. After creating SNMP views, you can specify an SNMP view for an SNMP group to limit the MIB objects that can be accessed by the SNMP group. |
|
|
Required. After creating an SNMP group, you can add SNMP users to the group when creating the users. Therefore, you can realize centralized management of users in the group through the management of the group. |
|
|
Required. Before creating an SNMP user, you need to create the SNMP group to which the user belongs. |
|
|
Optional. Allows you to configure that the agent can send SNMP traps to the NMS, and configure information about the target host of the SNMP traps By default, an agent is allowed to send SNMP traps to the NMS. |
|
|
Optional. |
Enabling SNMP agent
1. Select Device > SNMP from the navigation tree.
The SNMP configuration page appears.
Figure 44 Configuring SNMP settings
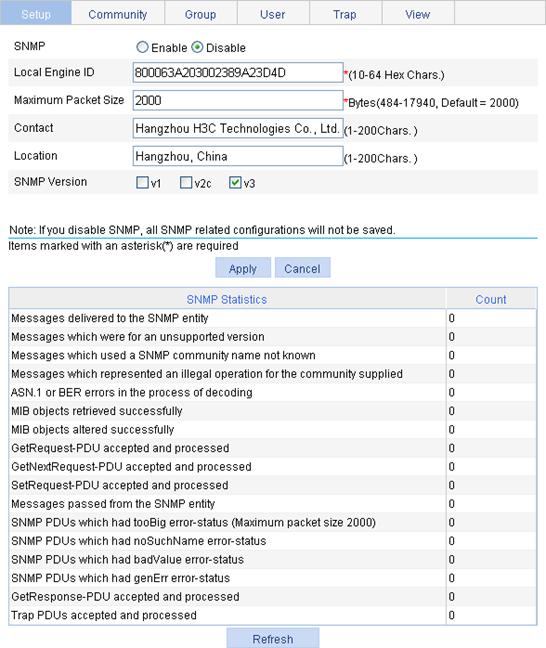
2. Configure SNMP settings on the upper part of the page as described in Table 23.
3. Click Apply.
|
Item |
Description |
|
SNMP |
Specify to enable or disable SNMP agent. |
|
Local Engine ID |
Configure the local engine ID. The validity of a user after it is created depends on the engine ID of the SNMP agent. If the engine ID when the user is created is not identical to the current engine ID, the user is invalid. |
|
Maximum Packet Size |
Configure the maximum size of an SNMP packet that the agent can receive/send. |
|
Contact |
Set a character string to describe the contact information for system maintenance. |
|
Location |
Set a character string to describe the physical location of the device. |
|
SNMP Version |
Set the SNMP version run by the system. |
Configuring an SNMP view
Creating an SNMP view
1. Select Device > SNMP from the navigation tree.
2. Click the View tab.
The view page appears.
Figure 45 View page
The Add View window appears.
Figure 46 Creating an SNMP view (1)

4. Enter the view name.
5. Click Apply.
The page in Figure 47 appears.
Figure 47 Creating an SNMP view (2)
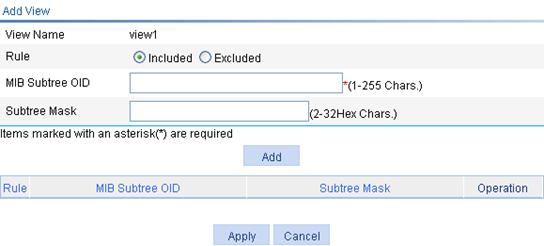
6. Configure the parameters as described in Table 24.
7. Click Add.
8. Repeat steps 6 and 7 to add more rules for the SNMP view.
9. Click Apply.
To cancel the view, click Cancel.
|
Item |
Description |
|
View Name |
Set the SNMP view name. |
|
Rule |
Select to exclude or include the objects in the view range determined by the MIB subtree OID and subtree mask. |
|
MIB Subtree OID |
Set the MIB subtree OID (such as 1.4.5.3.1) or name (such as system). MIB subtree OID identifies the position of a node in the MIB tree, and it can uniquely identify a MIB subtree. |
|
Subtree Mask |
Set the subtree mask. If no subtree mask is specified, the default subtree mask (all Fs) will be used for mask-OID matching. |
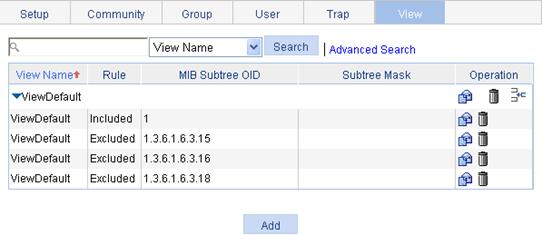
Adding rules to an SNMP view
1. Select Device > SNMP from the navigation tree.
2. Click the View tab.
The page in Figure 48 appears.
3. Click the ![]() icon of the target view.
icon of the target view.
The Add rule for the view ViewDefault window appears.
Figure 48 Adding rules to an SNMP view

4. Configure the parameters as described in Table 24.
5. Click Apply.
|
|
NOTE: You can modify the rules of a view in
the page you enter by clicking the |
Configuring an SNMP community
1. Select Device > SNMP from the navigation tree.
2. Click the Community tab.
The community tab page appears.
Figure 49 Configuring an SNMP community
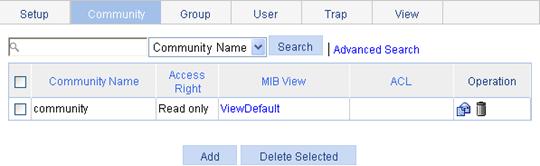
3. Click Add.
The Add SNMP Community page appears.
Figure 50 Creating an SNMP Community
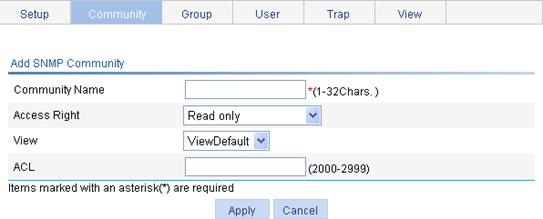
4. Configure SNMP community settings as described in Table 25.
5. Click Apply.
|
Item |
Description |
|
Community Name |
Set the SNMP community name. |
|
Access Right |
Configure the access rights: · Read only—The NMS can perform read-only operations to the MIB objects when it uses this community name to access the agent. · Read and write—The NMS can perform both read and write operations to the MIB objects when it uses this community name to access the agent. |
|
View |
Specify the view associated with the community to limit the MIB objects that can be accessed by the NMS. |
|
ACL |
Associate the community with a basic ACL to allow or prohibit the access to the agent from the NMS with the specified source IP address. |
Configuring an SNMP group
1. Select Device > SNMP from the navigation tree.
2. Click the Group tab.
The group tab page appears.
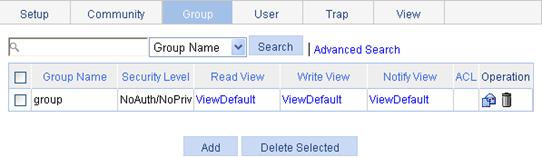
3. Click Add.
The Add SNMP Group page appears.
Figure 52 Creating an SNMP group

4. Configure SNMP group settings as described in Table 26.
5. Click Apply.
|
Item |
Description |
|
Group Name |
Set the SNMP group name. |
|
Security Level |
Select the security level for the SNMP group: · NoAuth/NoPriv—No authentication no privacy. · Auth/NoPriv—Authentication without privacy. · Auth/Priv—Authentication and privacy. |
|
Read View |
Select the read view of the SNMP group. |
|
Write View |
Select the write view of the SNMP group. If no write view is configured, the NMS cannot perform the write operations to all MIB objects on the device. |
|
Notify View |
Select the notify view of the SNMP group. The notify view can send trap messages. If no notify view is configured, the agent does not send traps to the NMS. |
|
ACL |
Associate a basic ACL with the group to restrict the source IP address of SNMP packets. You can configure to allow or prohibit SNMP packets with a specific source IP address to restrict the intercommunication between the NMS and the agent. |
Configuring an SNMP user
1. Select Device > SNMP from the navigation tree.
2. Click the User tab.
The user tab page appears.
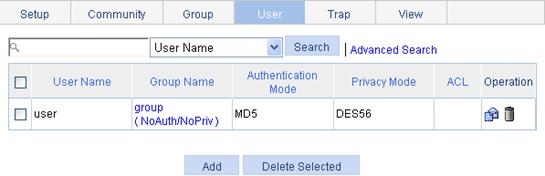
3. Click Add.
The Add SNMP User page appears.
Figure 54 Creating an SNMP user

4. Configure SNMP user settings as described in Table 27.
5. Click Apply.
|
Item |
Description |
|
User Name |
Set the SNMP user name. |
|
Security Level |
Select the security level for the SNMP group: · NoAuth/NoPriv—No authentication no privacy. · Auth/NoPriv—Authentication without privacy. · Auth/Priv—Authentication and privacy. |
|
Group Name |
Select an SNMP group to which the user belongs. · When the security level is NoAuth/NoPriv, you can select an SNMP group with no authentication no privacy. · When the security level is Auth/NoPriv, you can select an SNMP group with no authentication no privacy or authentication without privacy. · When the security level is Auth/Priv, you can select an SNMP group of any security level. |
|
Authentication Mode |
Select an authentication mode (including MD5 and SHA) when the security level is Auth/NoPriv or Auth/Priv. |
|
Authentication Password |
Set the authentication password when the security level is Auth/NoPriv or Auth/Priv. The confirm authentication password must be the same as the authentication password. |
|
Confirm Authentication Password |
|
|
Privacy Mode |
Select a privacy mode (including DES56, AES128, and 3DES) when the security level is Auth/Priv. |
|
Privacy Password |
Set the privacy password when the security level is Auth/Priv. The confirm privacy password must be the same as the privacy password. |
|
Confirm Privacy Password |
|
|
ACL |
Associate a basic ACL with the user to restrict the source IP address of SNMP packets. You can configure to allow or prohibit SNMP packets with a specific source IP address to allow or prohibit the specified NMS to access the agent by using name of the associated user. |
Configuring SNMP trap function
1. Select Device > SNMP from the navigation tree.
2. Click the Trap tab.
The trap configuration page appears.

3. Select Enable SNMP Trap.
4. Click Apply.
5. Click Add.
The page for adding a target host of SNMP traps appears.
Figure 56 Adding a target host of SNMP traps
6. Configure the settings for the target host as described in Table 28.
7. Click Apply.
|
Item |
Description |
|
Destination IP Address |
Set the destination IP address or domain. Select the IP address type: IPv4/Domain or IPv6, and then type the corresponding IP address or domain in the field according to the IP address type. |
|
Security Name |
Set the security name, which can be an SNMPv1 community name, an SNMPv2c community name, or an SNMPv3 user name. |
|
UDP Port |
Set UDP port number.
The default port number is 162, which is the SNMP-specified port used for receiving traps on the NMS. Typically (such as using IMC or MIB Browser as the NMS), you can use the default port number. To change this parameter to another value, you need to make sure that the configuration is the same as the configuration on the NMS. |
|
Security Model |
Select the security model, which is the SNMP version. The model must be the same as the model running on the NMS. Otherwise, the NMS cannot receive any trap. |
|
Security Level |
Set the authentication and privacy mode for SNMP traps when the security model is selected as v3. The available security levels are: no authentication no privacy, authentication but no privacy, and authentication and privacy. |
Displaying SNMP packet statistics
1. Select Device > SNMP from the navigation tree.
The page for displaying SNMP packet statistics appears.
Figure 57 SNMP packet statistics

SNMPv1/SNMPv2c configuration example
Network requirements
As shown in Figure 58, the NMS (1.1.1.2/24) uses SNMPv1 or SNMPv2c to manage the AC (1.1.1.1/24), and the AC automatically sends traps to report events to the NMS.

Configuring the AC (SNMP agent)
1. Enable SNMP agent:
a. Select Device > SNMP from the navigation tree.
The page in Figure 59 appears.
b. Select the Enable option.
c. Select the v1 and v2c boxes, as shown in Figure 59.
d. Click Apply.
Figure 59 Enabling SNMP agent

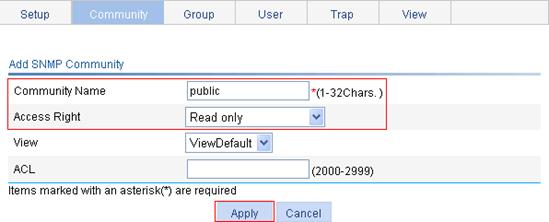
2. Configure an SNMP read-only community:
a. Click the Community tab.
b. Click Add.
c. Enter public in the Community Name field and select Read only from the Access Right list, as shown in Figure 60.
d. Click Apply.
Figure 60 Creating an SNMP read-only community
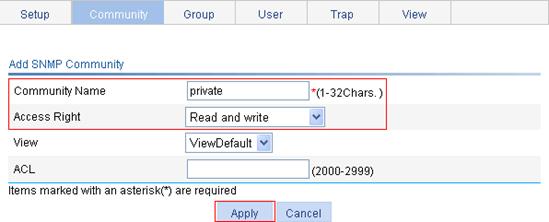
3. Configure an SNMP read/write community:
a. Click Add on the Community tab.
b. Enter private in the Community Name field and select Read and write from the Access Right list, as shown in Figure 61.
c. Click Apply.
Figure 61 Creating an SNMP read/write community
4. Enable the agent to send SNMP traps:
a. Click the Trap tab.
b. Select the Enable SNMP Trap box.
c. Click Apply.
Figure 62 Enabling the agent to send SNMP traps

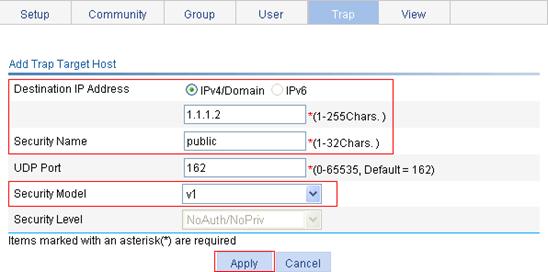
5. Configure an SNMP trap target host:
a. Click the Trap tab.
b. Click Add.
c. Select the IPv4/Domain option, enter the destination address 1.1.1.2, enter public in the Security Name field, and select v1 from the Security Model list, as shown in Figure 63.
To make sure the NMS can receive traps, specify the same SNMP version as configured on the NMS.
d. Click Apply.
Figure 63 Adding an SNMP trap target host
Configuring the NMS
|
|
IMPORTANT: The configuration on the NMS must be consistent with the configuration on the agent. Otherwise, you cannot perform corresponding operations. |
To configure the NMS:
1. Specify the SNMPv1 or SNMPv2c version.
2. Create a read-only community named public.
3. Create a read/write community named private.
For more information about configuration procedure on the NMS, see the NMS user manual.
Verifying the configuration
Verify that the NMS can access and set some MIB variables on the AC.
Shut down and bring up an idle interface on the AC, and verify that the NMS can receive the link traps from the AC.
SNMPv3 configuration example
Network requirements
As shown in Figure 64, the NMS (1.1.1.2/24) uses SNMPv3 to manage the AC (1.1.1.1/24), and the AC automatically sends traps to report events to the NMS.
The NMS and the AC perform authentication when they set up an SNMP session. The authentication algorithm is MD5 and the authentication key is authkey. The NMS and the agent also encrypt the SNMP packets between them by using the DES56 algorithm and the privacy key prikey.

Configuring the AC (SNMP agent)
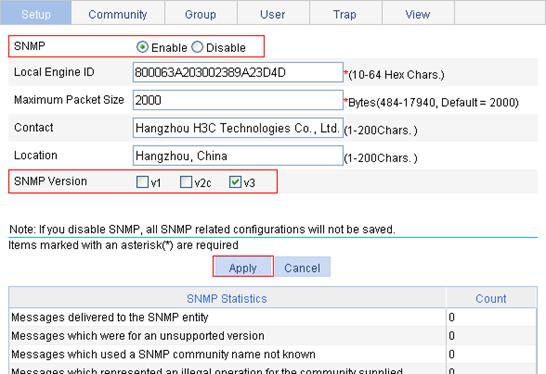
1. Enable SNMP agent:
a. Select Device > SNMP from the navigation tree.
b. Select the Enable option to enable the SNMP agent, and select v3 for SNMP Version, as shown in Figure 65.
c. Click Apply.
2. Configure an SNMP view:
a. Click the View tab.
b. Click Add.
The page in Figure 66 appears.
c. Enter view1 in the field.
d. Click Apply.
The page in Figure 67 appears.
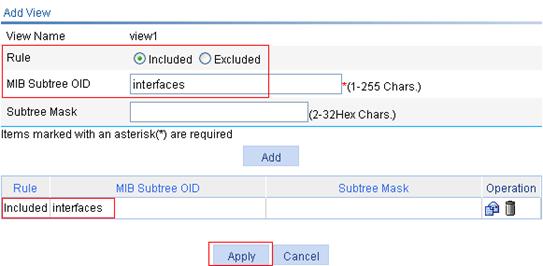
e. Select the Included radio box, enter the MIB subtree OID interfaces, and click Add.
f. Click Apply.
A configuration progress dialog box appears.
g. Click Close after the configuration process is complete.
Figure 66 Creating an SNMP view (1)
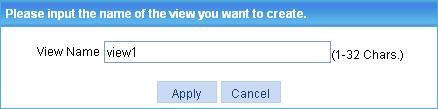
Figure 67 Creating an SNMP view (2)
a. Click the Group tab.
b. Click Add.
The page in Figure 68 appears.
c. Enter group1 in the field of Group Name, select view1 from the Read View box, and select view1 from the Write View box.
d. Click Apply.
Figure 68 Creating an SNMP group

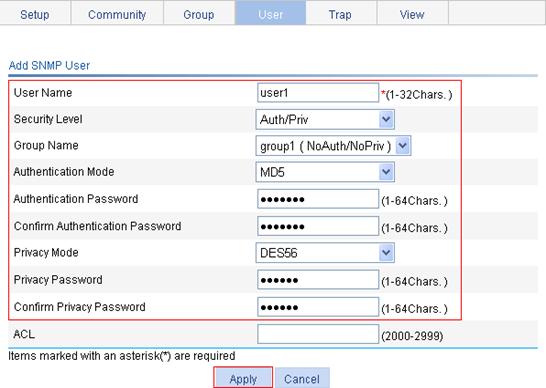
4. Configure an SNMP user:
a. Click the User tab.
b. Click Add.
The page in Figure 69 appears.
c. Enter user1 in the User Name field.
d. Select Auth/Priv from the Security Level list.
e. Select group1 from the Group Name list.
f. Select MD5 from the Authentication Mode list.
g. Enter authkey in the Authentication Password and Confirm Authentication Password fields.
h. Select DES56 from the Privacy Mode list.
i. Enter prikey in the Privacy Password and Conform Privacy Password fields.
j. Click Apply.
Figure 69 Creating an SNMP user
5. Enable the agent to send SNMP traps:
a. Click the Trap tab
The page in Figure 70 appears.
b. Select the Enable SNMP Trap box.
c. Click Apply.
Figure 70 Enabling the agent to send SNMP traps

6. Add target hosts of SNMP traps:
a. Click Add on the Trap tab.
The page in Figure 71 appears.
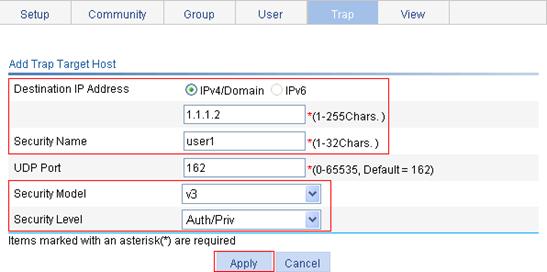
b. Select the destination IP address type as IPv4/Domain, enter the destination address 1.1.1.2, enter the user name user1, select v3 from the Security Model list, and select Auth/Priv from the Security Level list.
c. Click Apply.
Figure 71 Adding target hosts of SNMP traps
Configuring the NMS
|
|
IMPORTANT: The configuration on the NMS must be consistent with the configuration on the agent. Otherwise, you cannot perform corresponding operations. |
To configure the NMS:
1. Specify the SNMPv3 version.
2. Set the username to user1, authentication algorithm to MD5, authentication key to authkey, encryption algorithm to DES56, and privacy key to prikey.
For more information about configuring the NMS, see the NMS user manual.
Verifying the configuration
Verify that the NMS can access and set some MIB variables on the AC.
Shut down and bring up an idle interface on the AC, and verify that the NMS can receive the link traps from the AC.
Configuring loopback
You can check whether an Ethernet port works correctly by performing the Ethernet port loopback test. During the test the port cannot correctly forward data packets.
Ethernet port loopback test can be an internal loopback test or an external loopback test.
· In an internal loopback test, self loop is established in the switching chip to check whether there is a chip failure related to the functions of the port.
· In an external loopback test, a self-loop header is used on the port. Packets forwarded by the port will be received by itself through the self-loop header. The external loopback test can be used to check whether there is a hardware failure on the port.
Support of Ethernet ports for internal or external loopback test depends on the device model. For more information, see "About the H3C Access Controllers Web-Based Configuration Guide."
Configuration guidelines
When you perform a loopback test, follow these guidelines:
· You can perform an internal loopback test but not an external loopback test on a port that is physically down, while you can perform neither test on a port that is manually shut down.
· The system does not allow Rate, Duplex, Cable Type, and Port Status configuration on a port under a loopback test.
· An Ethernet port operates in full duplex mode when the loopback test is performed, and restores its original duplex mode after the loopback test.
Loopback operation
1. Select Device > Loopback from the navigation tree.
The loopback test configuration page appears.
Figure 72 Loopback test configuration page

2. Configure the loopback test parameters as described in Table 29.
|
Item |
Description |
|
|
Testing type |
External |
Set the loopback test type to External or Internal. Support for the test type depends on the device model. |
|
Internal |
||
3. Click Test to start the loopback test.
After the test is completed, the test result appears in the Result box.
Figure 73 Loopback test result (for internal loopback test)
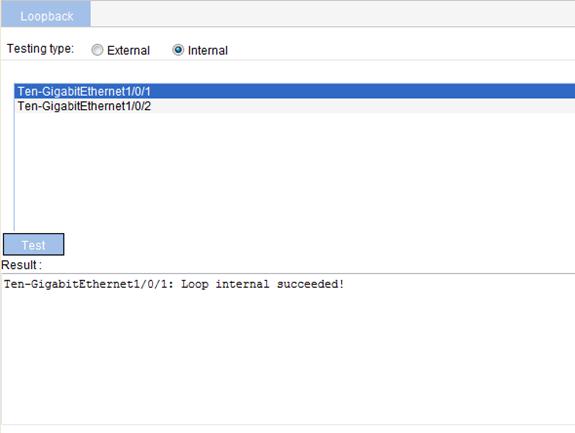
OAP management
Overview
In OAA, an Open Application Platform (OAP) module and network device are integrated to work as one device. From the perspective of an SNMP UDP domain-based NMS, however, the device and the OAP module are separate SNMP agents. They have different software systems and manage their own MIB objects. To access an SNMP agent, the NMS must obtain the IP address of the management interface on the agent. By default, the OAP module does not have an IP address, so you need to specify an IP address for the OAP module in the Web interface.
Support for OAP management depends on the device model. For more information, see "About the H3C Access Controllers Web-Based Configuration Guide."
Configuring a management IP address
1. Select Device > OAP Management from the navigation tree.
The OAP management configuration page appears.
2. Enter an IP address in the Management IP address field.
3. Click Apply.
Figure 74 OAP Management configuration page