- Table of Contents
-
- 03-Security Configuration Guide
- 00-Preface
- 01-Security zone configuration
- 02-Security policy configuration
- 03-Object group configuration
- 04-Object policy configuration
- 05-AAA configuration
- 06-IPoE configuration
- 07-Portal configuration
- 08-User identification configuration
- 09-Password control configuration
- 10-Public key management
- 11-PKI configuration
- 12-SSH configuration
- 13-SSL configuration
- 14-ASPF configuration
- 15-APR configuration
- 16-Session management
- 17-Connection limit configuration
- 18-Attack detection and prevention configuration
- 19-DDoS protection configuration
- 20-uRPF configuration
- 21-ARP attack protection configuration
- 22-ND attack defense configuration
- 23-IP-MAC binding configuration
- 24-Keychain configuration
- 25-Crypto engine configuration
- 26-SMS configuration
- 27-Terminal identification configuration
- 28-Flow manager configuration
- 29-Location identification configuration
- 30-Server connection detection configuration
- 31-Trusted access control configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 16-Session management | 198.38 KB |
Restrictions and guidelines: Session management configuration
Session management tasks at a glance
Setting the session aging time for different protocol states
Setting the session aging time for different application layer protocols or applications
Specifying persistent sessions
Specifying the mode for session state machine
Enabling session synchronization
Configuring session dual-active mode
Enabling session flow redirection
Enabling session statistics collection for software fast forwarding
Enabling session statistics collection for hardware fast forwarding
Enabling top session statistics
Enabling the deny session feature
Enabling top deny session statistics
Configuring alarms for abrupt session changes
Configuring alarms for abrupt session table usage changes
Configuring alarms for abrupt session creation rate changes
Configuring alarms for abrupt session attempt rate changes
Enabling ALG to process fragments
Display and maintenance commands for session management
Managing sessions
About session management
Session management is a common module, providing basic services for NAT, ASPF, and attack detection and protection to implement their session-based services.
Session management defines packet exchanges at transport layer as sessions. It updates session states and ages out sessions according to data flows from the initiators or responders. Session management allows multiple features to process the same service packet.
Session management operation
Session management tracks the session status by inspecting the transport layer protocol information. It performs unified status maintenance and management of all connections based on session tables and relation tables.
When a connection request passes through the device from a client to a server, the device creates a session entry. The entry can contain the request and response information, such as:
· Source IP address and port number.
· Destination IP address and port number.
· Transport layer protocol.
· Application layer protocol.
· Protocol state of the session.
A multichannel protocol requires that the client and the server negotiate a new connection based on an existing connection to implement an application. Session management enables the device to create a relation entry for each connection during the negotiation phase. The entry is used to associate the connection with the application. Relation entries will be removed after the associated connections are established.
If the destination IP address of a packet is a multicast IP address, the packet will be forwarded out of multiple ports. When a multicast connection request is received on an inbound interface, the device performs the following operations:
· Creates a multicast session entry on the inbound interface.
· Creates a corresponding multicast session entry for each outbound interface.
Unless otherwise stated, "session entry" in this chapter refers to both unicast and multicast session entries.
Session types
When receiving the first packet of a data flow, the device processes the packet and creates a session entry based on the processing result. For subsequent packets of the data flow, the device performs fast forwarding based on the session entry. For more information about fast forwarding, see Layer 3—IP Services Configuration Guide.
Sessions are classified into the following types according to the action taken on the packets that match a session entry:
· Permit session—The device permits all packets of a permit session. The device generates a permit session entry for a data flow if it permits the first packet of the data flow.
A permit session can only track connection status. It cannot deny potential attack packets. To deny specific packets, you must use permit sessions together with security features.
· Deny session—The device drops all packets of a deny session. The device generates a deny session entry for a data flow if it drops the first packet of the data flow.
Unless otherwise stated, the sessions in this document refer to permit sessions.
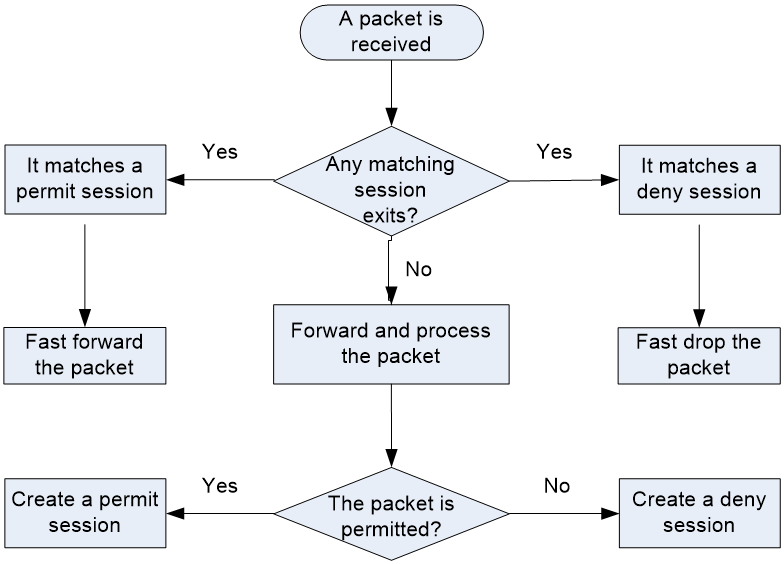
Figure 1 shows the workflow of session-based traffic forwarding.
Figure 1 Session-based traffic forwarding
Session management functions
Session management enables the device to provide the following functions:
· Creates sessions for protocol packets, updates session states, and sets aging time for sessions in different protocol states.
· Supports port mapping for application layer protocols (see "Configuring APR"), enabling application layer protocols to use customized ports.
· Sets aging time for sessions based on application layer protocols.
· Supports ICMP/ICMPv6 error packet mapping, enabling the device to search for original sessions according to the payloads in the ICMP/ICMPv6 error packets.
Because error packets are generated due to host errors, the mapping can help speed up the aging of the original sessions.
· Supports persistent sessions, which are kept alive for a long period of time.
· Supports session management for the control channels and dynamic data channels of application layer protocols, for example, FTP.
· Supports real-time synchronization for sessions and for dynamic entries of session-based services, such as NAT, ALG, and ASPF.
vSystem support for features
Non-default vSytems support the following features:
· Setting the aging time for the sessions in a protocol state.
· Setting the aging time for sessions of an application layer protocol or an application.
· Configuring session logging.
· Enabling session statistics collection for software fast forwarding.
· Enabling session statistics collection for hardware fast forwarding.
For information about the support of non-default vSystems for the commands, see session management command reference. For information about vSystem, see Virtual Technologies Configuration Guide.
Restrictions and guidelines: Session management configuration
For a TCP session in ESTABLISHED state, the priority order of the associated aging time is as follows:
· Aging time for persistent sessions.
· Aging time for sessions of application layer protocols.
· Aging time for sessions in different protocol states.
If the device has excessive sessions, do not set the aging time shorter than the default for a certain protocol state or an application layer protocol. Short aging time settings can make the device slow in response.
Session management tasks at a glance
To configure session management, perform the following tasks:
· Configure session management timers
¡ Setting the session aging time for different protocol states
¡ Setting the session aging time for different application layer protocols or applications
¡ Specifying persistent sessions
· Specifying the mode for session state machine
· Configuring session synchronization
¡ Enabling session synchronization
¡ Configuring session dual-active mode
· Enabling session flow redirection
· Configuring session statistics collection
¡ Enabling session statistics collection for software fast forwarding
¡ Enabling session statistics collection for hardware fast forwarding
¡ Enabling top session statistics
· Configuring alarms for abrupt session changes
· Enabling ALG to process fragments
Setting the session aging time for different protocol states
About this task
If a session in a certain protocol state has no packet hit before the aging time expires, the device automatically removes the session.
Procedure
1. Enter system view.
system-view
2. Set the session aging time for different protocol states.
session aging-time state { fin | icmp-reply | icmp-request | icmpv6-reply | icmpv6-request | rawip-open | rawip-ready | syn | tcp-close | tcp-est | tcp-time-wait | udp-open | udp-ready } time-value
The default aging time for sessions in different protocol states is as follows:
¡ FIN_WAIT: 30 seconds.
¡ ICMP-REPLY: 30 seconds.
¡ ICMP-REQUEST: 60 seconds.
¡ ICMPv6-REPLY: 30 seconds.
¡ ICMPv6-REQUEST: 60 seconds.
¡ RAWIP-OPEN: 30 seconds.
¡ RAWIP-READY: 60 seconds.
¡ TCP SYN-SENT and SYN-RCV: 30 seconds.
¡ TCP-CLOSE: 2 seconds.
¡ TCP ESTABLISHED: 3600 seconds.
¡ TCP-TIME-WAIT: 2 seconds.
¡ UDP-OPEN: 30 seconds.
¡ UDP-READY: 60 seconds.
Setting the session aging time for different application layer protocols or applications
About this task
The aging time for sessions of different application layer protocols or applications are valid for TCP sessions in ESTABLISHED state or UDP sessions in READY state. For sessions used by other application layer protocols, the aging time for sessions in different protocol states applies.
Supported application layer protocols or applications specified in this command depend on the APR module. For information about APR, see "Configuring APR."
Procedure
1. Enter system view.
system-view
2. Set the session aging time for different application layer protocols.
session aging-time application application-name time-value
By default, the aging time is 1200 seconds for sessions of application layer protocols or applications except for the following sessions:
¡ BOOTPC sessions: 120 seconds.
¡ BOOTPS sessions: 120 seconds.
¡ DNS sessions: 30 seconds.
¡ FTP sessions: 3600 seconds.
¡ FTP-DATA sessions: 240 seconds.
¡ GPRS-DATA sessions: 60 seconds.
¡ GPRS-SIG sessions: 60 seconds.
¡ GTP-CONTROL sessions: 60 seconds.
¡ GTP-USER sessions: 60 seconds.
¡ H.225 sessions: 3600 seconds.
¡ H.245 sessions: 3600 seconds.
¡ HTTPS sessions: 600 seconds.
¡ ILS sessions: 3600 seconds.
¡ L2TP sessions: 120 seconds.
¡ MGCP-CALLAGENT sessions: 60 seconds.
¡ MGCP-GATEWAY sessions: 60 seconds.
¡ NETBIOS-DGM sessions: 3600 seconds.
¡ NETBIOS-NS sessions: 3600 seconds.
¡ NETBIOS-SSN sessions: 3600 seconds.
¡ NTP sessions: 120 seconds.
¡ PPTP sessions: 3600 seconds.
¡ QQ sessions: 120 seconds.
¡ RAS sessions: 300 seconds.
¡ RIP sessions: 120 seconds.
¡ RSH sessions: 60 seconds.
¡ RTSP session: 3600 seconds.
¡ SCCP sessions: 3600 seconds.
¡ SIP sessions: 300 seconds.
¡ SNMP sessions: 120 seconds.
¡ SNMPTRAP sessions: 120 seconds.
¡ SQLNET sessions: 600 seconds.
¡ STUN sessions: 600 seconds.
¡ SYSLOG sessions: 120 seconds.
¡ TACACS-DS sessions: 120 seconds.
¡ TFTP sessions: 60 seconds.
¡ WHO sessions: 120 seconds.
¡ XDMCP sessions: 3600 seconds.
Specifying persistent sessions
About this task
This task is only for TCP sessions in ESTABLISHED state. You can specify TCP sessions that match the permit statements in the specified ACL as persistent sessions, and set longer lifetime or never-age-out persistent sessions.
A persistent session is not removed until one of the following events occurs:
· The session entry ages out.
· The device receives a connection close request from the initiator or responder.
· You manually clear the session entries.
Procedure
1. Enter system view.
system-view
2. Specify persistent sessions.
session persistent acl [ ipv6 ] acl-number [ aging-time time-value ]
Specifying the mode for session state machine
About this task
When asymmetric-path traffic exists in a hot backup system operating in session active/standby mode, set the mode of session state machine to loose to avoid abnormal traffic loss.
When asymmetric-path traffic exists in a hot backup system operating in session dual-active mode, set the mode of session state machine to compact for disconnected sessions to age out timely.
As a best practice, change the mode of session state machine only when asymmetric-path traffic exists. This feature degrades performance of session-based security check. Make sure you are fully aware of its impact when you use it on a live network.
Procedure
1. Enter system view.
system-view
2. Specify the mode for session state machine.
session state-machine mode { compact | loose }
By default, session state machine is in strict mode.
Enabling session synchronization
About this task
This feature enables devices to synchronize sessions and dynamic entries of session-based services. Typically, these devices back up each other and use a virtual IP address to communicate with a peer device. When the primary device fails, a backup device takes over to process and forward service traffic. The failover process is transparent to the peer device, and does not interrupt ongoing services.
This feature also provides automatic backup service for the device. The system automatically backs up session tables and relation tables that are generated by applications that use ALG. These applications include H.323, SIP, and ILS.
Enable session synchronization for DNS and HTTP in the following situations:
· Users are aware that the current HTTP or DNS sessions will last for a long time.
· HTTP or DNS session backup is required.
In a network that has asymmetric traffic, heavy service traffic might cause service delay or service unavailable because sessions cannot be backed up timely. For example, one device forwards the TCP SYN packets, and another device forwards its ACK packets. If the session tables of the two devices are not synchronized, the TCP packets will be dropped because of state error. To resolve this issue, enable session synchronization for asymmetric traffic.
Restrictions and guidelines
On an IRF fabric, the NAT configuration is dependent of session synchronization. If session synchronization is enabled, make sure NAT is configured on global interfaces such as aggregate interfaces and redundant interfaces. If you configure NAT on physical ports, disable session synchronization as a best practice.
This feature cannot be used together with the hot-backup enable command. For information about the HA group, see High Availability Command Reference.
Procedure
1. Enter system view.
system-view
2. Enable session synchronization.
session synchronization enable [ asymmetric ]
By default, session synchronization is disabled.
After session synchronization is enabled, session synchronization is enabled for all application layer protocols except DNS and HTTP by default.
3. (Optional.) Enable session synchronization for DNS, HTTP, or both.
session synchronization { dns | http } *
By default, session synchronization is disabled for DNS and HTTP.
Configuring session dual-active mode
About this task
In a hot backup system operating in session active/standby mode, only one device processes security services. Session dual-active mode increases load capacity of the system by enabling both devices to process security services.
To balance the service load on the devices, you can use one of the following session creation modes:
· Hash-based session creation—A session is created on the device to which its first packet is relayed according to the hash result. The device where a session is created might not be the device that receives the traffic. This mode applies if traffic is unevenly distributed among the devices.
· Local-based session creation—A session is created on the device where the first packet of the session arrives. This mode applies if traffic is evenly distributed among the devices.
In a hot backup system operating in session dual-active mode, a device cannot identify the direction of packets in a UDP traffic flow due to UDP mechanisms. By default, if the return packets of a session do not match any sessions, the device creates a new session. This results in the following issues:
· If the security control policy permits a UDP traffic flow in one direction, the return packets of the flow are dropped.
· If the security control policy permits a UDP traffic flow in both directions, two sessions are created for the flow. This affects traffic processing of security services.
To resolve these issues, you can enable transparent transmission for UDP packets. This feature allows a device to relay UDP packets that do not match any sessions to the other device in the hot back system. If the UDP packets also do not match any sessions on the other device, a new session is created locally.
In a hot backup system operating in session dual-active mode, a device can identify the direction of packets in a TCP traffic flow. If the device receives the packets of a new TCP traffic flow, it creates a session. If the return packets of an existing TCP traffic flow do not match any sessions, the device relays the packets to the other device.
Restrictions and guidelines
· In dual-active mode, devices support only Layer 3 forwarding. Layer 2 forwarding is not supported.
· In dual-active mode, devices support only the flow-based policy for flow classification. For more information about flow classification policies, see multi-CPU packet distribution in Layer 3—IP Services Configuration Guide.
· AFT is not supported in dual-active mode.
Procedure
1. Enter system view.
system-view
2. Enable session dual-active mode.
session dual-active enable
By default, session dual-active mode is disabled. The device is operating in session active/standby mode.
3. Enable session synchronization.
See "Enabling session synchronization."
4. (Optional.) Set the mode of session state machine to compact.
See "Specifying the mode for session state machine."
Enabling session flow redirection
About this task
This feature ensures that packets and return packets of a data flow can be correctly processed when they are forwarded to different security modules. After this feature is enabled, the system immediately synchronizes the session information created for the packets to the security module where return packets are processed. When the sessions for packets are deleted, the synchronized session information in other security modules will be deleted accordingly.
Typically, the system uses OpenFlow entries for packet forwarding to ensure that packets and return packets of a data flow can be processed in the same security module. The number of OpenFlow entries supported by the device is limited. When the upper limit is reached, packets and return packets of a data flow might be forwarded to different security modules, which causes packet processing failures. To resolve this problem, disable OpenFlow entry generation on service modules and enable session flow redirection.
For session flow redirection to take effect, make sure the OpenFlow entry generation by service modules is disabled. For information about disabling OpenFlow entry generation by service modules, see configuration guides of related service modules.
When both session flow redirection and hardware fast forwarding are enabled, the device does not issue session entries to hardware chips of security modules. As a result, hardware fast forwarding does not take effect on security modules. To use hardware fast forwarding and session flow redirection together, you must also enable hardware fast forwarding for session flow redirection. This feature enables the device to issue the session entry created for the first packet of a flow to hardware chips to speed up forwarding of subsequent traffic of the flow. For more information about hardware fast forwarding, see Layer 3—IP Services Configuration Guide.
Restrictions and guidelines
On networks where session flow redirection is enabled, if EIM PAT is used for address translation, configure the aggregation group to load share packets based on destination IP addresses. For information about EIM mapping mode, see NAT Configuration Guide. For information about link-aggregation load sharing for an aggregation group, see Ethernet link aggregation in Layer 2—LAN Switching Configuration Guide.
Hardware fast forwarding for session flow redirection takes effect only when both session flow redirection and hardware fast forwarding are enabled.
Procedure
1. Enter system view.
system-view
2. Enable session flow redirection.
session flow-redirect enable
By default, session flow redirection is disabled. Flows are redirected based on OpenFlow entries.
3. (Optional.) Enable hardware fast forwarding for session flow redirection.
session flow-redirect hardware-fast-forwarding
By default, hardware fast forwarding is disabled for session flow redirection.
Configuring session logging
About this task
Session logs provide information about user access, IP address translation, and network traffic for security auditing. These logs are sent to the log server or the information center.
The device supports time-based or traffic-based logging:
· Time-based logging—The device outputs session logs regularly.
· Traffic-based logging—The device outputs a session log when the traffic amount of a session reaches a threshold only when the session statistics collection for software fast forwarding feature is enabled. After outputting a session log, the device resets the traffic counter for the session. The traffic-based thresholds can be byte-based and packet-based. If you set both thresholds, the last configuration takes effect.
If you set both time-based and traffic-based logging, the device outputs a session log when whichever is reached. After outputting a session log, the device resets the traffic counter and restarts the interval for the session.
If you enable session logging but do not enable logging for session creation or deletion, the device does not output a session log when a session entry is created or removed.
Restrictions and guidelines
The session logging feature must work with the flow log or fast log output feature to generate session logs. Session logs can be output in flow log or fast log output format. By default, they are output in flow log format. For information about flow log and fast log output, see Network Management and Monitoring.
Procedure
1. Enter system view.
system-view
2. (Optional.) Set the threshold for time-based session logging.
session log time-active time-value
By default, no threshold is set for time-based session logging.
3. (Optional.) Set a threshold for traffic-based logging.
session log { bytes-active bytes-value | packets-active packets-value }
By default, no threshold is set for traffic-based logging.
4. (Optional.) Enable logging for session creation.
session log flow-begin
By default, logging for session creation is disabled.
5. (Optional.) Enable logging for session deletion.
session log flow-end
By default, logging for session deletion is disabled.
6. Enter interface view.
interface interface-type interface-number
7. Enable session logging.
session log enable { ipv4 | ipv6 } [ acl acl-number ] { inbound | outbound }
By default, session logging is disabled.
Enabling session statistics collection for software fast forwarding
About this task
This feature enables the device to collect session-based outbound and inbound packets and bytes. You can display session statistics based on different criteria.
· To display statistics per unicast session, use the display session table command.
· To display statistics per unicast packet type, use the display session statistics command.
· To display statistics per multicast session, use the display session table multicast command.
· To display statistics per multicast packet type, use the display session statistics multicast command.
This feature does not take effect on packets processed by hardware fast forwarding. To collect statistics of packets processed by hardware fast forwarding, enable the statistics collection for hardware fast forwarding feature. For information about fast forwarding, see Layer 3—IP Services Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enable session statistics collection for software fast forwarding.
session statistics enable
By default, session statistics collection is disabled for software fast forwarding.
Enabling session statistics collection for hardware fast forwarding
About this task
This feature enables the device to collect the packets processed by hardware fast forwarding for the session and other service modules. The session and other service modules will use the collected statistics for more accurate statistics collection.
Procedure
1. Enter system view.
system-view
2. Enable session statistics collection and set the logging threshold for hardware fast forwarding.
session statistics hardware-fast-forwarding { bytes-active bytes-value | packets-active packets-value }
By default, session statistics collection is disabled for hardware fast forwarding.
If you configure this command together with the session log { bytes-active | packets-active } command, make sure you have specified the same type of logging threshold.
Enabling top session statistics
About this task
This feature collects the number of sessions for session-based services and ranks the sessions by source address and by destination address separately.
Procedure
1. Enter system view.
system-view
2. Enable the top session statistics feature.
session top-statistics enable
By default, the top session statistics feature is disabled.
3. (Optional.) Display top session statistics.
display session top-statistics { last-1-hour | last-24-hours | last-30-days }
Configuring deny sessions
Enabling the deny session feature
About this task
By default, the device generates sessions only for permitted packets. If the device drops the first packet of a data flow, it will forward subsequent packets of the data flow according to the typical forwarding process. To improve forwarding performance, enable the deny session feature. This feature allows the device to generate a deny session for the dropped first packet of each data flow and perform fast packet dropping based on the deny sessions.
The system deletes deny sessions based on the deny session aging time. The deny session aging time is not refreshed when packets match deny sessions.
The maximum ratio of deny sessions to all sessions limits the number of deny sessions. When the ratio of deny session entries reaches this maximum ratio, the device stops generating deny sessions.
Restrictions and guidelines
The device generates deny sessions only for the packets dropped by the ASPF or connection limit module.
The device does not issue deny session entries to chips.
When session synchronization is enabled, the device synchronizes only permit session entries.
Procedure
1. Enter system view.
system-view
2. Enable the deny session feature for modules.
session fast-drop { aspf | connection-limit } * enable
By default, the deny session feature is enabled.
3. Set the aging time for deny sessions.
session fast-drop aging-time time-value
By default, the aging time for deny sessions is 3 seconds.
4. Set the maximum ratio of deny sessions to all sessions.
session fast-drop resource-ratio ratio
By default, the maximum ratio of deny sessions to all sessions is 10‰.
Enabling top deny session statistics
About this task
This feature collects the number of deny sessions for session-based services and ranks the deny sessions by source address and by destination address.
To display the top deny session statistics, use the display session fast-drop top-statistics command.
Procedure
1. Enter system view.
system-view
2. Enable the top deny session statistics feature.
session fast-drop top-statistics enable
By default, the top deny session statistics feature is disabled.
Configuring alarms for abrupt session changes
Configuring alarms for abrupt session table usage changes
About this task
Perform this task for the device to generate alarms for abrupt increase or drop in the session table usage. With this feature enabled, the system collects the session table usage at an interval of 10 seconds and checks whether the following indicators reach the corresponding alarm thresholds:
· Session table usage change in percentage—Obtained by dividing the difference between the session entry counts at the beginning and end of a collection interval by the session entry count at the beginning of the collection interval.
· Base session table usage in percentage—Obtained by dividing the session entry count at the beginning of a collection interval by the supported maximum number of session entries.
If both of the following conditions are met in a detection interval, the system generates an alarm for the abrupt change of the session table usage:
· The session table usage change threshold is reached.
· The base session table usage threshold is crossed.
Procedure
1. Enter system view.
system-view
2. Enable alarms for abrupt session table usage changes.
session alarm usage-abrupt enable
By default, alarms are disabled for abrupt session table usage changes.
3. Set the alarm thresholds for abrupt session table usage changes.
session alarm usage-abrupt threshold threshold-value [ base-threshold base-value ]
By default, the session table usage change threshold is 20%, and the base session table usage threshold is 10%.
Configuring alarms for abrupt session creation rate changes
About this task
Perform this task for the device to generate alarms for abrupt increase or drop in the session creation rate. With this feature enabled, the system collects the session creation rate at an interval of 10 seconds and checks whether the following indicators reach the corresponding alarm thresholds:
· Session creation rate change in percentage—Obtained by dividing the difference between the session creation rates at the beginning and end of a collection interval by the session creation rate at the beginning of the collection interval.
· Base session creation rate in percentage—Obtained by dividing the session creation rate at the beginning of a collection interval by 100000.
If both of the following conditions are met in a detection interval, the system generates an alarm for the abrupt change of the session creation rate:
· The session creation rate change threshold is reached.
· The base session creation rate threshold is crossed.
Procedure
1. Enter system view.
system-view
2. Enable alarms for abrupt session creation rate changes.
session alarm rate-abrupt enable
By default, alarms are disabled for abrupt session creation rate changes.
3. Set the alarm thresholds for abrupt session creation rate changes.
session alarm rate-abrupt threshold threshold-value [ base-threshold base-value ]
By default, the session creation rate change threshold is 20%, and the base session creation rate threshold is 10%.
Configuring alarms for abrupt session attempt rate changes
About this task
Perform this task for the device to generate alarms for abrupt increase or drop in the session creation attempt rate. With this feature enabled, the system collects the session creation attempt rate at an interval of 10 seconds and checks whether the following indicators reach the corresponding alarm thresholds:
· Session attempt rate change in percentage—Obtained by dividing the difference between the session creation attempt rates at the beginning and end of a collection interval by the session creation attempt rate at the beginning of the collection interval.
· Base session attempt rate in percentage—Obtained by dividing the session creation attempt rate at the beginning of a collection interval by 100000.
If both of the following conditions are met in a detection interval, the system generates an alarm for the abrupt change of the session creation attempt rate:
· The session attempt rate change threshold is reached.
· The base session attempt rate threshold is crossed.
Procedure
1. Enter system view.
system-view
2. Enable alarms for abrupt session attempt rate changes.
session alarm try-rate-abrupt enable
By default, alarms are disabled for abrupt session attempt rate changes.
3. Set the alarm thresholds for abrupt session attempt rate changes.
session alarm try-rate-abrupt threshold threshold-value [ base-threshold base-value ]
By default, the session attempt rate change threshold is 20%, and the base session attempt rate threshold is 10%.
Enabling ALG to process fragments
About this task
This task enables ALG to process fragments of specified protocols. In the current software version, ALG can process only SIP fragments.
Procedure
1. Enter system view.
system-view
2. Enable ALG to process fragments.
session alg fragment sip
By default, ALG does not process fragments.
Display and maintenance commands for session management
|
IMPORTANT: Non-default vSystems do not support some of the display and maintenance commands. For information about vSystem support for these commands, see session management command reference. |
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display the aging time for sessions of different application layer protocols. |
display session aging-time application |
|
Display the aging time for sessions in different protocol states. |
display session aging-time state |
|
Display unicast deny session statistics. |
In standalone mode: display session fast-drop statistics [ summary ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display session fast-drop statistics [ summary ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display IPv4 unicast deny session entries. |
In standalone mode: display session fast-drop table ipv4 [ slot slot-number [ cpu cpu-number ] ] [ verbose ] In IRF mode: display session fast-drop table ipv4 [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] [ verbose ] |
|
Display IPv6 unicast deny session entries. |
In standalone mode: display session fast-drop table ipv6 [ slot slot-number [ cpu cpu-number ] ] [ verbose ] In IRF mode: display session fast-drop table ipv6 [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] [ verbose ] |
|
Display top deny session statistics. |
display session fast-drop top-statistics { last-1-hour | last-24-hours | last-30-days } |
|
Display relation table entries. |
In standalone mode: display session relation-table { ipv4 | ipv6 } [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display session relation-table { ipv4 | ipv6 } [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display unicast session statistics. |
In standalone mode: display session statistics [ history-max | summary ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display session statistics [ history-max | summary ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display statistics about redirected sessions. |
In standalone mode: display session statistics flow-redirect { message | packet | session } [ slot slot-number cpu cpu-number ] In IRF mode: display session statistics flow-redirect { message | packet | session } [ chassis chassis-number slot slot-number cpu cpu-number ] |
|
Display IPv4 unicast session statistics. |
In standalone mode: display session statistics ipv4 [ [ responder ] { application application-name | destination-ip destination-ip | destination-port destination-port | destination-zone destination-zone-name | interface interface-type interface-number | protocol { dccp | dns | ftp | gtp | h323 | http | icmp | ils | mgcp | nbt | pptp | raw-ip | rsh | rtsp | sccp | sctp | sip | smtp | sqlnet | ssh | tcp | telnet | tftp | udp | udp-lite | xdmcp } | security-policy-rule rule-name | source-ip source-ip | source-port source-port | source-zone source-zone-name | state { dccp-closereq | dccp-closing | dccp-open | dccp-partopen | dccp-request | dccp-respond | dccp-timewait | icmp-reply | icmp-request | rawip-open | rawip-ready | sctp-closed | sctp-cookie-echoed | sctp-cookie-wait | sctp-established | sctp-shutdown-ack-sent | sctp-shutdown-recd | sctp-shutdown-sent | tcp-close | tcp-close-wait | tcp-est | tcp-fin-wait | tcp-last-ack | tcp-syn-recv | tcp-syn-sent | tcp-syn-sent2 | tcp-time-wait | udp-open | udp-ready | udplite-open | udplite-ready } | vpn-instance vpn-instance-name } * ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display session statistics ipv4 [ [ responder ] { application application-name | destination-ip destination-ip | destination-port destination-port | destination-zone destination-zone-name | interface interface-type interface-number | protocol { dccp | dns | ftp | gtp | h323 | http | icmp | ils | mgcp | nbt | pptp | raw-ip | rsh | rtsp | sccp | sctp | sip | smtp | sqlnet | ssh | tcp | telnet | tftp | udp | udp-lite | xdmcp } | security-policy-rule rule-name | source-ip source-ip | source-port source-port | source-zone source-zone-name | state { dccp-closereq | dccp-closing | dccp-open | dccp-partopen | dccp-request | dccp-respond | dccp-timewait | icmp-reply | icmp-request | rawip-open | rawip-ready | sctp-closed | sctp-cookie-echoed | sctp-cookie-wait | sctp-established | sctp-shutdown-ack-sent | sctp-shutdown-recd | sctp-shutdown-sent | tcp-close | tcp-close-wait | tcp-est | tcp-fin-wait | tcp-last-ack | tcp-syn-recv | tcp-syn-sent | tcp-syn-sent2 | tcp-time-wait | udp-open | udp-ready | udplite-open | udplite-ready } | vpn-instance vpn-instance-name } * ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display IPv6 unicast session statistics. |
In standalone mode: display session statistics ipv6 [ [ responder ] { application application-name | destination-ip destination-ip | destination-port destination-port | destination-zone destination-zone-name | interface interface-type interface-number | protocol { dccp | dns | ftp | gtp | h323 | http | icmpv6 | ils | mgcp | nbt | pptp | raw-ip | rsh | rtsp | sccp | sctp | sip | smtp | sqlnet | ssh | tcp | telnet | tftp | udp | udp-lite | xdmcp } | security-policy-rule rule-name | source-ip source-ip | source-port source-port | source-zone source-zone-name | state { dccp-closereq | dccp-closing | dccp-open | dccp-partopen | dccp-request | dccp-respond | dccp-timewait | icmpv6-reply | icmpv6-request | rawip-open | rawip-ready | sctp-closed | sctp-cookie-echoed | sctp-cookie-wait | sctp-established | sctp-shutdown-ack-sent | sctp-shutdown-recd | sctp-shutdown-sent | tcp-close | tcp-close-wait | tcp-est | tcp-fin-wait | tcp-last-ack | tcp-syn-recv | tcp-syn-sent | tcp-syn-sent2 | tcp-time-wait | udp-open | udp-ready | udplite-open | udplite-ready } | vpn-instance vpn-instance-name } * ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display session statistics ipv6 [ [ responder ] { application application-name | destination-ip destination-ip | destination-port destination-port | destination-zone destination-zone-name | interface interface-type interface-number | protocol { dccp | dns | ftp | gtp | h323 | http | icmpv6 | ils | mgcp | nbt | pptp | raw-ip | rsh | rtsp | sccp | sctp | sip | smtp | sqlnet | ssh | tcp | telnet | tftp | udp | udp-lite | xdmcp } | security-policy-rule rule-name | source-ip source-ip | source-port source-port | source-zone source-zone-name | state { dccp-closereq | dccp-closing | dccp-open | dccp-partopen | dccp-request | dccp-respond | dccp-timewait | icmpv6-reply | icmpv6-request | rawip-open | rawip-ready | sctp-closed | sctp-cookie-echoed | sctp-cookie-wait | sctp-established | sctp-shutdown-ack-sent | sctp-shutdown-recd | sctp-shutdown-sent | tcp-close | tcp-close-wait | tcp-est | tcp-fin-wait | tcp-last-ack | tcp-syn-recv | tcp-syn-sent | tcp-syn-sent2 | tcp-time-wait | udp-open | udp-ready | udplite-open | udplite-ready } | vpn-instance vpn-instance-name } * ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display multicast session statistics. |
In standalone mode: display session statistics multicast [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display session statistics multicast [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display IPv4 unicast session table entries. |
In standalone mode: display session table ipv4 [ slot slot-number [ cpu cpu-number ] ] [ [ responder ] { application application-name | destination-ip start-destination-ip [ end-destination-ip ] | destination-port destination-port | destination-zone destination-zone-name | interface interface-type interface-number | protocol { dccp | icmp | raw-ip | sctp | tcp | udp | udp-lite } | security-policy-rule rule-name | source-ip start-source-ip [ end-source-ip ] | source-port source-port | source-zone source-zone-name | state { dccp-closereq | dccp-closing | dccp-open | dccp-partopen | dccp-request | dccp-respond | dccp-timewait | icmp-reply | icmp-request | rawip-open | rawip-ready | sctp-closed | sctp-cookie-echoed | sctp-cookie-wait | sctp-established | sctp-shutdown-ack-sent | sctp-shutdown-recd | sctp-shutdown-sent | tcp-close | tcp-close-wait | tcp-est | tcp-fin-wait | tcp-last-ack | tcp-syn-recv | tcp-syn-sent | tcp-syn-sent2 | tcp-time-wait | udp-open | udp-ready | udplite-open | udplite-ready } | vpn-instance vpn-instance-name } * ] [ verbose ] In IRF mode: display session table ipv4 [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] [ [ responder ] { application application-name | destination-ip start-destination-ip [ end-destination-ip ] | destination-port destination-port | destination-zone destination-zone-name | interface interface-type interface-number | protocol { dccp | icmp | raw-ip | sctp | tcp | udp | udp-lite } | security-policy-rule rule-name | source-ip start-source-ip [ end-source-ip ] | source-port source-port | source-zone source-zone-name | state { dccp-closereq | dccp-closing | dccp-open | dccp-partopen | dccp-request | dccp-respond | dccp-timewait | icmp-reply | icmp-request | rawip-open | rawip-ready | sctp-closed | sctp-cookie-echoed | sctp-cookie-wait | sctp-established | sctp-shutdown-ack-sent | sctp-shutdown-recd | sctp-shutdown-sent | tcp-close | tcp-close-wait | tcp-est | tcp-fin-wait | tcp-last-ack | tcp-syn-recv | tcp-syn-sent | tcp-syn-sent2 | tcp-time-wait | udp-open | udp-ready | udplite-open | udplite-ready } | vpn-instance vpn-instance-name } * ] [ verbose ] |
|
Display IPv6 unicast session table entries. |
In standalone mode: display session table ipv6 [ slot slot-number [ cpu cpu-number ] ] [ [ responder ] { application application-name | destination-ip start-destination-ip [ end-destination-ip ] | destination-port destination-port | destination-zone destination-zone-name | interface interface-type interface-number | protocol { dccp | icmpv6 | raw-ip | sctp | tcp | udp | udp-lite } | security-policy-rule rule-name | source-ip start-source-ip [ end-source-ip ] | source-port source-port | source-zone source-zone-name | state { dccp-closereq | dccp-closing | dccp-open | dccp-partopen | dccp-request | dccp-respond | dccp-timewait | icmpv6-reply | icmpv6-request | rawip-open | rawip-ready | sctp-closed | sctp-cookie-echoed | sctp-cookie-wait | sctp-established | sctp-shutdown-ack-sent | sctp-shutdown-recd | sctp-shutdown-sent | tcp-close | tcp-close-wait | tcp-est | tcp-fin-wait | tcp-last-ack | tcp-syn-recv | tcp-syn-sent | tcp-syn-sent2 | tcp-time-wait | udp-open | udp-ready | udplite-open | udplite-ready } | vpn-instance vpn-instance-name } * ] [ verbose ] In IRF mode: display session table ipv6 [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] [ [ responder ] { application application-name | destination-ip start-destination-ip [ end-destination-ip ] | destination-port destination-port | destination-zone destination-zone-name | interface interface-type interface-number | protocol { dccp | icmpv6 | raw-ip | sctp | tcp | udp | udp-lite } | security-policy-rule rule-name | source-ip start-source-ip [ end-source-ip ] | source-port source-port | source-zone source-zone-name | state { dccp-closereq | dccp-closing | dccp-open | dccp-partopen | dccp-request | dccp-respond | dccp-timewait | icmpv6-reply | icmpv6-request | rawip-open | rawip-ready | sctp-closed | sctp-cookie-echoed | sctp-cookie-wait | sctp-established | sctp-shutdown-ack-sent | sctp-shutdown-recd | sctp-shutdown-sent | tcp-close | tcp-close-wait | tcp-est | tcp-fin-wait | tcp-last-ack | tcp-syn-recv | tcp-syn-sent | tcp-syn-sent2 | tcp-time-wait | udp-open | udp-ready | udplite-open | udplite-ready } | vpn-instance vpn-instance-name } * ] [ verbose ] |
|
Display IPv4 multicast session table entries. |
In standalone mode: display session table multicast ipv4 [ slot slot-number [ cpu cpu-number ] ] [ [ responder ] { destination-ip start-destination-ip [ end-destination-ip ] | destination-port destination-port | protocol { dccp | icmp | raw-ip | sctp | tcp | udp | udp-lite } | source-ip start-source-ip [ end-source-ip ] | source-port source-port } * ] [ verbose ] In IRF mode: display session table multicast ipv4 [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] [ [ responder ] { destination-ip start-destination-ip [ end-destination-ip ] | destination-port destination-port | protocol { dccp | icmp | raw-ip | sctp | tcp | udp | udp-lite } | source-ip start-source-ip [ end-source-ip ] | source-port source-port } * ] [ verbose ] |
|
Display IPv6 multicast session table entries. |
In standalone mode: display session table multicast ipv6 [ slot slot-number [ cpu cpu-number ] ] [ [ responder ] { destination-ip start-destination-ip [ end-destination-ip ] | destination-port destination-port | protocol { dccp | icmpv6 | raw-ip | sctp | tcp | udp | udp-lite } | source-ip start-source-ip [ end-source-ip ] | source-port source-port } * ] [ verbose ] In IRF mode: display session table multicast ipv6 [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] [ [ responder ] { destination-ip start-destination-ip [ end-destination-ip ] | destination-port destination-port | protocol { dccp | icmpv6 | raw-ip | sctp | tcp | udp | udp-lite } | source-ip start-source-ip [ end-source-ip ] | source-port source-port } * ] [ verbose ] |
|
Display top session statistics. |
display session top-statistics { last-1-hour | last-24-hours | last-30-days } |
|
Display statistics about transparently transmitted packets in session dual-active mode. |
In standalone mode: display session dual-active transparent statistics [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display session dual-active transparent statistics [chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Clear relation table entries. |
In standalone mode: reset session relation-table [ ipv4 | ipv6 ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: reset session relation-table [ ipv4 | ipv6 ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Clear unicast session statistics. |
In standalone mode: reset session statistics [ slot slot-number [ cpu cpu-number ] ] In IRF mode: reset session statistics [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Clear multicast session table entries. |
In standalone mode: reset session statistics multicast [ slot slot-number [ cpu cpu-number ] ] In IRF mode: reset session statistics multicast [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Clear IP unicast session table entries. |
In standalone mode: reset session table [ slot slot-number [ cpu cpu-number ] ] In IRF mode: reset session table [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Clear IPv4 unicast session table entries. |
In standalone mode: reset session table ipv4 [ slot slot-number [ cpu cpu-number ] ] [ source-ip source-ip ] [ destination-ip destination-ip ] [ protocol { dccp | icmp | raw-ip | sctp | tcp | udp | udp-lite } ] [ source-port source-port ] [ destination-port destination-port ] [ vpn-instance vpn-instance-name ] In IRF mode: reset session table ipv4 [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] [ source-ip source-ip ] [ destination-ip destination-ip ] [ protocol { dccp | icmp | raw-ip | sctp | tcp | udp | udp-lite } ] [ source-port source-port ] [ destination-port destination-port ] [ vpn-instance vpn-instance-name ] |
|
Clear IPv6 unicast session table entries. |
In standalone mode: reset session table ipv6 [ slot slot-number [ cpu cpu-number ] ] [ source-ip source-ip ] [ destination-ip destination-ip ] [ protocol { dccp | icmpv6 | raw-ip | sctp | tcp | udp | udp-lite } ] [ source-port source-port ] [ destination-port destination-port ] [ vpn-instance vpn-instance-name ] In IRF mode: reset session table ipv6 [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] [ source-ip source-ip ] [ destination-ip destination-ip ] [ protocol { dccp | icmpv6 | raw-ip | sctp | tcp | udp | udp-lite } ] [ source-port source-port ] [ destination-port destination-port ] [ vpn-instance vpn-instance-name ] |
|
Clear IP multicast session table entries. |
In standalone mode: reset session table multicast [ slot slot-number [ cpu cpu-number ] ] In IRF mode: reset session table multicast [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Clear IPv4 multicast session table entries. |
In standalone mode: reset session table multicast ipv4 [ slot slot-number [ cpu cpu-number ] ] [ source-ip source-ip ] [ destination-ip destination-ip ] [ protocol { dccp | icmp | raw-ip | sctp | tcp | udp | udp-lite } ] [ source-port source-port ] [ destination-port destination-port ] [ vpn-instance vpn-instance-name ] In IRF mode: reset session table multicast ipv4 [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] [ source-ip source-ip ] [ destination-ip destination-ip ] [ protocol { dccp | icmp | raw-ip | sctp | tcp | udp | udp-lite } ] [ source-port source-port ] [ destination-port destination-port ] [ vpn-instance vpn-instance-name ] |
|
Clear IPv6 multicast session table entries. |
In standalone mode: reset session table multicast ipv6 [ slot slot-number [ cpu cpu-number ] ] [ source-ip source-ip ] [ destination-ip destination-ip ] [ protocol { dccp | icmpv6 | raw-ip | sctp | tcp | udp | udp-lite } ] [ source-port source-port ] [ destination-port destination-port ] [ vpn-instance vpn-instance-name ] In IRF mode: reset session table multicast ipv6 [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] [ source-ip source-ip ] [ destination-ip destination-ip ] [ protocol { dccp | icmpv6 | raw-ip | sctp | tcp | udp | udp-lite } ] [ source-port source-port ] [ destination-port destination-port ] [ vpn-instance vpn-instance-name ] |