- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 02-NETCONF Troubleshooting Guide | 54.75 KB |
Troubleshooting system management
NETCONF issues
NETCONF over SOAP access failure
Symptom
The device acts as a NETCONF server. A user failed to log in to the device from a NETCONF over SOAP client.
Common causes
The following are the common causes of this type of issue:
· The SOAP client cannot communicate with the device. A TCP connection fails to be established.
· The device is disabled with NETCONF over SOAP.
· An ACL is configured on the server to control client access and the IP address of the client is not in an ACL-based access control permit rule.
· The local user is not authorized to use the HTTP or HTTPS service.
· The authentication method of the local user is not configured correctly.
· The number of HTTP/HTTPS login users has reached the upper limit.
Troubleshooting flow
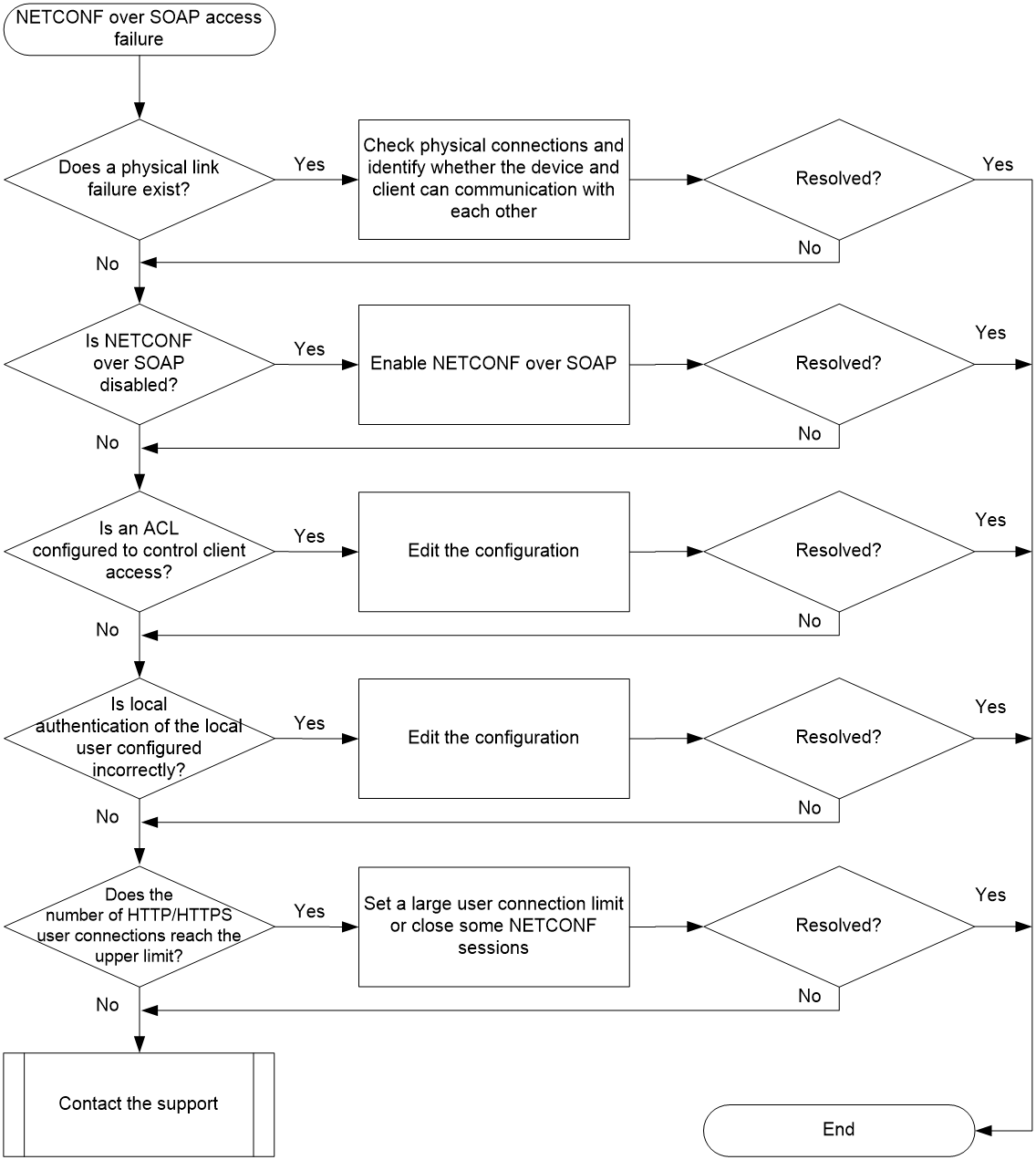
Figure 1 shows the troubleshooting flowchart.
Figure 1 Flowchart for troubleshooting NETCONF over SOAP access failure
Solution
1. Identify whether a physical link failure exists.
Log in to the device through Telnet (user role name network-admin). Identify whether the device can ping the IP address of the NETCONF client. If the ping operation fails, execute either the display ip routing-table command or the display route-static routing-table command to obtain the output interface for the route to the client. Then, execute the display interface command to check the interface state.
<Sysname> display interface gigabitethernet 0/0/1
GigabitEthernet0/0/1
Interface index: 386
Current state: Administratively DOWN
Line protocol state: DOWN
...
a. If the Current state field displays Administratively DOWN, execute the undo shutdown command on the interface to bring up the interface. If the Current state field displays DOWN, check the physical connection of the interface.
b. If other devices exist between the device and the client, check the interface state and restore physical connections on each device hop-by-hop as mentioned above.
2. Execute the display netconf service command to identify whether NETCONF over SOAP is enabled.
<Sysname> display netconf service
NETCONF over SOAP over HTTP: Disabled (port 80)
NETCONF over SOAP over HTTPS: Disabled (port 832)
NETCONF over SSH: Disabled (port 830)
NETCONF over Telnet: Enabled
NETCONF over Console: Enabled
...
If the NETCONF over SOAP over HTTP field displays Disabled, enable NETCONF over SOAP over HTTP by using the netconf soap http enable command in system view.
If the NETCONF over SOAP over HTTPS field displays Disabled, enable NETCONF over SOAP over HTTPS by using the netconf soap https enable command in system view.
3. Identify whether an ACL is configured to control client access.
<Sysname> display current-configuration | begin netconf
netconf soap http enable
netconf soap https enable
netconf soap http acl 2000
#
[Sysname] acl basic 2000
[Sysname-acl-ipv4-basic-2000] display this
#
acl basic 2000
rule 5 permit source 192.168.4.10 0
rule 10 permit source 192.168.4.15 0
...
If configuration about the netconf soap { http | https } acl command exists, use one of the following methods as required:
¡ Execute the rule command in the corresponding ACL view. Make sure the client IP address matches an ACL rule.
¡ Execute the undo netconf soap { http | https } acl command to disassociate NETCONF over SOAP from the ACL.
4. When local authentication is used, identify whether the local user corresponding to the client can use the HTTP and HTTPS services.
Enter local user view and execute the display this command. Make sure the service-type http https command is configured.
<Sysname> system-view
[Sysname] local-user test
[Sysname-luser-manage-test] display this
#
local-user test class manage
service-type http https
authorization-attribute user-role network-operator
5. When local authentication is used, execute the display domain command to check the authentication, authorization, and accounting configuration in the ISP domain.
<Sysname> display domain
Total 12 domains
Domain: system
Current state: Active
State configuration: Active
Default authentication scheme: Local
Default authorization scheme: Local
Default accounting scheme: Local
...
For example, in ISP domain system, execute the following commands to configure local authentication, authorization, and accounting for login users.
<Sysname> system-view
[Sysname] domain system
[Sysname-isp-system] authentication login local
[Sysname-isp-system] authorization login local
[Sysname-isp-system] accounting login local
6. Identify whether the number of users logging in to the device has reached the upper limit.
Execute the display netconf service command on the device to check the value for the Active Sessions field. This field indicates the number of active NETCONF sessions. If the value has reached the maximum number of concurrent HTTP or HTTPS users, use one of the following methods to resolve the issue:
¡ Execute the aaa session-limit { http | https } max-sessions command to set a large upper limit for concurrent HTTP or HTTPS users that can log in to the device.
¡ Perform the <kill-session> operation to forcibly release some established NETCONF over SOAP sessions so that new users can come online.
# Execute the display netconf session command to view NETCONF session information.
<Sysname> display netconf session
Session ID: 1 Session type : SOAP
Username : yy
...
# The XML message for the <kill-session> operation is as follows:
<rpc message-id="100" xmlns="urn:ietf:params:xml:ns:netconf:base:1.0">
<kill-session>
<session-id>1</session-id>
</kill-session>
</rpc>
7. If the issue persists, collect the following information and contact Technical Support:
¡ Results of each step.
¡ The configuration file, log messages, and alarm messages.
Related alarm and log messages
Alarm messages
N/A
Log messages
NETCONF/6/SOAP_XML_LOGIN
NETCONF over SSH access failure
Symptom
A configuration tool failed to log in to the device through SSH.
Solution
Troubleshoot the issue as shown in "Troubleshooting security."