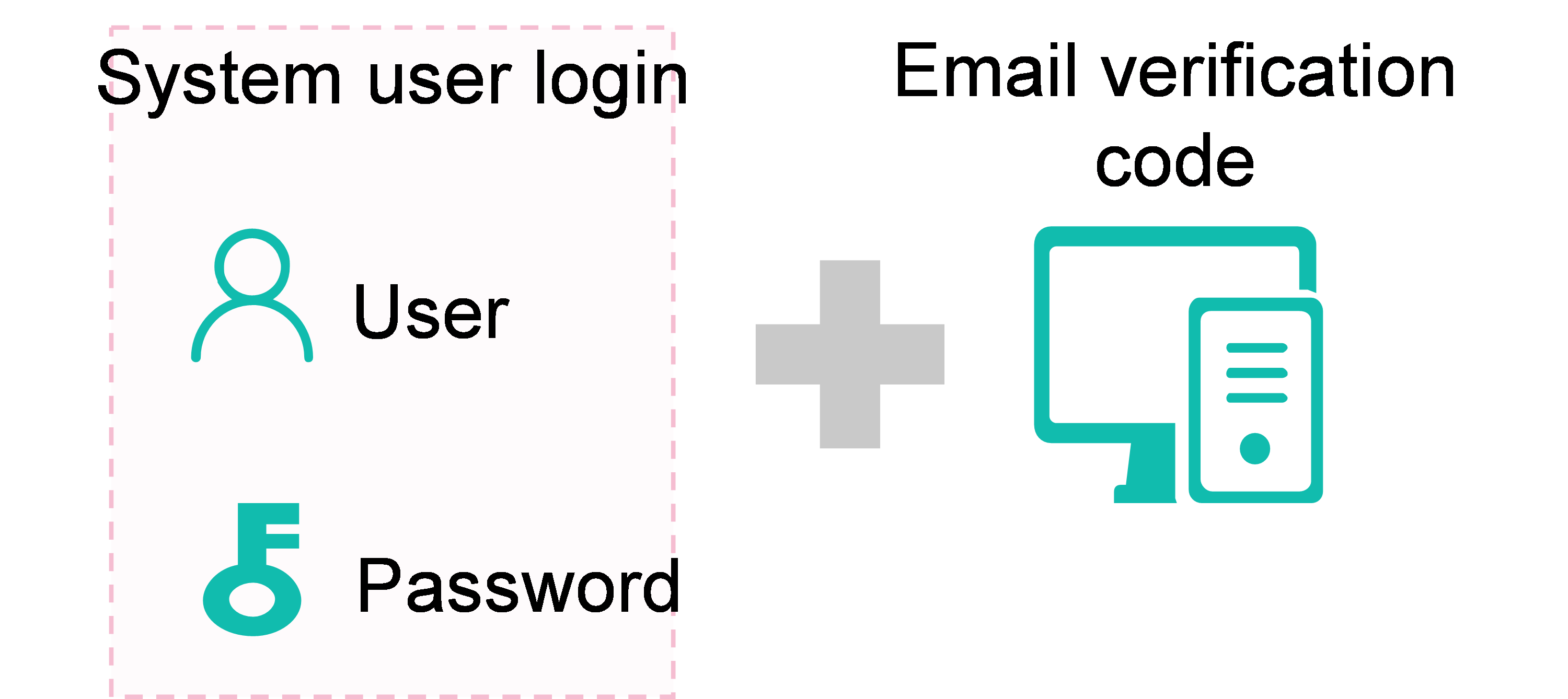- Table of Contents
-
- H3C Unified Platform Configuration Examples-E71xx-5W101
- 01-Unified Platform Operator Permission Management Configuration Examples
- 02-Unified Platform Dashboard Configuration Examples
- 03-Unified Platform Trap Filter Rule Configuration Examples
- 04-Unified Platform Trap-to-Alarm Rule Configuration Examples
- 05-Unified Platform Alarm Forwarding via SMS Configuration Examples
- 06-Unified Platform Alarm Aggregation Configuration Examples
- 07-Unified Platform Component License Registration and Expansion Configuration Examples
- 08-Unified Platform Alarm Forwarding via Mail Configuration Examples
- 09-Unified Platform Two-Factor Authentication Configuration Examples
- 10-Unified Platform Alarm Rendering Configuration Examples
- 11-Unified Platform Syslog Configuration Examples
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 09-Unified Platform Two-Factor Authentication Configuration Examples | 714.70 KB |
Unified Platform Two-Factor Authentication
Configuration Examples
Document version: 5W100-20250606
Software version: E7101
Copyright © 2025 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Example: Configuring two-factor authentication
Configuring graphic code authentication
Configuring SMS authentication
Configuring Google dynamic password authentication
Configuring FEITIAN dynamic password authentication
Configuring custom authentication
Selecting multiple authentication methods
Introduction
Two-factor authentication is a security measure that authenticates user identity by requiring users to provide two different types of authentication factors. The first authentication factor is username and password. The second authentication factor can be graphic code (CAPTCHA code), SMS verification code, Google dynamic password, FEITIAN dynamic password, or third-party authentication method. Two-factor authentication effectively prevents malicious attackers from illegally logging in by obtaining a user's username and password.
Prerequisites
· If two-factor authentication includes SMS authentication, you must configure the correct mobile number and make appropriate configuration in SMSC Settings. Otherwise, you cannot enable the SMS authentication method in two-factor authentication settings.
· If two-factor authentication includes Google dynamic password authentication, you must configure the correct email address and make appropriate configuration in Mail Server Settings. Otherwise, you cannot enable the Google dynamic password authentication method in two-factor authentication settings.
· If two-factor authentication includes FEITIAN dynamic password authentication, you must set up and configure the FEITIAN server before selecting this authentication method. Otherwise, you cannot receive FEITIAN dynamic passwords after logging out, preventing you from logging in again.
Configuration examples
Network configuration
Table 1 Two-factor authentication networks
|
Two-factor authentication method |
Schematic diagram |
|
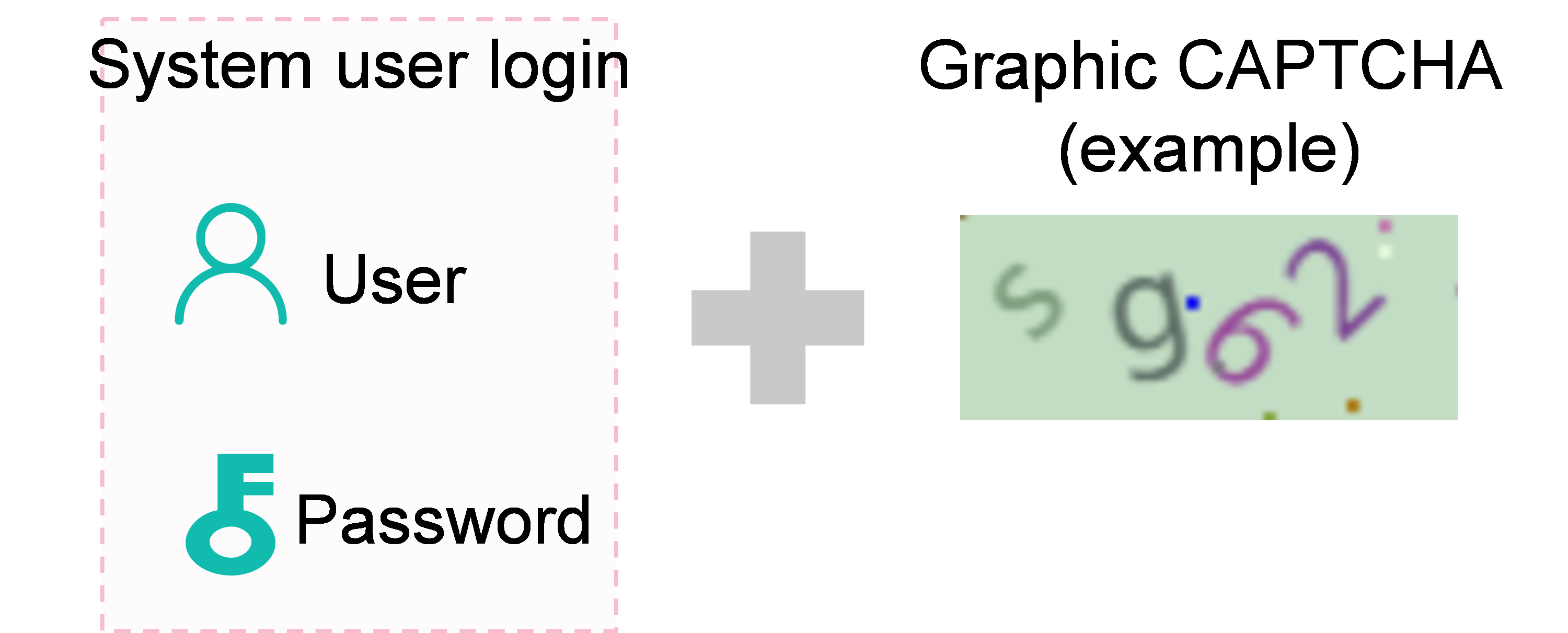
Graphic code authentication |
Company H wants the system to distinguish between real users and public automated programs during login. To meet this requirement, use the graphic code authentication method. |
|
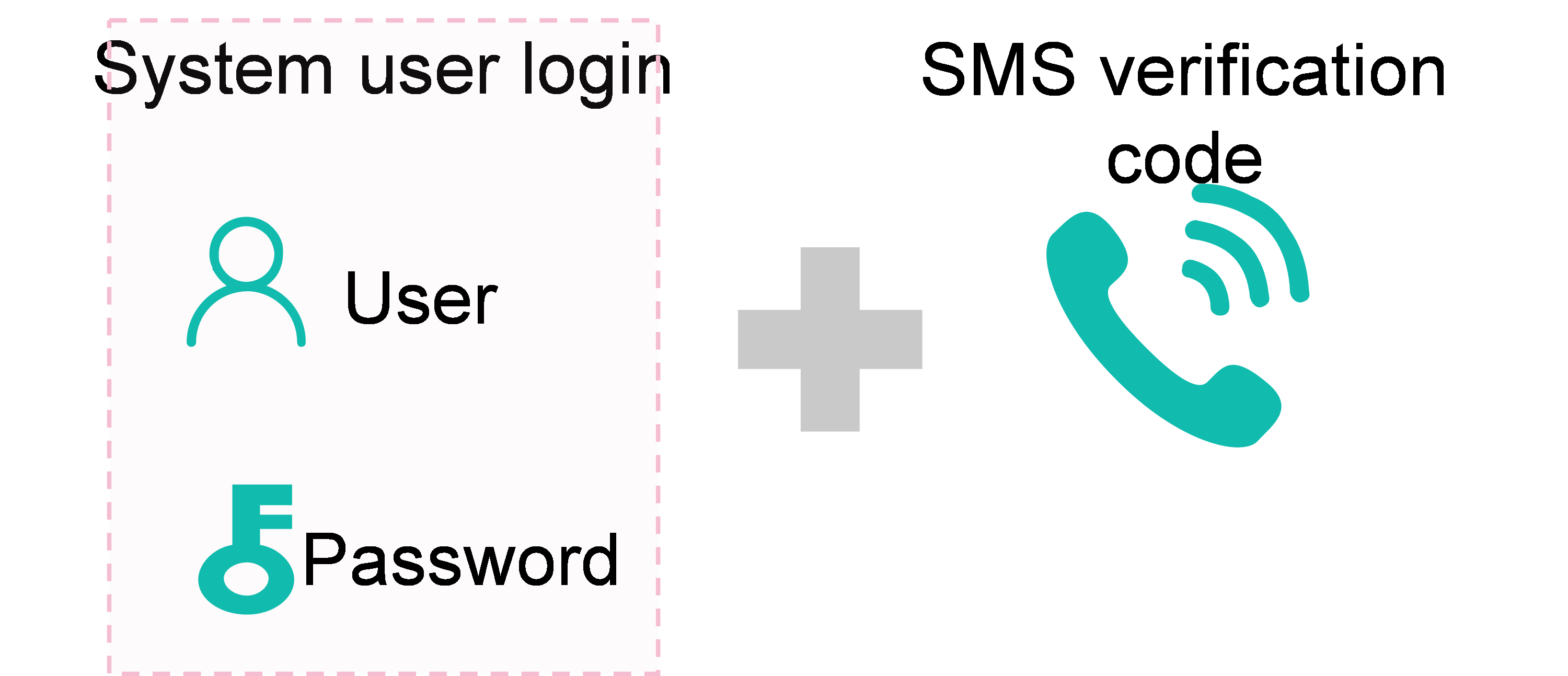
SMS authentication |
Since administrators at Company H frequently travel, they want to use personal devices for authentication and make sure the communication channels are secure and hard to intercept. To meet this requirement, consider using SMS authentication. |
|
Google dynamic password authentication |
Employees of Company H request remote login to Unified Platform. To verify their identity, use Google dynamic password authentication, which combines username, password, and mailbox verification code. |
|
FEITIAN dynamic password authentication |
Company H aims to enhance application security by implementing dynamic password-based identity authentication. This approach improves ease of use and convenience while reducing management and maintenance costs for identity authentication systems. To meet this requirement, consider using the FEITIAN dynamic password authentication method. |
Analysis
1. On the top navigation bar, click System. From the navigation pane, select System Settings > Security Settings > Authentication Settings to access the authentication settings page.
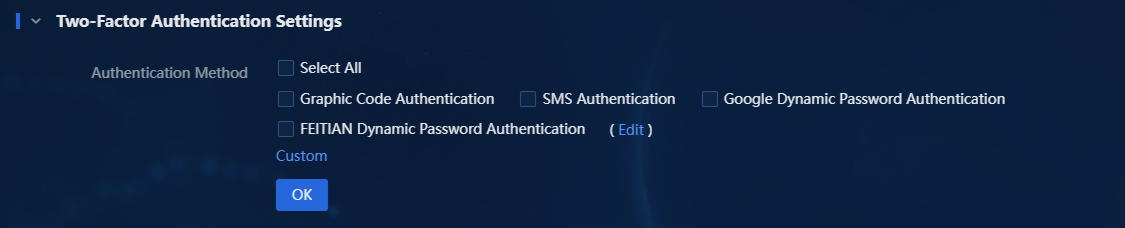
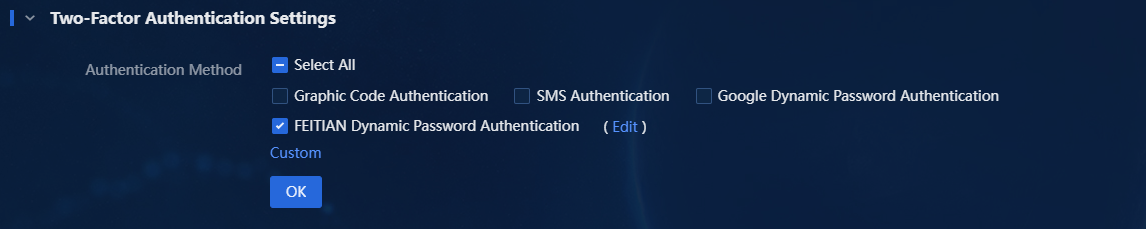
2. Expand the Two-Factor Authentication Settings area to display the supported two-factor authentication methods, including:
¡ Graphic code authentication.
¡ SMS authentication.
¡ Google dynamic password authentication.
¡ FEITIAN dynamic password authentication.
¡ Custom authentication.
Figure 1 Two-factor authentication methods
Software versions used
This configuration example was created and verified on Unified Platform E71xx.
Restrictions and guidelines
· After Unified Platform is installed, two-factor authentication is disabled by default. To enable two-factor authentication, go to the two-factor authentication settings to select the authentication methods. The two-factor authentication settings take effect the next time you log in.
· To ensure successful login after you enable SMS authentication, do not arbitrarily delete or edit the user's phone number.
Example: Configuring two-factor authentication
Configuring graphic code authentication
1. To enable graphic code authentication, unfold Two-Factor Authentication Settings, select Graphic Code Authentication as the authentication method, and then click OK.
Figure 2 Enabling graphic code authentication
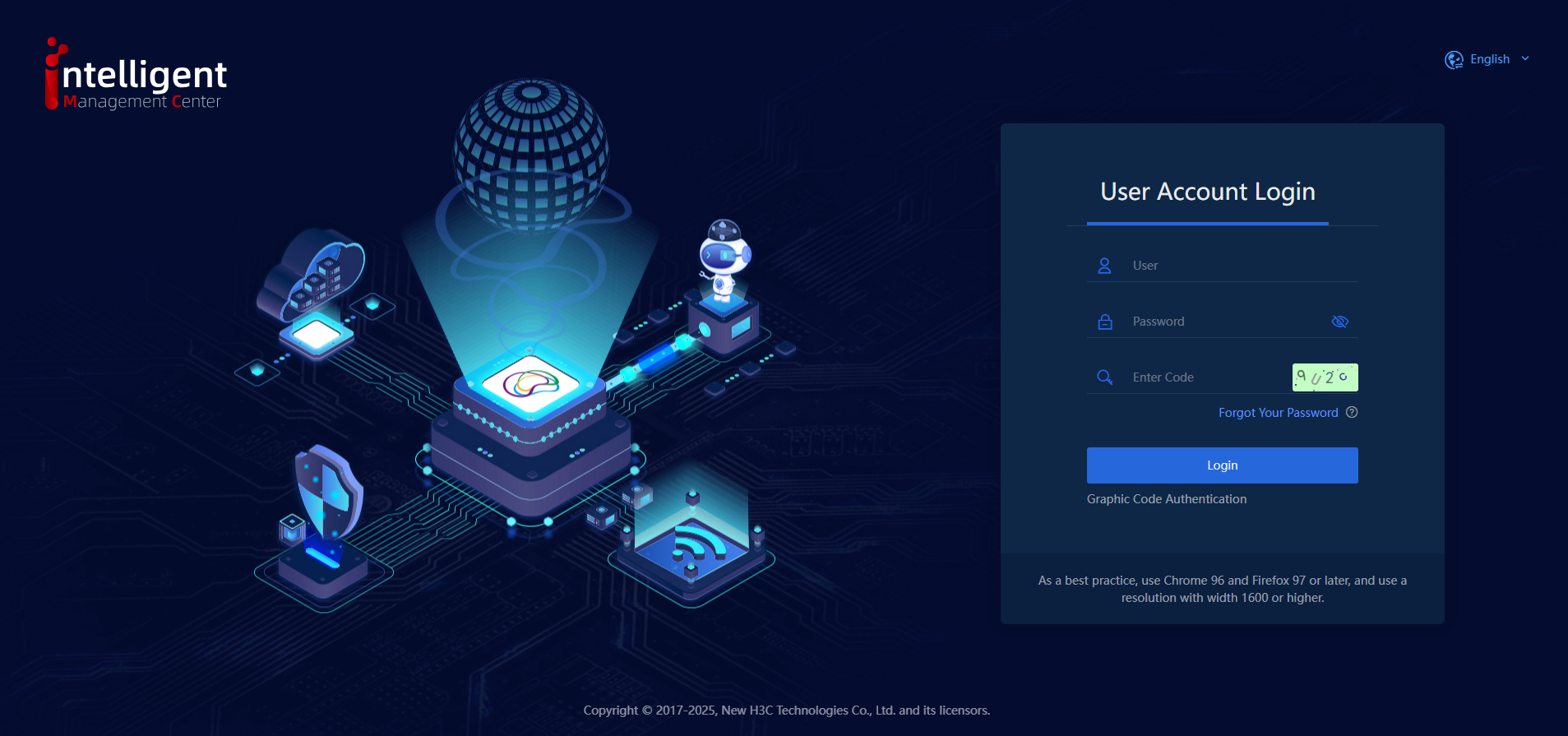
2. After graphic code authentication is enabled, the login page displays a graphical CAPTCHA as shown in the following figure.
Figure 3 Login interface after graphic code authentication is enabled
3. To successfully log into the system, users must enter the correct username, password, and CAPTCHA code.
Configuring SMS authentication
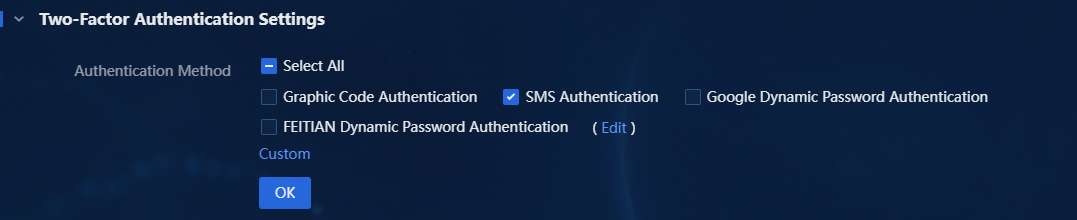
1. To enable SMS authentication, unfold Two-Factor Authentication Settings, select SMS Authentication as the authentication method, and then click OK.
Figure 4 Enabling SMS authentication
|
|
NOTE: To enable SMS
authentication, you must configure the correct mobile number and make
appropriate configuration in SMSC Settings. To configure the mobile number for the current user, go to the users
list, and then click the |
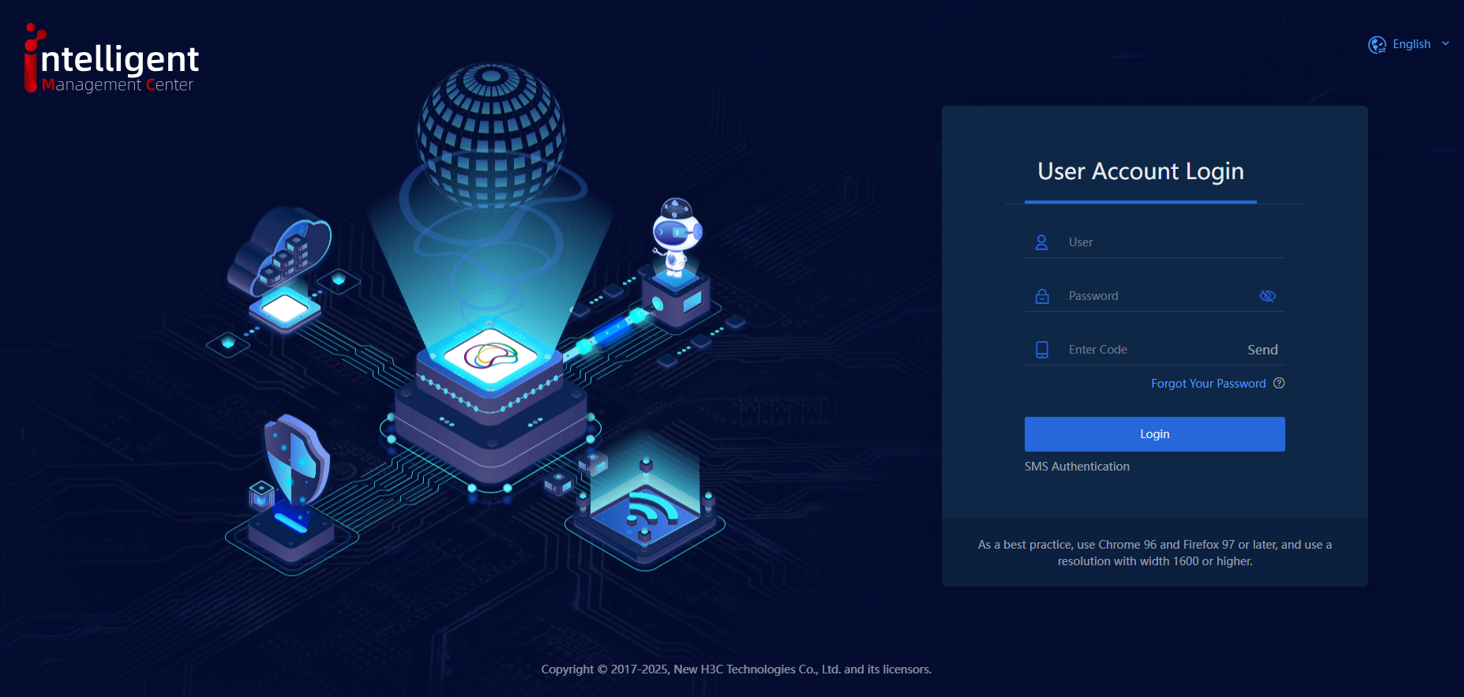
2. After SMS authentication is enabled, the login page displays the SMS authentication option, as shown in the following figure.
Figure 5 Login interface after SMS authentication is enabled.
3. After entering the correct username and password, click Send Verification Code to send a verification code. Then, enter the code received on your phone into the input box to log in to the system.
Configuring Google dynamic password authentication
1. To enable Google dynamic password authentication, unfold Two-Factor Authentication Settings, select Google Dynamic Password Authentication as the authentication method, and then click OK.
Figure 6 Enabling Google dynamic password authentication
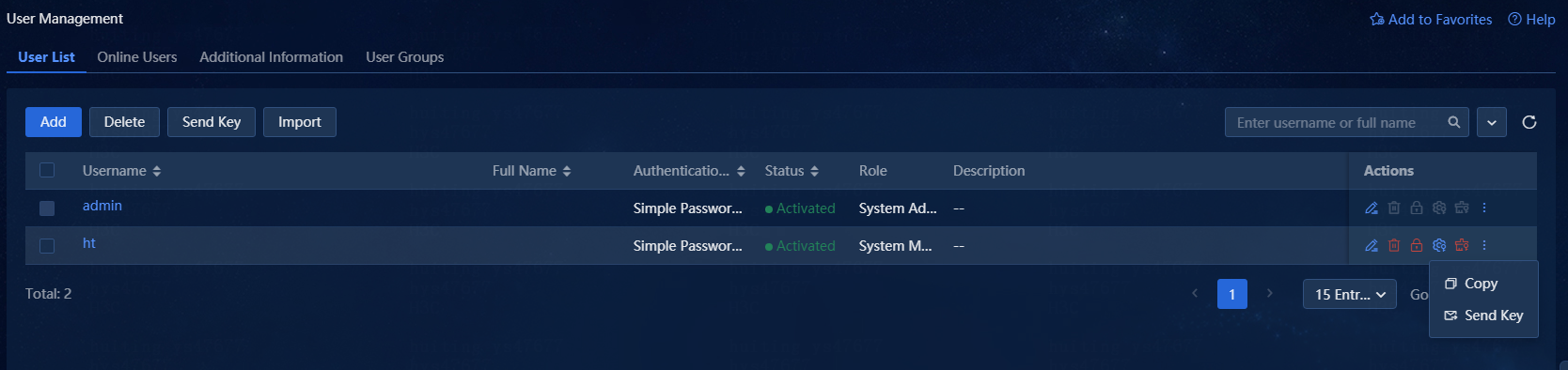
2. After the configuration, do not log out. Navigate to User Management > Users, and then click the send key icon in the Actions column for the current user to send the key, as shown in the following figure.
Figure 7 Sending a key in the users list
3. The user's mailbox will receive this key.
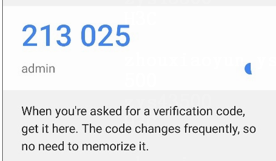
4. Download the Google Authenticator app on your mobile device. You can customize the account name and enter the content from your email into the secret key field. Click Add.
5. Open the Google Authenticator app homepage to get the verification code, as shown in the following figure.
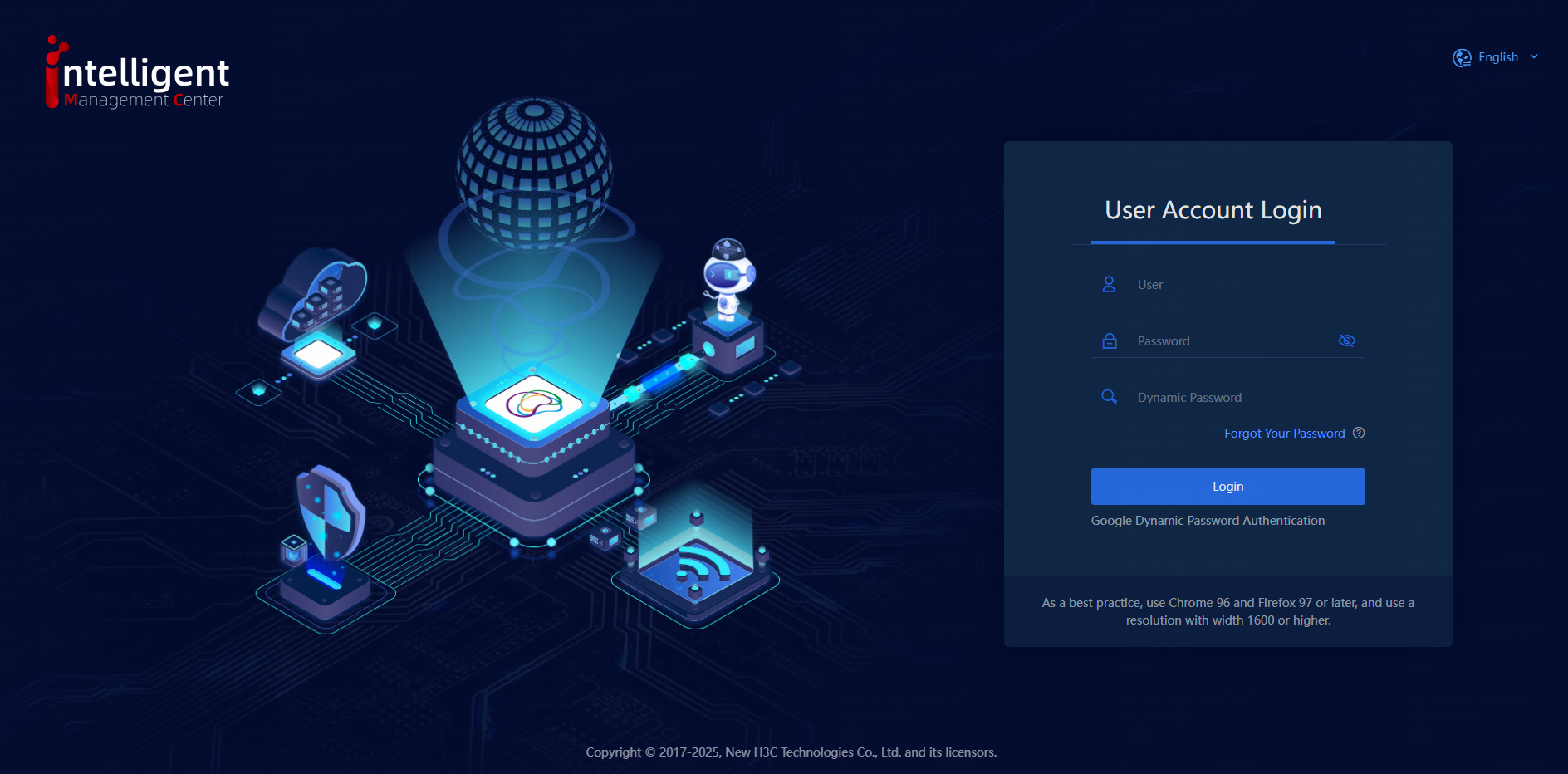
6. Open the login page, and enter the correct username and password. Then, enter the verification code in the dynamic password field to log in to the system, as shown in the following figure.
Figure 9 Login interface after Google dynamic password authentication is enabled
Configuring FEITIAN dynamic password authentication
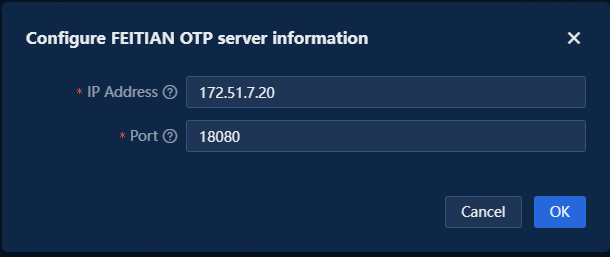
1. In two-factor authentication settings, click the Edit link next to the FEITIAN Dynamic Password Authentication method. On the window that opens, configure the FEITIAN OTP server information, including the IP address and port number.
Figure 10 Configuring FEITIAN server information
2. Click OK.
Figure 11 Enabling FEITIAN dynamic password authentication
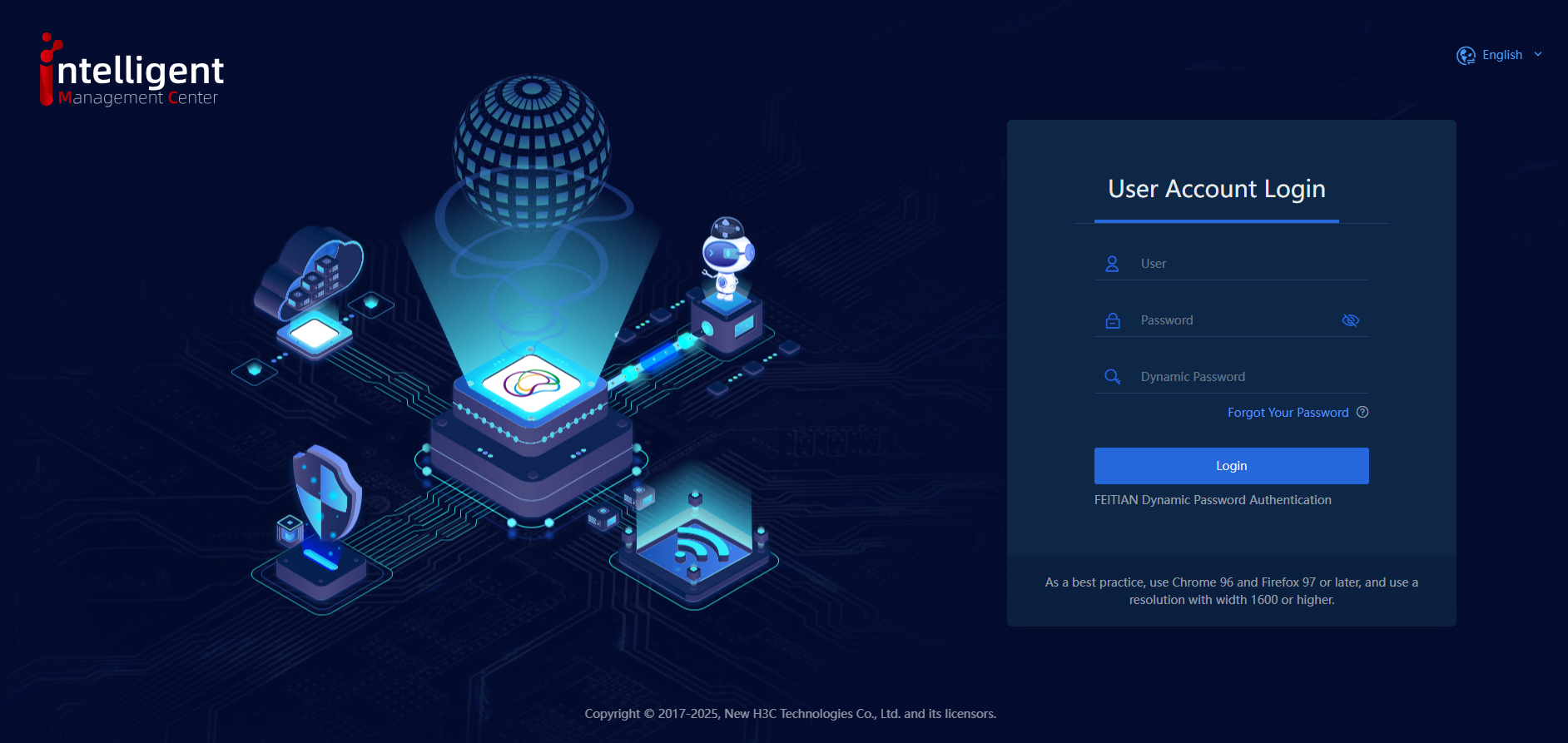
3. After FEITIAN dynamic password authentication is enabled, the login page will display the FEITIAN dynamic password field, as shown in the following figure.
Figure 12 Login interface with FEITIAN dynamic password authentication
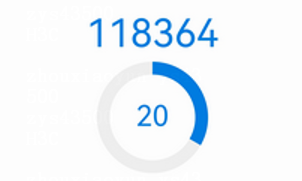
4. To successfully log into the system, users must enter the correct username, password, and FEITIAN dynamic password. View and obtain the dynamic password from the FEITIAN mobile token app, as shown in the following figure.
Figure 13 Dynamic password on the Mobile Token app client
Configuring custom authentication
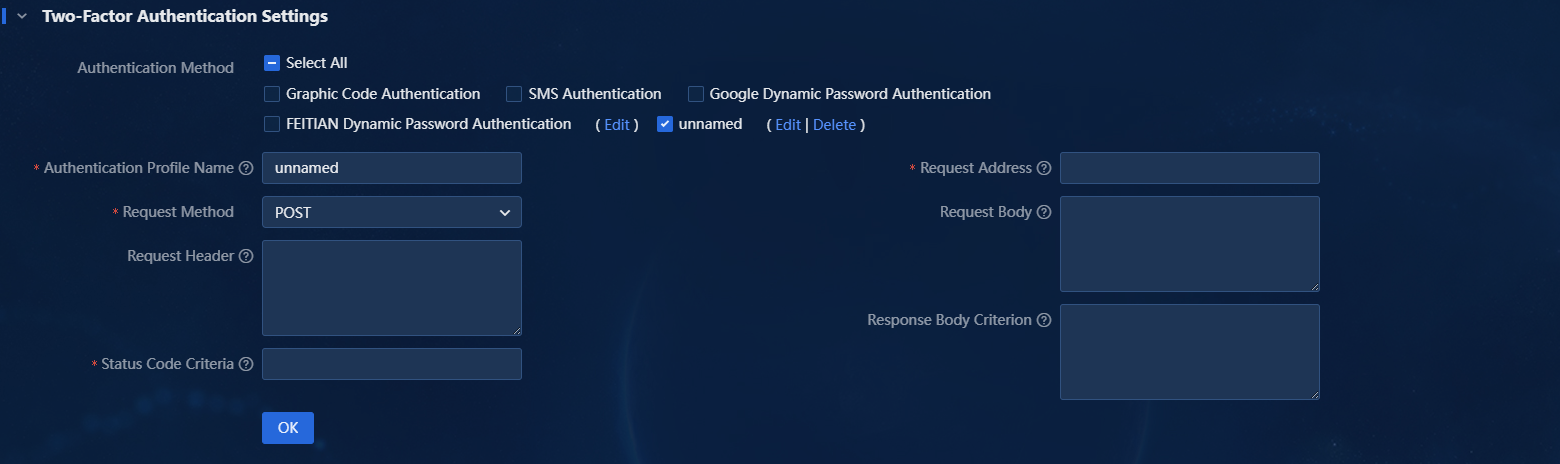
In the two-factor authentication settings, click the Custom link to configure custom authentication, as shown the following figure.
· Authentication Profile Name: Name of the custom two-factor authentication.
· Request Address: The interface address for the custom two-factor authentication. It is the domain name or IP address of a third-party authentication.
· Request Method: HTTP request method. Select either POST or GET based on actual requirements. The default is POST.
· Request Body: (Optional.) Connection parameters for third-party authentication. Configure it as needed.
· Request Header: (Optional.) Header for messages requesting connection to third-party authentication. Configure it as needed.
· Response Body Criterion: (Optional.) Successful response body from third-party authentication. If the response matches the specified content, the system determines that the third-party authentication succeeds. If you leave this field empty, the system does not check the respond body from the third-party authentication. Configure this field as needed.
· Status Code Criteria: Enter the status code returned after a successful request.
Figure 14 Custom authentication configuration
Selecting multiple authentication methods
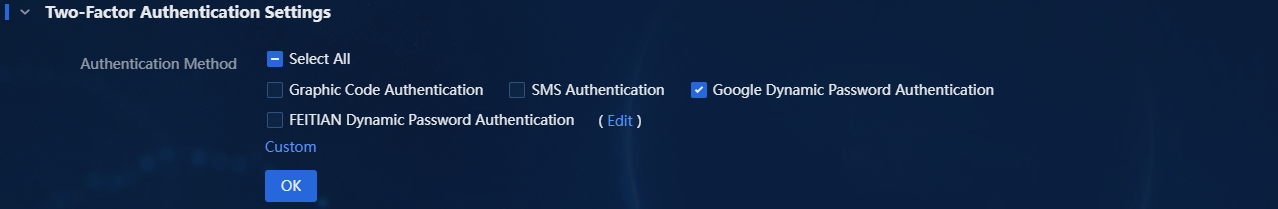
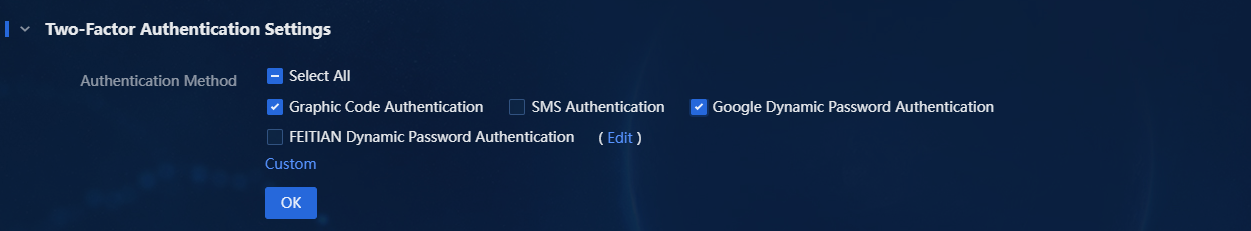
1. In two-factor authentication settings, you can select multiple authentication methods simultaneously, as shown in the following figure.
Figure 15 Selecting multiple authentication methods
2. This example selects graphic code authentication and Google dynamic password authentication. Select both Graphic Code Authentication and Google Dynamic Password Authentication, and then click OK. Exit to the login page.
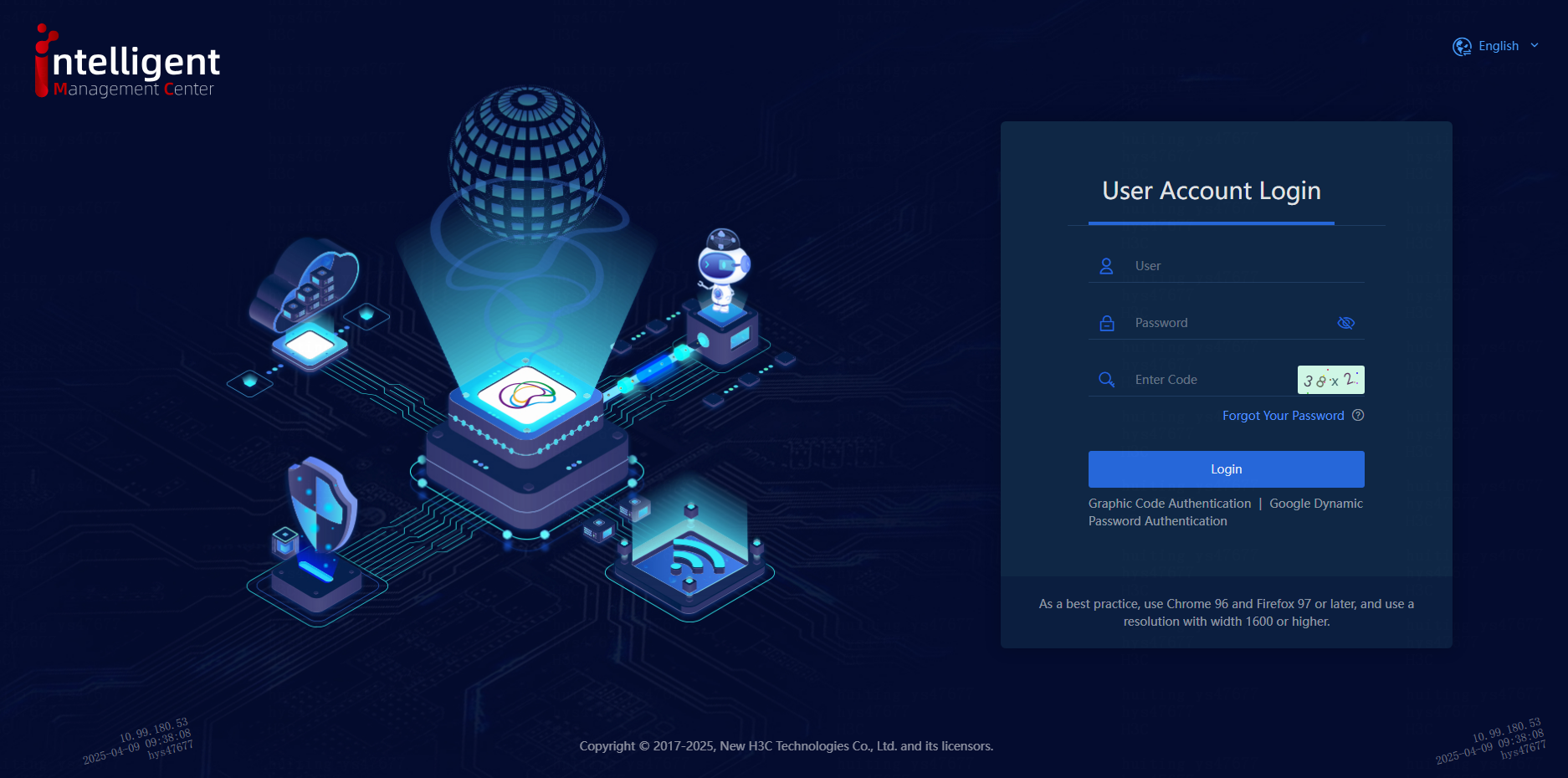
Figure 16 Login page with multiple authentication methods enabled
3. Click the Graphic Code Authentication or Google Dynamic Password Authentication link below the Log In button to switchover the login mode.
Figure 17 Switching the login mode
4. You can log in to the system after you pass either of the authentication methods.