- Table of Contents
-
- 02-Configuration Examples
- 01-H3C_AAA_Configuration_Examples
- 02-H3C_ACL_Configuration_Examples
- 03-H3C_ATM_Configuration_Examples
- 04-H3C_IGMP_Configuration_Examples
- 05-H3C_IP_Source_Guard_Configuration_Examples
- 06-H3C_Ethernet_OAM_Configuration_Examples
- 07-H3C_NQA_Configuration_Examples
- 08-H3C_QinQ_Configuration_Examples
- 09-H3C_OSPF_Configuration_Examples
- 10-H3C_MPLS_TE_Configuration_Examples
- 11-H3C_OpenFlow_Configuration_Examples
- 12-H3C_NAT_Configuration_Examples
- 13-H3C_RBAC_Configuration_Examples
- 14-H3C_IRF_Configuration_Examples
- 15-H3C_POS_Interface_Configuration_Examples
- 16-H3C_CPOS_Interface_Configuration_Examples
- 17-H3C_DHCP_Relay_Redundancy_Configuration_Examples
- 18-H3C_DLDP_Configuration_Examples
- 19-H3C_IS-IS_Configuration_Examples
- 20-H3C_MPLS_L3VPN_Configuration_Examples
- 21-H3C_SSH_Configuration_Examples
- 22-H3C_Login_Management_Configuration_Examples
- 23-H3C_SNMP_Configuration_Examples
- 24-H3C_Priority_Marking_and_Queue_Scheduling_Configuration_Examples
- 25-H3C_Multicast_VPN_Configuration_Examples
- 26-H3C_BGP_Configuration_Examples
- 27-H3C_HoVPN_Configuration_Examples
- 28-H3C_L2TP_Configuration_Examples
- 29-H3C_VRRP_Configuration_Examples
- 30-H3C_Traffic_Filtering_Configuration_Examples
- 31-H3C_Samplers_and_IPv4_NetStream_Configuration_Examples
- 32-H3C_Software_Upgrade_Examples
- 33-H3C_MPLS_L2VPN_Configuration_Examples
- 34-H3C_NetStream_Configuration_Examples
- 35-H3C_Policy-Based_Routing_Configuration_Examples
- 36-H3C_Traffic_Policing_Configuration_Examples
- 37-H3C_BFD_Configuration_Examples
- 38-H3C_OSPFv3_Configuration_Examples
- 39-H3C_VPLS_Configuration_Examples
- 40-H3C_GTS_and_Rate_Limiting_Configuration_Examples
- 41-H3C_IPv6_IS-IS_Configuration_Examples
- 42-H3C_MPLS OAM_Configuration_Examples
- 43-H3C_BGP_Route_Selection_Configuration_Examples
- 44-H3C_IS-IS_Route_Summarization_Configuration_Examples
- 45-H3C_SRv6 Configuration Examples
- 46-H3C_Attack_Protection_Configuration_Examples
- 47-H3C_OSPF_Multi-Process_Configuration_Examples
- 48-H3C_OSPF_with_Multi-Instance_Configuration_Examples
- 49-H3C_ARP_Attack_Protection_Configuration_Examples
- 50-H3C_DHCPv6_Server_and_DHCPv6_Prefix_Client_Configuration_Examples
- 51-CE1 Interface Connection Configuration Examples
- 52-GRE Tunnel Establishment Using OSPF Configuration Examples
- 53-GRE Tunnel Establishment Using Static Routes Configuration Examples
- 54-OSPF over IPsec for Overseas Branch Access Configuration Examples
- 55-General QoS Configuration Examples
- 56-QoS Configuration Examples for the Financial Industry
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 08-H3C_QinQ_Configuration_Examples | 121.43 KB |
Introduction
This document provides examples for using QinQ to transmit 802.1Q-tagged customer traffic in the service provider network.
A QinQ-enabled port tags all incoming frames (tagged or untagged) with the PVID tag.
The devices in the service provider network learn MAC addresses of CVLANs into the MAC address table of the SVLAN.
Prerequisites
The configuration examples in this document were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
This document assumes that you have basic knowledge of H3C QinQ, .
Example: Configuring QinQ
Network configuration
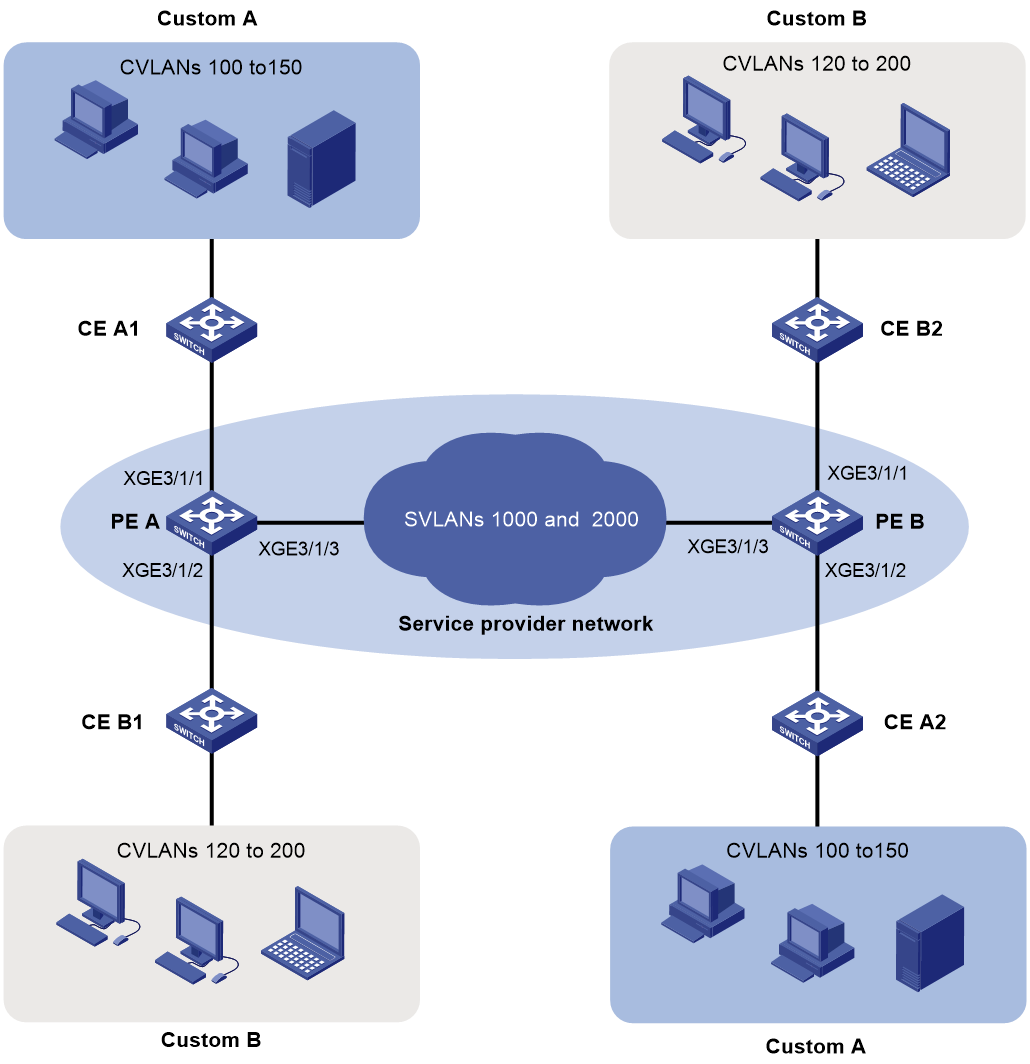
As shown in Figure 1:
· The service provider assigns VLAN 1000 to Company A's VLANs 100 through 150.
· The service provider assigns VLAN 2000 to Company B's VLANs 120 through 200.
Configure QinQ on PE A and PE B to transmit traffic in VLANs 1000 and 2000 for Company A and Company B, respectively.
Restrictions and guidelines
When you configure QinQ, follow these restrictions and guidelines:
· You only need to configure QinQ on customer-side ports of PEs.
· The link type of the customer-side port can be access, hybrid, or trunk.
¡ If the link type is access, you must assign the port to the SVLAN.
¡ If the link type is trunk, you must assign the port to the SVLAN, and set the SVLAN ID as the PVID of the port.
¡ If the link type is hybrid, you must assign the port to the SVLAN as an untagged VLAN member, and set the SVLAN ID as the PVID of the port. The settings ensure that the port can forward traffic to the customer site with the SVLAN tag removed.
· For QinQ frames to travel across the service provider network, you must perform the following tasks:
¡ Set the MTU to a minimum of 1504 bytes for each port on the path of QinQ frames. This value is the sum of the default Ethernet interface MTU (1500 bytes) and the length (4 bytes) of a CVLAN tag. The CVLAN tag of QinQ frames is treated as part of the payload during transmission.
¡ Configure all the ports on the forwarding path to allow frames from VLANs 1000 and 2000 to pass through without removing the VLAN tag.
Procedures
Configuring PE A
1. Create VLANs 1000 and 2000.
<PE_A> system-view
[PE_A] vlan 1000
[PE_A-vlan1000] quit
[PE_A] vlan 2000
[PE_A-vlan2000] quit
2. Configure Ten-GigabitEthernet 3/1/1:
# Configure the port as an access port, and assign the port to VLAN 1000.
[PE_A] interface ten-gigabitethernet 3/1/1
[PE_A-Ten-GigabitEthernet3/1/1] port link-mode bridge
[PE_A-Ten-GigabitEthernet3/1/1] port access vlan 1000
# Enable QinQ on the port.
[PE_A-Ten-GigabitEthernet3/1/1] qinq enable
[PE_A-Ten-GigabitEthernet3/1/1] quit
3. Configure Ten-GigabitEthernet 3/1/2:
# Configure the port as an access port, and assign the port to VLAN 2000.
[PE_A] interface ten-gigabitethernet 3/1/2
[PE_A-Ten-GigabitEthernet3/1/2] port link-mode bridge
[PE_A-Ten-GigabitEthernet3/1/2] port access vlan 2000
# Enable QinQ on the port.
[PE_A-Ten-GigabitEthernet3/1/2] qinq enable
[PE_A-Ten-GigabitEthernet3/1/2] quit
4. Configure Ten-GigabitEthernet 3/1/3:
# Configure the port as a trunk port.
[PE_A] interface ten-gigabitethernet 3/1/3
[PE_A-Ten-GigabitEthernet3/1/3] port link-mode bridge
[PE_A-Ten-GigabitEthernet3/1/3] port link-type trunk
# Assign the port to VLANs 1000 and 2000.
[PE_A-Ten-GigabitEthernet3/1/3] port trunk permit vlan 1000 2000
# Remove the port from VLAN 1.
[PE_A-Ten-GigabitEthernet3/1/3] undo port trunk permit vlan 1
Configuring PE B
# Configure PE B in the same way you configure PE A. (Details not shown.)
Configuring devices between PE A and PE B
# Set the MTU to a minimum of 1504 bytes for each port on the path of QinQ frames. (Details not shown.)
# Configure all ports on the forwarding path to allow frames from VLANs 1000 and 2000 to pass through without removing the VLAN tag. (Details not shown.)
Verifying the configuration
# Verify that each company's PCs can ping each other in the same CVLAN across the service provider network. (Details not shown.)
# Verify that the two companies' PCs cannot communicate at Layer 2 even if their CVLAN IDs are the same. The ARP tables on one company's PCs do not contain entries for MAC addresses of the other company's PCs. (Details not shown.)
Configuration files
PE A
#
vlan 1000
#
vlan 2000
#
interface ten-gigabitethernet 3/1/1
port link-mode bridge
port access vlan 1000
qinq enable
#
interface ten-gigabitethernet 3/1/2
port link-mode bridge
port access vlan 2000
qinq enable
#
interface ten-gigabitethernet 3/1/3
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 1000 2000
#
PE B
#
vlan 1000
#
vlan 2000
#
interface ten-gigabitethernet 3/1/1
port link-mode bridge
port access vlan 2000
qinq enable
#
interface ten-gigabitethernet 3/1/2
port link-mode bridge
port access vlan 1000
qinq enable
#
interface ten-gigabitethernet 3/1/3
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 1000 2000
#
Related documentation
· H3C SR8800-X Routers Layer 2—LAN Switching Command Reference
· H3C SR8800-X Routers Layer 2—LAN Switching Configuration Guide