- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 03-MAC Authentication Configuration | 122.85 KB |
Table of Contents
1 MAC Authentication Configuration
RADIUS-Based MAC Authentication
Configuring MAC Authentication
Displaying and Maintaining MAC Authentication
MAC Authentication Configuration Examples
Local MAC Authentication Configuration Example
RADIUS-Based MAC Authentication Configuration Example
ACL Assignment Configuration Example
When configuring MAC authentication, go to these sections for information you are interested in:
l Configuring MAC Authentication
l Displaying and Maintaining MAC Authentication
l MAC Authentication Configuration Examples
MAC Authentication Overview
MAC authentication provides a way for authenticating users based on ports and MAC addresses. Once detecting a new MAC address, the device initiates the authentication process. MAC authentication requires neither client software to be installed on the hosts, nor any username or password to be entered by users during authentication.
Currently, the device supports two MAC authentication modes: Remote Authentication Dial-In User Service (RADIUS) based MAC authentication and local MAC authentication. For detailed information about RADIUS authentication and local authentication, refer to AAA Configuration of the Security Volume.
MAC authentication supports two types of usernames:
l MAC address, where the MAC address of a user serves as both the username and password.
l Fixed username, where all users use the same preconfigured username and password for authentication, regardless of the MAC addresses.
RADIUS-Based MAC Authentication
In RADIUS-based MAC authentication, the device serves as a RADIUS client and requires a RADIUS server to cooperate with it.
l If the type of username is MAC address, the device forwards a detected MAC address as the username and password to the RADIUS server for authentication of the user.
l If the type of username is fixed username, the device sends the same username and password configured locally to the RADIUS server for authentication of each user.
If the authentication succeeds, the user will be granted permission to access the network resources.
Local MAC Authentication
In local MAC authentication, the device performs authentication of users locally and different items need to be manually configured for users on the device according to the specified type of username:
l If the type of username is MAC address, a local user must be configured for each user on the device, using the MAC address of the accessing user as both the username and password.
l If the type of username is fixed username, a single username and optionally a single password are required for the device to authenticate all users.
Related Concepts
MAC Authentication Timers
The following timers function in the process of MAC authentication:
l Offline detect timer: At this interval, the device checks to see whether there is traffic from a user. Once detecting that there is no traffic from a user within this interval, the device logs the user out and sends to the RADIUS server a stop accounting request.
l Quiet timer: Whenever a user fails MAC authentication, the device does not perform MAC authentication of the user during such a period.
l Server timeout timer: During authentication of a user, if the device receives no response from the RADIUS server in this period, it assumes that its connection to the RADIUS server has timed out and forbids the user to access the network.
Quiet MAC Address
When a user fails MAC authentication, the MAC address becomes a quiet MAC address, which means that any packets from the MAC address will be discarded silently by the device until the quiet timer expires. This prevents the device from authenticating an illegal user repeatedly in a short time.
![]()
If a quiet MAC address is the same as a static MAC address configured or an MAC address that has passed another type of authentication, the quiet function does not take effect.
VLAN Assigning
For separation of users from restricted network resources, users and restricted resources are usually put into different VLANs. After a user passes identity authentication, the authorization server assigns to the user the VLAN where the restricted resources reside as an authorized VLAN, and the port through which the user accesses the device will be assigned to the authorized VLAN. As a result, the user can access those restricted network resources.
ACL Assigning
ACLs assigned by an authorization server are referred to as authorization ACLs, which are designed to control access to network resources. If the RADIUS server is configured with authorization ACLs, the device will permit or deny data flows traversing through the port through which a user accesses the device according to the authorization ACLs. You can change access rights of users by modifying authorization ACL settings on the RADIUS server.
Configuring MAC Authentication
Configuration Prerequisites
l Create and configure an ISP domain.
l For local authentication, create the local users and configure the passwords.
l For RADIUS authentication, ensure that a route is available between the device and the RADIUS server, and add the usernames and passwords on the server.
![]()
When adding usernames and passwords on the device or server, ensure that:
l The type of username and password must be consistent with that used for MAC authentication.
l All the letters in the MAC address to be used as the username and password must be in lower case.
l The service type of the local users must be configured as lan-access.
Configuration Procedure
Follow these steps to configure MAC authentication:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable MAC authentication globally |
mac-authentication |
Required Disabled by default |
|
Enable MAC authentication for specified ports |
mac-authentication interface interface-list |
Required Use either approach. Disabled by default |
|
interface interface-type interface-number mac-authentication quit |
||
|
Specify the ISP domain for MAC authentication |
mac-authentication domain isp-name |
Optional The default ISP domain is used by default. |
|
Set the offline detect timer |
mac-authentication timer offline-detect offline-detect-value |
Optional 300 seconds by default |
|
Set the quiet timer |
mac-authentication timer quiet quiet-value |
Optional 60 seconds by default |
|
Set the server timeout timer |
mac-authentication timer server-timeout server-timeout-value |
Optional 100 seconds by default |
|
Configure the username and password for MAC authentication |
mac-authentication user-name-format { fixed [ account name ] [ password { cipher | simple } password ] | mac-address [ with-hyphen | without-hyphen ] } |
Optional By default, the user’s source MAC address serves as the username and password, without “-“ in the MAC address |
![]()
l You can configure MAC authentication for ports first. However, the configuration takes effect only after you enable MAC authentication globally.
l Enabling MAC authentication on a port is mutually exclusive with adding the port to an aggregation group and adding the port to a service loopback group.
l For details about the default ISP domain, refer to AAA Configuration in the Security Volume.
Displaying and Maintaining MAC Authentication
|
To do… |
Use the command… |
Remarks |
|
Display the global MAC authentication information or the MAC authentication information about specified ports |
display mac-authentication [ interface interface-list ] |
Available in any view |
|
Clear the MAC authentication statistics |
reset mac-authentication statistics [ interface interface-list ] |
Available in user view |
MAC Authentication Configuration Examples
Local MAC Authentication Configuration Example
Network requirements
As illustrated in Figure 1-1, a supplicant is connected to the device through port GigabitEthernet 2/0/1.
l Local MAC authentication is required on every port to control user access to the Internet.
l All users belong to domain aabbcc.net.
l Local users use their MAC addresses as the usernames and passwords for authentication.
l Set the offline detect timer to 180 seconds and the quiet timer to 3 minutes.
Network diagram
Figure 1-1 Network diagram for local MAC authentication
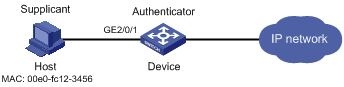
Configuration procedure
1) Configure MAC authentication on the device
# Add a local user, setting the username and password as 00-e0-fc-12-34-56, the MAC address of the user.
<Device> system-view
[Device] local-user 00-e0-fc-12-34-56
[Device-luser-00-e0-fc-12-34-56] password simple 00-e0-fc-12-34-56
[Device-luser-00-e0-fc-12-34-56] service-type lan-access
[Device-luser-00-e0-fc-12-34-56] quit
# Configure ISP domain aabbcc.net, and specify that the users in the domain use local authentication.
[Device] domain aabbcc.net
[Device-isp-aabbcc.net] authentication lan-access local
[Device-isp-aabbcc.net] quit
# Enable MAC authentication globally.
[Device] mac-authentication
# Enable MAC authentication for port GigabitEthernet 2/0/1.
[Device] mac-authentication interface GigabitEthernet 2/0/1
# Specify the ISP domain for MAC authentication.
[Device] mac-authentication domain aabbcc.net
# Set the MAC authentication timers.
[Device] mac-authentication timer offline-detect 180
[Device] mac-authentication timer quiet 180
# Specify MAC authentication username format.
[Device] mac-authentication user-name-format mac-address with-hyphen
2) Verify the configuration
# Display global MAC authentication information.
<Device> display mac-authentication
MAC address authentication is enabled.
User name format is MAC address, like xx-xx-xx-xx-xx-xx
Fixed username:mac
Fixed password:not configured
Offline detect period is 180s
Quiet period is 180s.
Server response timeout value is 100s
The max allowed user number is 2048 per slot
Current user number amounts to 1
Current domain is aabbcc.net
Silent Mac User info:
MAC Addr From Port Port Index
GigabitEthernet2/0/1 is link-up
MAC address authentication is enabled
Authenticate success: 1, failed: 0
Current online user number is 1
MAC Addr Authenticate state AuthIndex
00e0-fc12-3456 MAC_AUTHENTICATOR_SUCCESS 29
RADIUS-Based MAC Authentication Configuration Example
Network requirements
As illustrated in Figure 1-2, a host is connected to the device through port GigabitEthernet 2/0/1. The device authenticates, authorizes and keeps accounting on the host through the RADIUS server.
l MAC authentication is required on every port to control user access to the Internet.
l Set the offline detect timer to 180 seconds and the quiet timer to 3 minutes.
l All users belong to ISP domain 2000.
l The username type of fixed username is used for authentication, with the username being aaa and password being 123456.
Network diagram
Figure 1-2 Network diagram for MAC authentication using RADIUS
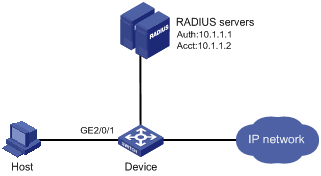
Configuration procedure
![]()
It is required that the RADIUS server and the device are reachable to each other and the username and password are configured on the server.
1) Configure MAC authentication on the device
# Configure a RADIUS scheme.
<Device> system-view
[Device] radius scheme 2000
[Device-radius-2000] primary authentication 10.1.1.1 1812
[Device-radius-2000] primary accounting 10.1.1.2 1813
[Device-radius-2000] key authentication abc
[Device-radius-2000] key accounting abc
[Device-radius-2000] user-name-format without-domain
[Device-radius-2000] quit
# Specify the AAA schemes for the ISP domain.
[Device] domain 2000
[Device-isp-2000] authentication default radius-scheme 2000
[Device-isp-2000] authorization default radius-scheme 2000
[Device-isp-2000] accounting default radius-scheme 2000
[Device-isp-2000] quit
# Enable MAC authentication globally.
[Device] mac-authentication
# Enable MAC authentication for port GigabitEthernet 2/0/1.
[Device] mac-authentication interface GigabitEthernet 2/0/1
# Specify the ISP domain for MAC authentication.
[Device] mac-authentication domain 2000
# Set the MAC authentication timers.
[Device] mac-authentication timer offline-detect 180
[Device] mac-authentication timer quiet 180
# Specify to use the username type of fixed username for MAC authentication.
[Device] mac-authentication user-name-format fixed account aaa password simple 123456
2) Verify the configuration
# Display global MAC authentication information.
<Device> display mac-authentication
MAC address authentication is enabled.
User name format is fixed account
Fixed username:aaa
Fixed password:123456
Offline detect period is 180s
Quiet period is 180s.
Server response timeout value is 100s
The max allowed user number is 2048 per slot
Current user number amounts to 1
Current domain is 2000
Silent Mac User info:
MAC Addr From Port Port Index
GigabitEthernet2/0/1 is link-up
MAC address authentication is enabled
Authenticate success: 1, failed: 0
Current online user number is 1
MAC Addr Authenticate state AuthIndex
00e0-fc12-3456 MAC_AUTHENTICATOR_SUCCESS 29
ACL Assignment Configuration Example
Network requirements
As shown in Figure 1-3, a host is connected to port GigabitEthernet 2/0/1 of the switch and must pass MAC authentication to access the Internet.
l Specify to use the MAC address of a user as the username and password for MAC authentication of the user.
l Configure the RADIUS server to assign ACL 3000.
l On port GigabitEthernet 2/0/1 of the switch, enable MAC authentication and configure ACL 3000.
After the host passes MAC authentication, the RADIUS server assigns ACL 3000 to port GigabitEthernet 2/0/1 of the switch. As a result, the host can access the Internet but cannot access the FTP server, whose IP address is 10.0.0.1.
Network diagram
Figure 1-3 Network diagram for ACL assignment
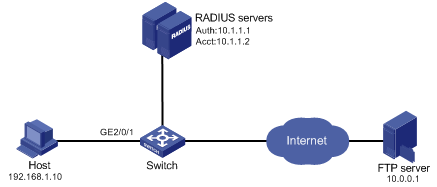
Configuration procedure
![]()
l Make sure that there is a route available between the RADIUS server and the switch.
l In this example, the switch uses the default username type (user MAC address) for MAC authentication. Therefore, you need to add the username and password of each user on the RADIUS server correctly.
l You need to configure the RADIUS server to assign ACL 3000 as the authorization ACL.
# Configure the RADIUS scheme.
<Switch> system-view
[Switch] radius scheme 2000
[Switch-radius-2000] primary authentication 10.1.1.1 1812
[Switch-radius-2000] primary accounting 10.1.1.2 1813
[Switch-radius-2000] key authentication abc
[Switch-radius-2000] key accounting abc
[Switch-radius-2000] user-name-format without-domain
[Switch-radius-2000] quit
# Create an ISP domain and specify the AAA schemes.
[Switch] domain 2000
[Switch-isp-2000] authentication default radius-scheme 2000
[Switch-isp-2000] authorization default radius-scheme 2000
[Switch-isp-2000] accounting default radius-scheme 2000
[Switch-isp-2000] quit
# Configure ACL 3000 to deny packets destined for 10.0.0.1.
[Switch] acl number 3000
[Switch-acl-adv-3000] rule 0 deny ip destination 10.0.0.1 0
[Switch-acl-adv-3000] quit
# Enable MAC authentication globally.
[Switch] mac-authentication
# Specify the ISP domain for MAC authentication users.
[Switch] mac-authentication domain 2000
# Specify the MAC authentication username type as MAC address, that is, using the MAC address of a user as the username and password for MAC authentication of the user.
[Switch] mac-authentication user-name-format mac-address
# Enable MAC authentication for port GigabitEthernet 2/0/1.
[Switch] interface GigabitEthernet 2/0/1
[Switch-GigabitEthernet2/0/1] mac-authentication
After completing the above configurations, you can use the ping command to verify whether the ACL 3000 assigned by the RADIUS server functions.
[Switch] ping 10.0.0.1
PING 10.0.0.1: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
--- 10.0.0.1 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss

