- Table of Contents
-
- 10-Security
- 00-Preface
- 01-AAA configuration
- 02-802.1X configuration
- 03-802.1X client configuration
- 04-MAC authentication configuration
- 05-Portal configuration
- 06-User profile configuration
- 07-Password control configuration
- 08-Public key management
- 09-PKI configuration
- 10-IPsec configuration
- 11-SSH configuration
- 12-SSL configuration
- 13-Session management
- 14-Connection limit configuration
- 15-Attack detection and prevention configuration
- 16-IP source guard configuration
- 17-ARP attack protection configuration
- 18-ND attack defense configuration
- 19-User isolation configuration
- 20-ASPF configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 20-ASPF configuration | 170.17 KB |
Feature and hardware compatibility
Command and hardware compatibility
Applying an ASPF policy to an interface
Displaying and maintaining ASPF
ASPF FTP application inspection configuration example
ASPF TCP application inspection configuration example
Configuring ASPF
The term "firewall" in this document refers to access controllers and access controller modules.
Overview
Advanced Stateful Packet Filter (ASPF) is proposed to address the issues that a packet-filter firewall cannot solve. An ASPF provides the following main functions:
· Application layer protocol inspection—ASPF checks the application layer information of packets, such as the protocol type and port number, and inspects the application layer protocol status for each connection. ASPF maintains the status information of each connection, and based on the status information, determines whether to permit a packet to pass through the firewall into the internal network. In this way, ASPF defends the internal network against attacks.
· Transport layer protocol inspection (generic TCP and UDP inspection)—ASPF checks a TCP/UDP packet's source and destination addresses and port numbers to determine whether to permit the packet to pass through the firewall into the internal network.
· ICMP error message check—ASPF inspects the connection information carried in an ICMP error message. If the information does not match the connection, ASPF drops the packet.
· TCP SYN check—ASPF checks the first packet of a TCP connection to determine if it is a SYN packet. If it is not a SYN packet, ASPF drops the packet. When a device attached to the network starts up, it can receive a non-SYN packet of an existing TCP connection for the first time. If you do not want to interrupt the existing TCP connection, you can disable the TCP SYN check. The device allows the first non-SYN packet that is used to establish a TCP connection to pass. After the network topology becomes steady, you can enable TCP SYN check again.
At the border of a network, ASPF can work with a packet-filter firewall to provide the network with a more comprehensive security policy that better meets the actual needs. The packet-filter firewall permits or denies packets according to ACL rules. The ASPF records information about the permitted packets to ensure that their return packets can pass through the packet-filter firewall.
ASPF basic concepts
Single-channel protocol and multichannel protocol
· Single-channel protocol—A single-channel protocol establishes only one connection to exchange both control messages and data for a user. SMTP and HTTP are examples of single-channel protocols.
· Multichannel protocol—A multichannel protocol establishes more than one connection for a user and transfers control messages and user data through different connections. FTP is one example of multichannel protocols.
Internal interface and external interface
On an edge device configured with ASPF to protect hosts and servers on the internal network, the interfaces on the device are divided into internal interfaces and external interface:
· Internal interfaces—Interfaces connected to the internal network.
· External interfaces—Interfaces connected to the external network.
To protect the internal network, you can apply an ASPF in the outbound direction of the external interfaces or in the inbound direction of the internal interfaces of the device.
ASPF inspections
This section introduces the basic idea of ASPF inspection on application layer and transport layer protocols.
Application layer protocol inspection
As shown in Figure 1, ACLs on the edge device deny incoming packets to the internal network. The ASPF application layer protocol inspection allows return packets from the external network to the internal network.
Figure 1 Application layer protocol inspection
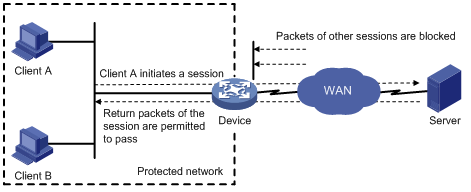
ASPF inspects all application layer sessions as follows:
· For a single-channel protocol, the inspection process is simple.
ASPF creates a session entry immediately after it detects the session's first packet sent to the external network, and ASPF removes the entry when the connection is terminated.
The session entry helps record outgoing packets and their return packets. It can maintain the session status and determine whether state transitions of the session are correct. All packets that match a session entry can pass through the packet-filter firewall.
· For a multichannel protocol, ASPF creates session entries, and one or more associated entries to associate the sessions initiated by the same application layer protocol. Associated entries are created during the protocol negotiation and are removed after the negotiation. ASPF uses the associated entries to match the first packets of the sessions. All packets of the sessions matching the associated entries can pass through the packet-filter firewall.
The following uses FTP to explain the process of multichannel application layer protocol inspection.
Figure 2 FTP inspection
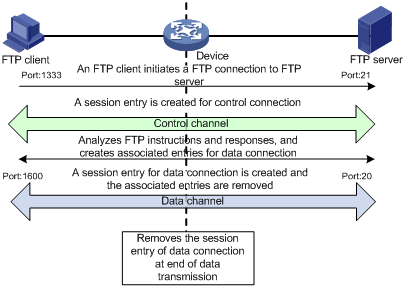
As shown in Figure 2, FTP connections are established and removed as follows:
1. The FTP client initiates an FTP control connection from port 1333 to port 21 of the FTP server.
2. As a result of negotiation, the server initiates a data connection from port 20 to port 1600 of the client.
3. When data transmission times out or ends, the data connection is removed.
ASPF implements FTP inspection during the FTP connection lifetime as follows:
1. ASPF checks the IP packets the FTP client sends to the FTP server to identify TCP-based FTP packets. Based on the port number, ASPF identifies the control connection between the FTP client and server and creates a control connection session entry.
2. ASPF checks each FTP control connection packet, and examines their TCP status based on the control connection session entry. ASPF analyzes the FTP instructions in the control connection packet. If the packet contains a data channel setup instruction, ASPF creates an associated entry for the data connection.
3. For return FTP control connection packets, ASPF examines their TCP status based on the control connection session entry to make packet forwarding decisions.
4. When the FTP data passes through the device, ASPF is triggered to create a session entry for the data connection and remove the associated entry.
5. For returned FTP data packets, ASPF examines their TCP status based on the data connection session entry to make packet forwarding decisions.
6. When the data transmission ends, ASPF removes the data connection session entry. When the FTP connection is removed, ASPF removes the control connection session entry.
Transport layer protocol inspection
Generic TCP/UDP inspection requires that return packets must match the corresponding packets that are previously sent out of the external interface. The return packets must have the same source/destination addresses and source/destination port numbers as the outgoing packets (but reversed). Otherwise, the return packets are blocked. For multichannel application layer protocols like FTP, the deployment of TCP inspection without application layer inspection leads to failure of establishing a data connection.
Compatibility information
Feature and hardware compatibility
|
Hardware series |
Model |
ASPF compatibility |
|
WX1800H series |
WX1804H WX1810H WX1820H |
Yes |
|
WX2500H series |
WX2510H WX2540H WX2560H |
Yes |
|
WX3000H series |
WX3010H WX3010H-L WX3010H-X WX3024H WX3024H-L |
No |
|
WX3500H series |
WX3508H WX3510H WX3520H WX3540H |
Yes |
|
WX5500E series |
WX5510E WX5540E |
Yes |
|
WX5500H series |
WX5540H WX5560H WX5580H |
Yes |
|
Access controller modules |
EWPXM1MAC0F EWPXM1WCME0 EWPXM2WCMD0F LSQM1WCMX20 LSQM1WCMX40 LSUM1WCME0 LSUM1WCMX20RT LSUM1WCMX40RT |
Yes |
Command and hardware compatibility
The WX1800H series and WX2500H series access controllers do not support the slot keyword or the slot-number argument.
ASPF configuration task list
|
Tasks at a glance |
|
(Required.) Configuring an ASPF policy |
|
(Required.) Applying an ASPF policy to an interface |
Configuring an ASPF policy
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an ASPF policy and enter its view. |
aspf-policy aspf-policy-number |
By default, no ASPF policies exist. |
|
3. (Optional.) Configure ASPF inspection for application layer protocols. |
detect { ftp | h323 | sccp | sip | gtp | ils | mgcp | nbt | pptp | rsh | rtsp | sqlnet | tftp | xdmcp } |
By default, ASPF inspection for application protocols is not configured. ASPF inspection for transport layer protocols is always enabled and is not configurable. |
|
4. (Optional.) Enable ICMP error message check. |
icmp-error drop |
By default, ICMP error message check is disabled. ASPF does not drop faked ICMP error messages. |
|
5. (Optional.) Enable TCP SYN check. |
tcp syn-check |
By default, TCP SYN check is disabled. ASPF does not drop the non-SYN packet when it is the first packet to establish a TCP connection. |
Applying an ASPF policy to an interface
You can apply an ASPF policy to inspect incoming or outgoing traffic on an interface. ASPF compares the packets against session entries. If a packet does not match any session entries, ASPF creates a new session entry.
You can apply both ASPF and packet filter to implement packet filtering. For example, you can apply a packet filtering policy to the inbound direction of the external interface and apply an ASPF policy to the outbound direction of the external interface. The application denies unsolicited access from the external network to the internal network and allows return packets from external to the internal network.
Check that a connection initiation packet and the corresponding return packet pass through the same interface, because an ASPF stores and maintains the application layer protocol status based on interfaces.
To apply an ASPF policy on an interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Apply an ASPF policy to the interface. |
aspf apply policy aspf-policy-number { inbound | outbound } |
By default, no ASPF policy is applied to the interface. |
Displaying and maintaining ASPF
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display the configuration of all ASPF policies and their applications. |
display aspf all |
|
Display ASPF policy applications on interfaces. |
display aspf interface |
|
Display the configuration of an ASPF policy. |
display aspf policy { aspf-policy-number | default } |
|
Display ASPF sessions. |
display aspf session [ ipv4 | ipv6 ] [ slot slot-number ] [ verbose ] |
|
Clear ASPF session statistics. |
ASPF configuration examples
ASPF FTP application inspection configuration example
Network requirements
Configure an ASPF policy on the AC to inspect the FTP traffic flows passing through the AC. Only return packets for FTP connections initiated by users on the internal network are permitted to pass through the AC and get into the internal network. All other types of packets from the external network to the internal network are blocked.
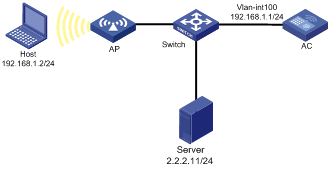
Configuration procedure
# Configure ACL 3111 to deny all IP packets.
<AC> system-view
[AC] acl advanced 3111
[AC-acl-ipv4-adv-3111] rule deny ip
[AC-acl-ipv4-adv-3111] quit
# Create ASPF policy 1 for FTP inspection.
[AC] aspf-policy 1
[AC-aspf-policy-1] detect ftp
[AC-aspf-policy-1] quit
# Apply ACL 3111 to deny all incoming IP packets on VLAN-interface 100.
[AC] interface vlan-interface 100
[AC-Vlan-interface100] packet-filter 3111 inbound
# Apply ASPF policy 1 to the outgoing traffic on VLAN-interface 100.
[AC-Vlan-interface100] aspf apply policy 1 outbound
Verifying the configuration
# Verify that an ASPF session has been established for the FTP connection between the host and the FTP server.
<AC> display aspf session ipv4
Initiator:
Source IP/port: 192.168.1.2/1877
Destination IP/port: 2.2.2.11/21
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Vlan-interface 100
Total sessions found: 1
# Verify that only the return packets of FTP connections can enter the internal network. (Details not shown.)
ASPF TCP application inspection configuration example
Network requirements
Local users on the internal network need to access the external network. To protect the internal network against ICMP and SYN packet attacks from the external network, configure an ASPF policy on the AC. The AC can then drop faked ICMP error messages and non-SYN packets that are the first packets over TCP connections.
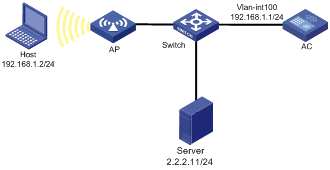
Configuration procedure
# Configure ACL 3111 to deny all IP packets.
<AC> system-view
[AC] acl advanced 3111
[AC-acl-ipv4-adv-3111] rule deny ip
[AC-acl-ipv4-adv-3111] quit
# Create ASPF policy 1.
[AC] aspf-policy 1
# Enable ICMP error message check.
[AC-aspf-policy-1] icmp-error drop
# Enable TCP SYN check.
[AC-aspf-policy-1] tcp syn-check
[AC-aspf-policy-1] quit
# Enable ASPF policy 1 to inspect FTP packets.
[AC-aspf-policy-1] detect ftp
# Apply ACL 3111 to deny all incoming IP packets on VLAN-interface 100.
[AC] interface Vlan-interface 100
[AC-Vlan-interface100] packet-filter 3111 inbound
# Apply ASPF policy 1 to outgoing traffic on interface VLAN-interface 100.
[AC-Vlan-interface100] aspf apply policy 1 outbound
Verifying the configuration
# Display the configuration of ASPF policy 1.
<AC> display aspf policy 1
ASPF policy configuration:
Policy number: 1
ICMP error message check: Enabled
TCP SYN packet check: Enabled
Inspected protocol
FTP
The AC can recognize faked ICMP error messages from external networks and drop the non-SYN packets that are the first packets to establish TCP connections.
