- Table of Contents
-
- 12-Security Configuration Guide
- 00-Preface
- 01-Security zone configuration
- 02-AAA configuration
- 03-802.1X configuration
- 04-MAC authentication configuration
- 05-Portal configuration
- 06-Port security configuration
- 07-User profile configuration
- 08-Password control configuration
- 09-Keychain configuration
- 10-Public key management
- 11-PKI configuration
- 12-IPsec configuration
- 13-Group domain VPN configuration
- 14-SSH configuration
- 15-SSL configuration
- 16-SSL VPN configuration
- 17-ASPF configuration
- 18-APR configuration
- 19-mGRE configuration
- 20-Session management
- 21-Connection limit configuration
- 22-Object group configuration
- 23-Object policy configuration
- 24-Security policy configuration
- 25-Attack detection and prevention configuration
- 26-IP source guard configuration
- 27-ARP attack protection configuration
- 28-ND attack defense configuration
- 29-uRPF configuration
- 30-Crypto engine configuration
- 31-FIPS configuration
- 32-Application account auditing configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 23-Object policy configuration | 112.61 KB |
Contents
Restrictions and guidelines: Object policy configuration
IPv4 object policy tasks at a glance
IPv6 object policy tasks at a glance
Prerequisites for object policies
Configuring IPv4 object policies
Creating an IPv4 object policy
Configuring an IPv4 object policy rule
Applying an IPv4 object policy to a zone pair
Enabling rule matching acceleration
Configuring IPv6 object policies
Creating an IPv6 object policy
Configuring an IPv6 object policy rule
Applying an IPv6 object policy to a zone pair
Enabling rule matching acceleration
Display and maintenance commands for object policies
Object policy configuration examples
Example: Configuring an IPv4 object policy
Configuring object policies
About object policies
An object policy is a set of rules for security control over packets between a source and a destination security zone. These two zones define a zone pair. The object policy matches the first packet of a traffic flow against the rules. If a match is found, the device stops the match process and takes the action defined in the rule on the packet and all subsequent packets of the flow.
For more information about zone pair and security zone configuration, see "Configuring security zones."
Object policy rules
An object policy contains one or multiple rules. Each object policy rule is a permit or deny statement for matching traffic based on criteria such as the source IP address, destination IP address, service type, application, and application group. The matching packets are processed based on actions stated in the rules. If no criterion is configured for an IPv4/IPv6 rule, the rule matches all IPv4/IPv6 packets.
Rule numbering
Each rule is uniquely identified by an ID. The rule ID can be manually configured or automatically assigned by the system when you create the rule. In automatic rule numbering, the system assigns the rule an integer next to the greatest ID being used. For example, if the greatest ID is 60000, the system automatically assigns 60001. If the greatest ID is 65534, the system assigns the smallest unused rule ID to the rule.
Rule match order
The system matches packets against rules in the order the rules were configured. The match process stops when a match is found. You can use the display this command in zone pair view to check the rule configuration order. You can use the move rule command in object policy view to change the rule configuration order.
As a best practice, configure rules that are more specific than others to be matched against first.
Rule matching acceleration
This feature accelerates rule matching. It enhances connection establishment and packet forwarding performance, especially for a device using multiple rules to match first packets from multiple users.
Restrictions and guidelines: Object policy configuration
· You can apply only one IPv4 object policy and one IPv6 object policy to each zone pair. Configuration fails if you apply more than one IPv4 or IPv6 object policies to a zone pair.
· For an object policy rule to take effect, make sure the specified object group is configured with objects or the specified application group has applications.
IPv4 object policy tasks at a glance
To configure IPv4 object policies, perform the following tasks:
1. Creating an IPv4 object policy
2. Configuring an IPv4 object policy rule
3. Applying an IPv4 object policy to a zone pair
4. (Optional.) Changing the rule match order
5. (Optional.) Enabling rule matching acceleration
IPv6 object policy tasks at a glance
To configure IPv6 object policies, perform the following tasks:
1. Creating an IPv6 object policy
2. Configuring an IPv6 object policy rule
3. Applying an IPv6 object policy to a zone pair
4. (Optional.) Changing the rule match order
5. (Optional.) Enabling rule matching acceleration
Prerequisites for object policies
Before configuring an object policy, complete the following tasks:
· Configure time ranges (see ACL and QoS Configuration Guide).
· Configure IPv4 address objects, IPv6 address objects, and service objects (see "Configuring object groups").
Configuring IPv4 object policies
Creating an IPv4 object policy
1. Enter system view.
system-view
2. Create an IPv4 object policy and enter its view.
object-policy ip object-policy-name
3. (Optional.) Configure a description for the object policy.
description text
By default, no description is configured for an object policy.
Configuring an IPv4 object policy rule
1. Enter system view.
system-view
2. Enter IPv4 object policy view.
object-policy ip object-policy-name
3. Configure an IPv4 object policy rule.
rule [ rule-id ] { drop | pass | inspect app-profile-name } [ [ source-ip { object-group-name | any } ] [ destination-ip { object-group-name | any } ] [ service { object-group-name | any } ] [ vrf vrf-name ] [ application application-name ] [ app-group app-group-name ] [ counting ] [ disable ] [ logging ] [ time-range time-range-name ] ] *
If you specify a nonexistent object group in a rule, the rule does not match packets.
When you specify an application or application group for a rule, specify only PBAR-classified applications. NBAR-classified applications cannot match any packets. For more information about PBAR and NBAR, see "Configuring ARP."
4. Append a criterion to the rule for packet matching.
rule rule-id append { application application-name | app-group app-group-name | destination-ip object-group-name | service object-group-name | source-ip object-group-name }
By default, no criterion is appended to an object policy rule.
5. (Optional.) Configure a description for the rule.
rule rule-id comment text
By default, an object policy rule does not have a description.
Applying an IPv4 object policy to a zone pair
1. Enter system view.
system-view
2. Create a zone pair in MDC system view and enter zone pair view.
zone-pair security source source-zone-name destination destination-zone-name
For more information about this command, see Security Command Reference.
3. Apply an IPv4 object policy to the zone pair.
object-policy apply ip object-policy-name
By default, no object policy is applied to a zone pair.
Changing the rule match order
About this task
The device matches packets against object policy rules in the order the rules were configured. You can change the rule match order by changing the position of an object policy rule in the rule list.
Procedure
1. Enter system view.
system-view
2. Enter IPv4 object policy view.
object-policy ip object-policy-name
3. Move an IPv4 object policy rule.
move rule rule-id before insert-rule-id
Enabling rule matching acceleration
About this task
With this feature enabled, the system detects rule changes at specific intervals and automatically accelerates rule matching if any rule changes. If there are more than 100 rules of the IPv4 version exist, the detection interval for these rules is 20 seconds. If there are less than or equal to 100 rules of the IPv4 version, the detection interval for these rules is 2 seconds.
Restrictions and guidelines
Enabling rule matching acceleration fails if resources are insufficient and matching of all rules can be performed at the low speed.
Rule matching acceleration fails for changed or newly added rules if resources are insufficient and these rules cannot be used for matching.
If the IP address object group specified for an object policy rule is configured with excluded IP addresses or a wildcard mask, rule matching acceleration fails for the object policy.
If the IP address object group specified for an object policy rule contains a user or user group, the rule cannot be accelerated.
Procedure
1. Enter system view.
system-view
2. Enter IPv4 object policy view.
object-policy ip object-policy-name
3. Enable rule matching acceleration.
accelerate
By default, rule matching acceleration is enabled for an object policy.
Configuring IPv6 object policies
Creating an IPv6 object policy
1. Enter system view.
system-view
2. Create an IPv6 object policy and enter its view.
object-policy ipv6 object-policy-name
3. (Optional.) Configure a description for the object policy.
description text
By default, no description is configured for an object policy.
Configuring an IPv6 object policy rule
1. Enter system view.
system-view
2. Enter IPv6 object policy view.
object-policy ipv6 object-policy-name
3. Configure an IPv6 object policy rule.
rule [ rule-id ] { drop | pass | inspect app-profile-name } [ [ source-ip { object-group-name | any } ] [ destination-ip { object-group-name | any } ] [ service { object-group-name | any } ] [ vrf vrf-name ] [ application application-name ] [ app-group app-group-name ] [ counting ] [ disable ] [ logging ] [ time-range time-range-name ] ] *
If you specify a nonexistent object group in a rule, the rule does not match packets.
When you specify an application or application group for a rule, specify only PBAR-classified applications. NBAR-classified applications cannot match any packets. For more information about PBAR and NBAR, see "Configuring ARP."
4. Append a criterion to the rule for packet matching.
rule rule-id append { application application-name | app-group app-group-name | destination-ip object-group-name | service object-group-name | source-ip object-group-name }
By default, no criterion is appended to an object policy rule.
5. (Optional.) Configure a description for the rule.
rule rule-id comment text
By default, an object policy rule does not have a description.
Applying an IPv6 object policy to a zone pair
1. Enter system view.
system-view
2. Create a zone pair in MDC system view and enter zone pair view.
zone-pair security source source-zone-name destination destination-zone-name
For more information about this command, see Security Command Reference.
3. Apply an IPv6 object policy to the zone pair.
object-policy apply ipv6 object-policy-name
By default, no object policy is applied to a zone pair.
Changing the rule match order
About this task
The device matches packets against object policy rules in the order the rules were configured. You can change the rule match order by changing the position of an object policy rule in the rule list.
Procedure
1. Enter system view.
system-view
2. Enter IPv6 object policy view.
object-policy ipv6 object-policy-name
3. Move an IPv6 object policy rule.
move rule rule-id before insert-rule-id
Enabling rule matching acceleration
About this task
With this feature enabled, the system detects rule changes at specific intervals and automatically accelerates rule matching if any rule changes. If there are more than 100 rules of the IPv6 version exist, the detection interval for these rules is 20 seconds. If there are less than or equal to 100 rules of the IPv6 version, the detection interval for these rules is 2 seconds.
Restrictions and guidelines
Enabling rule matching acceleration fails if resources are insufficient and matching of all rules can be performed at the low speed.
Rule matching acceleration fails for changed or newly added rules if resources are insufficient and these rules cannot be used for matching.
If the IP address object group specified for an object policy rule is configured with excluded IP addresses or a wildcard mask, rule matching acceleration fails for the object policy.
If the IP address object group specified for an object policy rule contains a user or user group, the rule cannot be accelerated.
Procedure
1. Enter system view.
system-view
2. Enter IPv6 object policy view.
object-policy ipv6 object-policy-name
3. Enable rule matching acceleration.
accelerate
By default, rule matching acceleration is enabled for an object policy.
Display and maintenance commands for object policies
Execute display commands in any view.
|
Task |
Command |
|
Display acceleration information for object policies. |
display object-policy accelerate { summary { ip | ipv6 } | verbose { ip object-policy-name | ipv6 object-policy-name } } In IRF mode: display object-policy accelerate { summary { ip | ipv6 } | verbose { ip object-policy-name | ipv6 object-policy-name } slot slot-number } |
|
Display information about IPv4 object policies. |
display object-policy ip [ object-policy-name ] |
|
Display information about IPv6 object policies. |
display object-policy ipv6 [ object-policy-name ] |
|
Display information about the object policies applied to zone pairs. |
display object-policy zone-pair security [ source source-zone-name destination destination-zone-name ] |
|
Display statistics for object policies applied to a zone pair. |
display object-policy statistics zone-pair security source source-zone-name destination destination-zone-name [ ip | ipv6 ] |
Object policy configuration examples
Example: Configuring an IPv4 object policy
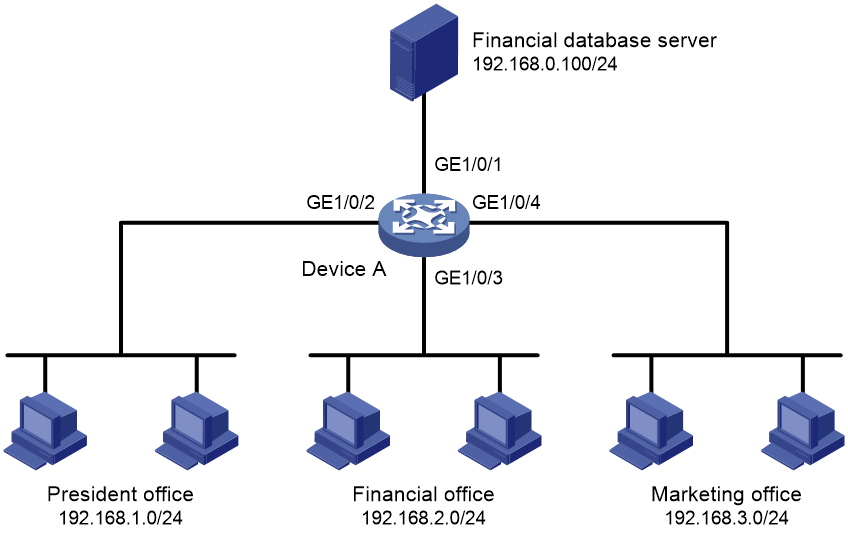
Network configuration
Configure object policies to achieve the following goals:
· The president office can access the financial database server through HTTP at any time.
· The financial office can access the financial database server through HTTP from 8:00 to 18:00 on weekdays.
· The marketing office cannot access the financial database server through HTTP at any time.
Procedure
1. Create a time range named work to cover 8:00 to 18:00 on weekdays.
<DeviceA> system-view
[DeviceA] time-range work 08:00 to 18:00 working-day
2. Create security zones:
# Create a security zone named president, and add GigabitEthernet 1/0/2 to the zone.
[DeviceA] security-zone name president
[DeviceA-security-zone-president] import interface gigabitethernet 1/0/2
[DeviceA-security-zone-president] quit
# Create a security zone named finance, and add GigabitEthernet 1/0/3 to the zone.
[DeviceA] security-zone name finance
[DeviceA-security-zone-finance] import interface gigabitethernet 1/0/3
[DeviceA-security-zone-finance] quit
# Create a security zone named market, and add GigabitEthernet 1/0/4 to the zone.
[DeviceA] security-zone name market
[DeviceA-security-zone-market] import interface gigabitethernet 1/0/4
[DeviceA-security-zone-market] quit
# Create a security zone named database, and add GigabitEthernet 1/0/1 to the zone.
[DeviceA] security-zone name database
[DeviceA-security-zone-database] import interface gigabitethernet 1/0/1
[DeviceA-security-zone-database] quit
3. Create object groups:
# Create an IPv4 address object group named president. Configure an IPv4 address object with the subnet address of 192.168.1.0/24 for the group.
[DeviceA] object-group ip address president
[DeviceA-obj-grp-ip-president] network subnet 192.168.1.0 24
[DeviceA-obj-grp-ip-president] quit
# Create an IPv4 address object group named finance. Configure an IPv4 address object with the subnet address of 192.168.2.0/24 for the group.
[DeviceA] object-group ip address finance
[DeviceA-obj-grp-ip-finance] network subnet 192.168.2.0 24
[DeviceA-obj-grp-ip-finance] quit
# Create an IPv4 address object group named market. Configure an IPv4 address object with the subnet address of 192.168.3.0/24 for the group.
[DeviceA] object-group ip address market
[DeviceA-obj-grp-ip-market] network subnet 192.168.3.0 24
[DeviceA-obj-grp-ip-market] quit
# Create an IPv4 address object group named database. Configure an IPv4 address object with the subnet address of 192.168.0.0/24 for the group.
[DeviceA] object-group ip address database
[DeviceA-obj-grp-ip-database] network subnet 192.168.0.0 24
[DeviceA-obj-grp-ip-database] quit
# Create a service object group named web. Configure a service object with the HTTP service.
[DeviceA] object-group service web
[DeviceA-obj-grp-service-web] service 6 destination eq 80
[DeviceA-obj-grp-service-web] quit
4. Create object policies and rules:
# Create an IPv4 object policy named president-database. Configure a rule that allows the president office to access the financial database server through HTTP at any time.
[DeviceA] object-policy ip president-database
[DeviceA-object-policy-ip-president-database] rule pass source-ip president destination-ip database service web
[DeviceA-object-policy-ip-president-database] quit
# Create an IPv4 object policy named finance-database. Configure a rule that allows the financial office to access the financial database server through HTTP from 8:00 to 18:00 on weekdays.
[DeviceA] object-policy ip finance-database
[DeviceA-object-policy-ip-finance-database] rule pass source-ip finance destination-ip database service web time-range work
[DeviceA-object-policy-ip-finance-database] quit
# Create an IPv4 object policy named market-database. Configure a rule that prohibits the marketing office from accessing the financial database server through HTTP at any time.
[DeviceA] object-policy ip market-database
[DeviceA-object-policy-ip-market-database] rule drop source-ip market destination-ip database service web
[DeviceA-object-policy-ip-market-database] quit
5. Apply object policies to zone pairs:
# Create a zone pair from security zone president to security zone database. Apply IPv4 object policy president-database to the zone pair.
[DeviceA] zone-pair security source president destination database
[DeviceA-zone-pair-security-president-database] object-policy apply ip president-database
[DeviceA-zone-pair-security-president-database] quit
# Create a zone pair from security zone finance to security zone database. Apply IPv4 object policy finance-database to the zone pair.
[DeviceA] zone-pair security source finance destination database
[DeviceA-zone-pair-security-finance-database] object-policy apply ip finance-database
[DeviceA-zone-pair-security-finance-database] quit
# Create a zone pair from security zone market to security zone database. Apply IPv4 object policy market-database to the zone pair.
[DeviceA] zone-pair security source market destination database
[DeviceA-zone-pair-security-market-database] object-policy apply ip market-database
[DeviceA-zone-pair-security-market-database] quit
Verifying the configuration
# Use a PC in each office to access the Web service of the financial database server through the browser. (Details not shown.)