- Table of Contents
-
- 03-Security Configuration Guide
- 00-Preface
- 01-Security zone configuration
- 02-Security policy configuration
- 03-ASPF configuration
- 04-Session management
- 05-Object group configuration
- 06-IP source guard configuration
- 07-AAA configuration
- 08-802.1X configuration
- 09-User identification configuration
- 10-Password control configuration
- 11-Portal configuration
- 12-MAC authentication configuration
- 13-IPoE configuration
- 14-Public key management
- 15-PKI configuration
- 16-SSH configuration
- 17-SSL configuration
- 18-Connection limit configuration
- 19-Attack detection and prevention configuration
- 20-Server connection detection configuration
- 21-ARP attack protection configuration
- 22-ND attack defense configuration
- 23-uRPF configuration
- 24-IP-MAC binding configuration
- 25-APR configuration
- 26-Keychain configuration
- 27-Crypto engine configuration
- 28-MAC learning through a Layer 3 device configuration
- 29-SMS configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 20-Server connection detection configuration | 79.79 KB |
Contents
Configuring server connection detection
About server connection detection
Restrictions: Hardware compatibility with server connection detection
Configuring server connection learning
Configuring SCD rules in an SCD policy
Display and maintenance commands for server connection detection
Configuring server connection detection
About server connection detection
Server connection detection (SCD) provides protections for internal servers. It enables the device to identify legal and illegal connections initiated by the protected servers. This helps you monitor internal servers and prevent them from becoming part of a botnet and launching attacks or performing internal network penetration.
Restrictions: Hardware compatibility with server connection detection
|
F1000 series |
Models |
Server connection detection compatibility |
|
F1000-X-G5 series |
F1000-A-G5, F1000-C-G5, F1000-C-G5-LI, F1000-E-G5, F1000-H-G5, F1000-S-G5 |
Yes |
|
F1000-X-G3 series |
F1000-A-G3, F1000-C-G3, F1000-E-G3, F1000-S-G3 |
Yes |
|
F1000-X-G2 series |
F1000-A-G2, F1000-C-G2, F1000-E-G2, F1000-S-G2 |
Yes |
|
F1000-9X0-AI series |
F1000-9390-AI, F1000-9385-AI, F1000-9380-AI, F1000-9370-AI, F1000-9360-AI, F1000-9350-AI, F1000-9330-AI, F1000-9320-AI, F1000-990-AI, F1000-980-AI, F1000-970-AI, F1000-960-AI, F1000-950-AI, F1000-930-AI, F1000-920-AI, F1000-910-AI, F1000-905-AI |
Yes |
|
F1000-C83X0 series |
F1000-C8395, F1000-C8390, F1000-C8385, F1000-C8380, F1000-C8370, F1000-C8360, F1000-C8350, F1000-C8330 |
Yes |
|
F1000-C81X0 series |
F1000-C8180, F1000-C8170, F1000-C8160, F1000-C8150, F1000-C8130, F1000-C8120, F1000-C8110 |
Yes |
|
F1000-7X0-HI series |
F1000-770-HI, F1000-750-HI, F1000-740-HI, F1000-730-HI, F1000-720-HI, F1000-710-HI |
Yes |
|
F1000-C-X series |
F1000-C-EI, F1000-C-HI, F1000-C-XI, F1000-E-XI |
Yes |
|
F1000-V series |
F1000-E-VG, F1000-S-VG |
Yes |
|
SecBlade IV |
LSPM6FWD8, LSQM2FWDSC8 |
No |
|
F100 series |
Models |
Server connection detection compatibility |
|
F100-X-G5 series |
F100-A-G5, F100-C-G5, F100-E-G5, F100-M-G5, F100-S-G5 |
Yes |
|
F100-X-G3 series |
F100-A-G3, F100-C-G3, F100-E-G3, F100-M-G3, F100-S-G3 |
Yes |
|
F100-X-G2 series |
F100-A-G2, F100-C-G2, F100-E-G2, F100-M-G2, F100-S-G2 |
Yes |
|
F100-WiNet series |
F100-A80-WiNet, F100-C80-WiNet, F100-C60-WiNet, F100-S80-WiNet, F100-A81-WiNet, F100-A91-WiNet, F100-C50-WiNet |
Yes |
|
F100-C-A series |
F100-C-A6, F100-C-A5, F100-C-A3, F100-C-A2, F100-C-A1, F100-C-A6-WL, F100-C-A5-W, F100-C-A3-W |
Yes |
|
F100-X-XI series |
F100-A-EI, F100-A-HI, F100-A-SI, F100-C-EI, F100-C-HI, F100-C-XI, F100-E-EI, F100-S-HI, F100-S-XI |
Yes |
SCD tasks at a glance
To configure SCD, perform the following tasks:
1. Configuring server connection learning
3. Configuring SCD rules in an SCD policy
Configuring server connection learning
About this task
Server connection learning learns connections initiated by given servers. The learning results provide the basis for you to create SCD policies to monitor and log illegal connections initiated by the servers.
Restrictions and guidelines
You cannot edit any settings in server connection learning configuration view if server connection learning is in progress.
Procedure
1. Enter system view.
system-view
2. Enter server connection learning configuration view.
scd learning
3. Specify an IP address object group for server connection learning.
source-ip object-group-name
By default, no IP address object groups are specified for server connection learning.
4. Enable server connection learning for a learning period.
auto-learn enable period { one-day | one-hour | seven-day | twelve-hour }
By default, server connection learning is disabled.
Configuring an SCD policy
About this task
An SCD policy monitors the connections initiated by the specified protected server. You can configure the following settings in an SCD policy:
· Protected server IP address.
· SCD rules to identify legal connections initiated by the server.
· Logging for illegal connections initiated by the server.
· SCD policy enabling status.
Restrictions and guidelines
An SCD policy monitors only the connections initiated by the server specified by the protected-server command.
The protected server IP address must be unique for each SCD policy.
Procedure
1. Enter system view.
system-view
2. Create an SCD policy and enter its view.
scd policy name policy-name
3. Specify the IP address of the protected server.
protected-server ip-address
By default, no protected server IP address is specified.
4. (Optional.) Enable logging for illegal connections initiated by the protected server.
logging enable
By default, the device does not log illegal connections initiated by the protected server.
5. Enable the SCD policy.
policy enable
By default, an SCD policy is disabled.
Configuring SCD rules in an SCD policy
About this task
You can configure multiple SCD rules in an SCD policy. Each SCD rule contains the following criteria to identify legal connections initiated by the protected server:
· A destination IP address criterion, which specifies the destination IP address for server-initiated connections.
· One or more protocol criteria. Each protocol criterion specifies a protocol and optionally a set of destination port numbers.
A connection initiated by the protected server matches the SCD rule if the connection matches both the destination IP address criterion and a protocol criterion. Connections initiated by the server that do not match any SCD rules are considered illegal connections.
Restrictions and guidelines
If you do not configure any rules in an SCD policy, all connections initiated by the protected server of the policy are illegal connections.
An SCD rule must contain one destination IP address criterion and a minimum of one protocol criteria.
In one SCD policy, each SCD rule must use a unique destination IP address.
Procedure
1. Enter system view.
system-view
2. Enter the view of an SCD policy.
scd policy name policy-name
3. Create an SCD rule and enter its view.
rule rule-id
4. Configure the destination IP address criterion.
permit-dest-ip ip-address
By default, the destination IP address criterion is not configured.
5. Configure a protocol criterion.
protocol { icmp | tcp port port-list | udp port port-list }
By default, no protocol criterion is configured in an SCD rule.
Display and maintenance commands for server connection detection
Execute display commands in any view.
Execute reset commands in user view.
|
Task |
Command |
|
Display the server connection learning information. |
display scd auto-learn config |
|
Display the server connection learning results. |
display scd learning record [ protected-server ip-address ] [ destination-ip ip-address ] |
|
Display the SCD policy information. |
display scd policy [ name policy-name ] |
|
Clear the server connection learning results. |
reset scd learning record |
SCD configuration examples
Example: Configuring SCD
Network configuration
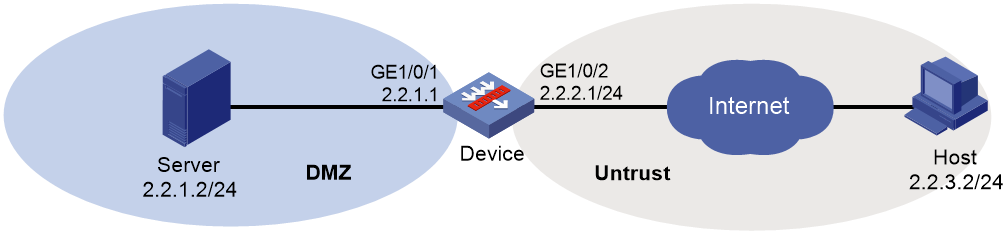
As shown in Figure 1, configure SCD on the device to perform the following tasks:
· Monitor connections initiated by servers in subnet 2.2.1.0/24 for one day.
· Logs all connections initiated by the server except for TCP connections destined for TCP ports 80 and 443 on host 2.2.3.2/24.
Procedure
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 2.2.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures a static route, and the next hop in the route is 2.2.2.2.
[Device] ip route-static 2.2.3.0 24 2.2.2.2
3. Add interfaces to security zones.
[Device] security-zone name dmz
[Device-security-zone-DMZ] import interface gigabitethernet 1/0/1
[Device-security-zone-DMZ] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
4. Configure a security policy:
# Configure a rule named dmz-untrust to permit the packets from the internal server to the Internet.
[Device] security-policy ip
[Device-security-policy-ip] rule name dmz-untrust
[Device-security-policy-ip-1-dmz-untrust] source-zone dmz
[Device-security-policy-ip-1-dmz-untrust] destination-zone untrust
[Device-security-policy-ip-1-dmz-untrust] source-ip-host 2.2.1.2
[Device-security-policy-ip-1-dmz-untrust] action pass
[Device-security-policy-ip-1-dmz-untrust] quit
[Device-security-policy-ip] quit
5. Create an IP address object group named abc and specify IPv4 address 2.2.1.0 and mask length 24 for the object group.
[Device] object-group ip address abc
[Device-obj-grp-ip-abc] network subnet 2.2.1.0 24
[Device-obj-grp-ip-abc] quit
6. Specify IP address object group abc for server connection learning and enable server connection learning for one day.
[Device] scd learning
[Device-scd-learning] source-ip abc
[Device-scd-learning] auto-learn enable period one-day
[Device-scd-learning] quit
7. Create an SCD policy named policy1.
[Device] scd policy name policy1
[Device-scd-policy-policy1] protected-server 2.2.1.2
[Device-scd-policy-policy1] logging enable
[Device-scd-policy-policy1] rule 1
[Device-scd-policy-policy1-1] permit-dest-ip 2.2.3.2
[Device-scd-policy-policy1-1] protocol tcp port 80 443
[Device-scd-policy-policy1-1] quit
[Device-scd-policy-policy1] policy enable
[Device-scd-policy-policy1] quit
Verifying the configuration
# After the server connection learning is complete, display the server connection learning results.
[Device] display scd learning record
Id Protected server Destination IPv4 address Protocol Port
1 2.2.1.2 2.2.3.2 TCP 80
2 2.2.1.2 2.2.3.2 TCP 443
3 2.2.1.2 2.2.3.2 UDP 4433
4 2.2.1.2 2.2.3.2 UDP 567
Total entries: 4
# Display information about SCD policy policy1.
<Sysname> display scd policy name policy1
SCD policy name: policy1
Protected server IPv4: 2.2.1.2
Logging: Enabled
Policy status: Enabled
Rule ID: 1
Permitted dest IPv4: 2.2.3.2
Protocol: TCP port 80,443