- Table of Contents
-
- H3C S3600 Series Ethernet Switches Operation Manual-Release 1510(V1.04)
- 00-1Cover
- 00-2Product Overview
- 01-CLI Operation
- 02-Login Operation
- 03-Configuration File Management Operation
- 04-VLAN Operation
- 05-IP Address and Performance Configuration Operation
- 06-Management VLAN Operation
- 07-Voice VLAN Operation
- 08-GVRP Operation
- 09-Port Basic Configuration Operation
- 10-Link Aggregation Operation
- 11-Port Isolation Operation
- 12-Port Security-Port Binding Operation
- 13-DLDP Operation
- 14-MAC Address Table Operation
- 15-Auto Detect Operation
- 16-MSTP Operation
- 17-Routing Protocol Operation
- 18-Multicast Operation
- 19-802.1x Operation
- 20-AAA-RADIUS-HWTACACS-EAD Operation
- 21-VRRP Operation
- 22-Centralized MAC Address Authentication Operation
- 23-ARP Operation
- 24-DHCP Operation
- 25-ACL Operation
- 26-QoS-QoS Profile Operation
- 27-Web Cache Redirection Operation
- 28-Mirroring Operation
- 29-IRF Fabric Operation
- 30-Cluster Operation
- 31-PoE-PoE Profile Operation
- 32-UDP Helper Operation
- 33-SNMP-RMON Operation
- 34-NTP Operation
- 35-SSH Terminal Service Operation
- 36-File System Management Operation
- 37-FTP and TFTP Operation
- 38-Information Center Operation
- 39-System Maintenance and Debugging Operation
- 40-VLAN-VPN Operation
- 41-HWPing Operation
- 42-DNS Operation
- 43-Access Management Operation
- 44-Appendix
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 35-SSH Terminal Service Operation | 5 MB |
Chapter 1 SSH Terminal Service
1.1.2 SSH Server Configuration
1.1.3 Configuring the SSH Client
1.1.4 Configuring the Device as an SSH Client
1.1.5 Displaying SSH Configuration
1.1.6 SSH Server Configuration Example
1.1.7 SSH Client Configuration Example
2.1.2 SFTP Server Configuration
2.1.3 SFTP Client Configuration
2.1.4 SFTP Configuration Example
Chapter 1 SSH Terminal Service
1.1 SSH Terminal Service
1.1.1 Introduction to SSH
Secure shell (SSH) provides secure communication and powerful authentication for remote user login to a switch over an insecure network, thus preventing assaults such as IP address spoofing, plain-text password interception.
Acting as an SSH server, a switch allows for the connections of multiple SSH clients. Through SSH Client, a user can establish a connection to a switch or UNIX host running SSH Server.
Figure 1-1 and Figure 1-2 shows two ways to establish SSH connection between client and server.
l Establishing SSH connection through a LAN

Figure 1-1 Establish SSH connection through a LAN
l Establishing SSH connection through a WAN

Figure 1-2 Establish SSH connection through a WAN
& Note:
At present, the device supports two SSH versions: SSH2 and SSH1. Unless otherwise noted, SSH refers to SSH2 throughout this document.
The communication process between a SSH client and server goes through the following five stages.
1) Version negotiation stage:
l The client sends a TCP connection request to the server.
l When a TCP connection is established, the two ends begin to negotiate an SSH version.
l If they get a successful negotiation, they go to the key negotiation stage. Otherwise the server terminates the TCP connection.
2) Key and algorithm negotiation stage:
l The server and the client send key algorithm negotiation packets to each other, which include the supported server-side public key algorithm list, encryption algorithm list, MAC algorithm list, and compression algorithm list.
l Based on the received algorithm negotiation packets, the server and the client figure out the algorithms to be used.
l The server and the client use the DH key exchange algorithm and parameters such as the host key pair to generate the session key and session ID.
Through the above steps, the server and the client get the same session key, which is to be used to encrypt and decrypt data exchanged between the server and the client later. The server and the client use session ID in the authentication stage.
3) Authentication negotiation stage:
l The client sends its username information to the server.
l The server starts to authenticate the user. If the user is configured as having no authentication on the server, the following step is skipped and the session request stage starts directly.
l The server authenticates the user in some way (see the following note), till the authentication succeeds or the connection is terminated due to authentication timeout.
& Note:
SSH provides two kinds of authentication: password authentication and RSA authentication.
(1) Password authentication works as follows:
l The client sends the username and password to the server.
l The server compares the received username and password against those configured locally. The user passes the authentication if the server finds a match for both username and password.
(2) RSA authentication works as follows:
l Configure the RSA public key of the client at the server.
l The client sends the member module of its RSA public key to the server.
l The server checks the validity of the member module. If it is valid, the server generates a random number, which is sent to the client after being encrypted with RSA public key of the client.
l Both the server and the client calculate authentication data by using the random number and session ID.
l The client sends the authentication data it calculates to the server.
l The server compares the received authentication data with the authentication data on itself. If they are identical, the authentication succeeds.
4) Session request stage. The client sends a session request to the server, which processes the request and establish a session.
5) Interactive session stage. Both ends exchange data till the session ends.
1.1.2 SSH Server Configuration
The following table describes SSH Server configuration tasks.
Table 1-1 SSH2.0 Server configuration tasks
|
Operation |
Command |
Related section |
|
Configure user interface(s) to support specified protocol(s) |
protocol inbound |
Section “Configuring user interface(s) to support specified protocol(s)" |
|
Generate local RSA key pairs |
rsa local-key-pair create |
|
|
Destroy local RSA key pairs |
rsa local-key-pair destroy |
|
|
Create an SSH user |
ssh user username |
Section “Create an SSH user” |
|
Specify a default authentication type for SSH users |
ssh authentication-type default |
|
|
Configure authentication type for an SSH user |
ssh user username authentication-type |
|
|
Set SSH authentication timeout time |
ssh server timeout |
Section “Configuring SSH management |
|
Set SSH authentication retry times |
ssh server authentication-retries |
|
|
Set server key update interval |
ssh server rekey-interval |
|
|
Configure SSH server to be compatible with SSH1.x clients |
ssh server compatible-ssh1x enable |
|
|
Configure a client public key for an SSH user |
ssh user username assign rsa-key keyname |
I. Configuring user interface(s) to support specified protocol(s)
Table 1-2 Configure user interface(s) to support specified protocol(s)
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Enter the view of one or multiple user interfaces |
user-interface [ type-keyword ] number [ ending-number ] |
Required |
|
Set the login authentication method |
authentication-mode scheme [ command-authorization ] |
Required |
|
Configure the user interface(s) to support specified protocol(s) |
protocol inbound { all |ssh | telnet } |
Optional By default, both Telnet and SSH are supported. |
![]() Caution:
Caution:
l If you have configured a user interface to support SSH protocol, to ensure a successful login to the user interface, you must configure AAA authentication for the user interface by using the authentication-mode scheme command.
l For a user interface, if you have executed the authentication-mode password or authentication-mode none command, the protocol inbound ssh command cannot be executed; if you have executed the protocol inbound ssh command, neither of the authentication-mode password and authentication-mode none commands can be executed.
II. Generating or destroying local RSA key pairs
This configuration task is used to generate or destroy the server's RSA key pairs, which are named in the format of switch name plus "_Host", and switch name plus "_Server", for example, H3C_Host and H3C_Server.
After you issue the rsa local-key-pair create command, the system prompts you to input a key length.
l In SSH1.x, the key length is in the range of 512 to 2,048 (bits).
l In SSH2.0, the key length is in the range of 1024 to 2048 (bits). To keep compatible with SSH1.x, SSH2.0 allows client keys to be 512 to 2,048 bits in length. But the server's key length must not be shorter than 1,024 bits; otherwise, clients cannot be authenticated.
Table 1-3 Generate or destroy local RSA key pairs
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Generate local RSA key pairs |
rsa local-key-pair create |
Required |
|
Destroy local RSA key pairs |
rsa local-key-pair destroy |
Optional |
![]() Caution:
Caution:
l For a successful SSH login, you must first generate the RSA key pairs of the server.
l You just need to execute the rsa local-key-pair create command once, and need not execute the command again after the system is rebooted.
l If you re-execute the rsa local-key-pair create command, the system will ask whether you want to replace the original key pairs with new ones.
l For a fabric made up of multiple devices, you need to execute the rsa local-key-pair create command on the management device to ensure that all devices in the fabric have the same local RSA key pairs.
& Note:
After the rsa local-key-pair create command is executed, you can execute the display rsa local-key-pair public command, which will display:
l Two public keys (in H3C_Host and H3C_Server) if the switch works in SSH1.x-compatible mode.
l Only one public key (in H3C_Host) if the switch works in SSH2.0 mode.
III. Create an SSH user
Table 1-4 Create an SSH user
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Create an SSH user |
ssh user username |
Required |
For an SSH user created by using this command, if you do not specify an authentication type by using the ssh user authentication-type command for this user, this SSH user adopts the default authentication type. On the other hand, if the default authentication type is not specified, you need to specify an authentication type for this SSH user.
IV. Configuring authentication type for a user
For a new user, you must specify the authentication type. Otherwise, the user cannot access the switch.
Table 1-5 Configure authentication type for a user
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Specify a default authentication type for SSH users |
ssh authentication-type default { password | rsa | password-publickey | all } |
At least one required; By default, no authentication type is specified for an SSH user, and the user can not access the switch. |
|
Configure authentication type for an SSH user |
ssh user username authentication-type { password | password-publickey | rsa| all } |
Note that:
l The ssh authentication-type default command is used to configure the default authentication type for all SSH users.
l The ssh user username authentication-type command is used to configure an authentication type for a specific SSH user.
l When both commands are configured with different authentication types, for the specific user (user specified by the username argument), the authentication type specified by the ssh user username authentication-type command will take effect instead of that specified for all SSH users.
![]() Caution:
Caution:
l If RSA authentication type is configured for a user, the RSA public key of the client user must be configured on the switch.
l By default, no authentication type is specified for a new user, and the new user cannot access the switch.
l For the password-publickey authentication type: SSH1 client users can access the switch as long as they pass any of the two kinds of authentications. SSH2 client users can access the switch only when they pass both kinds of authentications.
l For the password authentication type, username should be consistent with the valid user name defined in AAA; for the RSA authentication type, username is the SSH local user name, so that there is no need to configure a local user in AAA.
l If the default authentication type for SSH users is password and local AAA authentication is adopted, you need not use the ssh user command to create an SSH user. Instead, you can use the local-user command to create a user name and its password and then set the service type of the user to SSH.
l If the default authentication type for SSH users is password and remote authentication (RADIUS authentication, for example) is adopted, you need not use the ssh user command to create an SSH user, because it is created on the remote server. And the user can use its username and password configured on the remote server to access the network.
l If you use the ssh user username authentication-type command to specify an authentication type for an inexistent SSH user, the system will create the SSH user automatically.
l If the RSA authentication type is specified, you can use the user privilege level command to set the level of the commands available to the SSH users logging into the server. Additionally, the command levels accessible to the users adopting RSA authentication are the same.
l If the password authentication type is specified, the command levels accessible to SSH users logging into the server are determined through AAA. In this case, the command level may vary with users.
V. Configuring SSH management
The configuration of SSH management includes the setting of authentication timeout time, authentication retry times, server key update interval, and SSH compatible mode. After the configuration, the SSH management function is able to prevent illegal activities such as malicious password guessing, thus ensure the security of SSH connections.
Table 1-6 Configure SSH management
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Set SSH authentication timeout time |
ssh server timeout seconds |
Optional By default, the timeout time is 60 seconds. |
|
Set SSH authentication retry times |
ssh server authentication-retries times |
Optional By default, the number of retry times is 3. |
|
Set server key update interval |
ssh server rekey-interval hours |
Optional By default, the system does not update server keys. |
|
Configure SSH server to be compatible with SSH1.x clients |
ssh server compatible-ssh1x enable |
Optional By default, SSH server is compatible with SSH1.x clients. |
VI. Configuring a client public key for a user
On the switch, you can configure a client public key (generated randomly on a client) for a client user. This configuration is not required for password authentication type.
There are two methods to configure a client public key for a user.
1) Manual configuration
First, perform the following operations on a client:
l Use the SSH1.5/2.0 client software to randomly generate a RSA key pair.
l Use the SSHKEY.exe program to transform the public key in the RSA key pair to PKCS (public-key cryptography standards) format.
Then, perform the following operations on the server:
Table 1-7 Configure client public key for a user
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Enter public key view |
rsa peer-public-key keyname |
Required |
|
Enter public key edit view to input a client public key |
public-key-code begin |
— |
|
Configure the client public key |
Enter the content of the public key |
Required When you input the key data, spaces are allowed between the characters you input (because the system can remove the spaces automatically); you can also press <Enter> to continue your input at the next line. But the key you input should be a hexadecimal digit string coded in the public key format. |
|
Return to public key view from public key edit view |
public-key-code end |
The system saves the public key data you input when exiting public key edit view. |
|
Return to system view from public key view |
peer-public-key end |
— |
|
Assign a client public key to an SSH user |
ssh user username assign rsa-key keyname |
Required Keyname is the name of an existing public key. If the user has already been assigned with a public key, the newly assigned public key overwrites the old one. |
& Note:
l The above method requires you to transform the format of the public key on the client, and then manually configure the transformed public key on the server. So, the method is relatively more complex.
l If you use the ssh user username assign rsa-key command to assign an public key for an inexistent SSH user, the system will create the SSH user automatically.
l When configuring the public key for a client manually, you can copy the local host public key configuration on the client and then paste it to the server.
2) Automatic configuration
First, perform the following operations on a client:
l Use the SSH1.5/2.0 client software to randomly generate a RSA key pair.
l Use FTP/TFTP to transfer the corresponding public key file to the Flash memory of the server.
Then, perform the following operations on the server:
Table 1-8 Automatic configuration
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Transform the format of the key in a client public key file and automatically configure a client public key on the server |
rsa peer-public-key keyname import sshkey filename |
filename must be consistent with the name of a public key file in the Flash memory. |
& Note:
The above method does not require you to manually configure a public key. So the method is relatively simple and is the recommended method.
VII. Specifying a source IP address/interface for the SSH server
You can perform the following configurations to specify a source IP address or a source interface for the SSH server, thus enhancing traffic manageability.
Table 1-9 Specify a source IP address/interface for the SSH server
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Specify a source IP address for the SSH server |
ssh-server source-ip ip-address |
Optional |
|
Specify a source interface for the SSH server |
ssh-server source-interface interface-type interface-number |
Optional |
1.1.3 Configuring the SSH Client
A variety of SSH client software are available, such as PuTTY and OpenSSH. For an SSH client to establish a connection with an SSH server, you must complete these configuration tasks:
l Specifying the IP address of the server.
l Selecting the protocol for remote connection as SSH. Usually, a client can use a variety of remote connection protocols, such as Telnet, Rlogin, and SSH. To establish an SSH connection, you must select SSH.
l Selecting the SSH version. Since the device supports SSH Server 2.0 now, select 2.0 or lower for the client.
l Specifying the RSA private key file. On the server, if RSA authentication is enabled for an SSH user and a public key is set for the user, the private key file corresponding to the public key must be specified on the client. RSA key pairs are generated by a tool of the client software.
The following takes the client software of PuTTY, PuTTYGen and SSHKEY as examples to illustrate how to configure the SSH client:
I. Generating the Client Keys
To generate the client key pair, run PuTTYGen.exe, choose SSH-2 RSA under Parameters and click Generate.
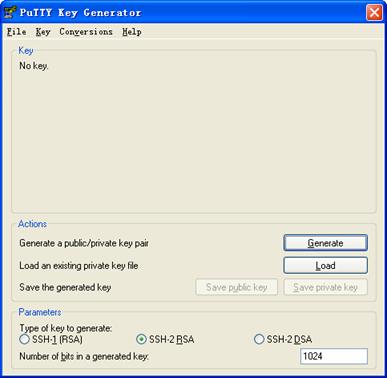
Figure 1-3 Generating the client keys (1)
Note that while generating the key pair, you must move the mouse continuously and keep the mouse off the green process bar in the blue box of shown in Figure 1-4. Otherwise, the process bar stops moving and the key pair generating process is stopped.
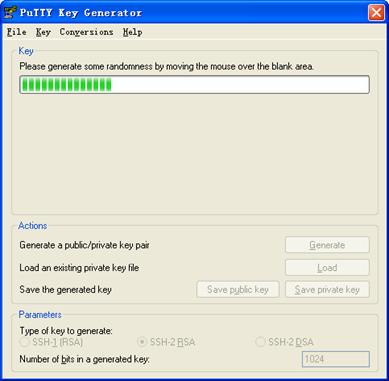
Figure 1-4 Generating the client keys (2)
After the key pair is generated, click Save public key and enter the name of the file for saving the public key (public in this case) to save the public key.
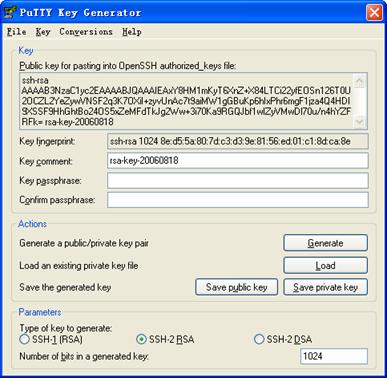
Figure 1-5 Generating the client keys (3)
Likewise, to save the private key, click Save private key. A warning window pops up to prompt you whether to save the private key without any precaution. Click Yes and enter the name of the file for saving the public key (private in this case) to save the private key.
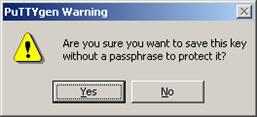
Figure 1-6 Generating the client keys (4)
To generate RSA public key in PKCS format, run SSHKEY.exe, click Browse and select the public key file, and then click Convert.
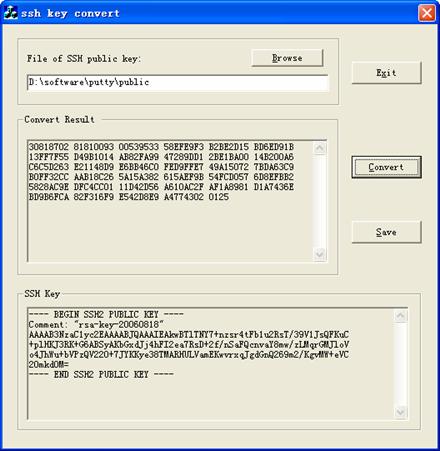
Figure 1-7 Generating the client keys (5)
II. Specifying the IP address of the Server
Launch PuTTY.exe. The following window appears.
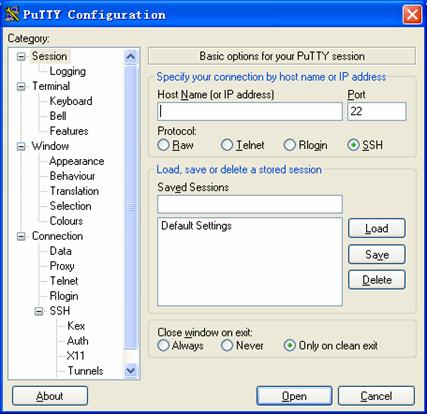
Figure 1-8 SSH client configuration interface 1
In the Host Name (or IP address) text box, enter the IP address of the server, Note that there must be a route available between the IP address of the server and the client.
III. Selecting the Protocol for Remote Connection
As shown in Figure 1-8, select SSH under Protocol.
IV. Selecting the SSH Version
From the category on the left pane of the window, select SSH under Connection. The window as shown in Figure 1-9 appears.
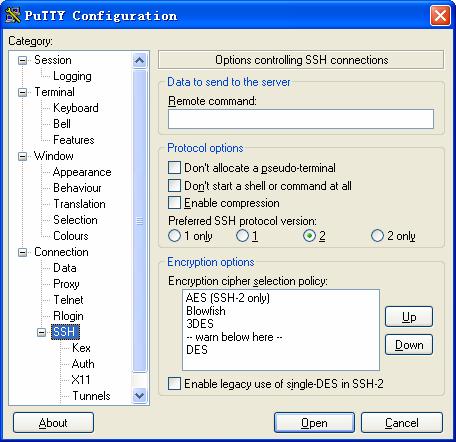
Figure 1-9 SSH client configuration interface 2
Under Protocol options, select 2 from Preferred SSH protocol version.
& Note:
Some SSH client software, for example, Tectia client software, supports the DES algorithm only when the ssh1 version is selected. The PuTTY client software supports DES algorithm negotiation ssh2.
V. Opening an SSH Connection with RSA
If the client needs to use RSA authentication, you must specify the RSA private key file. If the client needs to use password authentication, this is not required.
From the category on the left of the window, Select Connection/SSH/Auth. The following window appears.
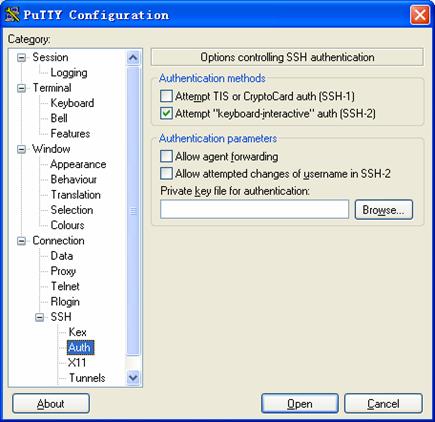
Figure 1-10 SSH client configuration interface 3
Click Browse… to bring up the file selection window, navigate to the private key file and click OK.
VI. Opening an SSH Connection with Password
1) From the window shown in Figure 1-10, click Open. The following SSH client interface appears. If the connection is normal, you will be prompted to enter the username and password, as shown in Figure 1-11.

Figure 1-11 SSH client interface
2) Enter the username and password to establish an SSH connection.
3) To log out, enter the quit command.
1.1.4 Configuring the Device as an SSH Client
When the device connects to the SSH server as an SSH client, you can configure the SSH client to authenticate the SSH server during the first access.
l The first authentication means that when the SSH client accesses the server for the first time and is not configured with the server host public key, the user can choose to continue accessing the server and save the host public key on the client for future authentication of the server.
l With first authentication not supported, the client cannot authenticate the server if it is not configured with the server host public key. In this case, you must configure the host public key of the server and specify the key name on the client beforehand, so that the client can authenticate the server.
You can configure the client to use a specified IP address or interface to access the SSH.
I. configure the device as an SSH client that supports first authentication
Table 1-10 Configure the device as an SSH client that supports first authentication
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Enable the client to run initial authentication |
ssh client first-time enable |
Optional By default, the client is enabled to run initial authentication. |
|
Start the client to establish a connection with an SSH server |
ssh2 { host-ip | host-name } [ port-num ] [ prefer_kex { dh_group1 | dh_exchange_group } | prefer_ctos_cipher { des | aes128 } | prefer_stoc_cipher { des | aes128 } | prefer_ctos_hmac { sha1 | sha1_96 | md5 | md5_96 } | prefer_stoc_hmac { sha1 | sha1_96 | md5 | md5_96 } ] * |
Required In this command, you can also specify the preferred key exchange algorithm, encryption algorithms and HMAC algorithms between the server and client. HMAC: Hash-based message authentication code |
II. configure the device as an SSH client that does not support first authentication
Table 1-11 Configure the device as an SSH client that does not support first authentication
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Disable the SSH client from performing first authentication for the SSH server to be accessed |
undo ssh client first-time |
Required By default, the SSH client performs first authentication. |
|
Enter public key view |
rsa peer-public-key keyname |
Optional |
|
Enter public key edit view |
public-key-code begin |
— |
|
Configure the public key for the server |
Input the public key directly |
— The input public key string can contain spaces and enters. The public key to be configured must be a hexadecimal string coded in the public format. |
|
Quit to public key view |
public-key-code end |
— The input public keys are saved when you quit the public key edit view. |
|
Quit to system view |
peer-public-key end |
— |
|
Specify the name of the host public key of the SSH server to be accessed on the SSH client |
ssh client { server-ip | server-name } assign rsa-key keyname |
Required |
|
Connect the SSH client to the SSH server, and specify the preferred key exchange algorithm, the preferred encryption algorithm and the preferred HMAC algorithm for the SSH client and the SSH server |
ssh2 { host-ip | host-name } [ port-num ] [ prefer_kex { dh_group1 | dh_exchange_group } | prefer_ctos_cipher { des | aes128 } | prefer_stoc_cipher { des | aes128 } | prefer_ctos_hmac { sha1 | sha1_96 | md5 | md5_96 } | prefer_stoc_hmac { sha1 | sha1_96 | md5 | md5_96 } ] * |
Required |
III. Specifying a source IP address/interface for the SSH client
You can perform the following configuration to specify a source IP address or a source interface for the SSH2.0 client, thus enhancing traffic manageability.
Table 1-12 Specify a source IP address/interface for the SSH client
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Specify a source IP address for the SSH2.0 client. |
ssh2 source-ip ip-address |
Optional |
|
Specify a source interface for the SSH2.0 client |
ssh2 source-interface interface-type interface-number |
Optional |
1.1.5 Displaying SSH Configuration
After the above configuration, you can execute the display command in any view to display the configuration information and running status of SSH, so as to verify your configuration.
Table 1-13 Display SSH configuration
|
Operation |
Command |
Description |
|
Display host and server public keys |
display rsa local-key-pair public |
You can execute the display command in any view. |
|
Display client RSA public key(s) |
display rsa peer-public-key [ brief | name keyname ] |
|
|
Display SSH status and session information |
display ssh server { status | session } |
|
|
Display SSH user information |
display ssh user-information [ username ] |
|
|
Display the current source IP address or the IP address of the source interface specified for the SSH server. |
display ssh-server source-ip |
|
|
Display the mappings between host public keys and SSH servers saved on a client |
display ssh server-info |
|
|
Display the current source IP address specified for the SSH2.0 Client. |
display ssh2 source-ip |
1.1.6 SSH Server Configuration Example
I. Network requirements
As shown in Figure 1-12, The PC (SSH Client) running an SSH2.0-supported client software, establish a local connection with the switch (SSH Server) to ensure the security of data exchange.
II. Network diagram

Figure 1-12 Network diagram for SSH server configuration
III. Configuration procedure
The configuration procedure varies with login authentication modes. However, you must complete the following three configuration tasks before any configuration procedure.
<H3C> system-view
[H3C] rsa local-key-pair create
Then, you must create a VLAN interface on the switch and assign an IP address, which the SSH client will use as the destination for SSH connection.
[H3C] interface vlan-interface 1
[H3C-Vlan-interface1] ip address 192.168.0.1 255.255.255.0
[H3C-Vlan-interface1] quit
Finally, you must configure an IP address (192.168.0.2 in this case) for the SSH client. This IP address and that of the VLAN interface on the switch must be in the same network segment.
1) Set user authentication method.
Settings for the two authentication types are described respectively in the following:
l Password authentication
# Set AAA authentication on user interfaces.
[H3C] user-interface vty 0 4
[H3C-ui-vty0-4] authentication-mode scheme
# Configure the user interfaces to support SSH.
[H3C-ui-vty0-4] protocol inbound ssh
[H3C-ui-vty0-4] quit
# Set login protocol to SSH, specify commands of level 3, and authentication password to "abc" for user clinet001.
[H3C] local-user client001
[H3C-luser-client001] password simple abc
[H3C-luser-client001] service-type ssh level 3
[H3C-luser-client001] quit
[H3C] ssh user client001 authentication-type password
& Note:
You can use the default SSH authentication timeout time and authentication retry times. After the above settings, run the SSH2.0-supported client software on a host connected to the switch, and log into the switch with the username client001 and password "abc".
l RSA public key authentication
# Set AAA authentication on the user interfaces.
[H3C] user-interface vty 0 4
[H3C-ui-vty0-4] authentication-mode scheme
# Set the user interfaces to support SSH.
[H3C-ui-vty0-4] protocol inbound ssh
# Set the command level for the login users to 3.
[H3C-ui-vty0-4] user privilege level 3
[H3C-ui-vty0-4] quit
# Set login protocol to SSH and authentication type to RSA for user client001.
[H3C] ssh user client001 authentication-type rsa
At this time, the client supporting SSH2.0 will generate a random RSA key pair, including public key and private key. You need to add the RSA public key, a hexadecimal character string encoded by the SSHKEY.EXE software in accordance with the public key cryptography standards (PKCS), to the rsa peer-public-key on the specified SSH server in the following way.
# Configure the client public key on the server, with a key name of Switch001.
[H3C] rsa peer-public-key Switch001
[H3C-rsa-public-key] public-key-code begin
[H3C-rsa-key-code] 308186028180739A291ABDA704F5D93DC8FDF84C427463
[H3C-rsa-key-code] 1991C164B0DF178C55FA833591C7D47D5381D09CE82913
[H3C-rsa-key-code] D7EDF9C08511D83CA4ED2B30B809808EB0D1F52D045DE4
[H3C-rsa-key-code] 0861B74A0E135523CCD74CAC61F8E58C452B2F3F2DA0DC
[H3C-rsa-key-code] C48E3306367FE187BDD944018B3B69F3CBB0A573202C16
[H3C-rsa-key-code] BB2FC1ACF3EC8F828D55A36F1CDDC4BB45504F020125
[H3C-rsa-key-code] public-key-code end
[H3C-rsa-public-key] peer-public-key end
or
[H3C] rsa peer-public-key Switch001 import sshkey Switch001
# Specify a public key of Switch001 for user client001.
[H3C] ssh user client001 assign rsa-key Switch001
For the RSA authentication, you not only need to configure the IP address, protocol type, and protocol version of the SSH server, but also need to specify an RSA private key file (generated by the client software at random) on the client. After the SSH connection is established, enter the username as prompted to go into the configuration interface of the switch.
1.1.7 SSH Client Configuration Example
I. Network requirements
As shown in Figure 1-13:
l Switch A serves as an SSH client, with a user name of client001.
l Switch B serves as an SSH server, with an IP address of 10.165.87.136.
II. Network diagram

Figure 1-13 Network diagram for SSH client configuration
III. Configuration procedure
1) Configure SwitchB
# Create an RSA host key pair and server key pair
<H3C> system-view
[H3C] rsa local-key-pair create
# Create a VLAN interface and assign an IP address, which the SSH client will use as the destination for SSH connection.
[H3C] interface vlan-interface 1
[H3C-Vlan-interface1] ip address 10.165.87.136 255.255.255.0
[H3C-Vlan-interface1] quit
# Set the authentication method of the user interface to AAA for SSH client.
[H3C] user-interface vty 0 4
[H3C-ui-vty0-4] authentication-mode scheme
# Set the protocol that a remote user uses to login as SSH.
[H3C-ui-vty0-4] protocol inbound ssh
[H3C-ui-vty0-4] quit
# Set login protocol to SSH, specify commands of level 3, and authentication password to "abc" for user clinet001.
[H3C] local-user client001
[H3C-luser-client001] password simple abc
[H3C-luser-client001] service-type ssh level 3
[H3C-luser-client001] quit
# Set the SSH authentication method to password. The SSH authentication timeout period, number of SSH authentication attempts and server key pair update interval can be the default values.
[H3C] ssh user client001 authentication-type password
& Note:
If you set the SSH authentication method to RSA, you need to configure a host public key of Switch A. For the specific configuration, refer to .1.1.6 SSH Server Configuration Example.
2) Configure SwitchA
# Configure an IP address (10.165.87.137 in this case) for the VLAN interface on SwitchA. This IP address and that of the VLAN interface on SwitchB must be in the same network segment.
<H3C> system-view
[H3C] interface vlan-interface 1
[H3C-Vlan-interface1] ip address 10.165.87.137 255.255.255.0
[H3C-Vlan-interface1] quit
# Establish an SSH connection to server 10.165.87.136.
[H3C] ssh2 10.165.87.136
Username: client001
Trying 10.165.87.136 ...
Press CTRL+K to abort
Connected to 10.165.87.136 ...
The Server is not authenticated. Do you continue to access it?(Y/N):y
Do you want to save the server's public key?(Y/N):n
Enter password:
*************************************************************************
* Copyright(c) 2004-2007 Hangzhou H3C Tech. Co., Ltd. All rights reserved.*
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
*************************************************************************
<H3C>
Chapter 2 SFTP Service
2.1 SFTP Service
2.1.1 Introduction to SFTP
Secure FTP (SFTP) is a new feature introduced in SSH2.0.
Since SFTP is based on SSH, it can provides security for remote users to log into the switch and perform file management and transfer operations (such as system update), thus providing more security for data transfer. Through the SFTP client function, you can securely log into a remote device and perform file transfer operations securely.
2.1.2 SFTP Server Configuration
The following sections describe SFTP Server configuration tasks:
l Configuring service type for an SSH user
l Setting connection idle timeout
I. Configuring service type for an SSH user
Table 2-1 Configure service type for an SSH user
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Configure service type for an SSH user |
ssh user username service-type { stelnet | sftp | all } |
Optional By default, the service type available for a user is stelnet. |
![]() Caution:
Caution:
If you use the ssh user username service-type command to specify a service type for an inexistent SSH user, the system will create the SSH user automatically.
II. Enabling SFTP Server
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
sftp server enable |
Required By default, SFTP Server is disabled. |
III. Setting connection idle timeout time
You can set the idle timeout time for SFTP connections, so that the system can automatically release a user connection when the user connection is idle for a time longer than the time threshold you set.
Table 2-3 Set connection idle timeout time
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Set idle timeout time for SFTP connections |
sftp timeout time-out-value |
Required By default, the connection idle timeout time is 10 minutes. |
2.1.3 SFTP Client Configuration
The following table describes SFTP Client configuration tasks:
Table 2-4 SFTP Client configuration tasks
|
Operation |
Command Keyword |
View |
Description |
|
|
Start SFTP Client |
sftp |
System view |
Required |
|
|
Stop SFTP Client |
bye |
SFTP client view |
Optional |
|
|
exit |
||||
|
quit |
||||
|
SFTP directory operations |
Change the current directory |
cd |
SFTP client view |
Optional |
|
Return to the upper directory |
cdup |
|||
|
Display the current directory |
pwd |
|||
|
Display the file list in a directory |
dir |
|||
|
ls |
||||
|
Create a new directory |
mkdir |
|||
|
Delete a directory |
rmdir |
|||
|
SFTP file operations |
Rename a file on the remote SFTP server |
rename |
SFTP client view |
Optional |
|
Download a file from the remote SFTP server |
get |
|||
|
Upload a local file to the remote SFTP server |
put |
|||
|
Display the file list in a directory |
dir |
|||
|
ls |
||||
|
Delete a file from the SFTP server |
delete |
|||
|
remove |
||||
|
Get help information about SFTP client commands |
help |
SFTP client view |
Optional |
|
I. Starting SFTP Client
You can start SFTP Client to establish a connection to a remote SFTP server and enter STP client view.
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Start SFTP Client |
sftp { host-ip | host-name } [ port-num ] [ prefer_kex { dh_group1 | dh_exchange_group } | prefer_ctos_cipher { des | aes128 } | prefer_stoc_cipher { des | aes128 } | prefer_ctos_hmac { sha1 | sha1_96 | md5 | md5_96 } | prefer_stoc_hmac { sha1 | sha1_96 | md5 | md5_96 } ] * |
Required |
II. Stopping SFTP Client
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Enter SFTP client view |
sftp { host-ip | host-name } |
— |
|
Stop SFTP Client |
bye |
The three commands have the same function. |
|
exit |
||
|
quit |
III. Performing SFTP directory operations
SFTP directory operations include: changing or displaying the current directory, creating or deleting a directory, displaying file or directory information in a specific directory.
Table 2-7 Perform SFTP directory operation
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Enter SFTP client view |
sftp { host-ip | host-name } |
— |
|
Change the current directory |
cd remote-path |
Optional |
|
Return to the upper directory |
cdup |
|
|
Display the current directory |
pwd |
|
|
Display the file list of a directory |
dir [ -a | -l ] [ remote-path ] |
Optional The dir and ls commands have the same function. |
|
ls [ -a | -l ] [ remote-path ] |
||
|
Create a directory on the SFTP server |
mkdir remote-path |
Optional |
|
Delete a directory from the SFTP server |
rmdir remote-path&<1-10> |
IV. Performing SFTP file operations
SFTP file operations include: renaming a file, downloading a file, uploading a file, displaying the file list, and deleting a file.
Table 2-8 Performing SFTP file operations
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
Optional |
|
Enter SFTP client view |
sftp { host-ip | host-name } |
|
|
Rename a file on the remote SFTP server |
rename old-name new-name |
|
|
Download a file from the remote SFTP server |
get remote-file [ local-file ] |
|
|
Upload a file to the remote SFTP server |
put local-file [ remote-file ] |
|
|
Display the file list of a directory |
dir [ -a | -l ] [ remote-path ] |
Optional The dir and ls commands have the same function. |
|
ls [ -a | -l ] [ remote-path ] |
||
|
Delete a file from the SFTP server |
delete remote-file&<1-10> |
Optional The delete and remove commands have the same function. |
|
remove remote-file&<1-10> |
V. Displaying help information
You can use the command here to display help information (such as syntax and parameters) about an SFTP client command.
Table 2-9 Display help information about an SFTP client command
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Enter SFTP client view |
sftp { host-ip | host-name } |
— |
|
Display help information about one or all SFTP client commands |
help [ all | command-name ] |
Optional |
VI. Specifying a source IP address or source interface for the SFTP client
You can use the command here to specify a source IP address or source interface for the SFTP client, thus enhancing traffic manageability.
Table 2-10 Specify a source IP address/interface for the SFTP client
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Specify a source IP address for the SFTP client |
sftp source-ip ip-address |
Optional |
|
Specify a source interface for the SFTP client |
sftp source-interface interface-type interface-number |
Optional |
|
Display the current source IP address or the IP address of the source interface specified for the SFTP client |
display sftp source-ip |
Optional You can execute this command in any view. |
2.1.4 SFTP Configuration Example
I. Network requirements
As shown in Figure 2-1: an SSH connection is established between SwitchA and SwitchB. SwitchA, an SFTP client, uses the username client001 and password abc to login to SwitchB for file management and file transfer.
II. Network diagram

Figure 2-1 Network diagram for SFTP configuration
III. Configuration procedure
1) Configure Switch B (SFTP server)
<H3C>system-view
[H3C] rsa local-key-pair create
# Create a VLAN interface on SwitchB and assign an IP address, which the SSH client uses as the destination for SSH connection.
[H3C] interface vlan-interface 1
[H3C-Vlan-interface1] ip address 192.168.0.1 255.255.255.0
[H3C-Vlan-interface1] quit
# Set the authentication method on the user interface to AAA.
[H3C] user-interface vty 0 4
[H3C-ui-vty0-4] authentication-mode scheme
# Set the protocol that a remote user uses to login as SSH.
[H3C-ui-vty0-4] protocol inbound ssh
[H3C-ui-vty0-4] quit
# Create local user client001.
[H3C] local-user client001
[H3C-luser-client001] password simple abc
[H3C-luser-client001] service-type ssh
[H3C-luser-client001] quit
# Set the SSH authentication method to password. The SSH authentication timeout period, number of SSH authentication attempts and server key pair update interval can be default values.
[H3C] ssh user client001 authentication-type password
& Note:
If you set the SSH authentication method to RSA, you need to configure the host public key of SwitchA. For the specific configuration, refer to .SSH Server Configuration Example.
# Specify SFTP service for SSH user abc.
[H3C] ssh user client001 service-type sftp
# Enable SFTP Server.
[H3C] sftp server enable
2) Configure Switch A (SFTP client)
# Configure an IP address (192.168.0.2 in this case) for the VLAN interface on SwitchA. This IP address and that of the VLAN interface on SwitchB must be in the same network segment.
<H3C> system-view
[H3C] interface vlan-interface 1
[H3C-Vlan-interface1] ip address 192.168.0.2 255.255.255.0
[H3C-Vlan-interface1] quit
# Establish a connection to the remote SFTP server and enter SFTP client view.
[H3C] sftp 192.168.0.1
Input Username: client001
Trying 192.168.0.1 ...
Press CTRL+K to abort
Connected to 192.168.0.1 ...
The Server is not authenticated. Do you continue access it? [Y/N]:y
Do you want to save the server's public key? [Y/N]:n
Enter password:
sftp-client>
# Display the current directory on the SFTP server, delete file z and verify the operation.
sftp-client> dir
-rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg
-rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2
-rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey1
drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new
-rwxrwxrwx 1 noone nogroup 225 Sep 01 06:55 pub
-rwxrwxrwx 1 noone nogroup 0 Sep 01 08:00 z
sftp-client> delete z
The following files will be deleted:
flash:/z
Are you sure to delete it?(Y/N):y
This operation may take a long time.Please wait...
File successfully Removed
sftp-client> dir
-rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg
-rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2
-rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey1
drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new
-rwxrwxrwx 1 noone nogroup 225 Sep 01 06:55 pub
# Create directory new1 and verify the operation.
sftp-client> mkdir new1
New directory created
sftp-client> dir
-rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg
-rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2
-rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey1
drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new
-rwxrwxrwx 1 noone nogroup 225 Sep 01 06:55 pub
drwxrwxrwx 1 noone nogroup 0 Sep 02 06:30 new1
# Rename directory new1 to new2 and verify the operation.
sftp-client> rename new1 new2
File successfully renamed
sftp-client> dir
-rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg
-rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2
-rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey1
drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new
-rwxrwxrwx 1 noone nogroup 225 Sep 01 06:55 pub
drwxrwxrwx 1 noone nogroup 0 Sep 02 06:33 new2
# Download file pubkey2 and rename it to public.
sftp-client> get pubkey2 public
This operation may take a long time, please wait...
Remote file:flash:/pubkey2 ---> Local file: public..
Downloading file successfully ended
# Upload the file pu to the SFTP server and rename it to puk. Verify the operations.
sftp-client> put pu puk
This operation may take a long time, please wait...
Local file: pu ---> Remote file: flash:/puk
Uploading file successfully ended
sftp-client> dir
-rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg
-rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2
-rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey1
drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new
drwxrwxrwx 1 noone nogroup 0 Sep 02 06:33 new2
-rwxrwxrwx 1 noone nogroup 283 Sep 02 06:35 pub
-rwxrwxrwx 1 noone nogroup 283 Sep 02 06:36 puk
sftp-client>
# Stop SFTP Client.
sftp-client> quit
Bye
[H3C]

