- Table of Contents
-
- 02-Layer 2 Configuration Guide
- 00-Preface
- 01-Ethernet Interface Configuration
- 02-Loopback and Null Interface Configuration
- 03-MAC Address Table Configuration
- 04-Ethernet Link Aggregation Configuration
- 05-Port Isolation Configuration
- 06-Spanning Tree Configuration
- 07-VLAN Configuration
- 08-GVRP Configuration
- 09-LLDP Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 07-VLAN Configuration | 395.91 KB |
Contents
Configuring basic VLAN settings
Configuring basic settings of a VLAN interface
Introduction to port-based VLAN
Assigning an access port to a VLAN
Assigning a trunk port to a VLAN
Assigning a hybrid port to a VLAN
Port-based VLAN configuration example
Introduction to MAC-based VLAN
MAC-based VLAN configuration example
Protocol-based VLAN configuration
Introduction to protocol-based VLAN
Configuring a protocol-based VLAN
Protocol-based VLAN configuration example
Displaying and maintaining VLAN
Security mode and normal mode of voice VLANs
Configuring QoS priority settings for voice traffic on an interface
Configuring a port to operate in automatic voice VLAN assignment mode
Configuring a port to operate in manual voice VLAN assignment mode
Displaying and maintaining voice VLAN
Voice VLAN configuration examples
Automatic voice VLAN mode configuration example
Manual voice VLAN assignment mode configuration example
This chapter includes these sections:
· Configuring basic VLAN settings
· Configuring basic settings of a VLAN interface
· Port-based VLAN configuration
· MAC-based VLAN configuration
· Protocol-based VLAN configuration
· Displaying and maintaining VLAN
|
|
NOTE: · The term "switch" or "device" in this chapter refers to the switching engine on a WX3000E wireless switch. · The WX3000E series comprises WX3024E and WX3010E wireless switches. · The port numbers in this chapter are for illustration only. |
Introduction to VLAN
VLAN overview
Ethernet is a network technology based on the Carrier Sense Multiple Access/Collision Detect (CSMA/CD) mechanism. As the medium is shared, collisions and excessive broadcasts are common on Ethernet networks. To address the issue, virtual LAN (VLAN) was introduced to break a LAN down into separate VLANs. VLANs are isolated from each other at Layer 2. A VLAN is a bridging domain, and all broadcast traffic is contained within it, as shown in Figure 1.
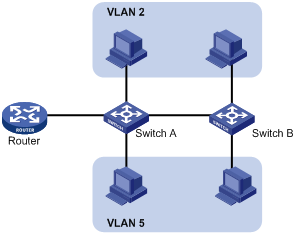
A VLAN is logically divided on an organizational basis rather than on a physical basis. For example, all workstations and servers used by a particular workgroup can be assigned to the same VLAN, regardless of their physical locations.
VLAN technology delivers the following benefits:
1. Confining broadcast traffic within individual VLANs. This reduces bandwidth waste and improves network performance.
2. Improving LAN security. By assigning user groups to different VLANs, you can isolate them at Layer 2. To enable communication between VLANs, routers or Layer 3 switches are required.
3. Flexible virtual workgroup creation. As users from the same workgroup can be assigned to the same VLAN regardless of their physical locations, network construction and maintenance is much easier and more flexible.
VLAN fundamentals
To enable a network device to identify frames of different VLANs, a VLAN tag field is inserted into the data link layer encapsulation.
The format of VLAN-tagged frames is defined in IEEE 802.1Q issued by the Institute of Electrical and Electronics Engineers (IEEE) in 1999.
In the header of a traditional Ethernet data frame, the field after the destination MAC address and the source MAC address is the Type field indicating the upper layer protocol type, as shown in Figure 2.
Figure 2 Traditional Ethernet frame format
![]()
IEEE 802.1Q inserts a four-byte VLAN tag after the DA&SA field, as shown in Figure 3.
Figure 3 Position and format of VLAN tag
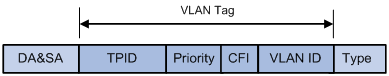
A VLAN tag comprises the following fields: tag protocol identifier (TPID), priority, canonical format indicator (CFI), and VLAN ID.
· The 16-bit TPID field with a value of 0x8100 indicates that the frame is VLAN-tagged.
· The 3-bit priority field indicates the 802.1p priority of the frame.
· The 1-bit CFI field specifies whether the MAC addresses are encapsulated in the standard format when packets are transmitted across different media. A value of 0 indicates that MAC addresses are encapsulated in the standard format; a value of 1 indicates that MAC addresses are encapsulated in a non-standard format. The value of the field is 0 by default.
· The 12-bit VLAN ID field identifies the VLAN the frame belongs to. The VLAN ID range is 0 to 4095. As 0 and 4095 are reserved, a VLAN ID actually ranges from 1 to 4094.
A network device handles an incoming frame depending on whether the frame is VLAN tagged and the value of the VLAN tag, if any. For more information, see “Introduction to port-based VLAN.”
|
|
NOTE: · The Ethernet II encapsulation format is used here. Besides the Ethernet II encapsulation format, Ethernet also supports other encapsulation formats, including 802.2 LLC, 802.2 SNAP, and 802.3 raw. The VLAN tag fields are added to frames encapsulated in these formats for VLAN identification. · For a frame with multiple VLAN tags, the device handles it according to its outer-most VLAN tag and transmits its inner VLAN tags as payload. |
VLAN types
You can implement VLANs based on the following criteria:
· Port
· MAC address
· Protocol
· IP subnet
· Policy
· Other criteria
|
|
NOTE: · The switching engine on a WX3000E wireless switch supports only port-based VLAN, MAC-based VLAN, and protocol-based VLAN. · You can configure these types of VLANs on a port at the same time. When determining to which VLAN a packet passing through the port should be assigned, the device looks up the VLANs in the default order of MAC-based VLAN, protocol-based VLAN, and port-based VLAN. |
Configuring basic VLAN settings
Follow these steps to configure basic VLAN settings:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Create VLANs |
vlan { vlan-id1 [ to vlan-id2 ] | all } |
Optional Use this command to create VLANs in bulk. |
|
Enter VLAN view |
vlan vlan-id |
Required By default, only the default VLAN (VLAN 1) exists in the system. If the specified VLAN does not exist, this command creates the VLAN first. |
|
Configure a name for the VLAN |
name text |
Optional By default, the name of a VLAN is its VLAN ID. For example, VLAN 0001. |
|
Configure the description of the VLAN |
description text |
Optional By default, the description of a VLAN is its VLAN ID. For example, VLAN 0001. |
|
|
NOTE: · As the default VLAN, VLAN 1 cannot be created or removed. · You cannot manually create or delete VLANs reserved for special purposes. · You cannot use the undo vlan command to delete the dynamic VLANs. · You cannot delete a VLAN with a QoS policy configured. · You cannot delete a VLAN configured as a source VLAN for port mirroring. To delete it, remove the source VLAN configuration first. |
Configuring basic settings of a VLAN interface
VLAN interface overview
For hosts of different VLANs to communicate, you must use a router or Layer 3 switch to perform Layer 3 forwarding. To achieve this, VLAN interfaces are used.
VLAN interfaces are virtual interfaces used for Layer 3 communication between different VLANs. They do not exist as physical entities on devices. For each VLAN, you can create one VLAN interface. You can assign the VLAN interface an IP address and specify it as the gateway of the VLAN to forward traffic destined for an IP subnet different from that of the VLAN.
Configuration procedure
Follow these steps to configure basic settings of a VLAN interface:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Create a VLAN interface and enter VLAN interface view |
interface vlan-interface vlan-interface-id |
Required If the VLAN interface already exists, you enter its view directly. |
|
Assign an IP address to the VLAN interface |
ip address ip-address { mask | mask-length } |
Optional By default, no IP address is assigned to any VLAN interface. |
|
Shut down the VLAN interface |
shutdown |
Optional By default, a VLAN interface is in the up state. The VLAN interface is up if one or more ports in the VLAN is up, and goes down if all ports in the VLAN go down. A VLAN interface shut down with the shutdown command, however, will be in the DOWN (Administratively) state until you bring it up, regardless of how the state of the ports in the VLAN changes. |
|
|
NOTE: Before creating a VLAN interface for a VLAN, create the VLAN first. |
Port-based VLAN configuration
Introduction to port-based VLAN
Port-based VLANs group VLAN members by port. A port forwards traffic for a VLAN only after it is assigned to the VLAN.
Port link type
You can configure the link type of a port as access, trunk, or hybrid. The link types use the following VLAN tag handling methods:
· An access port belongs to only one VLAN and sends traffic untagged. It is usually used to connect a terminal device unable to recognize VLAN tagged-packets or when there is no need to separate different VLAN members.
· A trunk port can carry multiple VLANs to receive and send traffic for them. Except traffic from the port VLAN ID (PVID), traffic sent through a trunk port will be VLAN tagged. Usually, ports connecting network devices are configured as trunk ports.
· Like a trunk port, a hybrid port can carry multiple VLANs to receive and send traffic for them. Unlike a trunk port, a hybrid port allows traffic of all VLANs to pass through VLAN untagged.
PVID
By default, VLAN 1 is the PVID for all ports. You can configure the PVID for a port as required.
Use the following guidelines when configuring the PVID on a port:
· An access port can join only one VLAN. The VLAN to which the access port belongs is the PVID of the port.
· A trunk or hybrid port can join multiple VLANs, and you can configure a PVID for the port.
· You can use a nonexistent VLAN as the PVID for a hybrid or trunk port but not for an access port. After you remove the VLAN that an access port resides in with the undo vlan command, the PVID of the port changes to VLAN 1. The removal of the VLAN specified as the PVID of a trunk or hybrid port, however, does not affect the PVID setting on the port.
|
|
NOTE: · Do not set the voice VLAN as the PVID of a port in automatic voice VLAN assignment mode. For information about voice VLAN, see the chapter “Voice VLAN configuration.” · H3C recommends that you set the same PVID ID for local and remote ports. · Make sure that a port is assigned to its PVID. Otherwise, when the port receives frames tagged with the PVID or untagged frames (including protocol packets such as MSTP BPDUs), the port filters out these frames. |
The following table shows how ports of different link types handle frames:
|
Port type |
Actions (in the inbound direction) |
Actions (in the outbound direction) |
|
|
Untagged frame |
Tagged frame |
||
|
Access |
Tags the frame with the PVID tag. |
· Receives the frame if its VLAN ID is the same as the PVID. · Drops the frame if its VLAN ID is different from the PVID. |
Removes the VLAN tag and sends the frame. |
|
Trunk |
Checks whether the PVID is permitted on the port: · If yes, tags the frame with the PVID tag. · If not, drops the frame. |
· Receives the frame if its VLAN is carried on the port. · Drops the frame if its VLAN is not carried on the port. |
· Removes the tag and send the frame if the frame carries the PVID tag and the port belongs to the PVID. · Sends the frame without removing the tag if its VLAN is carried on the port but is different from the PVID. |
|
Hybrid |
Sends the frame if its VLAN is carried on the port. The frame is sent with the VLAN tag removed or intact depending on your configuration with the port hybrid vlan command. This is true of the PVID. |
||
Assigning an access port to a VLAN
You can assign an access port to a VLAN in VLAN view, interface view (including Ethernet interface view, Layer 2 aggregate interface view, and port group view.
Follow these steps to assign one or multiple access ports to a VLAN in VLAN view:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter VLAN view |
vlan vlan-id |
Required If the specified VLAN does not exist, this command creates the VLAN first. |
|
Assign one or a group of access ports to the VLAN |
port interface-list |
Required By default, all ports belong to VLAN 1. |
Follow these steps to assign an access port (in interface view) or multiple access ports (in port group view) to a VLAN:
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enter interface view or port group view |
Enter Ethernet interface view |
interface interface-type interface-number |
Required Use any command. · The configuration made in Ethernet interface view applies only to the port. · The configuration made in port group view applies to all ports in the port group. · The configuration made in Layer 2 aggregate interface view applies to the aggregate interface and its aggregation member ports. If the system fails to apply the configuration to the aggregate interface, it stops applying the configuration to aggregation member ports. If the system fails to apply the configuration to an aggregation member port, it skips the port and moves to the next member port. |
|
Enter Layer 2 aggregate interface view |
interface bridge-aggregation interface-number |
||
|
Enter port group view |
port-group manual port-group-name |
||
|
Configure the link type of the ports as access |
port link-type access |
Optional By default, all ports are access ports. |
|
|
Assign the access ports to a VLAN |
port access vlan vlan-id |
Optional By default, all access ports belong to VLAN 1. |
|
|
|
NOTE: · Before assigning an access port to a VLAN, create the VLAN first. · In VLAN view, only Layer 2 Ethernet interfaces can be assigned to the VLAN. |
Assigning a trunk port to a VLAN
A trunk port can carry multiple VLANs. You can assign it to a VLAN in interface view (including Ethernet interface view, Layer 2 aggregate interface view, and port group view.
Follow these steps to assign a trunk port to one or multiple VLANs:
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enter interface view or port group view |
Enter Ethernet interface view |
interface interface-type interface-number |
Required Use any command. · The configuration made in Ethernet interface view applies only to the port. · The configuration made in port group view applies to all ports in the port group. · The configuration made in Layer 2 aggregate interface view applies to the aggregate interface and its aggregation member ports. If the system fails to apply the configuration to the aggregate interface, it stops applying the configuration to aggregation member ports. If the system fails to apply the configuration to an aggregation member port, it skips the port and moves to the next member port. |
|
Enter Layer 2 aggregate interface view |
interface bridge-aggregation interface-number |
||
|
Enter port group view |
port-group manual port-group-name |
||
|
Configure the link type of the ports as trunk |
port link-type trunk |
Required By default, all ports are access ports. |
|
|
Assign the trunk ports to the specified VLANs |
port trunk permit vlan { vlan-id-list | all } |
Required By default, a trunk port carries only VLAN 1. |
|
|
Configure the PVID of the trunk ports |
port trunk pvid vlan vlan-id |
Optional By default, the PVID is VLAN 1. |
|
|
|
NOTE: · To change the link type of a port from trunk to hybrid or vice versa, you must set the link type to access first. · After configuring the PVID for a trunk port, you must use the port trunk permit vlan command to configure the trunk port to allow packets from the PVID to pass through, so that the egress port can forward packets from the PVID. · When you use the port link-type { access | hybrid | trunk } command to change the link type of a port, the loopback-detection action configuration is restored to the default. For more information about the loopback-detection action command, see the Layer 2 Command Reference. |
Assigning a hybrid port to a VLAN
A hybrid port can carry multiple VLANs. You can assign it to a VLAN in interface view (including Ethernet interface view, Layer 2 aggregate interface view, and port group view.
Follow these steps to assign a hybrid port to one or multiple VLANs:
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enter interface view or port group view |
Enter Ethernet interface view |
interface interface-type interface-number |
Required Use any command. · The configuration made in Ethernet interface view applies only to the port. · The configuration made in port group view applies to all ports in the port group. · The configuration made in Layer 2 aggregate interface view applies to the aggregate interface and its aggregation member ports. If the system fails to apply the configuration to the aggregate interface, it stops applying the configuration to aggregation member ports. If the system fails to apply the configuration to an aggregation member port, it skips the port and moves to the next member port. |
|
Enter Layer 2 aggregate interface view |
interface bridge-aggregation interface-number |
||
|
Enter port group view |
port-group manual port-group-name |
||
|
Configure the link type of the ports as hybrid |
port link-type hybrid |
Required By default, all ports are access ports. |
|
|
Assign the hybrid ports to the specified VLANs |
port hybrid vlan vlan-id-list { tagged | untagged } |
Required By default, a hybrid port allows only packets of VLAN 1 to pass through untagged. |
|
|
Configure the PVID of the hybrid ports |
port hybrid pvid vlan vlan-id |
Optional By default, the PVID is VLAN 1. |
|
Port-based VLAN configuration example
Network requirements
As shown in Figure 4:
· Host A and Host C belong to Department A, and access the enterprise network through different devices. Host B and Host D belong to Department B. They also access the enterprise network through different devices.
· To ensure communication security and avoid broadcast storms, VLANs are configured in the enterprise network to isolate Layer 2 traffic of different departments. VLAN 100 is assigned to Department A, and VLAN 200 is assigned to Department B.
· Make sure that hosts within the same VLAN can communicate with each other. Host A can communicate with Host C, and Host B can communicate with Host D.
Figure 4 Network diagram for port-based VLAN configuration
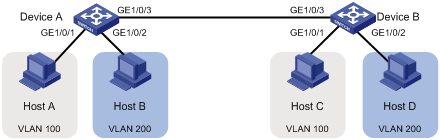
Configuration procedure
1. Configuration on Device A
# Create VLAN 100, and assign port GigabitEthernet 1/0/1 to VLAN 100.
<DeviceA> system-view
[DeviceA] vlan 100
[DeviceA-vlan100] port gigabitethernet 1/0/1
[DeviceA-vlan100] quit
# Create VLAN 200, and assign port GigabitEthernet 1/0/2 to VLAN 200.
[DeviceA] vlan 200
[DeviceA-vlan200] port gigabitethernet 1/0/2
[DeviceA-vlan200] quit
# Configure port GigabitEthernet 1/0/3 as a trunk port, and assign it to VLANs 100 and 200, enabling GigabitEthernet 1/0/3 to forward traffic of VLANs 100 and 200 to Device B.
[DeviceA] interface gigabitethernet 1/0/3
[DeviceA-GigabitEthernet1/0/3] port link-type trunk
[DeviceA-GigabitEthernet1/0/3] port trunk permit vlan 100 200
Please wait... Done.
2. Configure Device B as you configure Device A.
3. Configure Host A and Host C to be on the same IP subnet. For example, 192.168.100.0/24. Configure Host B and Host D to be on the same IP subnet. For example, 192.168.200.0/24.
Verification
1. Host A and Host C and ping each other successfully, but they both fail to ping Host B. Host B and Host D and ping each other successfully, but they both fail to ping Host A.
2. Check whether the configuration is successful by displaying relevant VLAN information.
# Display information about VLANs 100 and 200 on Device A.
[DeviceA-GigabitEthernet1/0/3] display vlan 100
VLAN ID: 100
VLAN Type: static
Route Interface: not configured
Description: VLAN 0100
Name: VLAN 0100
Tagged Ports:
GigabitEthernet1/0/3
Untagged Ports:
GigabitEthernet1/0/1
[DeviceA-GigabitEthernet1/0/3] display vlan 200
VLAN ID: 200
VLAN Type: static
Route Interface: not configured
Description: VLAN 0200
Name: VLAN 0200
Tagged Ports:
GigabitEthernet1/0/3
Untagged Ports:
GigabitEthernet1/0/2
MAC-based VLAN configuration
Introduction to MAC-based VLAN
The MAC-based VLAN feature assigns hosts to a VLAN based on their MAC addresses. This feature is usually used in conjunction with security technologies such as 802.1X to provide secure, flexible network access for terminal devices.
Static MAC-based VLAN assignment
Static MAC-based VLAN assignment applies to networks containing a small number of VLAN users. In such a network, you can create a MAC address-to-VLAN map containing multiple MAC address-to-VLAN entries on a port, enable the MAC-based VLAN feature on the port, and assign the port to MAC-based VLANs.
With static MAC-based VLAN assignment configured on a port, the device processes received frames by using the following guidelines:
· When the port receives an untagged frame, the device looks up the MAC address-to-VLAN map based on the source MAC address of the frame for a match.
¡ The device first performs a fuzzy match. In the fuzzy match, the device searches the MAC address-to-VLAN entries whose masks are not all-Fs and performs a logical AND operation on the source MAC address and each mask. If the result of an AND operation matches the corresponding MAC address, the device tags the frame with the corresponding VLAN ID.
¡ If the fuzzy match fails, the device performs an exact match. In the exact match, the device searches the MAC address-to-VLAN entries whose masks are all-Fs. If the MAC address of a MAC address-to-VLAN entry matches the source MAC address of the untagged frame, the device tags the frame with the corresponding VLAN ID.
¡ If no match is found, the device assigns a VLAN to the frame by using other criteria, such as IP subnet or protocol, and forwards the frame.
¡ If no VLAN is available, the device tags the frame with the PVID of the receiving port and forwards the frame.
· When the port receives a tagged frame, the port forwards the frame if the VLAN ID of the frame is permitted by the port, or otherwise drops the frame.
Dynamic MAC-based VLAN assignment
When you cannot determine the target MAC-based VLANs of a port, you can use dynamic MAC-based VLAN assignment on the port. To do that, you can create a MAC address-to-VLAN map containing multiple MAC address-to-VLAN entries, and enable the MAC-based VLAN feature and dynamic MAC-based VLAN assignment on the port.
Dynamic MAC-based VLAN assignment uses the following workflows:
· As shown in Figure 5, when the port receives an untagged frame, the port processes the frame by using the following guidelines:
¡ If the frame matches a MAC address-to-VLAN entry configured on the port, the port dynamically joins the corresponding MAC-based VLAN and forwards the frame.
¡ If the frame does not match any MAC address-to-VLAN entry, the port assigns a VLAN to the frame by using other criteria, such as IP subnet or protocol, and forwards the frame.
¡ If no VLAN is available, the port tags the frame with the PVID and forwards the frame if the PVID is permitted by the port, or otherwise drops the frame.
Figure 5 Flowchart for processing an untagged frame in dynamic MAC-based VLAN assignment
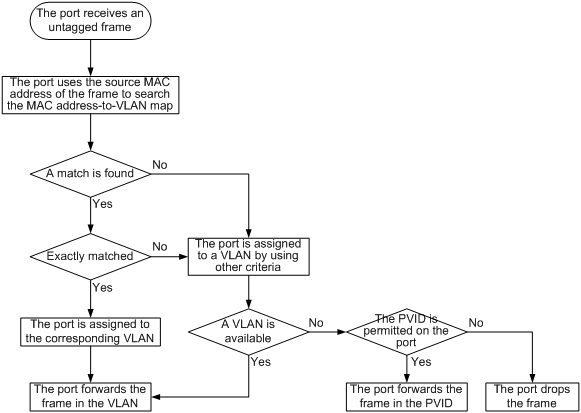
· When the port receives a tagged frame, the port forwards the frame if the VLAN ID of the frame is permitted by the port, or otherwise drops the frame.
|
|
NOTE: · When a port is assigned to the corresponding VLAN in a MAC address-to-VLAN entry, but has not been assigned to the VLAN by using the port hybrid vlan command, the port sends packets from the VLAN with VLAN tags removed. · If you configure both static and dynamic MAC-based VLAN assignment on the same port, dynamic MAC-based VLAN assignment applies. |
Dynamic MAC-based VLAN
You can use dynamic MAC-based VLAN with access authentication (such as 802.1X authentication based on MAC addresses) to implement secure, flexible terminal access. After configuring dynamic MAC-based VLAN on the device, you must configure the username-to-VLAN entries on the access authentication server.
When a user passes authentication of the access authentication server, the device obtains VLAN information from the server, generates a MAC address-to-VLAN entry by using the source MAC address of the user packet and the VLAN information, and assigns the port to the MAC-based VLAN. When the user goes offline, the device automatically deletes the MAC address-to-VLAN entry, and removes the port from the MAC-based VLAN.
|
|
NOTE: For more information about 802.1X, MAC, and portal authentication, see the Security Configuration Guide. |
Configuring a MAC-based VLAN
|
|
NOTE: · MAC-based VLANs are available only on hybrid ports. · With dynamic MAC-based VLAN assignment enabled, packets are delivered to the CPU for processing. The packet processing mode has the highest priority and overrides the configuration of MAC learning limit and disabling of MAC address learning. When dynamic MAC-based VLAN assignment is enabled, do not configure the MAC learning limit or disable MAC address learning. · Do not use dynamic MAC-based VLAN assignment together with 802.X and MAC authentication. · In dynamic MAC-based VLAN assignment, the port that receives a packet with an unknown source MAC address can be successfully assigned to the matched VLAN only when the matched VLAN is a static VLAN. · The MAC-based VLAN feature is mainly configured on the downlink ports of the user access devices. Do not enable this function together with link aggregation. · With MSTP enabled, if a port is blocked in the MST instance (MSTI) of the target MAC-based VLAN, the port drops the received packets, instead of delivering them to the CPU. As a result, the receiving port will not be dynamically assigned to the corresponding VLAN. Do not configure dynamic MAC-based VLAN assignment together with MSTP, because the former is mainly configured on the access side. |
Follow these steps to configure static MAC-based VLAN assignment:
|
To do... |
Use the command... |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Associate a specific MAC address with a VLAN |
mac-vlan mac-address mac-address [ mask mac-mask ] vlan vlan-id [ priority priority ] |
Required |
|
|
Enter interface view or port group view |
Enter Ethernet interface view |
interface interface-type interface-number |
Required Use either command. · The configuration made in Ethernet interface view applies only to the port. · The configuration made in port group view applies to all ports in the port group. |
|
Enter port group view |
port-group manual port-group-name |
||
|
Configure the link type of the ports as hybrid |
port link-type hybrid |
Required By default, all ports are access ports. |
|
|
Configure the hybrid ports to permit packets from specific MAC-based VLANs to pass through |
port hybrid vlan vlan-id-list { tagged | untagged } |
Required By default, a hybrid port only permits the packets from VLAN 1 to pass through. |
|
|
Enable the MAC-based VLAN feature |
mac-vlan enable |
Required Disabled by default. |
|
Follow these steps to configure dynamic MAC-based VLAN assignment:
|
To do... |
Use the command... |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Associate MAC addresses with a VLAN |
mac-vlan mac-address mac-address vlan vlan-id [ priority priority ] |
Required |
|
|
Enter interface view or port group view |
Enter Ethernet interface view |
interface interface-type interface-number |
Required Use either command. · The configuration made in Ethernet interface view applies only to the port. · The configuration made in port group view applies to all ports in the port group. |
|
Enter port group view |
port-group manual port-group-name |
||
|
Configure the link type of the port as hybrid |
port link-type hybrid |
Required By default, all ports are access ports. |
|
|
Enable the MAC-based VLAN feature |
mac-vlan enable |
Required Disabled by default. |
|
|
Enable dynamic MAC-based VLAN assignment |
mac-vlan trigger enable |
Required By default, dynamic MAC-based VLAN assignment is disabled. |
|
|
Disable the PVID of the port from forwarding packets with unknown source MAC addresses that do not match any MAC address-to-VLAN entry |
port pvid disable |
Optional By default, when a port receives a packet with an unknown source MAC address that does not match to any MAC address-to-VLAN entry, it forwards the packet in its PVID. |
|
Follow these steps to configure dynamic MAC-based VLAN:
|
To do... |
Use the command... |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enter interface view or port group view |
Enter Ethernet interface view |
interface interface-type interface-number |
Use either command. · The configuration made in Ethernet interface view applies only to the port. · The configuration made in port group view applies to all ports in the port group. |
|
Enter port group view |
port-group manual port-group-name |
||
|
Configure the link type of the ports as hybrid |
port link-type hybrid |
Required By default, all ports are access ports. |
|
|
Enable the MAC-based VLAN feature |
mac-vlan enable |
Required Disabled by default. |
|
MAC-based VLAN configuration example
Network requirements
As shown in Figure 6,
· GigabitEthernet 1/0/1 of Device A and Device C are each connected to a meeting room. Laptop 1 and Laptop 2 are used for meeting and may be used in any of the two meeting rooms.
· Laptop 1 and Laptop 2 are owned by different departments. The two departments use VLAN 100 and VLAN 200 respectively. Each laptop can access only its own department server no matter which meeting room it is used in.
· The MAC address of Laptop 1 is 000D-88F8-4E71, and that of Laptop 2 is 0014-222C-AA69.
Figure 6 Network diagram for MAC-based VLAN configuration
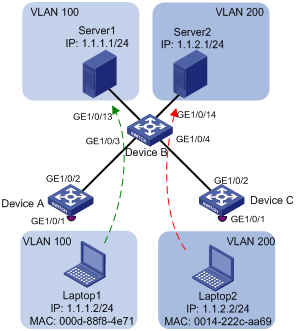
Configuration consideration
· Create VLANs 100 and 200.
· Configure the uplink ports of Device A and Device C as trunk ports, and assign them to VLANs 100 and 200.
· Associate the MAC address of Laptop 1 with VLAN 100, and the MAC address of Laptop 2 with VLAN 200.
Configuration procedure
1. Configuration on Device A
# Create VLANs 100 and 200.
<DeviceA> system-view
[DeviceA] vlan 100
[DeviceA-vlan100] quit
[DeviceA] vlan 200
[DeviceA-vlan200] quit
# Associate the MAC address of Laptop 1 with VLAN 100, and the MAC address of Laptop 2 with VLAN 200.
[DeviceA] mac-vlan mac-address 000d-88f8-4e71 vlan 100
[DeviceA] mac-vlan mac-address 0014-222c-aa69 vlan 200
# Configure Laptop 1 and Laptop 2 to access the network through GigabitEthernet 1/0/1: Configure GigabitEthernet 1/0/1 as a hybrid port that sends packets of VLANs 100 and 200 untagged, and enable the MAC-based VLAN feature on it.
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] port link-type hybrid
[DeviceA-GigabitEthernet1/0/1] port hybrid vlan 100 200 untagged
Please wait... Done.
[DeviceA-GigabitEthernet1/0/1] mac-vlan enable
[DeviceA-GigabitEthernet1/0/1] quit
# To enable the laptops to access Server 1 and Server 2, configure the uplink port GigabitEthernet 1/0/2 as a trunk port, and assign it to VLANs 100 and 200.
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] port link-type trunk
[DeviceA-GigabitEthernet1/0/2] port trunk permit vlan 100 200
[DeviceA-GigabitEthernet1/0/2] quit
2. Configuration on Device B
# Create VLANs 100 and 200. Assign GigabitEthernet 1/0/13 to VLAN 100, and GigabitEthernet 1/0/14 to VLAN 200.
<DeviceB> system-view
[DeviceB] vlan 100
[DeviceB-vlan100] port gigabitethernet 1/0/13
[DeviceB-vlan100] quit
[DeviceB] vlan 200
[DeviceB-vlan200] port gigabitethernet 1/0/14
[DeviceB-vlan200] quit
# Configure GigabitEthernet 1/0/3 and GigabitEthernet 1/0/4 as trunk ports, and assign them to VLANs 100 and 200.
[DeviceB] interface gigabitethernet 1/0/3
[DeviceB-GigabitEthernet1/0/3] port link-type trunk
[DeviceB-GigabitEthernet1/0/3] port trunk permit vlan 100 200
[DeviceB-GigabitEthernet1/0/3] quit
[DeviceB] interface gigabitethernet 1/0/4
[DeviceB-GigabitEthernet1/0/4] port link-type trunk
[DeviceB-GigabitEthernet1/0/4] port trunk permit vlan 100 200
[DeviceB-GigabitEthernet1/0/4] quit
3. Configuration on Device C
Configure Device C as you configure Device A.
Verification
1. Laptop 1 can access Server 1 only, and Laptop 2 can access Server 2 only.
2. On Device A and Device C, you can see that VLAN 100 is associated with the MAC address of Laptop 1, and VLAN 200 is associated with the MAC address of Laptop 2.
[DeviceA] display mac-vlan all
The following MAC VLAN addresses exist:
S:Static D:Dynamic
MAC ADDR MASK VLAN ID PRIO STATE
--------------------------------------------------------
000d-88f8-4e71 ffff-ffff-ffff 100 0 S
0014-222c-aa69 ffff-ffff-ffff 200 0 S
Total MAC VLAN address count:2
Configuration guidelines
1. MAC-based VLAN can be configured only on hybrid ports.
2. MAC-based VLAN is usually configured on the downlink ports of access layer devices, and cannot be configured together with the link aggregation function.
Protocol-based VLAN configuration
Introduction to protocol-based VLAN
You use the protocol-based VLAN feature to assign packets to VLANs by their application type.
The protocol-based VLAN feature assigns inbound packets to different VLANs based on their protocol type and encapsulation format. The protocols available for VLAN assignment include IP, IPX, and AppleTalk (AT), and the encapsulation formats include Ethernet II, 802.3 raw, 802.2 LLC, and 802.2 SNAP.
A protocol template defines a protocol type and an encapsulation format, and is uniquely identified by the combination of a VLAN ID and a protocol index. You can assign multiple protocol templates to a protocol-based VLAN.
Protocol-based VLAN assignment is available only on hybrid ports, and a protocol template applies only to untagged packets.
When an untagged packet arrives, a protocol-based VLAN assignment enabled hybrid port processes the packet by using the following workflow:
· If the protocol type and encapsulation format in the packet matches a protocol template, the packet is tagged with the VLAN tag specific to the protocol template.
· If no protocol template is matched, the packet is tagged with the PVID of the port.
The port processes a tagged packet as it processes tagged packets of a port-based VLAN.
· If the port is in the same VLAN as the packet, it forwards the packet.
· If not, the port drops the packet.
Configuring a protocol-based VLAN
Follow these steps to configure a protocol-based VLAN:
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Enter VLAN view |
vlan vlan-id |
Required If the specified VLAN does not exist, this command creates the VLAN first. |
|
|
Create a protocol template for the VLAN |
protocol-vlan [ protocol-index ] { at | ipv4 | ipv6 | ipx { ethernetii | llc | raw | snap } | mode { ethernetii etype etype-id | llc { dsap dsap-id [ ssap ssap-id ] | ssap ssap-id } | snap etype etype-id } } |
Required |
|
|
Exit VLAN view |
quit |
Required |
|
|
Enter interface view or port group view |
Enter Ethernet interface view |
interface interface-type interface-number |
Required Use any command. · The configuration made in Ethernet interface view applies only to the port. · The configuration made in port group view applies to all ports in the port group. · The configuration made in Layer 2 aggregate interface view applies to the aggregate interface and its aggregation member ports. If the system fails to apply the configuration to the aggregate interface, it stops applying the configuration to aggregation member ports. If the system fails to apply the configuration to an aggregation member port, it skips the port and moves to the next member port. |
|
Enter Layer 2 aggregate interface view |
interface bridge-aggregation interface-number |
||
|
Enter port group view |
port-group manual port-group-name |
||
|
Configure the port link type as hybrid |
port link-type hybrid |
Required By default, all ports are access ports. |
|
|
Assign the hybrid port to the specified protocol-based VLANs |
port hybrid vlan vlan-id-list { tagged | untagged } |
Required By default, a hybrid port is only in VLAN 1. |
|
|
Assign the protocol template you have created to the hybrid port |
port hybrid protocol-vlan vlan vlan-id { protocol-index [ to protocol-end ] | all } |
Required |
|
|
|
CAUTION: · In the protocol-vlan command, do not set the dsap-id argument and the ssap-id argument to 0xe0 (which corresponds to the ipx llc protocol template) or 0xff (which corresponds to the ipx raw protocol template) at the same time. · When you use the mode keyword to configure a protocol-based VLAN, do not set the etype-id argument of ethernetii packets to 0x0800, 0x8137, 0x809b, and 0x86dd, which correspond to ipv4, ipx, appletalk, and ipv6 protocol templates. · A protocol-based VLAN processes only untagged inbound packets, whereas the voice VLAN in automatic mode processes only tagged voice traffic. Do not configure a VLAN as both a protocol-based VLAN and a voice VLAN. For more information, see the chapter “Voice VLAN configuration.” |
Protocol-based VLAN configuration example
Network requirements
In a lab environment, as shown in Figure 7, most hosts run the IPv4 protocol, and the rest of the hosts run the IPv6 protocol for teaching purpose. To avoid interference, isolate IPv4 traffic and IPv6 traffic at Layer 2.
Figure 7 Network diagram for protocol-based VLAN configuration
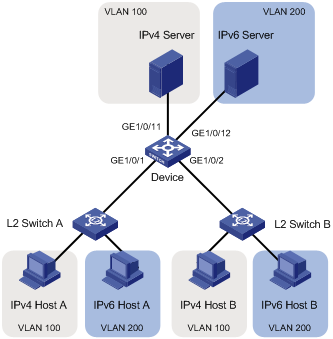
Configuration consideration
Create VLANs 100 and 200. Associate VLAN 100 with IPv4, and VLAN 200 with IPv6. Configure protocol-based VLANs to isolate IPv4 traffic and IPv6 traffic at Layer 2.
Configuration procedure
1. Configuration on Device
# Create VLAN 100, and assign port GigabitEthernet 1/0/11 to VLAN 100.
<Device> system-view
[Device] vlan 100
[Device-vlan100] description protocol VLAN for IPv4
[Device-vlan100] port gigabitethernet 1/0/11
[Device-vlan100] quit
# Create VLAN 200, and assign port GigabitEthernet 1/0/12 to VLAN 200.
[Device] vlan 200
[Device-vlan200] description protocol VLAN for IPv6
[Device-vlan200] port gigabitethernet 1/0/12
# Create an IPv6 protocol template in the view of VLAN 200, and an IPv4 protocol template in the view of VLAN 100.
[Device-vlan200] protocol-vlan 1 ipv6
[Device-vlan200] quit
[Device] vlan 100
[Device-vlan100] protocol-vlan 1 ipv4
[Device-vlan100] quit
# Configure port GigabitEthernet 1/0/1 as a hybrid port that forwards packets of VLANs 100 and 200 untagged.
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] port link-type hybrid
[Device-GigabitEthernet1/0/1] port hybrid vlan 100 200 untagged
Please wait... Done.
# Associate port GigabitEthernet 1/0/1 with the IPv4 protocol template of VLAN 100, and the IPv6 protocol template of VLAN 200.
[Device-GigabitEthernet1/0/1] port hybrid protocol-vlan vlan 100 1
[Device-GigabitEthernet1/0/1] port hybrid protocol-vlan vlan 200 1
[Device-GigabitEthernet1/0/1] quit
# Configure GigabitEthernet 1/0/2 as a hybrid port that forwards packets of VLANs 100 and 200 untagged, and associate GigabitEthernet 1/0/2 with the IPv4 protocol template of VLAN 100, and the IPv6 protocol template of VLAN 200.
[Device] interface gigabitethernet 1/0/2
[Device-GigabitEthernet1/0/2] port link-type hybrid
[Device-GigabitEthernet1/0/2] port hybrid vlan 100 200 untagged
Please wait... Done.
[Device-GigabitEthernet1/0/2] port hybrid protocol-vlan vlan 100 1
[Device-GigabitEthernet1/0/2] port hybrid protocol-vlan vlan 200 1
2. Keep the default settings of L2 Switch A and L2 Switch B.
3. Configure IPv4 Host A, IPv4 Host B, and IPv4 Server to be on the same IP subnet (for example, 192.168.100.0/24), and configure IPv6 Host A, IPv6 Host B, and IPv6 Server to be on the same IP subnet (for example, 192.168.200.0/24).
Verification
1. The hosts and the server in VLAN 100 can ping one another successfully. The hosts and the server in VLAN 200 can ping one another successfully. The hosts or server in VLAN 100 cannot ping the hosts or server in VLAN 200, and vice versa.
2. Display protocol-based VLAN information on Device to check whether the configurations have become valid.
# Display protocol-based VLAN configuration on Device.
[Device-GigabitEthernet1/0/2] display protocol-vlan vlan all
VLAN ID:100
Protocol Index Protocol Type
======================================================
1 ipv4
VLAN ID:200
Protocol Index Protocol Type
======================================================
1 ipv6
# Display protocol-based VLAN information on the ports of Device.
[Device-GigabitEthernet1/0/2] display protocol-vlan interface all
Interface: GigabitEthernet 1/0/1
VLAN ID Protocol Index Protocol Type
======================================================
100 1 ipv4
200 1 ipv6
Interface: GigabitEthernet 1/0/2
VLAN ID Protocol Index Protocol Type
======================================================
100 1 ipv4
200 1 ipv6
Configuration guidelines
Protocol-based VLAN configuration applies to hybrid ports only.
Displaying and maintaining VLAN
|
To do... |
Use the command… |
Remarks |
|
Display VLAN information |
display vlan [ vlan-id1 [ to vlan-id2 ] | all | dynamic | reserved | static ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display VLAN interface information |
display interface [ vlan-interface ] [ brief [ down ] ] [ | { begin | exclude | include } regular-expression ] display interface vlan-interface vlan-interface-id [ brief ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display hybrid ports or trunk ports on the device |
display port { hybrid | trunk } [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display MAC address-to-VLAN entries |
display mac-vlan { all | dynamic | mac-address mac-address [ mask mac-mask ] | static | vlan vlan-id } [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display all interfaces with MAC-based VLAN enabled |
display mac-vlan interface [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display protocol information and protocol indexes of the specified VLANs |
display protocol-vlan vlan { vlan-id [ to vlan-id ] | all } [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display protocol-based VLAN information on specified interfaces |
display protocol-vlan interface { interface-type interface-number [ to interface-type interface-number ] | all } [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Clear statistics on a port |
reset counters interface vlan-interface [ vlan-interface-id ] |
Available in user view |
This chapter includes these sections:
· Overview
· Displaying and maintaining voice VLAN
· Voice VLAN configuration examples
|
|
NOTE: · The term "switch" or "device" in this chapter refers to the switching engine on a WX3000E wireless switch. · The WX3000E series comprises WX3024E and WX3010E wireless switches. · The port numbers in this chapter are for illustration only. |
Overview
As voice communication technologies grow more mature, voice devices are more and more widely deployed, especially on broadband networks, where voice traffic and data traffic often co-exist. Usually, compared to data traffic, voice traffic is given a higher transmission priority for the purpose of reducing transmission delay and packet loss.
A voice VLAN is configured especially for voice traffic. After assigning the ports connecting to voice devices to a voice VLAN, the system automatically configures quality of service (QoS) parameters for voice traffic, improving the transmission priority of voice traffic and ensuring voice quality.
|
|
NOTE: Common voice devices include IP phones and integrated access devices (IADs). Only IP phones are used in the voice VLAN configuration examples in this chapter. |
OUI addresses
A device determines whether a received packet is a voice packet by checking its source MAC address. A packet whose source MAC address complies with the voice device’s Organizationally Unique Identifier (OUI) address is regarded as voice traffic.
You can configure the OUI addresses of a device in advance or use the default OUI addresses. Table 1 lists the default OUI address for each vendor’s devices.
Table 1 The default OUI addresses of different vendors
|
Number |
OUI address |
Vendor |
|
|
|
1 |
0001-E300-0000 |
Siemens phone |
||
|
2 |
0003-6B00-0000 |
Cisco phone |
||
|
3 |
0004-0D00-0000 |
Avaya phone |
||
|
4 |
00D0-1E00-0000 |
Pingtel phone |
||
|
5 |
0060-B900-0000 |
Philips/NEC phone |
||
|
6 |
00E0-7500-0000 |
Polycom phone |
||
|
7 |
00E0-BB00-0000 |
3Com phone |
||
|
|
NOTE: · In general, as the first 24 bits of a MAC address (in binary format), an OUI address is a globally unique identifier assigned to a vendor by IEEE. OUI addresses mentioned in this document, however, are different from those in common sense. OUI addresses in this document are used by the system to determine whether a received packet is a voice packet. They are the results of the AND operation of the two arguments mac-address and oui-mask in the voice vlan mac-address command. · You can remove the default OUI address of a device manually and then add new ones manually. |
Voice VLAN assignment modes
A port can be assigned to a voice VLAN in one of the following modes:
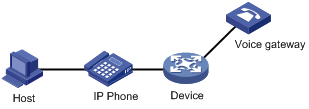
· In automatic mode, the system matches the source MAC address carried in the untagged packets sent when an IP phone is powered on against the device’s OUI addresses. If a match is found, the system automatically assigns the receiving port to the voice VLAN, issues ACL rules and configures the packet precedence. You can configure voice VLAN aging time on the device. The system will remove a port from the voice VLAN if no packet is received from the port during the aging time. Assigning/removing ports to/from a voice VLAN are automatically performed by the system. The automatic mode is suitable for scenarios where PCs and IP phones connected in series access the network through the device and ports on the device transmit both voice traffic and data traffic at the same time, as shown in Figure 8. When the voice VLAN works normally, in case of a system reboot, the system reassigns ports in automatic voice VLAN assignment mode to the voice VLAN after the reboot, ensuring that existing voice connections can work normally. Port assignment to the voice VLAN is not triggered by voice traffic streams.
Figure 8 PCs and IP phones connected in series access the network
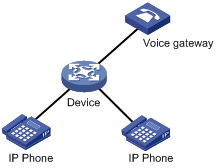
· In manual mode, you need to manually assign an IP phone accessing port to a voice VLAN. Then, the system matches the source MAC addresses carried in the packets against the device’s OUI addresses. If a match is found, the system issues ACL rules and configures the packet precedence. In this mode, assigning/removing ports to/from a voice VLAN are performed manually. The manual mode is suitable for scenarios where only IP phones access the network through the device and ports on the device only transmit voice traffic, as shown in Figure 9. In this mode, ports assigned to a voice VLAN transmit voice traffic exclusively, which prevents the impact of data traffic on the transmission of voice traffic.
Figure 9 Only IP phones access the network
Both modes forward tagged packets according to their tags.
Table 2 and Table 3 list the required configurations on ports of different link types in order for these ports to support tagged or untagged voice traffic sent from IP phones when different voice VLAN assignment modes are configured.
· IP phones send tagged voice traffic
|
Port link type |
Voice VLAN assignment mode |
Support for tagged voice traffic |
Configuration requirements |
|
Access |
Automatic |
No |
— |
|
Manual |
|||
|
Trunk |
Automatic |
Yes |
The PVID of the port cannot be the voice VLAN. |
|
Manual |
The PVID of the port cannot be the voice VLAN. Configure the port to permit packets of the voice VLAN to pass through. |
||
|
Hybrid |
Automatic |
Yes |
The PVID of the port cannot be the voice VLAN. |
|
Manual |
The PVID of the port cannot be the voice VLAN. Configure the port to permit packets of the voice VLAN to pass through tagged. |
· IP phones send untagged voice traffic
When IP phones send untagged voice traffic, you can only configure the voice traffic receiving ports on the device to operate in manual voice VLAN assignment mode.
|
Port link type |
Voice VLAN assignment mode |
Support for untagged voice traffic |
Configuration requirements |
|
Access |
Automatic |
No |
— |
|
Manual |
Yes |
Configure the PVID of the port as the voice VLAN. |
|
|
Trunk |
Automatic |
No |
— |
|
Manual |
Yes |
Configure the PVID of the port as the voice VLAN and assign the port to the voice VLAN. |
|
|
Hybrid |
Automatic |
No |
— |
|
Manual |
Yes |
Configure the PVID of the port as the voice VLAN and configure the port to permit packets of the voice VLAN to pass through untagged. |
|
|
CAUTION: · If an IP phone sends tagged voice traffic and its accessing port is configured with 802.1X authentication and guest VLAN, you should assign different VLAN IDs for the voice VLAN, the PVID of the connecting port, and the 802.1X guest VLAN. · If an IP phone sends untagged voice traffic, to implement the voice VLAN feature, you must configure the PVID of the IP phone’s accessing port as the voice VLAN. As a result, 802.1X authentication cannot be implemented. |
|
|
NOTE: · The PVID is VLAN 1 for all ports by default. You can configure the PVID of a port and assign a port to certain VLANs by using commands. For more information, see the chapter “VLAN configuration.” · Use the display interface command to display the PVID of a port and the VLANs to which the port is assigned. |
Security mode and normal mode of voice VLANs
Depending on their inbound packet filtering mechanisms, voice VLAN-enabled ports operate in the following modes:
· Normal mode: In this mode, voice VLAN-enabled ports receive packets carrying the voice VLAN tag and forward packets in the voice VLAN without checking their source MAC addresses against the OUI addresses configured for the device. If the PVID of the port is the voice VLAN and the port works in manual VLAN assignment mode, the port forwards all received untagged packets in the voice VLAN. In normal mode, the voice VLANs are vulnerable to traffic attacks. Vicious users may forge a large amount of voice packets and send them to the device to consume the voice VLAN bandwidth, affecting normal voice communication.
· Security mode: In this mode, only voice packets whose source MAC addresses match the recognizable OUI addresses can pass through the voice VLAN-enabled inbound port, but all other packets are dropped.
In a safe network, you can configure the voice VLANs to operate in normal mode, reducing the consumption of system resources due to source MAC addresses checking.
|
|
TIP: H3C does not recommend you transmit both voice traffic and non-voice traffic in a voice VLAN. If you have to, ensure that the voice VLAN security mode is disabled. |
Table 4 How a voice VLAN-enabled port processes packets in security/normal mode
|
Voice VLAN mode |
Packet type |
Packet processing mode |
|
Security mode |
Untagged packets |
If the source MAC address of a packet matches an OUI address configured for the device, it is forwarded in the voice VLAN; otherwise, it is dropped. |
|
Packets carrying the voice VLAN tag |
||
|
Packets carrying other tags |
Forwarded or dropped depending on whether the port allows packets of these VLANs to pass through |
|
|
Normal mode |
Untagged packets |
The port does not check the source MAC addresses of inbound packets. In this way, both voice traffic and non-voice traffic can be transmitted in the voice VLAN. |
|
Packets carrying the voice VLAN tag |
||
|
Packets carrying other tags |
Forwarded or dropped depending on whether the port allows packets of these VLANs to pass through |
Configuring a voice VLAN
Configuration prerequisites
Before you configure a voice VLAN, complete the following tasks:
· Create a VLAN.
· Configure QoS priority settings for voice VLAN traffic on an interface before enabling voice VLAN on the interface.
If the configuration order is reversed, your priority configuration will fail. For more information, see “Configuring QoS priority settings for voice traffic on an interface.”
· Configure the voice VLAN assignment mode.
For more information, see “Configuring a port to operate in automatic voice VLAN assignment mode” and “Configuring a port to operate in manual voice VLAN assignment mode.”
|
|
NOTE: · A port can be configured with only one voice VLAN. · You cannot enable the voice VLAN function on a port enabled with Link Aggregation Control Protocol (LACP). |
Configuring QoS priority settings for voice traffic on an interface
In voice VLAN applications, you can improve the quality of voice traffic by configuring the appropriate QoS priority settings, including the Class of Service (CoS) and Differentiated Services Code Point (DSCP) values, for voice traffic. Voice traffic carries its own QoS priority settings. You can configure the device either to modify or not to modify the QoS priority settings carried by incoming voice traffic.
Follow these steps to configure QoS priority settings for voice traffic:
|
To do... |
Use the command... |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter interface view |
interface interface-type interface-number |
— |
|
Configure the interface to trust the QoS priority settings in incoming voice traffic, but not to modify the CoS and DSCP values marked for incoming traffic of the voice VLAN |
voice vlan qos trust |
Required Use either command By default, an interface modifies the CoS value and the DSCP value marked for voice VLAN traffic into 6 and 46 respectively. The voice vlan qos command and the voice vlan qos trust command can overwrite each other, whichever is configured last. |
|
Configure the interface to modify the CoS and DSCP values marked for incoming traffic of the voice VLAN into specified values |
voice vlan qos cos-value dscp-value |
|
|
NOTE: Configure the QoS priority settings for voice traffic on an interface before enabling voice VLAN on the interface. If the configuration order is reversed, your priority trust setting will fail. |
Configuring a port to operate in automatic voice VLAN assignment mode
Follow these steps to set a port to operate in automatic voice VLAN assignment mode:
|
To do... |
Use the command... |
Remarks |
|
Enter system view |
system-view |
— |
|
Set the voice VLAN aging time |
voice vlan aging minutes |
Optional By default, the aging time of a voice VLAN is 1440 minutes. The voice VLAN aging time configuration is only applicable on ports in automatic voice VLAN assignment mode. |
|
Enable the voice VLAN security mode |
voice vlan security enable |
Optional By default, the voice VLAN security mode is enabled. |
|
Add a recognizable OUI address |
voice vlan mac-address oui mask oui-mask [ description text ] |
Optional By default, each voice VLAN has default OUI addresses configured. For the default OUI addresses of different vendors, see Table 1. |
|
Enter Ethernet interface view |
interface interface-type interface-number |
— |
|
Configure the port to operate in automatic voice VLAN assignment mode |
voice vlan mode auto |
Optional By default, the automatic voice VLAN assignment mode is enabled. The voice VLAN assignment modes on different ports are independent of one another. |
|
Enable the voice VLAN feature |
voice vlan vlan-id enable |
Required |
|
|
NOTE: A protocol-based VLAN on a hybrid port can process only untagged inbound packets, whereas the voice VLAN in automatic mode on a hybrid port can process only tagged voice traffic. Do not configure a VLAN as both a protocol-based VLAN and a voice VLAN. For more information, see the chapter “VLAN configuration.” |
Configuring a port to operate in manual voice VLAN assignment mode
Follow these steps to set a port to operate in manual voice VLAN assignment mode:
|
To do... |
Use the command... |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable the voice VLAN security mode |
voice vlan security enable |
Optional By default, the voice VLAN security mode is enabled. |
|
Add a recognizable OUI address |
voice vlan mac-address oui mask oui-mask [ description text ] |
Optional By default, each voice VLAN has default OUI addresses configured. For the default OUI addresses of different vendors, see Table 1. |
|
Enter interface view |
interface interface-type interface-number |
— |
|
Configure the port to operate in manual voice VLAN assignment mode |
undo voice vlan mode auto |
Required By default, the manual voice VLAN assignment mode is disabled. |
|
Assign the access, trunk, or hybrid port in manual voice VLAN assignment mode to the voice VLAN |
For the configuration procedure, see the chapter “VLAN configuration.” |
Required After you assign an access port to the voice VLAN, the voice VLAN becomes the PVID of the port automatically. |
|
Configure the voice VLAN as the PVID of the trunk or hybrid port |
For the configuration procedure, see the chapter “VLAN configuration.” |
Optional This operation is required for untagged inbound voice traffic and prohibited for tagged inbound voice traffic. |
|
Enable voice VLAN on the port |
voice vlan vlan-id enable |
Required Disabled by default. |
|
|
NOTE: · You can configure different voice VLANs on different ports at the same time. However, one port can be configured with only one voice VLAN, and this voice VLAN must be a static VLAN that already exists on the device. · You cannot enable the voice VLAN function on a port enabled with Link Aggregation Control Protocol (LACP). · To make voice VLAN take effect on a port that is enabled with voice VLAN and operates in manual voice VLAN assignment mode, you need to assign the port to the voice VLAN manually. |
Displaying and maintaining voice VLAN
|
To do... |
Use the command... |
Remarks |
|
Display the voice VLAN state |
display voice vlan state [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display the OUI addresses supported by system |
display voice vlan oui [ | { begin | exclude | include } regular-expression ] |
Available in any view |
Voice VLAN configuration examples
Automatic voice VLAN mode configuration example
Network requirements
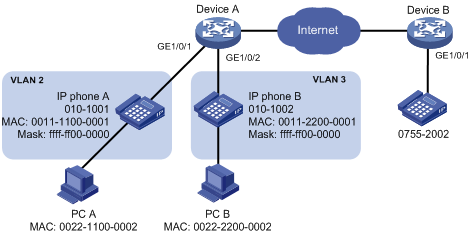
As shown in Figure 10,
· The MAC address of IP phone A is 0011-1100-0001. The phone connects to a downstream device named PC A whose MAC address is 0022-1100-0002 and to Ethernet 1/1 on an upstream device named Device A.
· The MAC address of IP phone B is 0011-2200-0001. The phone connects to a downstream device named PC B whose MAC address is 0022-2200-0002 and to Ethernet 1/2 on Device A.
· Device A uses voice VLAN 2 to transmit voice packets for IP phone A and voice VLAN 3 to transmit voice packets for IP phone B.
· Configure Ethernet 1/1 and Ethernet 1/2 to work in automatic voice VLAN assignment mode. In addition, if one of them has not received any voice packet in 30 minutes, the port is removed from the corresponding voice VLAN automatically.
Figure 10 Network diagram for automatic voice VLAN assignment mode configuration
Configuration procedure
# Create VLAN 2.
<DeviceA> system-view
[DeviceA] vlan 2
Please wait... Done.
# Set the voice VLAN aging time to 30 minutes.
[DeviceA] voice vlan aging 30
# Since GigabitEthernet 1/0/1 may receive both voice traffic and data traffic at the same time, to ensure the quality of voice packets and effective bandwidth use, configure voice VLANs to work in security mode. Configure the voice VLANs to transmit only voice packets. By default, voice VLANs work in security mode. (Optional)
[DeviceA] voice vlan security enable
# Configure the allowed OUI addresses as MAC addresses prefixed by 0011-1100-0000 or 0011-2200-0000. In this way, Device A identifies packets whose MAC addresses match any of the configured OUI addresses as voice packets.
[DeviceA] voice vlan mac-address 0011-1100-0001 mask ffff-ff00-0000 description IP phone A
[DeviceA] voice vlan mac-address 0011-2200-0001 mask ffff-ff00-0000 description IP phone B
# Configure GigabitEthernet 1/0/1 as a hybrid port.
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] port link-type hybrid
# Configure GigabitEthernet 1/0/1 to operate in automatic voice VLAN assignment mode. By default, a port operates in automatic voice VLAN assignment mode. (Optional)
[DeviceA-GigabitEthernet1/0/1] voice vlan mode auto
# Configure VLAN 2 as the voice VLAN for GigabitEthernet 1/0/1.
[DeviceA-GigabitEthernet1/0/1] voice vlan 2 enable
[DeviceA-GigabitEthernet1/0/1] quit
Verification
# Display the OUI addresses, OUI address masks, and description strings.
<DeviceA> display voice vlan oui
Oui Address Mask Description
0001-e300-0000 ffff-ff00-0000 Siemens phone
0003-6b00-0000 ffff-ff00-0000 Cisco phone
0004-0d00-0000 ffff-ff00-0000 Avaya phone
0011-1100-0000 ffff-ff00-0000 IP phone A
0011-2200-0000 ffff-ff00-0000 IP phone B
0060-b900-0000 ffff-ff00-0000 Philips/NEC phone
00d0-1e00-0000 ffff-ff00-0000 Pingtel phone
00e0-7500-0000 ffff-ff00-0000 Polycom phone
00e0-bb00-0000 ffff-ff00-0000 3com phone
# Display the states of voice VLANs.
<DeviceA> display voice vlan state
Maximum of Voice VLANs: 1
Current Voice VLANs: 1
Voice VLAN security mode: Security
Voice VLAN aging time: 30 minutes
Voice VLAN enabled port and its mode:
PORT VLAN MODE COS DSCP
--------------------------------------------------------------------
GigabitEthernet1/0/1 2 AUTO 6 46
GigabitEthernet1/0/2 2 AUTO 6 46
Manual voice VLAN assignment mode configuration example
Network requirements
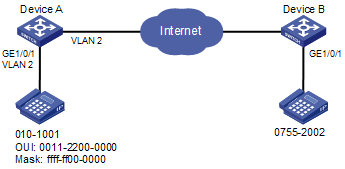
As shown in Figure 11,
· Create VLAN 2 and configure it as a voice VLAN permitting only voice traffic to pass through.
· The IP phones send untagged voice traffic. Configure GigabitEthernet 1/0/1 as a hybrid port.
· Configure GigabitEthernet 1/0/1 to operate in manual voice VLAN assignment mode. Configure GigabitEthernet 1/0/1 to allow voice traffic with an OUI address of 0011-2200-0000, a mask of ffff-ff00-0000, and a description string of test to be forwarded in the voice VLAN.
Figure 11 Network diagram for manual voice VLAN assignment mode configuration
Configuration procedure
# Configure the voice VLAN to operate in security mode. A voice VLAN operates in security mode by default. (Optional)
<DeviceA> system-view
[DeviceA] voice vlan security enable
# Add a recognizable OUI address 0011-2200-0000.
[DeviceA] voice vlan mac-address 0011-2200-0000 mask ffff-ff00-0000 description test
# Create VLAN 2.
[DeviceA] vlan 2
[DeviceA-vlan2] quit
# Configure GigabitEthernet 1/0/1 to operate in manual voice VLAN assignment mode.
[DeviceA] interface ethernet 1/1
[DeviceA-Ethernet1/1] undo voice vlan mode auto
# Configure GigabitEthernet 1/0/1 as a hybrid port.
[DeviceA-Ethernet1/1] port link-type hybrid
# Configure the voice VLAN (VLAN 2) as the PVID of GigabitEthernet 1/0/1 and configure GigabitEthernet 1/0/1 to permit the voice traffic of VLAN 2 to pass through untagged.
[DeviceA-Ethernet1/1] port hybrid pvid vlan 2
[DeviceA-Ethernet1/1] port hybrid vlan 2 untagged
# Enable voice VLAN on GigabitEthernet 1/0/1.
[DeviceA-Ethernet1/1] voice vlan 2 enable
Verification
# Display the OUI addresses, OUI address masks, and description strings.
<DeviceA> display voice vlan oui
Oui Address Mask Description
0001-e300-0000 ffff-ff00-0000 Siemens phone
0003-6b00-0000 ffff-ff00-0000 Cisco phone
0004-0d00-0000 ffff-ff00-0000 Avaya phone
0011-2200-0000 ffff-ff00-0000 test
00d0-1e00-0000 ffff-ff00-0000 Pingtel phone
0060-b900-0000 ffff-ff00-0000 Philips/NEC phone
00e0-7500-0000 ffff-ff00-0000 Polycom phone
00e0-bb00-0000 ffff-ff00-0000 3com phone
# Display the states of voice VLANs.
<DeviceA> display voice vlan state
Maximum of Voice VLANs: 1
Current Voice VLANs: 1
Voice VLAN security mode: Security
Voice VLAN aging time: 1440 minutes
Voice VLAN enabled port and its mode:
PORT VLAN MODE COS DSCP
--------------------------------------------------------------------
GigabitEthernet1/0/1 2 MANUAL 6 46
