- Table of Contents
-
- 16-BRAS Services Configuration Guide
- 00-Preface
- 01-BRAS services overview
- 02-AAA configuration
- 03-ANCP configuration
- 04-PPP configuration
- 05-ITA configuration
- 06-EDSG configuration
- 07-DHCP configuration
- 08-DHCPv6 configuration
- 09-User profile configuration
- 10-Connection limit configuration
- 11-L2TP configuration
- 12-PPPoE configuration
- 13-Portal configuration
- 14-IPoE configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 05-ITA configuration | 119.02 KB |
Restrictions: Hardware compatibility with ITA
Restrictions and guidelines: ITA configuration
Display and maintenance commands for ITA
Example: Configuring ITA for IPoE users
Example: Configuring dynamic ITA policy assignment for PPPoE users
Configuring ITA
About ITA
Intelligent Target Accounting (ITA) provides a flexible accounting solution for users that request services of different charge rates. By defining different traffic levels based on the destination addresses of users' traffic, you can use ITA to separate the traffic accounting statistics of different levels for each user.
You must deploy an ITA policy to implement ITA services.
If a user is assigned an ITA policy associated with a user group, the ITA services of that user will be assigned to the user group. Different user groups can be associated with different accounting levels and CAR actions. To dynamically change the ITA accounting levels and CAR actions for an online user, you can dynamically change the ITA policy of the user to assign the ITA services of that user to a new user group.
Restrictions: Hardware compatibility with ITA
ITA is supported only on CEPC and CSPEX (except CSPEX-1104-E) cards.
Restrictions and guidelines: ITA configuration
ITA is supported only when the device operates in standard mode. For more information about setting the system operating mode to standard, see device management in Fundamentals Configuration Guide.
ITA takes effect only on IPoE, portal, and PPPoE users.
When you specify a traffic level for ITA accounting, follow these restrictions and guidelines:
· For dual-stack PPPoE users, you cannot specify the same ITA traffic level for IPv4 ITA traffic and IPv6 ITA traffic. If you specify the same ITA traffic level for IPv4 ITA traffic and IPv6 ITA traffic, the most recent configuration takes effect.
· The device does not perform accounting on ITA traffic if you do not specify the ipv4 or ipv6 keyword in the accounting-level command.
· Supported traffic levels for ITA accounting vary by the access types of users, as shown in Table 1.
Table 1 ITA traffic accounting levels for different user types
|
User type |
Number of ITA traffic accounting levels |
|
|
CSPEX-1204 card |
CSPEX cards (except the CSPEX-1204 and CSPEX-1104-E cards) CEPC cards |
|
|
Portal users that access the network through VLAN interfaces |
7 (level-1 to level 8) |
7 (level-1 to level 8) |
|
Portal users that access the network through the following types of interfaces: · Layer 3 Ethernet interface. · Layer 3 Ethernet subinterface. · Layer 3 aggregate interface. · Layer 3 aggregate subinterface. |
1 (level-1) |
4 (level 1 to level 4) |
|
IPoE users |
1 (level-1) |
4 (level 1 to level 4) |
|
PPPoE users |
1 (level-1) |
4 (level 1 to level 4) |
ITA tasks at a glance
To deploy an ITA policy, perform the following tasks:
1. Configure a QoS policy to remark traffic destined for different IP addresses or subnets to different levels.
For more information about QoS, see ACL and QoS Configuration Guide.
2. Apply the QoS policy.
For ITA to operate correctly, choose only one of the following methods:
¡ Apply the QoS policy globally or to interfaces. This method is not applicable to portal users that access the network through VLAN interfaces.
¡ Configure a user profile, apply the QoS policy to the user profile, and assign the user profile to authenticated users.
Two methods are available for assigning the user profile to authenticated users. You can configure a remote server or the device to assign the user profile or specify the user profile in the authentication domain. The user profile assigned by a remote server or the device takes precedence over the user profile specified in the authentication domain.
For more information about user profiles, see "Configuring user profiles."
4. Apply the ITA policy to authenticated users. The following methods are available:
¡ Use a RADIUS server to assign the ITA policy.
¡ Specify the ITA policy in the authentication domain.
The ITA policy assigned by a RADIUS server takes precedence over the ITA policy specified in the authentication domain.
Configuring an ITA policy
1. Enter system view.
system-view
2. Create an ITA policy and enter ITA policy view.
ita policy policy-name
3. Specify accounting methods in the ITA policy.
accounting-method { none | radius-scheme radius-scheme-name [ none ] }
By default, the accounting method is none.
4. Specify a traffic level for ITA accounting.
accounting-level level { { ipv4 | ipv6 } | [ car { inbound cir committed-information-rate [ pir peak-information-rate ] | outbound cir committed-information-rate [ pir peak-information-rate ] } * } *
By default, no traffic levels are specified for ITA accounting.
5. (Optional.) Enable accounting merge.
accounting-merge enable
By default, accounting merge is disabled.
6. (Optional.) Configure access control for users that have used up their ITA data quotas.
traffic-quota-out { offline | online } [ no-accounting-update ]
By default, the device sends accounting-update packets to the server to request new accounting quotas for the users that have used up their accounting quotas. A user is logged off if the device does not receive any new quota from the server for the user.
7. (Optional.) Exclude the amount of specific-level ITA traffic from the overall traffic statistics that are sent to the accounting server.
traffic-separate enable [ level level&<1-8> ]
By default, the amount of ITA traffic is included in the overall traffic statistics that are sent to the accounting server.
8. (Optional.) Specify a user group for the ITA policy.
user-group name group-name [ nat-instance instance-name ]
By default, no user groups are specified for an ITA policy.
Display and maintenance commands for ITA
Execute display commands in any view.
|
Task |
Command |
|
Display ITA policy information. |
display ita policy [ policy-name ] |
ITA configuration examples
Example: Configuring ITA for IPoE users
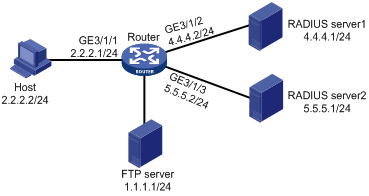
Network configuration
As shown in Figure 1, the router performs IPoE authentication.
Configure the router to meet the following requirements:
· Use RADIUS server 1 to perform authentication, authorization, and accounting for IPoE users.
· Use RADIUS server 2 to perform ITA accounting for IPoE users. The traffic destined for the FTP server is configured as level 1 traffic. The router counts the traffic as IPv4 traffic.
· Exclude ITA traffic statistics from the overall traffic statistics reported to RADIUS server 1.
· Prohibit users from accessing the FTP server after their level-1 data quotas are used up.
The RADIUS servers are FreeRADIUS servers.
Configuring RADIUS servers
Configure RADIUS client information on RADIUS server 1 and RADIUS server 2.
# Configure the clients.conf file.
client 4.4.4.2/32 {
ipaddr = 4.4.4.2
netmask=32
secret=radius
}
client 5.5.5.2/32 {
ipaddr = 5.5.5.2
netmask=32
secret=radius
}
# Configure the IP address of the user in the users file.
2.2.2.2 Cleartext-Password :="radius"
Configuring the router
1. Configure the IP address of each interface, as shown in Figure 1. (Details not shown.)
2. Configure a RADIUS scheme for AAA:
# Create a RADIUS scheme named rs1 and enter RADIUS scheme view.
<Router> system-view
[Router] radius scheme rs1
# Specify the primary RADIUS authentication server at 4.4.4.1.
[Router-radius-rs1] primary authentication 4.4.4.1
# Specify the primary RADIUS accounting server at 4.4.4.1.
[Router-radius-rs1] primary accounting 4.4.4.1
# Set the authentication shared key to radius in plaintext form for secure communication between the router and RADIUS server 1.
[Router-radius-rs1] key authentication simple radius
# Set the accounting shared key to radius in plaintext form for secure communication between the router and RADIUS server 1.
[Router-radius-rs1] key accounting simple radius
# Exclude domain names from the usernames sent to RADIUS server 1.
[Router-radius-rs1] user-name-format without-domain
[Router-radius-rs1] quit
3. Configure a RADIUS scheme for the ITA service:
# Create a RADIUS scheme named rs2 and enter RADIUS scheme view.
[Router] radius scheme rs2
# Specify the primary accounting server at 5.5.5.1.
[Router-radius-rs2] primary accounting 5.5.5.1
# Set the accounting shared key to radius in plaintext form for secure communication between the router and RADIUS server 2.
[Router-radius-rs2] key accounting simple radius
# Exclude domain names from the usernames sent to RADIUS server 2.
[Router-radius-rs1] user-name-format without-domain
[Router-radius-rs1] quit
4. Create a traffic class named class1, and define match criteria for the traffic class to match the packets of users that have passed IPoE, portal, or PPPoE authentication and match ACL 3000.
[Router] traffic classifier class1 operator and
[Router-classifier-class1] if-match authenticated-user
[Router-classifier-class1] if-match acl 3000
[Router-classifier-class1] quit
5. Configure a QoS policy for the ITA service:
# Configure IPv4 advanced ACL 3000 and enter its view.
[Router] acl advanced 3000
# Permit all packets destined for 1.1.1.1.
[Router-acl-ipv4-adv-3000] rule 0 permit ip destination 1.1.1.1 0
[Router-acl-ipv4-adv-3000] quit
# Create a traffic class named classifier_1.
[Router] traffic classifier classifier_1
# Define a match criterion for traffic class classifier_1 to match advanced ACL 3000.
[Router-classifier-classifier_1] if-match acl 3000
[Router-classifier-classifier_1] quit
# Create a traffic behavior named behavior_1 and enter traffic behavior view.
[Router] traffic behavior behavior_1
# Mark level-1 traffic for ITA accounting.
[Router-behavior-behavior_1] remark account-level 1
# Measure the traffic in bytes.
[Router-behavior-behavior_1] accounting byte
[Router-behavior-behavior_1] quit
# Define a QoS policy named policy and enter QoS policy view.
[Router] qos policy policy
# Associate traffic class classifier_1 with traffic behavior behavior_1 in the QoS policy.
[Router-qospolicy-policy] classifier classifier_1 behavior behavior_1
[Router-qospolicy-policy] quit
6. Apply QoS policy policy to the inbound traffic of users on GigabitEthernet 3/1/1.
[Router] interface gigabitethernet 3/1/1
[Router-GigabitEthernet3/1/1] qos apply policy policy inbound
[Router–GigabitEthernet3/1/1] quit
7. Configure an ITA policy:
# Create an ITA policy named ita and enter ITA policy view.
[Router] ita policy ita
# Configure the accounting method for users that match the ITA policy.
[Router-ita-policy-ita] accounting-method radius-scheme rs2
# Specify level-1 traffic for ITA accounting and count the traffic as IPv4 traffic.
[Router-ita-policy-ita] accounting-level 1 ipv4
# Exclude the amount of ITA traffic from the overall traffic statistics that are sent to RADIUS server 1.
[Router-ita-policy-ita] traffic-separate enable
# Prohibit users from accessing the authorized IP subnets after their ITA data quotas are used up.
[Router-ita-policy-ita] traffic-quota-out offline
[Router-ita-policy-ita] quit
8. Configure an ISP domain:
# Create an ISP domain named dm1 and enter ISP domain view.
[Router] domain name dm1
# Configure the authentication, authorization, and accounting methods for IPoE users in the domain.
[Router-isp-dm1] authentication ipoe radius-scheme rs1
[Router-isp-dm1] authorization ipoe radius-scheme rs1
[Router-isp-dm1] accounting ipoe radius-scheme rs1
# Apply ITA policy ita to the ISP domain.
[Router-isp-dm1] ita-policy ita
[Router-isp-dm1] quit
9. Configure IPoE:
# Enter the view of GigabitEthernet 3/1/1.
[Router] interface gigabitethernet 3/1/1
# Enable IPoE and configure Layer 3 access mode on the port.
[Router–GigabitEthernet3/1/1] ip subscriber routed enable
# Enable the unclassified-IP users.
[Router–GigabitEthernet3/1/1] ip subscriber initiator unclassified-ip enable
# Specify dm1 as the ISP domain.
[Router–GigabitEthernet3/1/1] ip subscriber unclassified-ip domain dm1
# Set the password to radius in plaintext form for IPoE authentication.
[Router–GigabitEthernet3/1/1] ip subscriber password plaintext radius
[Router–GigabitEthernet3/1/1] quit
Verifying the configuration
# Use password radius to pass IPoE authentication on the host. (Details not shown.)
# Verify that RADIUS server 2 performs accounting for the IPoE user when the user accesses the FTP server at 1.1.1.1. (Details not shown.)
# Verify that RADIUS server 1 performs accounting for the non-ITA traffic of the IPoE user. (Details not shown.)
# Display detailed information about the sessions of online IPoE users. Verify that the user has generated ITA traffic statistics.
[Router] display ip subscriber session verbose
Example: Configuring dynamic ITA policy assignment for PPPoE users
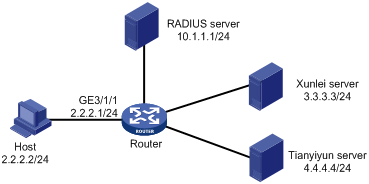
Network configuration
As shown in Figure 2, the host accesses the router through PPPoE. The router acts as a BRAS device and provides address translation services for the host through CGN cards.
Configure the router to meet the following requirements:
· The router acts as the PPPoE server and uses CHAP to perform RADIUS-based authentication for the host user. After the user passes authentication, the router assigns an IP address to the host from the DHCP address pool.
· The router uses the RADIUS server to perform authentication, authorization, and accounting for the host user. The shared key is expert for securing the communication between the router and the RADIUS server. The router sends the username with the domain name to the RADIUS server.
· NAT on the router cooperates with BRAS. When the user passes authentication, the router assigns public address 111.8.0.200 and a port block to the host in addition to a private address.
· When the user is online, the router cooperates with the RADIUS server to dynamically assign ITA policies to the user. Multiple ITA policies are configured on the router. A traffic level is defined for each of them.
¡ Level-3 traffic is destined for and originated from the Xunlei server. The downstream CIR is 30 M.
¡ Level-1 traffic is destined for and originated from the Tianyiyun server. The upstream CIR is 20 M and the downstream CIR is 20 M.
¡ Level-4 traffic is destined for and originated from the Xunlei server or the Tianyiyun server. The upstream CIR is 20 M and the downstream CIR is 30 M.
· The router excludes the amount of ITA traffic from the overall traffic statistics that are sent to the RADIUS server. ITA traffic and non-ITA traffic are separated in accounting.
The RADIUS server can assign an ITA policy that does not have any configuration on the router (default in this example) to remove the ITA policies that have been assigned to a user.
Configuring the RADIUS server
# Set the shared keys to expert for secure communication with the router, add an account for the PPP user, and specify the user password. (Details not shown.)
Configuring the router
1. Configure user groups:
# Create user group nat1.
<Router> system-view
[Router] user-group nat1
[Router-ugroup-nat1] quit
# Create user group nat1_xunlei.
[Router] user-group nat1_xunlei
[Router-ugroup-nat1_xunlei] quit
# Create user group nat1_tianyiyun.
[Router] user-group nat1_tianyiyun
[Router-ugroup-nat1_tianyiyun] quit
# Create user group nat1_allapp.
[Router] user-group nat1_allapp
[Router-ugroup-nat1_allapp] quit
2. Configure the authentication domain:
# Create RADIUS scheme rad and enter its view.
[Router] radius scheme rad
# Specify the RADIUS server at 10.1.1.1 as the primary RADIUS accounting server and set the accounting port number to 1813 (the default value).
[Router-radius-rad] primary accounting 10.1.1.1 1813
# Specify the RADIUS server at 10.1.1.1 as the primary RADIUS authentication server and set the authentication port number to 1812 (the default value).
[Router-radius-rad] primary authentication 10.1.1.1 1812
# Set the authentication shared key to expert in plaintext form for secure communication between the router and the RADIUS authentication server.
[Router-radius-rad] key authentication simple expert
# Set the accounting shared key to expert in plaintext form for secure communication between the router and the RADIUS accounting server.
[Router-radius-rad] key accounting simple expert
# Include the domain name in the username sent to the RADIUS server.
[Router-radius-rad] user-name-format with-domain
[Router-radius-rad] quit
# Create ISP domain pppoe and enter its view.
[Router] domain name pppoe
# Bind user group nat1 to NAT instance nat1.
[Router-isp-pppoe] user-group name nat1 bind nat-instance nat1
# Configure the ISP domain to use RADIUS scheme rad for PPP user authentication, authorization, and accounting.
[Router-isp-pppoe] authentication ppp radius-scheme rad
[Router-isp-pppoe] authorization ppp radius-scheme rad
[Router-isp-pppoe] accounting ppp radius-scheme rad
# Specify the private IPv4 address type for users in the ISP domain. The router will trigger NAT address assignment for users that use this type of addresses after they pass authentication.
[Router-isp-pppoe] user-address-type private-ipv4
# Configure DHCP address pool pool1 as the authorization IP address pool in ISP domain pppoe.
[Router-isp-pppoe] authorization-attribute ip-pool pool1
[Router-isp-pppoe] quit
3. Configure ITA policies:
# Create ITA policy nat1_xunlei and enter its view.
[Router] ita policy nat1_xunlei
# Configure the accounting method for users that match the ITA policy.
[Router-ita-policy-nat1_xunlei] accounting-method radius-scheme rad
# Specify level-3 traffic for ITA accounting, count the traffic as IPv4 traffic, and set the outbound CIR to 30720 kbps (30 M).
[Router-ita-policy-nat1_xunlei] accounting-level 3 ipv4 car outbound cir 30720
# Specify user group nat1_xunlei for the ITA policy and bind the user group to NAT instance nat1 in the ITA policy.
[Router-ita-policy-nat1_xunlei] user-group name nat1_xunlei nat-instance nat1
# Enable the accounting merge feature.
[Router-ita-policy-nat1_xunlei] accounting-merge enable
# Exclude the amount of level-3 ITA traffic from the overall traffic statistics that are sent to the accounting server.
[Router-ita-policy-nat1_xunlei] traffic-separate enable level 3
[Router-ita-policy-nat1_xunlei] quit
# Create ITA policy nat1_tianyiyun and enter its view.
[Router] ita policy nat1_tianyiyun
# Configure the accounting method for users that match the ITA policy.
[Router-ita-policy-nat1_tianyiyun] accounting-method radius-scheme rad
# Specify level-1 traffic for ITA accounting, count the traffic as IPv4 traffic, set the inbound CIR to 20480 kbps (20 M), and set the outbound CIR to 20480 kbps (20 M).
[Router-ita-policy-nat1_tianyiyun] accounting-level 1 ipv4 car inbound cir 20480 outbound cir 20480
# Specify user group nat1_tianyiyun for the ITA policy and bind the user group to NAT instance nat1 in the ITA policy.
[Router-ita-policy-nat1_tianyiyun] user-group name nat1_tianyiyun nat-instance nat1
# Enable the accounting merge feature.
[Router-ita-policy-nat1_tianyiyun] accounting-merge enable
# Exclude the amount of level-1 ITA traffic from the overall traffic statistics that are sent to the accounting server.
[Router-ita-policy-nat1_tianyiyun] traffic-separate enable level 1
[Router-ita-policy-nat1_tianyiyun] quit
# Create ITA policy nat1_allapp and enter its view.
[Router] ita policy nat1_allapp
# Configure the accounting method for users that match the ITA policy.
[Router-ita-policy-nat1_allapp] accounting-method radius-scheme rad
# Specify level-4 traffic for ITA accounting, count the traffic as IPv4 traffic, set the inbound CIR to 20480 kbps (20 M), and set the outbound CIR to 30720 kbps (30 M).
[Router-ita-policy-nat1_allapp] accounting-level 4 ipv4 car inbound cir 20480 outbound cir 30720
# Specify user group nat1_allapp for the ITA policy and bind the user group to NAT instance nat1 in the ITA policy.
[Router-ita-policy-nat1_allapp] user-group name nat1_allapp nat-instance nat1
# Enable the accounting merge feature.
[Router-ita-policy-nat1_allapp] accounting-merge enable
# Exclude the amount of level-4 ITA traffic from the overall traffic statistics that are sent to the accounting server.
[Router-ita-policy-nat1_allapp] traffic-separate enable level 4
[Router-ita-policy-nat1_allapp] quit
# Create an ITA policy named default. Do not configure the ITA policy. The ITA policy will be used by the RADIUS server to remove ITA policies that have been assigned to a user.
[Router] ita policy default
[Router-ita-policy-default] quit
4. Configure ACLs to match ITA traffic:
# Create advanced ACL 3000, and configure the ACL to permit all packets destined for 3.3.3.3 from users in user group nat1_xunlei.
[Router] acl advanced 3000
[Router-acl-ipv4-adv-3000] rule 0 permit ip destination 3.3.3.3 0 user-group nat1_xunlei
[Router-acl-ipv4-adv-3000] quit
# Create advanced ACL 3001, and configure the ACL to permit all packets originated from 3.3.3.3 to users in user group nat1_xunlei.
[Router] acl advanced 3001
[Router-acl-ipv4-adv-3001] rule 0 permit ip source 3.3.3.3 0 user-group nat1_xunlei
[Router-acl-ipv4-adv-3001] quit
# Create advanced ACL 3100, and configure the ACL to permit all packets destined for 4.4.4.4 from users in user group nat1_tianyiyun.
[Router] acl advanced 3100
[Router-acl-ipv4-adv-3100] rule 0 permit ip destination 4.4.4.4 0 user-group nat1_tianyiyun
[Router-acl-ipv4-adv-3100] quit
# Create advanced ACL 3101, and configure the ACL to permit all packets originated from 4.4.4.4 to users in user group nat1_tianyiyun.
[Router] acl advanced 3101
[Router-acl-ipv4-adv-3101] rule 0 permit ip source 4.4.4.4 0 user-group nat1_tianyiyun
[Router-acl-ipv4-adv-3101] quit
# Create advanced ACL 3200, and configure the ACL to permit all packets destined for 3.3.3.3 and 4.4.4.4 from users in user group nat1_allapp.
[Router] acl advanced 3200
[Router-acl-ipv4-adv-3200] rule 0 permit ip destination 3.3.3.3 0 user-group nat1_allapp
[Router-acl-ipv4-adv-3200] rule 5 permit ip destination 4.4.4.4 0 user-group nat1_allapp
[Router-acl-ipv4-adv-3200] quit
# Create advanced ACL 3201, and configure the ACL to permit all packets originated from 3.3.3.3 and 4.4.4.4 to users in user group nat1_allapp.
[Router] acl advanced 3201
[Router-acl-ipv4-adv-3201] rule 0 permit ip source 3.3.3.3 0 user-group nat1_allapp
[Router-acl-ipv4-adv-3201] rule 5 permit ip source 4.4.4.4 0 user-group nat1_allapp
[Router-acl-ipv4-adv-3201] quit
# Create advanced ACL 3301, and configure the ACL to permit all packets originated from and destined for the users in user group nat1 to pass through.
[Router] acl advanced 3301
[Router-acl-ipv4-adv-3301] rule 0 permit ip user-group nat1
[Router-acl-ipv4-adv-3301] quit
5. Configure QoS policies:
# Create traffic class nat1_xunlei_shangxing_class and configure the traffic class to match ACL 3000.
[Router] traffic classifier nat1_xunlei_shangxing_class
[Router-classifier-nat1_xunlei_shangxing_class] if-match acl 3000
[Router-classifier-nat1_xunlei_shangxing_class] quit
# Create traffic behavior nat1_xunlei_shangxing_action, and configure a traffic accounting action in the traffic behavior to count traffic in bytes. Configure the traffic behavior to mark matching packets with accounting level 3, and configure a NAT instance binding action for the traffic behavior.
[Router] traffic behavior nat1_xunlei_shangxing_action
[Router-behavior-nat1_xunlei_shangxing_action] accounting byte
[Router-behavior-nat1_xunlei_shangxing_action] remark account-level 3
[Router-behavior-nat1_xunlei_shangxing_action] bind nat-instance nat1
[Router-behavior-nat1_xunlei_shangxing_action] quit
# Create traffic class nat1_xunlei_xiaxing_class and configure the traffic class to match ACL 3001.
[Router] traffic classifier nat1_xunlei_xiaxing_class
[Router-classifier-nat1_xunlei_xiaxing_class] if-match acl 3001
[Router-classifier-nat1_xunlei_xiaxing_class] quit
# Create traffic behavior nat1_xunlei_xiaxing_action, and configure a traffic accounting action in the traffic behavior to count traffic in bytes, and configure the traffic behavior to mark matching packets with accounting level 3.
[Router] traffic behavior nat1_xunlei_xiaxing_action
[Router-behavior-nat1_xunlei_xiaxing_action] accounting byte
[Router-behavior-nat1_xunlei_xiaxing_action] remark account-level 3
[Router-behavior-nat1_xunlei_xiaxing_action] quit
# Create traffic class nat1_tianyiyun_shangxing_class and configure the traffic class to match ACL 3100.
[Router] traffic classifier nat1_tianyiyun_shangxing_class
[Router-classifier-nat1_tianyiyun_shangxing_class] if-match acl 3100
[Router-classifier-nat1_tianyiyun_shangxing_class] quit
# Create traffic behavior nat1_tianyiyun_shangxing_action, and configure a traffic accounting action in the traffic behavior to count traffic in bytes. Configure the traffic behavior to mark matching packets with accounting level 1, and configure a NAT instance binding action for the traffic behavior.
[Router] traffic behavior nat1_tianyiyun_shangxing_action
[Router-behavior-nat1_tianyiyun_shangxing_action] accounting byte
[Router-behavior-nat1_tianyiyun_shangxing_action] remark account-level 1
[Router-behavior-nat1_tianyiyun_shangxing_action] bind nat-instance nat1
[Router-behavior-nat1_tianyiyun_shangxing_action] quit
# Create traffic class nat1_tianyiyun_xiaxing_class and configure the traffic class to match ACL 3101.
[Router] traffic classifier nat1_tianyiyun_xiaxing_class
[Router-classifier-nat1_tianyiyun_xiaxing_class] if-match acl 3101
[Router-classifier-nat1_tianyiyun_xiaxing_class] quit
# Create traffic behavior nat1_tianyiyun_xiaxing_action, and configure a traffic accounting action in the traffic behavior to count traffic in bytes, and configure the traffic behavior to mark matching packets with accounting level 1.
[Router] traffic behavior nat1_tianyiyun_xiaxing_action
[Router-behavior-nat1_tianyiyun_xiaxing_action] accounting byte
[Router-behavior-nat1_tianyiyun_xiaxing_action] remark account-level 1
[Router-behavior-nat1_tianyiyun_xiaxing_action] quit
# Create traffic class nat1_allapp_shangxing_class and configure the traffic class to match ACL 3200.
[Router] traffic classifier nat1_allapp_shangxing_class
[Router-classifier-nat1_allapp_shangxing_class] if-match acl 3200
[Router-classifier-nat1_allapp_shangxing_class] quit
# Create traffic behavior nat1_allapp_shangxing_action, and configure a traffic accounting action in the traffic behavior to count traffic in bytes. Configure the traffic behavior to mark matching packets with accounting level 4, and configure a NAT instance binding action for the traffic behavior.
[Router] traffic behavior nat1_allapp_shangxing_action
[Router-behavior-nat1_allapp_shangxing_action] accounting byte
[Router-behavior-nat1_allapp_shangxing_action] remark account-level 4
[Router-behavior-nat1_allapp_shangxing_action] bind nat-instance nat1
[Router-behavior-nat1_allapp_shangxing_action] quit
# Create traffic class nat1_allapp_xiaxing_class and configure the traffic class to match ACL 3201.
[Router] traffic classifier nat1_allapp_xiaxing_class
[Router-classifier-nat1_allapp_xiaxing_class] if-match acl 3201
[Router-classifier-nat1_allapp_xiaxing_class] quit
# Create traffic behavior nat1_allapp_xiaxing_action, configure a traffic accounting action in the traffic behavior to count traffic in bytes, and configure the traffic behavior to mark matching packets with accounting level 4.
[Router] traffic behavior nat1_allapp_xiaxing_action
[Router-behavior-nat1_allapp_xiaxing_action] accounting byte
[Router-behavior-nat1_allapp_xiaxing_action] remark account-level 4
[Router-behavior-nat1_allapp_xiaxing_action] quit
# Create traffic class nat1_class and configure the traffic class to match ACL 3301.
[Router] traffic classifier nat1_class
[Router-classifier-nat1_class] if-match acl 3301
[Router-classifier-nat1_class] quit
# Create traffic behavior nat1_action, configure a traffic accounting action in the traffic behavior to count traffic in bytes, and configure a NAT instance binding action for the traffic behavior.
[Router] traffic behavior nat1_action
[Router-behavior-nat1_action] accounting byte
[Router-behavior-nat1_action] bind nat-instance nat1
[Router-behavior-nat1_action] quit
# Create QoS policy shangxing and associate traffic classes that match inbound traffic with traffic behaviors.
[Router] qos policy shangxing
[Router-qospolicy-shangxing] classifier nat1_xunlei_shangxing_class behavior nat1_xunlei_shangxing_action
[Router-qospolicy-shangxing] classifier nat1_tianyiyun_shangxing_class behavior nat1_tianyiyun_shangxing_action
[Router-qospolicy-shangxing] classifier nat1_allapp_shangxing_class behavior nat1_allapp_shangxing_action
[Router-qospolicy-shangxing] classifier nat1_class behavior nat1_action
[Router-qospolicy-shangxing] quit
# Create QoS policy xiaxing and associate traffic classes that match outbound traffic with traffic behaviors.
[Router] qos policy xiaxing
[Router-qospolicy-xiaxing] classifier nat1_xunlei_xiaxing_class behavior nat1_xunlei_xiaxing_action
[Router-qospolicy-xiaxing] classifier nat1_tianyiyun_xiaxing_class behavior nat1_tianyiyun_xiaxing_action
[Router-qospolicy-xiaxing] classifier nat1_allapp_xiaxing_class behavior nat1_allapp_xiaxing_action
[Router-qospolicy-xiaxing] quit
# Apply the QoS policies globally.
[Router] qos apply policy shangxing global inbound
[Router] qos apply policy xiaxing global outbound
6. Configure PPPoE:
# Enable the DHCP service.
[Router] dhcp enable
# Create DHCP address pool pool1 and the IP addresses are in the range of 2.2.2.2 to 2.2.2.255.
[Router] dhcp server ip-pool pool1
[Router-dhcp-pool-pool1] network 2.2.2.2 24
[Router-dhcp-pool-pool1] gateway-list 2.2.2.1
# Exclude IP address 2.2.2.1 from dynamic allocation in DHCP address pool pool1.
[Router-dhcp-pool-pool1] forbidden-ip 2.2.2.1
[Router-dhcp-pool-pool1] quit
# Create interface Virtual-Template 1, configure the interface to authenticate the peer by using CHAP in ISP domain pppoe, and enable PPP accounting on the interface.
[Router] interface virtual-template 1
[Router-Virtual-Template1] ppp authentication-mode chap domain pppoe
[Router-Virtual-Template1] ppp account-statistics enable
[Router-Virtual-Template1] quit
# Enable the PPPoE server on GigabitEthernet 3/1/1 and bind the interface with Virtual-Template 1.
[Router] interface gigabitethernet 3/1/1
[Router-GigabitEthernet3/1/1] pppoe-server bind virtual-template 1
[Router-GigabitEthernet3/1/1] quit
7. Configure CGN cards to provide NAT services:
# Create failover group failgrp with group ID 1 and enter its view.
[Router] failover group failgrp id 1
# Configure slot 2 as the primary node and slot 3 as the secondary node in failover group failgrp.
[Router-failover-group-failgrp] bind slot 2 primary
[Router-failover-group-failgrp] bind slot 3 secondary
[Router-failover-group-failgrp] quit
# Create service instance group sgrp and enter its view.
[Router] service-instance-group sgrp
# Associate failover group failgrp with service instance group sgrp.
[Router-service-instance-group-sgrp] failover-group failgrp
[Router-service-instance-group-sgrp] quit
# Create advanced ACL 3600, and configure the ACL to permit packets from 2.2.2.0/24 to pass through.
[Router] acl advanced 3600
[Router-acl-ipv4-adv-3600] rule permit ip source 2.2.2.0 0.0.0.255
[Router-acl-ipv4-adv-3600] quit
# Create a NAT address group numbered 1, add IP address 111.8.0.200 to the address group, specify a port range, and set the port block size to 2048.
[Router] nat address-group 1
[Router-address-group-1] port-block block-size 2048
[Router-address-group-1] port-range 1024 65535
[Router-address-group-1] address 111.8.0.200 111.8.0.200
[Router-address-group-1] quit
# Create NAT instance nat1 and enter its view.
[Router] nat instance nat1 id 1
# Associate NAT instance nat1 with service instance group sgrp.
[Router-nat-instance-nat1] service-instance-group sgrp
# Configure an outbound dynamic NAT rule for NAT instance nat1 to translate the source addresses of outgoing packets permitted by ACL 3600 into the addresses in address group 1.
[Router-nat-instance-nat1] nat outbound 3600 address-group 1
[Router-nat-instance-nat1] quit
# Configure IP prefix list prefix-a to permit routes destined for network 111.8.0.200/24.
[Router] ip prefix-list prefix-a index 10 permit 111.8.0.200 32 less-equal 32
# Configure a routing policy.
[Router] route-policy 1 permit node 1
[Router-route-policy-1-1] if-match ip address prefix-list prefix-a
[Router-route-policy-1-1] quit
# Redistribute direct routes that match the routing policy.
[Router] ospf 99
[Router-ospf-99] import-route direct route-policy 1
[Router-ospf-99] quit
8. Configure the RADIUS DAS feature:
# Enable the RADIUS DAS feature and enter RADIUS DAS view.
[Router] radius dynamic-author server
# Specify the RADIUS server at 10.1.1.1 as a DAC and set the shared key to expert in plaintext form.
[Router-radius-da-server] client ip 10.1.1.1 key simple expert
[Router-radius-da-server] quit
Verifying the configuration
# The PPP user accesses the router and passes authentication. (Details not shown.)
# Display detailed information about the PPP user.
<Router> display ppp access-user user-type pppoe verbose
Basic:
Interface: BAS1
PPP index: 0x140002381
User ID: 0x20102324
Username: PPPOE@pppoe
Domain: pppoe
Access interface: GE3/1/1
Service-VLAN/Customer-VLAN: -/-
VXLAN ID: -
MAC address: 0010-9400-0051
IP address: 2.2.2.2
IPv6 address:
IPv6 PD prefix: -
IPv6 ND prefix: -
User address type: private-ipv4
VPN instance: -
Access type: PPPoE
Authentication type: CHAP
PPPoE:
Session ID: 1
AAA:
Authentication state: Authenticated
Authorization state: Authorized
Realtime accounting switch: Open
Realtime accounting interval: 720s
Login time: 2019-02-21 15:25:03:924
Accounting start time: 2019-02-21 15:25:04:54
Online time(hh:mm:ss): 00:00:05
Accounting state: Accounting
Acct start-fail action: Online
Acct update-fail action: Online
Acct quota-out action: Offline
Dual-stack accounting mode: Merge
Idle cut: 0 sec 0 bytes, direction: Both
Session timeout: -
Time remained: -
Traffic quota: -
Traffic remained: -
Redirect WebURL: -
ITA policy name: N/A
MRU: 1492 bytes
IPv4 MTU: 1492 bytes
IPv6 MTU: 1492 bytes
Subscriber ID: -
ACL&QoS:
User profile: -
Session group profile: -
User group acl: -
Inbound CAR: -
Outbound CAR: -
User inbound priority: -
User outbound priority: -
NAT:
Global IP address: 111.8.0.200
Port block: 1024-3071
Flow Statistic:
IPv4 uplink packets/bytes: 11/810
IPv4 downlink packets/bytes: 0/0
IPv6 uplink packets/bytes: 0/0
IPv6 downlink packets/bytes: 0/0
ITA:
Acct merge: Disabled
Traffic separate levels: None
Acct quota-out action: Offline
# Use the RADIUS server to assign ITA policy nat1_xunlei to the online user through CoA messages. (Details not shown.)
# Display detailed information about the PPP user. Verify that ITA policy nat1_xunlei has been assigned to the user.
<Router> display ppp access-user user-type pppoe verbose
Basic:
Interface: BAS1
PPP index: 0x140002381
User ID: 0x20102324
Username: PPPOE@pppoe
Domain: pppoe
Access interface: GE3/1/1
Service-VLAN/Customer-VLAN: -/-
VXLAN ID: -
MAC address: 0010-9400-0051
IP address: 2.2.2.2
IPv6 address: -
IPv6 PD prefix: -
IPv6 ND prefix: -
User address type: private-ipv4
VPN instance: -
Access type: PPPoE
Authentication type: CHAP
PPPoE:
Session ID: 1
AAA:
Authentication state: Authenticated
Authorization state: Authorized
Realtime accounting switch: Open
Realtime accounting interval: 720s
Login time: 2019-02-21 15:25:03:924
Accounting start time: 2019-02-21 15:25:04:54
Online time(hh:mm:ss): 00:00:05
Accounting state: Accounting
Acct start-fail action: Online
Acct update-fail action: Online
Acct quota-out action: Offline
Dual-stack accounting mode: Merge
Idle cut: 0 sec 0 bytes, direction: Both
Session timeout: -
Time remained: -
Traffic quota: -
Traffic remained: -
Redirect WebURL: -
ITA policy name: nat1_xunlei
MRU: 1492 bytes
IPv4 MTU: 1492 bytes
IPv6 MTU: 1492 bytes
Subscriber ID: -
ACL&QoS:
User profile: -
Session group profile: -
User group acl: nat1_xunlei (active)
Inbound CAR: -
Outbound CAR: -
User inbound priority: -
User outbound priority: -
NAT:
Global IP address: 100.8.0.200
Port block: 1024-1033
Flow Statistic:
IPv4 uplink packets/bytes: 11/810
IPv4 downlink packets/bytes: 0/0
IPv6 uplink packets/bytes: 0/0
IPv6 downlink packets/bytes: 0/0
ITA:
Acct merge: Enabled
Traffic separate levels: 3
Acct quota-out action: Offline
Level-3 Inbound CAR : -
Outbound CAR: CIR 30720 kbps PIR 30720 kbps
IPv4 uplink packets/bytes: 0/0
IPv4 downlink packets/bytes: 0/0
IPv6 uplink packets/bytes: 0/0
IPv6 downlink packets/bytes: 0/0
Accounting state: Accounting
Session timeout: -
Time remained: -
Traffic quota: -
Traffic remained: -
Denied state: Not denied
