- Table of Contents
-
- H3C S3610[5510] Series Ethernet Switches Operation Manual-Release 0001-(V1.02)
- 00-1Cover
- 00-2Product Overview
- 01-Login Operation
- 02-VLAN Operation
- 03-IP Address and Performance Operation
- 04-QinQ-BPDU Tunnel Operation
- 05-Port Correlation Configuration Operation
- 06-MAC Address Table Management Operation
- 07-MAC-IP-Port Binding Operation
- 08-MSTP Operation
- 09-Routing Overview Operation
- 10-IPv4 Routing Operation
- 11-IPv6 Routing Operation
- 12-IPv6 Configuration Operation
- 13-Multicast Protocol Operation
- 14-802.1x-HABP-MAC Authentication Operation
- 15-AAA-RADIUS-HWTACACS Operation
- 16-ARP Operation
- 17-DHCP Operation
- 18-ACL Operation
- 19-QoS Operation
- 20-Port Mirroring Operation
- 21-Cluster Management Operation
- 22-UDP Helper Operation
- 23-SNMP-RMON Operation
- 24-NTP Operation
- 25-DNS Operation
- 26-File System Management Operation
- 27-Information Center Operation
- 28-System Maintenance and Debugging Operation
- 29-NQA Operation
- 30-VRRP Operation
- 31-SSH Operation
- 32-Appendix
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 12-IPv6 Configuration Operation | 575 KB |
Table of Contents
1.1.2 Introduction to IPv6 Address
1.1.3 Introduction to IPv6 Neighbor Discovery Protocol
1.1.5 Introduction to IPv6 DNS
1.2 Configuring Basic IPv6 Functions
1.2.1 Configuring the IPv6 Function
1.2.2 Configuring an IPv6 Unicast Address
1.3.1 Configuring a Static Neighbor Entry
1.3.2 Configuring the Maximum Number of Neighbors Dynamically Learned
1.3.3 Configuring Parameters Related to an RA Message
1.3.4 Configuring the Attempts to Send an NS Message for Duplicate Address Detection
1.4 Configuring PMTU Discovery
1.4.1 Configuring a Static PMTU for a Specified IPv6 Address
1.4.2 Configuring the Aging Time for PMTU
1.5 Configuring IPv6 TCP Properties
1.6 Configuring the IPv6 FIB Caching Function
1.7 Configuring the Maximum Number of IPv6 ICMP Error Packets Sent within a Specified Time
1.8.1 Configuring Static IPv6 DNS
1.8.2 Configuring Dynamic IPv6 DNS
1.9 Displaying and Maintaining IPv6
1.10 IPv6 Configuration Example
Chapter 2 IPv6 Application Configuration
2.1 Introduction to IPv6 Application
2.4.1 Configuration Preparation
2.5.1 Configuration Prerequisites
2.5.2 Setting up IPv6 Telnet Connections
2.5.3 Displaying and Maintaining IPv6 Telnet
2.6 Examples of Typical IPv6 Application Configurations
2.7 Troubleshooting IPv6 Application
2.7.1 Unable to Ping a Remote Destination
2.7.2 Unable to Run Traceroute
Chapter 3 Dual Stack Configuration
3.1 Introduction to the Technologies for Implementing IPv6 over IPv4
3.3.1 Enabling IPv4/IPv6 Dual-Stack Supporting
3.4 Displaying Device Operating Mode
Chapter 4 Tunneling Configuration
4.1.1 How IPv6-over-IPv4 Tunneling Works
4.1.2 Manual tunnel and automatic tunnel
4.1.3 IPv6-over-IPv4 Tunneling Modes
4.2 Tunneling Configuration Tasks
4.3 Configuring Manual IPv6 Tunnel
4.3.1 Configuration Prerequisites
4.4 Configuring Automatic IPv4-Compatible IPv6 Tunnel
4.4.1 Configuration Prerequisites
4.5.1 Configuration Prerequisites
4.6.1 Configuration Prerequisites
4.7 Displaying and Maintaining Tunneling Configuration
4.8 Troubleshooting Tunneling Configuration
Chapter 1 IPv6 Configuration
& Note:
The word “router” in this document refers to routers and Layer 3 switches with routing protocols employed.
1.1 IPv6 Overview
Internet protocol version 6 (IPv6), also called IP next generation (IPng), was designed by the Internet Engineering Task Force (IETF) as the successor to Internet protocol version 4 (IPv4). The significant difference between IPv6 and IPv4 is that IPv6 increases the IP address size from 32 bits to 128 bits.
1.1.1 IPv6 Features
I. Header format simplification
IPv6 cuts down some IPv4 header fields or move them to extension headers to reduce the load of basic IPv6 headers, thus making IPv6 packet handling simple and improving the forwarding efficiency. Although the IPv6 address size is four times that of IPv4 addresses, the size of basic IPv6 headers is only twice that of IPv4 headers (excluding the Options field).

Figure 1-1 Comparison between IPv4 header format and IPv6 header format
II. Adequate address space
The source IPv6 address and the destination IPv6 address are both 128 bits (16 bytes) long.IPv6 can provide 3.4 x 1038 addresses to completely meet the requirements of hierarchical address division as well as allocation of public and private addresses.
III. Hierarchical address structure
IPv6 adopts the hierarchical address structure to quicken route search and reduce the system source occupied by the IPv6 routing table by means of route aggregation.
IV. Automatic address configuration
To simplify the host configuration, IPv6 supports stateful address configuration and stateless address configuration.
l Stateful address configuration means that a host acquires an IPv6 address and related information from the server (for example, DHCP server).
l Stateless address configuration means that the host automatically configures an IPv6 address and related information based on its own link-layer address and the prefix information issued by the router.
In addition, a host can generate a link-local address based on its own link-layer address and the default prefix (FE80::/64) to communicate with other hosts on the link.
V. Built-in security
IPv6 uses IPSec as its standard extension header to provide end-to-end security. This feature provides a standard for network security solutions and improves the interoperability between different IPv6 applications.
VI. Support for QoS
The Flow Label field in the IPv6 header allows the device to label packets in a flow and provide special handling for these packets.
VII. Enhanced neighbor discovery mechanism
The IPv6 neighbor discovery protocol means a group of Internet control message protocol version 6 (ICMPv6) messages manages the interaction between neighbor nodes (nodes on the same link).The group of ICMPv6 messages takes the place of address resolution protocol (ARP), Internet control message protocol version 4 (ICMPv4), and ICMPv4 redirection messages to provide a series of other functions.
VIII. Flexible extension headers
IPv6 cancels the Options field in IPv4 packets but introduces multiple extension headers. In this way, IPv6 enhances the flexibility greatly to provide scalability for IP while improving the processing efficiency. The Options field in IPv4 packets contains only 40 bytes, while the size of IPv6 extension headers is restricted by that of IPv6 packets.
1.1.2 Introduction to IPv6 Address
I. IPv6 address format
An IPv6 address is represented as a series of 16-bit hexadecimals, separated by colons. An IPv6 address is divided into eight groups, 16 bits of each group are represented by four hexadecimal numbers which are separated by colons, for example, 2001:0000:130F:0000:0000:09C0:876A:130B.
To simplify the representation of IPv6 addresses, zeros in IPv6 addresses can be handled as follows:
l Leading zeros in each group can be removed. For example, the above-mentioned address can be represented in shorter format as 2001:0:130F:0:0:9C0:876A:130B.
l If an IPv6 address contains two or more consecutive groups of zeros, they can replaced by the double-colon :: option. For example, the above-mentioned address can be represented in the shortest format as 2001:0:130F::9C0:876A:130B.
![]() Caution:
Caution:
The double-colon :: can be used only once in an IPv6 address. Otherwise, the device is unable to determine how many zeros the double-colon represents when converting it to zeros to restore the IPv6 address to a 128-bit address.
An IPv6 address consists of two parts: address prefix and interface ID. The address prefix and the interface ID are respectively equivalent to the network ID to the host ID in an IPv4 address.
An IPv6 address prefix is written in IPv6-address/prefix-length notation, where IPv6-address is an IPv6 address in any of the notations and prefix-length is a decimal number indicating how many bits from the utmost left of an IPv6 address are the address prefix.
II. IPv6 address classification
The type of an IPv6 address is designated by the first several bits called format prefix. Table 1-1 lists the mapping between major address types and format prefixes.
Table 1-1 Mapping between address types and format prefixes
|
Type |
Format prefix (binary) |
IPv6 prefix ID |
|
|
Unicast address |
Unassigned address |
00...0 (128 bits) |
::/128 |
|
Loopback address |
00...1 (128 bits) |
::1/128 |
|
|
Link-local address |
1111111010 |
FE80::/10 |
|
|
Site-local address |
1111111011 |
FEC0::/10 |
|
|
Global unicast address |
other forms |
— |
|
|
Multicast address |
11111111 |
FF00::/8 |
|
|
Anycast address |
Anycast addresses are taken from unicast address space and are not syntactically distinguishable from unicast addresses. |
||
IPv6 addresses mainly fall into three types: unicast address, multicast address and anycast address.
l Unicast address: An identifier for a single interface, similar to an IPv4 unicast address. A packet sent to a unicast address is delivered to the interface identified by that address.
l Multicast address: An identifier for a set of interfaces (typically belonging to different nodes), similar to an IPv4 multicast address. A packet sent to a multicast address is delivered to all interfaces identified by that address.
l Anycast address: An identifier for a set of interfaces (typically belonging to different nodes). A packet sent to an anycast address is delivered to one the interfaces identified by that address (the nearest one, according to the routing protocols’ measure of distance).
& Note:
There are no broadcast addresses in IPv6. Their function is superseded by multicast addresses.
III. Unicast address
There are several forms of unicast address assignment in IPv6, including aggregatable global unicast address, link-local address, and site-local address.
l The aggregatable global unicast address, equivalent to an IPv4 public address, is used for aggregatable links and provided for network service providers. The structure of such a type of address allows efficient routing aggregation to restrict the number of global routing entries.
l The link-local address is used for communication between link-local nodes in neighbor discovery and stateless autoconfiguration. Routers must not forward any packets with link-local source or destination addresses to other links.
l IPv6 unicast site-local addresses are similar to private IPv4 addresses. Routers must not forward any packets with site-local source or destination addresses outside of the site (equivalent to a private network).
l Loopback address: The unicast address 0:0:0:0:0:0:0:1 (represented in shorter format as ::1) is called the loopback address and may never be assigned to any physical interface. Like the loopback address in IPv4, it may be used by a node to send an IPv6 packet to itself.
l Unassigned address: The unicast address :: is called the unassigned address and may not be assigned to any node. Before acquiring a valid IPv6 address, a node may fill this address in the source address field of an IPv6 packet, but may not use it as a destination IPv6 address.
IV. Multicast address
Multicast addresses listed in Table 1-2 are reserved for special purpose.
Table 1-2 Reserved IPv6 multicast addresses
|
Address |
Application |
|
FF01::1 |
Node-local scope all-nodes multicast address |
|
FF02::1 |
Link-local scope all-nodes multicast address |
|
FF01::2 |
Node-local scope all-routers multicast address |
|
FF02::2 |
Link-local scope all-routers multicast address |
|
FF05::2 |
Site-local scope all-routers multicast address |
Besides, there is another type of multicast address: solicited-node address. The solicited-node multicast address is used to acquire the link-layer addresses of neighbor nodes on the same link and is also used for duplicate address detection. Each IPv6 unicast or anycast address has one corresponding solicited-node address. The format of a solicited-node multicast address is as follows:
FF02:0:0:0:0:1:FFXX:XXXX
V. Interface identifier in IEEE EUI-64 format
Interface identifiers in IPv6 unicast addresses are used to identify interfaces on a link and they are required to be unique on that link. Interface identifiers in IPv6 unicast addresses are currently required to be 64 bits long. An interface identifier is derived from the link-layer address of that interface. Interface identifiers in IPv6 addresses are 64 bits long, while MAC addresses are 48 bits long. Therefore, the hexadecimal number FFFE needs to be inserted in the middle of MAC addresses (behind the 24 high-order bits).To ensure the interface identifier obtained from a MAC address is unique, it is necessary to set the universal/local (U/L) bit (the seventh high-order bit) to “1”.Thus, an interface identifier in EUI-64 format is obtained.

Figure 1-2 Convert a MAC address into an EUI-64 address
1.1.3 Introduction to IPv6 Neighbor Discovery Protocol
The IPv6 neighbor discovery protocol (NDP) uses five types of ICMPv6 messages to implement the following functions:
l Address resolution
l Neighbor unreachability detection
l Duplicate address detection
l Router/prefix discovery and address autoconfiguration
l Redirection
Table 1-3 lists the types and functions of ICMPv6 messages used by the NDP.
Table 1-3 Types and functions of ICMPv6 messages
|
ICMPv6 message |
Function |
|
Neighbor solicitation (NS) message |
Used to acquire the link-layer address of a neighbor |
|
Used to verify whether the neighbor is reachable |
|
|
Used to perform a duplicate address detection |
|
|
Neighbor advertisement (NA) message |
Used to respond to a neighbor solicitation message |
|
When the link layer changes, the local node initiates a neighbor advertisement message to notify neighbor nodes of the node information change. |
|
|
Router solicitation (RS) message |
After started, a host sends a router solicitation message to request the router for an address prefix and other configuration information for the purpose of autoconfiguration. |
|
Router advertisement (RA) message |
Used to respond to a router solicitation message |
|
With the RA message suppression disabled, the router regularly sends a router advertisement message containing information such as address prefix and flag bits. |
|
|
Redirect message |
When a certain condition is satisfied, the default gateway sends a redirect message to the source host so that the host can reselect a correct next hop router to forward packets. |
The NDP mainly provides the following functions:
I. Address resolution
Similar to the ARP function in IPv4, a node acquires the link-layer address of neighbor nodes on the same link through NS and NA messages. Figure 1-3 shows how node A acquires the link-layer address of node B.

The address resolution procedure is as follows:
1) Node A multicasts an NS message. The source address of the NS message is the IPv6 address for the interface of node A and the destination address is the solicited-node multicast address of node B. The NS message contains the link-layer address of node A.
2) After receiving the NS message, node B judges whether the destination address of the packet is the corresponding solicited-node multicast address of its own IPv6 address. If yes, node B returns an NA message containing the link-layer address of node B.
3) Node A acquires the link-layer address of node B from the NA message. After that, node A and node B can communicate.
II. Neighbor unreachability detection
After node A acquires the link-layer address of its neighbor node B, node A can verify whether node B is reachable according to NS and NA messages.
1) Node A sends an NS message whose destination address is the IPv6 address of node B.
2) If node A receives an NA message from node B, node A considers that node B is reachable. Otherwise, node B is unreachable.
III. Duplicate address detection
After node A acquires an IPv6 address, it should perform the duplicate address detection to determine whether the address is being used by other nodes (similar to the gratuitous ARP function). The duplication address detection is accomplished through NS and NA messages. Figure 1-4 shows the duplicate address detection procedure.

Figure 1-4 Duplicate address detection
The duplicate address detection procedure is as follows:
1) Node A sends an NS message whose source address is the unassigned address :: and destination address is the corresponding solicited-node multicast address of the IPv6 address to be detected. The NS message contains the IPv6 address.
2) If node B uses this IPv6 address, node B returns an NA message. The NA message contains the IPv6 address of node B.
3) Node A learns that the IPv6 address is being used by node B after receiving the NA message from node B. Otherwise, node B is not using the IPv6 address and node A can use it.
IV. Router/prefix discovery and address autoconfiguration
Router/prefix discovery means that a host acquires the neighbor router, the prefix of the network where the router is located, and other configuration parameters from the received RA message.
Stateless address autoconfiguration means that a host automatically configures an IPv6 address according to the information obtained through router/prefix discovery.
The router/prefix discovery and address autoconfiguration is implemented through RS and RA messages. The router/prefix discovery and address autoconfiguration procedure is as follows:
1) After started, a host sends an RS message to request the router for the address prefix and other configuration information for the purpose of autoconfiguration.
2) The router returns an RA message containing information such as address prefix and flag bits. (The router also regularly sends an RA message.)
V. Redirection
When a host is started, its routing table may contain only the default route to the gateway. When certain conditions are satisfied, the gateway sends an ICMPv6 redirect message to the source host so that the host can select a better next hop router to forward packets (similar to the ICMP redirection function in IPv4).
The gateway will send an IPv6 ICMP redirect message when the following conditions are satisfied:
l The receiving interface and the forwarding interface are the same.
l The selected route itself is not created or modified by an IPv6 ICMP redirect message.
l The selected route is not the default route.
l The forwarded IPv6 packet does not contain any extension header carrying the routing information of intermediate nodes on the forwarding path.
1.1.4 IPv6 PMTU Discovery
The links that a packet passes from the source to the destination may have different MTUs. In IPv6, when the packet size exceeds the MTU of a link, the packet will be fragmented at the source so as to reduce the processing pressure of the forwarding device and utilize network resources rationally.
The path MTU (PMTU) discovery mechanism is to find the minimum MTU on the path from the source to the destination. Figure 1-5 shows the working procedure of the PMTU discovery.

Figure 1-5 Working procedure of the PMTU discovery
The working procedure of the PMTU discovery is as follows:
1) The source host uses its MTU to fragment packets and then sends them to the destination host.
2) If the MTU supported by the packet forwarding interface is less than the size of a packet, the forwarding device will discard the packet and return an ICMPv6 error packet containing the interface MTU to the source host.
3) After receiving the ICMPv6 error packet, the source host uses the returned MTU to fragment the packet again and then sends it.
1.1.5 Introduction to IPv6 DNS
In the IPv6 network, a domain name system (DNS) supporting IPv6 converts domain names into IPv6 addresses. Different from an IPv4 DNS, an IPv6 DNS converts domain names into IPv6 addresses, instead of IPv4 addresses.
However, just like an IPv4 DNS, an IPv6 DNS also covers static domain name resolution and dynamic domain name resolution. The function and implementation of these two types of domain name resolution are the same as those of an IPv4 DNS. For details, refer to DNS module.
1.1.6 Protocol Specifications
Protocol specifications related to IPv6 include:
l RFC 1881: IPv6 Address Allocation Management
l RFC 1887: An Architecture for IPv6 Unicast Address Allocation
l RFC 1981: Path MTU Discovery for IP version 6
l RFC 2375: IPv6 Multicast Address Assignments
l RFC 2460: Internet Protocol, Version 6 (IPv6) Specification.
l RFC 2461: Neighbor Discovery for IP Version 6 (IPv6)
l RFC 2462: IPv6 Stateless Address Autoconfiguration
l RFC 2463: Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 (IPv6) Specification
l RFC 2464: Transmission of IPv6 Packets over Ethernet Networks
l RFC 2526: Reserved IPv6 Subnet Anycast Addresses
l RFC 3307: Allocation Guidelines for IPv6 Multicast Addresses
l RFC 3513: Internet Protocol Version 6 (IPv6) Addressing Architecture
l RFC 3596: DNS Extensions to Support IP Version 6
1.2 Configuring Basic IPv6 Functions
1.2.1 Configuring the IPv6 Function
Table 1-4 Follow these steps to configure the IPv6 function
|
To do... |
Use the command... |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable the IPv6 function |
ipv6 |
Required Disabled by default. |
1.2.2 Configuring an IPv6 Unicast Address
IPv6 site-local addresses and aggregatable global unicast addresses can be configured in either of the following ways:
l EUI-64 format: When the EUI-64 format is adopted to form IPv6 addresses, the IPv6 address prefix of an interface is the configured prefix and the interface identifier is derived from the link-layer address of the interface.
l Manual configuration: IPv6 site-local addresses or aggregatable global unicast addresses are configured manually.
IPv6 link-local addresses can be acquired in either of the following ways:
l Automatic generation: The device automatically generates a link-local address for an interface according to the link-local address prefix (FE80::/64) and the link-layer address of the interface.
l Manual assignment: IPv6 link-local addresses can be assigned manually.
Table 1-5 Follow these steps to configure an IPv6 link-local address
|
To do... |
Use the command... |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enter interface view |
interface interface-type interface-number |
— |
|
|
Configure an IPv6 aggregatable global unicast address or site-local address |
Manually assign an IPv6 address |
ipv6 address { ipv6-address prefix-length | ipv6-address/prefix-length } |
Alternative By default, no site-local address or aggregatable global unicast address is configured for an interface. |
|
Adopt the EUI-64 format to form an IPv6 address |
ipv6 address ipv6-address/prefix-length eui-64 |
||
|
Configure an IPv6 link-local address |
Automatically generate a link-local address |
ipv6 address auto link-local |
Optional By default, after an IPv6 site-local address or aggregatable global unicast address is configured for an interface, a link-local address will be generated automatically. |
|
Manually assign a link-local address for an interface. |
ipv6 address ipv6-address link-local |
||
& Note:
l After an IPv6 site-local address or aggregatable global unicast address is configured for an interface, a link-local address will be generated automatically. The automatically generated link-local address is the same as the one generated by using the ipv6 address auto link-local command. If a link-local address is manually assigned to an interface, this link-local address takes effect. If the manually assigned link-local address is deleted, the automatically generated link-local address takes effect.
l The manual assignment takes precedence over the automatic generation. That is, if you first adopt the automatic generation and then the manual assignment, the manually assigned link-local address will overwrite the automatically generated one. If you first adopt the manual assignment and then the automatic generation, the automatically generated link-local address will not take effect and the link-local address of an interface is still the manually assigned one. You must delete the manually assigned link-local address before adopting the automatic generation.
l You must have carried out the ipv6 address auto link-local command before you carry out the undo ipv6 address auto link-local command. However, if an IPv6 site-local address or aggregatable global unicast address is already configured for an interface, the interface still has a link-local address because the system automatically generates one for the interface. If no IPv6 site-local address or aggregatable global unicast address is configured, the interface has no link-local address.
l When you configure a local IPv6 address or a global unicast address in LoopBack interface view, the prefix can only be 128 bits in length.
1.3 Configuring IPv6 NDP
1.3.1 Configuring a Static Neighbor Entry
The IPv6 address of a neighbor node can be resolved into a link-layer address dynamically through NS and NA messages or statically through manual configuration.
The device uniquely identifies a static neighbor entry according to the IPv6 address and the layer 3 interface ID.
You can configure the corresponding IPv6 address and link-layer address for a layer 3 interface.
Table 1-6 Follow these steps to configure a static neighbor entry
|
To do... |
Use the command... |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure a static neighbor entry |
ipv6 neighbor ipv6-address mac-address { vlan-id port-type port-number | interface interface-type interface-number } |
Required |
1.3.2 Configuring the Maximum Number of Neighbors Dynamically Learned
The device can dynamically acquire the link-layer address of a neighbor node through NS and NA messages. Too large a neighbor table from which neighbor entries can be dynamically acquired may lead to the forwarding performance degradation of the device. Therefore, you can restrict the size of the neighbor table by setting the maximum number of neighbors that an interface can dynamically learn. When the number of dynamically learned neighbors reaches the threshold, the interface will stop learning neighbor information.
Table 1-7 Follow these steps to configure the maximum number of neighbors dynamically learned:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter interface view |
interface interface-type interface-number |
— |
|
Configure the maximum number of neighbors dynamically learned by an interface |
ipv6 neighbors max-learning-num number |
Optional The default value is 2560 |
1.3.3 Configuring Parameters Related to an RA Message
You can configure whether the interface sends an RA message, the interval for sending RA messages, and parameters in RA messages. After receiving an RA message, a host can use these parameters to perform corresponding operations. Table 1-8 lists the configurable parameters in an RA message and their descriptions.
Table 1-8 Parameters in an RA message and their descriptions
|
Parameters |
Description |
|
Cur hop limit |
When sending an IPv6 packet, a host uses the value of this parameter to fill the Hop Limit field in IPv6 headers. Meanwhile, the value of this parameter is equal to the value of the Cur Hop Limit field in response messages of the device. |
|
Prefix information options |
After receiving the prefix information, the hosts on the same link can perform stateless autoconfiguration operations. |
|
M flag |
This field determines whether hosts use the stateful autoconfiguration to acquire IPv6 addresses. If the M flag is set to 1, hosts use the stateful autoconfiguration to acquire IPv6 addresses. Otherwise, hosts use the stateless autoconfiguration to acquire IPv6 addresses, that is, hosts configure IPv6 addresses according to their own link-layer addresses and the prefix information issued by the router. |
|
O flag |
This field determines whether hosts use the stateful autoconfiguration to acquire information other than IPv6 addresses. If the O flag is set to 1, hosts use the stateful autoconfiguration (for example, DHCP server) to acquire information other than IPv6 addresses. Otherwise, hosts use the stateless autoconfiguration to acquire information other than IPv6 addresses. |
|
Router lifetime |
This field is used to set the lifetime of the router that sends RA messages to serve as the default router of hosts. According to the router lifetime in the received RA messages, hosts determine whether the router sending RA messages can serve as the default router of hosts. |
|
Retrans timer |
If a node fails to receive a response message within the specified time after sending an NS message, the node will retransmit it. |
|
Reachable time |
After the neighbor unreachability detection shows that a neighbor is reachable, a node considers the neighbor is reachable within the reachable time. If the node needs to send a packet to a neighbor after the reachable time expires, the node will again confirm whether the neighbor is reachable. |
& Note:
The values of the Retrans Timer field and the reachable time field configured for an interface are sent to hosts via RA messages. Furthermore, the interface sends NS messages at intervals of the value of the Retrans Timer field and considers a neighbor reachable in the time of the value of the reachable time field.
Table 1-9 Follow these steps to configure parameters related to an RA message
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure the current hop limit |
ipv6 nd hop-limit value |
Optional 64 by default. |
|
Enter interface view |
interface interface-type interface-number |
— |
|
Disable the RA message suppression. |
undo ipv6 nd ra halt |
Optional By default, RA messages are suppressed. |
|
Configure the interval for sending RA messages |
ipv6 nd ra interval max-interval-value min-interval-value |
Optional By default, the maximum interval for sending RA messages is 600 seconds, and the minimum interval is 200 seconds. The device sends RA messages at intervals of a random value between the maximum interval and the minimum interval. The minimum interval should be less than or equal to 0.75 times the maximum interval. |
|
Configure the prefix information options in RA messages |
ipv6 nd ra prefix { ipv6-address prefix-length | ipv6-address/prefix-length } valid-lifetime preferred-lifetime [ no-autoconfig | off-link ]* |
Optional By default, no prefix information is configured in RA messages and the IPv6 address of the interface sending RA messages is used as the prefix information. |
|
Set the M flag to 1 |
ipv6 nd autoconfig managed-address-flag |
Optional By default, the M flag bit is set to 0, that is, hosts acquire IPv6 addresses through stateless autoconfiguration |
|
Set the O flag bit to 1. |
ipv6 nd autoconfig other-flag |
Optional By default, the O flag bit is set to 0, that is, hosts acquire other information through stateless autoconfiguration |
|
Configure the router lifetime in RA messages |
ipv6 nd ra router-lifetime value |
Optional 1,800 seconds by default |
|
Set the retrans timer |
ipv6 nd ns retrans-timer value |
Optional By default, the local interface sends NS messages at intervals of 1,000 milliseconds and the Retrans Timer field in RA messages sent by the local interface is equal to 0. |
|
Set the reachable time |
ipv6 nd nud reachable-time value |
Optional By default, the neighbor reachable time on the local interface is 30,000 milliseconds and the Reachable Timer field in RA messages is 0. |
![]() Caution:
Caution:
The maximum interval for sending RA messages should be less than or equal to the router lifetime in RA messages.
1.3.4 Configuring the Attempts to Send an NS Message for Duplicate Address Detection
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter interface view |
interface interface-type interface-number |
— |
|
Configure the attempts to send an NS message for duplicate address detection |
ipv6 nd dad attempts value |
Optional 1 by default. When the value argument is set to 0, the duplicate address detection is disabled. |
1.4 Configuring PMTU Discovery
1.4.1 Configuring a Static PMTU for a Specified IPv6 Address
You can configure a static PMTU for a specified IPv6 address. When forwarding packets, an interface compares the MTU of the interface with the static PMTU of the specified destination IPv6 address, and uses the smaller one to fragment packets.
Table 1-11 Follow these steps to configure a static PMTU for a specified address
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure a static PMTU for a specified IPv6 address |
ipv6 pathmtu ipv6-address [ value ] |
Required By default, no static PMTU is configured. |
1.4.2 Configuring the Aging Time for PMTU
After the MTU of the path from the source host to the destination host is dynamically determined, the source host uses this MTU to send subsequent packets to the destination host. After the aging time expires, the dynamically determined PMTU is deleted and the source host re-determines the MTU to send packets according to the PMTU mechanism.
The aging time is invalid for static PMTU.
Table 1-12 Follow these steps to configure the aging time for PMTU
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure the aging time for PMTU |
ipv6 pathmtu age age-time |
Optional 10 minutes by default. |
1.5 Configuring IPv6 TCP Properties
The IPv6 TCP properties you can configure include:
l synwait timer: When a SYN packet is sent, the synwait timer is triggered. If no response packet is received before the synwait timer expires, the IPv6 TCP connection establishment fails.
l finwait timer: When the IPv6 TCP connection status is FIN_WAIT_2, the finwait timer is triggered. If no packet is received before the finwait timer expires, the IPv6 TCP connection is terminated. If FIN packets are received, the IPv6 TCP connection status becomes TIME_WAIT. If other packets are received, the finwait timer is reset from the last packet and the connection is terminated after the finwait timer expires.
l Size of IPv6 TCP receiving/sending buffer.
Table 1-13 Follow these steps to configure IPv6 TCP properties
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Set the finwait timer of IPv6 TCP packets |
tcp ipv6 timer fin-timeout wait-time |
Optional 675 seconds by default |
|
Set the synwait timer of IPv6 TCP packets |
tcp ipv6 timer syn-timeout wait-time |
Optional 75 seconds by default |
|
Configure the size of IPv6 TCP receiving/sending buffer |
tcp ipv6 window size |
Optional 8 KB by default |
1.6 Configuring the IPv6 FIB Caching Function
After the IPv6 FIB caching function is enabled, the device searches the FIB cache, thus reducing the IP packet searching time and improving the forwarding efficiency.
Through the load sharing mode of IPv6 FIB, the device can decide how to select an equivalent route to forward packets. Currently, there are two load sharing modes:
l Load sharing based on the HASH algorithm: A certain algorithm based on the source IPv6 address and destination IPv6 address is adopted to select an equivalent route to forward packets. The algorithm can ensure that the same equivalent route is used to forward packets with the same source IPv6 address.
l Load sharing based on polling: Each equivalent route is used in turn to forward packets.
Table 1-14 Follow these steps to configure the IPv6 FIB caching function
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enable the IPv6 FIB caching function |
ipv6 fibcache |
Required Disabled by default |
|
|
Configure the IPv6 FIB load sharing mode |
Configure the load sharing based on the HASH algorithm |
ipv6 fib-loadbalance-type hash-based |
Optional By default, the load sharing based on polling is adopted, that is, each equivalent route is used in turn to forward packets. |
|
Configure the load sharing based on polling |
undo ipv6 fib-loadbalance-type hash-based |
||
1.7 Configuring the Maximum Number of IPv6 ICMP Error Packets Sent within a Specified Time
If too many IPv6 ICMP error packets are sent within a short time in a network, network congestion may occur. To avoid network congestion, you can control the maximum number of IPv6 ICMP error packets sent within a specified time. Currently, the token bucket algorithm is adopted.
You can set the capacity of a token bucket, namely, the number of tokens in the bucket. In addition, you can set the update period of the token bucket, namely, the interval for updating the number of tokens in the token bucket to the configured capacity. One token allows one IPv6 ICMP error packet to be sent. Each time an IPv6 ICMP error packet is sent, the number of tokens in a token bucket decreases by 1. If the number of the IPv6 ICMP error packets that are continuously sent out reaches the capacity of the token bucket, the subsequent IPv6 ICMP error packets cannot be sent out until new tokens are put into the token bucket based on the specified update frequency.
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure the capacity of the token bucket controlling the number of IPv6 ICMP error packets sent within a specified time as well as the update period |
ipv6 icmp-error { bucket bucket-size | ratelimit interval }* |
Optional By default, the capacity of a token bucket is 10 and the update period to 100 milliseconds. That is, at most 10 IPv6 ICMP error packets can be sent within an update period. |
1.8 Configuring IPv6 DNS
1.8.1 Configuring Static IPv6 DNS
You can establish the mapping between host name and IPv6 address through the following configuration. You can directly use a host name when applying telnet applications and the system will resolve the host name into an IPv6 address. Each host name can correspond to one IPv6 addresses at most.
Table 1-16 Follow these steps to configure a host name and the corresponding IPv6 address
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure a host name and the corresponding IPv6 address |
ipv6 host hostname ipv6-address |
Required |
1.8.2 Configuring Dynamic IPv6 DNS
If you want to use the dynamic domain name function, you can use the following command to enable the dynamic domain name resolution function. In addition, you should configure a DNS server so that a query request message can be sent to the correct server for resolution. The system can support at most six DNS servers.
Table 1-17 Follow these steps to configure dynamic IPv6 DNS
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable the dynamic domain name resolution function |
dns resolve |
Required Disabled by default. |
|
Configure an IPv6 DNS server |
dns server ipv6 ipv6-address [ interface-type interface-number ] |
Required If the IPv6 address of the DNS server is a link-local address, the interface-type and interface-number arguments are required. |
|
Configure the domain suffix. |
dns domain domain-name |
Required By default, no domain name suffix is configured, that is, the domain name is resolved according to the input information. |
& Note:
The dns resolve and dns domain commands are the same as those of IPv4 DNS. For details about the commands, refer to DNS module.
1.9 Displaying and Maintaining IPv6
Table 1-18 Follow the following steps to display and debug IPv6
|
To do… |
Use the command… |
Remarks |
|
Display DNS domain name suffix information |
display dns domain [ dynamic ] |
Available in any view |
|
Display IPv6 dynamic domain name cache information. |
display dns ipv6 dynamic-host |
|
|
Display DNS server information |
display dns server [ dynamic ] |
|
|
Display the FIB entries |
display ipv6 fib [ ipv6-address ] |
|
|
Display the total number of routes in the FIB cache |
display ipv6 fibcache |
|
|
Display the mapping between host name and IPv6 address |
display ipv6 host |
|
|
Display the brief IPv6 information of an interface |
display ipv6 interface [ interface-type interface-number | brief ] |
|
|
Display neighbor information |
display ipv6 neighbors [ ipv6-address | all | dynamic | interface interface-type interface-number | static | vlan vlan-id ] [ | { begin | exclude | include } text ] |
|
|
Display the total number of neighbor entries satisfying the specified conditions |
display ipv6 neighbors { all | dynamic | static | interface interface-type interface-number | vlan vlan-id } count |
|
|
Display the PMTU information of an IPv6 address |
display ipv6 pathmtu { ipv6-address | all | dynamic | static } |
|
|
Display information related to a specified socket |
display ipv6 socket [ socktype socket-type ] [ task-id socket-id ] |
|
|
Display the statistics of IPv6 packets and IPv6 ICMP packets |
display ipv6 statistics |
|
|
display tcp ipv6 statistics |
||
|
Display the IPv6 TCP connection status |
display tcp ipv6 status |
|
|
Display the statistics of IPv6 UDP packets |
display udp ipv6 statistics |
|
|
Clear IPv6 dynamic domain name cache information |
reset dns ipv6 dynamic-host |
Available in user view |
|
Clear FIB cache entries |
reset ipv6 fibcache |
|
|
Clear IPv6 neighbor information |
reset ipv6 neighbors [ all | dynamic | interface interface-type interface-number | static ] |
|
|
Clear the corresponding PMTU |
reset ipv6 pathmtu { all | static | dynamic} |
|
|
Clear the statistics of IPv6 packets |
reset ipv6 statistics |
|
|
Clear the statistics of all IPv6 TCP packets |
reset tcp ipv6 statistics |
|
|
Clear the statistics of all IPv6 UDP packets |
reset udp ipv6 statistics |
& Note:
The display dns domain and display dns server commands are the same as those of IPv4 DNS. For details about the commands, refer to DNS module.
1.10 IPv6 Configuration Example
I. Network requirements
Two switches are directly connected through two Ethernet ports. The Ethernet ports belong to VLAN2. Different types of IPv6 addresses are configured for the VLAN2 interface to verify the connectivity between two switches. The IPv6 prefix in the EUI-64 format is 2001::/64, the aggregatable global unicast address of Switch A is 3001::1/64, and the aggregatable global unicast address of Switch B is 3001::2/64.
II. Network diagram
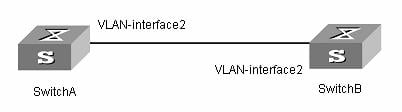
Figure 1-6 Network diagram for IPv6 address configuration
III. Configuration procedure
1) Configure Switch A.
# Enable the IPv6 packet forwarding function on Switch A.
<SwitchA> system-view
[SwitchA] ipv6
# Configure an automatically generated link-local address for the VLAN-interface2.
[SwitchA] interface Vlan-interface 2
[SwitchA-Vlan-interface2] ipv6 address auto link-local
# Configure an EUI-64 address for the VLAN-interface2.
[SwitchA-Vlan-interface2] ipv6 address 2001::/64 eui-64
# Configure an aggregatable global unicast address for the VLAN-interface2.
[SwitchA-Vlan-interface2] ipv6 address 3001::1/64
2) Configure Switch B.
# Enable the IPv6 packet forwarding function.
<SwitchB> system-view
[SwitchB] ipv6
# Configure an automatically generated link-local address for the VLAN-interface2.
[SwitchB] interface Vlan-interface 2
[SwitchB-Vlan-interface2] ipv6 address auto link-local
# Configure an EUI-64 address for the VLAN-interface2.
[SwitchB-Vlan-interface2] ipv6 address 2001::/64 eui-64
# Configure an aggregatable global unicast address for the VLAN-interface2.
[SwitchB-Vlan-interface2] ipv6 address 3001::2/64
IV. Verification
# Display the brief IPv6 information of an interface on Switch A.
[SwitchA-Vlan-interface2] display ipv6 interface vlan-interface 2
Vlan-interface2 current state : UP
Line protocol current state : UP
IPv6 is enabled, link-local address is FE80::20F:E2FF:FE49:8048
Global unicast address(es):
2001::20F:E2FF:FE49:8048, subnet is 2001::/64
3001::1, subnet is 3001::/64
Joined group address(es):
FF02::1:FF00:1
FF02::1:FF49:8048
FF02::2
FF02::1
MTU is 1500 bytes
ND DAD is enabled, number of DAD attempts: 1
ND reachable time is 30000 milliseconds
ND retransmit interval is 1000 milliseconds
Hosts use stateless autoconfig for addresses
# Display the brief IPv6 information of the interface on Switch B.
[SwitchB-Vlan-interface2] display ipv6 interface vlan-interface 2
Vlan-interface2 current state : UP
Line protocol current state : UP
IPv6 is enabled, link-local address is FE80::20F:E2FF:FE00:1
Global unicast address(es):
2001::20F:E2FF:FE00:1, subnet is 2001::/64
3001::2, subnet is 3001::/64
Joined group address(es):
FF02::1:FF00:2
FF02::1:FF00:1
FF02::2
FF02::1
MTU is 1500 bytes
ND DAD is enabled, number of DAD attempts: 1
ND reachable time is 30000 milliseconds
ND retransmit interval is 1000 milliseconds
Hosts use stateless autoconfig for addresses
# On Switch A, ping the link-local address, EUI-64 address, and aggregatable global unicast address of Switch B. If the configurations are correct, the above three types of IPv6 addresses can be pinged.
![]() Caution:
Caution:
When you ping the link-local address, you should use the “–i” parameter to specify the interface for a link-local address.
[SwitchA-Vlan-interface2] ping ipv6 FE80::20F:E2FF:FE00:1 -i vlan-interface 2
PING FE80::20F:E2FF:FE00:1 : 56 data bytes, press CTRL_C to break
Reply from FE80::20F:E2FF:FE00:1
bytes=56 Sequence=1 hop limit=255 time = 80 ms
Reply from FE80::20F:E2FF:FE00:1
bytes=56 Sequence=2 hop limit=255 time = 60 ms
Reply from FE80::20F:E2FF:FE00:1
bytes=56 Sequence=3 hop limit=255 time = 60 ms
Reply from FE80::20F:E2FF:FE00:1
bytes=56 Sequence=4 hop limit=255 time = 70 ms
Reply from FE80::20F:E2FF:FE00:1
bytes=56 Sequence=5 hop limit=255 time = 60 ms
--- FE80::20F:E2FF:FE00:1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 60/66/80 ms
[SwitchA-Vlan-interface2] ping ipv6 2001::20F:E2FF:FE00:1
PING 2001::20F:E2FF:FE00:1 : 56 data bytes, press CTRL_C to break
Reply from 2001::20F:E2FF:FE00:1
bytes=56 Sequence=1 hop limit=255 time = 40 ms
Reply from 2001::20F:E2FF:FE00:1
bytes=56 Sequence=2 hop limit=255 time = 70 ms
Reply from 2001::20F:E2FF:FE00:1
bytes=56 Sequence=3 hop limit=255 time = 60 ms
Reply from 2001::20F:E2FF:FE00:1
bytes=56 Sequence=4 hop limit=255 time = 60 ms
Reply from 2001::20F:E2FF:FE00:1
bytes=56 Sequence=5 hop limit=255 time = 60 ms
--- 2001::20F:E2FF:FE00:1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 40/58/70 ms
[SwitchA-Vlan-interface2] ping ipv6 3001::2
PING 3001::2 : 56 data bytes, press CTRL_C to break
Reply from 3001::2
bytes=56 Sequence=1 hop limit=255 time = 50 ms
Reply from 3001::2
bytes=56 Sequence=2 hop limit=255 time = 60 ms
Reply from 3001::2
bytes=56 Sequence=3 hop limit=255 time = 60 ms
Reply from 3001::2
bytes=56 Sequence=4 hop limit=255 time = 70 ms
Reply from 3001::2
bytes=56 Sequence=5 hop limit=255 time = 60 ms
--- 3001::2 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 50/60/70 ms
Chapter 2 IPv6 Application Configuration
2.1 Introduction to IPv6 Application
IPv6 has become widely used as it is developing with time. Most of IPv6 applications are the same as those of IPv4, including:
l Ping
l Traceroute
l TFTP
l Telnet
2.2 Ping IPv6
The ping ipv6 command is commonly used for testing the reachability of a host. This command sends an ICMPv6 message to the destination host and records the time for the response message to be received. For details about the ping command, see the System Debugging and Maintenance module.
Table 2-1 Follow the following step to ping IPv6
|
To do… |
Use the command… |
Remarks |
|
Ping IPv6 |
ping ipv6 [ -a source-ipv6 | -c count | -m interval | -s packet-size | -t timeout ]* remote-system [ -i interface-type interface-number ] |
Required Available in any view |
![]() Caution:
Caution:
It is required to specify the -i parameter when the destination address is a link local address or multicast address.
2.3 Traceroute IPv6
Traceroute IPv6 is used to record the route of IPv6 packets from source to destination, so as to check whether the link is available and determine the point of trouble.

As Figure 2-1 shows, the traceroute process is as follows:
l The source sends an IP datagram with TTL as 1 (the UDP port number of the carrier UDP packet is a port number that is not available to any application in the destination.
l If the first device receiving the datagram reads the TTL as 1, it will discard the packet and return an ICMP timeout error message. Thus, the source can get the first device’s address in the route.
l The source sends a datagram with TTL as 2 and the second hop device returns a ICMP timeout error message. And the source gets the second device’s address in the route.
l This process continues until the datagram reaches the destination host. As there is no application using the UDP port, the destination returns a “port unreachable” ICMP error message.
l The source receives the “port unreachable” ICMP error message and understands that the packet has reached the destination, thus determines the route of the packet from source to destination.
Table 2-2 Follow the following step to traceroute IPv6
|
To do… |
Use the command… |
Remarks |
|
Traceroute IPv6 |
tracert ipv6 [ -f first-ttl | -m max-ttl | -p port | -q packet-num | -w timeout ]* remote-system |
Required Available in any view |
2.4 TFTP Configuration
IPv6 supports TFTP (Trivial File Transfer Protocol). As a client, the device can download files from or upload files to a TFTP server. For details about TFTP, see the File system Management module.
2.4.1 Configuration Preparation
Start the TFTP server and specify the route to download or upload files. Refer to TFTP server configuration specifications for specific instructions.
2.4.2 TFTP Configuration
I. Manage users’ access to TFTP servers
You can associate an existing ACL with TFTP application. By configuring IPv6 ACL rules, you can enable or disable users' access to specific TFTP servers in a network. For information about defining an ACL, see the ACL module.
Table 2-3 Follow these steps to configure the relation of ACL to TFTP application
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure the relation of ACL to TFTP application to enable or disable the access to a specific TFTP server |
tftp-server ipv6 acl acl-number |
Required ACL is not related to TFTP application by default |
II. Download/Upload files
You can use the commands listed in Table 2-4 to download files from a TFTP server or upload files to a TFTP server.
Table 2-4 Follow the following steps to download/upload files to TFTP servers
|
To do… |
Use the command… |
Remarks |
|
Download files from TFTP server |
tftp ipv6 remote-system [ -i interface-type interface-number ] get source-filename [ destination-filename ] |
Required Available in user view |
|
Upload files to TFTP servers |
tftp ipv6 remote-system [-i interface-type interface-number ] put source-filename [ destination-filename ] |
![]() Caution:
Caution:
It is required to specify the -i parameter when the destination address is a link local address.
2.5 IPv6 Telnet
Telnet protocol belongs to application layer protocols of the TCP/IP protocol suite, and is used to provide remote login and virtual terminals. The device can be used either as a Telnet client or a Telnet server.

Figure 2-2 Providing Telnet services
2.5.1 Configuration Prerequisites
Telnet has three kinds of authentications: None, Password and Scheme, with the default as Password. Refer to Login module for more.
2.5.2 Setting up IPv6 Telnet Connections
Table 2-5 Follow the following steps to set up IPv6 Telnet connections
|
To do… |
Use the command… |
Remarks |
|
Perform the Telnet command at the Telnet client to login and manage other devices |
telnet ipv6 remote-system [ -i interface-type interface-number ] [ port-number ] |
Required Available in user view |
![]() Caution:
Caution:
It is required to specify the -i parameter when the destination address is a link local address.
2.5.3 Displaying and Maintaining IPv6 Telnet
Table 2-6 Follow the following steps to display and debug IPv6 Telnet
|
To do… |
Use the command… |
Remarks |
|
Display the use information of the user’s interface |
display users [ all ] |
Available in any view |
2.6 Examples of Typical IPv6 Application Configurations
2.6.1 Network requirements
In Figure 2-3, SWA, SWB and SWC represent three switches in the public domain. In the same LAN, there is a Telnet server and a TFTP server for providing Telnet service and TFTP service to the switch respectively.
2.6.2 Network diagram

Figure 2-3 IPv6 application network diagram
2.6.3 Configuration procedure
& Note:
You need configure IPv6 address at the switch’s and server’s interfaces and ensure that the route between the switch and the server is accessible before the following configuration.
# Ping SWB’s IPv6 address from SWA.
<SWA> ping ipv6 3003::1
PING 3003::1 : 64 data bytes, press CTRL_C to break
Reply from 3003::1
bytes=56 Sequence=1 hop limit=64 time = 110 ms
Reply from 3003::1
bytes=56 Sequence=2 hop limit=64 time = 31 ms
Reply from 3003::1
bytes=56 Sequence=3 hop limit=64 time = 31 ms
Reply from 3003::1
bytes=56 Sequence=4 hop limit=64 time = 31 ms
Reply from 3003::1
bytes=56 Sequence=5 hop limit=64 time = 31 ms
--- 3003::1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 31/46/110 ms
# Trace the IPv6 route from SWA to SWC.
<SWA> tracert ipv6 3002::1
traceroute to 3002::1 30 hops max,60 bytes packet
1 3003::1 30 ms 0 ms 0 ms
2 3002::1 10 ms 10 ms 0 ms
# SWC download a file from TFTP server 3001::3.
<SWC> tftp ipv6 3001::3 get filetoget flash:/filegothere
.
File will be transferred in binary mode
Downloading file from remote tftp server, please wait....
TFTP: 13 bytes received in 0 second(s)
File downloaded successfully.
# Connect to Telnet server 3001::2.
<SWA> telnet ipv6 3001::2
Trying 3001::2...
Press CTRL+K to abort
Connected to 3001::2 ...
Telnet Server>
# Set up a Telnet connection from SWA to SWC.
Trying 3002::1 ...
Press CTRL+K to abort
Connected to 3002::1 ...
*************************************************************************
* Copyright(c) 2004-2006 Hangzhou H3C Technologies Co., Ltd. *
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
*************************************************************************
<SWC>
2.7 Troubleshooting IPv6 Application
2.7.1 Unable to Ping a Remote Destination
I. Symptom
Unable to ping a remote destination and return an error message.
II. Solution
l Use the display ipv6 interface command to determine the interfaces of the source and the destination and the link-layer protocol between them are in the up state.
l Use the display current-configuration command to check whether the IPv6 forward function is enabled. If not, enable it with the ipv6 command.
l Use the ping ipv6 -t timeout { destination-ipv6-address | hostname } [ -i interface-type interface-number ] command to increase the timeout time limit, so as to determine whether it is due to the timeout limit is too small.
2.7.2 Unable to Run Traceroute
I. Symptom
Unable to trace the route by performing traceroute operations.
II. Solution
l Determine whether you can Ping the destination host.
l If yes, check whether the UDP port used by Traceroute has the required application in the destination host If yes again, specify a UDP port that is unreachable in the tracert ipv6 command.
2.7.3 Unable to Run TFTP
I. Symptom
Unable to download and upload files by performing TFTP operations.
II. Solution
l Determine that the ACL configured for the TFTP server does not block the connection to the TFTP server.
l Determine that the file system of the device is usable. You can check it by running the dir command under the user view.
l Make sure that the route between the device and the TFTP server is reachable.
2.7.4 Unable to Run Telnet
I. Symptom
Unable to login to Telnet server by performing Telnet operations.
II. Solution
l Determine the Telnet server application is running on the server. Check the configuration allows the server reachable.
l Make sure that the route between the device and the TFTP server is reachable.
Chapter 3 Dual Stack Configuration
3.1 Introduction to the Technologies for Implementing IPv6 over IPv4
As Internet expands, the existing IPv4 addresses become tighter and tighter. Although the technologies such as temporary IPv4 address allocation and network address translation (NAT) relieve the shortage of IPv4 addresses to some extent, they not only increases the overhead in address resolution and processing, but also leads to high-level application failures. Furthermore, they will still face the problem that IPv4 addresses will eventually be used up. IPv6 adopting the 128-bit addressing scheme completely solves the problem that the 32-bit addressing scheme of IPv4 is inadequate to meet the demands of Internet growth. Since significant improvements have been made in address space, security, network management, mobility, and QoS, IPv6 becomes one of the core standards for the next generation Internet protocol. IPv6 is compatible with all other protocols except IPv4 in the TCP/IP family. Therefore, IPv6 can completely take the place of IPv4.
Before IPv6 becomes a major protocol, the network using the IPv6 protocol stack is expected to communicate with the Internet currently supported by IPv4. Therefore, an IPv6-IPv4 interworking technology must be developed to ensure the smooth transition from IPv4 to IPv6. In addition, the interworking technology should provide efficient, seamless information transfer. The Internet Engineering Task Force (IETF) set up the next generation transition (NGTRANS) working group to study problems about IPv4-IPv6 transition and efficient, seamless IPv4-IPv6 interworking. Currently, multiple transition technologies and interworking solutions are available. With their own characteristics, they are used to solve communication problems in different transition stages under different environments. Some are mature to become RFC, but some are just Internet drafts and need to be improved.
Currently, there are three major transition technologies: dual protocol stack (RFC2893 obsolete RFC1933), tunneling (RFC2893), and NAT-PT (RFC2766).
& Note:
S3610&S5510 series Ethernet switches support dual stack and tunneling.
3.2 Dual Stack Overview
Dual stack is the most direct approach to making IPv6 nodes compatible with IPv4 nodes. The best way for an IPv6 node to be compatible with an IPv4 node is to maintain a complete IPv4 Stack. A network node that supports both IPv4 and IPv6 is called a dual stack node. A dual stack node configured with an IPv4 and an IPv6 addresses can have both IPv4 and IPv6 packets transmitted.
For an upper layer application supporting both IPv4 and IPv6, either TCP or UDP can be selected at the transport layer, while at network layer, IPv6 stack is preferred. Figure 3-1 illustrates the IPv4/IPv6 dual stack in relation to the IPv4 stack.

Figure 3-1 IPv4/IPv6 dual stack in relation to IPv4 stack (on Ethernet)
3.3 Configuring Dual Stack
3.3.1 Enabling IPv4/IPv6 Dual-Stack Supporting
Table 3-1 Enable IPv4/IPv6 dual-stack supporting
|
Operation |
Command |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure the protocol stack to be supported |
switch-mode { default | dual-ipv4-ipv6 } |
Required By default, only IPv4 protocol stack is supported. |
& Note:
l The configuration listed in Table 3-1 takes effect only after the device is restarted.
l Before enabling dual-stack, you need to enable IPv4/IPv6 dual-stack supporting by using the switch-mode dual-ipv4-ipv6 command. Otherwise, IPv6 packets cannot be forwarded even if dual-stack is enabled.
3.3.2 Configuring Dual-Stack
To implement dual-stack function, you need to enable IPv6 first. Otherwise, the device cannot forward IPv6 packets even if IPv6 addresses are configured for interfaces.
Table 3-2 Follow these steps to configure dual stack on a gateway
|
To do… |
Use the command… |
Remarks |
||
|
Enter system view |
system-view |
— |
||
|
Enable the IPv6 packet forwarding function |
ipv6 |
Required Disabled by default. |
||
|
Enter interface view |
interface interface-type interface-number |
— |
||
|
Configure an IPv4 address for the interface |
ip address ip-address { mask | mask-length } [ sub ] |
Required By default, no IP address is configured |
||
|
Configure an IPv6 address on the interface |
Configure IPv6 global unicast address or local address |
Manually specify an IPv6 address |
ipv6 address { ipv6-address prefix-length | ipv6-address/prefix-length } |
Use either command By default, no local address or global unicast address is configured on an interface |
|
Configure an IPv6 address in the format of EUI-64 |
ipv6 address ipv6-address/prefix-length eui-64 |
|||
|
Configure IPv6 link-local address |
Automatically create IPv6 link-local address |
ipv6 address auto link-local |
Optional By default, after you configured IPv6 local address or global unicast address, the link local address is automatically created |
|
|
Manually specify IPv6 link-local address |
ipv6 address ipv6-address link-local |
|||
3.4 Displaying Device Operating Mode
You can use the display switch-mode command in any view to display the information about device operating mode.
Table 3-3 Display device operating mode
|
Operation |
Command |
|
Display the information about the current system operating mode, the system operating mode after the device reboots the next time, and related system information |
display switch-mode |
Chapter 4 Tunneling Configuration
4.1 Introduction to Tunneling
Tunneling is a Layer 3 tunnel protocol that is widely used in virtual private network (VPN). A tunnel is a virtual point-to-pint connection. Currently, only the virtual interfaces of point-to-point connections can be tunnel interfaces. A tunnel provides a path along which encapsulated datagrams are transmitted. In addition, datagrams are encapsulated/decapsulated on tunnel ends.
The S3610&S5510 Series Switches support IPv6-over-IPv4 tunneling.
4.1.1 How IPv6-over-IPv4 Tunneling Works
The IPv6 over IPv4 tunneling mechanism encapsulates an IPv4 header in IPv6 data packets so that IPv6 packets can pass an IPv4 network through a tunnel to realize interworking between isolated IPv6 networks, as shown in Figure 4-1.
![]() Caution:
Caution:
The devices on both sides of the IPv6 over IPv4 tunnel must support IPv4/IPv6 dual stack.

Figure 4-1 Principle of IPv6 over IPv4 tunnel
The IPv6 over IPv4 tunnel processes packets in the following way:
l A host in the IPv6 network sends an IPv6 packet to the device at the source end of the tunnel.
l After determining according to the routing table that the packet needs to be forwarded through the tunnel, the device at the source end of the tunnel encapsulates an IPv4 header in the IPv6 packet.
l The encapsulated packet goes through the tunnel to reach the device at the destination end of the tunnel. After judging that the destination address of the encapsulated packet is the device at the destination end, the device at the destination end decapsulates the packet.
l The device at the destination end of the tunnel forwards the packet according to the destination address in the decapsulated IPv6 packet. If the destination address is the device itself, the device at the destination end forwards the IPv6 packet to the upper-layer protocol for processing.
4.1.2 Manual tunnel and automatic tunnel
An IPv6 over IPv4 tunnel can be established between hosts, between hosts and devices, and between devices. The tunnel destination needs to forward the packet if the tunnel destination is not the eventual destination of the IPv6 packet.
According to the way the IPv4 address of the tunnel destination is acquired, tunnels are divided into manual tunnel and automatic tunnel.
l If the tunnel destination is not the eventual destination of the IPv6 packet, the device at the destination end of the tunnel (usually a router) will decapsulate the IPv6 packet and forward it to the eventual destination after the IPv6 packet reaches the tunnel destination. In this case, the IPv4 address of the tunnel destination cannot be acquired from the destination address of the IPv6 packet and it needs to be configured manually. Such a tunnel is called manual tunnel.
l If the tunnel destination is just the eventual destination of the IPv6 packet, an IPv4 address can be embedded into an IPv6 address so that the IPv4 address of the tunnel destination can automatically be acquired from the destination address of the IPv6 packet. Such a tunnel is called automatic tunnel.
4.1.3 IPv6-over-IPv4 Tunneling Modes
According to the way the IPv6 packet is encapsulated, IPv6 over IPv4 tunnels are divided into the following modes:
l IPv6 manually configured tunnel
l Automatic IPv4-compatible IPv6 tunnel
l 6to4 tunnel
l Intra-site automatic tunnel addressing protocol (ISATAP)
Among the above tunnels, the IPv6 manually configured tunnel is manual tunnels, while the automatic IPv4 compatible IPv6 tunnel, 6to4 tunnel, and ISATAP tunnel are automatic tunnels.
1) IPv6 manually configured tunnel
A manually configured tunnel is a point-to-point link. One link is a separate tunnel. The IPv6 manually configured tunnel is mainly used for stable connections requiring regular secure communication between two border routers or between a border router and a host, or for connections to remote IPv6 networks.
2) Automatic IPv4-compatible IPv6 tunnel
An automatic IPv4-compatible IPv6 tunnel is a point-to-multipoint link. IPv4-compatible IPv6 addresses are adopted at both ends of such a tunnel. The address format is 0:0:0:0:0:0:a.b.c.d/96, where a.b.c.d represents an embedded IPv4 address. The tunnel destination is automatically determined by the embedded IPv4 address, which makes it easy to create a tunnel for IPv6 over IPv4. However, because an automatic IPv4-compatible IPv6 tunnel must use IPv4-compatible IPv6 addresses and it is still dependent on IPv4 addresses. Therefore, automatic IPv4-compatible IPv6 tunnels have limitations.
3) 6to4 tunnel
An automatic 6to4 tunnel is a point-to-multipoint tunnel and is used to connect multiple isolated IPv6 domains over an IPv4 network to remote IPv6 networks. The embedded IPv4 address in an IPv6 address is used to automatically acquire the destination of the tunnel. The automatic 6to4 tunnel adopts 6to4 addresses. The address format is 2002:abcd:efgh subnet number::interface ID/64, where abcd:efgh represents the 32-bit source IPv4 address of the 6to4 tunnel, denoted in a hexadecimals. For example, 1.1.1.1 can be represented by 0101:0101. The tunnel destination is automatically determined by the embedded IPv4 address, which makes it easy to create a 6to4 tunnel.
Since the 16-bit subnet number of the 64-bit address prefix in 6to4 addresses can be customized and the first 48 bits in the address prefix are fixed by a permanent value and the IPv4 address of the tunnel source or destination, it is possible that IPv6 packets can be forwarded by the tunnel. A 6to4 tunnel interconnects IPv6 networks and overcomes the limitations of an automatic IPv4-compatible IPv6 tunnel.
4) ISATAP tunnel
With the deployment of the IPv6 technology, there will be more and more IPv6 hosts in the existing IPv4 network. The ISATAP tunneling technology provides a satisfactory solution for IPv6 deployment. An ISATAP tunnel is a point-to-point automatic tunneling technology. The destination of a tunnel can automatically be acquired by the embedded IPv4 address in the destination address of an IPv6 packet. When an ISATAP tunnel is used, the destination address of an IPv6 packet and the IPv6 address of a tunnel interface both adopt special addresses: ISATAP addresses. The ISATAP address format is prefix(64bit):0:5EFE:ip-address. The ip-address is in the form of a.b.c.d or abcd:efgh, where abcd:efgh represents a 32-bit source IPv4 address. Through the embedded IPv4 address, an ISATAP tunnel can automatically be created to transfer IPv6 packets. The ISATAP tunnel is mainly used for connection between IPv6 routers or between a host and an IPv6 router in the IPv4 network.

4.1.4 Expedite termination
For a tunnel packet arriving at the device, if the source IP address matches the address of the expedite termination subnet, the hardware driver sends the packet to an IPv6 tunnel protocol engine to forward or sends it to the CPU for processing. If the tunnel packet needs forwarding, the IPv6 tunnel protocol engine removes the IP encapsulation to obtain the original IPv6 packet and then forwards it directly. If the destination of the tunnel packet is the device itself, the device sends it to the CPU for processing.
The IPv6 over IPv4 tunnel supports the expedite termination function. There are two cases:
l The expediting subnet is not applicable to a manual tunnel (for example, IPv6 manually configured tunnel). After the expedite termination function is enabled, the system will automatically consider the destination address of a tunnel as the address of the expedite termination subnet, and the subnet mask as 255.255.255.255.
l For automatic tunnels (for example, automatic IPv4-compatible IPv6 tunnel, automatic 6to4 tunnel, and ISATAP tunnel), you must carry out the expediting subnet command to designate an IP address and subnet for the expedite termination subnet after carrying out the expediting enable command.
The expedite termination function must be enabled if you need to run a dynamic routing protocol (such as OSPFv3) on a manually established tunnel, ping a link-local address configured on a tunnel interface, or automatically obtain a global IPv6 address through an ISATAP tunnel.
4.2 Tunneling Configuration Tasks
Table 4-1 Complete these tasks to configure the tunneling feature
|
To do… |
Use the command… |
Related section |
|
|
Configure an IPv6-over-IPv4 tunnel |
Configuring a manual IPv6 tunnel |
Optional Perform this configuration based on actual networking application. |
Section 4.3 Configuring Manual IPv6 Tunnel". |
|
Configuring an automatic IPv4-compatible IPv6 tunnel |
Optional Perform this configuration based on actual networking application. |
Section 4.4 Configuring Automatic IPv4-Compatible IPv6 Tunnel". |
|
|
Configuring a 6-to-4 tunnel |
Optional Perform this configuration based on actual networking application. |
Section 4.5 Configuring 6to4 Tunnel". |
|
|
Configuring an ISATAP tunnel |
Optional Perform this configuration based on actual networking application. |
Section 4.6 Configuring ISATAP Tunnel". |
|
4.3 Configuring Manual IPv6 Tunnel
4.3.1 Configuration Prerequisites
IP addresses are configured for interfaces such as VLAN interface and loopback interface on the device so that they can communicate. These interfaces serve as the source interface of the tunnel interface to ensure that the tunnel destination address is reachable.
4.3.2 Configuration Procedure
Table 4-2 Follow these steps to configure a manual IPv6 tunnel
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enable the IPv6 packet forwarding function |
ipv6 |
Required By default, the IPv6 packet forwarding function is disabled. |
|
|
Create a tunnel interface and enter tunnel interface view |
interface Tunnel number |
Required By default, there is no tunnel interface on the device. |
|
|
Configure an IPv6 address for the tunnel interface |
Configure an IPv6 link-local address |
ipv6 address auto link-local |
Optional By default, after an interface is configured with a local IPv6 address or global unicast address, the link-local address is generated automatically. |
|
ipv6 address ipv6-address link-local |
|||
|
Configure a local IPv6 address or global unicast address |
ipv6 address { ipv6-address prefix-length | ipv6-address/prefix-length } |
Either is required. By default, no IPv6 global unicast address or local IPv6 address is configured for a tunnel interface. |
|
|
ipv6 address ipv6-address/prefix-length eui-64 |
|||
|
Configure the tunnel to a manual IPv6 tunnel. |
tunnel-protocol ipv6-ipv4 |
Optional The default tunnel mode is manual IPv6. The same tunnel mode should be configured at both ends of the tunnel. Otherwise, packet delivery will fail. |
|
|
Configure a source address for the tunnel interface |
source { ip-address | interface-type interface-num } |
Required By default, no source address is configured for the tunnel interface. |
|
|
Configure a destination address for the tunnel interface |
destination ip-address |
Required By default, no destination address is configured for the tunnel interface. |
|
|
Configure the service-loop group ID to be referenced by the tunnel interface |
aggregation-group aggregation-group-id |
Required |
|
|
Enable the expedite termination function |
expediting enable |
Optional By default, the expedite termination function is disabled. |
|
![]() Caution:
Caution:
l After the tunnel interface is deleted, all the above features configured on the tunnel interface will be deleted.
l If the addresses of the tunnel interfaces at the two ends of a tunnel are not in the same network segment, a forwarding route through the tunnel to the peer must be configured so that the encapsulated packet can be forwarded normally. You can configure static or dynamic routes. For the detailed configuration, refer to “IPv4 Routing” or “IPv6 Routing” module.
l When you configure a static route, you need to configure a route to the destination address (the destination IP address of the packet, instead of the IPv4 address of the tunnel destination) and set the next-hop to the tunnel interface number or network address at the local end of the tunnel. Such configurations must be performed at both ends of the tunnel.
l Before configuring dynamic routes, you must enable the dynamic routing protocol on the tunnel interfaces at both ends of the tunnel.
4.3.3 Configuration Example
I. Network requirements
Two IPv6 networks are connected through a manual IPv6 tunnel between SwitchA and SwitchB. As shown in Figure 4-3, Vlan-interface100 on SwitchA and Vlan-interface100 on SwitchB can communicate with each other normally and the packet route is reachable.
II. Network diagram

Figure 4-3 Network diagram for a manual IPv6 tunnel
III. Configuration procedure
The following example shows how to configure a manual IPv6 tunnel between SwitchA and SwitchB. Before configuration, you must specify IP addresses for the source and destination of the tunnel.
1) Configuration on SwitchA
# Configure an IPv4 address for Vlan-interface100.
<SwitchA> system-view
[SwitchA] interface Vlan-interface 100
[SwitchA-Vlan-interface100] ip address 192.168.100.1 255.255.255.0
[SwitchA-Vlan-interface100] quit
# Enable the IPv6 forwarding function.
[SwitchA] ipv6
# Configure a service-loop group. (Note that to add a port to a service-loop group, you need to disable STP on the port.)
[SwitchA] link-aggregation group 1 mode manual
[SwitchA] link-aggregation group 1 service-type tunnel
[SwitchA] interface Ethernet 1/0/1
[SwitchA-Ethernet1/0/1] stp disable
[SwitchA-Ethernet1/0/1] port link-aggregation group 1
[SwitchA-Ethernet1/0/1] quit
# Configure a manual IPv6 tunnel.
[SwitchA] interface Tunnel 0
[SwitchA-Tunnel0] ipv6 address 3001::1/64
[SwitchA-Tunnel0] source Vlan-interface 100
[SwitchA-Tunnel0] destination 192.168.50.1
[SwitchA-Tunnel0] tunnel-protocol ipv6-ipv4
# Configure service-loop group 1 to be referenced by the tunnel in tunnel interface view.
[SwitchA-Tunnel0] aggregation-group 1
2) Configuration on SwitchB
# Configure an IPv4 address for Vlan-interface100.
<SwitchB> system-view
[SwitchB] interface Vlan-interface 100
[SwitchB-Vlan-interface100] ip address 192.168.50.1 255.255.255.0
[SwitchB-Vlan-interface100] quit
# Enable the IPv6 forwarding function.
[SwitchB] ipv6
# Configure a service-loop group. (Note that to add a port to a service-loop group, you need to disable STP on the port.)
[SwitchB] link-aggregation group 2 mode manual
[SwitchB] link-aggregation group 2 service-type tunnel
[SwitchB] interface Ethernet 1/0/1
[SwitchB-Ethernet1/0/1] stp disable
[SwitchB-Ethernet1/0/1] port link-aggregation group 2
[SwitchB-Ethernet1/0/1] quit
# Configure a manual IPv6 tunnel.
[SwitchB] interface Tunnel 0
[SwitchB-Tunnel0] ipv6 address 3001::2/64
[SwitchB-Tunnel0] source Vlan-interface 100
[SwitchB-Tunnel0] destination 192.168.100.1
[SwitchB-Tunnel0] tunnel-protocol ipv6-ipv4
# Configure service-loop group 2 to be referenced by the tunnel in tunnel interface view.
[SwitchB-Tunnel0] aggregation-group 2
IV. Configuration verification
After the above configurations, ping the IPv6 address of the peer tunnel interface from one switch.
4.4 Configuring Automatic IPv4-Compatible IPv6 Tunnel
4.4.1 Configuration Prerequisites
IP addresses are configured for interfaces such as VLAN interface and loopback interface on the device so that they can communicate. These interfaces serve as the source interface of the virtual tunnel interface to ensure that the tunnel destination address is reachable.
4.4.2 Configuration Procedure
Table 4-3 Follow these steps to configure an automatic IPv4-compatible IPv6 tunnel
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enable the IPv6 packet forwarding function |
ipv6 |
Required By default, the IPv6 packet forwarding function is disabled. |
|
|
Create a tunnel interface and enter tunnel interface view |
interface Tunnel number |
Required By default, there is no tunnel interface on the device. |
|
|
Configure an IPv6 address for the tunnel interface |
Configure an IPv6 link-local address |
ipv6 address auto link-local |
Optional. By default, after an interface is configured with a local IPv6 address or global unicast address, the link-local address is generated automatically. |
|
ipv6 address ipv6-address link-local |
|||
|
Configure a local IPv6 address or global unicast address |
ipv6 address { ipv6-address prefix-length | ipv6-address/prefix-length } |
Either is required. By default, no IPv6 global unicast address or local IPv6 address is configured for a tunnel interface. |
|
|
ipv6 address ipv6-address/prefix-length eui-64 |
|||
|
Configure an automatic IPv4-compatible IPv6 tunnel |
tunnel-protocol ipv6-ipv4 auto-tunnel |
Required By default, the tunnel is a manually configured tunnel. The same tunnel mode should be configured at both ends of the tunnel. Otherwise, packet delivery will fail. |
|
|
Configure a source address for the tunnel interface |
source { ip-address | interface-type interface-num } |
Required By default, no source address is configured for the tunnel interface. |
|
|
Configure the service-loop group ID to be referenced by the tunnel interface |
aggregation-group aggregation-group-id |
Required |
|
|
Enable the expedite termination function |
expediting enable |
Optional By default, the expedite termination function is disabled. |
|
|
Configure an address and mask for the expedite termination subnet |
expediting subnet ip-address mask |
Optional By default, no expedite termination subnet is configured for a tunnel. |
|
![]() Caution:
Caution:
l Only one tunnel can automatically be configured at the same tunnel source.
l No destination address needs to be configured for an automatic IPv4-compatible IPv6 tunnel.
l If the addresses of the tunnel interfaces at the two ends of a tunnel are not in the same network segment, a forwarding route through the tunnel to the peer must be configured so that the encapsulated packet can be forwarded normally. You can configure static or dynamic routes. For the detailed configuration, refer to “IPv4 Routing” or “IPv6 Routing” module.
l When you configure a static route, you need to configure a route to the destination address (the destination IP address of the packet, instead of the IPv4 address of the tunnel destination) and set the next-hop to the tunnel interface number or network address at the local end of the tunnel. Such a route must be configured at both ends of the tunnel.
4.4.3 Configuration Example
I. Network requirements
Between SwitchA and SwitchB is an IPv4 network. It is required that an IPv6 connection be established through an automatic IPv4-compatible IPv6 tunnel between the two dual-stack routers.
II. Network diagram

Figure 4-4 Network diagram for an automatic IPv4-compatible IPv6 tunnel
III. Configuration procedure
The following example shows how to configure an automatic IPv4-compatible IPv6 tunnel between SwitchA and SwitchB. No address needs to be specified for the tunnel destination because the destination can automatically obtain an address from the embedded IPv4 address in an IPv4-compatible IPv6 address.
1) Configuration on SwitchA
# Enable the IPv6 forwarding function.
<SwitchA> system-view
[SwitchA] ipv6
# Configure an IPv4 address for Vlan-interface100.
[SwitchA] interface Vlan-interface 100
[SwitchA-Vlan-interface100] ip address 2.1.1.1 255.0.0.0
[SwitchA-Vlan-interface100] quit
# Configure a service-loop group. (Note that to add a port to a service-loop group, you need to disable STP on the port.)
[SwitchA] link-aggregation group 1 mode manual
[SwitchA] link-aggregation group 1 service-type tunnel
[SwitchA] interface Ethernet 1/0/1
[SwitchA-Ethernet1/0/1] stp disable
[SwitchA-Ethernet1/0/1] port link-aggregation group 1
[SwitchA-Ethernet1/0/1] quit
# Configure an automatic IPv4-comptabile IPv6 tunnel.
[SwitchA] interface Tunnel 0
[SwitchA-Tunnel0] ipv6 address ::2.1.1.1/96
[SwitchA-Tunnel0] source Vlan-interface 100
[SwitchA-Tunnel0] tunnel-protocol ipv6-ipv4 auto-tunnel
# Configure service-loop group 1 to be referenced by the tunnel in tunnel interface view.
[SwitchA-Tunnel0] aggregation-group 1
2) Configuration on SwitchB
# Enable the IPv6 forwarding function.
<SwitchB> system-view
[SwitchB] ipv6
# Configure an IPv4 address for Vlan-interface100.
[SwitchB] interface Vlan-interface 100
[SwitchB-Vlan-interface100] ip address 2.1.1.2 255.0.0.0
[SwitchB-Vlan-interface100] quit
# Configure a service-loop group.
[SwitchB] link-aggregation group 2 mode manual
[SwitchB] link-aggregation group 2 service-type tunnel
[SwitchB] interface Ethernet 1/0/1
[SwitchB-Ethernet1/0/1] stp disable
[SwitchB-Ethernet1/0/1] port link-aggregation group 2
[SwitchB-Ethernet1/0/1] quit
# Configure an automatic IPv4-comptabile IPv6 tunnel.
[SwitchB] interface Tunnel 0
[SwitchB-Tunnel0] ipv6 address ::2.1.1.2/96
[SwitchB-Tunnel0] source Vlan-interface 100
[SwitchB-Tunnel0] tunnel-protocol ipv6-ipv4 auto-tunnel
# Configure service-loop group 2 to be referenced by the tunnel in tunnel interface view.
[SwitchB-Tunnel0] aggregation-group 2
IV. Configuration verification
After the above configurations, ping the IPv4-compatible IPv6 address of the peer tunnel interface from one router.
# Ping the IPv4-compatible IPv6 address of the tunnel peer from Router A.
PING ::2.1.1.2 : 56 data bytes, press CTRL_C to break
Reply from ::2.1.1.2
bytes=56 Sequence=1 hop limit=255 time = 219 ms
Reply from ::2.1.1.2
bytes=56 Sequence=2 hop limit=255 time = 15 ms
Reply from ::2.1.1.2
bytes=56 Sequence=3 hop limit=255 time = 31 ms
Reply from ::2.1.1.2
bytes=56 Sequence=4 hop limit=255 time = 31 ms
Reply from ::2.1.1.2
bytes=56 Sequence=5 hop limit=255 time = 32 ms
--- ::2.1.1.2 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 15/65/219 ms
4.5 Configuring 6to4 Tunnel
4.5.1 Configuration Prerequisites
IP addresses are configured for interfaces such as VLAN interface and loopback interface on the device so that they can communicate. These interfaces serve as the source interface of the virtual tunnel interface to ensure that the tunnel destination address is reachable.
4.5.2 Configuration Procedure
Table 4-4 Follow these steps to configure a 6to4 tunnel
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enable the IPv6 packet forwarding function |
ipv6 |
Required By default, the IPv6 packet forwarding function is disabled. |
|
|
Create a tunnel interface and enter tunnel interface view |
interface Tunnel number |
Required By default, there is no tunnel interface on the device. |
|
|
Configure an IPv6 address for the tunnel interface |
Configure an IPv6 link-local address |
ipv6 address auto link-local |
Optional By default, after an interface is configured with a local IPv6 address or global unicast address, the link-local address is generated automatically. |
|
ipv6 address ipv6-address link-local |
|||
|
Configure a local IPv6 address or global unicast address |
ipv6 address { ipv6-address prefix-length | ipv6-address/prefix-length } |
Either is required. By default, no IPv6 global unicast address or local IPv6 address is configured for a tunnel interface. |
|
|
ipv6 address ipv6-address/prefix-length eui-64 |
|||
|
Set the tunnel to a 6to4 tunnel |
tunnel-protocol ipv6-ipv4 6to4 |
Required By default, the tunnel is a manually configured tunnel. The same tunnel mode should be configured at both ends of the tunnel. Otherwise, packet delivery will fail. |
|
|
Configure a source address for the tunnel interface |
source { ip-address | interface-type interface-num } |
Required By default, no source address is configured for the tunnel interface. |
|
|
Configure the service-loop group ID to be referenced by the tunnel interface |
aggregation-group aggregation-group-id |
Required |
|
|
Enable the expedite termination function |
expediting enable |
Optional By default, the expedite termination function is disabled. |
|
|
Configure an address and mask for the expedite termination subnet |
expediting subnet ip-address mask |
Optional By default, no expedite termination subnet is configured for a tunnel. |
|
![]() Caution:
Caution:
l Only one tunnel can automatically be configured at the same tunnel source.
l No destination address needs to be configured for an automatic tunnel because the destination can automatically obtain an address from the embedded IPv4 address in an IPv4-compatible IPv6 address.
l If the addresses of the tunnel interfaces at the two ends of a tunnel are not in the same network segment, a forwarding route through the tunnel to the peer must be configured so that the encapsulated packet can be forwarded normally. You can configure static or dynamic routes. For the detailed configuration, refer to “IPv4 Routing” or “IPv6 Routing” module.
l When you configure a static route, you need to configure a route to the destination address (the destination IP address of the packet, instead of the IPv4 address of the tunnel destination) and set the next-hop to the tunnel interface number or network address at the local end of the tunnel. Such a route must be configured at both ends of the tunnel.
4.5.3 Configuration Example
I. Network requirements
Isolated IPv6 networks are interconnected through a 6to4 tunnel established in the IPv4 network.
II. Network diagram

Figure 4-5 Network diagram for a 6to4 tunnel
III. Configuration procedure
The following example shows how to configure a 6to4 tunnel between border switches on isolated IPv6 networks. After the IPv4 address 2.1.1.1 is converted into an IPv6 address, the address prefix is 2002:0201:0101::/64. The configured static route directs all traffic destined for the IPv6 address with the prefix 2002::/16 to the tunnel interface of the 6to4 tunnel.
1) Configuration on SwitchA.
# Enable the IPv6 forwarding function.
<SwitchA> system-view
[SwitchA] ipv6
# Configure an IPv4 address for Vlan-interface100.
[SwitchA] interface Vlan-interface 100
[SwitchA-Vlan-interface100] ip address 2.1.1.1 24
[SwitchA-Vlan-interface100] quit
# Configure a route from Vlan-interface100 of SwitchA to Vlan-interface100 of SwitchB. (Here the next-hop address of the static route is represented by [nexthop]. In practice, you should configure the real next-hop address according to the networking.)
[SwitchA] ip route-static 5.1.1.1 24 [nexthop]
# Configure an IPv6 address for Vlan-interface101.
[SwitchA] interface Vlan-interface 101
[SwitchA-Vlan-interface101] ipv6 address 2002:0201:0101:1::1/64
[SwitchA-Vlan-interface101] quit
# Configure a service-loop group. (Note that to add a port to a service-loop group, you need to disable STP on the port.)
[SwitchA] link-aggregation group 1 mode manual
[SwitchA] link-aggregation group 1 service-type tunnel
[SwitchA] interface Ethernet 1/0/1
[SwitchA-Ethernet1/0/1] stp disable
[SwitchA-Ethernet1/0/1] port link-aggregation group 1
[SwitchA-Ethernet1/0/1] quit
# Configure a 6to4 tunnel.
[SwitchA] interface Tunnel 0
[SwitchA-Tunnel0] ipv6 address 2002:201:101::1/64
[SwitchA-Tunnel0] source Vlan-interface 100
[SwitchA-Tunnel0] tunnel-protocol ipv6-ipv4 6to4
[SwitchA-Tunnel0] quit
# Configure the tunnel to reference service-loop group 1.
[SwitchA-Tunnel0] aggregation-group 1
[SwitchA-Tunnel0] quit
# Configure a static route whose destination address is 2002::16 and next-hop is the tunnel interface.
[SwitchA] ipv6 route-static 2002:: 16 Tunnel 0
2) Configuration on SwitchB
# Enable the IPv6 forwarding function.
<SwitchB> system-view
[SwitchB] ipv6
# Configure an IPv6 address for Vlan-interface100.
[SwitchB] interface Vlan-interface 100
[SwitchB-Vlan-interface100] ip address 5.1.1.1 24
[SwitchB-Vlan-interface100] quit
# Configure a route from Vlan-interface100 of SwitchA to Vlan-interface100 of SwitchB. (Here the next-hop address of the static route is represented by [nexthop]. In practice, you should configure the real next-hop address according to the networking.)
[SwitchB] ip route-static 2.1.1.1 24 [nexthop]
# Configure an IPv6 address for Vlan-interface101.
[SwitchB] interface Vlan-interface 101
[SwitchB-Vlan-interface101] ipv6 address 2002:0501:0101:1::1/64
[SwitchB-Vlan-interface101] quit
# Configure a service-loop group. (Note that to add a port to a service-loop group, you need to disable STP on the port.)
[SwitchB] link-aggregation group 2 mode manual
[SwitchB] link-aggregation group 2 service-type tunnel
[SwitchB] interface Ethernet 1/0/1
[SwitchB-Ethernet1/0/1] stp disable
[SwitchB-Ethernet1/0/1] port link-aggregation group 2
[SwitchB-Ethernet1/0/1] quit
# Configure a 6to4 tunnel.
[SwitchB] interface Tunnel 0
[SwitchB-Tunnel0] ipv6 address 2002:0501:0101::1/64
[SwitchB-Tunnel0] source Vlan-interface 100
[SwitchB-Tunnel0] tunnel-protocol ipv6-ipv4 6to4
# Configure service-loop group 2 to be referenced by the tunnel in tunnel interface view.
[SwitchB-Tunnel0] aggregation-group 2
[SwitchB-Tunnel0] quit
# Configure a static route whose destination address is 2002::16 and next-hop is the tunnel interface.
[SwitchB] ipv6 route-static 2002:: 16 Tunnel 0
IV. Configuration verification
After the above configuration, ping PC 2 from PC 1 or ping PC1 from PC 2.
4.6 Configuring ISATAP Tunnel
4.6.1 Configuration Prerequisites
IP addresses are configured for interfaces such as VLAN interface and loopback interface on the device so that they can communicate. These interfaces serve as the source interface of the virtual tunnel interface to ensure that the tunnel destination address is reachable.
4.6.2 Configuration Procedure
Table 4-5 Follow these steps to configure an ISATAP tunnel
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enable the IPv6 packet forwarding function |
ipv6 |
Required By default, the IPv6 packet forwarding function is disabled. |
|
|
Create a tunnel interface and enter tunnel interface view |
interface Tunnel number |
Required By default, there is no tunnel interface on the device. |
|
|
Configure an IPv6 address for the tunnel interface |
Configure an IPv6 link-local address |
ipv6 address auto link-local |
Optional By default, after an interface is configured with a local IPv6 address or global unicast address, the link-local address is generated automatically. |
|
ipv6 address ipv6-address link-local |
|||
|
Configure a local IPv6 address or global unicast address |
ipv6 address { ipv6-address prefix-length | ipv6-address/prefix-length } |
Either is required. By default, no IPv6 global unicast address or local IPv6 address is configured for a tunnel interface. |
|
|
ipv6 address ipv6-address/prefix-length eui-64 |
|||
|
Set the tunnel to an ISATAP tunnel |
tunnel-protocol ipv6-ipv4 isatap |
Required By default, the tunnel is a manually configured tunnel. The same tunnel mode should be configured at both ends of the tunnel. Otherwise, packet delivery will fail. |
|
|
Configure a source address for the tunnel interface |
source { ip-address | interface-type interface-num } |
Required By default, no source address is configured for the tunnel interface. |
|
|
Configure the service-loop group ID to be referenced by the tunnel interface |
aggregation-group aggregation-group-id |
Required |
|
|
Enable the expedite termination function |
expediting enable |
Optional By default, the expedite termination function is disabled. |
|
|
Configure an address and mask for the expedite termination subnet |
expediting subnet ip-address mask |
Optional By default, no expedite termination subnet is configured for a tunnel. |
|
![]() Caution:
Caution:
l If the addresses of the tunnel interfaces at the two ends of a tunnel are not in the same network segment, a forwarding route through the tunnel to the peer must be configured so that the encapsulated packet can be forwarded normally. You can configure static or dynamic routes. For the detailed configuration, refer to “IPv4 Routing” or “IPv6 Routing” module.
l When you configure a static route, you need to configure a route to the destination address (the destination IP address of the packet, instead of the IPv4 address of the tunnel destination) and set the next-hop to the tunnel interface number or network address at the local end of the tunnel. Such a route must be configured at both ends of the tunnel.
4.6.3 Configuration Example
I. Network requirements
The destination address of a tunnel is an ISATAP address. It is required that IPv6 hosts in the IPv4 network can access the IPv6 network via an ISATAP tunnel.
II. Network diagram

Figure 4-6 Network diagram for an ISATAP tunnel
III. Configuration procedure
The following example shows how to configure an ISATAP tunnel between the router and the ISATAP host, which allows a separate ISATAP host to access the IPv6 network.
1) Configuration on the ISATAP switch
# Enable the IPv6 forwarding function.
<Sysname> system-view
[Sysname] ipv6
# Configure addresses for interfaces.
[Sysname] interface Vlan-interface 100
[Sysname-Vlan-interface100] ipv6 address 3001::1/64
[Sysname-Vlan-interface100] quit
[Sysname] interface Vlan-interface 101
[Sysname-Vlan-interface101] ip address 2.1.1.1 255.0.0.0
[Sysname-Vlan-interface100] quit
# Configure a service-loop group. (Note that to add a port to a service-loop group, you need to disable STP on the port.)
[Sysname] link-aggregation group 1 mode manual
[Sysname] link-aggregation group 1 service-type tunnel
[Sysname] interface Ethernet 1/0/1
[Sysname-Ethernet1/0/1] stp disable
[Sysname-Ethernet1/0/1] port link-aggregation group 1
[Sysname-Ethernet1/0/1] quit
# Configure an ISATAP tunnel.
[Sysname] interface Tunnel 0
[Sysname-Tunnel0] ipv6 address 2001::1/64 eui-64
[Sysname-Tunnel0] source Vlan-interface 101
[Sysname-Tunnel0] tunnel-protocol ipv6-ipv4 isatap
# Configure service-loop group 1 to be referenced by the tunnel in tunnel interface view.
[Sysname-Tunnel0] aggregation-group 1
# Disable the RA suppression so that hosts can acquire information such as the address prefix from the RA message released by the ISATAP switch.
[Sysname-Tunnel0] undo ipv6 nd ra halt
2) Configuration on the ISATAP host
The specific configuration on the ISATAP host is related to the operating system of the host. The following example shows the configuration of the host running the Windows XP.
#On a Windows XP-based host, the ISATAP interface is usually interface 2. Configure the IPv4 address of the ISATAP router on the ISATAP interface to complete the configuration on the host. The ISATAP interface information is as follows:
C:\> ipv6 if 2
Interface 2: Automatic Tunneling Pseudo-Interface
{48FCE3FC-EC30-E50E-F1A7-71172AEEE3AE}
does not use Neighbor Discovery
does not use Router Discovery
routing preference 1
EUI-64 embedded IPv4 address: 0.0.0.0
router link-layer address: 0.0.0.0
preferred link-local fe80::5efe:2.1.1.2, life infinite
link MTU 1280 (true link MTU 65515)
current hop limit 128
reachable time 42500ms (base 30000ms)
retransmission interval 1000ms
DAD transmits 0
# A link-local address (fe80::5efe:2.1.1.2) in the ISATAP format is automatically generated for the ISATAP interface. Configure the IPv4 address of the ISATAP router on the ISATAP interface.
C:\>ipv6 rlu 2 2.1.1.1
After carrying out the above command, look at the ISATAP interface information.
C:\> ipv6 if 2
Interface 2: Automatic Tunneling Pseudo-Interface
{48FCE3FC-EC30-E50E-F1A7-71172AEEE3AE}
does not use Neighbor Discovery
uses Router Discovery
routing preference 1
EUI-64 embedded IPv4 address: 2.1.1.2
router link-layer address: 2.1.1.1
preferred global 2001::5efe:2.1.1.2, life 29d23h59m46s/6d23h59m46s (public)
preferred link-local fe80::5efe:2.1.1.2, life infinite
link MTU 1500 (true link MTU 65515)
current hop limit 255
reachable time 42500ms (base 30000ms)
retransmission interval 1000ms
DAD transmits 0
# By comparison, it is found that the host acquires the address prefix 2001::/64 and automatically generates the address 2001::5efe:2.1.1.2. In addition, “uses Router Discovery” is displayed, indicating that the router discovery function is enabled on the host. At this time, ping the IPv6 address of the tunnel interface of the router. If the address is successfully pinged, an ISATAP tunnel is established.
IV. Configuration verification
After the above configuration, the ISATAP host can access the host in the IPV6 network.
4.7 Displaying and Maintaining Tunneling Configuration
Table 4-6 Follow the following steps to display and debug tunneling configuration
|
To do… |
Use the command… |
Remarks |
|
Display information related to a specified tunnel interface |
display interface Tunnel number |
Available in any view |
|
Display IPv6 information related to a specified tunnel interface |
display ipv6 interface Tunnel number |
4.8 Troubleshooting Tunneling Configuration
Symptom: After the configuration of related parameters such as tunnel source address, tunnel destination address, and tunnel mode, the tunnel interface is still not up.
Solution: Follow the steps below:
1) The common cause is that the physical interface of the tunnel source is not up. Use the display interface Tunnel or display ipv6 interface Tunnel commands to view whether the physical interface of the tunnel source is up or down.
2) Another possible cause is that the tunnel destination is unreachable. Use the display ipv6 routing-table or display ip routing-table command to view whether the tunnel destination is reachable. If no routing entry is available for tunnel communication in the routing table, configure related routes.
