- Table of Contents
-
- 11-Security Configuration Guide
- 00-Preface
- 01-Security Overview
- 02-AAA Configuration
- 03-802.1X Configuration
- 04-MAC Authentication Configuration
- 05-Portal Configuration
- 06-Password Control Configuration
- 07-Public Key Configuration
- 08-IPsec Configuration
- 09-SSH Configuration
- 10-Blacklist Configuration
- 11-TCP and ICMP Attack Protection Configuration
- 12-IP Source Guard Configuration
- 13-ARP Attack Protection Configuration
- 14-ND Attack Defense Configuration
- 15-URPF Configuration
- 16-PKI Configuration
- 17-SSL Configuration
- 18-FIPS Configuration
- 19-Attack Detection and Protection Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 03-802.1X Configuration | 385.55 KB |
Contents
Controlled/uncontrolled port and port authorization status
Initiating 802.1X authentication
802.1X client as the initiator
Access device as the initiator
802.1X authentication procedures
Comparing EAP relay and EAP termination
Using 802.1X authentication with other features
802.1X configuration task list
Enabling EAP relay or EAP termination
Setting the port authorization state
Specifying an access control method
Setting the maximum number of concurrent 802.1X users on a port
Setting the maximum number of authentication request attempts
Setting the 802.1X authentication timeout timers
Configuring the online user handshake function
Configuring the authentication trigger function
Specifying a mandatory authentication domain on a port
Enabling the periodic online user re-authentication function
Configuring an 802.1X guest VLAN
Configuring an 802.1X Auth-Fail VLAN
Specifying supported domain name delimiters
Displaying and maintaining 802.1X
802.1X authentication configuration example
802.1X guest VLAN and VLAN assignment configuration example
802.1X is a port-based network access control protocol initially proposed by the IEEE 802 LAN/WAN committee for securing wireless LANs (WLANs), and it has also been widely used on Ethernet networks for access control.
802.1X controls network access by authenticating the devices connected to 802.1X-enabled LAN ports.
802.1X architecture
802.1X operates in the client/server model. It comprises three entities: the client (the supplicant), the network access device (the authenticator), and the authentication server.
Figure 1 802.1X architecture
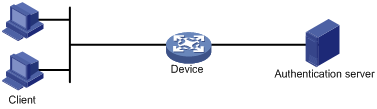
· The client—A user terminal seeking access to the LAN. It must have 802.1X software to authenticate to the network access device.
· The network access device—Authenticates the client to control access to the LAN. In a typical 802.1X environment, the network access device uses an authentication server to perform authentication.
· The authentication server—Provides authentication services for the network access device. The authentication server authenticates 802.1X clients by using the data sent from the network access device, and returns the authentication results for the network access device to make access decisions. The authentication server is typically a Remote Authentication Dial-in User Service (RADIUS) server. In a small LAN, you can also use the network access device as the authentication server.
Controlled/uncontrolled port and port authorization status
802.1X defines two logical ports for the network access port: controlled port and uncontrolled port. Any packet arriving at the network access port is visible to both logical ports.
· Controlled port—Allows incoming and outgoing traffic to pass through when it is in the authorized state, and denies incoming and outgoing traffic when it is in the unauthorized state, as shown in Figure 2. The controlled port is set in the authorized state if the client has passed authentication, and in the unauthorized state, if the client has failed authentication.
· Uncontrolled port—Always open to receive and transmit EAPOL frames.
Figure 2 Authorization state of a controlled port
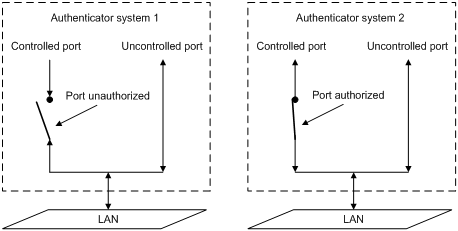
In unauthorized state, a controlled port controls traffic in one of the following ways:
· Performs bidirectional traffic control to deny traffic to and from the client.
· Performs unidirectional traffic control to deny traffic from the client.
The H3C devices support only unidirectional traffic control.
802.1X-related protocols
802.1X uses the Extensible Authentication Protocol (EAP) to transport authentication information for the client, the network access device, and the authentication server. EAP is an authentication framework that uses the client/server model. It supports a variety of authentication methods, including MD5-Challenge, EAP-Transport Layer Security (EAP-TLS), and Protected EAP (PEAP).
802.1X defines EAP over LAN (EAPOL) for passing EAP packets between the client and the network access device over a wired or wireless LAN. Between the network access device and the authentication server, 802.1X delivers authentication information in one of the following methods:
· Encapsulates EAP packets in RADIUS by using EAP over RADIUS (EAPOR), as described in "EAP relay."
· Extracts authentication information from the EAP packets and encapsulates the information in standard RADIUS packets, as described in "EAP termination."
Packet formats
EAP packet format
Figure 3 shows the EAP packet format.
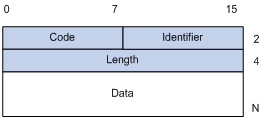
· Code—Type of the EAP packet. Options include Request (1), Response (2), Success (3), or Failure (4).
· Identifier—Used for matching Responses with Requests.
· Length—Length (in bytes) of the EAP packet. The length is the sum of the Code, Identifier, Length, and Data fields.
· Data—Content of the EAP packet. This field appears only in a Request or Response EAP packet. The Data field comprises the request type (or the response type) and the type data. Type 1 (Identify) and type 4 (MD5-challenge) are two examples for the type field.
EAPOL packet format
Figure 4 shows the EAPOL packet format.
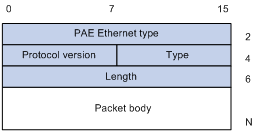
· PAE Ethernet type—Protocol type. It takes the value 0x888E for EAPOL.
· Protocol version—The EAPOL protocol version used by the EAPOL packet sender.
· Type—Type of the EAPOL packet. Table 1 lists the types of EAPOL packets supported by H3C implementation of 802.1X.
Table 1 Types of EAPOL packets
|
Value |
Type |
Description |
|
0x00 |
EAP-Packet |
The client and the network access device uses EAP-Packets to transport authentication information. |
|
0x01 |
EAPOL-Start |
The client sends an EAPOL-Start message to initiate 802.1X authentication to the network access device. |
|
0x02 |
EAPOL-Logoff |
The client sends an EAPOL-Logoff message to tell the network access device that it is logging off. |
· Length—Data length in bytes, or length of the Packet body. If packet type is EAPOL-Start or EAPOL-Logoff, this field is set to 0, and no Packet body field follows.
· Packet body—Content of the packet. When the EAPOL packet type is EAP-Packet, the Packet body field contains an EAP packet.
EAP over RADIUS
RADIUS adds two attributes, EAP-Message and Message-Authenticator, for supporting EAP authentication. For the RADIUS packet format, see "Configuring AAA."
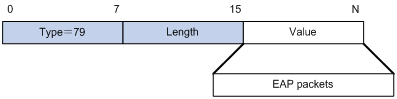
EAP-Message
RADIUS encapsulates EAP packets in the EAP-Message attribute, as shown in Figure 5. The Type field takes 79, and the Value field can be up to 253 bytes. If an EAP packet is longer than 253 bytes, RADIUS encapsulates it in multiple EAP-Message attributes.
Figure 5 EAP-Message attribute format
Message-Authenticator
RADIUS includes the Message-Authenticator attribute in all packets that have an EAP-Message attribute to check their integrity. The packet receiver drops the packet if the calculated packet integrity checksum is different than the Message-Authenticator attribute value. The Message-Authenticator prevents EAP authentication packets from being tampered with during EAP authentication.
Figure 6 Message-Authenticator attribute format
![]()
Initiating 802.1X authentication
Both the 802.1X client and the access device can initiate 802.1X authentication.
802.1X client as the initiator
The client sends an EAPOL-Start packet to the access device to initiate 802.1X authentication. The destination MAC address of the packet is the IEEE 802.1X specified multicast address 01-80-C2-00-00-03 or the broadcast MAC address. If any intermediate device between the client and the authentication server does not support the multicast address, you must use an 802.1X client, the H3C iNode 802.1X client for example, that can send broadcast EAPOL-Start packets.
Access device as the initiator
The access device initiates authentication, if a client cannot send EAPOL-Start packets (for example, an 802.1X client available with Windows XP).
The access device supports the following modes:
· Multicast trigger mode—The access device multicasts Identity EAP-Request packets periodically (every 30 seconds by default) to initiate 802.1X authentication.
· Unicast trigger mode—Upon receiving a frame with the source MAC address not in the MAC address table, the access device sends an Identity EAP-Request packet out of the receiving port to the unknown MAC address. It retransmits the packet if no response has been received within a certain time interval.
802.1X authentication procedures
802.1X provides two authentication methods: EAP relay and EAP termination. You choose either mode depending on the support of the RADIUS server for EAP packets and EAP authentication methods.
· EAP relay mode:
EAP relay is defined in IEEE 802.1X. In this mode, the network device uses EAPoR packets to send authentication information to the RADIUS server, as shown in Figure 7.
In EAP relay mode, the client must use the same authentication method as the RADIUS server. On the network access device, you only need to use the dot1x authentication-method eap command to enable EAP relay.
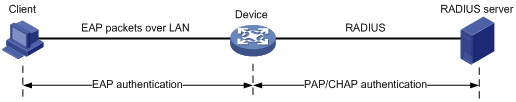
· EAP termination mode:
In EAP termination mode, the network access device terminates the EAP packets received from the client, encapsulates the client authentication information in standard RADIUS packets, and uses PAP or CHAP to authenticate to the RADIUS server, as shown in Figure 8.
Comparing EAP relay and EAP termination
|
Packet exchange method |
Benefits |
Limitations |
|
EAP relay |
· Supports various EAP authentication methods. · The configuration and processing is simple on the network access device |
The RADIUS server must support the EAP-Message and Message-Authenticator attributes, and the EAP authentication method used by the client. |
|
EAP termination |
Works with any RADIUS server that supports PAP or CHAP authentication. |
· Supports only MD5-Challenge EAP authentication and the "username + password" EAP authentication initiated by an H3C iNode 802.1X client. · The processing is complex on the network access device. |
EAP relay
Figure 9 shows the basic 802.1X authentication procedure in EAP relay mode, assuming that EAP-MD5 is used.
Figure 9 802.1X authentication procedure in EAP relay mode
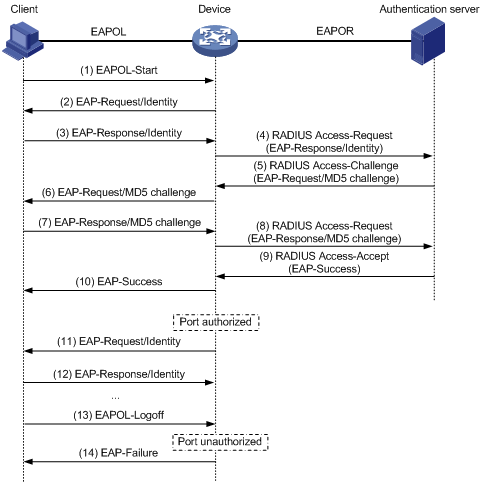
1. When a user launches the 802.1X client software and enters a registered username and password, the 802.1X client software sends an EAPOL-Start packet to the network access device.
2. The network access device responds with an Identity EAP-Request packet to ask for the client username.
3. In response to the Identity EAP-Request packet, the client sends the username in an Identity EAP-Response packet to the network access device.
4. The network access device relays the Identity EAP-Response packet in a RADIUS Access-Request packet to the authentication server.
5. The authentication server uses the identity information in the RADIUS Access-Request to search its user database. If a matching entry is found, the server uses a randomly generated challenge (EAP-Request/MD5 challenge) to encrypt the password in the entry, and sends the challenge in a RADIUS Access-Challenge packet to the network access device.
6. The network access device relays the EAP-Request/MD5 Challenge packet in a RADIUS Access-Request packet to the client.
7. The client uses the received challenge to encrypt the password, and sends the encrypted password in an EAP-Response/MD5 Challenge packet to the network access device.
8. The network access device relays the EAP-Response/MD5 Challenge packet in a RADIUS Access-Request packet to the authentication server.
9. The authentication server compares the received encrypted password with the one it generated at step 5. If the two are identical, the authentication server considers the client valid and sends a RADIUS Access-Accept packet to the network access device.
10. Upon receiving the RADIUS Access-Accept packet, the network access device sends an EAP-Success packet to the client, and sets the controlled port in the authorized state so the client can access the network.
11. After the client comes online, the network access device periodically sends handshake requests to check whether the client is still online. By default, if two consecutive handshake attempts fail, the device logs off the client.
13. The client can also send an EAPOL-Logoff packet to ask the network access device for a logoff. Then
14. In response to the EAPOL-Logoff packet, the network access device changes the status of the controlled port from authorized to unauthorized and sends an EAP-Failure packet to the client.
EAP termination
Figure 10 shows the basic 802.1X authentication procedure in EAP termination mode, assuming that CHAP authentication is used.
Figure 10 802.1X authentication procedure in EAP termination mode
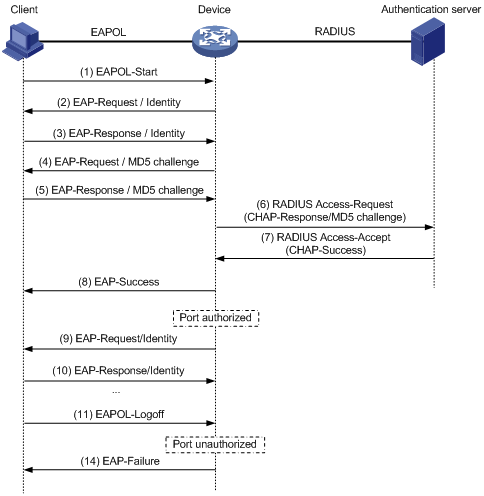
In EAP termination mode, the network access device rather than the authentication server generates a random MD5 challenge for password encryption (see Step 4). The network access device then sends the MD5 challenge together with the username and encrypted password in a standard RADIUS packet to the RADIUS server.
This chapter describes how to configure 802.1X on an H3C device.
H3C implementation of 802.1X
Access control methods
H3C implements port-based access control as defined in the 802.1X protocol, and extends the protocol to support MAC-based access control.
· Port-based access control—Once an 802.1X user passes authentication on a port, any subsequent user can access the network through the port without authentication. When the authenticated user logs off, all other users are logged off.
· MAC-based access control—Each user is separately authenticated on a port. When a user logs off, no other online users are affected.
Using 802.1X authentication with other features
VLAN assignment
You can configure the authentication server to assign a VLAN for an 802.1X user that has passed authentication. The way that the network access device handles VLANs on an 802.1X-enabled port differs by 802.1X access control mode.
|
Access control |
VLAN manipulation |
|
Port-based |
Assigns the VLAN to the port as the port VLAN (PVID). The authenticated 802.1X user and all subsequent 802.1X users can access the VLAN without authentication. When the user logs off, the previous PVID restores, and all other online users are logged off. |
|
MAC-based |
· If the port is a hybrid port with MAC-based VLAN enabled, maps the MAC address of each user to the VLAN assigned by the authentication server. The PVID of the port does not change. When a user logs off, the MAC-to-VLAN mapping for the user is removed. · If the port is an access, trunk, or MAC-based VLAN disabled hybrid port, assigns the first authenticated user's VLAN to the port as the PVID. If a different VLAN is assigned for a subsequent user, the user cannot pass the authentication. |
With 802.1X authentication, a hybrid port is always assigned to a VLAN as an untagged member. After the assignment, do not re-configure the port as a tagged member in the VLAN.
On a periodic online user re-authentication enabled port, if a user has been online before you enable the MAC-based VLAN function, the access device does not create a MAC-to-VLAN mapping for the user unless the user passes re-authentication and the VLAN for the user has changed.
For more information about VLAN configuration and MAC-based VLAN, see Layer 2—LAN Switching Configuration Guide.
Guest VLAN
You can configure a guest VLAN on a port to accommodate users that have not performed 802.1X authentication, so they can access a limited set of network resources, such as a software server, to download anti-virus software and system patches. After a user in the guest VLAN passes 802.1X authentication, it is removed from the guest VLAN and can access authorized network resources. The way that the network access device handles VLANs on the port differs by 802.1X access control mode.
1. On a port that performs port-based access control:
|
Authentication status |
VLAN manipulation |
|
No 802.1X user has performed authentication within 90 seconds after 802.1X is enabled. |
Assigns the 802.1X guest VLAN to the port as the PVID. All 802.1X users on this port can access only resources in the guest VLAN. If no 802.1X guest VLAN is configured, the access device does not perform any VLAN operation. |
|
A user in the 802.1X guest VLAN fails 802.1X authentication. |
If an 802.1X Auth-Fail VLAN (see "Auth-Fail VLAN") is available, assigns the Auth-Fail VLAN to the port as the PVID. All users on this port can access only resources in the Auth-Fail VLAN. If no Auth-Fail VLAN is configured, the PVID on the port is still the 802.1X guest VLAN. All users on the port are in the guest VLAN. |
|
A user in the 802.1X guest VLAN passes 802.1X authentication. |
· Assigns the VLAN specified for the user to the port as the PVID, and removes the port from the 802.1X guest VLAN. After the user logs off, the user configured PVID restores. · If the authentication server assigns no VLAN, the user configured PVID applies. The user and all subsequent 802.1X users are assigned to the user-configured PVID. After the user logs off, the PVID remains unchanged. |
2. On a port that performs MAC-based access control:
|
Authentication status |
VLAN manipulation |
|
A user has not passed 802.1X authentication yet. |
Creates a mapping between the MAC address of the user and the 802.1X guest VLAN. The user can access resources in the guest VLAN. |
|
A user in the 802.1X guest VLAN fails 802.1X authentication. |
If an 802.1X Auth-Fail VLAN is available, re-maps the MAC address of the user to the Auth-Fail VLAN. The user can access only resources in the Auth-Fail VLAN. If no 802.1X Auth-Fail VLAN is configured, the user is still in the 802.1X guest VLAN. |
|
A user in the 802.1X guest VLAN passes 802.1X authentication. |
Re-maps the MAC address of the user to the VLAN specified for the user. If the authentication server assigns no VLAN, re-maps the MAC address of the user to the initial PVID on the port. |
To use the 802.1X guest VLAN function on a port that performs MAC-based access control, make sure that the port is a hybrid port, and enable MAC-based VLAN on the port.
The network device assigns a hybrid port to an 802.1X guest VLAN as an untagged member.
For more information about VLAN configuration and MAC-based VLAN, see Layer 2—LAN Switching Configuration Guide.
Auth-Fail VLAN
You can configure an Auth-Fail VLAN to accommodate users that have failed 802.1X authentication because of the failure to comply with the organization security strategy, such as using a wrong password. Users in the Auth-Fail VLAN can access a limited set of network resources, such as a software server, to download anti-virus software and system patches.
The Auth-Fail VLAN does not accommodate 802.1X users that have failed authentication for authentication timeouts or network connection problems. The way that the network access device handles VLANs on the port differs by 802.1X access control mode.
1. On a port that performs port-based access control:
|
Authentication status |
VLAN manipulation |
|
A user fails 802.1X authentication. |
Assigns the Auth-Fail VLAN to the port as the PVID. All 802.1X users on this port can access only resources in the Auth-Fail VLAN. |
|
A user in the Auth-Fail VLAN fails 802.1X re-authentication. |
The Auth-Fail VLAN is still the PVID on the port, and all 802.1X users on this port are in this VLAN. |
|
A user passes 802.1X authentication. |
· Assigns the VLAN specified for the user to the port as the PVID, and removes the port from the Auth-Fail VLAN. After the user logs off, the user-configured PVID restores. · If the authentication server assigns no VLAN, the initial PVID applies. The user and all subsequent 802.1X users are assigned to the user-configured PVID. After the user logs off, the PVID remains unchanged. |
2. On a port that performs MAC-based access control:
|
Authentication status |
VLAN manipulation |
|
A user fails 802.1X authentication. |
Re-maps the MAC address of the user to the Auth-Fail VLAN. The user can access only resources in the Auth-Fail VLAN. |
|
A user in the Auth-Fail VLAN fails 802.1X re-authentication. |
The user is still in the Auth-Fail VLAN. |
|
A user in the Auth-Fail VLAN passes 802.1X authentication. |
Re-maps the MAC address of the user to the server-assigned VLAN. If the authentication server assigns no VLAN, re-maps the MAC address of the user to the initial PVID on the port. |
To perform the 802.1X Auth-Fail VLAN function on a port that performs MAC-based access control, you must make sure that the port is a hybrid port, and enable MAC-based VLAN on the port.
The network device assigns a hybrid port to an 802.1X Auth-Fail VLAN as an untagged member.
For more information about VLAN configuration and MAC-based VLAN, see Layer 2—LAN Switching Configuration Guide.
Configuration prerequisites
· Configure an ISP domain and AAA scheme (local or RADIUS authentication) for 802.1X users.
· If RADIUS authentication is used, create user accounts on the RADIUS server.
· If local authentication is used, create local user accounts on the access device and set the service type to lan-access.
802.1X configuration task list
|
Task |
Remarks |
|
Required. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Setting the maximum number of concurrent 802.1X users on a port |
Optional. |
|
Setting the maximum number of authentication request attempts |
Optional. |
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Enabling the periodic online user re-authentication function |
Optional. |
|
Optional. |
|
|
Optional. |
|
|
Optional. |
Enabling 802.1X
802.1X is mutually exclusive with link aggregation group configuration on a port.
To enable 802.1X on a port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable 802.1X globally. |
dot1x |
By default, 802.1X is disabled globally. |
|
3. Enable 802.1X on a port in system or Ethernet interface view. |
· In system view: · In Ethernet interface view: a. interface interface-type interface-number b. dot1x |
By default, 802.1X is disabled on a port. |
Enabling EAP relay or EAP termination
When configuring EAP relay or EAP termination, consider the following factors:
· The support of the RADIUS server for EAP packets
· The authentication methods supported by the 802.1X client and the RADIUS server
If the client supports only MD5-Challenge EAP authentication, you can use both EAP termination and EAP relay. To use EAP-TL, PEAP, or any other EAP authentication methods, you must use EAP relay. When you make your decision, see "Comparing EAP relay and EAP termination" for help.
For more information about EAP relay and EAP termination, see "802.1X authentication procedures."
To configure EAP relay or EAP termination:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure EAP relay or EAP termination. |
dot1x authentication-method { chap | eap | pap } |
By default, the network access device performs EAP termination and uses CHAP to communicate with the RADIUS server. Specify the eap keyword to enable EAP termination. Specify the chap or pap keyword to enable CHAP-enabled or PAP-enabled EAP relay. |
|
|
NOTE: If EAP relay mode is used, the user-name-format command configured in RADIUS scheme view does not take effect. The access device sends the authentication data from the client to the server without any modification. |
Setting the port authorization state
The port authorization state determines whether the client is granted access to the network. You can control the authorization state of a port by using the dot1x port-control command and the following keywords:
· authorized-force—Places the port in the authorized state, enabling users on the port to access the network without authentication.
· unauthorized-force—Places the port in the unauthorized state, denying any access requests from users on the port.
· auto—Places the port initially in the unauthorized state to allow only EAPOL packets to pass, and after a user passes authentication, sets the port in the authorized state to allow access to the network. You can use this option in most scenarios.
You can set authorization state for one port in interface view, or for multiple ports in system view. If different authorization state is set for a port in system view and interface view, the one set later takes effect.
To set the authorization state of a port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the port authorization state in system or Ethernet interface view. |
· In system view: · In Ethernet interface view: a. interface interface-type interface-number b. dot1x port-control { authorized-force | auto | unauthorized-force } |
By default, auto applies. |
Specifying an access control method
You can specify an access control method for one port in interface view or for multiple ports in system view. If different access control methods are specified for a port in system view and interface view, the one specified later takes effect.
To specify the access control method:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify an access control method in system or Ethernet interface view. |
· In system view: · In Ethernet interface view: a. interface interface-type interface-number b. dot1x port-method { macbased | portbased } |
By default, MAC-based access control applies. To use both 802.1X and portal authentication on a port, you must specify MAC-based access control. For information about portal authentication, see "Configuring portal authentication." |
Setting the maximum number of concurrent 802.1X users on a port
You can set the maximum number of concurrent 802.1X users for ports individually in interface view or in bulk in system view. If different settings are configured for a port in both views, the setting configured later takes effect.
To set the maximum number of concurrent 802.1X users on a port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the maximum number of concurrent 802.1X users on a port in system or Ethernet interface view. |
· In system view: · In Ethernet interface view: a. interface interface-type interface-number b. dot1x max-user user-number [ interface interface-list ] |
The default setting is 16384. |
Setting the maximum number of authentication request attempts
The network access device retransmits an authentication request if it receives no response to the request it has sent to the client within a period of time (specified by using the dot1x timer tx-period tx-period-value command or the dot1x timer supp-timeout supp-timeout-value command). The network access device stops retransmitting the request, if it has made the maximum number of request transmission attempts but still received no response.
To set the maximum number of authentication request attempts:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the maximum number of attempts for sending an authentication request. |
dot1x retry max-retry-value |
The default setting is 2. |
Setting the 802.1X authentication timeout timers
The network device uses the following 802.1X authentication timeout timers:
· Client timeout timer—Starts when the access device sends an EAP-Request/MD5 Challenge packet to a client. If no response is received when this timer expires, the access device retransmits the request to the client.
· Server timeout timer—Starts when the access device sends a RADIUS Access-Request packet to the authentication server. If no response is received when this timer expires, the access device retransmits the request to the server.
You can set the client timeout timer to a high value in a low-performance network, and adjust the server timeout timer to adapt to the performance of different authentication servers. In most cases, the default settings are sufficient.
To set the 802.1X authentication timeout timers:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the client timeout timer. |
dot1x timer supp-timeout supp-timeout-value |
The default setting is 30 seconds. |
|
3. Set the server timeout timer. |
dot1x timer server-timeout server-timeout-value |
The default setting is 100 seconds. |
Configuring the online user handshake function
The online user handshake function checks the connectivity status of online 802.1X users. The network access device sends handshake messages to online users at the interval specified by the dot1x timer handshake-period command. If no response is received from an online user after the maximum number of handshake attempts (set by the dot1x retry command) has been made, the network access device sets the user in the offline state.
If iNode clients are deployed, you can also enable the online handshake security function to check for 802.1X users that use illegal client software to bypass security inspection such as dual network interface cards (NICs) detection. This function checks the authentication information in client handshake messages. If a user fails the authentication, the network access device logs the user off.
Configuration guidelines
Follow these guidelines when you configure the online user handshake function:
· To use the online handshake security function, make sure the online user handshake function is enabled. H3C recommends that you use the iNode client software and IMC server to guarantee the normal operation of the online user handshake security function.
· If the network has 802.1X clients that cannot exchange handshake packets with the network access device, disable the online user handshake function to prevent their connections from being inappropriately torn down.
Configuration procedure
To configure the online user handshake function:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the handshake timer. |
dot1x timer handshake-period handshake-period-value |
Optional. The default setting is 15 seconds. |
|
3. Enter Ethernet interface view. |
interface interface-type interface-number |
N/A |
|
4. Enable the online handshake function. |
dot1x handshake |
Optional. By default, the function is enabled. |
|
5. Enable the online handshake security function. |
dot1x handshake secure |
Optional. By default, the function is disabled. |
Configuring the authentication trigger function
The authentication trigger function enables the network access device to initiate 802.1X authentication when 802.1X clients cannot initiate authentication.
This function provides the following types of authentication trigger:
· Multicast trigger—Periodically multicasts Identity EAP-Request packets out of a port to detect 802.1X clients and trigger authentication.
· Unicast trigger—Enables the network device to initiate 802.1X authentication when it receives a data frame from an unknown source MAC address. The device sends a unicast Identity EAP/Request packet to the unknown source MAC address, and retransmits the packet if it has received no response within a period of time. This process continues until the maximum number of request attempts set with the dot1x retry command (see "Setting the maximum number of authentication request attempts") is reached.
The identity request timeout timer sets both the identity request interval for the multicast trigger and the identity request timeout interval for the unicast trigger.
Configuration guidelines
Follow these guidelines when you configure the authentication trigger function:
· Enable the multicast trigger on a port when the clients attached to the port cannot send EAPOL-Start packets to initiate 802.1X authentication.
· Enable the unicast trigger on a port if only a few 802.1X clients are attached to the port and these clients cannot initiate authentication.
· To avoid duplicate authentication packets, do not enable both triggers on a port.
Configuration procedure
To configure the authentication trigger function on a port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the username request timeout timer. |
dot1x timer tx-period tx-period-value |
Optional. The default setting is 30 seconds. |
|
3. Enter Ethernet interface view. |
interface interface-type interface-number |
N/A |
|
4. Enable an authentication trigger. |
dot1x { multicast-trigger | unicast-trigger } |
Required if you want to enable the unicast trigger. By default, the multicast trigger is enabled, and the unicast trigger is disabled. |
Specifying a mandatory authentication domain on a port
You can place all 802.1X users in a mandatory authentication domain for authentication, authorization, and accounting on a port. No user can use an account in any other domain to access the network through the port. The implementation of a mandatory authentication domain enhances the flexibility of 802.1X access control deployment.
To specify a mandatory authentication domain for a port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Ethernet interface view. |
interface interface-type interface-number |
N/A |
|
3. Specify a mandatory 802.1X authentication domain on the port. |
dot1x mandatory-domain domain-name |
By default, no mandatory 802.1X authentication domain is specified. |
Configuring the quiet timer
The quiet timer enables the network access device to wait a period of time before it can process any authentication request from a client that has failed an 802.1X authentication.
You can set the quiet timer to a high value in a vulnerable network or a low value for quicker authentication response.
To configure the quiet timer:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the quiet timer. |
dot1x quiet-period |
By default, the timer is disabled. |
|
3. Set the quiet timer. |
dot1x timer quiet-period quiet-period-value |
Optional. The default setting is 60 seconds. |
Enabling the periodic online user re-authentication function
Periodic online user re-authentication tracks the connection status of online users and updates the authorization attributes assigned by the server, such as the ACL. The re-authentication interval is user configurable.
To enable the periodic online user re-authentication function:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the periodic re-authentication timer. |
dot1x timer reauth-period reauth-period-value |
Optional. The default is 3600 seconds. |
|
3. Enter Ethernet interface view. |
interface interface-type interface-number |
N/A |
|
4. Enable periodic online user re-authentication. |
dot1x re-authenticate |
By default, the function is disabled. |
The periodic online user re-authentication timer can also be set by the authentication server in the session-timeout attribute. The server-assigned timer overrides the timer setting on the access device, and enables periodic online user re-authentication, even if the function is not configured. Support for the server assignment of re-authentication timer and the re-authentication timer configuration on the server vary with servers.
The VLAN assignment status must be consistent before and after re-authentication. If the authentication server has assigned a VLAN before re-authentication, it must also assign a VLAN at re-authentication. If the authentication server has assigned no VLAN before re-authentication, it must not assign one at re-authentication. Violation of either rule can cause the user to be logged off. The VLANs assigned to an online user before and after re-authentication can be the same or different.
Configuring an 802.1X guest VLAN
Follow these guidelines when you configure an 802.1X guest VLAN:
· You can configure only one 802.1X guest VLAN on a port. The 802.1X guest VLANs on different ports can be different.
· Assign different IDs to the PVID and the 802.1X guest VLAN on a port, so the port can correctly process incoming VLAN tagged traffic.
· With 802.1X authentication, a hybrid port is always assigned to a VLAN as an untagged member. After the assignment, do not re-configure the port as a tagged member in the VLAN.
· Use Table 2 when configuring multiple security features on a port.
Table 2 Relationships of the 802.1X guest VLAN and other security features
|
Feature |
Relationship description |
Reference |
|
Super VLAN |
You cannot specify a VLAN as both a super VLAN and an 802.1X guest VLAN. |
See "Super VLAN configuration." |
|
MAC authentication guest VLAN on a port that performs MAC-based access control |
Only the 802.1X guest VLAN take effect. A user that fails MAC authentication will not be assigned to the MAC authentication guest VLAN. |
See "MAC authentication configuration." |
|
802.1X Auth-Fail VLAN on a port that performs MAC-based access control |
The 802.1X Auth-Fail VLAN has a higher priority. |
Before you configure an 802.1X guest VLAN, complete the following tasks:
· Create the VLAN to be specified as the 802.1X guest VLAN.
· If the 802.1X-enabled port performs port-based access control, enable 802.1X multicast trigger.
· If the 802.1X-enabled port performs MAC-based access control, configure the port as a hybrid port, enable MAC-based VLAN on the port, and assign the port to the 802.1X guest VLAN as an untagged member. For more information about the MAC-based VLAN function, see Layer 2—LAN Switching Configuration Guide.
To configure an 802.1X guest VLAN:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure an 802.1X guest VLAN for one or more ports in system or Ethernet interface view. |
· In system view: · In Ethernet interface view: a. interface interface-type interface-number b. dot1x guest-vlan guest-vlan-id |
By default, no 802.1X guest VLAN is configured on any port. |
Configuring an 802.1X Auth-Fail VLAN
Follow these guidelines when you configure an 802.1X Auth-Fail VLAN
· Assign different IDs to the PVID and the 802.1X Auth-Fail VLAN on a port, so the port can correctly process VLAN tagged incoming traffic.
· You can configure only one 802.1X Auth-Fail VLAN on a port. The 802.1X Auth-Fail VLANs on different ports can be different.
· Use Table 3 when configuring multiple security features on a port.
Table 3 Relationships of the 802.1X Auth-Fail VLAN with other features
|
Feature |
Relationship description |
Reference |
|
Super VLAN |
You cannot specify a VLAN as both a super VLAN and an 802.1X Auth-Fail VLAN. |
See Layer 2—LAN Switching Configuration Guide |
|
MAC authentication guest VLAN on a port that performs MAC-based access control |
The 802.1X Auth-Fail VLAN has a high priority. |
See "MAC authentication configuration" |
Before you configure an Auth-Fail VLAN, complete the following tasks:
· Create the VLAN to be specified as the 802.1X Auth-Fail VLAN.
· If the 802.1X-enabled port performs port-based access control, enable 802.1X multicast trigger.
· If the 802.1X-enabled port performs MAC-based access control, configure the port as a hybrid port, enable MAC-based VLAN on the port, and assign the port to the Auth-Fail VLAN as an untagged member. For more information about the MAC-based VLAN function, see Layer 2—LAN Switching Configuration Guide.
To configure an Auth-Fail VLAN:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Ethernet interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the Auth-Fail VLAN on the port. |
dot1x auth-fail vlan authfail-vlan-id |
By default, no Auth-Fail VLAN is configured. |
Specifying supported domain name delimiters
By default, the access device supports the at sign (@) as the delimiter. You can also configure the access device to accommodate 802.1X users that use other domain name delimiters.
The configurable delimiters include the at sign (@), back slash (\), and forward slash (/).
If an 802.1X username string contains multiple configured delimiters, the leftmost delimiter is the domain name delimiter. For example, if you configure @, /, and \ as delimiters, the domain name delimiter for the username string 123/22\@abc is the forward slash (/).
If a username string contains none of the delimiters, the access device authenticates the user in the mandatory or default ISP domain. The access selects a domain delimiter from the delimiter set in this order: @, /, and \.
To specify a set of domain name delimiters:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify a set of domain name delimiters for 802.1X users. |
dot1x domain-delimiter string |
By default, only the at sign (@) delimiter is supported. |
|
|
NOTE: If you configure the access device to include the domain name in the username sent to the RADIUS server, make sure the domain delimiter in the username can be recognized by the RADIUS server. For username format configuration, see the user-name-format command in Security Command Reference. |
Displaying and maintaining 802.1X
|
Task |
Command |
Remarks |
|
Display 802.1X session information, statistics, or configuration of specified or all ports. |
display dot1x [ sessions | statistics ] [ interface interface-list ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Clear 802.1X statistics. |
reset dot1x statistics [ interface interface-list ] |
Available in user view. |
802.1X configuration examples
By default, Ethernet interfaces, VLAN interfaces, and aggregate interfaces are in the state of DOWN. To configure such an interface, use the undo shutdown command to bring it up first.
802.1X authentication configuration example
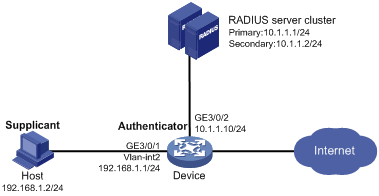
Network requirements
As shown in Figure 11, the access device performs 802.1X authentication for users that connect to port GigabitEthernet 3/0/1. Implement MAC-based access control on the port, so the logoff of one user does not affect other online 802.1X users.
Use RADIUS servers to perform authentication, authorization, and accounting for the 802.1X users. If RADIUS authentication fails, perform local authentication on the access device. If RADIUS accounting fails, the access device logs the user off.
Configure the host at 10.1.1.1/24 as the primary authentication and accounting servers, and the host at 10.1.1.2/24 as the secondary authentication and accounting servers. Assign all users to the ISP domain aabbcc.net, which accommodates up to 30 users.
Configure the shared key as name for packets between the access device and the authentication server, and as money for packets between the access device and the accounting server.
Configuration procedure
1. Configure the 802.1X client. If H3C iNode is used, do not select the Carry version info option in the client configuration. (Details not shown.)
2. Configure the RADIUS servers and add user accounts for the 802.1X users. (Details not shown.)
For information about the RADIUS commands used on the access device in this example, see Security Command Reference.
3. Assign an IP address to each interface on the access device. (Details not shown.)
4. Configure user accounts for the 802.1X users on the access device:
# Add a local user with the username localuser, and password localpass in plaintext. (Make sure the username and password are the same as those configured on the RADIUS server.)
<Device> system-view
[Device] local-user localuser
[Device-luser-localuser] service-type lan-access
[Device-luser-localuser] password simple localpass
# Configure the idle cut function to log off any online user that has been idled for 20 minutes.
[Device-luser-localuser] authorization-attribute idle-cut 20
[Device-luser-localuser] quit
5. Configure a RADIUS scheme:
# Create the RADIUS scheme radius1 and enter its view.
[Device] radius scheme radius1
# Specify the IP addresses of the primary authentication and accounting RADIUS servers.
[Device-radius-radius1] primary authentication 10.1.1.1
[Device-radius-radius1] primary accounting 10.1.1.1
# Configure the IP addresses of the secondary authentication and accounting RADIUS servers.
[Device-radius-radius1] secondary authentication 10.1.1.2
[Device-radius-radius1] secondary accounting 10.1.1.2
# Specify the shared key between the access device and the authentication server.
[Device-radius-radius1] key authentication name
# Specify the shared key between the access device and the accounting server.
[Device-radius-radius1] key accounting money
# Exclude the ISP domain name from the username sent to the RADIUS servers.
[Device-radius-radius1] user-name-format without-domain
[Device-radius-radius1] quit
|
|
NOTE: The access device must use the same username format as the RADIUS server. If the RADIUS server includes the ISP domain name in the username, so must the access device. |
6. Configure the ISP domain:
# Create the ISP domain aabbcc.net and enter its view.
[Device] domain aabbcc.net
# Apply the RADIUS scheme radius1 to the ISP domain, and specify local authentication as the secondary authentication method.
[Device-isp-aabbcc.net] authentication lan-access radius-scheme radius1 local
[Device-isp-aabbcc.net] authorization lan-access radius-scheme radius1 local
[Device-isp-aabbcc.net] accounting lan-access radius-scheme radius1 local
# Set the maximum number of concurrent users in the domain to 30.
[Device-isp-aabbcc.net] access-limit enable 30
# Configure the idle cut function to log off any online domain user that has been idle for 20 minutes.
[Device-isp-aabbcc.net] idle-cut enable 20
[Device-isp-aabbcc.net] quit
# Specify aabbcc.net as the default ISP domain. If a user does not provide any ISP domain name, it is assigned to the default ISP domain.
[Device] domain default enable aabbcc.net
7. Configure 802.1X:
# Enable 802.1X globally.
[Device] dot1x
# Enable 802.1X on port GigabitEthernet 3/0/1.
[Device] interface GigabitEthernet 3/0/1
[Device-GigabitEthernet3/0/1] dot1x
[Device-GigabitEthernet3/0/1] quit
# Enable MAC-based access control on the port. (Optional. MAC-based access control is the default setting.)
[Device] dot1x port-method macbased interface GigabitEthernet 3/0/1
Verifying the configuration
Use the display dot1x interface GigabitEthernet 3/0/1 command to verify the 802.1X configuration. After an 802.1X user passes RADIUS authentication, you can use the display connection command to view information about the user connection. If the user fails RADIUS authentication, local authentication is performed.
802.1X guest VLAN and VLAN assignment configuration example
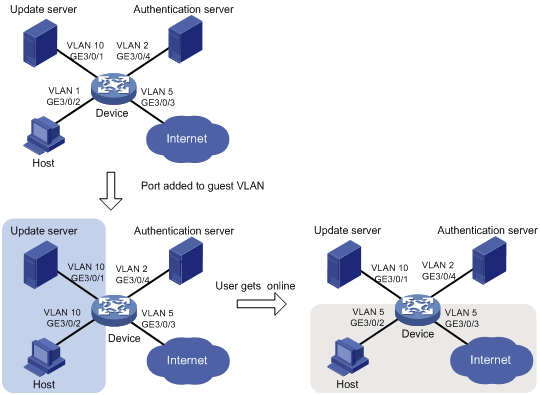
Network requirements
See Figure 12:
· A host is connected to port GigabitEthernet 3/0/2 of the device and must pass 802.1X authentication to access the Internet. GigabitEthernet 3/0/2 is in VLAN 1.
· GigabitEthernet 3/0/2 implements port-based access control.
· GigabitEthernet 3/0/3 is in VLAN 5 and is for accessing the Internet.
· The authentication server runs RADIUS and is in VLAN 2.
· The update server in VLAN 10 is for client software download and upgrade.
If no user performs 802.1X authentication on GigabitEthernet 3/0/2 within a period of time, the device adds GigabitEthernet 3/0/2 to its guest VLAN, VLAN 10. The host and the update server are both in VLAN 10 and the host can access the update server and download the 802.1X client software.
After the host passes 802.1X authentication, the network access device assigns the host to VLAN 5 where GigabitEthernet 3/0/3 is. The host can access the Internet.
Configuration procedure
1. Make sure the 802.1X client can update its IP address after the access port is assigned to the guest VLAN or a server-assigned VLAN. (Details not shown.)
2. Configure the RADIUS server to provide authentication, authorization, and accounting services. Configure user accounts and server-assigned VLAN, VLAN 5 in this example. (Details not shown.)
3. Create VLANs, and assign ports to the VLANs.
<Device> system-view
[Device] vlan 1
[Device-vlan1] port GigabitEthernet 3/0/2
[Device-vlan1] quit
[Device] vlan 10
[Device-vlan10] port GigabitEthernet 3/0/1
[Device-vlan10] quit
[Device] vlan 2
[Device-vlan2] port GigabitEthernet 3/0/4
[Device-vlan2] quit
[Device] vlan 5
[Device-vlan5] port GigabitEthernet 3/0/3
[Device-vlan5] quit
4. Configure a RADIUS scheme:
# Configure RADIUS scheme 2000 and enter its view.
<Device> system-view
[Device] radius scheme 2000
# Specify primary and secondary authentication and accounting servers. Set the shared key to abc for authentication and accounting packets.
[Device-radius-2000] primary authentication 10.11.1.1 1812
[Device-radius-2000] primary accounting 10.11.1.1 1813
[Device-radius-2000] key authentication abc
[Device-radius-2000] key accounting abc
# Exclude the ISP domain name from the username sent to the RADIUS server.
[Device-radius-2000] user-name-format without-domain
[Device-radius-2000] quit
5. Configure an ISP domain:
# Create ISP domain bbb and enter its view.
[Device] domaim bbb
# Apply RADIUS scheme 2000 to the ISP domain for authentication, authorization, and accounting.
[Device-isp-bbb] authentication lan-access radius-scheme 2000
[Device-isp-bbb] authorization lan-access radius-scheme 2000
[Device-isp-bbb] accounting lan-access radius-scheme 2000
[Device-isp-bbb] quit
6. Configure 802.1X:
# Enable 802.1X globally.
[Device] dot1x
# Enable 802.1X for port GigabitEthernet 3/0/2.
[Device] interface GigabitEthernet 3/0/2
[Device- GigabitEthernet3/0/2] dot1x
# Implement port-based access control on the port.
[Device-GigabitEthernet3/0/2] dot1x port-method portbased
# Set the port authorization mode to auto. This step is optional. By default, the port is in auto mode.
[Device-GigabitEthernet3/0/2] dot1x port-control auto
[Device-GigabitEthernet3/0/2] quit
# Set VLAN 10 as the 802.1X guest VLAN for port GigabitEthernet 3/0/2.
[Device] dot1x guest-vlan 10 interface GigabitEthernet 3/0/2
Verifying the configuration
Use the display dot1x interface GigabitEthernet 3/0/2 command to verify the 802.1X guest VLAN configuration on GigabitEthernet 3/0/2. If no user passes authentication on the port within a specific period of time, use the display vlan 10 command to verify whether GigabitEthernet 3/0/2 is assigned to VLAN 10.
After a user passes authentication, you can use the display interface GigabitEthernet 3/0/2 command to verity that port GigabitEthernet 3/0/2 has been added to VLAN 5.
