- Table of Contents
-
- H3C S3610[5510] Series Ethernet Switches Operation Manual-Release 0001-(V1.02)
- 00-1Cover
- 00-2Product Overview
- 01-Login Operation
- 02-VLAN Operation
- 03-IP Address and Performance Operation
- 04-QinQ-BPDU Tunnel Operation
- 05-Port Correlation Configuration Operation
- 06-MAC Address Table Management Operation
- 07-MAC-IP-Port Binding Operation
- 08-MSTP Operation
- 09-Routing Overview Operation
- 10-IPv4 Routing Operation
- 11-IPv6 Routing Operation
- 12-IPv6 Configuration Operation
- 13-Multicast Protocol Operation
- 14-802.1x-HABP-MAC Authentication Operation
- 15-AAA-RADIUS-HWTACACS Operation
- 16-ARP Operation
- 17-DHCP Operation
- 18-ACL Operation
- 19-QoS Operation
- 20-Port Mirroring Operation
- 21-Cluster Management Operation
- 22-UDP Helper Operation
- 23-SNMP-RMON Operation
- 24-NTP Operation
- 25-DNS Operation
- 26-File System Management Operation
- 27-Information Center Operation
- 28-System Maintenance and Debugging Operation
- 29-NQA Operation
- 30-VRRP Operation
- 31-SSH Operation
- 32-Appendix
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 31-SSH Operation | 5 MB |
Table of Contents
Chapter 1 SSH Terminal Services
1.2 Configuring the SSH Server
1.2.2 Configuring the Protocols for the SSH Client User Interface to Support
1.2.3 Creating/Destroying/Exporting RSA Keys
1.2.4 Configuring the Authentication Method for an SSH User
1.2.5 Setting the SSH Management Parameters
1.2.6 Configuring the RSA Public Key for a User
1.3 Configuring the SSH Client
1.3.1 Generating the Client Keys
1.3.2 Specifying the IP address of the server
1.3.3 Selecting the protocol for remote connection
1.3.4 Selecting the SSH version
1.3.5 Opening an SSH Connection with RSA
1.3.6 Opening an SSH Connection with Password
1.4 Displaying and Maintaining the SSH Protocol
Chapter 1 SSH Terminal Services
1.1 SSH Overview
Secure shell (SSH) offers an approach to securely logging into a remote device. It can protect devices against attacks such as IP spoofing and plain text password interception.
In a typical SSH scenario, a device running SSH server works as an SSH server and accepts connections from SSH clients, which run SSH client. The connections are called SSH connections and can be established either on the local network or over WANs, as shown in Figure 1-1 and Figure 1-2.

Figure 1-1 SSH channel on the local network

Figure 1-2 SSH channel over a WAN
![]() Note:
Note:
At present, the device only supports SSH1.5 version.
The communication process between the server and client includes these five stages:
1) Version number negotiation
l The server opens port 22 to wait for connection requests from clients
l A client initiates a TCP connection request to the server. After the TCP connection is established, the server sends the first packet, including the version flag string in the format of “SSH-<primary protocol version number>.<secondary protocol version number>-<software version number>”. The primary and secondary protocol version numbers form the protocol version number, and the software version number is provided mainly for debugging.
l After receiving the packet, the client begins packet analysis. If the protocol version number of the server is smaller than that of the client and the client supports the lower version, the client adopts the protocol version of the server. Otherwise, the client uses its own protocol version.
l The client sends a response packet which contains the protocol version number determined by the client. The server compares the version number sent from the client with its own to decide whether to work with the client.
l If the version number negotiation succeeds, key algorithm negotiation begins. Otherwise, the server terminates the TCP connection.
& Note:
The above packets are transmitted in plain text.
2) Key algorithm negotiation
l After the version number negotiation succeeds, the server sends a packet to the client, which contains the host public key, the server public key, the supported encryption algorithm, authentication algorithm, protocol extension flags, and a 8-byte (64-bit) cookie (a random number). And this packet is also transmitted in plain text. Then, the server and the client start to calculate the session ID. Both sides use the same parameters to generate the same session ID, whose length is 16 bytes. The calculation expression is as follows:
![]()
Figure 1-3 Session ID calculation format
l The client will generate a 32-byte session key, which will be used to encrypt the data to be transmitted. However, the client does not send the key to the server directly but first processes the session key in the following way. First, the client uses the first 16-byte of the session key to perform AND/OR calculation with that of the session ID, and keeps the last 16-byte unchanged. Then it arranges the result (result1) in the order of most significant bit (MSB) first to form an MP (multi-precision) integer. The MP integer will then be encrypted by the public key with smaller modulus to get a new result (result2), which will be arranged in the order of MSB first to form a new MP integer. At last, the client encrypts the new MP integer with the public key having larger modulus. The whole process is shown in the following figure.
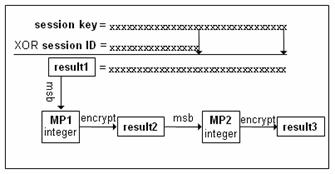
Figure 1-4 Encryption of the session key
l The final result (result3) is the encrypted session key to be transmitted to the server. The client will send it together with its determined encryption algorithm, the 8-byte cookie sent from the server, and its protocol flag to the server. After the server receives the message containing the session key information, the server reverts the encrypted session key to the original one.
l After the above steps, the server and client get the same session key. During a session, both sides use the session key for encryption and decryption, thus ensuring the data security.
3) Authentication method negotiation
The client sends its username to the server, and the server starts to authenticate the user.
SSH provides two authentication methods: password authentication and RSA authentication.
For password authentication:
l The client encrypts the username and password, encapsulates them into a password authentication request, and sends the request to the server.
l Upon receiving the request, the server decrypts the username and password, compares them against those it maintains, and then informs the client of the authentication result.
For RSA authentication, the server must have been configured with the client RSA public key.
l The client sends an RSA authentication request together with its public key modulus to the server. The server performs validity check on the request, if it is not valid, the server sends failure message to the client. Otherwise, a 32-byte random number is generated, and processed in the way mentioned above to form an MP integer. And the server encrypts the integer with the public key of the client to initiate an authentication challenge to the client.
l When the client receives the challenge, it decrypts the challenge with its private key to obtain the MP integer, and then uses the integer and the session ID to generate a MD5 value. Then, the client encrypts the 16-byte MD5 value and sends it to the server.
l After the server receives the message, it decrypts the message to get the MD5 value and compares the MD5 value with that calculated by itself. If the two MD5 values are the same, the authentication succeeds and the server sends the success message; otherwise it sends the failure message.
This authentication process indicates that only the user who owns the private key can log into the server. The following figure shows the process.
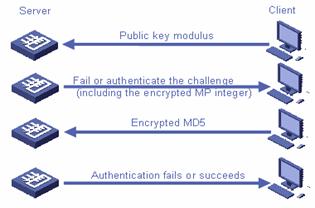
Figure 1-5 RSA authentication process
4) Session request
After passing authentication, the client sends a session request to the server, while the server listens to and processes the request from the client and sends back to the client the result, which can be an SSH_SMSG_SUCCESS packet for successful processing or an SSH_SMSG_FAILURE packet if the processing fails or it cannot resolve the request. In the former case, the server and the client enter the interactive session phase.
5) Interactive session
The server and the client exchanges data in this way:
l The client encrypts the command to be executed and sends it to the server.
l The server decrypts and executes the command, and then encrypts and sends the result to the client.
l The client decrypts the result and displays the result on the terminal.
l During interactive session, the client can send the commands to be performed by pasting the text, which must be within 2000 bytes. It is recommended that the text pasted be commands in the same view; otherwise, the server may not be able to perform the commands.
l If the text exceeds 2000 bytes, you can upload the configuration file to the server and use the configuration file to restart the server so that the server executes the commands.
1.2 Configuring the SSH Server
1.2.1 Enabling SSH Server
Follow these steps to enable SSH server:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable SSH server |
ssh server enable |
Required Disabled by default |
1.2.2 Configuring the Protocols for the SSH Client User Interface to Support
After enabling SSH server, you must configure the device to support the remote SSH login protocol. Note that the configuration takes effect at next login.
Follow these steps to configure the protocols for the current user interface to support:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter single-user interface view or multi-user interface view |
user-interface [ type-keyword ] number [ ending-number ] |
Required |
|
Set the login authentication method |
authentication-mode scheme [ command-authorization ] |
Required |
|
Specify the protocols for the user interfaces to support |
protocol inbound { all | ssh | telnet } |
Optional All of the two are supported by default |
![]() Caution:
Caution:
l If you configure a user interface to support SSH, be sure to configure the authentication-mode scheme command.
l For a user interface configured to support SSH, you cannot configure the authentication-mode password or authentication-mode none command.
1.2.3 Creating/Destroying/Exporting RSA Keys
I. Creating RSA keys
The length of a server/host key must be in the range 512 to 2048 bits. After you enter the rsa local-key-pair create command, the system prompts you to enter the length of the key:
Follow these steps to create the host key pair and server key pair:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Create the RSA host key pair and server key pair |
rsa local-key-pair create |
Required |
II. Destroying RSA keys
Follow these steps to destroy the host key pair and server key pair:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Destroy the RSA host key pair and server key pair |
rsa local-key-pair destroy |
Required |
III. Displaying/exporting the public host key
Once created, the public host key can be displayed on the screen or exported to a specified file.
Follow these steps to export the host key pair:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Display the RSA host public key on the screen or export it to a specified file |
rsa local-key-pair export ssh1 [ filename ] |
Required |
![]() Caution:
Caution:
l The configuration of the rsa local-key-pair create command can survive a reboot. You only need to configure it once.
l If the key pair already exists, the system will ask you whether you want to overwrite it.
1.2.4 Configuring the Authentication Method for an SSH User
The configured authentication method takes effect when the user logs in next time.
Follow these steps to configure the authentication method for an SSH user:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Specify the authentication method for an SSH user |
ssh user username authentication-type { password | rsa | all } |
Optional RSA authentication by default |
![]() Caution:
Caution:
For a user using RSA authentication, you must configure the username and public keys on the device (a switch or a router). For a user using password authentication, you can configure the accounting information on the device or the remote authentication server (such as RADIUS authentication server).
1.2.5 Setting the SSH Management Parameters
l Setting the server key pair update interval can help secure your SSH connections.
l Setting the SSH user authentication timeout period.
l Setting the maximum number of SSH authentication attempts can assist in avoiding malicious connection requests.
Follow these steps to set the SSH management parameters:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Set the server key pair update interval |
ssh server rekey-interval hours |
Optional 0 by default, that is, the server key pair is not updated. |
|
Set the SSH user authentication timeout period |
ssh server authentication-timeout time-out-value |
Optional 60 seconds by default |
|
Set the maximum number of SSH authentication attempts |
ssh server authentication-retries times |
Optional 3 by default |
1.2.6 Configuring the RSA Public Key for a User
These configurations are required for an SSH user using RSA authentication. For an SSH user using password authentication, they are not required.
This configuration task is for configuring the RSA public key of a client with an SSH user. The RSA private key for the SSH user must be configured on the client. The client key pair is generated randomly by the SSH1.5 client software.
You can also import an RSA public key from a public key file. When you import a public key, the system automatically converts the public key in SSH1 format to a string coded using the PKCS standard. Before importing the public key, you must upload the public key file to the server through FTP or TFTP.
![]() Caution:
Caution:
l You can use either of the following two ways to configure the RSA public key of an SSH user.
l The purpose of creating SSH users on SSH server is to specify the authentication mode and user shared key for SSH users. You configure any of these two commands to create an SSH user: ssh user assign rsa-key, ssh user authentication-type. By default, the authentication method for an SSH user is RSA
l If no SSH users are created, but there are local users whose service type is SSH, the SSH client can still logs in the SSH server through these users. Here, the system performs password authentication.
I. Configuring the RSA public key manually
Follow these steps to configure the RSA public key manually:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter public key view |
rsa peer-public-key keyname |
Required |
|
Enter public key code view |
public-key-code begin |
— |
|
Configure the client public key |
Enter the content of the public key |
— The content must be a hexadecimal string that is generated randomly by the SSH-supported client software and coded compliant to PKCS. Spaces and carriage returns are allowed between characters. |
|
Return from public key code view to public key view |
public-key-code end |
— When you exit public key code view, the system automatically saves the public key. |
|
Return from public key view to system view |
peer-public-key end |
— |
|
Assign a public key to a user |
ssh user username assign rsa-key keyname |
Required The public key must exist. If the user has already a public key, the new public key overwrites the old one. |
II. Importing the RSA public key from a public key file
Follow these steps to import the RSA public key from a public key file:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Import the RSA public key from a public key file |
rsa peer-public-key keyname import sshkey filename |
Required |
1.3 Configuring the SSH Client
A variety of SSH client software are available, such as PuTTY and OpenSSH. For an SSH client to establish a connection with an SSH server, you must complete these configuration tasks:
l Specifying the IP address of the server.
l Selecting the protocol for remote connection. Usually, a client can use a variety of remote connection protocols, such as Telnet, Rlogin, SSH. To establish an SSH connection, you must select SSH.
l Selecting the SSH version. Multiple SSH versions are available. However, since the device supports SSH Server 1.5 now, select 1.5 or lower for the client.
l Specifying the RSA private key file. On the server, if RSA authentication is enabled for an SSH user and a public key is set for the user, the private key file corresponding to the public key must be specified on the client. RSA key pairs are generated by a tool of the client software.
The following takes the client software of PuTTY, PuTTYGen and SSHKEY as examples to illustrate how to configure the SSH client:
1.3.1 Generating the Client Keys
To generate the client key pair, run PuTTYGen.exe, choose SSH-1 RSA under Parameters and click Generate.

Figure 1-6 Generating the client keys (1)
Note that while generating the key pair, you must move the mouse continuously and keep the mouse off the green process bar in the blue box of shown in Figure 1-7. Otherwise, the process bar stops moving and the key pair generating process is stopped.

Figure 1-7 Generating the client keys (2)
After the key pair is generated, click Save public key and enter the name of the file for saving the public key (public in this case) to save the public key.

Figure 1-8 Generating the client keys (3)
Likewise, to save the private key, click Save private key. A warning window pops up to prompt you whether to save the private key without any precaution. Click Yes and enter the name of the file for saving the public key (private in this case) to save the private key.
Figure 1-9 Generating the client keys (4)
To generate RSA public key in PKCS format, run SSHKEY.exe, click Browse and select the public key file, and then click Convert.

Figure 1-10 Generating the client keys (5)
1.3.2 Specifying the IP address of the server
Launch PuTTY. The following window appears.

Figure 1-11 SSH client interface 1
In the [Host Name (or IP address)] text box, enter the IP address of the server,. Note that the IP address can be the IP address of any interface on the server that has SSH in the state of up and a route to the client.
1.3.3 Selecting the protocol for remote connection
As shown in Figure 1-11, select the [SSH] option from the [Protocol] section.
1.3.4 Selecting the SSH version
From the category on the left of the window, click [Connection/SSH]. The following window appears.

Figure 1-12 SSH client interface 2
As shown in Figure 1-12, select [1] from the [Preferred SSH protocol version] section.
1.3.5 Opening an SSH Connection with RSA
If the client needs to use RSA authentication, you must specify the RSA private key file. If the client needs to use password authentication, this is not required.
From the category on the left of the window, click [Connection/SSH/Auth]. The following window appears.
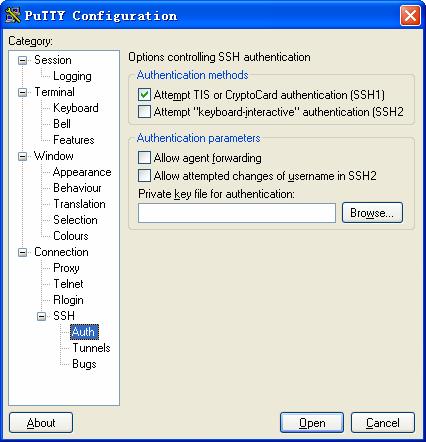
Figure 1-13 SSH client interface 3
Click <Browse> to bring up the file selection window, navigate to the private key file and click <OK>.
1.3.6 Opening an SSH Connection with Password
1) Click <Open>. The following SSH client interface appears. If the connection is normal, you will be prompted to enter the username and password, as shown in Figure 1-14.

Figure 1-14 SSH client interface 4
2) Enter the username and password. The SSH connection should be created.
3) To log out, enter the quit command.
1.4 Displaying and Maintaining the SSH Protocol
|
To do… |
Use the command… |
Remarks |
|
Display the public keys of the host key pair and server key pair |
display rsa local-key-pair public |
Available in any view |
|
Display the peer RSA public keys |
display rsa peer-public-key [ brief | name keyname ] |
Available in any view |
|
Display the status information or session information of the SSH server |
display ssh server { status | session } |
Available in any view |
|
Display the information of the SSH user |
display ssh user-information [ username ] |
Available in any view |
1.5 SSH Configuration Example
I. Network requirements
As shown in Figure 1-15, a local connection is established between the configuration terminal (SSH client) and the Switch. Users log in to the switch via the SSH protocol to ensure that data is exchanged in a secure way. The username of the SSH client is client001 and the password is aabbcc.
II. Network diagram

Figure 1-15 Network diagram for SSH configuration
III. Configuration procedure
The configuration procedure varies with login authentication modes. However, you must complete the following three configuration tasks before any configuration procedure.
First, create an RSA host key pair and server key pair and enable the SSH server.
<Sysname> system-view
[Sysname] rsa local-key-pair create
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
It will take a few minutes.
Input the bits in the modulus[default = 1024]:
Generating keys...
...++++++++++++
...++++++++++++
............++++++++
.....++++++++
......Done!
[Sysname] ssh server enable
Then, you must create a VLAN interface on the switch and assign an IP address, through which the SSH client will be connected with the switch.
[Sysname] interface Vlan-interface 1
[Sysname-Vlan-interface1] ip address 192.168.0.1 255.255.255.0
[Sysname-Vlan-interface1] quit
Finally, you must configure an IP address (192.168.0.2) for the SSH client. This IP address and that of the VLAN interface on the switch must be in the same network segment.
1) Set the SSH authentication mode to password
# Set the authentication mode on the user interface to AAA.
[Sysname] user-interface vty 0 4
[Sysname-ui-vty0-4] authentication-mode scheme
# Set the protocol that a remote user uses to log in to the switch to SSH.
[Sysname-ui-vty0-4] protocol inbound ssh
[Sysname-ui-vty0-4] quit
# Create a local user client001 Set the service type to SSH, Specify commands of level 3 are available to the user.
[Sysname] local-user client001
[Sysname-luser-client001] password simple aabbcc
[Sysname-luser-client001] service-type ssh level 3
[Sysname-luser-client001] quit
The SSH authentication timeout time, number of SSH authentication attempts, and server key update period can be default values. After the above configurations, run SSH1.5 on the client to be connected with the switch, and log in to the switch with username as client001 and password as aabbcc.
2) Set the SSH authentication mode to RSA
# Set the authentication mode on the user interface to AAA.
[Sysname] user-interface vty 0 4
[Sysname-ui-vty0-4] authentication-mode scheme
# Set the command level for the login users to 3.
[Sysname-ui-vty0-4] user privilege level 3
# Set the protocol that a remote user uses to log in to the switch to SSH.
[Sysname-ui-vty0-4] protocol inbound ssh
[Sysname-ui-vty0-4] quit
# Set the SSH user authentication mode to RSA on the switch.
[Sysname] ssh user client001 authentication-type rsa
Here an RSA key pair (including the public and private keys) needs to be generated randomly on the SSH1.5 supporting client software. And you should input the RSA public key (which is a hexadecimal string obtained after using the SSHKEY.EXE software to perform the PKCS coding) to the public key specified by the rsa peer-public-key command on the SSH server in the following way.
# Set the RSA keys on the switch.
[Sysname] rsa peer-public-key Switch001
[Sysname-rsa-public-key] public-key-code begin
[Sysname-rsa-key-code]30818602 818078C4 32AD7864 BB0137AA 516284BB 3F55F0E3
[Sysname-rsa-key-code]F6DD9FC2 4A570215 68D2B3F7 5188A1C3 2B2D40BE D47A08FA
[Sysname-rsa-key-code]CF41AF4E 8CCC2ED0 C5F9D1C5 22FC0625 BA54BCB3 D1CBB500
[Sysname-rsa-key-code]A177E917 642BE3B5 C683B0EB 1EC041F0 08EF60B7 8B6ED628
[Sysname-rsa-key-code]9830ED46 0BA21FDB F55E7C81 5D1A2045 54BFC853 5358E5CF
[Sysname-rsa-key-code]7D7DDF25 03C44C00 E2F49539 5C4B0201 25
[Sysname-rsa-key-code] public-key-code end
[Sysname-rsa-public-key] peer-public-key end
# Directly import the public key of the client if it is stored in the format of a file named Switch001 on the server.
[Sysname] rsa peer-public-key Switch001 import sshkey Switch001
# Specify a public key Switch001 for the user client001.
[Sysname] ssh user client001 assign rsa-key Switch001
& Note:
On the client, you need to specify the corresponding RSA private key of the RSA public key for the SSH user client001.
By now, you can run SSH1.5 on the terminal containing the RSA private key and perform corresponding configuration to establish an SSH connection.
