- Table of Contents
-
- 03-Policies
- 01-Security policy
- 02-Attack defense
- 03-Connection limit
- 04-uRPF
- 05-NAT
- 06-AFT
- 07-Application audit
- 08-Bandwidth management
- 09-Load balancing common configuration
- 10-Server load balancing
- 11-Outbound link load balancing
- 12-Inbound link load balancing
- 13-Transparent DNS proxy
- 14-Application proxy
- 15-NetShare control
- 16-Security policy hit analysis
- 17-Security policy redundancy analysis
- 18-Global load balancing
- 19-IP reputation
- 20-NAT66
- 21-Server connection detection
- 22-Security policy optimization
- 23-Server load balancing
- 24-Load balancing common configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 19-IP reputation | 129.28 KB |
This help contains the following topics:
¡ Enable top hit statistics collection
¡ Configure actions for an attack category
¡ Configure the exception IP list
Introduction
|
The use of IP reputation requires a license. When the license expires, the existing IP reputation list is available but it cannot be upgraded. For more information, see the license help. |
IP reputation uses the IP address information on the IP reputation list to filter network traffic.
IP reputation list
Attack category and action
The device takes an action (drop or permit) when the source IP address or destination IP address of a packet has a hit on the IP reputation list. Logging for the packet is also supported.
On the IP reputation list, an IP address might belong to multiple attack categories. Each attack category has an associated action.
If an IP address belongs to only one attack category, the action that the device takes on matching packets is consistent with the action of the attack category. If an IP address belongs to multiple attack categories, the device takes an action that has highest priority among all actions of the attack categories. The drop action has higher priority than the permit action.
If logging is enabled for any one of attack categories to which the IP address belongs, the device generates a log for the matching packets.
Exception IP list
A packet is forwarded if its source IP address or destination IP address has a match on the exception IP list. The device does not perform IP reputation check on subsequent IP packets with this source or destination IP address.
Blacklist operation
The device supports adding IP addresses on the IP reputation list to or removing them from the blacklist. An IP address on the IP reputation list can be added to the source address blacklist or destination address blacklist, depending on direction attribute of the IP address.
All IP addresses on the IP reputation list are public addresses. The VRF is public network for blacklist entries that are added based on IP reputation.
The default aging time for blacklist entries is 7 days. To modify the aging time, access the Policies > Attack Defense > Blacklist page.
For more information about the blacklist, see the attack defense help.
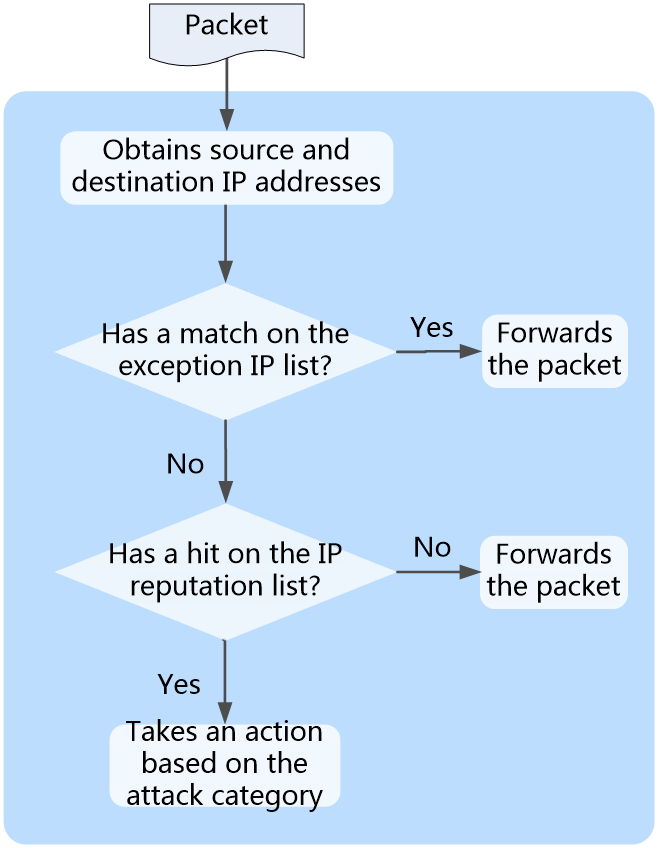
IP reputation workflow
Figure 1 describes the IP reputation workflow.
Figure 1 IP reputation workflow
IP reputation processes a packet as follows:
1. The device determines whether the source IP address or destination IP address has a match on the exception IP list. If a match is found, the packet is passed through. If no match exists, the device proceeds to the next step.
2. The device determines whether the source IP address or destination IP address has a match on the IP reputation list. IP addresses on the IP reputation list has the direction attribute, including source, destination, and bidirection. The match succeeds only when the IP address in the packet has the same direction attribute as the IP address on the list. If the direction attribute of an IP address is bidirection, the match succeeds if the source or destination IP address is the same as the IP address on the IP reputation list. If a match is found, the device takes an action based on the attack category of the IP address. If no match exists, the device forwards the packet. The device supports the following actions:
¡ Permit—Allows packets to pass through.
¡ Drop—Drops packets.
¡ Logging—Generates IP reputation logs.
Restrictions and guidelines
· Top hit statistics are cleared after you disable top hit statistics.
· The source IP blacklist entries added by IP reputation does not carry DS-Lite peer address information. To modify DS-Lite peer address information, access the Policies > Attack Defense > Blacklist page.
· If the IP reputation list update fails for 7 days consecutively, the device clears the IP reputation list and the IP reputation becomes unusable.
· Make sure the system time is the same as the network time.
Configure IP reputation
Enable IP reputation
1. Click the Policies tab.
2. In the navigation pane, select Threat Intelligence > IP Reputation.
3. Select Enable for IP reputation.
4. To query an IP address, click IP address search, enter the IP address, and click Search. Information about the IP address is displayed. You can add the IP address to or remove it from the blacklist or exception IP list.
Enable top hit statistics collection
1. Click the Policies tab.
2. In the navigation pane, select Threat Intelligence > IP Reputation.
3. Select Enable for IP reputation.
4. Select Enable for IP address hit statistics.
5. To open the Top Hit Statistics page, click Top hit statistics. To view top hit statistics ranking information, configure statistics conditions. You can also add an IP address to or remove it from the blacklist or exception IP list.
Configure actions for an attack category
1. Click the Policies tab.
2. In the navigation pane, select Threat Intelligence > IP Reputation.
3. Select Enable for IP reputation.
4. In the Action configuration area, specify a Permit or Drop action for an attack category and select whether to enable logging for packet matching events.
5. To restore the default configuration, click Restore default.
6. Click Apply.
Configure the exception IP list
1. Click the Policies tab.
2. In the navigation pane, select Threat Intelligence > IP Reputation.
3. Select Enable for IP reputation.
4. In the Exception IP list area, enter IP addresses. Each IP address occupies a line.
5. Click Apply.